1. Introduction
The Internet of things (IoT) provides a big picture and foundation for a new era. Diverse types of “things”, ranging from tiny chip-embedded physical objects to powerful computers, are allowed to connect and communicate with each other through the IoT [
1]. The IoT has attracted plenty of application implementations and protocol designs from industry and academia [
2]. Applications can run on the IoT, along with a set of supporting technologies, such as designated modifications of IPv6, network stacks with light-weight requirements for hardware, etc. Currently, there are still open issues in several areas, such as interoperation with different networks, heterogeneity adaption resolutions, efficient routing with hardware constraints, transmission security, and so on [
3,
4]. There are plenty of categories of IoT networks, among which the low-power and lossy network (LLN) was considered as a key target network scenario by the Routing over Low Power and Lossy Network Working Group (ROLL WG) of the Internet Engineering Task Force (IETF) (
https://datatracker.ietf.org/wg/roll/about/ (accessed on 5 February 2023)), which is an essential building block in the IoT-based infrastructure [
5].
LLN works with unstable connections and resource-constrained devices. The unstable connections cannot sustain reliable long-range communications, while the resource-constrained devices bring strong limitations in data computing and storage capabilities. In the designs of the routing protocol for LLN, all the above features play important roles, which makes conditions more limited than that in traditional host networks [
6]. In order to meet these challenges, the IPv6 routing protocol for low-power and lossy networks (RPL) [
7,
8] is proposed and adopted as a routing solution to the scenarios defined in IEEE 802.15.4e [
9]. In around 2009, RPL was discussed to perform as a routing protocol to meet the particular requirements of wireless sensor networks, through a gradient routing strategy [
10]. Specifically, IETF ROLL WG worked to implement it and proposed the early foundational works [
11,
12]. With continuous improvements, RPL was recognized as a standard for LLN in RFC 6550 [
13] in 2012.
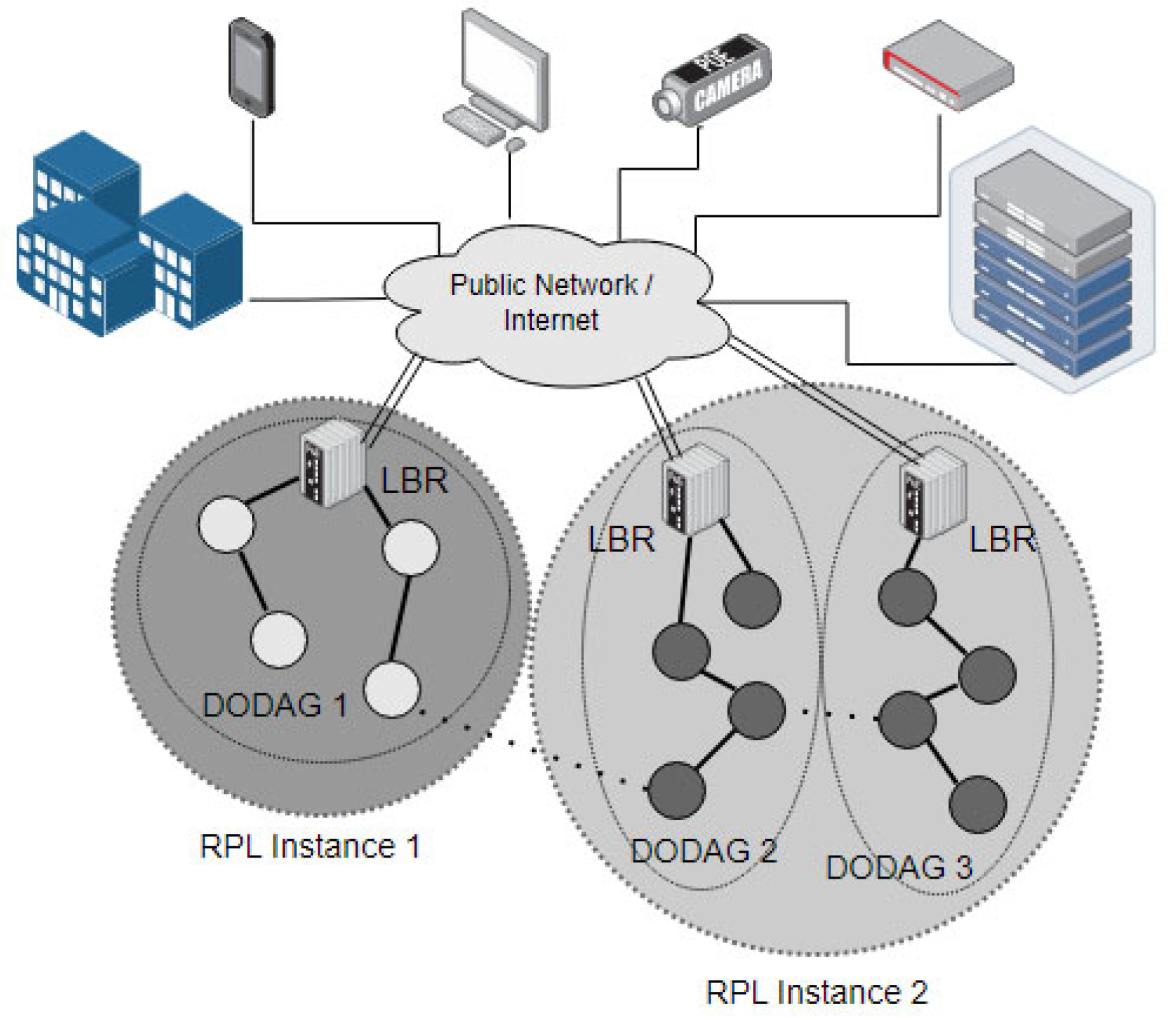
RPL adopts an ad hoc logical routing topology, which is based on, but different from, a physical device layer topology. The basic unit of RPL is an instance. One instance consists of one or more destination-oriented directed acyclic graphs (DODAGs) [
14,
15]. Each instance has different environment parameter settings, and a DODAG can be upgraded by issuing a new version number. Briefly, a DODAG is a directed acyclic graph anchored on a single root that is also called a LLN border router (LBR) [
16,
17]. LBR governs the internal RPL network, and also acts as a bridge to interoperate between the internal RPL network and the external IPv6 networks.
Figure 1 illustrates this high-level structure.
In the RFC 6550 [
13], RPL is designed with three in-built categories of communications: (1) point-to-point (P2P); (2) point-to-multipoint (P2MP); and (3) multipoint-to-point (MP2P) communications. Specifically, P2P refers to the data traffic from any node to any node, P2MP means the data traffic from root to multiple nodes, and MP2P indicates the data traffic from multiple nodes to root. Two distinct routing schemes, upward routing and downward routing, are proposed to support these communication patterns. Upward routing refers to the data flow from leaf node, through routers, to the root. On the contrary, the data flow from root to leaf nodes is defined as downward routing. MP2P is implemented by upward routing, P2MP utilizes downward routing. Finally, P2P adopts a combination of upward routing and downward routing.
