Analysis on the Performance of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles in Dual-Hop Emergency Wireless Communication Systems under the Jamming of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles
Abstract
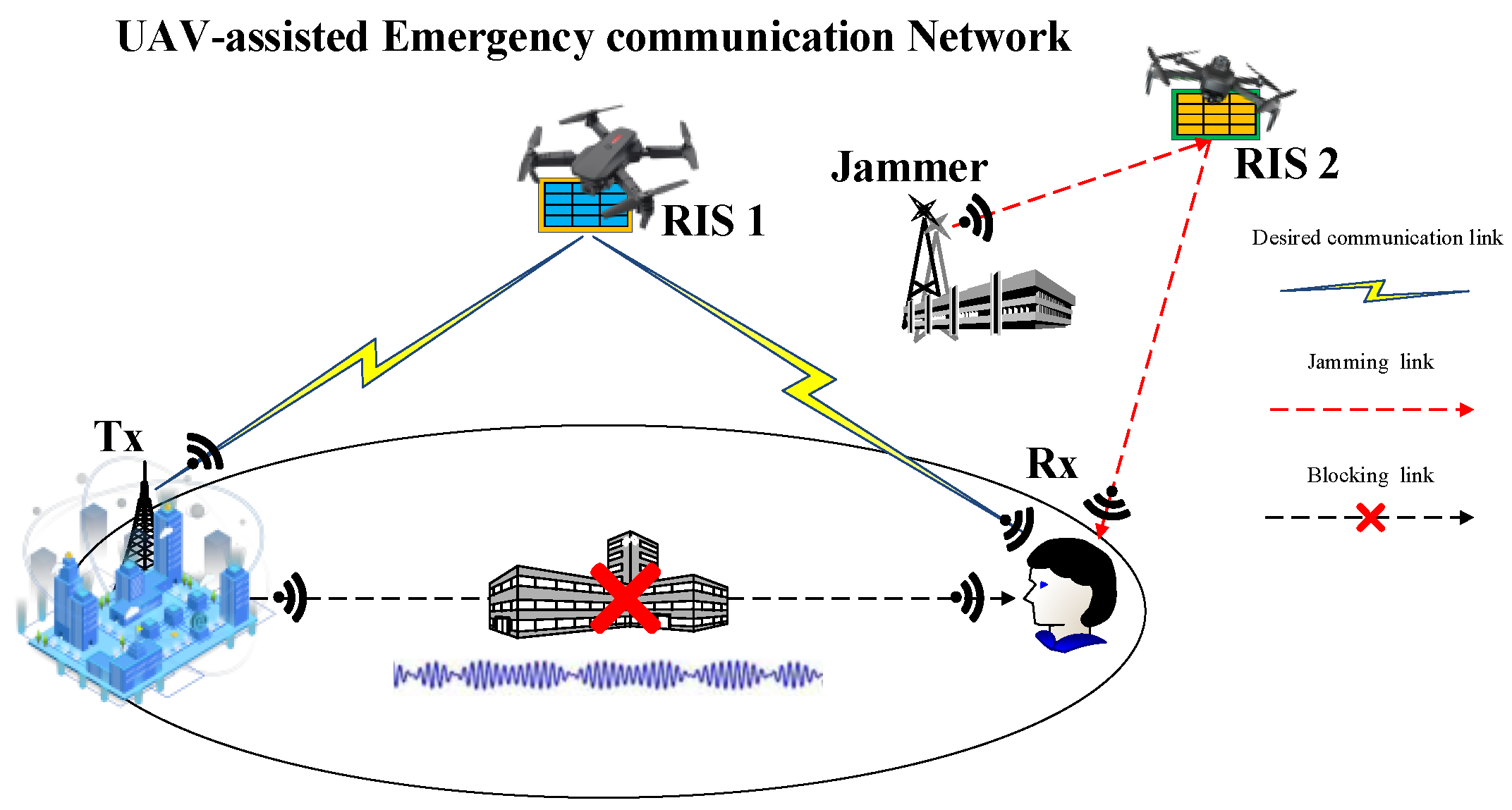
1. Introduction
- We derived and presented a closed-form expression for the probability density function (PDF) of the legitimate channel and jamming channel in the RIS-Equipped UAV dual-hop wireless communication systems. Additionally, we derived a novel closed-form expression for the PDF of the received signal-to jamming ratio (SJR).
