Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool
Abstract
:1. Introduction
- A vulnerability refers to a weakness or flaw in a system that puts information security at risk. An attacker could exploit it to compromise the integrity, availability, or confidentiality of information, hence the need for detection and elimination.
- A threat is related to an action that exploits a known vulnerability to attack the security of an information system. They can come from provoked attacks (viruses, theft), physical events (fire, power failure), or negligence in the use of systems (unencrypted connections, missing passwords). Vulnerabilities can always be exploited, hence threats.
- A risk refers to the likelihood of a security incident occurring and materializing as a threat.
1.1. Motivation
- Increased Attack Surface: The proliferation of IoT devices in smart buildings leads to a larger attack surface. Each connected device represents a potential entry point for cyber threats.
- Lack of Standardization: The diversity of IoT devices often results in a lack of standardized security protocols. This variability makes implementing consistent and adequate security measures across all devices challenging.
- Insecure Devices: Many IoT devices are designed with a focus on functionality and cost, rather than robust security. This makes them susceptible to exploitation by malicious actors.
- Insufficient Authentication and Authorization: Weak authentication mechanisms and inadequate authorization processes in IoT devices can make it easier for unauthorized entities to access sensitive systems and data.
- Data Privacy Concerns: IoT devices often collect and transmit sensitive data. These data can be intercepted or manipulated if not adequately secured, leading to privacy breaches and potential misuse.
- Supply Chain Risks: Security vulnerabilities may be introduced at various IoT device supply chain stages, from manufacturing to deployment. Malicious actors can exploit these weaknesses for their benefit.
- Limited Update Mechanisms: Some IoT devices lack robust mechanisms for receiving security updates. This makes them vulnerable to known exploits, as patches and fixes may not be promptly applied.
- Interconnectedness: The interconnected nature of IoT systems means that a compromise in one device can have a cascading effect, potentially affecting the entire smart building ecosystem.
- Insufficient Encryption: Inadequate encryption practices in communication between IoT devices and central systems can expose sensitive information to eavesdropping and unauthorized access.
1.2. Our Contributions
- A detailed study of the primary risks, threats, and vulnerabilities found in intelligent buildings and their components;
- Vulnerability classification databases and associated nomenclature are reviewed, to serve as a tutorial for future research works;
- Analysis and guidelines for Shodan as a potential tool to detect vulnerabilities;
- Based on previous analysis, we propose a three-step methodology utilizing the Shodan search engine to gather information from the real world. This is applied to smart building environments for smart cities;
- The obtained results are thoroughly analyzed, to determine which of these vulnerabilities can be potentially exploited.
2. State of the Art: Smart Building and Technologies
2.1. Smart Buildings
2.2. Technologies in Smart Buildings
2.3. Vulnerability Detection and Tools
3. Vulnerabilities in Connected Buildings
3.1. Common Threats in Smart Buildings
3.1.1. Communication Protocols: Common Characteristics and Threats
3.1.2. Threats Related to Specific Systems
- Concerning connectivity, it is noteworthy that all three options endorse WiFi security protocols. The device may face harm if the network is attacked via weak security measures in the wireless protocol. With regards to the Honeywell range of thermostats, there may be some issues initially. During setup, an attacker may be able to register the thermostat by collecting information provided by the thermostat’s web server before the user has a chance to complete registration. This vulnerability can be prevented by using a secret value for registration and implementing a protocol such as WPA2 (WiFi protected access);
- In terms of cloud connection, all three options employ encryption techniques, ensuring that no sensitive data are exposed. In the case of Nest, the device can utilize CA to authenticate the identity of remote web servers by establishing TLS connections, thereby rendering it impervious to man-in-the-middle attacks;
- Access to this form of home thermostat can be obtained through either a web portal or a mobile application, which facilitates its management. If the password has a low level of security, an unauthorized user may commandeer the system without prior consent. Additionally, Ecobee thermostats offer an API for device interaction, which presents a new possible vulnerability.
- Device scanning: The MAC (medium access control) address space can be monitored to determine the status of all online sockets. This could reveal which users are using default passwords;
- Brute force attack: If password changes are made, they may disrupt processes;
- Spoofing attack: The remote application may be manipulated to send a user’s authentication credentials, which can then be intercepted for login purposes;
- Firmware attack: The goal here is to have malicious firmware loaded on the socket, even allowing root access to the system.
- Denial of service (DoS): With this type of attack, access to monitoring and management of building resources can be blocked through the mobile interface, posing a risk to the building;
- Power and internet supply failure: For the former, the presence of backup batteries can minimize its occurrence. For the latter, it is advisable to have a backup service;
- Malicious code injection: This requires the execution of code or scripts via an exploit. The attacker aims to gain complete access to the home control application and potentially steal the user’s personal data;
- Software failures: These malfunctions can be resolved through consistent updates and manufacturer support;
- Attacks using weak encryption mechanisms and passwords: The confidentiality of user data is jeopardized during authentication by weak encryption mechanisms and passwords;
- Eavesdropping attack: Real-time information transmitted by smart devices through the network can be obtained;
- Man-in-the-middle attack: Data are first sent to an intermediary, which can manipulate them. Appropriate communication protocols can reduce these risks.
- Denial of service: Blocking the radio frequency spectrum can result in the denial of remote access. This can be achieved through radio or Bluetooth interference. Real-time traffic analysis is currently employed to detect this issue, and channel hopping is a widely used measure to avoid it;
- Lack of authentication and encryption: Devices using the same communication standard as the lighting system can easily connect to it, as there are no encryption or authentication schemes for incoming connections. This opens up the possibility of unauthorized users modifying the behavior of the lighting. In the specific case of ZLL, relying solely on the use of a network master key is critical;
- Malicious firmware updates: Attackers can exploit the microcontroller for over-the-air updates, to facilitate undesirable actions. The firmware’s physical access port can also be used for malicious purposes, including brute force or denial-of-service attacks.
- Side channel attack (SCA): This technique exploits physical parameters and cryptographic implementation weaknesses. This method can obtain details about the communication process and circumvent encryption by altering the physical parameters of the device.
3.2. Global Mitigation Strategies
- Increase security awareness and develop security know-how: different actors need to be aware of the issues involved in exposing buildings to the threats described, from developers, integrators, or suppliers to maintenance personnel and end users. It is important to make good choices when selecting the devices to be used, configuring the network, updating the different elements, etc. Small training sessions adapted to the profile of the specific actor can contribute to this training, progressively reduce the existing margin for improvement, avoid unnecessary risks, and permit dealing with emergency situations [40,44]. Simple operations, such as modifying default user credentials or not executing and downloading files from unknown sources, should become common practice [58]. Likewise, from a hardware perspective, device configuration should not be manipulated without prior knowledge, as this can become a gateway to a new threat, resulting from a lack of knowledge [54];
- Having a matrix of responsibilities: if the specific activities that should be reviewed and executed by different actors have been previously determined, it is possible to have greater control over the actions carried out in the building in terms of security [44];
- Ongoing system maintenance: Regularly updating the operating system and firmware by applying security patches is essential. To do this, it is necessary to select devices that support this type of update in advance and for vendors to offer this alternative. In addition, the standard approach should be to remove all services that are not clearly needed and close ports that will not be used intentionally [40]. In this regard, it is important to perform regular audits, to be aware of threats, system hot spots, and vulnerabilities already identified [44];
- Device software updates: vendors should offer these patches but also inform customers about them. On the other hand, customers must be able to apply them, i.e., the update mechanism must not be too complex for the intended user. From the software point of view, it is up to developers to bring trusted applications to the market using strong and secure encryption [44,54].
