On the Dependability of 6G Networks
Abstract
1. Introduction
2. Related Work and Our Contributions
2.1. Related Work
2.2. Contributions of the Paper
- We analyze the role of dependability in 6G networks from a system-wide point of view, studying each of the four components of dependability separately.
- We analyze how the omnipresence and distributed nature of AI/ML affects the dependability of 6G systems.
- We study the importance of dependability in MCAs, analyzing every aspect of dependability separately.
- We identify future research directions that are summarized in Table 1 and will help to increase the dependability of future 6G networks.
3. Dependability
3.1. Reliability
3.2. Availability
3.3. Safety
3.4. Security
4. 6G and Dependability
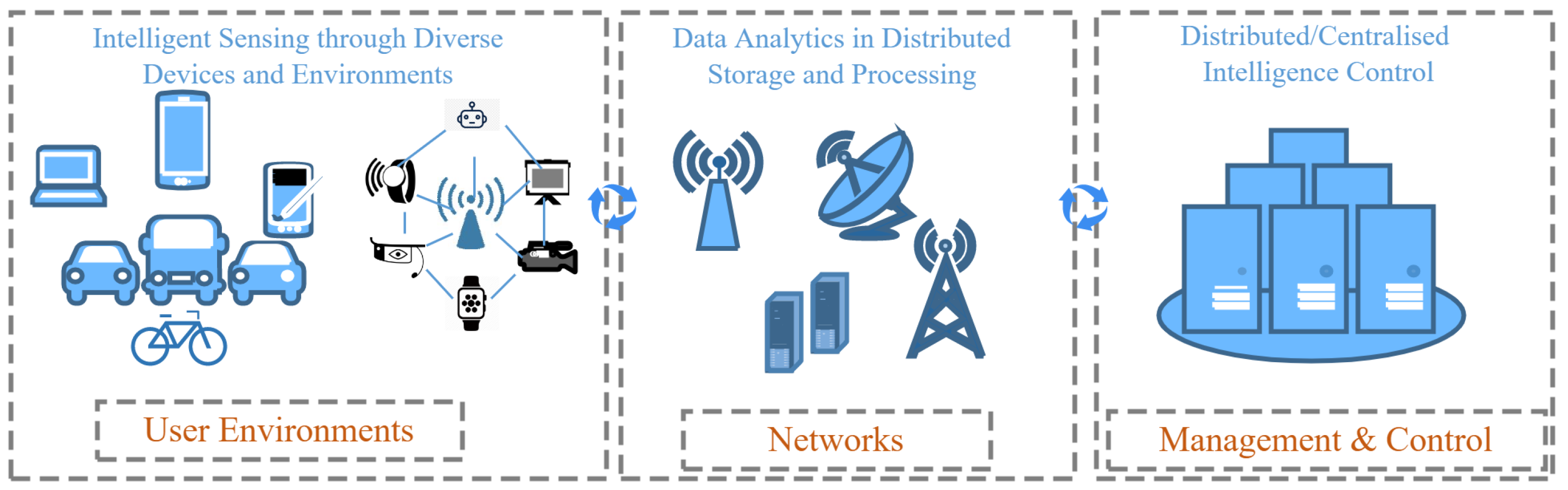
4.1. Brief Introduction to 6G Networks
4.2. Dependability in 6G Networks
4.2.1. Reliability
4.2.2. Availability
4.2.3. Safety
4.2.4. Security
5. Machine Learning, Dependability, and 6G
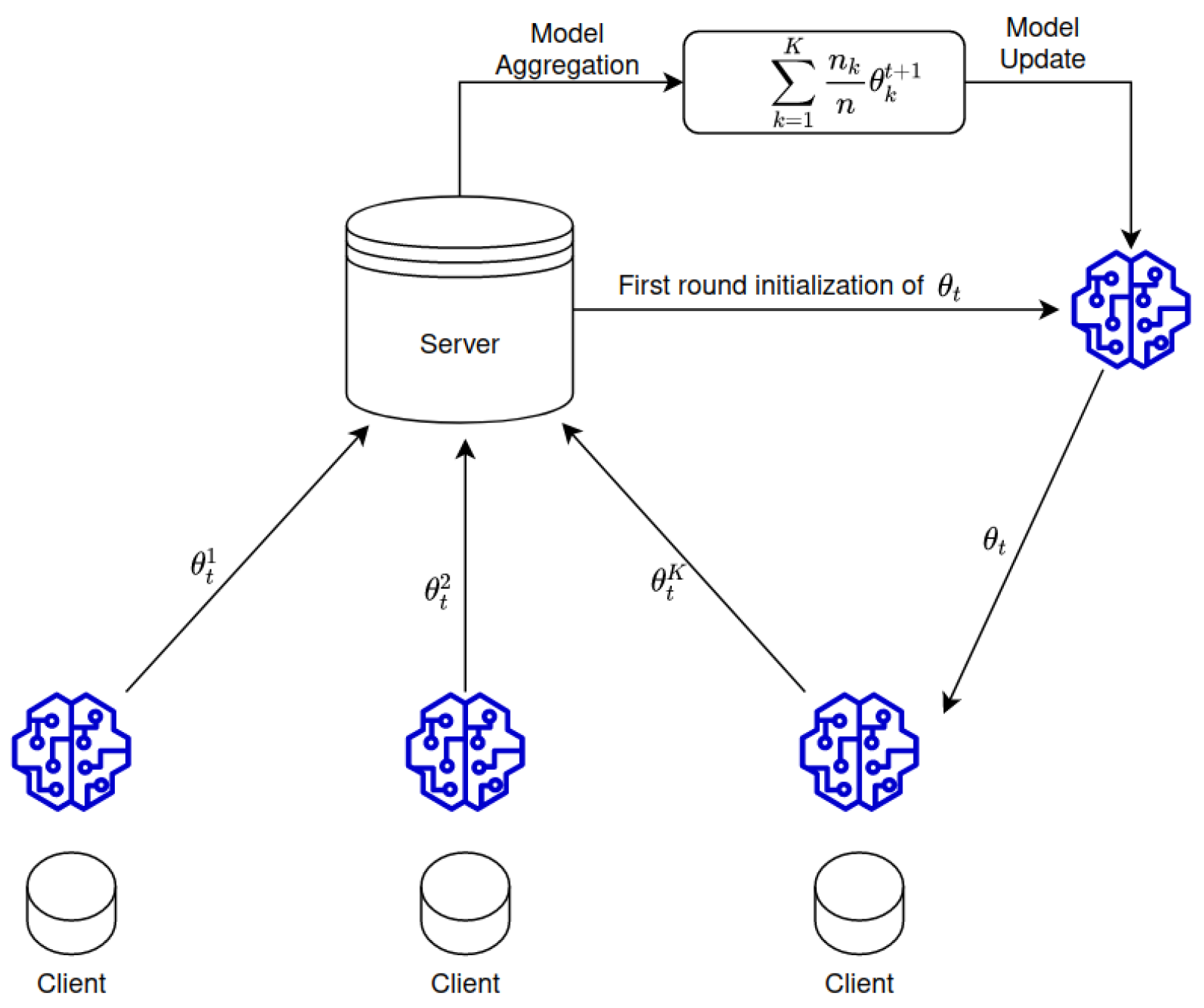
5.1. Background in Brief
- A number of clients is selected by the server based on certain conditions, such as being idle or its bandwidth limitation, to download the model parameters and use them to initialize their local model.
- Using their local data, each device trains and optimizes the downloaded model. This is done by using stochastic gradient descent, a determined number of minibatch steps, and several epochs in order to increase the update quality and reduce the communications cost.
- When the training is done, clients send their updates towards the server. It is important to notice that some clients might drop out due to connectivity issues, lack of processing power, etc. Nevertheless, the round continues with the received updates. If there are too many dropped out clients, the current round is abandoned.
- The server receives the updates, weights them based on their training set sizes, and finally, aggregates them. A new model is built on the server, and the next round begins.
