Crypto-Ransomware: A Revision of the State of the Art, Advances and Challenges
Abstract
:1. Introduction
2. Ransomware-as-a-Service Ecosystems, Crypto-Coins and Extortion
- Device locker. It is aimed at locking the victim’s device functions, such as the screen or keyboard. W32.Rasith or Android.LockDroid.H are some examples of this typology.
- Crypto-ransomware. Contrary to the previous type, this focuses on encrypting the victim’s data. The victim should pay a ransom to obtain the key for deciphering the affected files and recovering them.
- Victim intimidation (scareware). This kind of ransomware just scares the victim through specific messages indicating that their files are blocked or ciphered, although that is not true.
- Data exfiltration (leakware or doxware). Sensitive information is exfiltrated from the victim’s device. Different from crypto-ransomware, the victim can still access the files.
3. Crypto-Ransomware Attack Model
- Reconnaissance. In this phase, the attacker gathers as much data as possible about potential targets from, e.g., email lists, social networks, system and service vulnerabilities, among other sources of information. Such information will help the attacker to perform a targeted, more robust attack [23].
- Weaponization. The malicious payload is prepared to be delivered to the target in this stage.
- Delivery. In this phase, the attacker searches for a valid way to deliver the malicious payload to the targets. For instance, by sending a compromised email to them.
- Exploitation. This comprises methods and techniques for exploiting vulnerabilities on the target computer and allowing attackers to execute the malicious payload.
- Installation. The methods through which attackers are able to access and compromise nearby nodes and install administrative tools like Remote Access Trojans (RAT) or backdoors [24] are involved in this phase.
- Command & Control. The attacker builds dedicated communication channels to manage the compromised system.
- Actions. In this phase, the attacker carries out actions on the compromised system according to the main attack objective. For instance, file ciphering, data exfiltration or data erasing.
3.1. Reconnaissance Stage
- Time-based evasion techniques schedule the attack execution or measure how long the attack execution was. They, in turn, can be split into two: delayed and event-based execution. The first ones delay the ciphering procedure, while the second ones wait for a specific system event to start the ciphering process (e.g., a system reboot).
- Data-based evasion schemes are focused on removing all the attack evidence, making them difficult to detect and identify. As an example, anti-memory-dumping techniques make reverse engineering difficult in the case of applying digital forensic analysis. To do that, removing executable file headers or moving them to different memory locations can be implemented. One more example is ADS (Alternate Data Streams) [30], which consists of adding extra attributes to the file containing the malware.
- Code-based evasion techniques have four variants. The first typology is called the debugger evasion technique and it tries to detect if the code is being debugged. In that case, the malware stops its execution or tries to kill the debugger. Some other techniques add useless pieces of code/data to obfuscate it; the reverse engineering process thus becomes more difficult and the antivirus detection performance is reduced [31]. They are also known as anti-disassembling evasion techniques. Anti-sandboxing code evasion techniques are devised to detect and avoid running a malware sample in a virtualized environment or sandbox, which is usually employed by security analysts to safely characterize the malware behavior. Finally, polymorphism and metamorphism techniques add little modifications to malware samples so that they can evade signature-based detection techniques.
- Network-based evasion techniques are applied to network communications with the main aim of fooling IDS/IPS (Intrusion Detection Systems/Intrusion Prevention Systems). Network traffic ciphering or anonymizing, domain shadowing and fast flux are some examples of such kind of techniques. Thus, ciphering C&C communications prevent external analysis. Network traffic anonymization, using darknets, for instance, does not only cipher but also prevents the disclosing of the source of the communication. Attackers also use domain shadowing, which consists of first stealing a legitimate domain to be subsequently used for building sub-domains. Then, such sub-domains are periodically rotated to point to malicious servers. Finally, fast flux techniques prevent the attacker’s IP from belonging to black lists. For that, the associated IP is periodically changed according to a predefined list.
3.2. Exploitation Stage
3.3. Installation Stage
3.4. C&C Stage
3.5. Action Stage
4. Crypto-Ransomware Evolution
4.1. The Origins
4.2. Use of Cryptocurrencies
4.3. Crypto-Ransomware Explosion
4.4. New Extortion Techniques
4.5. Critical Infrastructure Attacks
- An attack on the supply chain. This attack tries to extend the radius of affection of ransomware to the entire software supply chain by inserting malicious code into a trusted component [113].
- The use of the RaaS model to launch and maintain an attack campaign [10].
- An attack on unpatched systems. While new ransomware to exploit zero-day vulnerabilities appears, known vulnerabilities continue to be exploited on unpatched systems.
- Phishing. Although they are not the main cause, phishing emails are frequent in ransomware attacks.
- Multiple extortion. New extortion models include multiple levels of extortion, personalization and evolution towards new protected goods such as IoT (Internet of Things) [114]. It should be noted that, according to a report by the consulting firm Unit 42 [115], some families of ransomware have evolved from double to quadruple extortion [116]. The Suncrypt group even called the victim to pressure her into making the payment [117].
5. Defence against Crypto-Ransomware
5.1. Crypto-Ransomware Mitigation
- Periodically patching software and firmware, since ransomware usually attacks known vulnerabilities [124].
- Blocking access to web resources that are potentially dangerous such as name servers and malicious or suspicious IP addresses, ports and protocols.
- Use of whitelists for authorized applications.
- Use of standard accounts instead of privileged ones.
- Establishing BYOD (Bring Your Own Device) policies for personal devices on corporate environments [127].
- Avoiding the use of personal applications on the equipment such as email clients or social networks.
- Training staff and users about security risks, in particular regarding social engineering. Associated behaviors should be supervised.
- Managing authorization credentials to every asset in the organization. In particular, regarding the file system.
- Making periodic off-site backups [128].
- Protecting against data ex-filtration events, which are identified in the MITRE ATT&CK report [129].
5.1.1. Access Control
5.1.2. Data Backups
5.1.3. Deception Techniques
5.1.4. User Training and Awareness
5.2. Detection of Crypto-Ransomware
5.2.1. Data Source
5.2.2. Processing
| Name | Classification Algorithm(s) | Feature(s) | Ref. |
|---|---|---|---|
| - | Random Forest (RF) | Raw bytes | [255] |
| DNAact-Ran | LiR | K-mer frequency | [256] |
| RansomWall | ANN, GTB, LR, RF, SVM | System calls/API | [167] |
| - | DT, LR, NB, RF | Logfiles | [166] |
| - | ANN, DT, KNN, LiR, LR, SVM | File I/O | [257] |
| PEDA | RF | System Calls/API | [252] |
| - | SVM | System calls/API | [258] |
| - | SVM | System calls/API | [259] |
| DPBD-FE | ANN, Boosting, CART, DT, KNN, | System calls/API | [260] |
| LDA, LR, NB, RF | |||
| DRDT | CNN | System calls/API | [261] |
| - | ANN | Log files | [262] |
| - | KNN, LR, NB, RF, SGD, SVM | System calls/API | [263] |
| - | DT, LiR | System calls/API | [264] |
| - | AdaBoost, Bagging, BN, DT, | System calls/API, RAM memory dump | [265] |
| LogiBoost, LR, NB, RF | |||
| iBagging/ESRS | Linear regression | System calls/API | [247] |
| RAPPER | ANN (LSTM) | HPC | [224] |
| - | BN, RF, SVM, RT | Network traffic | [266] |
| - | ANN, KNN, RF, SVM | CPU consumption | [267] |
| - | RF | Network traffic | [268] |
| - | CNN | Operation codes | [201] |
| - | SVM | Operation code sequences/byte | [269] |
| - | CNN | PE executable headers | [270] |
| - | DT, LR, NB, RF, SVM | DLL calls, Operation/bytes codes | [271] |
| - | DT, LR, RF, SVM | DLL calls, operation code/byte sequences | [272] |
| DRTHIS | CNN, LSTM | Event sequences | [254] |
| - | NB, SVM | Network traffic | [273] |
| DRDT | TextCNN | System calls | [261] |
| - | RF | DDL calls, OS resources | [250] |
| - | RF, OoW | DDL calls | [249] |
| - | KNN, LR, NB, RF, SGD, SVM | System calls | [195] |
| AIRaD | AI | DLL calls | [198] |
| DeepRan | BiLSTM, FC | Logs | [193] |
| RanStop | LSTM | Hardware events | [225] |
| MUSTARD | RF | Folders, file operations and types | [274] |
| DIMAQS | CPN, DNN | DB SQL queries | [275] |
| BGPGuard | CNNs, GBDT, GRU, LSTM, RNNs | Features selection | [276] |
| - | RF | Network traffic (PSO) | [277] |
| SwiftR | HNN, LSTM | Binary code, word-embedded) | [278] |
| RANDES | GAT | lists of assembly mnemonic | [279] |
| - | NN | API calls | [280] |
| - | GP, CC | API calls, extension of dropped files, | [281] |
| Registry key operations, embedded strings |
5.3. Response to Crypto-Ransomware
| Work | No. Samples | No. Active samples | TP Rate | Ratio Active Samples/Family | Source of the Collection or Method |
|---|---|---|---|---|---|
| Ahmed [196] | 1254 | 673 | 98.8 | 48.1 | virusshare.com, virustotal.com (accessed on 25 October 2023), spider to repositories, forums |
| Berrueta [294] | 70 | NA | NA | NA | PCAP repository http://dataset.tlm.unavarra.es/ransomware/ (accessed on 25 October 2023) |
| Cabaj [212] | NA | 787 | 98 | 395.5 | malwr.com, ransomtracker.abuse.ch (accessed on 25 October 2023) |
| ISOT [295] | 669 | NA | NA | NA | www.uvic.ca/ecs/ece/isot/datasets/botnet-ransomware/ (accessed on 25 October 2023) |
| Morato [214] | NA | 54 | 100 | 2.8 | NA |
| RISSP [296] | 540 | NA | NA | NA | github.com/rissgrouphub/ransomwaredataset2016 (accessed on 23 October 2023) |
| Temple [297] | 1156 | NA | NA | NA | Critical Infrastructures incidents (2013–2021) https://sites.temple.edu/care/ci-rw-attacks/ (accessed on 25 October 2023) |
| CIRW [298] | NA | NA | NA | NA | Critical Infrastructure RansomWare. Available by request |
| Zscaler ThreatLabz | NA | NA | NA | NA | Repository of ransom notes https://github.com/threatlabz/ransomware_notes/ (accessed on 25 October 2023) |
6. Trends and Challenges
- Estimating the adequate model is a complex task, since the occurrence of over/under-training, and thus bias, is feasible [307].