- Network monitoring mechanisms: to be able to identify intruders and detect potential threats in advance [44,54]., by first capturing packets to have a database that characterizes normal activity, and then being able to identify abnormal activity with good results [39]. For intrusion detection, physical measurements can be used as an alternative to unmask anomalies in the system if they are meaningless.
- Protecting the system from denial of service attacks: routing access restrictions, detection of false routing information, and detection of wormholes can be configured [39];
- Provide some degree of modularity between the elements of different systems: this allows preventing an attack on one entity from compromising all the others. A good practice is to configure the global system so that different networks exist, avoiding attackers having access to more if one network is compromised. Conversely, it should be noted that monitoring different networks may require additional maintenance efforts [40,44,59];
- Having backup systems for critical elements of the systems [40].
4. Shodan Tool Overview
4.1. The Shodan Tool
4.2. General Concepts about the Use of Shodan
5. Detecting Vulnerabilities with Shodan
5.1. Detection Methodology
- Data collection: different sources of information were analyzed. A series of key terms were identified to be used in the searches, to obtain data on the devices of interest. The terms used included the different types of devices considered within a smart building (connected camera, smart meter, smart thermostat, smart home, etc.) and variants, such as the proper names of specific devices and their manufacturers. In the first phase, tests were carried out manually via the web interface offered by the tool, using simple filters. Once interesting results had been found, it was necessary to consult additional information on the type of device, which could be provided through the manufacturer’s documentation, user manuals, etc.;
- Results extraction: a set of scripts in Python programming language was programmed to interact with the Shodan API. The Shodan interface allowed us to perform very general queries on specific devices, but it was more appropriate to automate the analysis of detailed cases using the API. The query strings used the same simple terms and filters as explored in the previous block. The returned data were processed and labeled to facilitate the results extraction block;
- Vulnerability identification: the results obtained were analyzed to identify security vulnerabilities. The results were checked against the information available in the Common Vulnerabilities and Exposures (CVE) database for equivalent terms and other selected search terms listed below, which allowed completing the particular analysis of each case. After compiling the results, manual checks were carried out to ensure their validity, and the most frequent vulnerabilities were also consulted in the National Vulnerability Database, to complete the information and obtain the severity score for each.
5.2. Data Sources
5.3. Vulnerability Classification
