AIBPSF-IoMT: Artificial Intelligence and Blockchain-Based Predictive Security Framework for IoMT Technologies
Abstract
:1. Introduction
2. Internet of Things (IoT) in Brief
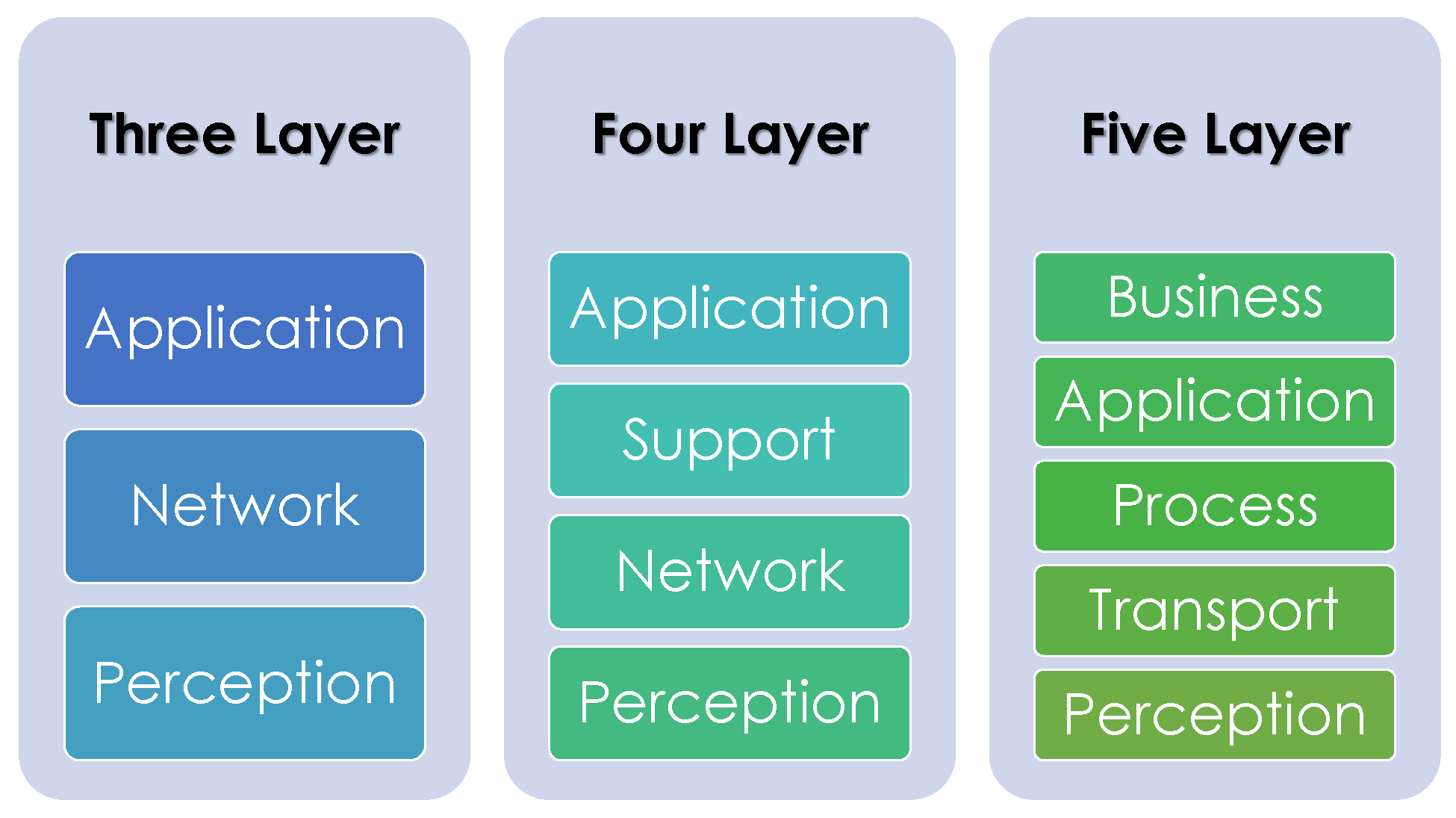
2.1. IoT Architecture
2.2. IoT Security Principles
2.3. Impact of Artificial Intelligence on IoT Security
3. Blockchain Background and Security-Related Research
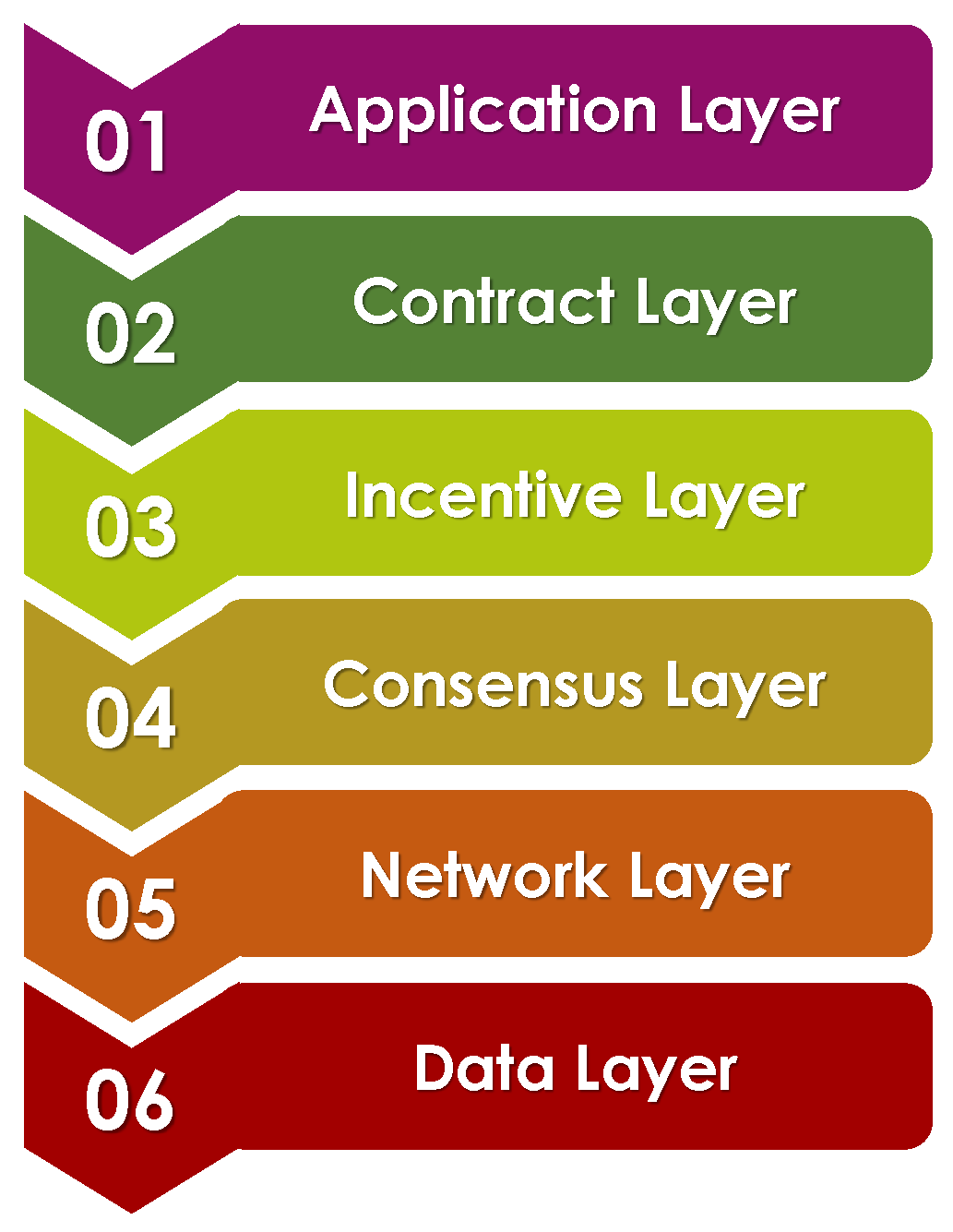
3.1. Blockchain Structure
3.2. Security of Blockchains
3.3. Blockchain and IoT Integration from a Security Perspective
4. Discussion of the Proposed Framework: AIBPSF-IoMT