- The cost involved in ML classification and detection techniques can be high. To avoid that, dimensional reduction techniques are useful, like PCA in reference [308].
- Despite current detection schemes being efficient, new ransomware samples can implement novel tactics to evade detection procedures in what is called Adversarial ML [309]. To solve this problem, hybrid classifiers are developed, which combine both static and dynamic features [310] or different classification algorithms (ensemble malware detection) [243].
- Also related to detection evasion, papers like reference [204] analyze the resilience of ML algorithms against security incidents.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- TrendLabs: Ransomware: Past, Present and Future. Report. 2022. Available online: https://documents.trendmicro.com/assets/wp/wp-ransomware-past-present-and-future.pdf (accessed on 25 October 2023).
- ENISA: ENISA Threat Landscape (July 2021 to July 2022). European Union Agency for Cybersecurity. Available online: https://www.enisa.europa.eu/publications/enisa-threat-landscape-2022 (accessed on 25 October 2023).
- Liska, A. Ransomware: Understand, Prevent, Recover; ActualTech Media: North Charleston, SC, USA, 2021. [Google Scholar]
- Corbet, S.; Goodell, J.W. The reputational contagion effects of ransomware attacks. Financ. Res. Lett. 2022, 47, 102715. [Google Scholar] [CrossRef]
- Microsoft. Destructive Malware Targeting Ukranian Organizations. Available online: https://www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/ (accessed on 25 October 2023).
- Embroker. Top 10 Cybersecurity Threats in 2022. Available online: https://www.embroker.com/blog/top-10-cybersecurity-threats-2022/ (accessed on 25 October 2023).
- Imperva. 2021 Cyberthreat Defense Report. Cyberedge Group. 2021. Available online: https://www.imperva.com/resources/resource-library/reports/2021-cyberthreat-defense-report/ (accessed on 25 October 2023).
- Morrison, A. Cyber Security Landscape 2022. Deloitte. 2022. Available online: https://docplayer.net/228758092-Cyber-security-landscape-2022.html (accessed on 25 October 2023).
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Kumar, P.R.; Ramlie, H.R.E.B.H. Anatomy of Ransomware: Attack Stages, Patterns and Handling Techniques. In Computational Intelligence in Information Systems (CIIS); Advances in Intelligent Systems and, Computing; Suhaili, W.S.H., Siau, N.Z., Omar, S., Phon-Amuaisuk, S., Eds.; Springer: Cham, Switzerland, 2021; Volume 1321. [Google Scholar] [CrossRef]
- Beaman, C.; Barkworth, A.; Akande, T.D.; Hakak, S.; Khan, M.K. Ransomware: Recent advances, analysis, challenges and future research directions. Comput. Secur. 2021, 111, 102490. [Google Scholar] [CrossRef] [PubMed]
- Buker, K. Ransomware as a Service (RaaS) Explained. Crowstrike. February 2022. Available online: https://www.crowdstrike.com/cybersecurity-101/ransomware/ransomware-as-a-service-raas/ (accessed on 25 October 2023).
- Barr-Smith, F.; Ugarte-Pedrero, X.; Graziano, M.; Spolaor, R.; Martinovic, I. Survivalism: Systematic Analysis of Windows Malware Living-Off-The-Land. In Proceedings of the IEEE Symposium on Security and Privacy (SP), Francisco, CA, USA, 24–27 May 2021; pp. 1557–1574. [Google Scholar] [CrossRef]
- Lakshmanan, R. Dridex Malware Deploying Entropy Ransomware on Hacked Computers. The Hacker News. February 2022. Available online: https://thehackernews.com/2022/02/dridex-malware-deploying-entropy.html (accessed on 25 October 2023).
- Insikt Group. New Ransomware-as-a-Service Tool ’Thanos’ Shows Connections to ’Hakbit’. Recorded Future. June 2020. Available online: https://www.recordedfuture.com/thanos-ransomware-builder/ (accessed on 25 October 2023).
- de Jesús, M.; Ladores, D.O. Chaos Ransomware: A Proof of Concept With Potentially Dangerous Applications. Trend Micro. August 2021. Available online: https://www.trendmicro.com/en_us/research/21/h/chaos-ransomware-a-dangerous-proof-of-concept.html (accessed on 25 October 2023).
- Gray, I.W.; Cable, J.; Cuiujuclu, V.; Brown, B.; McCoy, D. Money Over Morals: A Business Analysis of Conti Ransomware. In Proceedings of the IEEE Symposium on Electronic Crime Research (eCrime), Boston, MA, USA, 30 November–2 December 2022; Available online: https://damonmccoy.com/papers/Ransomware_eCrime22.pdf (accessed on 25 October 2023).
- Schwartz, M.J. Cybercrime Moves: Conti Ransomware Absorbs TrickBot Malware, Baank Info Security. February 2022. Available online: https://www.bankinfosecurity.com/cybercrime-moves-conti-ransomware-absorbs-trickbot-malware-a-18573 (accessed on 25 October 2023).
- Dargahi, T.; Dehghantanha, A.; Bahrami, P.N.; Conti, M.; Bianchi, G. A Cyber-Kill-Chain based taxonomy of crypto-ransomware features. J. Comput. Virol. Hack Tech. 2019, 15, 277–305. [Google Scholar] [CrossRef]
- Mirza, Q.K.A.; Brown, M.; Halling, O.; Shand, L.; Alam, A. Ransomware Analysis using Cyber Kill Chain. In Proceedings of the 8th International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 23–25 August 2021; pp. 58–65. [Google Scholar] [CrossRef]
- Mahdipour, E.; Aghamohammadpour, A.; Attarzadeh, I. Ransomware Modeling Based on a Process Mining Approach. Int. J. Inf. Commun. Technol. 2022, 14, 27–36. [Google Scholar] [CrossRef]
- Martin, L. The Cyber Kill Chain. Available online: http://www.lockheedmartin.com/us/what-we-do/aerospace-defense/cyber/cyber-kill-chain.html (accessed on 25 October 2023).
- Mayukha, S.; Vadivel, R. Reconnaissance for Penetration Testing Using Active Scanning of MITRE ATT&CK. In Information and Communication Technology for Competitive Strategies (ICTCS 2021); Lecture Notes in Networks and, Systems; Kaiser, M.S., Xie, J., Rathore, V.S., Eds.; Springer: Singapore, 2023; Volume 401. [Google Scholar] [CrossRef]
- Zimba, A.; Wang, Z. Malware-Free Intrusions: Exploitation of Built-in Pre-Authentication Services for APT Attack Vectors. Int. J. Comput. Netw. Inf. Secur. (IJCNIS) 2017, 9, 1–10. [Google Scholar] [CrossRef]
- Xiong, W.; Legrand, E.; Åberg, O.; Lagerström, R. Cyber security threat modeling based on the MITRE Enterprise ATT&CK Matrix. Softw. Syst. Model 2022, 21, 157–177. [Google Scholar] [CrossRef]
- Genç, Z.A.; Lenzini, G.; Ryan, P.Y.A. Next Generation Cryptographic Ransomware. In Secure IT Systems. NordSec 2018; Lecture Notes in Computer Science; Gruschka, N., Ed.; Springer; Cham, Switzerland, 2018; Volume 11252. [Google Scholar] [CrossRef]
- Olaimat, M.N.; Maarof, M.A.; Al-rimy, B.A.S. Ransomware Anti-Analysis and Evasion Techniques: A Survey and Research Directions. In Proceedings of the 3rd International Cyber Resilience Conference (CRC), Virtual, 29–31 January 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Afianian, A.; Niksefat, S.; Sadeghiyan, B.; Baptiste, D. Malware Dynamic Analysis Evasion Techniques: A Survey. ACM Comput. Surv. 2020, 52, 1–28. [Google Scholar] [CrossRef]
- Veerappan, C.S.; Keong, P.L.K.; Tang, Z.; Tan, F. Taxonomy on malware evasion countermeasures techniques. In Proceedings of the IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 558–563. [Google Scholar] [CrossRef]
- Wilson, C. Forensic Analysis of the Zone. Identifier Stream, Digital Forensic. Blog. 2021. Available online: https://www.digital-detective.net/forensic-analysis-of-zone-identifier-stream/ (accessed on 25 October 2023).
- Ghafarian, A.; Keskin, D.; Helton, G. An Assessment of Obfuscated Ransomware Detection and Prevention Methods. In Advances in Information and Communication. FICC 2021; Advances in Intelligent Systems and Computing; Arai, K., Ed.; Springer: Cham, Switzerland, 2021; Volume 1363. [Google Scholar] [CrossRef]
- Hassan, N.A. Ransomware Distribution Methods. In Ransomware Revealed; Apress: Berkeley, CA, USA, 2019. [Google Scholar] [CrossRef]
- Gangwar, K.; Mohanty, S.; Mohapatra, A.K. Analysis and Detection of Ransomware Through Its Delivery Methods. In Data Science and Analytics. REDSET 2017; Communications in Computer and Information Science; Panda, B., Sharma, S., Roy, N., Eds.; Springer: Singapore, 2018; Volume 799. [Google Scholar] [CrossRef]
- Alkhalil, Z.; Hewage, C.; Nawaf, L.; Khan, I. Phishing Attacks: A Recent Comprehensive Study and a New Anatomy. Front. Comput. Sci. 2021, 3, 563060. [Google Scholar] [CrossRef]
- Salahdine, F.; Kaabouch, N. Social Engineering Attacks: A Survey. Future Internet 2019, 11, 89. [Google Scholar] [CrossRef]
- Veeam. 2021 Ransomware Retrospective. Veeam Software. 2021. Available online: https://www.veeam.com/2021-ransomware-retrospective.html (accessed on 30 October 2022).
- He, G.Q.; Liu, C.; Huang, A. Ransomware Families: 2021 Data to Supplement the Unit42 Ransomware Threat Report. Unit42. July 2021. Available online: https://unit42.paloaltonetworks.com/ransomware-families/ (accessed on 25 October 2023).