- Base metrics: these refer to intrinsic qualities of a vulnerability that are not dependent on time and environment, and present in all user environments. In turn, they consist of two groups of metrics: those of exploitability, and those of impact. Exploitability reflects the ease and technical means with which a vulnerability can be exploited (AV, AC, PR, UI), while impact reflects the direct consequence of using an exploit successfully (C, I, A). Finally, the scope (S) metric complements the global assessment of the previous metrics, providing a higher or lower value to the result, depending on the resources affected (Table 4);
- Temporal metrics: these refer to vulnerability characteristics that change over time but are constant in a user’s environment. They are a set of optional metrics, whose value can be omitted;
- Environment metrics: refer to vulnerability characteristics related to a particular user’s environment. Optional set of metrics, which may not be used in the final assessment if no particular metric exists.
6. Results
6.1. Relevant Manual Searches
- Webcams. It is common to find video surveillance systems that use default credentials or passwords that are easy to crack. This is the case with Blue Iris, the IP camera management software for Windows. It is possible to view all content via the integrated UI3 web server and using the term “ui3 -” yielded 193 results. The lack of authentication on the devices allowed access to live cameras without specifying any parameters. Similarly, running the query “IP CAMERA Viewer” yielded 338 devices, many of them offering access to live cameras without authentication.
- Smart thermostats. Information associated with two types of devices was found in the search for smart thermostat management applications that were not password protected. The ICY Clever thermostat could be accessed through the query title: “ICY Clever Thermostat”, while the Heatmiser WiFi thermostat could be accessed through the filter title: “Status & Control”, obtaining 12 and 164 results, respectively.
- Network elements. The query “default password” returned a significant number of devices with default passwords. By combining that information with specific filters to find specific devices, such as with the query “default password” product: “TP-LINK WR841N WAP http config”, we could access that router model.
- Smart home systems. Providing access to the management software of individual smart devices, such as a thermostat, is dangerous, and even more so at the building level. This is the case if access to home applications, such as those offered by FHEM, OpenHAB, and HomeMatic, is not properly protected. FHEM can be controlled directly via the web or a smartphone, and the query “FHEM home automation” returned 47 results. HomeMatic offers a similar solution for different activities in the home. The search query “homematic” returned 751 results. Finally, OpenHAB allows connecting devices and services from different providers. The default search for OpenHAB returned four results, some of them fully accessible.
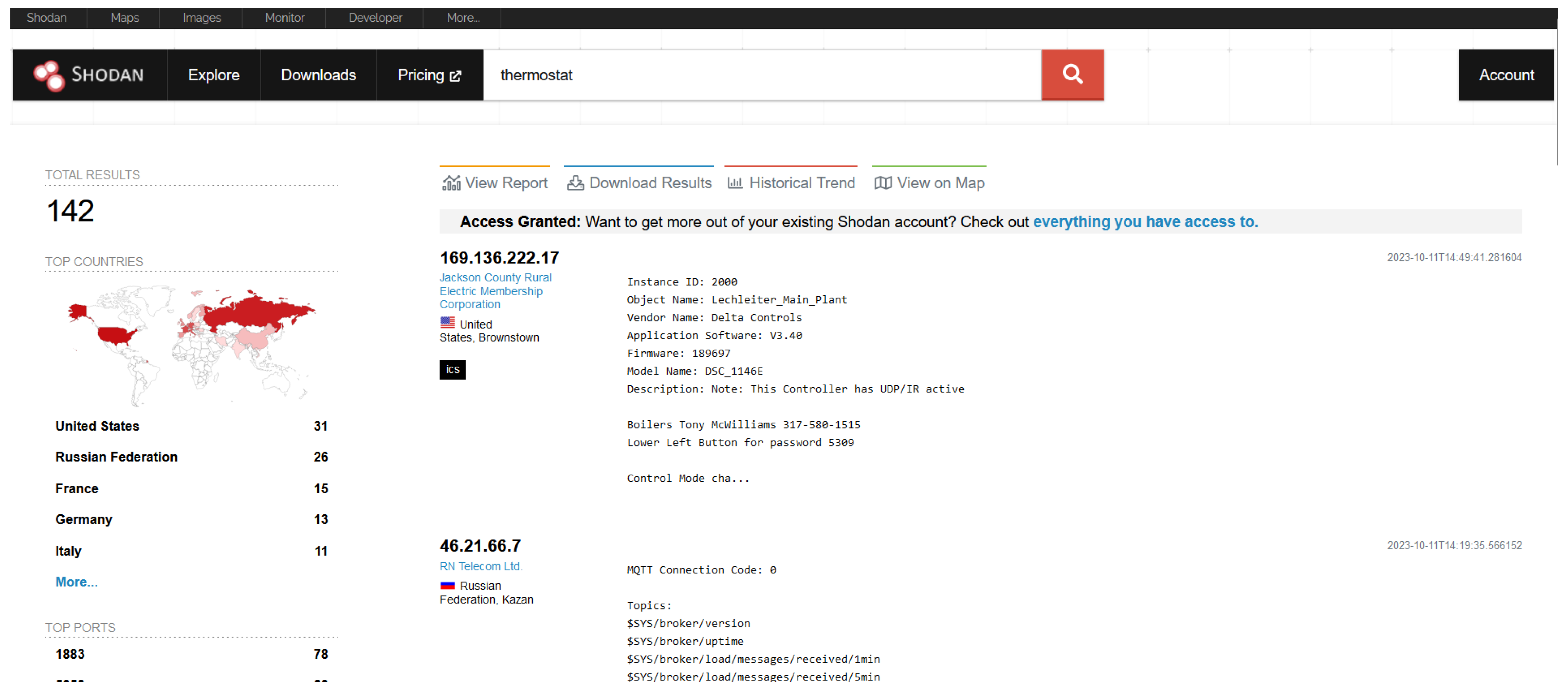
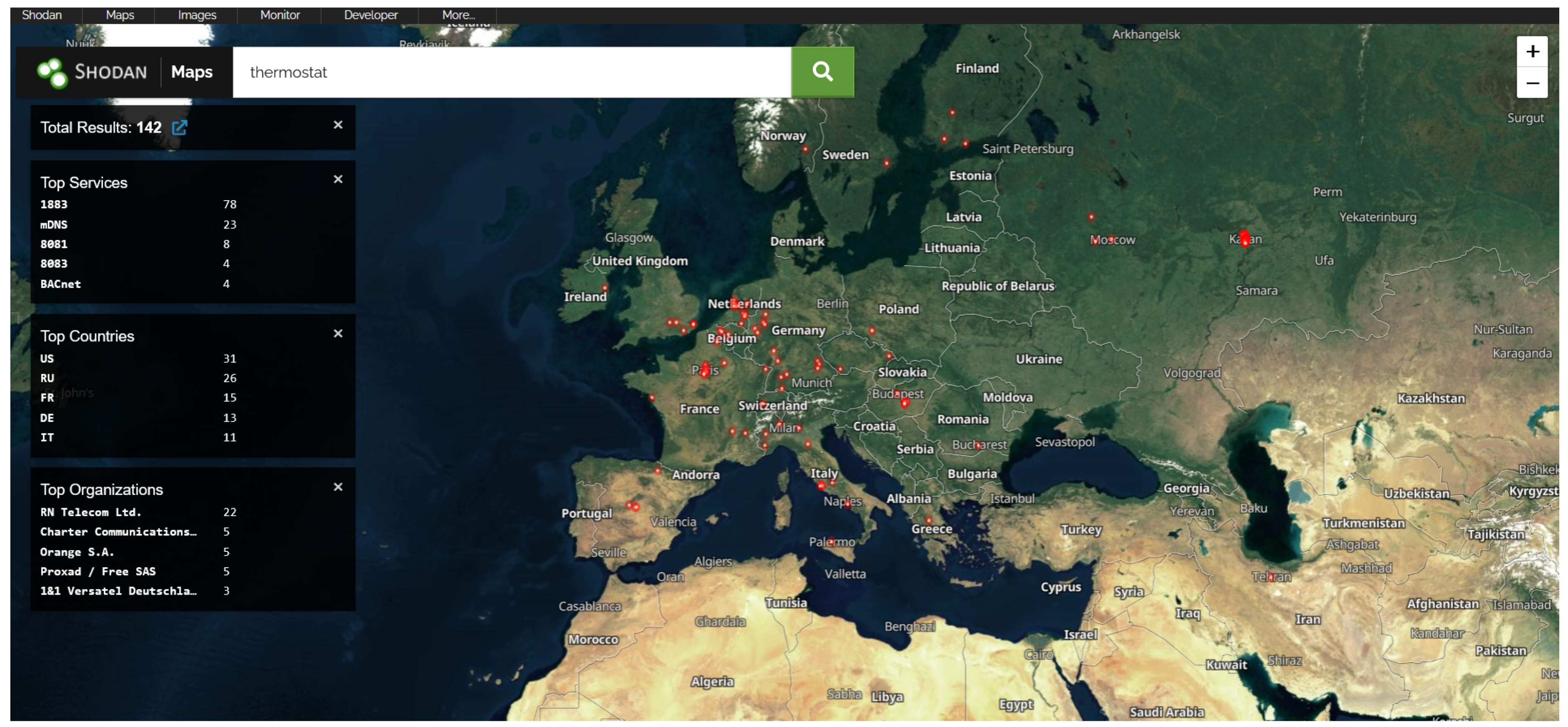
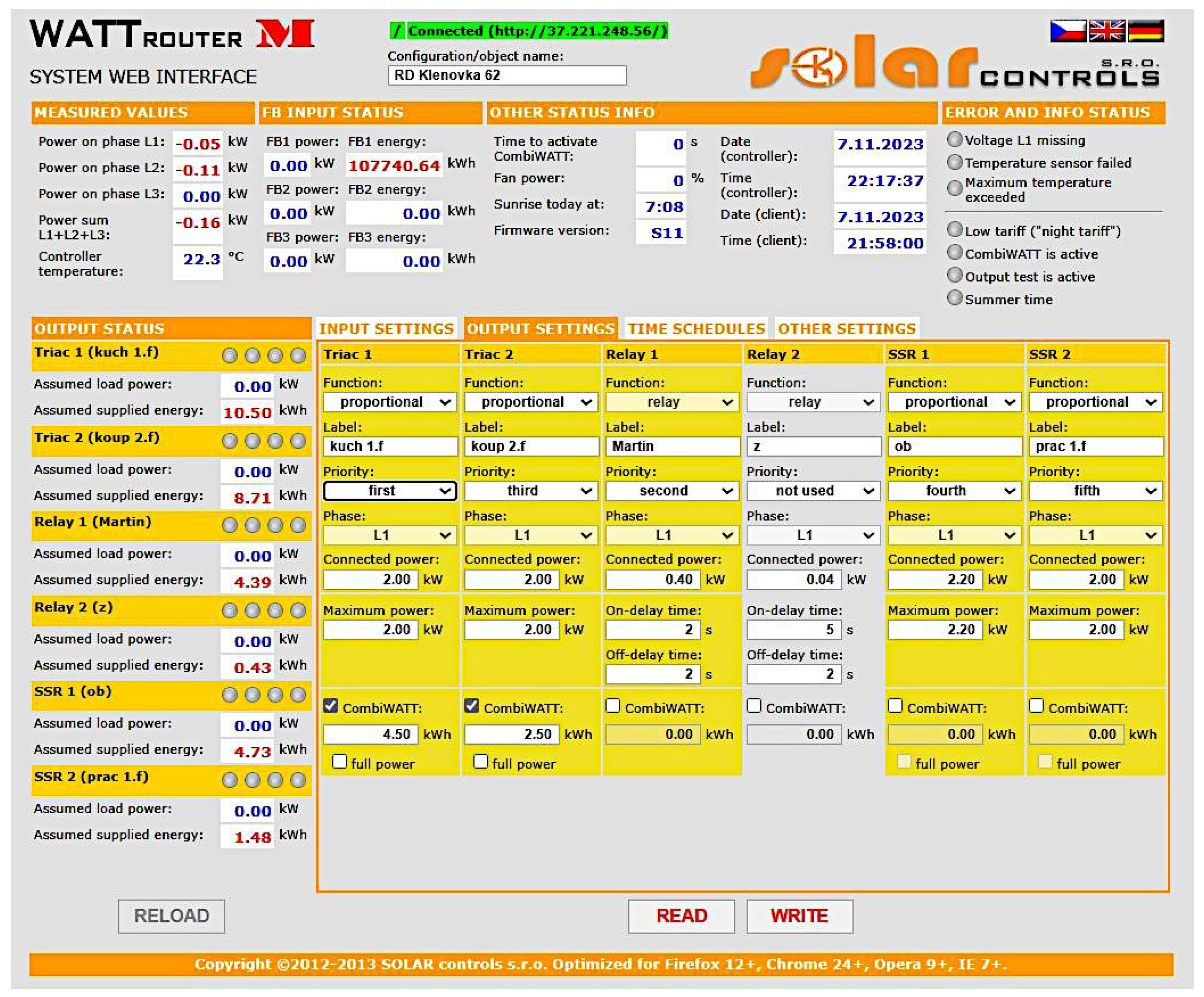
- Grid elements The solar country: CZ search identified several IPs associated with solar farms. Some of them were not protected, and through the WATTrouter Mx tool, which is a programmable controller for optimizing the self-consumption of the energy produced by a PV plant, it was possible to obtain the information of the installations. Figure 4, Figure 5 and Figure 6 show some of the results obtained for the devices mentioned in this sub-section.