5.2. Dependability of Federated Learning
5.2.1. Reliability
5.2.2. Availability
5.2.3. Safety
5.2.4. Security
6. Dependability for MCAs in 6G
6.1. MCA Use Cases
6.2. Dependability Analysis of 6G MCAs
6.2.1. Reliability
6.2.2. Availability
6.2.3. Safety
6.2.4. Security
7. Future Research Directions
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| Acronym | Full Term(s) |
| 3D | Three Dimension |
| 5G | Fifth Generation |
| 6G | Sixth Generation |
| AI | Artificial Intelligence |
| AR | Augmented Reality |
| CPS | Cyber-Physical System |
| D2D | Device to Device |
| DLT | Distributed Ledger Technology |
| DoS | Denial of Service |
| DPI | Deep Packet Inspection |
| eMMB | enhanced Mobile Broadband |
| FL | Federated Learning |
| ICT | Information and Communication Technologies |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| IPS | Intrusion Prevention System |
| IT | Information Technology |
| MCA | Mission-Critical Application |
| MEC | Multi-access Edge Computing |
| MIMO | Multi-Input Multi-Output |
| mIoT | massive IoT |
| ML | Machine Learning |
| NFV | Network Function Virtualization |
| QoS | Quality of Service |
| RAN | Radio Access Network |
| SDN | Software Defined Networking |
| VLC | Visible Light Communication |
| VNF | Virtual Network Function |
| VR | Virtual Reality |
| WSN | Wireless Sensor Networks |
| XR | Extended Reality |
References
- Saad, W.; Bennis, M.; Chen, M. A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems. IEEE Netw. 2020, 34, 134–142. [Google Scholar] [CrossRef]
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G Networks: Use Cases and Technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Ahmad, I.; Suomalainen, J.; Porambage, P.; Gurtov, A.; Huusko, J.; Höyhtyä, M. Security of Satellite-Terrestrial Communications: Challenges and Potential Solutions. IEEE Access 2022, 10, 96038–96052. [Google Scholar] [CrossRef]
- AbdulRahman, S.; Tout, H.; Ould-Slimane, H.; Mourad, A.; Talhi, C.; Guizani, M. A survey on federated learning: The journey from centralized to distributed on-site learning and beyond. IEEE Internet Things J. 2021, 8, 5476–5497. [Google Scholar] [CrossRef]
- Peltonen, E.; Bennis, M.; Capobianco, M.; Debbah, M.; Ding, A.; Gil-Castiñeira, F.; Jurmu, M.; Karvonen, T.; Kelanti, M.; Kliks, A.; et al. 6G white paper on edge intelligence. arXiv 2020, arXiv:2004.14850. [Google Scholar]
- Sekaran, R.; Patan, R.; Raveendran, A.; Al-Turjman, F.; Ramachandran, M.; Mostarda, L. Survival Study on Blockchain Based 6G-Enabled Mobile Edge Computation for IoT Automation. IEEE Access 2020, 8, 143453–143463. [Google Scholar] [CrossRef]
- Nawaz, S.J.; Sharma, S.K.; Mansoor, B.; Patwary, M.N.; Khan, N.M. Non-Coherent and Backscatter Communications: Enabling Ultra-Massive Connectivity in 6G Wireless Networks. IEEE Access 2021, 9, 38144–38186. [Google Scholar] [CrossRef]
- Bariah, L.; Mohjazi, L.; Muhaidat, S.; Sofotasios, P.C.; Kurt, G.K.; Yanikomeroglu, H.; Dobre, O.A. A Prospective Look: Key Enabling Technologies, Applications and Open Research Topics in 6G Networks. IEEE Access 2020, 8, 174792–174820. [Google Scholar] [CrossRef]
- Ren, J.; Zhang, D.; He, S.; Zhang, Y.; Li, T. A Survey on End-Edge-Cloud Orchestrated Network Computing Paradigms: Transparent Computing, Mobile Edge Computing, Fog Computing, and Cloudlet. ACM Comput. Surv. 2019, 52. [Google Scholar] [CrossRef]
- Hashima, S.; Fadlullah, Z.M.; Fouda, M.M.; Mohamed, E.M.; Hatano, K.; ElHalawany, B.M.; Guizani, M. On Softwarization of Intelligence in 6G Networks for Ultra-Fast Optimal Policy Selection: Challenges and Opportunities. IEEE Netw. 2022, 1–9. [Google Scholar] [CrossRef]
- Letaief, K.B.; Shi, Y.; Lu, J.; Lu, J. Edge Artificial Intelligence for 6G: Vision, Enabling Technologies, and Applications. IEEE J. Sel. Areas Commun. 2022, 40, 5–36. [Google Scholar] [CrossRef]
- Avizienis, A.; Laprie, J.C.; Randell, B. Fundamental Concepts of Dependability; Department of Computing Science Technical Report Series; University of Newcastle upon Tyne: Newcastle upon Tyne, UK, 2001. [Google Scholar]