- VirusTotal. Ransomware in a Global Context. 2021. Available online: https://www.virustotal.com/go/ransomware-in-a-global-context-2021 (accessed on 30 October 2022).
- Trend Micro. Exploit kit. Available online: https://www.trendmicro.com/vinfo/us/security/definition/exploit-kit (accessed on 25 October 2023).
- Suren, E.; Angin, P. Know Your EK: A Content and Workflow Analysis Approach for Exploit Kits. J. Internet Serv. Inf. Secur. (JISIS) 2019, 9, 24–47. Available online: http://isyou.info/jisis/vol9/no1/jisis-2019-vol9-no1-02.pdf (accessed on 25 October 2023).
- Trend Micro. New Exploit Kit Fallout Delivering Gandcrab Ransomware. 2018. Available online: https://www.trendmicro.com/vinfo/es/security/news/cybercrime-and-digital-threats/new-exploit-kit-fallout-delivering-gandcrab-ransomware (accessed on 25 October 2023).
- Gatlan, S. Maze Ransomware Now Delivered by Spelevo Exploit Kit. Blee Ping Computer. October 2019. Available online: https://www.bleepingcomputer.com/news/security/maze-ransomware-now-delivered-by-spelevo-exploit-kit/ (accessed on 25 October 2023).
- Malware Bytes. GandCrab Ransomware Distributed by RIG and GrandSoft Exploit Kits. Malware Bytes. January 2018. Available online: https://www.malwarebytes.com/blog/news/2018/01/gandcrab-ransomware-distributed-by-rig-and-grandsoft-exploit-kits (accessed on 25 October 2023).
- CSW. Ransomware—Through the Lens of Threat and Vulnerability Management. CSW SecurityWorks, Spotlight Report, Index Update Q2–Q3. 2022. Available online: https://cybersecurityworks.com/ransomware/ (accessed on 25 October 2023).
- S21Sec. Threat Landscape Report. S21Sec Cyber Solutions, Second semester of 2022. Available online: https://www.s21sec.com/es/descargar-threat-landscape-report/ (accessed on 25 October 2023).
- Van Impe, K. How Attackers Exploit the Remote Desktop Protocol. Security Intelligence. 15 November 2021. Available online: https://securityintelligence.com/articles/exploiting-remote-desktop-protocol/ (accessed on 25 October 2023).
- Stocchetti, V. (Ed.) Exploited Protocols: Server Message Block (SMB). Center for Internet Security (CSI). 2021. Available online: https://learn.cisecurity.org/CIS_Controls_v8_Exploited_Protocols_Server_Message_Block_SMB (accessed on 30 October 2022).
- Cimpanu, C. Top Exploits Used by Ransomware Gangs are VPN Bugs, but RDP Still Reigns Supreme. ZDNet. August 2020. Available online: https://www.zdnet.com/article/top-exploits-used-by-ransomware-gangs-are-vpn-bugs-but-rdp-still-reigns-supreme/ (accessed on 25 October 2023).
- Ogu, E.C.; Ojesanmi, O.A.; Awodele, O.; Kuyoro, S. A Botnets Circumspection: The Current Threat Landscape, and What We Know So Far. Information 2019, 10, 337. [Google Scholar] [CrossRef]
- Fortinet. The Ins and Outs of the Ransomware: How to Mitigate Email-based Attacks. Fortinet White Paper. 2019. Available online: https://www.insightsforprofessionals.com/it/security/the-ins-and-outs-of-ransomware (accessed on 25 October 2023).
- Yuste, J.; Pastrana, S. Avaddon ransomware: An in-depth analysis and decryption of infected systems. Comput. Secur. 2021, 109, 102388. [Google Scholar] [CrossRef]
- Yüceel, H.C. TTPs used by BlackByte Ransomware Targeting Critical Infrastructure. Pycus Security. February 2022. Available online: https://www.picussecurity.com/resource/ttps-used-by-blackbyte-ransomware-targeting-critical-infrastructure (accessed on 25 October 2023).
- Mendrez, R. BlackByte Ransomware—Pt. 1 In-Depth Analysis. Trustwave. October 2021. Available online: https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/blackbyte-ransomware-pt-1-in-depth-analysis/ (accessed on 25 October 2023).
- Hill, J. ALPHV (BlackCat) Ransomware, Inside Out Security. January 2022. Available online: https://www.varonis.com/blog/alphv-blackcat-ransomware (accessed on 25 October 2023).
- Tanner, A.; Hinchliffe. Threat Assessment: BlackCat Ransomware. Palo Alto Network. January 2022. Available online: https://unit42.paloaltonetworks.com/blackcat-ransomware/ (accessed on 25 October 2023).
- Kara, I.; Aydos, M. Static and Dynamic Analysis of Third Generation Cerber Ransomware. In Proceedings of the International Congress on Big Data, Deep Learning and Fighting Cyber Terrorism (IBIGDELFT), Ankara, Turkey, 3–4 December 2018; pp. 12–17. [Google Scholar] [CrossRef]
- Pletinckx, S.; Trap, C.; Doerr, C. Malware Coordination using the Blockchain: An Analysis of the Cerber Ransomware. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Kurniawan, A.; Riadi, I. Detection and Analysis Cerber Ransomware Based on Network Forensics Behavior. Int. J. Netw. Secur. 2018, 20, 836–843. [Google Scholar] [CrossRef]
- DFIR. Diavol Ransomware. The DFIR Report. December 2021. Available online: https://thedfirreport.com/2021/12/13/diavol-ransomware/ (accessed on 25 October 2023).
- Neemani, D.; Rubinfeld, A. Diavol—A New Ransomware Used By Wizard Spider? Forninet. July 2021. Available online: https://www.fortinet.com/blog/threat-research/diavol-new-ransomware-used-by-wizard-spider (accessed on 25 October 2023).
- Masson, D. What the EKANS Ransomware Attack Reveals about the Future of OT Cyber-Attacks. Darktrace Blog. June 2020. Available online: https://www.darktrace.com/en/blog/what-the-ekans-ransomware-attack-reveals-about-the-future-of-ot-cyber-attacks/ (accessed on 25 October 2023).
- Dragos. EKANS Ransomware and ICS Operations. Dragos. March 2020. Available online: https://www.dragos.com/blog/industry-news/ekans-ransomware-and-ics-operations/ (accessed on 25 October 2023).
- Bradt, A. Dridex Bots Deliver Entropy Ransomware in Recent Attacks. Sophos News. February 2022. Available online: https://news.sophos.com/en-us/2022/02/23/dridex-bots-deliver-entropy-ransomware-in-recent-attacks/ (accessed on 25 October 2023).
- Palazolo, G.; Duarte, F. Reverse Engineering Dridex and Automating IOC Extraction. Appgate. September 2020. Available online: https://www.appgate.com/blog/reverse-engineering-dridex-and-automating-ioc-extraction (accessed on 25 October 2023).
- CCN-CERT. Hive ransomware. CCN-CERT ID-15/21. December 2021. Available online: https://www.ccn-cert.cni.es/informes/informes-ccn-cert-publicos/6326-ccn-cert-id-15-21-hive-ransomware-1/file.html (accessed on 25 October 2023).
- Muir, M. Analysis of Novel Khonsari Ransomware Deployed by the Log4Shell Vulnerability. Cado Security. December 2021. Available online: https://www.cadosecurity.com/analysis-of-novel-khonsari-ransomware-deployed-by-the-log4shell-vulnerability/ (accessed on 25 October 2023).
- MacRae, J.; Franqueira, V.N.L. On Locky Ransomware, Al Capone and Brexit. In Digital Forensics and Cyber Crime. ICDF2C 2017; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Matoušek, P., Schmiedecker, M., Eds.; Springer: Cham, Switzerland, 2018; Volume 216. [Google Scholar] [CrossRef]
- Broadhurst, R.; Trivedi, H. Malware in spam email: Risks and trends in the Australian spam intelligence database. Trends and Issues in Crime and Criminal Justice. Electron. Resour. 2020, 603, 1–18. [Google Scholar] [CrossRef]
- Avast. A Closer Look at the Locky Ransomware. Avast. March 2016. Available online: https://blog.avast.com/a-closer-look-at-the-locky-ransomware (accessed on 25 October 2023).
- Bison, D. MegaCortex Ransomware v2 Released With Anti-Analysis Features, Security Intelligence. 2019. Available online: https://securityintelligence.com/news/megacortex-ransomware-v2-released-with-anti-analysis-features/ (accessed on 25 October 2023).
- Gupta, S. Kaseya VSA Downed by REvil in Monumental Supply-Chain Attack. CSOnline. July 2021. Available online: https://cybersecurityworks.com/blog/ransomware/kaseya-vsa-downed-by-revil-in-monumental-supply-chain-attack.html (accessed on 25 October 2023).
- Elshinbary, A. Deep Analysis of Ryuk Ransomware. GitHub. May 2020. Available online: https://n1ght-w0lf.github.io/malwareanalysis/ryuk-ransomware/ (accessed on 25 October 2023).
- Mason, B. Ryuk Malware - Analysis and Reverse Engineering. Ben’s ideas and projects Blog. April 2020. Available online: https://ben.the-collective.net/posts/2020-04-08-ryuk-malware-analysis-and-reverse-engineering/ (accessed on 25 October 2023).
- Avertium. An In-Depth Look at Ransomware Gang. Sabbath. January 2022. Available online: https://www.avertium.com/resources/threat-reports/in-depth-look-at-sabbath-ransomware-gang (accessed on 25 October 2023).
- McAfee. McAfee ATR Analyzes Sodinokibi aka REvil Ransomware-as-a-Service—What The Code Tells Us. McAfee. October 2019. Available online: https://www.mcafee.com/blogs/other-blogs/mcafee-labs/mcafee-atr-analyzes-sodinokibi-aka-revil-ransomware-as-a-service-what-the-code-tells-us/ (accessed on 25 October 2023).
- Shushan, A.B.; Lifshitz, N.; Kushnir, A.; Korman, M.; Wasserman, B. Lazarus Group’s Mata Framework Leveraged To Deploy TFlower Ransomware. Sygnia. August 2021. Available online: https://blog.sygnia.co/lazarus-groups-mata-framework-leveraged-to-deploy-tflower-ransomware (accessed on 25 October 2023).