6.2. Manual and API Searches
- Smart thermostat. For the smart thermostat group, the specific device selected was a Heatmiser Wifi Thermostat. No vulnerabilities associated with the specific device type were obtained in either of the two cases analyzed. On the other hand, it was observed that the problems with the highest incidence were related to communication protocols and the use of specific servers and databases. Two examples of vulnerabilities obtained for the global category and one example for the specific thermostat model were selected. Their information is shown in Table 7. The three selected vulnerabilities have a critical severity, and all of them have associated exploits to exploit them.
- Smart Plug. The specific device selected was a WeMo Switch, and no vulnerabilities were found in any of the directions found in Shodan. No vulnerabilities associated with this type of specific device were found in the global case. It was also observed that the problems with the highest incidence were related to communication protocols, and the use of specific servers and databases. Two examples of vulnerabilities obtained for the global category were selected. This information is shown in Table 7. The first vulnerability has a medium severity, while the second one is critical. In addition, both have an associated exploit to exploit the vulnerability in the system.
- Smart Camera. The specific device selected was the D-Link DCS-2121. No vulnerabilities associated with the specific type of device were found in either of the two cases analyzed. On the other hand, it can be seen that the problems with the highest incidence were related to communication protocols, the use of specific servers, and the operating system. One example of a vulnerability was selected for the global category, and another for the chosen camera model. This information is shown in Table 7. The first vulnerability has a medium severity, while the second one is high. In addition, both have an associated exploit. In the case of the global category, the results included vulnerabilities already analyzed in previous sections, specifically: CVE-2018-1312 with 13 occurrences, CVE-2017-7679 with 12 occurrences, and CVE-2017-15906 with 5 occurrences. For the specific device analyzed, the vulnerability CVE-2019-0220 was also found 2 times and CVE-2018-1312 another 2 times.
- Smartphone and applications. The specific device selected for the management of different systems in the building was HomeMatic. No vulnerabilities associated with this specific type of device were found in either of the two cases analyzed. On the other hand, it can be seen that the problems with the highest incidence were related to communication protocols, the use of specific servers, and databases. Two examples of vulnerabilities obtained were selected, one for the global category, and the other for the selected application model. This information is shown in Table 7. The first vulnerability has a medium severity, while the second one has a high severity. In addition, both have associated exploits (1 for the first, and 2 for the second). In the case of the global category, the results included vulnerabilities already analyzed in previous sections, specifically: CVE-2017-15906 10 times, CVE-2018-1312 with 5 occurrences, CVE-2017-7679 with 5 occurrences, and CVE-2019-0220 with 5 occurrences. For the specific device analyzed, the vulnerability CVE-2019-0220 was also found 7 times, CVE-2018-1312 6 times, CVE-2017-15906 5 times, and CVE-2018-15919 5 times.
- Smart Lighting. For the smart lighting group, the results obtained are included in Table 6. The specific device selected within the category was a Philips Hue. No vulnerabilities associated with the specific device type were obtained in either of the two cases analyzed. On the other hand, it can be seen that the problems with the highest incidence were related to communication protocols, the use of specific servers, the operating system, and databases. An example of vulnerability obtained for the global category has been selected. This information is shown in Table 7. The vulnerability analyzed has a medium severity and also has 2 associated exploits. In the case of the global category, the results included vulnerabilities already analyzed in the previous sections, specifically CVE-2019-0220 with 4 occurrences; as well as CVE-2018-17199 and CVE 2018-1312, CVE-2019-0211 on 3 occasions; and on 2 occasions, CVE-2018-15919 and CVE-2017-15906. For the specific category, we again found twice the vulnerabilities CVE-2019-0220, CVE-2019-0211 and CVE-2018-15919, while 1 time we found CVE 2018-1312.
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| API | Application Programming Interface |
| BACnet | Building Automation and Control networks |
| BIM | Building Information Modeling |
| BLE | Bluetooth Low Energy |
| BPIE | Buildings Performance Institute Europe |
| CABA | Continental Automated Buildings Association |
| CIB | International Council for Building Research and Innovation in Building and Construction |
| CSV | Comma-Separated Values |
| CVE | Common Vulnerabilities Exposures |
| CVSS | Common Vulnerability Space System |
| DoS/DDoS | Denial of Service/Distributed Denial of Service |
| DSL | Digital Subscriber Line |
| DCCNN | Dual Channel Convolution Neural Network |
| DVR | Digital Video Recorder |
| EC | European Commission |
| FTP | File Transfer Protocol |
| HTTP | Hypertext Transfer Protocol |
| HVAC | Heating, Ventilation and Air Conditioning |
| IBM | International Business Machines Corporation |
| IEEE | Institute of Electrical and Electronics Engineers |
| IBI | Intelligent Building Institution |
| IoT | Internet of Things |
| IP | Internet Protocol |
| JSON | JavaScript Object Notation |
| LON | Local Operating Network |
| MAC | Medium Access Control |
| ML | Machine Learning |
| MiTM | Man-in-The-Middle |
| MQTT | Message Queuing Telemetry Transport |
| NAS | Network Attached Storage |
| Nmap | Network mapper |
| NTP | Network Time Protocol |
| NVD | National Vulnerability Database |
| RDP | Remote Desktop Protocol |
| RTP/SRTP | Real-time Transport Protocol/Secure Real-time Transport Protocol |
| SCA | Side-Channel Attack |
| SCADA | Supervisory Control And Data Acquisition |
| SMO | Spider Monkey Optimization |
| SNMP | Simple Network Management Protocol |
| SSH | Secure Shell |
| SSL/TLS | Secure Sockets Layer/Transport Layer Security |
| SVM | Support Vector Machine |
| TCP | Transport Layer Security |
| Telnet | Teletype Network |
| ICT | Information and Communication Technology |
| UDP | User Datagram Protocol |
| WiFi | Wireless Fidelity |
| WPA | WiFi Protected Access |
| XML | EXtensive Markup Language |
| ZLL | Zigbee Light Link |
References
- Beyrouti, M.; Lounis, A.; Lussier, B.; Bouadallah, A.; Samhat, A.E. Vulnerability and Threat Assessment Framework for Internet of Things Systems. In Proceedings of the 6th Conference on Cloud and Internet of Things (CIoT), Lisbon, Portugal, 20–22 March 2023; pp. 62–69. [Google Scholar] [CrossRef]
- Villar Miguelez, C.; Monzon Baeza, V.; Parada, R.; Monzo, C. Guidelines for Renewal and Securitization of a Critical Infrastructure Based on IoT Networks. Smart Cities 2023, 6, 728–743. [Google Scholar] [CrossRef]
- Tarazona Lizarraga, C. Análisis de las Necesidades de una Smart City en el Marco de un Desarrollo Sostenible; Universitat Oberta de Catalunya: Barcelona, Spain, 2020. [Google Scholar]
- Omar, S. Intelligent building, definitions, factors and evaluation criteria of selection. Alex. Eng. J. 2018, 57, 2903–2910. [Google Scholar] [CrossRef]
- Mulero Palencia, S. Vulnerabilidades en Edificios Inteligentes; Universitat Oberta de Catalunya: Barcelona, Spain, 2021. [Google Scholar]
- Commission, E. Smart Building: Energy Efficiency Application. 2017. Available online: https://ati.ec.europa.eu/sites/default/files/2020-06/Smart%20Building-%20Energy%20efficiency%20application%20%28v1%29.pdf (accessed on 1 October 2023).