- Using the Gauss–Laguerre Approximation, we derived expressions for the ABER under BPSK and QAM modulation.
- We analyzed the effects of jamming probability, the location of the legitimate RIS, and different channel conditions on the performance of the ABER through analytical and simulation results.
2. System and Channel Models
3. ABER Analysis
3.1. BPSK
3.2. QAM
4. Numerical Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
References
- Jian, M.; Alexandropoulos, G.C.; Basar, E.; Huang, C.; Liu, R.; Liu, Y.; Yuen, C. Reconfigurable intelligent surfaces for wireless communications: Overview of hardware designs, channel models, and estimation techniques. Intell. Converg. Netw. 2022, 3, 1–32. [Google Scholar] [CrossRef]
- Wang, J.; Gao, D.; Li, J.; Huang, L.; Ding, H.; Zhou, S. Analysis and Mitigating Methods for Jamming in the Optical Reconfigurable Intelligent Surfaces-Assisted Dual-Hop FSO Communication Systems. Electronics 2024, 13, 1730. [Google Scholar] [CrossRef]
- Yuan, X.; Zhang, Y.-J.A.; Shi, Y.; Yan, W.; Liu, H. Reconfigurable-intelligent-surface empowered wireless communications: Challenges and opportunities. IEEE Wirel. Commun. 2021, 28, 136–143. [Google Scholar]
- Cao, K.; Ding, H.; Lv, L.; Su, Z.; Tao, J.; Gong, F.; Wang, B. Physical Layer Security for Intelligent Reflecting Surface aided Wireless Powered Communication. IEEE Internet Things J. 2023, 10, 18097–18110. [Google Scholar] [CrossRef]
- Chen, Q.; Guo, Z.; Meng, W.; Han, S.; Li, C.; Quek, T.Q. A Survey on Resource Management in Joint Communication and Computing-Embedded SAGIN. arXiv 2024, arXiv:2403.17400. [Google Scholar] [CrossRef]
- Khoshafa, M.H.; Maraqa, O.; Moualeu, J.M.; Aboagye, S.; Ngatched, T.; Ahmed, M.H.; Gadallah, Y.; Di Renzo, M. RIS-Assisted Physical Layer Security in Emerging RF and Optical Wireless Communication Systems: A Comprehensive Survey. arXiv 2024, arXiv:2403.10412. [Google Scholar]
- Basharat, S.; Hassan, S.A.; Pervaiz, H.; Mahmood, A.; Ding, Z.; Gidlund, M. Reconfigurable intelligent surfaces: Potentials, applications, and challenges for 6G wireless networks. IEEE Wirel. Commun. 2021, 28, 184–191. [Google Scholar] [CrossRef]
- ElMossallamy, M.A.; Zhang, H.; Song, L.; Seddik, K.G.; Han, Z.; Li, G.Y. Reconfigurable intelligent surfaces for wireless communications: Principles, challenges, and opportunities. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 990–1002. [Google Scholar] [CrossRef]
- Pan, C.; Zhou, G.; Zhi, K.; Hong, S.; Wu, T.; Pan, Y.; Ren, H.; Di Renzo, M.; Swindlehurst, A.L.; Zhang, R. An overview of signal processing techniques for RIS/IRS-aided wireless systems. IEEE J. Sel. Top. Signal Process. 2022, 16, 883–917. [Google Scholar] [CrossRef]
- Hameed, I.; Koo, I. Enhancing Throughput in IoT Networks: The Impact of Active RIS on Wireless Powered Communication Systems. Electronics 2024, 13, 1402. [Google Scholar] [CrossRef]
- Sikander, M.; Butt, F.A.; Chattha, J.N.; Naqvi, I.H. Improving Wireless Communication through Beamwidth Optimization in Reconfigurable Intelligent Surfaces. In Proceedings of the 2023 10th International Conference on Wireless Networks and Mobile Communications (WINCOM), Istanbul, Turkey, 26–28 October 2023; pp. 1–5. [Google Scholar]
- Renzo, M.D.; Danufane, F.H.; Tretyakov, S. Communication Models for Reconfigurable Intelligent Surfaces: From Surface Electromagnetics to Wireless Networks Optimization. Proc. IEEE 2022, 110, 1164–1209. [Google Scholar] [CrossRef]