However, that three types of communications are supported differently according to RFC 6550. Because upward routing is just sending messages to its preferred parent, which is already determined in the topology setting up stage, MP2P is a primitive scheme and receives efficient support from the standard. P2MP and P2P are also supported by the standard, but extraneous control mechanisms and huge control messages are required to perform, which causes the performances of both P2MP and P2P to subside. In conclusion, the performance of the MP2P communication pattern is completely supported in RFC 6550, whereas the supports to P2MP and P2P patterns are trivial.
Precisely, in upward routing, control information is transferred from children to their parent, then to the parent of the parent recursively until it reaches the root. Upward routing is deeply embedded with the DODAG formation process. When a DODAG is formed, an upward routing is established. As a counterpart, downward routing happens after or within a DODAG formation stage. Generally, downward routing drives data from a parent to its children, then to the children of the children recursively until to a destination node or a leaf node.
Furthermore, downward routing can be divided into two types of mode of operations (MOPs): storing mode and the non-storing mode. When a node starts to establish a downward routing, it sends destination advertisement object messages (DAOs) to its preferred parent, which includes all the information for finding a child. In the non-storing mode, a parent does not store or even not process the DAOs from its children. Instead, a parent forwards that DAOs to its parent up to the root. In this case, all downward routing information is stored in the root, and such a scheme is known as source routing. On the other hand, in storing mode, all the related parents extract and store the downward routing information of their subtrees from that DAOs. In summary, both MOPs require enough memory space in the nodes or root, which is a limitation on resource-constrained devices.
Due to the different levels of performance support to different data traffic patterns in RPL, in the networks adopting RPL as a routing protocol, MP2P communication with an upward routing scheme dominates the scenarios among such types [
18]. However, P2P communication is also an important component in certain LLN applications where a node needs to exchange data with another node [
19]. In a given deployment of RPL, RFC 6550 prescribes that all nodes must use the same MOP. So, it is compulsory to choose one of the two MOPs in a DODAG. This problem is termed the MOPs incompatibility problem in this article. Consequently, in a memory constrained LLN, the non-storing mode is preferred, which may reduce the requirement for the memory capacity of intermediate nodes. On the other hand, when memory is not a severe concern, the storing mode is a better choice for improving the downward routing performance by reducing unnecessary overhead.
In a network where only one MOP is required to work efficiently, there is no MOPs incompatibility problem. However, if two MOPs can be compatible in a heterogenous network, where different hardware configurations and performance expectations coexist, the efficiency of downward routing will be significantly improved. Because it can flexibly choose different MOPs according to the actual situation of each node to maintain the advantages of the two MOPs and avoid the disadvantages of both at the same time. Therefore, in order to achieve high performance of P2P communication, the related LLN applications prefer to solve the MOPs incompatibility problem in RPL to achieve the above objectives [