- Hybrid Analysis. tflower.exe. October 2019. Available online: https://hybrid-analysis.com/sample/7ca3494c165647424222f80b8b61a9fb80ff695c2be77a9fb6a0a352f5df3140?environmentId=120 (accessed on 25 October 2023).
- Kao, D.; Hsiao, S. The dynamic analysis of WannaCry ransomware. In Proceedings of the 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018; pp. 159–166. [Google Scholar] [CrossRef]
- Hsiao, S.; Kao, D. The static analysis of WannaCry ransomware. In Proceedings of the 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018; pp. 153–158. [Google Scholar] [CrossRef]
- Chesti, I.A.; Humayun, M.; Sama, N.U.; Zaman, N. Evolution, Mitigation, and Prevention of Ransomware. In Proceedings of the 2nd International Conference on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, 13–15 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Zimba, A.; Chishimba, M. Understanding the Evolution of Ransomware: Paradigm Shifts in Attack Structures. Int. J. Comput. Netw. Inf. Secur. (IJCNIS) 2019, 11, 26–39. [Google Scholar] [CrossRef]
- Ramsdell, K.A.W.; Esbeck, K.E. Evolution of Ransomware. The Mitre Corporation. July 2021. Available online: https://healthcyber.mitre.org/wp-content/uploads/2021/08/Ransomware-Paper-V2.pdf (accessed on 25 October 2023).
- Martin, J.; Whelan, C. Ransomware through the lens of state crime. State Crime J. 2023, 12, 1–25. [Google Scholar] [CrossRef]
- Zscaler. CovidLock: Android Ransomware Walkthrough and Unlocking Routine. 2020. Available online: https://www.zscaler.com/blogs/security-research/covidlock-android-ransomware-walkthrough-and-unlocking-routine (accessed on 25 October 2023).
- Goliate. Hidden-Tear. Available online: https://github.com/goliate/hidden-tear (accessed on 25 October 2023).
- Ryu, S. Anatomy of Chaos Ransomware Builder and Its Origin (feat. Open-source Hidden Tear Ransomware). S2W Blog. August 2021. Available online: https://medium.com/s2wblog/anatomy-of-chaos-ransomware-builder-and-its-origin-feat-open-source-hidden-tear-ransomware-ffd5937d005f (accessed on 25 October 2023).
- Zhang, X.; Xiao, X. Thoughts on Vulnerability Security by Ransomware Virus. Int. J. Soc. Sci. Educ. Res. 2022, 5, 120–124. [Google Scholar] [CrossRef]
- Security. COVID-19 Pandemic Sparks 72% Ransomware Growth, Mobile Vulnerabilities Grow 50%. Security Magazine. July 2020. Available online: https://www.securitymagazine.com/articles/92886-covid-19-pandemic-sparks-72-ransomware-growth-mobile-vulnerabilities-grow-50 (accessed on 25 October 2023).
- Europol. COVID-19: Ransomware. December 2021. Available online: https://www.europol.europa.eu/covid-19/covid-19-ransomware (accessed on 25 October 2023).
- McAfee. McAfee Labs COVID-19 Threats Report. July 2020. Available online: https://www.mcafee.com/blogs/other-blogs/mcafee-labs/mcafee-covid-19-report-reveals-pandemic-threat-evolution/ (accessed on 25 October 2023).
- Lallie, H.S.; Shepherd, L.A.; Erola, J.C.N.A.; Epiphaniou, G.; Maple, C.; Bellekens, X. Cyber security in the age of COVID-19: A timeline and analysis of cyber-crime and cyber-attacks during the pandemic. Comput. Secur. 2021, 105, 102248. [Google Scholar] [CrossRef]
- Gatlan, S. Qlocker Ransomware Returns to Target QNAP NAS Devices Worldwide. BleepingComputer. January 2022. Available online: https://www.bleepingcomputer.com/news/security/qlocker-ransomware-returns-to-target-qnap-nas-devices-worldwide/ (accessed on 25 October 2023).
- Sachiel. Analysis of ’Heaven’s Gate’ Part 1. January 2021. Available online: https://sachiel-archangel.medium.com/analysis-of-heavens-gate-part-1-62cca0ace6f0 (accessed on 25 October 2023).
- Lifars. A Deep Dive into The Grief Ransomware’s Capabilities. Lifars. 2021. Available online: https://www.lifars.com/wp-content/uploads/2020/11/Whitepaper-Cybersecurity-Exercises-1.0.pdf (accessed on 25 October 2023).
- Varma, G.; Chauhan, R. Cybercriminals Strike Where It Hurts Most: SARS-Cov-2 Pandemic and its Influence on Critical Infrastructure Ransomware Attacks. In Proceedings of the 16th International Conference on Ubiquitous Information Management and Communication (IMCOM), Seoul, Republic of Korea, 3–5 January 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Din, A. The Full Source Code for the Babuk Ransomware Published on a Russian Hacker Forum. Heimdal Security. September 2021. Available online: https://heimdalsecurity.com/blog/the-full-source-code-for-the-babuk-ransomware-published-on-a-russian-hacker-forum/ (accessed on 25 October 2023).
- Tudor, D. Babuk Focuses On Data-Theft Extortion. Heimdal Security. May 2020. Available online: https://heimdalsecurity.com/blog/babuk-focuses-on-data-theft-extortion/ (accessed on 25 October 2023).
- Sadeen, A. Ransomware’s Favorite Target: Critical Infrastructure and Its Industrial Control Systems. Dark Reading. March 2023. Available online: https://www.darkreading.com/ics-ot/ransomware-s-favorite-target-critical-infrastructure-and-its-industrial-control-systems (accessed on 25 October 2023).
- CyberEdge. 2023 Cyberthreat Defense Report. CyberEdge Group. 2023. Available online: https://betanews.com/2023/04/11/multiple-threat-ransomware-attacks-become-more-common/ (accessed on 25 October 2023).
- Hammond, C.; Villadsen, O. Ex-Conti and FIN7 Actors Collaborate with New Domino Backdoor. Security Intelligence. April 2023. Available online: https://securityintelligence.com/posts/ex-conti-fin7-actors-collaborate-new-domino-backdoor/ (accessed on 25 October 2023).
- Nelson, N. IceFire Ransomware Portends a Broader Shift From Windows to Linux. Dark Reading. March 2023. Available online: https://www.darkreading.com/endpoint/icefire-ransomware-portends-broader-shift-windows-linux (accessed on 25 October 2023).
- Kovacs, E. LockBit Ransomware Group Developing Malware to Encrypt Files on macOS. Security Weeks. April 2023. Available online: https://www.securityweek.com/lockbit-ransomware-group-developing-malware-to-encrypt-files-on-macos/ (accessed on 25 October 2023).
- Invictus. Ransomware in the Cloud. Invictus Incident Response. April 2023. Available online: https://invictus-ir.medium.com/ransomware-in-the-cloud-7f14805bbe82 (accessed on 25 October 2023).
- Raheem, A.; Raheem, R.; Chen, T.M.; Alkhayyat, A. Estimation of Ransomware Payments in Bitcoin Ecosystem. In Proceedings of the IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), New York, NY, USA, 30 September–3 October 2021; pp. 1667–1674. [Google Scholar] [CrossRef]
- Bin Mohamed Yunus, Y.K.; Bin Ngah, S. Ransomware: Stages, detection and evasion. In Proceedings of the International Conference on Software Engineering & Computer Systems and 4th International Conference on Computational Science and Information Management (ICSECS-ICOCSIM), Pekan, Malaysia, 24–26 August 2021; pp. 227–231. [Google Scholar] [CrossRef]
- Meland, P.H.; Bayoumy, Y.F.F.; Sindre, G. The Ransomware-as-a-Service economy within the darknet. Comput. Secur. 2020, 1017, 92. [Google Scholar] [CrossRef]
- Karapapas, C.; Pittaras, I.; Fotiou, N.; Polyzos, G.C. Ransomware as a Service using Smart Contracts and IPFS. In Proceedings of the IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Kapoor, A.; Gupta, A.; Gupta, R.; Tanwar, S.; Sharma, G.; Davidson, I.E. Ransomware Detection, Avoidance, and Mitigation Scheme: A Review and Future Directions. Sustainability 2022, 14, 8. [Google Scholar] [CrossRef]
- Farhat, D.; Awan, M.S. A Brief Survey on Ransomware with the Perspective of Internet Security Threat Reports. In Proceedings of the 9th International Symposium on Digital Forensics and Security (ISDFS), Elazig, Turkey, 28–29 June 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Mehra, C.; Sharma, A.K.; Sharma, A. Elucidating Ransomware Attacks In Cyber-Security. Int. J. Innov. Technol. Explor. Eng. 2019, 9, 3536–3541. [Google Scholar] [CrossRef]
- Haber, M.J. Privileged Attack Vectors; Apress: Berkeley, CA, USA, 2020. [Google Scholar] [CrossRef]
- Kerner, M. Ransomware Trends, Statistics and Facts in 2021. TechTarger. November 2021. Available online: https://www.techtarget.com/searchsecurity/feature/Ransomware-trends-statistics-and-facts (accessed on 25 October 2023).
- Blessman, D. Protecting Your Software Supply Chain. Risk Manag. 2019, 66, 10–11. [Google Scholar]
- Haber, M.J.; Hills, C.; Chappell, B.; Maude, J. Beyond Trust Cybersecurity Trend Predictions for 2022 & Beyond. BeyondTrust. October 2021. Available online: https://www.beyondtrust.com/blog/entry/beyondtrust-cybersecurity-trend-predictions-for-2022 (accessed on 25 October 2023).
- Vaas, L. Ransomware Payments Explode Amid ’Quadruple Extortion’. ThreatPost. 2021. Available online: https://threatpost.com/ransomware-payments-quadruple-extortion/168622/ (accessed on 25 October 2023).
- Radware. 2021–2022 Global Threat Analysis Report. Radware Ltd. 2022. Available online: https://www.radware.com/2021-2022-global-threat-analysis-report/ (accessed on 25 October 2023).
- Collier, K. Ransomware Hackers’ New Tactic: Calling You Directly. NBC News. January 2022. Available online: https://www.nbcnews.com/tech/security/ransomware-hackers-new-tactic-calling-directly-rcna6466 (accessed on 25 October 2023).