- Dao, N.-N.; Pham, Q.-V.; Tu, N.H.; Thanh, T.T.; Bao, V.N.Q.; Lakew, D.S.; Cho, S. Survey on aerial radio access networks: Toward a comprehensive 6G access infrastructure. IEEE Commun. Surv. Tutor. 2021, 23, 1193–1225. [Google Scholar] [CrossRef]
- Nguyen, V.-L.; Lin, P.-C.; Cheng, B.-C.; Hwang, R.-H.; Lin, Y.-D. Security and privacy for 6G: A survey on prospective technologies and challenges. IEEE Commun. Surv. Tutor. 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Rodriguez, J.; Verikoukis, C.; Vardakas, J.S.; Passas, N. Enabling 6G Mobile Networks; Springer: New York, NY, USA, 2022. [Google Scholar]
- Saqib, N.U.; Haroon, M.S.; Lee, H.Y.; Park, K.; Song, H.-G.; Jeon, S.-W. THz Communications: A Key Enabler for Future Cellular Networks. IEEE Access 2023, 11, 117474–117493. [Google Scholar] [CrossRef]
- Huang, J.; Wang, C.-X.; Sun, Y.; Feng, R.; Huang, J.; Guo, B.; Zhong, Z.; Cui, T.J. Reconfigurable intelligent surfaces: Channel characterization and modeling. Proc. IEEE 2022, 110, 1290–1311. [Google Scholar] [CrossRef]
- Amri, M.M.; Tran, N.M.; Park, J.H.; Kim, D.I.; Choi, K.W. Sparsity-Aware Channel Estimation for Fully Passive RIS-Based Wireless Communications: Theory to Experiments. IEEE Internet Things J. 2022, 10, 8046–8067. [Google Scholar] [CrossRef]
- Fu, X.; Peng, R.; Liu, G.; Wang, J.; Yuan, W.; Kadoch, M. Channel modeling for RIS-assisted 6G communications. Electronics 2022, 11, 2977. [Google Scholar] [CrossRef]
- Sikri, A.; Mathur, A.; Kaddoum, G. Joint impact of phase error, transceiver hardware impairments, and mobile interferers on RIS-aided wireless system over κ-μ fading channels. IEEE Commun. Lett. 2022, 26, 2312–2316. [Google Scholar] [CrossRef]
- Yang, L.; Li, P.; Yang, Y.; Li, S.; Trigui, I.; Ma, R. Performance analysis of RIS-aided networks with co-channel interference. IEEE Commun. Lett. 2021, 26, 49–53. [Google Scholar] [CrossRef]
- Xu, J.; Zuo, J.; Zhou, J.T.; Liu, Y. Active Simultaneously Transmitting and Reflecting (STAR)-RISs: Modeling and Analysis. IEEE Commun. Lett. 2023, 27, 2466–2470. [Google Scholar] [CrossRef]
- Zhou, G.; Pan, C.; Ren, H.; Wang, K.; Peng, Z. Secure Wireless Communication in RIS-Aided MISO System with Hardware Impairments. IEEE Wirel. Commun. Lett. 2021, 10, 1309–1313. [Google Scholar] [CrossRef]
- Sikri, A.; Mathur, A.; Verma, G.; Kaddoum, G. Distributed RIS-based dual-hop mixed FSO-RF systems with RIS-aided jammer. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall) (IEEE2021), Virtual, 27–30 September 2021; pp. 1–5. [Google Scholar]
- Adoni, W.Y.H.; Lorenz, S.; Fareedh, J.S.; Gloaguen, R.; Bussmann, M. Investigation of autonomous multi-UAV systems for target detection in distributed environment: Current developments and open challenges. Drones 2023, 7, 263. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Othman, N.Q.H.; Li, Y.; Alsharif, M.H.; Khan, M.A. Unmanned aerial vehicles (UAVs): Practical aspects, applications, open challenges, security issues, and future trends. Intell. Serv. Robot. 2023, 16, 109–137. [Google Scholar] [CrossRef] [PubMed]
- Saif, A.; Dimyati, K.; Noordin, K.A.; Mosali, N.A.; Deepak, G.; Alsamhi, S.H. Skyward bound: Empowering disaster resilience with multi-UAV-assisted B5G networks for enhanced connectivity and energy efficiency. Internet Things 2023, 23, 100885. [Google Scholar] [CrossRef]