- IEEE Std 2785-2023; IEEE Standard for Architectural Framework and General Requirements for Smart Home Systems. IEEE: Piscataway, NJ, USA, 2023; pp. 1–50. [CrossRef]
- Eneyew, D.D.; Capretz, M.A.M.; Bitsuamlak, G.T. Toward Smart-Building Digital Twins: BIM and IoT Data Integration. IEEE Access 2022, 10, 130487–130506. [Google Scholar] [CrossRef]
- Ma, G.; Dang, S.; Alouini, M.S.; Shihada, B. Smart Buildings Enabled by 6G Communications. IEEE Internet Things Mag. 2022, 5, 181–186. [Google Scholar] [CrossRef]
- Mohammed, B.H.; Sallehudin, H.; Mohamed, S.A.; Satar, N.S.M.; Hussain, A.H.B. Internet of Things-Building Information Modeling Integration: Attacks, Challenges, and Countermeasures. IEEE Access 2022, 10, 74508–74522. [Google Scholar] [CrossRef]
- Kumari, P.; Gupta, H.P. An Energy-Efficient Smart Building System using Autonomous Networks. IEEE Commun. Stand. Mag. 2022, 6, 32–36. [Google Scholar] [CrossRef]
- Nguyen, D.H. Enhancing Building Energy Efficiency Through Its Windows. In Proceedings of the 2023 10th International Conference on Power and Energy Systems Engineering (CPESE), Nagoya, Japan, 8–10 September 2023; pp. 141–146. [Google Scholar] [CrossRef]
- Kim, D.; Yoon, Y.; Lee, J.; Mago, P.J.; Lee, K.; Cho, H. Design and Implementation of Smart Buildings: A Review of Current Research Trend. Energies 2022, 15, 4278. [Google Scholar] [CrossRef]
- Yagüe García, S. Análisis del rol de las Casas Inteligentes en Smart City; Universitat Oberta de Catalunya: Barcelona, Spain, 2021. [Google Scholar]
- Aliero, M.S.; Qureshi, K.N.; Pasha, M.F.; Jeon, G. Smart Home Energy Management Systems in Internet of Things networks for green cities demands and services. Environ. Technol. Innov. 2021, 22, 101443. [Google Scholar] [CrossRef]
- Apanavičienė, R.; Shahrabani, M.M.N. Key Factors Affecting Smart Building Integration into Smart City: Technological Aspects. Smart Cities 2023, 6, 1832–1857. [Google Scholar] [CrossRef]
- Habash, R. 4 - Building as a smart system. In Sustainability and Health in Intelligent Buildings; Habash, R., Ed.; Woodhead Publishing Series in Civil and Structural Engineering; Woodhead Publishing: Sawston, UK, 2022; pp. 95–128. [Google Scholar] [CrossRef]
- Qolomany, B.; Al-Fuqaha, A.; Gupta, A.; Benhaddou, D.; Alwajidi, S.; Qadir, J.; Fong, A.C. Leveraging Machine Learning and Big Data for Smart Buildings: A Comprehensive Survey. IEEE Access 2019, 7, 90316–90356. [Google Scholar] [CrossRef]
- IoTSF. Can You Trust Your Smart Building? Understanding the Security Issues and Why They Are Important to You. 2019. Available online: https://www.iotsecurityfoundation.org/wp-content/uploads/2019/07/IoTSF-Smart-Buildings-White-Paper-PDFv2.pdf (accessed on 1 October 2023).
- Li, G.; Ren, L.; Fu, Y.; Yang, Z.; Adetola, V.; Wen, J.; Zhu, Q.; Wu, T.; Candan, K.; O’Neill, Z. A critical review of cyber-physical security for building automation systems. Annu. Rev. Control 2023, 55, 237–254. [Google Scholar] [CrossRef]
- Bi, Y.; Huang, J.; Liu, P.; Wang, L. Benchmarking Software Vulnerability Detection Techniques: A Survey. arXiv 2023, arXiv:2303.16362. [Google Scholar]
- Jain, V.K.; Tripathi, M. Multi-Objective Approach for Detecting Vulnerabilities in Ethereum Smart Contracts. In Proceedings of the 2023 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 16–18 August 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Mariappan, U.; Balakrishnan, D.; Rajendran, S.; Alagusundar, N.; Sheriff, A.A.; K, A. Cyber Security Threat Detection in Internet of Things Using Optimized Deep Learning Technique. In Proceedings of the 2023 3rd Asian Conference on Innovation in Technology (ASIANCON), Ravet, IN, India, 25–27 August 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Saidin, S.B.; Hisham, S.B.I. A Survey on Supervised Machine Learning in Intrusion Detection Systems for Internet of Things. In Proceedings of the 2023 IEEE 8th International Conference On Software Engineering and Computer Systems (ICSECS), Penang, Malaysia, 25–27 August 2023; pp. 419–423. [Google Scholar] [CrossRef]
- Khatri, A.; Khatri, R. DDoS Attack Detection Using Artificial Neural Network on IoT Devices in a Simulated Environment. In International Conference on IoT, Intelligent Computing and Security: Select Proceedings of IICS 2021; Agrawal, R., Mitra, P., Pal, A., Sharma Gaur, M., Eds.; Springer: Singapore, 2023; pp. 221–233. [Google Scholar]
- Abdaljabar, Z.H.; Ucan, O.N.; Ali Alheeti, K.M. An Intrusion Detection System for IoT Using KNN and Decision-Tree Based Classification. In Proceedings of the 2021 International Conference of Modern Trends in Information and Communication Technology Industry (MTICTI), Sana’a, Yemen, 4–6 December 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Talita, A.S.; Nataza, O.S.; Rustam, Z. Naïve Bayes Classifier and Particle Swarm Optimization Feature Selection Method for Classifying Intrusion Detection System Dataset. J. Phys. Conf. Ser. 2021, 1752. [Google Scholar] [CrossRef]
- Salimi, S.; Kharrazi, M. VulSlicer: Vulnerability detection through code slicing. J. Syst. Softw. 2022, 193, 111450. [Google Scholar] [CrossRef]
- Tenable. Nessus Scan Tuning Guide. Available online: https://docs.tenable.com/quick-reference/nessus-scan-tuning/Content/PDF/Nessus_Scan_Tuning_Guide.pdf (accessed on 28 October 2023).
- Kali. Skipfish Home Page. Available online: https://www.kali.org/tools/skipfish/ (accessed on 28 October 2023).