- Barker, W.C.; Fisher, W.; Scarfone, K.; Souppaya, M. NIST 8374; Ransomware Risk Management: A Cybersecurity Framework Profile. National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2022. [CrossRef]
- Bradley, S. Ransomware. SANS Whitepapers. 2021. Available online: https://www.sans.org/white-papers/37317/ (accessed on 25 October 2023).
- Ekta; Bansal, U. A Review on Ransomware Attack. In Proceedings of the 2nd International Conference on Secure Cyber Computing and Communications (ICSCCC), Jalandhar, India, 21–23 May 2021; pp. 221–226. [Google Scholar] [CrossRef]
- CIS. Ransomware Impacts and Defense Controls. Available online: https://www.cisecurity.org/insights/blog/ransomware-impacts-and-defense-controls (accessed on 25 October 2023).
- CCCS. Ransomware playbook (ITSM.00.099). Canadian Centre for Cyber Security. 2021. Available online: https://cyber.gc.ca/sites/default/files/cyber/2021-12/itsm00099-ransomware-playbook-2021-final3-en.pdf (accessed on 25 October 2023).
- Sharma, N.; Shanker, R. Analysis of Ransomware Attack and Their Countermeasures: A Review. In Proceedings of the International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 1877–1883. [Google Scholar] [CrossRef]
- Midtrapanon, S.; Wills, G. Linux patch management: With security assessment features. In Proceedings of the 4th International Conference on Internet of Things, Big Data and Security, Heraklion, Crete, Greece, 2–4 May 2019; pp. 270–277. [Google Scholar]
- Liu, W. Modeling Ransomware Spreading by a Dynamic Node-Level Method. IEEE Access 2019, 7, 142224–142232. [Google Scholar] [CrossRef]
- Nair, A. The Why and How of adopting Zero Trust Model in Organizations. TechRxiv 2021, arXiv:techrxiv.14184671.v1. Available online: https://www.techrxiv.org/articles/preprint/The_Why_and_How_of_adopting_Zero_Trust_Model_in_Organizations/14184671/1 (accessed on 25 October 2023). [CrossRef]
- Atanassov, N.; Chowdhury, M.M. Mobile Device Threat: Malware. In Proceedings of the IEEE International Conference on Electro Information Technology (EIT), Mt. Pleasant, MI, USA, 14–15 May 2021; pp. 007–013. [Google Scholar] [CrossRef]
- Galinkin, E. Winning the Ransomware Lottery. In Decision and Game Theory for Security. GameSec 2021; Lecture Notes in Computer, Science; Bošanský, B., González, C., Rass, S., Sinha, A., Eds.; Springer: Cham, Switzerland, 2021; Volume 13061. [Google Scholar] [CrossRef]
- CIS. Ransomware: The Data Exfiltration and Double Extortion Trends. Center for Internet Security. Available online: https://www.cisecurity.org/insights/blog/ransomware-the-data-exfiltration-and-double-extortion-trend (accessed on 25 October 2023).
- Pagán, A.; Elleithy, K. A Multi-Layered Defense Approach to Safeguard Against Ransomware. In Proceedings of the 11th IEEE Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 0942–0947. [Google Scholar] [CrossRef]
- Margarov, G.; Mitrofanova, E. Management of Ransomware Detection and Prevention in Multilevel Environmental Monitoring Information System. In Functional Nanostructures and Sensors for CBRN Defence and Environmental Safety and Security; NATO Science for Peace and Security Series C: Environmental Security; Sidorenko, A., Hahn, H., Eds.; Springer: Dordrecht, The Netherlands, 2020; pp. 125–131. [Google Scholar] [CrossRef]
- Salunke, M.D.; Kumbharkar, P.B.; Pramod, K. A Proposed Methodology to Mitigate the Ransomware Attack. In Recent Trends in Intensive Computing; Rajesh, M., Vengatesan, K., Gnanasekar, M., Sitharthan, R., Pawar, A.B., Kalvadekar, P.N., Saiprasad, P.M., Eds.; IOS Press: Amsterdam, The Netherlands, 2021; Volume 39, pp. 16–21. [Google Scholar] [CrossRef]
- Singh, A.; Ikuesan, A.R.; Venter, H.S. Digital Forensic Readiness Framework for Ransomware Investigation. In Digital Forensics and Cyber Crime. ICDF2C 2018; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Breitinger, F., Baggili, I., Eds.; Springer: Cham, Switzerland, 2019; Volume 259, pp. 91–105. [Google Scholar] [CrossRef]
- Mundt, M.; Baier, H. Threat-based Simulation of Data Exfiltration Towards Mitigating Multiple Ransomware Extortions. Digit. Threat. Res. Pract. 2022, 4, 54. [Google Scholar] [CrossRef]
- Keshavarzi, M.; Ghaffary, H.R. An ontology-driven framework for knowledge representation of digital extortion attacks. Comput. Hum. Behav. 2023, 139, 107520. [Google Scholar] [CrossRef] [PubMed]
- Zhang, C.; Luo, F.; Ranzi, G. Multistage Game Theoretical Approach for Ransomware Attack and Defense. IEEE Trans. Serv. Comput. 2023, 16, 2800–2811. [Google Scholar] [CrossRef]
- Tiu, Y.L.; Zolkipli, M.F. Study on Prevention and Solution of Ransomware Attack. J. IT Asia 2021, 9, 133–139. [Google Scholar] [CrossRef]
- Manjezi, Z.; Botha, R.A. Preventing and Mitigating Ransomware. In Information Security. ISSA 2018; Communications in Computer and Information, Science; Venter, H., Loock, M., Coetzee, M., Eloff, M., Eloff, J., Eds.; Springer: Cham, Switzerland, 2019; Volume 973, pp. 149–162. [Google Scholar] [CrossRef]
- McIntosh, T.; Kayes, A.S.M.; Chen, Y.P.; Ng, A.; Watters, P. Dynamic user-centric access control for detection of ransomware attacks. Comput. Secur. 2021, 111, 102461. [Google Scholar] [CrossRef]
- Ami, O.; Elovici, Y.; Hendler, D. Ransomware prevention using application authentication-based file access control. In Proceedings of the 33rd Annual ACM Symposium on Applied Computing, New York, NY, USA, 9–13 April 2018; pp. 1610–1619. [Google Scholar] [CrossRef]
- Turaev, H.; Zavarsky, P.; Swar, B. Prevention of Ransomware Execution in Enterprise Environment on Windows OS: Assessment of Application Whitelisting Solutions. In Proceedings of the 1st International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 8–10 April 2018; pp. 110–118. [Google Scholar] [CrossRef]
- Kim, D.; Lee, J. Blacklist vs. Whitelist-Based Ransomware Solutions. IEEE Consum. Electron. Mag. 2020, 9, 22–28. [Google Scholar] [CrossRef]
- Genç, Z.A.; Lenzini, G.; Ryan, P. No random, no ransom: A key to stop cryptographic ransomware. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA), Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018; Volume 10885, pp. 234–255. [Google Scholar] [CrossRef]
- Lee, S.; Kim, H.K.; Kim, K. Ransomware protection using the moving target defense perspective. Comput. Electr. Eng. 2019, 78, 288–299. [Google Scholar] [CrossRef]
- McIntosh, T.; Watters, P.; Kayes, A.; Ng, A.; Chen, Y. Enforcing situation-aware access control to build malware-resilient file systems. Future Gener. Comput. Syst. 2021, 115, 568–582. [Google Scholar] [CrossRef]
- VLCM. Sophos Intercept X: The World’s Best Endpoint Protection. 2023. Available online: https://www.vlcm.com/intercept-x (accessed on 25 October 2023).
- Microsoft. Protect Important Folders with Controlled Folder Access. 2022. Available online: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/controlled-folders?view=o365-worldwide (accessed on 25 October 2023).
- Microsoft. What’s new in Microsoft Defender for Identity. 2023. Available online: https://learn.microsoft.com/en-us/defender-for-identity/whats-new (accessed on 25 October 2023).
- Ahn, J.; Park, D.; Lee, C.; Min, D.; Lee, J.; Park, S.; Chen, Q.; Kim, Y. KEY-SSD: Access-Control Drive to Protect Files from Ransomware Attacks. arXiv 2019. [Google Scholar] [CrossRef]
- Siddiqui, A.S.; Lee, C.-C.; Saqib, F. Hardware based protection against malwares by PUF based access control mechanism. In Proceedings of the 60th IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 6–9 August 2017; pp. 1312–1315. [Google Scholar] [CrossRef]
- Akbanov, M.; Vassilakis, V.G.; Logothetis, M.D. Ransomware detection and mitigation using software-defined networking: The case of WannaCry. Comput. Electr. Eng. 2019, 76, 111–121. [Google Scholar] [CrossRef]
- McIntosh, T.; Kayes, A.S.M.; Chen, Y.P.P.; Ng, A.; Watters, P. Applying staged event-driven access control to combat ransomware. Comput. Secur. 2023, 128, 103160. [Google Scholar] [CrossRef]
- Thomas, J.; Galligher, G. Improving backup system evaluations in information security risk assessments to combat ransomware. Comput. Inf. Sci. 2018, 11, 14–25. [Google Scholar] [CrossRef]
- Min, D.; Park, D.; Ahn, J.; Walker, R.; Lee, J.; Park, S.; Kim, Y. Amoeba: An autonomous backup and recovery ssd for ransomware attack defense. IEEE Comput. Archit. Lett. 2017, 17, 245–248. [Google Scholar] [CrossRef]
- Baykara, M.; Sekin, B. A novel approach to ransomware: Designing a safe zone system. In Proceedings of the 6th International Symposium on Digital Forensic and Security (ISDFS), Antalya, Turkey, 22–25 March 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Lao, W.; Chen, Z.; Gao, B.; Wang, J.; Ta, Y.; Zhang, R. RAP: RAnsomware Protection Scheme Based on Blockchain. In Proceedings of the 2nd International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 14–16 January 2022; pp. 13–20. [Google Scholar] [CrossRef]
- Dell. Dell PowerProtect Cyber Recovery. 2022. Available online: https://www.delltechnologies.com/asset/zh-hk/products/data-protection/briefs-summaries/isolated-recovery-solution-overview.pdf (accessed on 25 October 2023).