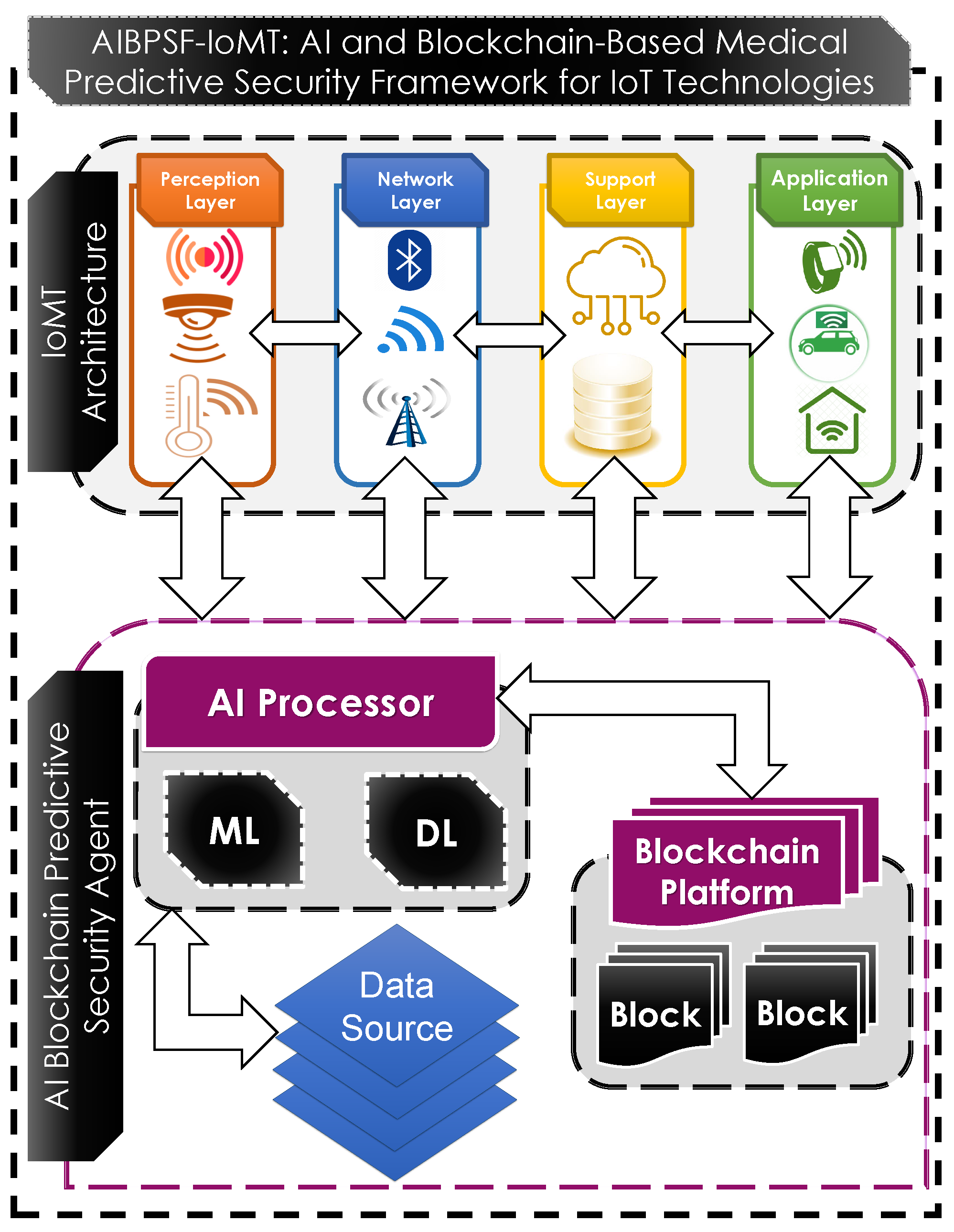
4.1. AI Blockchain-Based Secure IoT Architecture Framework
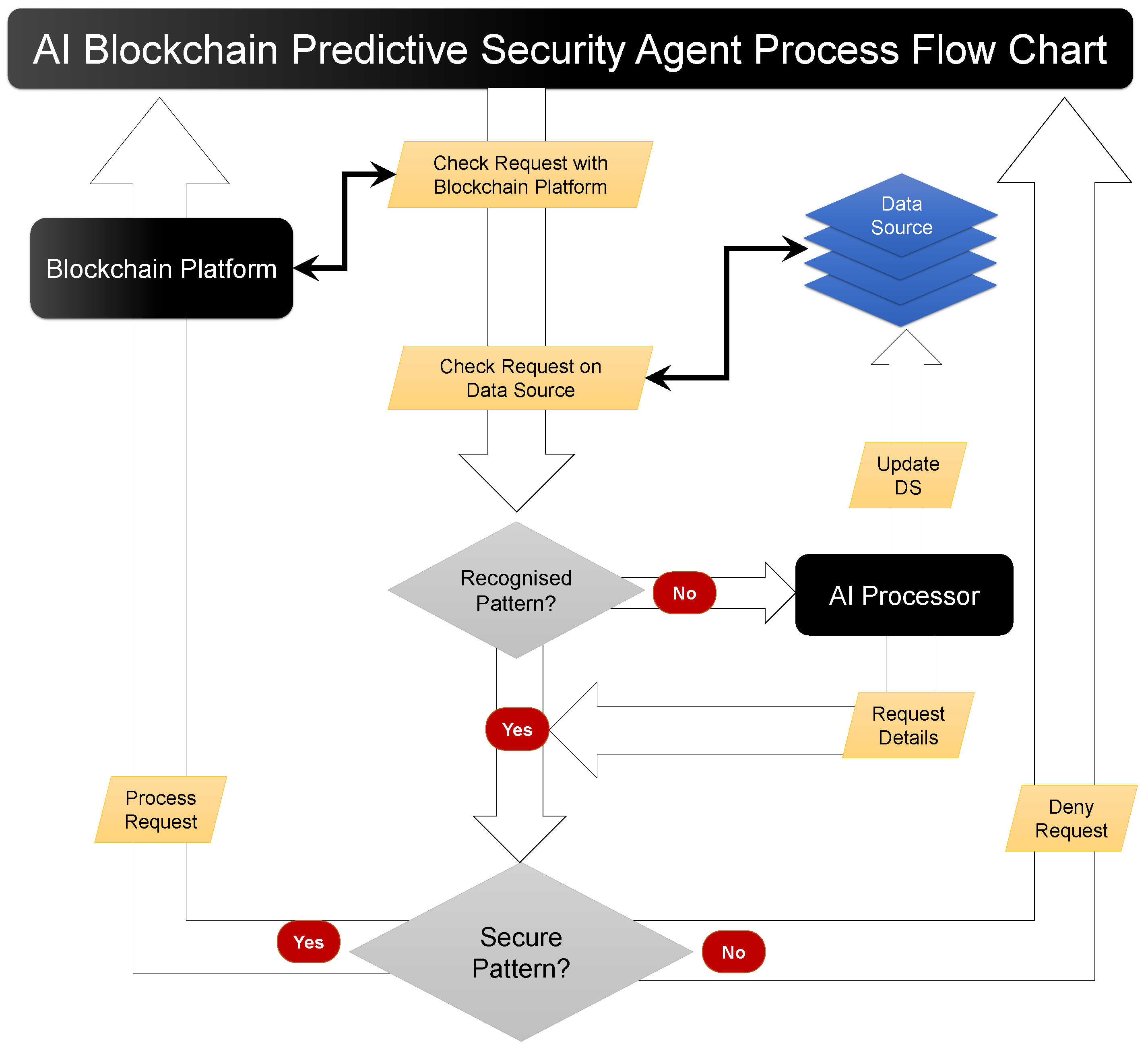
4.2. AI Blockchain Predictive Security Agent
4.2.1. Blockchain Platform
4.2.2. Data Source (DS)
4.2.3. Artificial Intelligence (AI) Processor
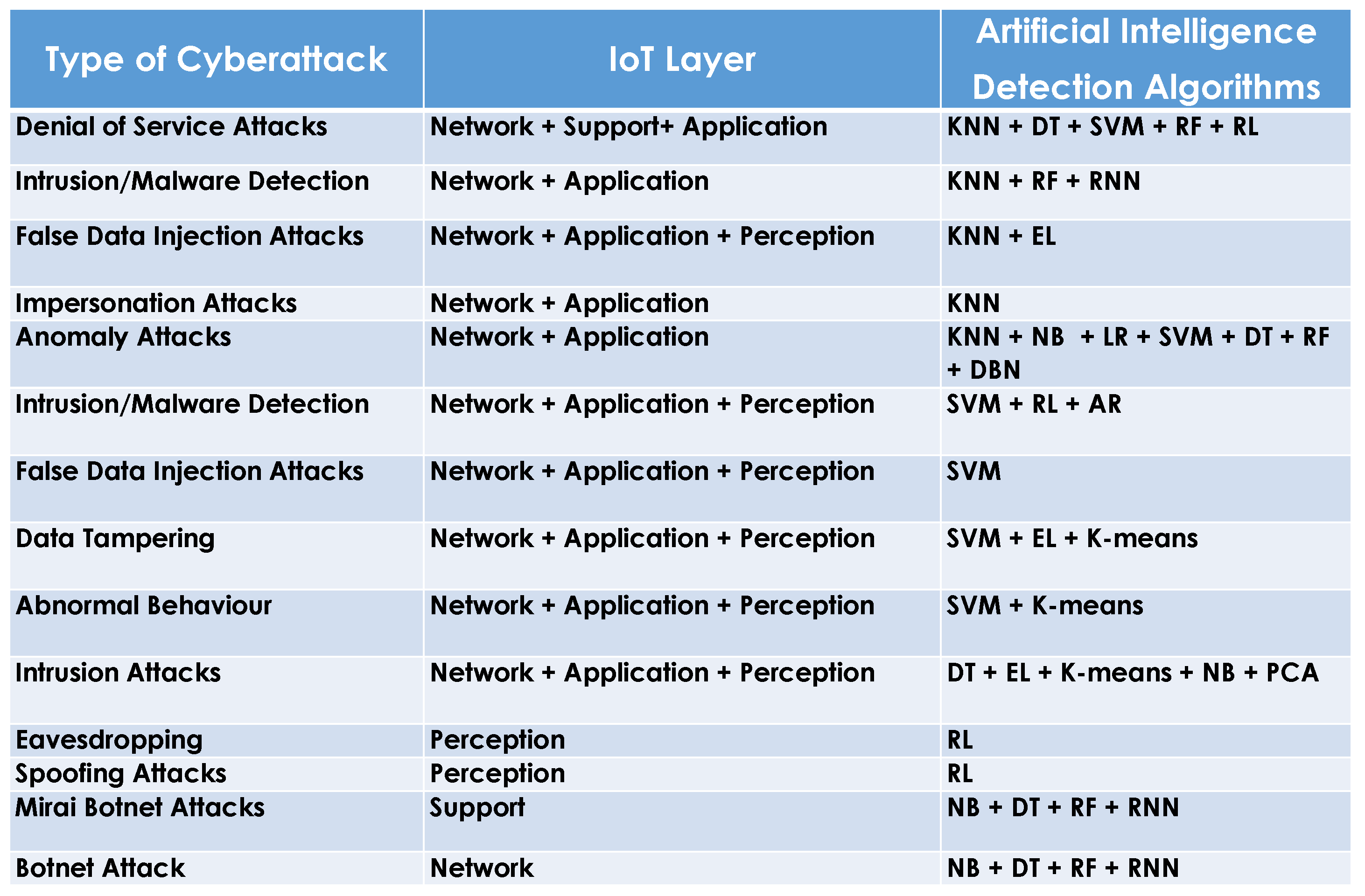
4.3. Cyberattacks on IoT and Their AI Detection Algorithms
5. IoT Medical Case Study
5.1. Dataset Used in Context
5.2. Pre-Processing Features
5.3. Selection Features
5.4. ML and DL Algorithm Selection
5.4.1. Machine Learning Algorithms
5.4.2. Deep Learning Algorithms
6. Case Study Results Analysis
6.1. Dataset Preparation
6.2. Performance Evaluation Measurements
6.2.1. Precision
6.2.2. Accuracy
6.2.3. Recall
6.2.4. F1 Score
6.3. Discussion of Results
7. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Singh, S.K.; Rathore, S.; Park, J.H. BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Kandaswamy, R.; Furlonger, D. Blockchain-Based Transformation. 2021. Available online: https://www.gartner.com/en/doc/3869696-blockchain-based-transformation-a-gartner-trend-insight-report (accessed on 20 May 2022).