- Mankali, L.; Patnaik, S.; Limaye, N.; Knechtel, J.; Sinanoglu, O. VIGILANT: Vulnerability Detection Tool Against Fault-Injection Attacks for Locking Techniques. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2023, 42, 3571–3584. [Google Scholar] [CrossRef]
- Censys. Censys Official Web Page. Available online: https://censys.io (accessed on 28 October 2023).
- ZoomEye. ZoomEye Official Web Page. Available online: https://www.zoomeye.org (accessed on 28 October 2023).
- Thingful. Thingful Official Web Page. Available online: https://www.thingful.net (accessed on 28 October 2023).
- Shodan. 2013. Available online: https://www.shodan.io/ (accessed on 1 October 2023).
- Tundis, A.; Mazurczyk, W.; Mühlhäuser, M. A Review of Network Vulnerabilities Scanning Tools: Types, Capabilities and Functioning. In Proceedings of the 13th International Conference on Availability, Reliability and Security, New York, NY, USA, 27–30 August 2018. [Google Scholar] [CrossRef]
- Safavi, S.; Meer, A.; Keneth Joel Melanie, E.; Shukur, Z. Review and Solutions. In Proceedings of the Cyber Resilience Conference (CRC), Putrajaya, Malasia, 13–15 November 2018. [Google Scholar]
- Fernández-Caramés, T.; Fraga-Lamas, P. Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through practical use cases. Sensors 2020, 20, 3048. [Google Scholar] [CrossRef]
- Ciholas, P.; Lennie, A.; Sadigova, P.; Such, J. The Security of Smart Buildings: A systematic literature review. arXiv 2019, arXiv:1901.05837. [Google Scholar]
- Brooks, D. Security threats and risks of Intelligent Building Systems: Protecting facilities from current and emerging vulnerabilities. In Security Threats and Risks of Intelligent Building Systems: Protecting Facilities from Current and Emerging Vulnerabilities; IGI Global: Hershey, PA, USA, 2012; pp. 1–16. [Google Scholar] [CrossRef]
- Graveto, V.; Cruz, T.; Simöes, P. Security of Building Automation and Control Systems: Survey and future research directions. Comput. Secur. 2022, 112, 102527. [Google Scholar] [CrossRef]
- Seferi, R.; Giangiacomi, S.; Berberi, K. Vulnerabilities and Attacks in a Smart Buildings Scenario. In Proceedings of the 2019 IEEE 23rd International Symposium on Consumer Technologies (ISCT), Ancona, Italy, 19–21 June 2019; pp. 296–298. [Google Scholar] [CrossRef]
- Smart Home/Smart Building Connectivity Options and Their Cybersecurity. 2020. Available online: https://society5.com/smart-cities/smart-building-smart-home-connectivity-cybersecurity/ (accessed on 1 October 2023).
- Wendzel, S.; Tonejc, J.; Kaur, J.; Kobekova, A. Cyber Security of Smart Buildings. In En Security and Privacy in Cyber-Physical Systems: Foundations, Principles, and Applications; John Wiley & Sons Ltd.: Hoboken, NJ, USA, 2018; pp. 327–351. [Google Scholar]
- Mekala, S.H.; Baig, Z.; Anwar, A.; Zeadally, S. Cybersecurity for Industrial IoT (IIoT): Threats, countermeasures, challenges and future directions. Comput. Commun. 2023, 208, 294–320. [Google Scholar] [CrossRef]
- Ignacio Porro Sáez, I.C. IoT: Protocolos de Comunicación, Ataques y Recomendaciones. 2019. Available online: https://www.incibe-cert.es/blog/iot-protocolos-comunicacion-ataques-y-recomendaciones (accessed on 1 October 2023).
- Zohourian, A.; Dadkhah, S.; Neto, E.C.P.; Mahdikhani, H.; Danso, P.K.; Molyneaux, H.; Ghorbani, A.A. IoT Zigbee device security: A comprehensive review. Internet Things 2023, 22, 100791. [Google Scholar] [CrossRef]
- Keşkişoğlu, A.; Turhan, C. Challenges on smart thermostat systems in Intelligent Buildings. In Proceedings of the 4th International Energy and Engineering Congress, Gaziantep, Turkey, 24–25 October 2019. [Google Scholar]
- Moody, M.; Hunter, A. Exploiting known vulnerabilities of a smart thermostat. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 50–53. [Google Scholar] [CrossRef]
- Ling, Z.; Luo, J.; Xu, Y.; Gao, C.; Wu, K.; Fu, X. Security Vulnerabilities of Internet of Things: A Case Study of the Smart Plug System. IEEE Internet Things J. 2017, 4, 1899–1909. [Google Scholar] [CrossRef]
- Suryadevara, N.K.; Biswal, G.R. Smart Plugs: Paradigms and Applications in the Smart City-and-Smart Grid. Energies 2019, 12, 1957. [Google Scholar] [CrossRef]
- Bugeja, J.; Jönsson, D.; Jacobsson, A. An Investigation of Vulnerabilities in Smart Connected Cameras. In Proceedings of the 2018 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Athens, Greece, 19–23 March 2018; pp. 537–542. [Google Scholar] [CrossRef]
- Alharbi, R.; Aspinall, D. An IoT analysis framework: An investigation of IoT smart cameras’ vulnerabilities. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT—2018, London, UK, 28–29 March 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Teixeira, D.; Assunção, L.; Paiva, S. Security of Smart Home-Smartphones Systems. In Proceedings of the 2020 15th Iberian Conference on Information Systems and Technologies (CISTI), Seville, Spain, 24–27 June 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Karimi, K.; Krit, S. Smart home-Smartphone Systems: Threats, Security Requirements and Open research Challenges. In Proceedings of the 2019 International Conference of Computer Science and Renewable Energies (ICCSRE), Agadir, Morocco, 22–24 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Morgner, P.; Mattejat, S.; Benenson, Z. All Your Bulbs Are Belong to Us: Investigating the Current State of Security in Connected Lighting Systems. arXiv 2016, arXiv:1608.03732. [Google Scholar]
- Gui, Y.; Siddiqui, A.S.; Tamore, S.M.; Saqib, F. Investigation of Vulnerabilities on Smart Grid End Devices. In Proceedings of the 2019 IEEE CyberPELS (CyberPELS), Knoxville, TN, USA, 29 April–1 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, H.N.; Salman, O.; Chehab, A. Ethical hacking for IoT: Security issues, challenges, solutions and recommendations. Internet Things Cyber-Phys. Syst. 2023, 3, 280–308. [Google Scholar] [CrossRef]
- Hammi, B.; Zeadally, S.; Khatoun, R.; Nebhen, J. Survey on smart homes: Vulnerabilities, risks, and countermeasures. Comput. Secur. 2022, 117, 102677. [Google Scholar] [CrossRef]
- Matherly, J. The Complete Guide to Shodan: Collect. Analyze Visualize. Make Internet Intelligence Work for You; Leanpub: Victoria, BC, Canada, 2016. [Google Scholar]
- Fagroud, F.Z.; Ajallouda, L.; Ben Lahmar, E.H.; Toumi, H.; Achtaich, K.; Filali, S.E. IOT Search Engines: Exploratory Data Analysis. Procedia Comput. Sci. 2020, 175, 572–577. [Google Scholar] [CrossRef]
- Tundalwar, D.S.; Pandhare, R.A.; Digalwar, M.A. A Taxonomy of IoT Security Attacks and Emerging Solutions. In Proceedings of the 2023 2nd International Conference on Paradigm Shifts in Communications Embedded Systems, Machine Learning and Signal Processing (PCEMS), Nagpur, India, 5–6 April 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Papp, D.; Ma, Z.; Buttyan, L. Embedded systems security: Threats, vulnerabilities, and attack taxonomy. In Proceedings of the 2015 13th Annual Conference on Privacy, Security and Trust (PST), Izmir, Turkey, 21–23 July 2015; pp. 145–152. [Google Scholar] [CrossRef]