- Tafkov, S.; Minchev, Z. Decentralized File Storage and Ransomware Protection. In Proceedings of the 12th International Conference on Business Information Security (BISEC-2021), Belgrade, Serbia, 3 December 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Golev, A.; Hristev, R.; Veselinova, M.; Kolev, K. Crypto-ransomware attacks on Linux servers: A data recovery method. Int. J. Differ. Equ. Appl. 2022, 21, 19–29. [Google Scholar] [CrossRef]
- Hutton, W. Immunizing Files Against Ransomware with Koalafied Immunity. In Intelligent Computing, Proceedings of the 2022 Computing Conference; Lecture Notes in Networks and, Systems; Arai, K., Ed.; Springer: Cham, Switzerland, 2022; Volume 508, pp. 735–741. [Google Scholar] [CrossRef]
- Han, X.; Kheir, N.; Balzarotti, D. Deception Techniques in Computer Security: A Research Perspective. ACM Comput. Surv. 2019, 51, 80. [Google Scholar] [CrossRef]
- Genç, Z.A.; Lenzini, G.; Sgandurra, D. On Deception-Based Protection Against Cryptographic Ransomware. In Detection of Intrusions and Malware, and Vulnerability Assessment. DIMVA 2019; Lecture Notes in Computer, Science; Perdisci, R., Maurice, R., Giacinto, G., Almgren, M., Eds.; Springer: Cham, Switzerland, 2019; Volume 11543. [Google Scholar] [CrossRef]
- Wang, Z.; Wu, X.; Liu, C.; Liu, Q.; Zhang, J. RansomTracer: Exploiting Cyber Deception for Ransomware Tracing. In Proceedings of the IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 21 June 2018; pp. 227–234. [Google Scholar] [CrossRef]
- Patel, A.; Tailor, J.P. A malicious activity monitoring mechanism to detect and prevent ransomware. Comput. Fraud. Secur. 2020, 2020, 14–19. [Google Scholar] [CrossRef]
- Moussaileb, R.; Bouget, B.; Palisse, A.; Le Bouder, H.; Cuppens-Boulahia, N.; Lanet, J.L. Ransomware’s Early Mitigation Mechanisms. In Proceedings of the 13th International Conference on Availability, Reliability and Security, New York, NY, USA, 27–30 August 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Mehnaz, S.; Mudgerikar, A.; Bertino, E. RWGuard: A Real-Time Detection System Against Cryptographic Ransomware. In Research in Attacks, Intrusions, and Defenses; Lecture Notes in Computer, Science; Bailey, M., Holz, T., Stamatogiannakis, M., Ioannidis, S., Eds.; Springer: Cham, Switzerland, 2018; Volume 11050, pp. 114–136. [Google Scholar] [CrossRef]
- Shaukat, S.K.; Ribeiro, V.J. RansomWall: A layered defense system against cryptographic ransomware attacks using machine learning. In Proceedings of the 10th International Conference on Communication Systems & Networks (COMSNETS), Bengaluru, India, 3–7 January 2018; pp. 356–363. [Google Scholar] [CrossRef]
- Al-Nemera, G.; Al-Otaibi, S.; Tahir, R.; Alkhatib, M. Making Honey Files Sweeter: SentryFS—A Service-Oriented Smart Ransomware Solution. arXiv 2021. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, H.; Qin, S.; Li, W.; Tu, T.; Shen, A.; Liu, W. KRProtector: Detection and Files Protection for IoT Devices on Android Without ROOT Against Ransomware Based on Decoys. IEEE Internet Things J. 2022, 9, 18251–18266. [Google Scholar] [CrossRef]
- Sheen, S.; Asmitha, K.A.; Venkatesan, S. R-Sentry: Deception based ransomware detection using file access patterns. Comput. Electr. Eng. 2022, 103, 108346. [Google Scholar] [CrossRef]
- Gómez-Hernández, J.A.; Álvarez-González, L.; García-Teodoro, P. R-Locker: Thwarting Ransomware Action through a Honeyfile-based Approach. Comput. Secur. 2018, 73, 389–398. [Google Scholar] [CrossRef]
- Gómez-Hernández, J.A.; Sánchez-Fernández, R.; García-Teodoro, P. Inhibiting crypto-ransomware on Windows platforms through a honeyfile-based approach with R-Locker. IET Inf. Secur. 2021, 16, 64–74. [Google Scholar] [CrossRef]
- Lin, Y.S.; Lee, C.F. Ransomware Detection and Prevention through Strategically Hidden Decoy File. Int. J. Netw. Secur. 2023, 25, 212–220. [Google Scholar] [CrossRef]
- Ganfure, G.O.; Wu, C.F.; Chang, Y.H.; Shih, W.K. RTrap: Trapping and Containing Ransomware With Machine Learning. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1433–1448. [Google Scholar] [CrossRef]
- Bello, A.; Maurushat, A. Technical and Behavioural Training and Awareness Solutions for Mitigating Ransomware Attacks. In Applied Informatics and Cybernetics in Intelligent Systems. CSOC 2020; Advances in Intelligent Systems and Computing; Silhavy, R., Ed.; Springer: Cham, Switzerland, 2020; Volume 1226. [Google Scholar] [CrossRef]
- Thomas, J. Individual Cyber Security: Empowering Employees to Resist Spear Phishing to Prevent Identity Theft and Ransomware Attacks. Int. J. Bus. Manag. 2018, 13, 1–14. [Google Scholar] [CrossRef]
- Ophoff, J.; Lakay, M. Mitigating the Ransomware Threat: A Protection Motivation Theory Approach. In Information Security. ISSA 2018; Communications in Computer and Information, Science; Venter, H., Loock, M., Coetzee, M., Eloff, M., Eloff, J., Eds.; Springer: Cham, Switzerland, 2019; Volume 973, pp. 163–175. [Google Scholar] [CrossRef]
- Chung, M. Why employees matter in the fight against ransomware. Comput. Fraud. Secur. 2019, 8, 8–11. [Google Scholar] [CrossRef]
- Angafor, G.N.; Yevseyeva, I.; He, Y. Bridging the Cyber Security Skills Gap: Using Tabletop Exercises to Solve the CSSG Crisis. In Serious Games. JCSG 2020; Lecture Notes in Computer Science; Ma, M., Fletcher, B., Göbel, S., Baalsrud Hauge, J., Marsh, T., Eds.; Springer: Cham, Switzerland, 2020; Volume 12434, pp. 117–131. [Google Scholar] [CrossRef]
- Hull, G.; John, H.; Arief, B. Ransomware deployment methods and analysis: Views from a predictive model and human responses. Crime Sci. 2019, 8, 2. [Google Scholar] [CrossRef]
- Maigida, A.M.; Abdulhamid, S.M.; Olalere; Ismaila. An Intelligent Crypto-Locker Ransomware Detection Technique using Support Vector Machine Classification and Grey Wolf Optimization Algorithms. i-manager’s J. Softw. Eng. 2019, 13, 15–23. [Google Scholar] [CrossRef]
- Nadir, I.; Bakhshi, T. Contemporary cybercrime: A taxonomy of ransomware threats & mitigation techniques. In Proceedings of the International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 3–4 March 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Pont, J.; Abu Oun, O.; Brierley, C.; Arief, B.; Hernández-Castro, J. A Roadmap for Improving the Impact of Anti-ransomware Research. In Secure IT Systems, NordSec; Lecture Notes in Computer Science; Askarov, A., Hansen, R., Rafnsson, W., Eds.; Springer: Cham, Switzerland, 2019; Volume 11875. [Google Scholar] [CrossRef]
- Herrera Silva, J.A.; Barona López, L.I.; Valdivieso Caraguay, A.L.; Hernández-Álvarez, M.A. A Survey on Situational Awareness of Ransomware Attacks, Detection and Prevention Parameters. Remote Sens. 2019, 10, 1168. [Google Scholar] [CrossRef]
- Baek, S.; Jung, Y.; Mohaisen, A.; Lee, S.; Nyang, D. SSD-insider: Internal defense of solid-state drive against ransomware with perfect data recovery. In Proceedings of the IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–5 July 2018; pp. 875–884. [Google Scholar] [CrossRef]
- Natanzon, A.; Derbeko, P.; Stern, U.; Bakshi, M.; Manusov, Y. Ransomware detection using I/O patterns. US Patent 10,078,459, 2018. [Google Scholar]
- Bottazzi, G.; Italiano, G.; Spera, D. Preventing Ransomware Attacks Through File System Filter Drivers. In Proceedings of the Second Italian Conference on Cyber Security, Milan, Italy, 6–9 February 2018; pp. 1–10. [Google Scholar]
- Constantinescu, C.; Seshadri, S. Sentinel: Ransomware detection in file storage. In Proceedings of the 14th ACM International Conference on Systems and Storage (SYSTOR), New York, NY, USA, 14–16 June 2021; Volume 1, p. 28. [Google Scholar] [CrossRef]
- Ahmed, M.E.; Kim, H.; Camtepe, S.; Nepa, S. Peeler: Profiling Kernel-Level Events to Detect Ransomware. In Computer Security—ESORICS 2021; Lecture Notes in Computer Science; Bertino, E., Shulman, H., Waidner, M., Eds.; Springer: Cham, Switzerland, 2021; Volume 12972, pp. 240–260. [Google Scholar] [CrossRef]
- May, M.J.; Laron, E. Combating Ransomware using Content Analysis and Complex File Events. In Proceedings of the 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Herrera Silva, J.A.; Hernández-Alvarez, M. Large scale ransomware detection by cognitive security. In Proceedings of the IEEE Second Ecuador Technical Chapters Meeting (ETCM), Salinas, Ecuador, 16–20 October 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Bahrani, A.; Bidgly, A.J. Ransomware detection using process mining and classification algorithm. In Proceedings of the 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Mashhad, Iran, 28–29 August 2019; pp. 73–77. [Google Scholar] [CrossRef]
- Roy, K.C.; Chen, Q. DeepRan: Attention-based BiLSTM and CRF for Ransomware Early Detection and Classification. Inf. Syst. Front. 2021, 23, 299–315. [Google Scholar] [CrossRef]
- Arfeen, A.; Khan, M.A.; Zafar, O.; Ahsan, U. Process based volatile memory forensics for ransomware detection. Concurr. Comput. Pr. Exper. 2022, 34, e6672. [Google Scholar] [CrossRef]