- Ahmed, W.; Wu, Y.W. A survey on reliability in distributed systems. J. Comput. Syst. Sci. 2013, 79, 1243–1255. [Google Scholar] [CrossRef]
- Foukalas, F.; Pop, P.; Theoleyre, F.; Boano, C.A.; Buratti, C. Dependable Wireless Industrial IoT Networks: Recent Advances and Open Challenges. In Proceedings of the 2019 IEEE European Test Symposium (ETS), Baden, Germany, 27–31 May 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.; Verissimo, P. Towards Secure and Dependable Software-Defined Networks. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking (HotSDN ’13), Hong Kong, China, 16 August 2013; pp. 55–60. [Google Scholar] [CrossRef]
- Scanzio, S.; Wisniewski, L.; Gaj, P. Heterogeneous and dependable networks in industry—A survey. Comput. Ind. 2021, 125, 103388. [Google Scholar] [CrossRef]
- She, C.; Dong, R.; Gu, Z.; Hou, Z.; Li, Y.; Hardjawana, W.; Yang, C.; Song, L.; Vucetic, B. Deep Learning for Ultra-Reliable and Low-Latency Communications in 6G Networks. IEEE Netw. 2020, 34, 219–225. [Google Scholar] [CrossRef]
- Salh, A.; Audah, L.; Shah, N.S.M.; Alhammadi, A.; Abdullah, Q.; Kim, Y.H.; Al-Gailani, S.A.; Hamzah, S.A.; Esmail, B.A.F.; Almohammedi, A.A. A Survey on Deep Learning for Ultra-Reliable and Low-Latency Communications Challenges on 6G Wireless Systems. IEEE Access 2021, 9, 55098–55131. [Google Scholar] [CrossRef]
- Masaracchia, A.; Li, Y.; Nguyen, K.K.; Yin, C.; Khosravirad, S.R.; Costa, D.B.D.; Duong, T.Q. UAV-Enabled Ultra-Reliable Low-Latency Communications for 6G: A Comprehensive Survey. IEEE Access 2021, 9, 137338–137352. [Google Scholar] [CrossRef]
- Gupta, A.; Fernando, X.; Das, O. Reliability and Availability Modeling Techniques in 6G IoT Networks: A Taxonomy and Survey. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin City, China, 28 June–2 July 2021; pp. 586–591. [Google Scholar] [CrossRef]
- Li, S.; Cheng, X.; Huang, X.; Otaibi, S.A.; Wang, H. Cooperative Conflict Detection and Resolution and Safety Assessment for 6G Enabled Unmanned Aerial Vehicles. IEEE Trans. Intell. Transp. Syst. 2022, 24, 2183–2198. [Google Scholar] [CrossRef]
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and beyond. IEEE Commun. Surv. Tutor. 2019, 21, 3682–3722. [Google Scholar] [CrossRef]
- Ylianttila, M.; Kantola, R.; Gurtov, A.; Mucchi, L.; Oppermann, I.; Yan, Z.; Nguyen, T.H.; Liu, F.; Hewa, T.; Liyanage, M.; et al. 6G white paper: Research challenges for trust, security and privacy. arXiv 2020, arXiv:2004.11665. [Google Scholar]
- Avizienis, A.; Laprie, J.C.; Randell, B.; Landwehr, C. Basic concepts and taxonomy of dependable and secure computing. IEEE Trans. Dependable Secur. Comput. 2004, 1, 11–33. [Google Scholar] [CrossRef]
- Heimann, D.I.; Mittal, N.; Trivedi, K.S. Dependability modeling for computer systems. In Proceedings of the Annual Reliability and Maintainability Symposium, Orlando, FL, USA, 29–31 January 1991; pp. 120–128. [Google Scholar]
- Chen, D.; Garg, S.; Kintala, C.M.; Trivedi, K.S. Dependability Enhancement for IEEE 802.11 Wireless LAN with Redundancy Techniques. In Proceedings of the Dependable Systems and Networks, San Francisco, CA, USA, 22–25 June 2003; pp. 521–528. [Google Scholar]
- Laprie, J.C. Dependable computing: Concepts, limits, challenges. In Proceedings of the Special issue of the 25th International Symposium on Fault-Tolerant Computing, Pasadena, CA, USA, 27–30 June 1995; pp. 42–54. [Google Scholar]
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra -Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521. [Google Scholar] [CrossRef]
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in Software Defined Networks: A Survey. IEEE Commun. Surv. Tutorials 2015, 17, 2317–2346. [Google Scholar] [CrossRef]
- Banerjee, A.; Venkatasubramanian, K.K.; Mukherjee, T.; Gupta, S.K.S. Ensuring Safety, Security, and Sustainability of Mission-Critical Cyber–Physical Systems. Proc. IEEE 2012, 100, 283–299. [Google Scholar] [CrossRef]
- Raytis, J.L.; Yuh, B.E.; Lau, C.S.; Fong, Y.; Lew, M.W. Anesthetic Implications of Robotically Assisted Surgery with the Da Vinci Xi Surgical Robot. Open J. Anesthesiol. 2016, 6, 115–118. [Google Scholar] [CrossRef]