- Al-Alami, H.; Hadi, A.; Al-Bahadili, H. Vulnerability scanning of IoT devices in Jordan using Shodan. In Proceedings of the 2017 2nd International Conference on the Applications of Information Technology in Developing Renewable Energy Processes & Systems (IT-DREPS), Amman, Jordan, 6–7 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Ahamed, J.; Rajan, A.V. Internet of Things (IoT): Application systems and security vulnerabilities. In Proceedings of the 2016 5th International Conference on Electronic Devices, Systems and Applications (ICEDSA), Ras Al Khaimah, United Arab Emirates, 6–8 December 2016; pp. 1–5. [Google Scholar] [CrossRef]
- McMahon, E.; Williams, R.; El, M.; Samtani, S.; Patton, M.; Chen, H. Assessing medical device vulnerabilities on the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; pp. 176–178. [Google Scholar] [CrossRef]
- Albataineh, A.; Alsmadi, I. IoT and the Risk of Internet Exposure: Risk Assessment Using Shodan Queries. In Proceedings of the 2019 IEEE 20th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Washington, DC, USA, 10–12 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Markowsky, L.; Markowsky, G. Scanning for vulnerable devices in the Internet of Things. In Proceedings of the 2015 IEEE 8th International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Warsaw, Poland, 24–26 September 2015; Volume 1, pp. 463–467. [Google Scholar] [CrossRef]
- Bodenheim, R.; Butts, J.; Dunlap, S.; Mullins, B. Evaluation of the ability of the Shodan search engine to identify Internet-facing industrial control devices. Int. J. Crit. Infrastruct. Prot. 2014, 7, 114–123. [Google Scholar] [CrossRef]
- Patton, M.; Gross, E.; Chinn, R.; Forbis, S.; Walker, L.; Chen, H. Uninvited Connections: A Study of Vulnerable Devices on the Internet of Things (IoT). In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference, The Hague, The Netherlands, 24–26 September 2014; pp. 232–235. [Google Scholar] [CrossRef]
- Antonio López. Métricas de Evaluación de Vulnerabilidades: CVSS 3.0. 2015. Available online: https://www.incibe.es/incibe-cert/blog/cvss3-0 (accessed on 1 October 2023).
- (INCIBE), H.R.S. Midiendo la Severidad de las Vulnerabilidades: Cambios en CVSS 3.1. 2019. Available online: https://www.incibe-cert.es/blog/midiendo-severidad-las-vulnerabilidades-cambios-cvss-31 (accessed on 1 October 2023).
- FIRST. Common Vulnerability Scoring System v3.1: Specification Document. 2019. Available online: https://www.first.org/cvss/v3.1/specification-document (accessed on 1 October 2023).
- NVD. Common Vulnerability Scoring System Calculator. 2019. Available online: https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator (accessed on 1 October 2023).



| Tool | Type | Features | Limitations |
|---|---|---|---|
| Nessus [29] | Interactive | Free version, Limited use | Unsuitable for large-scale scans |
| Skipfish [30] | Interactive | Open-source, Free | No user interface, Challenging to navigate |
| Vigilant [31] | Interactive | Fault-injection attacks hardware implementation | Limited to simulations |
| Censys [32] | Automatic | User-friendly interface | API limitations |
| ZoomEye [33] | Automatic | Different search criteria | Specific keyword search, results can not be downloaded |
| Thingful [34] | Automatic | Extensive data, Multi-domain information | Limited public data availability |
| Shodan [35] | Automatic | User-friendly web and API | Various license options Academic use opportunities |
| Classification | Characteristics | Specific Attack | Attack Impact |
|---|---|---|---|
| Hardware attacks | Related to vulnerabilities that affect the hardware part of the systems. | Physical attacks | Limited or no physical protection to restrict access to internal parts of the device. |
| System batteries/energy use | Reduce uptime. | ||
| Denial of service (DoS) | Many machines attack a device at the same time and the device may become unresponsive. | ||
| Reverse engineering | Analyzes the architecture and technology of a device to replicate or modify it. | ||
| Software attacks | Linked to software bugs and misbehavior that compromise the security of systems. | Inconsistent software and firmware updates | Devices not patched and updated correctly. |
| Reverse engineering | Find security risks in programs. | ||
| Malicious software injection | Purposes such as accessing restricted information or increasing user privileges. | ||
| Improper device integration | Systems are not integrated correctly. | ||
| Incorrect configurations | Bad configuration due to simple/default passwords, etc. | ||
| Poor cryptographic key management | Information can be easily intercepted. | ||
| Connectivity attacks | Problems related to attacks focused on intercepting data exchanged between different elements of a network, or impersonating an authorised third party. | Denial of service/distributed denial of service (DoS/DDoS) | Requests are generated to a service, consuming its resources and reducing its response capacity. |
| Man-in-the-middle (MiTM) | Impersonation and eavesdropping on the network. | ||
| Insecure interfaces | Configurations lacking security (web interfaces, APIs, cloud services). | ||
| Jamming | Alter or cancel a communication, so that the receiver cannot interpret the message correctly. |
| Technology | Protocol | Key Aspects | |
|---|---|---|---|
| Wired technology | KNX | Benefits | Open standard that can be used as a backbone to connect several networks together [44]. |
| Drawbacks | Simple access control mechanisms that transmit passwords in plain text over the network. Security layer is based on TCP or UDP. | ||
| LONTalk | Benefits | Used in the distributed automation system called LONWorks, lighting, and HVAC systems. | |
| Drawbacks | No data encryption, but sender authentication is available. It suffers from DoS attacks, and the lack of encryption technology allows eavesdropping on network traffic [40,44]. | ||
| BACnet | Benefits | Standard protocol that aims to support the interoperability between vendors. | |
| Drawbacks | Message security is applied at the network level, and authentication is used. It can suffer spoofing attacks, DoS, write ownership, or disabling of network connections [19,40]. | ||
| Modbus | Benefits | Serial communications protocol mainly used in industrial control applications. | |
| Drawbacks | Modbus/RTU offer neither encryption nor authentication. Modbus/TCP sends messages as unencrypted text over the network and can be easily intercepted, but TLS cryptography prevents MiTM attacks [19,45]. | ||
| HTTP | Benefits | Connectionless client/server protocol that is transaction-oriented, useful for sending large amounts of information. | |
| Drawbacks | The use of SSL/TLS over HTTP is recommended to ensure the correct transmission of information over an encrypted channel and avoid servers in IoT devices [19]. | ||