- Moreira, C.; Sales, C., Jr.; Moreira, D. Understanding Ransomware Actions Through Behavioral Feature Analysis. JCIS 2022, 37, 61–76. [Google Scholar] [CrossRef]
- Ahmed, Y.A.; Koçer, B.; Al-rimy, B.A.S. Automated Analysis Approach for the Detection of High Survivable Ransomware. KSII Trans. Internet Inf. Syst. 2020, 14, 2236–2257. [Google Scholar] [CrossRef]
- Ahmed, Y.A.; Koçer, B.; Huda, S.; Al-rimy, B.A.S.; Hassan, M.M. System call refinement-based enhanced Minimum Redundancy Maximum Relevance method for ransomware early detection. J. Netw. Comput. Appl. 2020, 167, 102753. [Google Scholar] [CrossRef]
- Poudyal, S.; Dasgupta, D. Analysis of Crypto-Ransomware Using ML-Based Multi-Level Profiling. IEEE Access 2021, 9, 122532–122547. [Google Scholar] [CrossRef]
- Sharma, S.; Kumar, R.; Krishna, C.R. A survey on analysis and detection of Android ransomware. Concurr. Comput. Pr. Exper. 2021, 33, e6272. [Google Scholar] [CrossRef]
- Saleh, M.A. A Proactive Approach for Detecting Ransomware based on Hidden Markov Model (HMM). Int. J. Intell. Comput. Res. (IJICR) 2019, 10, 1004–1013. [Google Scholar] [CrossRef]
- Zhang, B.; Xiao, W.; Xiao, X.; Sangaiah, A.K.; Zhang, W.; Zhang, J. Ransomware classification using patch-based CNN and self-attention network on embedded N-grams of opcodes. Future Gener. Comput. Syst. 2020, 110, 708–720. [Google Scholar] [CrossRef]
- Zhang, H.; Xiao, X.; Mercaldo, F.; Ni, S.; Martinelli, F.; Sangaiah, A.K. Classification of ransomware families with machine learning based on N-gram of opcodes. Future Gener. Comput. Syst. 2019, 90, 211–221. [Google Scholar] [CrossRef]
- Sharma, S.; Singh, S. Texture-Based Automated Classification of Ransomware. J. Inst. Eng. India Ser. B 2021, 102, 131–142. [Google Scholar] [CrossRef]
- Chen, Q.; Islam, S.R.; Haswell, H.; Bridges, R.A. Automated Ransomware Behavior Analysis: Pattern Extraction and Early Detection. In Science of Cyber Security. SciSec 2019; Lecture Notes in Computer Science; Liu, F., Xu, J., Xu, S., Yung, M., Eds.; Springer: Cham, Switzerland, 2019; Volume 11933, pp. 1–16. [Google Scholar] [CrossRef]
- Ayub, M.A.; Sira, A. Similarity Analysis of Ransomware based on Portable Executable (PE) File Metadata. In Proceedings of the IEEE Symposium Series on Computational Intelligence (SSCI), Orlando, FL, USA, 5–7 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Ganta, V.G.; Harish, G.; Kumar, V.; Rao, G.R. Ransomware Detection in Executable Files Using Machine Learning. In Proceedings of the International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT), Bangalore, India, 12–13 November 2020; pp. 282–286. [Google Scholar] [CrossRef]
- Ramesh, G.; Menen, A. Automated dynamic approach for detecting ransomware using finite-state machine. Decis. Support Syst. 2020, 138, 113400. [Google Scholar] [CrossRef]
- Xia, T.; Sun, Y.; Zhu, S.; Rasheed, Z.; Hassan-Shafique, K. A Network-Assisted Approach for Ransomware Detection. arXiv 2020, arXiv:2008.12428. [Google Scholar]
- Goyal, P.S.; Kakkar, A.; Vinod, G.; Joseph, G. Crypto-Ransomware Detection Using Behavioural Analysis. In Reliability, Safety and Hazard Assessment for Risk-Based Technologies; Lecture Notes in Mechanical Engineering; Varde, P., Prakash, R., Vinod, G., Eds.; Springer: Singapore, 2020; pp. 239–251. [Google Scholar] [CrossRef]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R. Know Abnormal, Find Evil: Frequent Pattern Mining for Ransomware Threat Hunting and Intelligence. IEEE Trans. Emerg. Top. Comput. 2018, 8, 341–351. [Google Scholar] [CrossRef]
- Salehi, S.; Shahriari, H.; Ahmadian, M.M.; Tazik, L. A Novel Approach for Detecting DGA-based Ransomwares. In Proceedings of the 15th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Tehran, Iran, 28–29 August 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Cabaj, K.; Gregorczyk, M.; Mazurczyk, W. Software-defined networking-based crypto ransomware detection using HTTP traffic characteristics. Comput. Electr. Eng. 2018, 66, 353–368. [Google Scholar] [CrossRef]
- Monge, M.A.S.; Vidal, J.M.; García Villalba, L.J. A novel Self-Organizing Network solution towards Crypto-ransomware Mitigation. In Proceedings of the 13th International Conference on Availability, Reliability and Security (ARES), New York, NY, USA, 27–30 August 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Morato, D.; Berrueta, E.; Magaña, E.; Izal, M. Ransomware early detection by the analysis of file sharing traffic. J. Netw. Comput. Appl. 2018, 124, 14–32. [Google Scholar] [CrossRef]
- Almousa, M.; Osawere, J.; Anwar, M. Identification of Ransomware families by Analyzing Network Traffic Using Machine Learning Techniques. In Proceedings of the Third International Conference on Transdisciplinary AI (TransAI), Laguna Hills, CA, USA, 20–22 September 2021; pp. 19–24. [Google Scholar] [CrossRef]
- Alhawi, O.M.K.; Baldwin, J.; Dehghantanha, A. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection. In Cyber Threat Intelligence; Advances in Information Security; Dehghantanha, A., Conti, M., Dargahi, T., Eds.; Springer: Cham, Switzerland, 2018; Volume 70. [Google Scholar] [CrossRef]
- Modi, J.; Traore, I.; Ghaleb, A.; Ganame, K.; Ahmed, S. Detecting Ransomware in Encrypted Web Traffic. In Foundations and Practice of Security FPS 2019; Lecture Notes in Computer Science; Benzekri, A., Barbeau, M., Gong, G., Laborde, R., Garcia-Alfaro, J., Eds.; Springer: Cham, Switzerland, 2020; Volume 12056. [Google Scholar] [CrossRef]
- Chaithanya, B.N.; Brahmananda, S.H. Detecting Ransomware Attacks Distribution Through Phishing URLs Using Machine Learning. In Computer Networks and Inventive Communication Technologies; Lecture Notes on Data Engineering and Communications Technologies; Smys, S., Bestak, R., Palanisamy, R., Kotuliak, I., Eds.; Springer: Singapore, 2022; Volume 75, pp. 821–832. [Google Scholar] [CrossRef]
- Iffländer, L.; Dmitrienko, A.; Hagen, C.; Jobst, M.; Kounev, S. Hands Off my Database: Ransomware Detection in Databases through Dynamic Analysis of Query Sequences. arXiv 2019, arXiv:1907.06775. [Google Scholar]
- Alzahrani, A.; Alshehri, A.; Alshahrani, H.; Alharthi, R.; Fu, H.; Liu, A.; Zhu, Y. RanDroid: Structural Similarity Approach for Detecting Ransomware Applications in Android Platform. In Proceedings of the IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; pp. 0892–0897. [Google Scholar] [CrossRef]
- García Villalba, L.J.; Orozco, A.L.S.; López Vivar, A.; Vega, E.A.A.; Kim, T.H. Ransomware Automatic Data Acquisition Tool. IEEE Access 2018, 6, 55043–55052. [Google Scholar] [CrossRef]
- Lemmou, Y.; Lanet, J.L.; Souidi, E.M. In-Depth Analysis of Ransom Note Files. Computers 2021, 10, 145. [Google Scholar] [CrossRef]
- Reidys, B.; Liu, P.; Huang, J. RSSD: Defend against ransomware with hardware-isolated network-storage codesign and post-attack analysis. In Proceedings of the 27th ACM International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS), New York, NY, USA, 27 April–1 May 2022; pp. 726–739. [Google Scholar] [CrossRef]
- Ala, M.; Sinh, S.; Bhattachary, S.; Dutta, S.; Mukhopadhyay, D.; Chattopadhyay, A. RAPPER: Ransomware prevention via performance counters. arXiv 2018. [Google Scholar] [CrossRef]
- Pundir, N.; Tehranipoor, M.; Fahim, F. RanStop: A Hardware-assisted Runtime Crypto-Ransomware Detection Technique. arXiv 2020. [Google Scholar] [CrossRef]
- Aurangzeb, S.; Rais, R.N.B.; Aleem, M.; Islam, M.A.; Iqbal, M.A. On the classification of Microsoft-Windows ransomware using hardware profile. PeerJ Comput. Sci. 2021, 7, e361. [Google Scholar] [CrossRef]
- Anand, P.M.; Charan, P.V.S.; Shukla, S.K. Early Detection of Ransomware Activity based on Hardware Performance Counters. In Proceedings of the 2023 Australasian Computer Science Week January, New York, NY, USA, 30 January–3 February 2023; pp. 10–17. [Google Scholar] [CrossRef]
- Sokolov, K. Ransomware Activity and Blockchain Congestion. J. Financ. Econ. 2018, 141, 771–782. [Google Scholar] [CrossRef]
- Balachandar, A.; Alsowdh, A.; Arumugam, K. Design and Development of Future Estimate in Confronting Ransomware. J. Phys. Conf. Ser. 2021, 1717, 012063. [Google Scholar] [CrossRef]
- Joshi, Y.S.; Mahajan, H.; Joshi, S.N.; Gupta, K.P.; Agarkar, A.A. Signature-less ransomware detection and mitigation. J. Comput. Virol. Hack Tech. 2021, 17, 299–306. [Google Scholar] [CrossRef]
- Medhat, M.; Gaber, S.; Abdelbaki, N. A New Static-Based Framework for Ransomware Detection. In Proceedings of the IEEE 16th Intl Conf on Dependable, Autonomic and Secure Computing, 16th Intl Conf on Pervasive Intelligence and Computing, 4th Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress(DASC/PiCom/ DataCom/CyberSciTech), Athens, Greece, 25–28 October 2018; pp. 710–715. [Google Scholar] [CrossRef]
- Yara. Yara’s Documentation. Available online: https://yara.readthedocs.io/en/stable/ (accessed on 25 October 2023).