- Rim, L.J. Anesthetic considerations for robotic surgery. Korean J. Anesth. 2014, 66, 3–11. [Google Scholar] [CrossRef]
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G security challenges and solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43. [Google Scholar] [CrossRef]
- Ahmad, I.; Shahabuddin, S.; Malik, H.; Harjula, E.; Leppänen, T.; Lovén, L.; Anttonen, A.; Sodhro, A.H.; Mahtab Alam, M.; Juntti, M.; et al. Machine Learning Meets Communication Networks: Current Trends and Future Challenges. IEEE Access 2020, 8, 223418–223460. [Google Scholar] [CrossRef]
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mämmelä, A.; Ahmad, I. Machine learning threatens 5G security. IEEE Access 2020, 8, 190822–190842. [Google Scholar] [CrossRef]
- Ahmad, I.; Shahabuddin, S.; Sauter, T.; Harjula, E.; Kumar, T.; Meisel, M.; Juntti, M.; Ylianttila, M. The Challenges of Artificial Intelligence in Wireless Networks for the Internet of Things: Exploring Opportunities for Growth. IEEE Ind. Electron. Mag. 2020, 15, 16–29. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Xia, Y.; Xu, X.; Jolfaei, A.; Bashir, A.K.; Tariq, U.; Yu, D.; Vasilakos, A.V. Investigating the Prospect of Leveraging Blockchain and Machine Learning to Secure Vehicular Networks: A Survey. IEEE Trans. Intell. Transp. Syst. 2021, 23, 683–700. [Google Scholar] [CrossRef]
- Hui, Y.; Cheng, N.; Su, Z.; Huang, Y.; Zhao, P.; Luan, T.H.; Li, C. Secure and Personalized Edge Computing Services in 6G Heterogeneous Vehicular Networks. IEEE Internet Things J. 2021, 9, 5920–5931. [Google Scholar] [CrossRef]
- Singh, R.; Ahmad, I.; Huusko, J. The Role of Physical Layer Security in Satellite-Based Networks. arXiv 2023, arXiv:2302.07375. [Google Scholar]
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G Wireless Networks: Vision, Requirements, Architecture, and Key Technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar] [CrossRef]
- David, K.; Berndt, H. 6G Vision and Requirements: Is There Any Need for Beyond 5G? IEEE Veh. Technol. Mag. 2018, 13, 72–80. [Google Scholar] [CrossRef]
- Tariq, F.; Khandaker, M.R.A.; Wong, K.K.; Imran, M.A.; Bennis, M.; Debbah, M. A Speculative Study on 6G. IEEE Wirel. Commun. 2020, 27, 118–125. [Google Scholar] [CrossRef]
- Nezami, Z.; Zamanifar, K. Internet of ThingsInternet of Everything: Structure and Ingredients. IEEE Potentials 2019, 38, 12–17. [Google Scholar] [CrossRef]
- Wang, X.; Han, Y.; Wang, C.; Zhao, Q.; Chen, X.; Chen, M. In-Edge AI: Intelligentizing Mobile Edge Computing, Caching and Communication by Federated Learning. IEEE Netw. 2019, 33, 156–165. [Google Scholar] [CrossRef]
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A Survey of Multi-Access Edge Computing in 5G and Beyond: Fundamentals, Technology Integration, and State-of-the-Art. IEEE Access 2020, 8, 116974–117017. [Google Scholar] [CrossRef]
- Osorio, D.P.M.; Ahmad, I.; Sánchez, J.D.V.; Gurtov, A.; Scholliers, J.; Kutila, M.; Porambage, P. Towards 6G-enabled Internet of Vehicles: Security and Privacy. IEEE Open J. Commun. Soc. 2022, 3, 82–105. [Google Scholar] [CrossRef]
- Okwuibe, J.; Haavisto, J.; Kovacevic, I.; Harjula, E.; Ahmad, I.; Islam, J.; Ylianttila, M. SDN-Enabled Resource Orchestration for Industrial IoT in Collaborative Edge-Cloud Networks. IEEE Access 2021, 9, 115839–115854. [Google Scholar] [CrossRef]
- Zhou, Z.; Chen, X.; Li, E.; Zeng, L.; Luo, K.; Zhang, J. Edge Intelligence: Paving the Last Mile of Artificial Intelligence with Edge Computing. Proc. IEEE 2019, 107, 1738–1762. [Google Scholar] [CrossRef]
- Deng, S.; Zhao, H.; Fang, W.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Edge Intelligence: The Confluence of Edge Computing and Artificial Intelligence. IEEE Internet Things J. 2020, 7, 7457–7469. [Google Scholar] [CrossRef]
- Li, C.; Guo, W.; Sun, S.C.; Al-Rubaye, S.; Tsourdos, A. Trustworthy Deep Learning in 6G-Enabled Mass Autonomy: From Concept to Quality-of-Trust Key Performance Indicators. IEEE Veh. Technol. Mag. 2020, 15, 112–121. [Google Scholar] [CrossRef]