| MQTT | Benefits | Message transport protocol based on publications and subscriptions, widely used in communications linked to IoT devices. | |
| Drawbacks | Should be used in conjunction with TLS to secure communication over TCP (no authentication or encryption) [45]. | ||
| Wireless technology | Bluetooth | Benefits | Short-range technology widely used in smart homes and buildings. |
| Drawbacks | Authentication, authorization, confidentiality, data integrity, and pairing. It can suffer from reverse and social engineering attacks, passive eavesdropping, MiTM, Bluebugging, and FalseTiming attacks. | ||
| EnOcean | Benefits | Proprietary protocol mainly used in home and building automation. | |
| Drawbacks | Communications can be protected by authentication code. | ||
| WiFi | Benefits | Used in intelligent buildings for high-performance audio or video, centralized management applications, and connection between multiple devices. | |
| Drawbacks | Compatible encryption mechanisms susceptible to radio interference, risk of DoS network, eavesdropping and packet sniffing in traffic, Evil Twins or Hotspots [46]. | ||
| Zigbee | Benefits | Communication protocol for wireless personal area networks. | |
| Drawbacks | Data packet encryption, susceptible to injection, wormhole, DDoS, and eavesdropping attacks [47]. |
| Group | Metric | Possible Values | Meaning |
|---|---|---|---|
| Exploitability | Attack Vector (AV) | [N, A, L, P] | It reflects the context in which the vulnerability can be exploited. |
| (Network, Adjacent, Local, Physical) | |||
| Attack Complexity (AC) | [L, H] | Describes the conditions that must be present for the vulnerability to be exploited. | |
| (Low, High) | |||
| Privileges Required (PR) | (N, L, H) | Checks whether privileges are required to perform the attack. | |
| (None, Low, High) | |||
| User Interaction (UI) | (N, R) | Describes whether a user interaction is necessary for the attack to succeed. | |
| (None, Required) | |||
| Impact | Confidentiality (C) | (N, L, H) | Assesses the extent to which a component’s vulnerability compromised info confidentiality. |
| (None, Low, High) | |||
| Integrity (I) | (N, L, H) | Assesses the effect on the integrity of a vulnerability that has been successfully exploited. | |
| (None, Low, High) | |||
| Availability (A) | (N, L, H) | Assesses the effect on the accessibility of the element by a vulnerability successfully exploited. | |
| (None, Low, High) | |||
| Scope | Scope (S) | Captures whether a vulnerability in one vulnerable component impacts resources in components beyond its security scope. |
| Category | Keyword (Shodan) | Results | Keyword (CVE DB) | Vulnerabilities |
|---|---|---|---|---|
| Smart thermostat | Thermostat | 109 | Smart thermostat | 1156 |
| Heatmiser Wifi Thermostat | 350 | Heatmiser/EcoBee/Radio Termostat | 3 | |
| Smart plug | Smart plug | 98 | Smart plug | 3 |
| WeMo Switch | 10 | Meross device/ WeMo device | 12 | |
| Smart Camera | Smart Camera/ Connected Camera | 1843/83 | Connected Camera/Network Camera/Smart Camera/IP Camera | 168 |
| DCS-2121 | 1237 | D-Link DCS | 43 | |
| Smartphone | Smart home phone | 31 | Smart home phone | 121 |
| HomeMatic | 751 | OpenHAB/Homematic | 34 | |
| Smart Lighting | Smart light | 146 | Smart bulb | 8 |
| Philips Hue | 169 | Philips Hue/Osram Lightify | 11 |
| Category | Type | Vulnerabilities | |||||
|---|---|---|---|---|---|---|---|
| Shodan | Device | Protocol | Other | ||||
| Thermostat | Global | 205 | 0 | 62 | HTTP, FTP | 63 | Apache HTTPD, ProFTPD, OpenSSH, mySQL, PostgreSQL |
| Heatmiser Wifi (sp.) | 16 | 0 | 2 | HTTP | 2 | Apache HTTPD | |
| Heatmiser Wifi (gl.) | 16 | 0 | 2 | HTTP | 2 | Apache HTTPD | |
| Plug | Global | 152 | 0 | 38 | SSH, HTTP, FTP, SNMP | 37 | OpenSSH, Apache HTTPD, PostgreSQL, mySQL |
| WeMo Switch (sp.) | 0 | 0 | 0 | - | 0 | - | |
| WeMo Switch (gl.) | 0 | 0 | 0 | - | 0 | - | |
| Camera | Global | 125 | 0 | 61 | HTTP, FTP, SSH | 83 | Apache HTTPD, OpenSSH, Linux, ProFTPD |
| DCS-2121 (sp.) | 40 | 0 | 32 | RDP, HTTP, FTP | 30 | Apache HTTPD, ProFTPD | |
| DCS-2121 (gl.) | 40 | 0 | 32 | RDP, HTTP, FTP | 30 | Apache HTTPD, ProFTPD | |
| Home System | Global | 344 | 0 | 84 | HTTP, SSH, SNMP, FTP | 80 | OpenSSH, Apache HTTPD, ProFTPD, PostgreSQL, mySQL |
| HomeMatic (sp.) | 206 | 0 | 78 | HTTP, FTP, SSH | 77 | Apache HTTPD, OpsenSSH, mySQL, NGINX, PostgreSQL | |
| HomeMatic (gl.) | 206 | 0 | 78 | HTTP, FTP, SSH | 77 | Apache HTTPD, OpsenSSH, mySQL, NGINX, PostgreSQL | |
| Lighting | Global | 205 | 0 | 32 | HTTP | 52 | Apache HTTPD, OpenSSH, Linux, PostgreSQL |
| Philips Hue (sp.) | 28 | 0 | 25 | HTTP | 27 | Apache HTTPD, OpenSSH | |
| Philips Hue (gl.) | 28 | 0 | 25 | HTTP | 27 | Apache HTTPD, OpenSSH | |
| Category | Type | Code | Overall CVSS | Occurrences | Exploits | Description |
|---|---|---|---|---|---|---|
| Thermostat | FTP, ProFTPD | CVE-2019-12815 | 9.8 | 1 | 1 | Allows remote code execution and information disclosure without authentication. |
| HTTP, Apache HTTPD | CVE-2018-1312 | 9.8 | 10 | 1 | In common Digest authentication configuration, an attacker could replay HTTP requests. | |
| CVE-2017-7679 | 9.8 | 1 | 2 | Read one byte beyond the end of a buffer when sending malicious content. | ||
| Plug | SSH, OpenSSH | CVE-2017-15906 | 5.3 | 4 | 1 | An OpenSSH function allows attackers to create zero-length files. |
| PostgreSQL | CVE-2017-15098 | 8.1 | 1 | 1 | Some calls may crash the server or reveal some bytes of server memory. | |
| Camera | HTTP, Apache HTTPD | CVE-2019-0220 | 5.3 | 10 | 1 | A vulnerability was found in Apache HTTP Server related to consecutive slashes. |
| CVE-2018-17199 | 7.5 | 2 | 1 | The session expiry time is checked before decoding the session, and is ignored in some sessions. | ||
| Smartphone | SSH, OpenSSH | CVE-2018-15919 | 5.3 | 10 | 1 | A behaviour observed in OpenSSH could even be used by remote attackers to detect the existence of users on a target system when GSS2 is in use. |
| CVE-2019-0211 | 7.8 | 7 | 2 | Executed code in secondary process/subprocessed having limited privileges could execute random code with root privileges. | ||
| Lighting | Linux | CVE-2019-9193 | 7.2 | 1 | 2 | A functionality is enabled by default and can be abused to execute arbitrary operating system commands on Windows, Linux, and macOS. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mulero-Palencia, S.; Monzon Baeza, V. Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool. Electronics 2023, 12, 4815. https://doi.org/10.3390/electronics12234815
Mulero-Palencia S, Monzon Baeza V. Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool. Electronics. 2023; 12(23):4815. https://doi.org/10.3390/electronics12234815
Chicago/Turabian StyleMulero-Palencia, Sofía, and Victor Monzon Baeza. 2023. "Detection of Vulnerabilities in Smart Buildings Using the Shodan Tool" Electronics 12, no. 23: 4815. https://doi.org/10.3390/electronics12234815