- Sharma, A.; Vanjani, P.; Paliwal, N.; Basnayaka, C.M.W.; Jayakody, D.N.K.; Wang, H.-C.; Muthuchidambaranathan, P. Communication and networking technologies for UAVs: A survey. J. Netw. Comput. Appl. 2020, 168, 102739. [Google Scholar] [CrossRef]
- Qi, W.; Yang, C.; Song, Q.; Guan, Y.; Guo, L.; Jamalipour, A. Minimizing Age of Information for Hybrid UAV-RIS-Assisted Vehicular Networks. IEEE Internet Things J. 2024, 11, 17886–17895. [Google Scholar] [CrossRef]
- Pogaku, A.C.; Do, D.T.; Lee, B.M.; Nguyen, N.D. UAV-Assisted RIS for Future Wireless Communications: A Survey on Optimization and Performance Analysis. IEEE Access 2022, 10, 16320–16336. [Google Scholar] [CrossRef]
- Nikjah, R.; Beaulieu, N.C. Antijamming capacity and performance analysis of multiple access spread spectrum systems in AWGN and fading environments. In Proceedings of the 2006 IEEE International Conference on Communications (IEEE2006), Istanbul, Turkey, 11–15 June 2006; pp. 5153–5159. [Google Scholar]
- Park, S.; Stark, W.E. Performance analysis of concatenated convolutional codes for STBC systems in pulse jamming. In Proceedings of the 2014 IEEE Military Communications Conference (IEEE2014), Baltimore, MA, USA, 6–8 October 2014; pp. 1510–1515. [Google Scholar]
- Chen, Y.; Cheng, W.; Zhang, W. Reconfigurable Intelligent Surface Equipped UAV in Emergency Wireless Communications: A New Fading–Shadowing Model and Performance Analysis. IEEE Trans. Commun. 2024, 72, 1821–1834. [Google Scholar] [CrossRef]
- Arthur, A.G.; Allen, H.L. Digital Communications BER Performance in AWGN (BPSK in Fading). In Modeling of Digital Communication Systems Using SIMULINK; Wiley: New York, NY, USA, 2015; pp. 119–140. [Google Scholar]
- Ke, X.; Lu, N.; Lu, Z. The simulation of QAM modulation/demodulation and the performance analyse in the RoFSO system. Laser J. 2010, 31, 21–23. [Google Scholar]
- Abramowitz, M.; Stegun, I.A. Handbook of Mathematical Functions with Formulas, Graphs, and Mathematical Tables; US Govt. Print: Washington, DC, USA, 2006. [Google Scholar]







Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, J.; Wang, G.; Liu, J.; Wang, D.; Jin, H.; Zhou, J. Analysis on the Performance of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles in Dual-Hop Emergency Wireless Communication Systems under the Jamming of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles. Electronics 2024, 13, 2618. https://doi.org/10.3390/electronics13132618
Li J, Wang G, Liu J, Wang D, Jin H, Zhou J. Analysis on the Performance of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles in Dual-Hop Emergency Wireless Communication Systems under the Jamming of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles. Electronics. 2024; 13(13):2618. https://doi.org/10.3390/electronics13132618
Chicago/Turabian StyleLi, Juan, Gang Wang, Jiong Liu, Dan Wang, Hengzhou Jin, and Jing Zhou. 2024. "Analysis on the Performance of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles in Dual-Hop Emergency Wireless Communication Systems under the Jamming of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles" Electronics 13, no. 13: 2618. https://doi.org/10.3390/electronics13132618
APA StyleLi, J., Wang, G., Liu, J., Wang, D., Jin, H., & Zhou, J. (2024). Analysis on the Performance of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles in Dual-Hop Emergency Wireless Communication Systems under the Jamming of Reconfigurable Intelligent Surface-Equipped Unmanned Aerial Vehicles. Electronics, 13(13), 2618. https://doi.org/10.3390/electronics13132618