20]. How to support the two MOPs working in a single network is still an open issue. It is also the requirement for and the purpose of this research to propose an effective hybrid-MOPs solution to the MOPs incompatibility problem in RPL.
To achieve this hybrid-MOPs objective, we propose the try-the-best RPL (TB-RPL), where each node tries its best to store DAO messages to achieve high performance of downward routing in RPL. In a high-level description, all the nodes in TB-RPL should run in a single and uniformly fused mode by default. Two cases are defined based on a threshold α for the maximum number of route entries. The node stays in a normal case and stores children’s information normally if the memory space for route entries does not run out. Otherwise, the node enters a weak case and asks its preferred parent to help save that information. If this preferred parent also runs out of the space for route entries, it repeats the previous mechanism until the root obtains a request to help save the route information. In this design, there is no distinction between MOPs; put it in other words, the MOPs incompatibility problem is solved. All nodes perform in a single TB-RPL mode that includes the consistent logic and the same working context.
Furthermore, based on the proposed TB-RPL, the RPL reliability is improved to some extent. Specifically, the downward routing collapse problem in the non-storing mode caused by DODAG root failure is relieved. In the non-storing mode, the downward routes of all nodes are stored by a root. If a root fails (even if temporarily), all the downward routings are broken, which is termed the DODAG root failure problem in this article. In TB-RPL, it allows for not relaying all P2P traffic through the root. So, in case of a DODAG root failure, the root’s immediate children can take over the root duty in their own subtree. This process can be performed recursively. That means part of the DODAG can still work when the DODAG root failure problem occurs. In conclusion, TB-RPL mitigates the DODAG root failure problem, and consequently improves the RPL reliability.
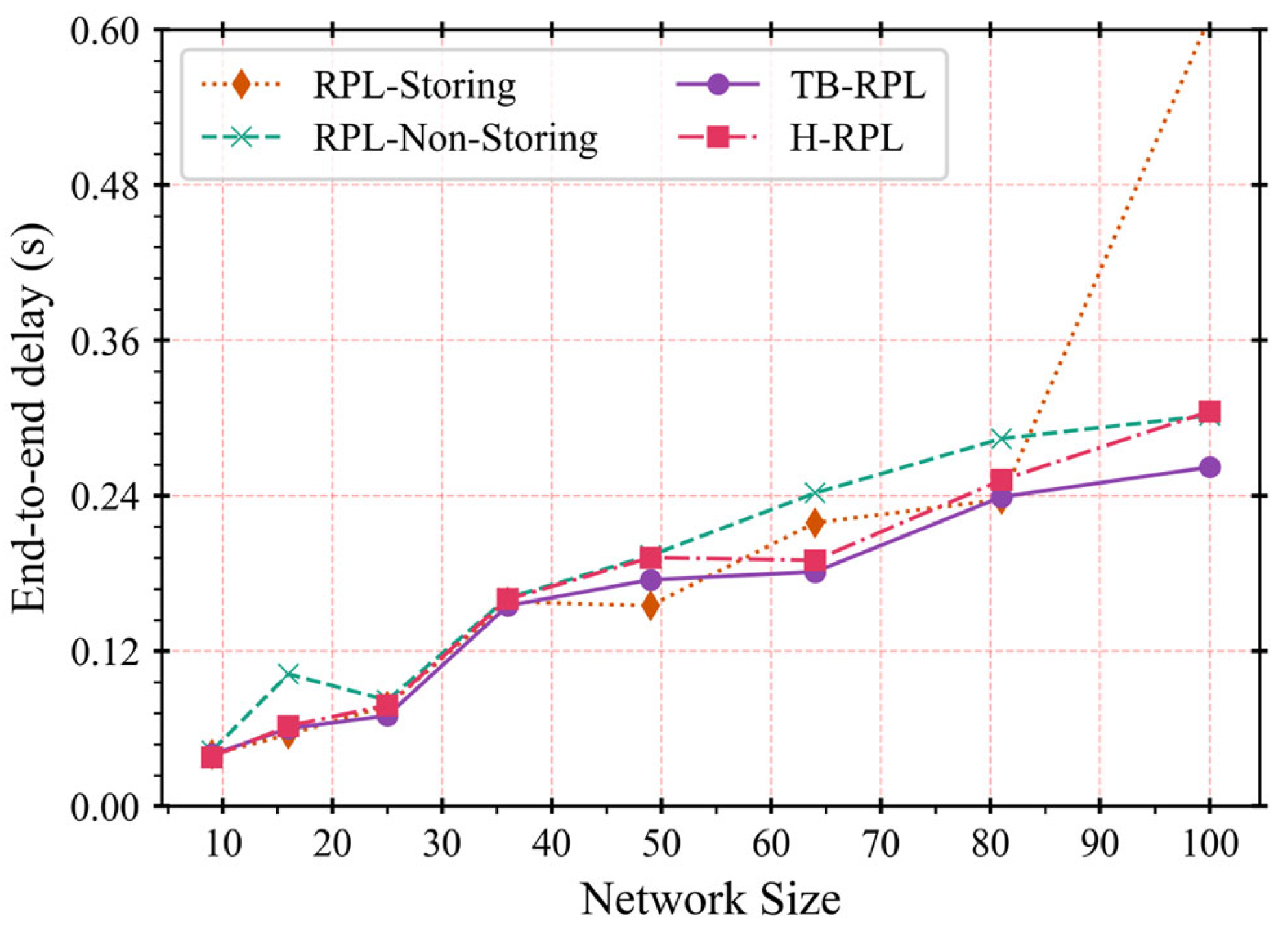
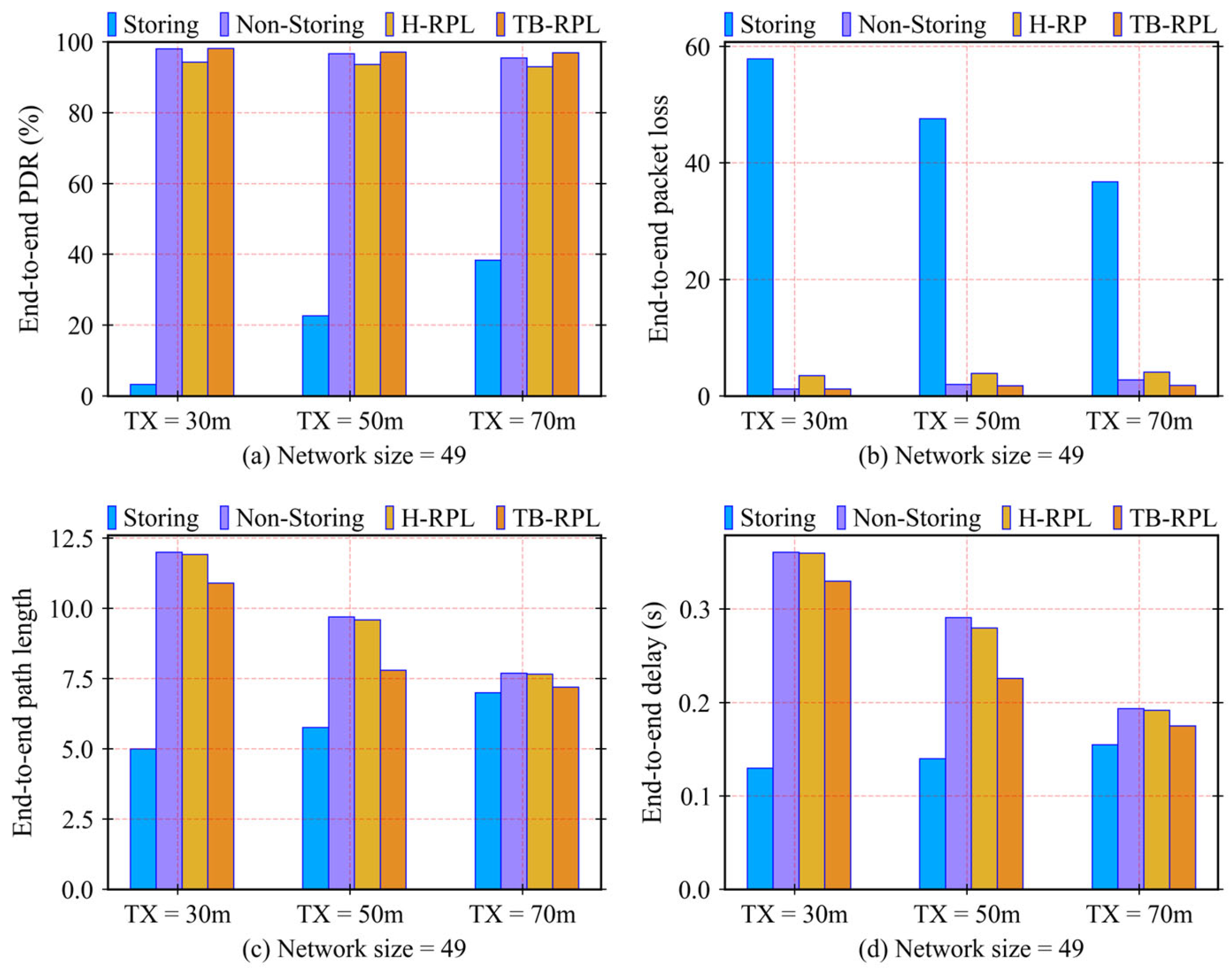
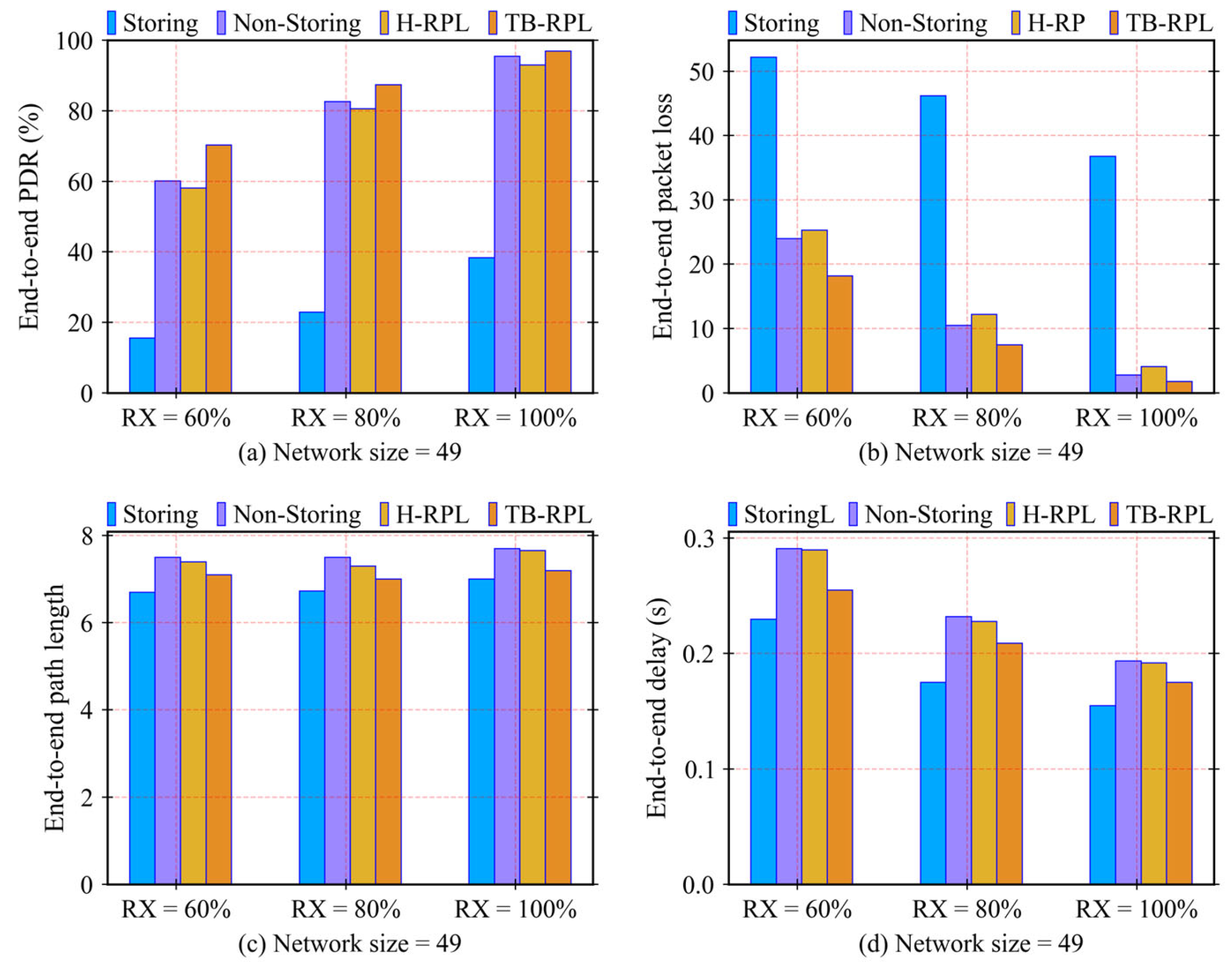
Within the above theoretical framework, three more detailed problems are identified in this article, existing in the current downward routing mechanisms in RFC 6550 and related works. They are the long-path problem, children-unreachable problem, and hybrid-overhead problem. The children-unreachable problem is derived from memory limitation, which is more visible in a network. In this research, they can be considered the same. We executed a series of experiments to ensure that the proposed TB-RPL deals with these problems and improves network performance in terms of a lower end-to-end delay by solving the long-path problem, a higher packet delivery ratio by overcoming the children-unreachable problem, and a lower packet loss by avoiding the hybrid-overhead problem. Furthermore, the three problems also affect each other. An overall performance promotion relies on solving a set of problems, instead of just solving any single one.