- Harjula, E.; Karhula, P.; Islam, J.; Leppänen, T.; Manzoor, A.; Liyanage, M.; Chauhan, J.; Kumar, T.; Ahmad, I.; Ylianttila, M. Decentralized IoT edge nanoservice architecture for future gadget-free computing. IEEE Access 2019, 7, 119856–119872. [Google Scholar] [CrossRef]
- Herlich, M.; Maier, C. Measuring and Monitoring Reliability of Wireless Networks. IEEE Commun. Mag. 2021, 59, 76–81. [Google Scholar] [CrossRef]
- Bhagwan, R.; Savage, S.; Voelker, G.M. Understanding availability. In Proceedings of the International Workshop on Peer-to-Peer Systems, Berkeley, CA, USA, 21–22 February 2003; Springer: Berlin/Heidelberg, Germany; pp. 256–267. [Google Scholar]
- Ahmad, I.; Karunarathna, S.N.; Ylianttila, M.; Gurtov, A. Load Balancing in Software Defined Mobile Networks. In Software Defined Mobile Networks (SDMN): Beyond LTE Network Architecture; Wiley: Hoboken, NJ, USA, 2015; pp. 225–245. [Google Scholar]
- Young, W.; Leveson, N.G. An integrated approach to safety and security based on systems theory. Commun. ACM 2014, 57, 31–35. [Google Scholar] [CrossRef]
- Ahmad, I.; Lembo, S.; Rodriguez, F.; Mehnert, S.; Vehkaperä, M. Security of Micro MEC in 6G: A Brief Overview. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 332–337. [Google Scholar] [CrossRef]
- Kodheli, O.; Lagunas, E.; Maturo, N.; Sharma, S.K.; Shankar, B.; Montoya, J.F.M.; Duncan, J.C.M.; Spano, D.; Chatzinotas, S.; Kisseleff, S.; et al. Satellite Communications in the New Space Era: A Survey and Future Challenges. IEEE Commun. Surv. Tutor. 2021, 23, 70–109. [Google Scholar] [CrossRef]
- Guo, H.; Li, J.; Liu, J.; Tian, N.; Kato, N. A Survey on Space-Air-Ground-Sea Integrated Network Security in 6G. IEEE Commun. Surv. Tutor. 2022, 24, 53–87. [Google Scholar] [CrossRef]
- Ma, J.; Shrestha, R.; Adelberg, J.; Yeh, C.Y.; Hossain, Z.; Knightly, E.; Jornet, J.M.; Mittleman, D.M. Security and eavesdropping in terahertz wireless links. Nature 2018, 563, 89–93. [Google Scholar] [CrossRef] [PubMed]
- Song, F. A note on quantum security for post-quantum cryptography. In Proceedings of the International Workshop on Post-Quantum Cryptography, Waterloo, ON, Canada, 23 September 2014; pp. 246–265. [Google Scholar]
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Alshoura, W.H.; Arshad, H. The internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494. [Google Scholar] [CrossRef]
- Khan, L.U.; Pandey, S.R.; Tran, N.H.; Saad, W.; Han, Z.; Nguyen, M.N.H.; Hong, C.S. Federated Learning for Edge Networks: Resource Optimization and Incentive Mechanism. IEEE Commun. Mag. 2020, 58, 88–93. [Google Scholar] [CrossRef]
- Mittal, M.; Kumar, K.; Behal, S. Deep learning approaches for detecting DDoS attacks: A systematic review. Soft Comput. 2022, 1–37. [Google Scholar] [CrossRef]
- Mwase, C.; Jin, Y.; Westerlund, T.; Tenhunen, H.; Zou, Z. Communication-efficient distributed AI strategies for the IoT edge. Future Gener. Comput. Syst. 2022, 131, 292–308. [Google Scholar] [CrossRef]
- Liu, Y.; Yuan, X.; Xiong, Z.; Kang, J.; Wang, X.; Niyato, D. Federated learning for 6G communications: Challenges, methods, and future directions. China Commun. 2020, 17, 105–118. [Google Scholar] [CrossRef]
- Kairouz, P.; McMahan, H.B.; Avent, B.; Bellet, A.; Bennis, M.; Bhagoji, A.N.; Bonawitz, K.; Charles, Z.; Cormode, G.; Cummings, R.; et al. Advances and open problems in federated learning. Found. Trends® Mach. Learn. 2021, 14, 1–210. [Google Scholar] [CrossRef]
- Lim, W.Y.B.; Luong, N.C.; Hoang, D.T.; Jiao, Y.; Liang, Y.C.; Yang, Q.; Niyato, D.; Miao, C. Federated Learning in Mobile Edge Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2031–2063. [Google Scholar] [CrossRef]
- Mahmood, N.H.; Böcker, S.; Munari, A.; Clazzer, F.; Moerman, I.; Mikhaylov, K.; López, O.L.A.; Park, O.; Mercier, E.; Bartz, H.; et al. White Paper on Critical and Massive Machine Type Communication Towards 6G. arXiv 2020, arXiv:2004.14146. [Google Scholar]