- Gartner Research. Forecast: IT Services for IoT, Worldwide, 2019–2025. Technical Report. 2021. Available online: https://www.gartner.com/en/documents/4004741 (accessed on 20 May 2022).
- Statista Research Department. Internet of Things (IoT) Connected Devices Installed Base Worldwide from 2015 to 2025. Resreport, Statista. 2016. Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 20 May 2022).
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Karie, N.M.; Sahri, N.M.; Haskell-Dowland, P. IoT Threat Detection Advances, Challenges and Future Directions. In Proceedings of the 2020 Workshop on Emerging Technologies for Security in IoT (ETSecIoT), Sydney, NSW, Australia, 21 April 2020; pp. 22–29. [Google Scholar] [CrossRef]
- Alfandi, O.; Khanji, S.; Ahmad, L.; Khattak, A. A survey on boosting IoT security and privacy through blockchain. Clust. Comput. 2021, 24, 37–55. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Internet Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Javaid, U.; Aman, M.N.; Sikdar, B. Blockpro: Blockchain based data provenance and integrity for secure iot environments. In Proceedings of the 1st Workshop on Blockchain-enabled Networked Sensor Systems, Shenzhen, China, 4 November 2018; pp. 13–18. [Google Scholar] [CrossRef]
- Yu, Y.; Li, Y.; Tian, J.; Liu, J. Blockchain-Based Solutions to Security and Privacy Issues in the Internet of Things. IEEE Wirel. Commun. 2018, 25, 12–18. [Google Scholar] [CrossRef]
- Javaid, U.; Aman, M.N.; Sikdar, B. DrivMan: Driving Trust Management and Data Sharing in VANETs with Blockchain and Smart Contracts. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 26 November 2023).
- Aste, T.; Tasca, P.; Di Matteo, T. Blockchain technologies: The foreseeable impact on society and industry. Computer 2017, 50, 18–28. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Peters, G.; Panayi, E.; Chapelle, A. Trends in Cryptocurrencies and Blockchain Technologies: A Monetary Theory and Regulation Perspective. J. Financ. Perspect. 2015, 3, 3. [Google Scholar]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–3. [Google Scholar] [CrossRef]
- Agbo, C.C.; Mahmoud, Q.H.; Eklund, J.M. Blockchain Technology in Healthcare: A Systematic Review. Healthcare 2019, 7, 56. [Google Scholar] [CrossRef]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Samaniego, M.; Jamsrandorj, U.; Deters, R. Blockchain as a Service for IoT. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016; pp. 433–436. [Google Scholar] [CrossRef]
- Lao, L.; Li, Z.; Hou, S.; Xiao, B.; Guo, S.; Yang, Y. A survey of IoT applications in blockchain systems: Architecture, consensus, and traffic modeling. ACM Comput. Surv. (CSUR) 2020, 53, 1–32. [Google Scholar] [CrossRef]
- Bahga, A.; Madisetti, V.K. Blockchain Platform for Industrial Internet of Things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Republic of Korea, 19–22 February 2017; pp. 464–467. [Google Scholar] [CrossRef]
- Sharma, P.K.; Singh, S.; Jeong, Y.S.; Park, J.H. DistBlockNet: A Distributed Blockchains-Based Secure SDN Architecture for IoT Networks. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Sundmaeker, H.; Guillemin, P.; Friess, P.; Woelfflé, S. Vision and challenges for realising the Internet of Things. Clust. Eur. Res. Proj. Internet Things Eur. Commision 2010, 3, 34–36. [Google Scholar]
- Riahi Sfar, A.; Natalizio, E.; Challal, Y.; Chtourou, Z. A roadmap for security challenges in the Internet of Things. Digit. Commun. Netw. 2018, 4, 118–137. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Salah, K.; Rehman, M.H.U.; Nizamuddin, N.; Al-Fuqaha, A. Blockchain for AI: Review and Open Research Challenges. IEEE Access 2019, 7, 10127–10149. [Google Scholar] [CrossRef]
- Lewis, F.L. Wireless sensor networks. Smart Environ. Technol. Protoc. Appl. 2004, 11, 46. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Jesus, E.F.; Chicarino, V.R.; De Albuquerque, C.V.; Rocha, A.A.d.A. A survey of how to use blockchain to secure internet of things and the stalker attack. Secur. Commun. Netw. 2018, 2018, 9675050. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.S. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef]
- Darwish, D. Improved layered architecture for Internet of Things. Int. J. Comput. Acad. Res. (IJCAR) 2015, 4, 214–223. [Google Scholar]
- Recommendation Y.4000/Y.2060 (06/12); Y.2060 Overview of Internet of Things; ITU-T: Geneva, Switzerland, 2012; p. 570.