To summarize, the motivations of this article are:
- -
Providing an efficient P2P communication mechanism which standard RPL did not achieve. At the same time, improving the memory limitation problem on resource-constrained devices;
- -
Solving the MOPs incompatibility problem in standard RPL to act as a specific mean by which the performance of P2P communication is improved in a heterogenous LLN.
While the contributions of this article are:
- -
The two set objectives from the above motivations are achieved successfully by the proposed TB-RPL;
- -
TB-RPL improves RPL reliability by mitigating the DODAG root failure problem recursively;
- -
Three more detailed problems are defined explicitly, which provides a framework for clearer qualitative and quantitative analyses of P2P communication performance issues in RPL;
- -
To the best of our knowledge, it is a breakthrough to achieve two MOPs fusion and unification, where all nodes perform in the same single TB-RPL mode that includes the consistent logic and the common working context.
The rest of this paper is organized as follows.
Section 2 presents a literature review to solve the commonly concerned problems, which is the state of the art of this topic.
Section 3 provides preliminaries of standard RPL, detailed definitions of the issued three problems, as well as the practical motivation to propose new mechanisms.
Section 4 illustrates the complete mechanism of TB-RPL in detail.
Section 5 shows the experiment settings and corresponding results and discussions.
Section 6 concludes this article and suggests future works. Abbreviation provides a summary and expansion of abbreviations in this article.
2. Literature Review
In this section, the main mechanisms of related works are stated in sequence. Then a summary and analysis of the related works will be provided. Last, compared to related works, the differences and contributions of our work will be discussed.
There have been several works on the hybrid-MOPs topic [
21,
22] since the first related research was proposed by Gan et al. [
23], which is called a more memory-efficient RPL (MERPL). MERPL provides a way to change the non-storing mode to the storing mode and determines the upper limit of the number of route entries for each node of the storing mode, through which to reduce memory consumption. However, downward routes establishment starts from leaf nodes and proceeds to the root, which indicates that children would receive full memory earlier than parents in normal case. It is a reverse order of the proposed mechanism. Moreover, the switch from the non-storing mode to the storing mode requires a statistic number of route entries of each child, which introduces new control overhead.
Ko et al. [
24] have proposed the DualMOP RPL. Their work solves the network connectivity problem by allowing interoperation between by mixing the two modes in downward routing, without switching them. The nodes in the storing mode save downward routing information and make decisions based on conditions of the next-hop node. If there is the non-storing mode of the next-hop node, the current node performs a source routing to destination. Otherwise, the current node sends packets normally to the next-hop in a standard storming mode way. However, the coexistence of two modes keeps drawbacks of them both. Even though that downward routing avoids partition from connectivity, there is still room for a higher network performance compared to switching modes dynamically. Moreover, extra control overhead also is introduced, due to the fact that a parent must know which MOP its child uses.
Kiraly et al. [
25] have proposed the D-RPL, which uses a multicast group that acts as the special memory space for downward routing. When a node’s preferred parent’s memory is full and cannot store downward routes information, the node issues a request to register as a member of the downward routing multicast group. Then it is termed a junction node, due to the fact that it can perform both in the normal case and in that multicast group case. The root transmits some packets to a junction node in that group, when the root does not know where the packets’ destination is. Then, the junction node takes the duty to forward these packets through normal downward routing. Even though nodes of full memory can be skipped in downward routing, the memory space in the multicast group is still part of network, which does not improve the memory limitation of overall network. Moreover, the long-path problem is not solved thoroughly; there are still many packets going through the root.
Ghaleb et al. [
26] have proposed the Enhanced RPL. According to their work, a node is permitted to send DAO messages through multiple parents to lighten the storage burden of a single preferred parent. In detail, a node sorts all its candidate parents based on the parents’ rank. The parent of highest rank in the list is selected to receive DAO messages. However, the parent can refuse DAO messages. If it does so, it will be removed from the list of children to send DAO messages. Then, the child continues to try to send DAO to the first parent in the current list. Generally, the proposed mechanism is more related to the selection of DAO parents instead of handling MOPs. In this case, the memory limitation problem can be improved by polling each candidate parent in sequence. However, a polling process is time and resources consuming, which is also a control overhead. Moreover, results are more random and unpredictable, so the proposed mechanism is not efficient enough.
Oh et al. [
27] have proposed the hybrid mode RPL. In this scheme, the authors try to achieve both advantages of two modes in RPL. Specifically, the root only saves downward route information of leaf nodes, while other middle nodes store route information of non-leaf nodes. In addition, a modified hop extension header is designed to provide the last one hop from routers to leaf nodes. This mechanism reduces the storage burden of the root. However, the large number of middle nodes still suffer memory limitations, which leads to the child-unreachable problem when a network size is large.
Vyas et al. [
28] have proposed an adaptive RPL (ARPL). The authors utilized the situation where the required number of route entries of a node depends on the relative position to the root. The closer to the root, the greater number of entries are required. Therefore, a mechanism was proposed to switch MOPs adaptively based on whether a node’s memory space is full of route entries. Initially, all the nodes work in storing mode. However, the nodes in the storing mode perform like the root in the non-storing mode to perform source routing to destinations. When the number of route entries is full, the MOP is switched to the non-storing mode. At the same time, the entries of mode-switched nodes are removed. Other schemes are kept the same with operations in RFC 6550. Amal et al. [
29] have proposed the H-RPL, which is like the design in [
28]. However, it considered the residual battery condition of nodes. Generally, the authors provide a better method to utilize the memory space of each node by switching MOPs on certain conditions. However, the switch is unidirectional and introduces hybrid-overhead by flushing the previously established route entries during the MOP switch process.