- Wirz, R.; Torres, L.G.; Swaney, P.J.; Gilbert, H.; Alterovitz, R.; Webster, R.J.; Weaver, K.D.; Russell, P.T. An experimental feasibility study on robotic endonasal telesurgery. Neurosurgery 2015, 76, 479. [Google Scholar] [CrossRef]
- Gupta, R.; Shukla, A.; Tanwar, S. BATS: A Blockchain and AI-empowered Drone-assisted Telesurgery System towards 6G. IEEE Trans. Netw. Sci. Eng. 2020, 8, 2958–2967. [Google Scholar] [CrossRef]
- Gupta, R.; Thakker, U.; Tanwar, S.; Obaidat, M.S.; Hsiao, K.F. BITS: A Blockchain-driven Intelligent Scheme for Telesurgery System. In Proceedings of the 2020 International Conference on Computer, Information and Telecommunication Systems (CITS), Hangzhou, China, 5–7 October 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Ahmad, I.; Asghar, Z.; Kumar, T.; Li, G.; Manzoor, A.; Mikhaylov, K.; Shah, S.A.; Höyhtyä, M.; Reponen, J.; Huusko, J.; et al. Emerging Technologies for Next Generation Remote Health Care and Assisted Living. IEEE Access 2022, 10, 56094–56132. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Yang, B.; Cao, X.; Xiong, K.; Yuen, C.; Guan, Y.L.; Leng, S.; Qian, L.; Han, Z. Edge Intelligence for Autonomous Driving in 6G Wireless System: Design Challenges and Solutions. IEEE Wirel. Commun. 2021, 28, 40–47. [Google Scholar] [CrossRef]
- Qi, W.; Li, Q.; Song, Q.; Guo, L.; Jamalipour, A. Extensive Edge Intelligence for Future Vehicular Networks in 6G. IEEE Wirel. Commun. 2021, 28, 128–135. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Seddik, K.; Elsabrouty, M.; Muta, O.; Furukawa, H.; Abdel-Rahman, A. Game Theory Meets Wireless Sensor Networks Security Requirements and Threats Mitigation: A Survey. Sensors 2016, 16, 1003. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Muta, O. A Game-Theoretic Approach for Enhancing Security and Data Trustworthiness in IoT Applications. IEEE Internet Things J. 2020, 7, 11250–11261. [Google Scholar] [CrossRef]
- Almeida, J.; Rufino, J.; Alam, M.; Ferreira, J. A Survey on Fault Tolerance Techniques for Wireless Vehicular Networks. Electronics 2019, 8, 1358. [Google Scholar] [CrossRef]
- Zhou, Z.; Yu, H.; Xu, C.; Zhang, Y.; Mumtaz, S.; Rodriguez, J. Dependable Content Distribution in D2D-Based Cooperative Vehicular Networks: A Big Data-Integrated Coalition Game Approach. IEEE Trans. Intell. Transp. Syst. 2018, 19, 953–964. [Google Scholar] [CrossRef]
- Boukerche, A.; Kantarci, B.; Kaptan, C. Towards ensuring the reliability and dependability of vehicular crowd-sensing data in GPS-less location tracking. Pervasive Mob. Comput. 2020, 68, 101248. [Google Scholar] [CrossRef]
- Olowononi, F.O.; Rawat, D.B.; Liu, C. Dependable Adaptive Mobility in Vehicular Networks for Resilient Mobile Cyber Physical Systems. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Chakrabarti, K. Deep learning based offloading for mobile augmented reality application in 6G. Comput. Electr. Eng. 2021, 95, 107381. [Google Scholar] [CrossRef]
- Arpaia, P.; De Benedetto, E.; Dodaro, C.A.; Duraccio, L.; Servillo, G. Metrology-Based Design of a Wearable Augmented Reality System for Monitoring Patient’s Vitals in Real Time. IEEE Sensors J. 2021, 21, 11176–11183. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, Q. Code-Partitioning Offloading Schemes in Mobile Edge Computing for Augmented Reality. IEEE Access 2019, 7, 11222–11236. [Google Scholar] [CrossRef]
- Zhang, X.; Slavin, R.; Wang, X.; Niu, J. Privacy Assurance for Android Augmented Reality Apps. In Proceedings of the 2019 IEEE 24th Pacific Rim International Symposium on Dependable Computing (PRDC), Kyoto, Japan, 1–3 December 2019; pp. 114–1141. [Google Scholar] [CrossRef]
- Bahaei, S.S.; Gallina, B.; Laumann, K.; Skogstad, M.R. Effect of Augmented Reality on Faults Leading to Human Failures in Socio-technical Systems. In Proceedings of the 2019 4th International Conference on System Reliability and Safety (ICSRS), Rome, Italy, 20–22 November 2019; pp. 236–245. [Google Scholar] [CrossRef]
- Sterbenz, J.P.; Hutchison, D.; Çetinkaya, E.K.; Jabbar, A.; Rohrer, J.P.; Schöller, M.; Smith, P. Resilience and survivability in communication networks: Strategies, principles, and survey of disciplines. Comput. Netw. 2010, 54, 1245–1265. [Google Scholar] [CrossRef]