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017, 9324035. [Google Scholar] [CrossRef]
- Krčo, S.; Pokrić, B.; Carrez, F. Designing IoT architecture(s): A European perspective. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Republic of Korea, 6–8 March 2014; pp. 79–84. [Google Scholar] [CrossRef]
- Yelamarthi, K.; Aman, M.S.; Abdelgawad, A. An application-driven modular IoT architecture. Wirel. Commun. Mob. Comput. 2017, 2017, 1350929. [Google Scholar] [CrossRef]
- Al-Qaseemi, S.A.; Almulhim, H.A.; Almulhim, M.F.; Chaudhry, S.R. IoT architecture challenges and issues: Lack of standardization. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 731–738. [Google Scholar] [CrossRef]
- Grammatikis, P.I.R.; Sarigiannidis, P.G.; Moscholios, I.D. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Oualha, N.; Nguyen, K.T. Lightweight Attribute-Based Encryption for the Internet of Things. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Guo, F.; Mu, Y.; Susilo, W.; Wong, D.S.; Varadharajan, V. CP-ABE With Constant-Size Keys for Lightweight Devices. IEEE Trans. Inf. Forensics Secur. 2014, 9, 763–771. [Google Scholar] [CrossRef]
- Touati, L.; Challal, Y.; Bouabdallah, A. C-CP-ABE: Cooperative Ciphertext Policy Attribute-Based Encryption for the Internet of Things. In Proceedings of the 2014 International Conference on Advanced Networking Distributed Systems and Applications, Bejaia, Algeria, 17–19 June 2014; pp. 64–69. [Google Scholar] [CrossRef]
- Huang, X.; Fu, R.; Chen, B.; Zhang, T.; Roscoe, A.W. User interactive Internet of things privacy preserved access control. In Proceedings of the 2012 International Conference for Internet Technology and Secured Transactions, London, UK, 10–12 December 2012; pp. 597–602. [Google Scholar]
- Evans, D.; Eyers, D.M. Efficient Data Tagging for Managing Privacy in the Internet of Things. In Proceedings of the 2012 IEEE International Conference on Green Computing and Communications, Besancon, France, 20–23 November 2012; pp. 244–248. [Google Scholar] [CrossRef]
- Appavoo, P.; Chan, M.C.; Bhojan, A.; Chang, E.C. Efficient and privacy-preserving access to sensor data for Internet of Things (IoT) based services. In Proceedings of the 2016 8th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 5–10 January 2016; pp. 1–8. [Google Scholar]
- Alcaide, A.; Palomar, E.; Montero-Castillo, J.; Ribagorda, A. Anonymous authentication for privacy-preserving IoT target-driven applications. Comput. Secur. 2013, 37, 111–123. [Google Scholar] [CrossRef]
- Gheisari, M.; Najafabadi, H.E.; Alzubi, J.A.; Gao, J.; Wang, G.; Abbasi, A.A.; Castiglione, A. OBPP: An ontology-based framework for privacy-preserving in IoT-based smart city. Future Gener. Comput. Syst. 2021, 123, 1–13. [Google Scholar] [CrossRef]
- Maleh, Y.; Ezzati, A.; Belaissaoui, M. Dos attacks analysis and improvement in dtls protocol for internet of things. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, Blagoevgrad, Bulgaria, 10–11 November 2016; pp. 1–7. [Google Scholar]
- Kumar, P.M.; Gandhi, U.D. Enhanced DTLS with CoAP-based authentication scheme for the internet of things in healthcare application. J. Supercomput. 2020, 76, 3963–3983. [Google Scholar] [CrossRef]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar] [CrossRef]
- Cusack, B.; Tian, Z.; Kyaw, A.K. Identifying DOS and DDOS attack origin: IP traceback methods comparison and evaluation for IoT. In Interoperability, Safety and Security in IoT; Springer: Cham, Switzerland, 2016; pp. 127–138. [Google Scholar]
- Kothmayr, T.; Schmitt, C.; Hu, W.; Brünig, M.; Carle, G. DTLS based security and two-way authentication for the Internet of Things. Ad Hoc Netw. 2013, 11, 2710–2723. [Google Scholar] [CrossRef]
- Hong, N. A security framework for the internet of things based on public key infrastructure. Adv. Mater. Res. 2013, 671–674, 3223–3226. [Google Scholar] [CrossRef]
- Pranata, H.; Athauda, R.; Skinner, G. Securing and governing access in ad-hoc networks of internet of things. In Proceedings of the IASTED International Conference on Engineering and Applied Science, EAS, Colombo, Sri Lanka, 27–29 December 2012; pp. 84–90. [Google Scholar]
- Wu, Z.Q.; Zhou, Y.W.; Ma, J.F. A security transmission model for internet of things. Jisuanji Xuebao (Chin. J. Comput.) 2011, 34, 1351–1364. [Google Scholar] [CrossRef]
- Pham, C.D.; Dang, T.K. A lightweight authentication protocol for D2D-enabled IoT systems with privacy. Pervasive Mob. Comput. 2021, 74, 101399. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Engels, D.W. A secure IoT architecture for Smart Cities. In Proceedings of the 2016 13th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 812–813. [Google Scholar] [CrossRef]
- Branitskiy, A.; Kotenko, I.; Saenko, I. Applying machine learning and parallel data processing for attack detection in IoT. IEEE Trans. Emerg. Top. Comput. 2021, 9, 1642–1653. [Google Scholar] [CrossRef]
- Sharma, D.K.; Dhankhar, T.; Agrawal, G.; Singh, S.K.; Gupta, D.; Nebhen, J.; Razzak, I. Anomaly detection framework to prevent DDoS attack in fog empowered IoT networks. Ad Hoc Netw. 2021, 121, 102603. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A Survey of IoT Security Based on a Layered Architecture of Sensing and Data Analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef] [PubMed]
- Mishra, N.; Pandya, S. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- K, S.K.; Sahoo, S.; Mahapatra, A.; Swain, A.K.; Mahapatra, K. Security Enhancements to System on Chip Devices for IoT Perception Layer. In Proceedings of the 2017 IEEE International Symposium on Nanoelectronic and Information Systems (iNIS), Bhopal, India, 18–20 December 2017; pp. 151–156. [Google Scholar] [CrossRef]
- Liao, C.H.; Shuai, H.H.; Wang, L.C. Eavesdropping prevention for heterogeneous Internet of Things systems. In Proceedings of the 2018 15th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–2. [Google Scholar] [CrossRef]
- Anti-Phishing Working Group, Inc. Phishing Activity Trends Report. 2005. Available online: http://www.antiphishing.org/APWG_Phishing-Activity_Report_Jul_05.pdf (accessed on 22 May 2023).