In addition, A. K. Mishra et al. [
22] have proposed a new hybrid MOP scheme for P2P communication. There are two cases defined, where ranks and number of children are considered to decide MOPs in case one. In case two, the probabilities of transmission are included as a condition and performed in cellular schemes. However, it is similar to the other hybrid-MOPs works in that extra control overheads are introduced along with the more complex data control and information collection mechanisms.
All the previous related works can be viewed as to attempts to implement hybrid-MOPs in downward routing of RPL. Generally, three categories could be classified based on the specific hybrid methods: (1) interoperation; (2) switch; (3) modification of storing mode. Furthermore, the term “interoperation” means that the two MOPs are existing at the same time and fixed, and the concern is how to foster interaction between the two different modes. The term “switch” indicates that the MOPs of nodes could be changed on some conditions. Specifically, the storing mode changes to the non-storing mode or vice versa. The last one is the modification of storing mode. In this category, compared to the standard way, the mechanism of the storing mode is modified to meet some specific functions in order to obtain hybrid-MOPs. The summary of related works is shown in
Table 1, based on previous classification.
Given all the related works, TB-RPL in this article constructs a new single type of MOP, which is a functional fusion of the storing mode and the non-storing mode intended to produce a new single one. It is different from the previous three hybrid-MOP types. There is no distinction between different modes. All nodes perform in the same single TB-RPL mode that includes the consistent logic and the common working context, which achieves the advantages of the storing mode and the non-storing mode simultaneously. Based on the review of previous works, and to the best of our knowledge, it is a breakthrough to achieve MOPs fusion and unification. The proposed TB-RPL aims to achieve better network performance by solving the long-path problem, overcoming the children-unreachable problem, and avoiding the hybrid-overhead problem. In the following sections, we describe, explain, and verify the specification of TB-RPL in detail.
4. TB-RPL Mechanism
Here, we state the proposed TB-RPL mechanism at the general level. Three components are crucial: (1) data structure of DAO message; (2) functions to process input and output DAO messages; (3) a specific downward routing table. This section introduces these three components in sequence.
4.1. Presentation of TB-RPL Mechanism
TB-RPL slightly modified the original DAO format to fit the proposed functions. The modified DAO format is shown in
Figure 4. The
Flags is an 8-bit undefined field reserved for future use, which benefits our design exactly. The first bit in that field is used to indicate whether it is a weak DAO message. That is the only modification of the standard DAO format. The components of DAO, as well as the combination of options, are the foundation of the whole process. In the RPL standard, a DAO message format consists of a base object along with several other options. These options include target options (TO) and transit information options (TIO), in which both options can be more than one.
Based on the context of standard RPL, three terms are defined explicitly: originator, producer, and forwarder of the DAO. A DAO originator indicates the node to whom downward routes are provided. A DAO forwarder refers to the node that works in the non-storing mode and just forwards the DAO initialized by the originator. A DAO producer means the node works in the storing mode and produces the current DAO in the DAOs set initialized by the originator.
Among types of DAO message components, the following is the summary of the most important and closely related fields:
- -
The “TO” field: it contains the IPv6 address of an originator node. That IPv6 address is also called the destination used by the DAO producer to reach the originator; also, the originator node itself can be a DAO producer;
- -
The “TIO” field: it includes the IPv6 address of the direct DAO parent of this DAO producer (in the storing mode)/originator (in the non-storing mode), which is stored in the parent address subfield.
For more details, the destination is the ID (IPv6 address) of the originator, to whom downward routes are provided. In standard RPL, this corresponds simply to what is advertised by a node in its DAO messages. In TB-RPL, however, any node on the path to the DODAG root may advertise one of its downstream nodes by generating a DAO containing the ID thereof as a TO. A node that generates such a DAO with a TO for one of its downstream nodes is called a DAO producer. DAOs are treated like any corresponding types of DAOs in standard RPL.
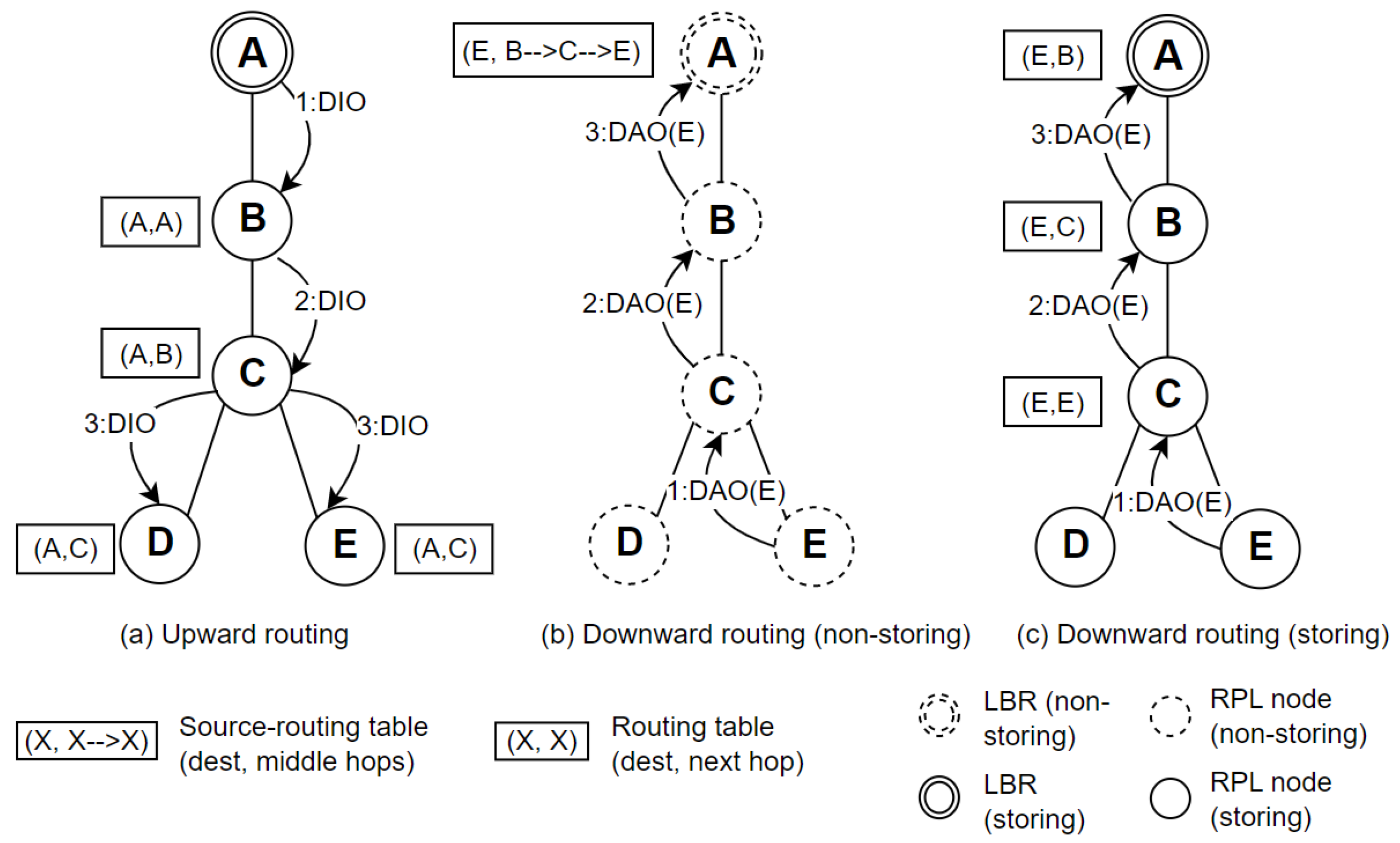
First, a DAO initialized by the originator contains: (1) the ID of the originator of the DAOs set (contained in TO, and the child is the originator node itself in this case); (2) the ID of the preferred parent of the originator (contained in TIO). Second, a DAO transmitted through a forwarder contains the same as that of the originator (because it is just a simple forwarding). Third, a DAO made by a producer contains: (1) the ID of the originator of the DAOs set (contained in TO, and the originator is a child of the current forwarder); (2) the ID of the preferred parent of the current producer (contained in TIO). Last, an example of detailed two types of downward routing schemes in RPL is illustrated in
Figure 5.