- Nunes, B.A.A.; Mendonca, M.; Nguyen, X.N.; Obraczka, K.; Turletti, T. A survey of software-defined networking: Past, present, and future of programmable networks. IEEE Commun. Surv. Tutor. 2014, 16, 1617–1634. [Google Scholar] [CrossRef]
- Namal, S.; Ahmad, I.; Gurtov, A.; Ylianttila, M. Enabling secure mobility with OpenFlow. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; pp. 1–5. [Google Scholar]
- Ahmad, I.; Liyanage, M.; Namal, S.; Ylianttila, M.; Gurtov, A.; Eckert, M.; Bauschert, T.; Faigl, Z.; Bokor, L.; Saygun, E.; et al. New concepts for traffic, resource and mobility management in software-defined mobile networks. In Proceedings of the 2016 12th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Cortina d’Ampezzo, Italy, 20–22 January 2016; pp. 1–8. [Google Scholar]
- Namal, S.; Ahmad, I.; Gurtov, A.; Ylianttila, M. SDN based inter-technology load balancing leveraged by flow admission control. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; pp. 1–5. [Google Scholar]
- García-Martín, E.; Rodrigues, C.F.; Riley, G.; Grahn, H. Estimation of energy consumption in machine learning. J. Parallel Distrib. Comput. 2019, 134, 75–88. [Google Scholar] [CrossRef]
| Dependability | Challenge | Potential Future Research Directions |
|---|---|---|
| Reliability | Distributed control and management will increase the complexity of the overall system which can lead to reliability challenges. | Dependable 6G would require a hierarchical architecture that provide logical centralized view of the overall network including the architecture and infrastructure elements, and loosely coupled distributed control elements, all synchronized through a global view can simplify the overall system. |
| Availability | Due to the distributed control, availability can be increased in principle, however, availability can be compromised through weaknesses in security, reliability and safety. | The architecture should be modular and distributed as it is, and designed such that the effects of cascading failures are avoided, where availability of one module or component does not compromise the availability of another. |
| Safety | Safety is a rarely researched topic from technical perspectives and is intertwined with security. | The main work needed in increasing safety of future communications networks is defining safety in technical terms and aligning safety research with the rest, similar to security-by-design, safety-by-design must be brought into discussions and research. |
| Security | Security in 6G is extremely complicated in terms of new technologies, modular distributed design, and the increasingly vanishing physical-cyber borders leading to highly complex network architectures. | First, it will be important to know early whether to build 6G security on top of the 5G standards or rethink according to the new disruptive technologies from application to physical layers. How to design security systems for the loosely coupled, highly distributed, and inter-dependent systems that are synchronized on one hand and avoid the risks related to cascading failures on the other hand, will be extremely important. Furthermore, AI related risks and challenges including its sustainability will exacerbate in 6G and will require serious research efforts. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, I.; Rodriguez, F.; Huusko, J.; Seppänen, K. On the Dependability of 6G Networks. Electronics 2023, 12, 1472. https://doi.org/10.3390/electronics12061472
Ahmad I, Rodriguez F, Huusko J, Seppänen K. On the Dependability of 6G Networks. Electronics. 2023; 12(6):1472. https://doi.org/10.3390/electronics12061472
Chicago/Turabian StyleAhmad, Ijaz, Felipe Rodriguez, Jyrki Huusko, and Kari Seppänen. 2023. "On the Dependability of 6G Networks" Electronics 12, no. 6: 1472. https://doi.org/10.3390/electronics12061472
APA StyleAhmad, I., Rodriguez, F., Huusko, J., & Seppänen, K. (2023). On the Dependability of 6G Networks. Electronics, 12(6), 1472. https://doi.org/10.3390/electronics12061472