- Li, C.; Chen, C. A multi-stage control method application in the fight against phishing attacks. In Proceeding of the 26th Computer Security Academic Communication across the Country; 2011; p. 145. [Google Scholar]
- Biggio, B.; Roli, F. Wild patterns: Ten years after the rise of adversarial machine learning. Pattern Recognit. 2018, 84, 317–331. [Google Scholar] [CrossRef]
- Kong, Z.; Xue, J.; Wang, Y.; Huang, L.; Niu, Z.; Li, F. A survey on adversarial attack in the age of artificial intelligence. Wirel. Commun. Mob. Comput. 2021, 2021, 4907754. [Google Scholar] [CrossRef]
- Ucci, D.; Aniello, L.; Baldoni, R. Survey of machine learning techniques for malware analysis. Comput. Secur. 2019, 81, 123–147. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.H. Botnet Attack Detection by Using CNN-LSTM Model for Internet of Things Applications. Secur. Commun. Netw. 2021, 2021, 3806459. [Google Scholar] [CrossRef]
- Mudassir, M.; Unal, D.; Hammoudeh, M.; Azzedin, F. Detection of Botnet Attacks against Industrial IoT Systems by Multilayer Deep Learning Approaches. Wirel. Commun. Mob. Comput. 2022, 2022, 2845446. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Al-Dala’ien, M. ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks. J. Sens. Actuator Netw. 2022, 11, 18. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q. Top-Down Machine Learning-Based Architecture for Cyberattacks Identification and Classification in IoT Communication Networks. Front. Big Data 2022, 4, 782902. [Google Scholar] [CrossRef] [PubMed]
- Özçelik, M.; Chalabianloo, N.; Gür, G. Software-Defined Edge Defense Against IoT-Based DDoS. In Proceedings of the 2017 IEEE International Conference on Computer and Information Technology (CIT), Helsinki, Finland, 21–23 August 2017; pp. 308–313. [Google Scholar] [CrossRef]
- Roldán, J.; Boubeta-Puig, J.; Luis Martínez, J.; Ortiz, G. Integrating complex event processing and machine learning: An intelligent architecture for detecting IoT security attacks. Expert Syst. Appl. 2020, 149, 113251. [Google Scholar] [CrossRef]
- Istiaque Ahmed, K.; Tahir, M.; Hadi Habaebi, M.; Lun Lau, S.; Ahad, A. Machine Learning for Authentication and Authorization in IoT: Taxonomy, Challenges and Future Research Direction. Sensors 2021, 21, 5122. [Google Scholar] [CrossRef]
- Bagaa, M.; Taleb, T.; Bernabe, J.B.; Skarmeta, A. A Machine Learning Security Framework for Iot Systems. IEEE Access 2020, 8, 114066–114077. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A Malicious Bot-IoT Traffic Detection Method in IoT Network Using Machine-Learning Techniques. IEEE Internet Things J. 2021, 8, 3242–3254. [Google Scholar] [CrossRef]
- Sarker, I.H.; Abushark, Y.B.; Alsolami, F.; Khan, A.I. IntruDTree: A Machine Learning Based Cyber Security Intrusion Detection Model. Symmetry 2020, 12, 754. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A Honeypot with Machine Learning based Detection Framework for defending IoT based Botnet DDoS Attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024. [Google Scholar] [CrossRef]
- Kumar, A.; Lim, T.J. EDIMA: Early Detection of IoT Malware Network Activity Using Machine Learning Techniques. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 289–294. [Google Scholar] [CrossRef]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H.P. Machine Learning in Wireless Sensor Networks: Algorithms, Strategies, and Applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef]
- Branch, J.; Szymanski, B.; Giannella, C.; Wolff, R.; Kargupta, H. In-Network Outlier Detection in Wireless Sensor Networks. In Proceedings of the 26th IEEE International Conference on Distributed Computing Systems (ICDCS’06), Lisboa, Portugal, 4–7 July 2006; p. 51. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Yarman Vural, F.T.; Kulkarni, S.R.; Poor, H.V. Machine Learning Methods for Attack Detection in the Smart Grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef] [PubMed]
- Tan, Z.; Jamdagni, A.; He, X.; Nanda, P.; Liu, R.P. A System for Denial-of-Service Attack Detection Based on Multivariate Correlation Analysis. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 447–456. [Google Scholar] [CrossRef]
- Mohammed, T.; Albeshri, A.; Katib, I.; Mehmood, R. UbiPriSEQ—Deep Reinforcement Learning to Manage Privacy, Security, Energy, and QoS in 5G IoT HetNets. Appl. Sci. 2020, 10, 7120. [Google Scholar] [CrossRef]
- Miao, Q.; Lin, H.; Wang, X.; Hassan, M.M. Federated deep reinforcement learning based secure data sharing for Internet of Things. Comput. Netw. 2021, 197, 108327. [Google Scholar] [CrossRef]
- Shi, W.C.; Sun, H.M. DeepBot: A time-based botnet detection with deep learning. Soft Comput. 2020, 24, 16605–16616. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Xu, R.; Cheng, Y.; Liu, Z.; Xie, Y.; Yang, Y. Improved Long Short-Term Memory based anomaly detection with concept drift adaptive method for supporting IoT services. Future Gener. Comput. Syst. 2020, 112, 228–242. [Google Scholar] [CrossRef]
- Yin, C.; Zhang, S.; Wang, J.; Xiong, N.N. Anomaly Detection Based on Convolutional Recurrent Autoencoder for IoT Time Series. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 112–122. [Google Scholar] [CrossRef]
- Alsoufi, M.A.; Razak, S.; Siraj, M.M.; Nafea, I.; Ghaleb, F.A.; Saeed, F.; Nasser, M. Anomaly-Based Intrusion Detection Systems in IoT Using Deep Learning: A Systematic Literature Review. Appl. Sci. 2021, 11, 8383. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Munir, M.; Siddiqui, S.A.; Dengel, A.; Ahmed, S. DeepAnT: A Deep Learning Approach for Unsupervised Anomaly Detection in Time Series. IEEE Access 2019, 7, 1991–2005. [Google Scholar] [CrossRef]
- Thamilarasu, G.; Chawla, S. Towards Deep-Learning-Driven Intrusion Detection for the Internet of Things. Sensors 2019, 19, 1977. [Google Scholar] [CrossRef]