In
Figure 5a, node E is the originator, nodes C and B are forwarders, and node A is the root. “1:DAO(E, C)” here means the originator of the whole DAOs set is node E, and the preferred parent of the originator is node C, and the number 1 before “:” refers to that it is the first DAO message in the DAOs set. “2:DAO(E, C)” and “3:DAO(E, C)” follow the same rule.
In
Figure 5b, node E is the originator, nodes C and B are producers, and node A is the root. “1:DAO(E, C)” here means the originator of the whole DAOs set is node E, and the preferred parent of the originator is node C. “2:DAO(E, B)” means that the originator is node E and the preferred parent of the current producer is node B. “3:DAO(E, A)” indicates that the originator is node E, and the preferred parent of the current producer is node A.
Specifically, for node E, all the DAOs shown in
Figure 5 are necessary. If any DAO in the logical set is missed, then the downward routing of node E cannot be established. They form the indivisible whole. Each node performs the role of originator (in both modes) and forwarder (in the non-storing mode)/producer (in the storing mode) and sends corresponding types of DAO to its preferred parent periodically by the control of a DAO timer.
The node, of which the memory space for storing downward routing table runs out, is defined as a weak node. A weak node will set a weak flag that is defined as the indicator that the current DAO is produced by a weak node.
Figure 4 shows the usage of this flag in a DAO message. The function of the weak flag is to tell the receiver of this DAO that it should read and store the content of TIO field in the provided order for producing a source routing header in the future (the mechanism to implement this step is the same as the source routing mechanism of the root in the non-storing mode).
One or more TO(s) must be followed by one or more TIO(s). In this designated option sequence, a TIO represents a DODAG parent, while a TO describes a child node [
13]. A typical non-storing node operates multiple TIOs and sends DAO message directly to the root. A typical storing node employs one TIO without a parent address subfield and sends the DAO message to the preferred parent. Assume that
Trg(
T) represents a TO for a target T, and
Trnst(
P) refers to a TIO including a parent P. Then, a complete DAO message is defined as follows:
where
m ≥
n in standard RPL and thus the set
Trg(
T) is defined to own parents
Trnst(
P). The DAO producer itself also belongs to
Trg(
T). Even though the two MOPs have the same DAO structure, the contents are different. In the non-storing mode, the parent address subfield must be filled in for LBR to generate source routing header.
However, this subfield is empty in the storing mode. Because the DAO message is processed by the sender’s direct parent itself, there is no need to set parent information in the DAO message. The receiver just stores the originator address and next-hop address information, which is enough for implementing a hop-by-hop routing function. It is worth noting that the next-hop address is not included in DAO message, while it is implicitly the sender address in the IPv6 header. In summary, both MOPs use the same DAO message structure, which involves one base object, one or more TO, and one or more TIO. However, the parent address subfield must be written in the non-storing mode, while it is empty in the storing mode.
In summary, each node performs:
In the storing mode by default;
If the memory space used to store downward routing table runs out, this node becomes a weak node;
Then, a weak flag is set in the currently produced DAO, with the corresponding content of TO and TIO;
In detail, the content of TIO contains the segment of the path to originator that the middle weak node(s) cannot store. While TO is still simply the originator of the DAOs set;
When the receiver obtains this DAO including the weak flag, it (if the receiver is not a weak node) will read and store the content of TIO field in the provided order for producing a source routing header in the future and then performs the related functions like the LBR in the non-storing mode.
For comparison, in the storing mode of standard RPL, when a node’s memory is full and cannot store more routing entries, the new coming DAO will be just discarded. Then, the node will not send any consequent DAOs to its preferred parent, while, in our proposed work, the designed content in a designated order is contained in DAOs to solve that problem.
TB-RPL DAOs set works on the above foundation.
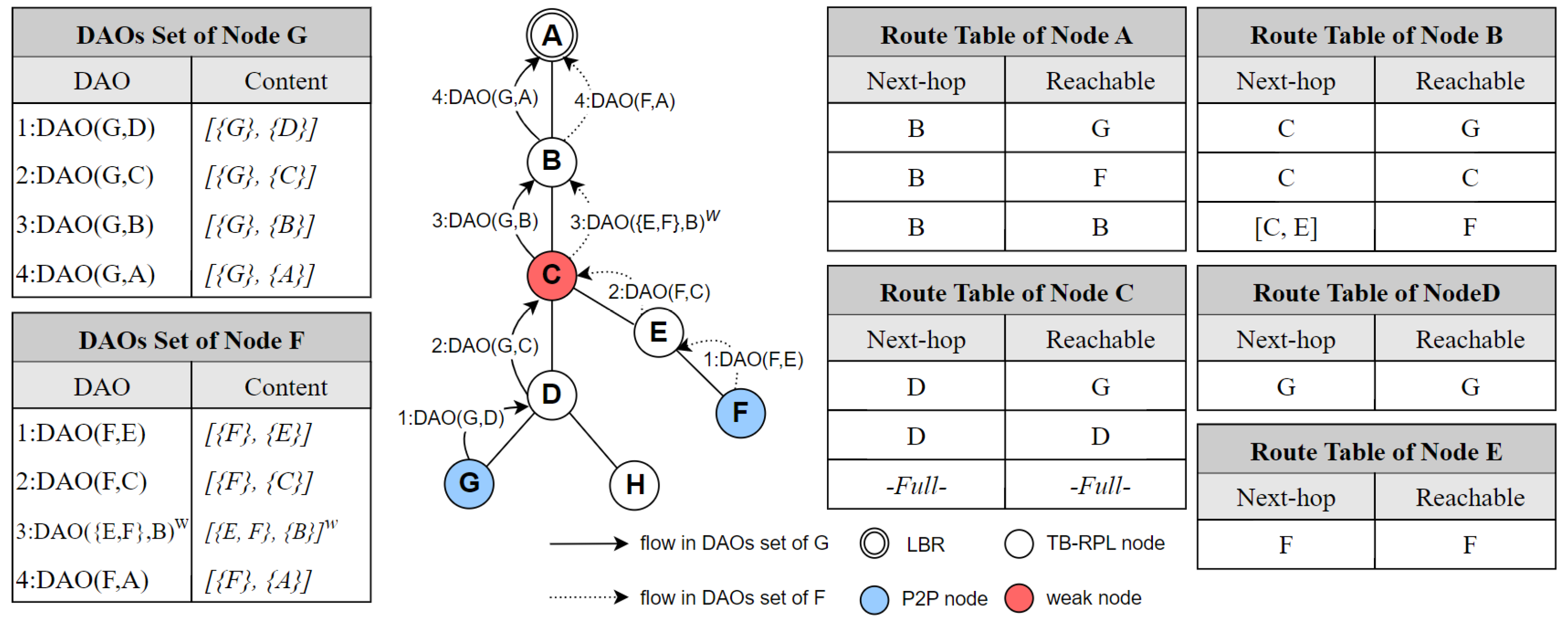
Figure 6 describes a complete process of TB-RPL to establish a downward route. In this case, node G is assumed to finish a downward routing establishment before node F. Currently, node C stores the downward route information of nodes G and D, then it runs out of memory space for route entries. So, node C does not save node F’s downward route. When 2:DAO(F,C) arrives at node C, it turns into a weak node and outputs a DAO with the weak flag to its preferred parent node B. For a weak DAO, the order of element in
Trg(
T) is strictly designated, which will be used by node B to perform source routing in the future. This order-designated
Trg(
T) is stored by node B into an ordered tuple [C, E] as an atomic unit. At last, 4:DAO(F,A) is processed by node A, then the downward routes to node G and F have been established, respectively.
Based on this downward route, node G and node F can send messages to each other.
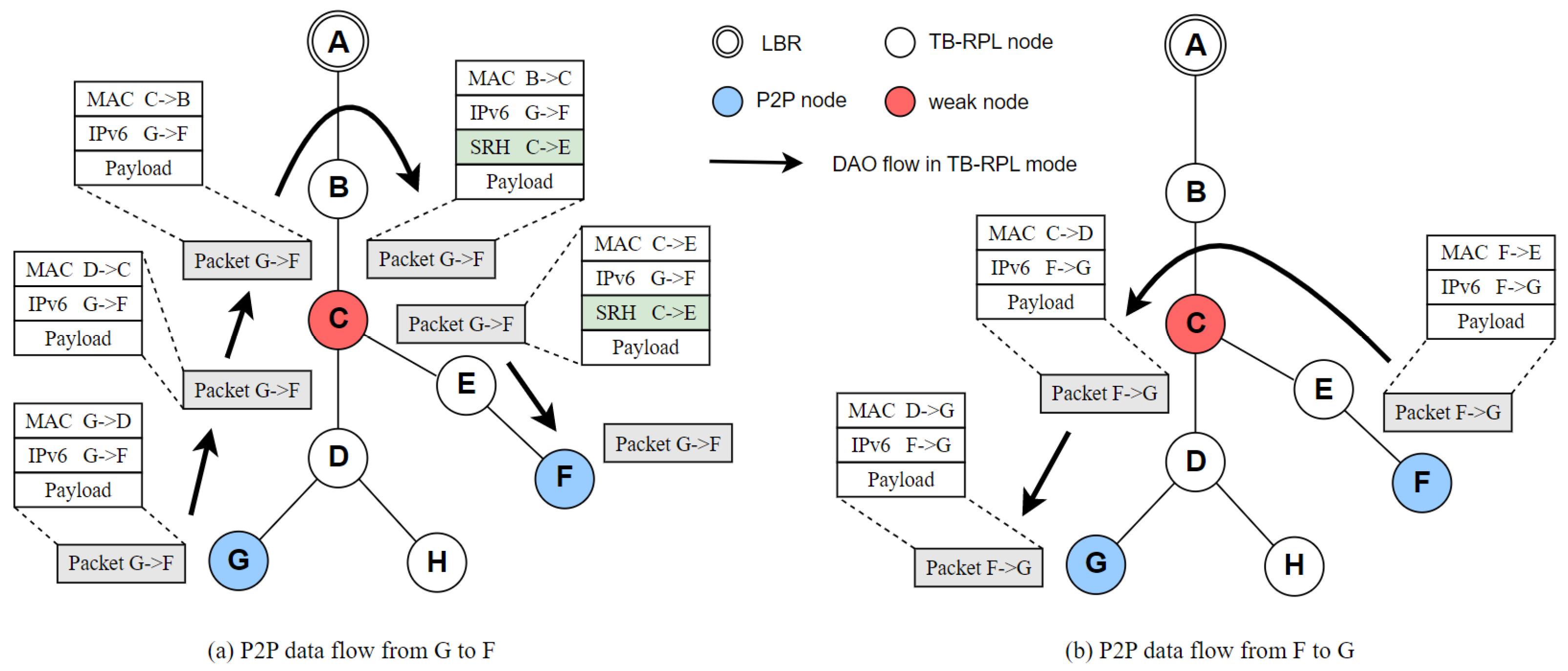
Figure 7 illustrates the data flows and related message control headers. Node B produces a source routing header, due to node C not storing the related route segment to node F. With the guide of source routing from node B, node C successfully forwards packets to node E. Then, the source routing finishes, and node E can find a route to F through its own route table. The other packets are transmitted as designed. P2P communications between node G and F are performed successfully.
4.2. Detailed Process of TB-RPL
In the previous section, a representation of the overall workflow was provided, which is a big picture of TB-RPL. This section offers the perspective of each node to process TB-RPL in detail. At the beginning, all the nodes select TB-RPL MOP. This MOP decision has been made already in the initialization DIO messages from LBR. After a DODAG is formed, each node starts to unicast its own DAO message to the preferred parent, and the downward routing establishment begins.
During the downward routing path establishment, the deeply resource-constrained devices cannot keep storing routing information about their children continuously. When a network is large-scale and contains a mass of nodes, these devices’ memory space will finally be used up to store the subtree routing information. In order to avoid the memory failure of weak nodes, a route entries threshold α is defined as the upper boundary of a node’s allowed number of route entries. Every node tries it best to store children’s routing information. When a node’s number of stored route entries is higher than α, it asks for help from its preferred parent.