- Mo, R.; Pei, Y.; Venkatarayalu, N.; Nathaniel, P.; Premkumar, A.B.; Sun, S. An Unsupervised TCN-based Outlier Detection for Time Series with Seasonality and Trend. In Proceedings of the 2021 IEEE VTS 17th Asia Pacific Wireless Communications Symposium (APWCS), Osaka, Japan, 30–31 August 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Hwang, R.H.; Peng, M.C.; Huang, C.W.; Lin, P.C.; Nguyen, V.L. An Unsupervised Deep Learning Model for Early Network Traffic Anomaly Detection. IEEE Access 2020, 8, 30387–30399. [Google Scholar] [CrossRef]
- Bansal, A.; Garg, C.; Padappayil, R.P. Optimizing the implementation of COVID-19 “immunity certificates” using blockchain. J. Med. Syst. 2020, 44, 140. [Google Scholar] [CrossRef]
- Khurshid, A. Applying Blockchain Technology to Address the Crisis of Trust During the COVID-19 Pandemic. JMIR Med. Inform. 2020, 8, e20477. [Google Scholar] [CrossRef]
- He, W.; Zhang, Z.J.; Li, W. Information technology solutions, challenges, and suggestions for tackling the COVID-19 pandemic. Int. J. Inf. Manag. 2021, 57, 102287. [Google Scholar] [CrossRef]
- Tanwar, S.; Bhatia, Q.; Patel, P.; Kumari, A.; Singh, P.K.; Hong, W.C. Machine Learning Adoption in Blockchain-Based Smart Applications: The Challenges, and a Way Forward. IEEE Access 2020, 8, 474–488. [Google Scholar] [CrossRef]
- Chong, A.Y.L.; Lim, E.T.; Hua, X.; Zheng, S.; Tan, C.W. Business on chain: A comparative case study of five blockchain-inspired business models. J. Assoc. Inf. Syst. 2019, 20, 9. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetrò, A.; De Martin, J.C. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy on Blockchain. ACM Comput. Surv. 2019, 52, 1–34. [Google Scholar] [CrossRef]
- Lin, I.C.; Liao, T.C. A survey of blockchain security issues and challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Deepa, N.; Pham, Q.V.; Nguyen, D.C.; Bhattacharya, S.; Prabadevi, B.; Gadekallu, T.R.; Maddikunta, P.K.R.; Fang, F.; Pathirana, P.N. A survey on blockchain for big data: Approaches, opportunities, and future directions. Future Gener. Comput. Syst. 2022, 131, 209–226. [Google Scholar] [CrossRef]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Meng, W.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When Intrusion Detection Meets Blockchain Technology: A Review. IEEE Access 2018, 6, 10179–10188. [Google Scholar] [CrossRef]
- Conti, M.; Sandeep Kumar, E.; Lal, C.; Ruj, S. A Survey on Security and Privacy Issues of Bitcoin. IEEE Commun. Surv. Tutor. 2018, 20, 3416–3452. [Google Scholar] [CrossRef]
- Signorini, M.; Pontecorvi, M.; Kanoun, W.; Di Pietro, R. BAD: A Blockchain Anomaly Detection Solution. IEEE Access 2020, 8, 173481–173490. [Google Scholar] [CrossRef]
- Jin, R.; Wei, B.; Luo, Y.; Ren, T.; Wu, R. Blockchain-Based Data Collection With Efficient Anomaly Detection for Estimating Battery State-of-Health. IEEE Sensors J. 2021, 21, 13455–13465. [Google Scholar] [CrossRef]
- Morishima, S. Scalable anomaly detection in blockchain using graphics processing unit. Comput. Electr. Eng. 2021, 92, 107087. [Google Scholar] [CrossRef]
- Medhane, D.V.; Sangaiah, A.K.; Hossain, M.S.; Muhammad, G.; Wang, J. Blockchain-Enabled Distributed Security Framework for Next-Generation IoT: An Edge Cloud and Software-Defined Network-Integrated Approach. IEEE Internet Things J. 2020, 7, 6143–6149. [Google Scholar] [CrossRef]
- Rathore, S.; Wook Kwon, B.; Park, J.H. BlockSecIoTNet: Blockchain-based decentralized security architecture for IoT network. J. Netw. Comput. Appl. 2019, 143, 167–177. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and IoT Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [PubMed]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security Services Using Blockchains: A State of the Art Survey. IEEE Commun. Surv. Tutor. 2019, 21, 858–880. [Google Scholar] [CrossRef]
- Lee, J.Y.; Lee, J. Current research trends in IoT security: A systematic mapping study. Mob. Inf. Syst. 2021, 2021, 8847099. [Google Scholar] [CrossRef]
- Alphand, O.; Amoretti, M.; Claeys, T.; Dall’Asta, S.; Duda, A.; Ferrari, G.; Rousseau, F.; Tourancheau, B.; Veltri, L.; Zanichelli, F. IoTChain: A blockchain security architecture for the Internet of Things. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Ouaddah, A.; Abou Elkalam, A.; Ait Ouahman, A. FairAccess: A new Blockchain-based access control framework for the Internet of Things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Pinno, O.J.A.; Gregio, A.R.A.; De Bona, L.C.E. ControlChain: Blockchain as a Central Enabler for Access Control Authorizations in the IoT. In Proceedings of the GLOBECOM 2017–2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Novo, O. Scalable Access Management in IoT Using Blockchain: A Performance Evaluation. IEEE Internet Things J. 2019, 6, 4694–4701. [Google Scholar] [CrossRef]
- Mishra, R.K.; Yadav, R.K.; Nath, P. Blockchain-Based Decentralized Authorization Technique for Data Sharing in the Internet of Things. In Proceedings of the 2021 5th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 22–23 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Mohanty, S.N.; Ramya, K.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.; Khanna, A. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Future Gener. Comput. Syst. 2020, 102, 1027–1037. [Google Scholar] [CrossRef]
- Du, M.; Wang, K.; Liu, Y.; Qian, K.; Sun, Y.; Xu, W.; Guo, S. Spacechain: A Three-Dimensional Blockchain Architecture for IoT Security. IEEE Wirel. Commun. 2020, 27, 38–45. [Google Scholar] [CrossRef]
- Lao, L.; Dai, X.; Xiao, B.; Guo, S. G-PBFT: A Location-based and Scalable Consensus Protocol for IoT-Blockchain Applications. In Proceedings of the 2020 IEEE International Parallel and Distributed Processing Symposium (IPDPS), New Orleans, LA, USA, 18–22 May 2020; pp. 664–673. [Google Scholar] [CrossRef]
- Azbeg, K.; Ouchetto, O.; Jai Andaloussi, S. BlockMedCare: A healthcare system based on IoT, Blockchain and IPFS for data management security. Egypt. Inform. J. 2022, 23, 329–343. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Ai, N. Decentralized AI Blockchain Whitepaper; Nebula AI Team: Montreal, QC, Canada, 2018. [Google Scholar]
- Dinh, T.N.; Thai, M.T. AI and Blockchain: A Disruptive Integration. Computer 2018, 51, 48–53. [Google Scholar] [CrossRef]
- Rathore, S.; Pan, Y.; Park, J.H. BlockDeepNet: A Blockchain-Based Secure Deep Learning for IoT Network. Sustainability 2019, 11, 3974. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Moustafa, N.; Hawash, H.; Razzak, I.; Sallam, K.M.; Elkomy, O.M. Federated Intrusion Detection in Blockchain-Based Smart Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2021, 23, 2523–2537. [Google Scholar] [CrossRef]
- Alsemmeari, R.A.; Dahab, M.Y.; Alsulami, A.A.; Alturki, B.; Algarni, S. Resilient Security Framework Using TNN and Blockchain for IoMT. Electronics 2023, 12, 2252. [Google Scholar] [CrossRef]
- Sudhakaran, P. Energy efficient distributed lightweight authentication and encryption technique for IoT security. Int. J. Commun. Syst. 2022, 35, e4198. [Google Scholar] [CrossRef]
- Tahsien, S.M.; Karimipour, H.; Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 2020, 161, 102630. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A review on machine learning and deep learning perspectives of IDS for IoT: Recent updates, security issues, and challenges. Arch. Comput. Methods Eng. 2021, 28, 3211–3243. [Google Scholar] [CrossRef]
- Aljuhani, A. Machine Learning Approaches for Combating Distributed Denial of Service Attacks in Modern Networking Environments. IEEE Access 2021, 9, 42236–42264. [Google Scholar] [CrossRef]
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Barnawi, A.; Alzahrani, B.A. Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research. J. Netw. Comput. Appl. 2020, 157, 102537. [Google Scholar] [CrossRef]
- Kuzlu, M.; Fair, C.; Guler, O. Role of artificial intelligence in the Internet of Things (IoT) cybersecurity. Discov. Internet Things 2021, 1, 1–14. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. MQTTset, a New Dataset for Machine Learning Techniques on MQTT. Sensors 2020, 20, 6578. [Google Scholar] [CrossRef] [PubMed]
- Ghazanfar, S.; Hussain, F.; Rehman, A.U.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT-Flock: An Open-source Framework for IoT Traffic Generation. In Proceedings of the 2020 International Conference on Emerging Trends in Smart Technologies (ICETST), Karachi, Pakistan, 26–27 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Hussain, F.; Abbas, S.G.; Shah, G.A.; Pires, I.M.; Fayyaz, U.U.; Shahzad, F.; Garcia, N.M.; Zdravevski, E. A Framework for Malicious Traffic Detection in IoT Healthcare Environment. Sensors 2021, 21, 3025. [Google Scholar] [CrossRef]

| Classifier | Performance Measurements | |||||||
|---|---|---|---|---|---|---|---|---|
| Precision | Recall | Accuracy | F1 Score | |||||
| V1 | V2 | V1 | V2 | V1 | V2 | V1 | V2 | |
| NB | 78.6480 | 96.4624 | 78.5683 | 96.3131 | 78.2341 | 96.5710 | 78.5292 | 96.1949 |
| KNN | 81.6286 | 97.1058 | 81.6171 | 97.1411 | 82.4633 | 97.4667 | 81.6045 | 97.1172 |
| RF | 89.9983 | 99.9872 | 89.8325 | 99.9878 | 90.2591 | 99.9894 | 89.7879 | 99.9875 |
| GB | 87.6908 | 99.7180 | 87.6105 | 99.7640 | 87.9219 | 99.7403 | 87.5802 | 99.7406 |
| DT | 96.8762 | 100.0 | 96.8635 | 100.0 | 96.5710 | 100.0 | 96.8562 | 100.0 |
| Classifier | Performance Measurements | |||||||
|---|---|---|---|---|---|---|---|---|
| Precision | Recall | Accuracy | F1 Score | |||||
| V1 | V2 | V1 | V2 | V1 | V2 | V1 | V2 | |
| CNN | 78.1730 | 99.3337 | 76.8360 | 99.3684 | 77.1795 | 99.3057 | 76.5439 | 99.3470 |
| RNN | 80.9068 | 99.7547 | 80.8552 | 99.7465 | 81.5729 | 99.7880 | 80.8283 | 99.7501 |
| GRU | 87.5437 | 99.6448 | 86.4697 | 99.6505 | 86.5440 | 99.6979 | 86.2995 | 99.6473 |
| LSTM | 85.0663 | 99.8090 | 84.6829 | 99.8041 | 85.2244 | 99.8357 | 84.6397 | 99.8064 |
| CNN + LSTM | 84.8737 | 99.6155 | 84.1229 | 99.6275 | 84.4506 | 99.6767 | 83.9883 | 99.6192 |
| CNN + GRU | 85.2915 | 99.5167 | 84.7879 | 99.5487 | 85.0760 | 99.5919 | 84.6826 | 99.5291 |
| RNN + GRU | 86.5751 | 99.8186 | 86.2702 | 99.8080 | 86.4380 | 99.8410 | 86.1876 | 99.8126 |
| RNN + LSTM | 86.9917 | 99.5003 | 86.7917 | 99.5153 | 86.9256 | 99.5760 | 86.7354 | 99.5038 |
| RNN + CNN | 85.1768 | 99.8542 | 84.4807 | 99.8590 | 84.9170 | 99.8781 | 84.3648 | 99.8563 |
| Classifier | Performance Measurements | |||||||
|---|---|---|---|---|---|---|---|---|
| Precision | Recall | Accuracy | F1 Score | |||||
| Benchmark | V2 | Benchmark | V2 | Benchmark | V2 | Benchmark | V2 | |
| NB | 79.6711 | 96.4624 | 99.7053 | 96.3131 | 52.1823 | 96.5710 | 68.5092 | 96.1949 |
| KNN | 99.6502 | 97.1058 | 99.6867 | 97.1411 | 99.4873 | 97.4667 | 99.5869 | 97.1172 |
| RF | 99.7068 | 99.9872 | 99.7952 | 99.9878 | 99.5123 | 99.9894 | 99.6535 | 99.9875 |
| DT | 99.6944 | 100.0 | 99.7993 | 100.0 | 99.4789 | 100.0 | 99.6388 | 100.0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alshammari, B.M. AIBPSF-IoMT: Artificial Intelligence and Blockchain-Based Predictive Security Framework for IoMT Technologies. Electronics 2023, 12, 4806. https://doi.org/10.3390/electronics12234806
Alshammari BM. AIBPSF-IoMT: Artificial Intelligence and Blockchain-Based Predictive Security Framework for IoMT Technologies. Electronics. 2023; 12(23):4806. https://doi.org/10.3390/electronics12234806
Chicago/Turabian StyleAlshammari, Bandar M. 2023. "AIBPSF-IoMT: Artificial Intelligence and Blockchain-Based Predictive Security Framework for IoMT Technologies" Electronics 12, no. 23: 4806. https://doi.org/10.3390/electronics12234806
APA StyleAlshammari, B. M. (2023). AIBPSF-IoMT: Artificial Intelligence and Blockchain-Based Predictive Security Framework for IoMT Technologies. Electronics, 12(23), 4806. https://doi.org/10.3390/electronics12234806