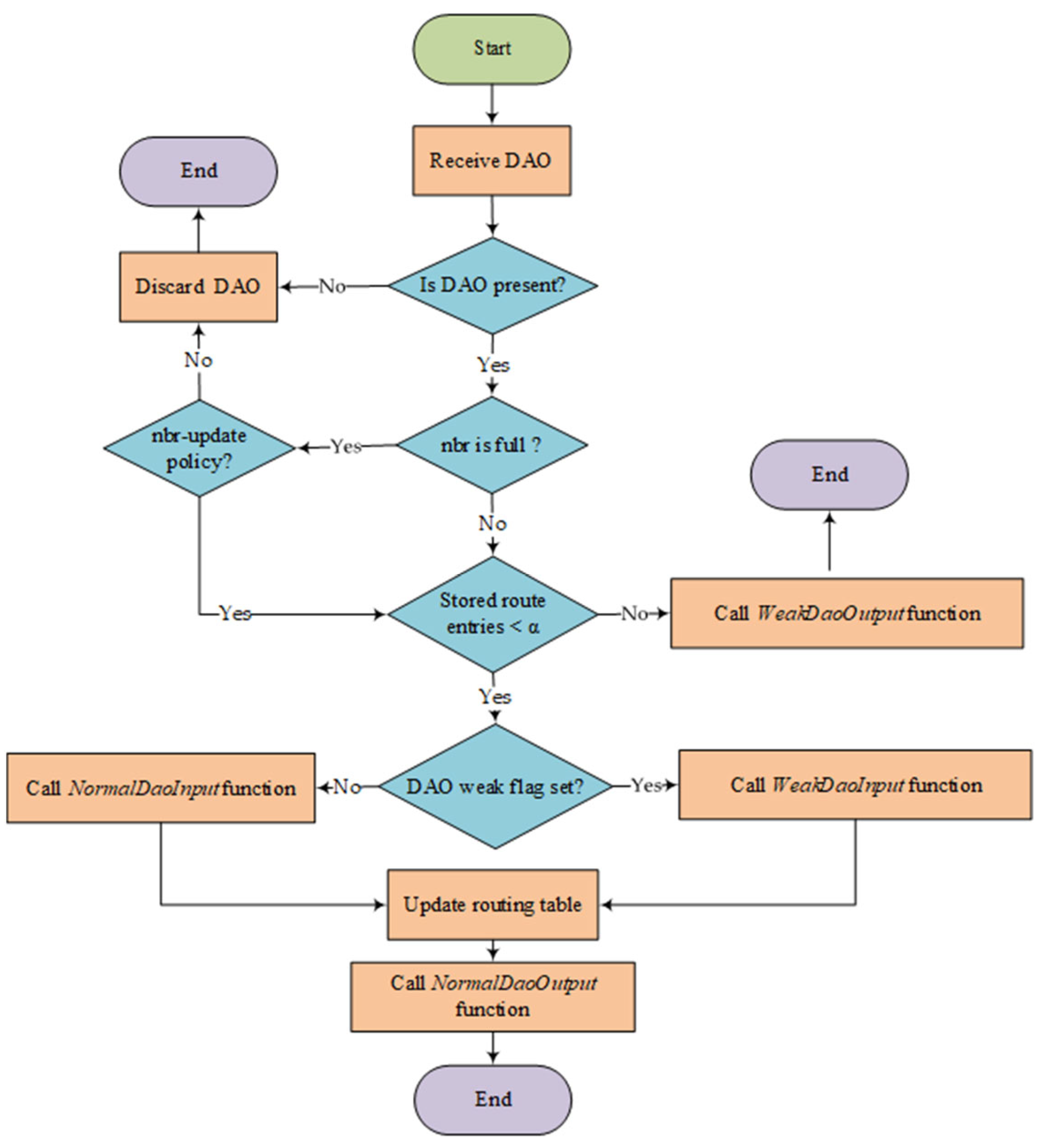
If the parent node’s memory is enough, it will store the weak DAO message from its children. Otherwise, the parent node asks its own parent for help—in the worst case, until it reaches LBR. In this sense, the middle parents perform source routing for some P2P paths located in its subtree.
Figure 8 summarizes the logic flow when a parent node receives a DAO message. It is worth noting that neighbor table is the prerequisite of setting up downward routes. In RFC 6550, three sets are defined and have the following relationship [
13]. The preferred parent set is the subset of the parent set, which is the subset of the candidate neighbor set. In further detail, the establishment and maintenance of those three sets are performed by a specific neighbor discovery mechanism and objective function. If a node is not recognized as a neighbor, it cannot be included as a route further. The neighbor table is governed by a tailored policy. In addition, there is a point worth explaining, i.e., that the specific mechanism for neighbor discovery is not decided in RFC 6550, which will finally depend on the implementation choice.
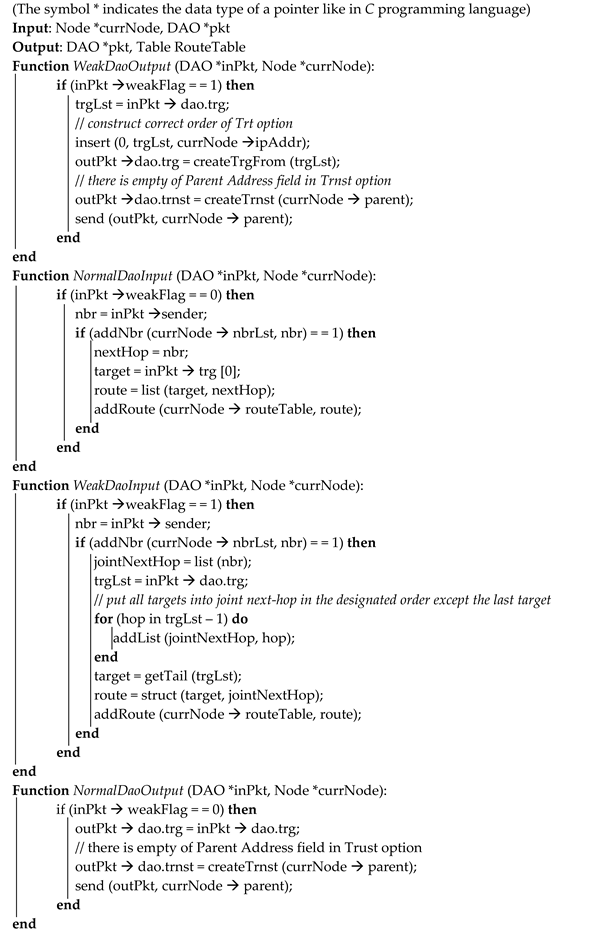
There are four functions referred to in the logic flow, which are the essential functions of TB-RPL. Algorithm 1 shows the pseudocode about the identified four functions in
Figure 8. Generally, currNode is the current node that performs current processing function. pkt refers to the DAO packet waiting to be handled. Specifically, inPkt is the input DAO, while the outPkt is output DAO. Then, trgLst is abbreviation for target list, which is a general list data structure. For the function
WeakDaoOutput, its purpose is to produce an output DAO based on the input DAO’s set of
Trg(
T) in a strict order, which is utilized by the parent to produce source routing header. Function
WeakDaoInput updates the current node’s route entries based on the input DAO by producing and storing a source routing information in weak case. The remained functions,
NormalDaoOutput and
NormalDaoInput, are the normal routines to handle corresponding DAO messages.
In summary, TB-RPL provides a unified framework and mechanism to allow every memory limited node to do its best to save downward routing information, so overall memory availability increases. The memory limited problem has been improved. Moreover, in downward routing, the shortest route is generally selected by nodes at any given situation. The long-path problem has been solved. Finally, with the consistent logic and common working context, there are no concepts of switch or interoperate with different MOPs required, so time and resource overheads for switching or interoperating between MOPs are saved. The hybrid-overhead problem has been overcome.
| Algorithm 1: TB-RPL DAO message process |
![Electronics 12 01639 i001 Electronics 12 01639 i001]() |