- Keyes, D.S.; Li, B.; Kaur, G.; Lashkari, A.H.; Gagnon, F.; Massicotte, F. EntropLyzer: Android Malware Classification and Characterization Using Entropy Analysis of Dynamic Characteristics. In Proceedings of the Reconciling Data Analytics, Automation, Privacy, and Security: A Big Data Challenge (RDAAPS), Hamilton, ON, Canada, 17–19 May 2021; pp. 1–12. [Google Scholar] [CrossRef]
- Zhu, J.; Jang-Jaccard, J.; Singh, A.; Welch, I.; AI-Sahaf, H.; Camtepe, S. A Few-Shot Meta-Learning based Siamese Neural Network using Entropy Features for Ransomware Classification. arXiv 2021, arXiv:2112.00668. [Google Scholar] [CrossRef]
- Simon, R.D.; Macfarlane, R.; Buchanan, W.J. Differential area analysis for ransomware attack detection within mixed file datasets. Comput. Secur. 2021, 108, 1–14. [Google Scholar] [CrossRef]
- Hsu, C.M.; Yang, C.C.; Cheng, H.H.; Setiasabda, P.E.; Leu, J.S. Enhancing File Entropy Analysis to Improve Machine Learning Detection Rate of Ransomware. IEEE Access 2021, 9, 138345–138351. [Google Scholar] [CrossRef]
- McIntosh, T.; Jang-Jaccard, J.; Watters, P.; Susnjak, T. The Inadequacy of Entropy-Based Ransomware Detection. In Neural Information Processing. ICONIP 2019; Communications in Computer and Information Science; Gedeon, T., Wong, K., Lee, M., Eds.; Springer: Cham, Switzerland, 2019; Volume 1143. [Google Scholar] [CrossRef]
- Boutsikas, J.; Eren, M.E.; Varga, C.; Raff, E.; Matuszek, C.; Nicholas, C. Evading malware classifiers via monte carlo mutant feature discovery. arXiv 2021, arXiv:2106.07860. [Google Scholar]
- Lee, J.; Lee, K. A Method for Neutralizing Entropy Measurement-Based Ransomware Detection Technologies Using Encoding Algorithms. Entropy 2022, 24, 239. [Google Scholar] [CrossRef] [PubMed]
- Jiao, J.; Zhao, H.; Liu, Y. Analysis and Detection of Android Ransomware for Custom Encryption. In Proceedings of the IEEE 4th International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 13–15 August 2021; pp. 220–225. [Google Scholar] [CrossRef]
- Kim, G.Y.; Paik, J.Y.; Kim, Y.; Cho, E.S. Byte Frequency Based Indicators for Crypto-ransomware Detection from Empirical Analysis. J. Comput. Sci. Technol. 2022, 37, 423–442. [Google Scholar] [CrossRef]
- Kakavand, M.; Arulsamy, L.; Mustapha, A.; Dabbagh, M. A Novel Crypto-Ransomware Family Classification Based on Horizontal Feature Simplification. In Advances in Computer, Communication and Computational Sciences; Advances in Intelligent Systems and Computing; Bhatia, S.K., Tiwari, S., Ruidan, S., Trivedi, M.C., Mishra, K.K., Eds.; 2021; Volume 1158, pp. 3–14. [Google Scholar] [CrossRef]
- Rani, N.; Dhavale, S.V.; Singh, A.; Mehra, A. A Survey on Machine Learning-Based Ransomware Detection. In Seventh International Conference on Mathematics and Computing; Advances in Intelligent Systems and Computing; Giri, D., Raymond Choo, K.K., Ponnusamy, S., Meng, W., Akleylek, S., Prasad Maity, S., Eds.; Springer: Singapore, 2022; Volume 1412, pp. 171–186. [Google Scholar] [CrossRef]
- Fernando, D.W.; Komninos, N.; Chen, T. A Study on the Evolution of Ransomware Detection Using Machine Learning and Deep Learning Techniques. IoT 2020, 1, 551–604. [Google Scholar] [CrossRef]
- Hwang, J.; Kim, J.; Lee, S.; Kim, K. Two-Stage Ransomware Detection Using Dynamic Analysis and Machine Learning Techniques. Wireless Pers. Commun. 2020, 112, 2597–2609. [Google Scholar] [CrossRef]
- Egunjobi, S.; Parkinson, S.; Crampton, A. Classifying Ransomware Using Machine Learning Algorithms. In Intelligent Data Engineering and Automated Learning—IDEAL 2019; Yin, H., Camacho, D., Tino, P., Tallón-Ballesteros, A., Menezes, R., Allmendinger, R., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11872. [Google Scholar] [CrossRef]
- Al-rimy, B.; Maarof, M.; Shaid, S. Crypto-ransomware early detection model using movel incremental bagging with enhanced semi-random subspace selection. Future Gener. Comput. Syst. 2019, 101, 476–491. [Google Scholar] [CrossRef]
- Fernando, D.W.; Komninos, N. FeSA: Feature selection architecture for ransomware detection under concept drift. Comput. Secur. 2022, 116, 102659. [Google Scholar] [CrossRef]
- Molina, R.M.A.; Torabi, S.; Sarieddine, K.; Bou-Harb, E.; Bouguila, N.; Assi, C. On Ransomware Family Attribution Using Pre-Attack Paranoia Activities. IEEE Trans. Netw. Serv. Manag. 2021, 19, 19–36. [Google Scholar] [CrossRef]
- Arabo, A.; Dijoux, R.; Poulain, T.; Chevalier, G. Detecting Ransomware Using Process Behavior Analysis. Procedia Comput. Sci. 2020, 168, 289–296. [Google Scholar] [CrossRef]
- Zahoora, U.; Rajarajan, M.; Pan, Z.; Khan, A. Zero-day Ransomware Attack Detection using Deep Contractive Autoencoder and Voting based Ensemble Classifier. Appl. Intell. 2022, 52, 13941–13960. [Google Scholar] [CrossRef]
- Kok, S.; Abdullah, A.; Jhanjhi, N. Early detection of crypto-ransomware using pre-encryption detection algorithm. J. King Saud Univ. -Comput. Inf. Sci. 2020, 34, 1984–1999. [Google Scholar] [CrossRef]
- Tasnim, N.; Sarker, I.H. Ransomware Family Classification With Ensemble Model Based On Behavior Analysis. In Machine Intelligence and Data Science Applications. Lecture Notes on Data Engineering and Communications Technologies; Skala, V., Singh, T.P., Choudhury, T., Tomar, R., Abul Bashar, M., Eds.; Springer: Singapore, 2022; Volume 132. [Google Scholar] [CrossRef]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R.; Choo, K.K.R.; Newton, D.E. DRTHIS: Deep ransomware threat hunting and intelligence system at the fog layer. Future Gener. Comput. Syst. 2019, 90, 94–104. [Google Scholar] [CrossRef]
- Khammas, B. Ransomware detection using random forest technique. ICT Express 2020, 6, 325–331. [Google Scholar] [CrossRef]
- Khan, F.; Ncube, C.; Ramasamy, L.K.; Kadry, S.; Nam, Y. A digital DNA sequencing engine for ransomware detection using machine learning. IEEE Access 2020, 8, 119710–119719. [Google Scholar] [CrossRef]
- Lee, K.; Lee, S.-Y.; Yim, K. Machine Learning Based File Entropy Analysis for Ransomware Detection in Backup Systems. IEEE Access 2019, 7, 110205–110215. [Google Scholar] [CrossRef]
- Takeuchi, Y.; Sakai, K.; Fukumoto, S. Detecting ransomware using support vector machines. In Proceedings of the 47th International Conference on Parallel Processing Companion, New York, NY, USA, 13–16 August 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Walker, A.; Sengupta, S. Insights into malware detection via behavioral frequency analysis using machine learning. In Proceedings of the IEEE Military Communications Conference (MILCOM), Norfolk, VA, USA, 12–14 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Al-Rimy, B.A.S.; Maarof, M.A.; Alazab, M.; Alsolami, F.; Shaid, S.Z.M.; Ghaleb, F.A.; Al-Hadhrami, T.; Ali, A.M. A Pseudo Feedback-Based Annotated TF-IDF Technique for Dynamic Crypto-Ransomware Pre-Encryption Boundary Delineation and Features Extraction. IEEE Access 2020, 8, 140586–140598. [Google Scholar] [CrossRef]
- Qin, B.; Wang, Y.; Ma, C. API Call Based Ransomware Dynamic Detection Approach Using TextCNN. In Proceedings of the International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Fuzhou, China, 12–14 June 2020; pp. 162–166. [Google Scholar] [CrossRef]
- Ayub, M.A.; Continella, A.; Siraj, A. An I/O Request Packet (IRP) Driven Effective Ransomware Detection Scheme Using Artificial Neural Network. In Proceedings of the IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI 2020), Las Vegas, NV, USA, 11–13 August 2020; pp. 319–324. [Google Scholar] [CrossRef]
- Bae, S.; Lee, G.; Im, E. Ransomware detection using machine learning algorithms. Concurr. Comput. Pract. Exp. 2020, 32, e5422. [Google Scholar] [CrossRef]
- Javaheri, D.; Hosseinzadeh, M.; Rahmani, A.M. Detection and Elimination of Spyware and Ransomware by Intercepting Kernel-Level System Routines. IEEE Access 2018, 6, 78321–78332. [Google Scholar] [CrossRef]
- Cohen, A.; Nissim, N. Trusted detection of ransomware in a private cloud using machine learning methods leveraging meta-features from volatile memory. Expert Syst. Appl. 2018, 102, 158–178. [Google Scholar] [CrossRef]
- Almashhadani, A.O.; Kaiiali, M.; Sezer, S.; O’Kane, P. A multi-classifier network-based crypto ransomware detection system: A case study of Locky ransomware. IEEE Access 2019, 7, 47053–47067. [Google Scholar] [CrossRef]
- Azmoodeh, A.; Dehghantanha, A.; Conti, M.; Choo, K.K.R. Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient. Intell. Human Comput. 2018, 9, 1141–1152. [Google Scholar] [CrossRef]
- Cusack, G.; Michel, O.; Keller, E. Machine Learning-Based Detection of Ransomware Using SDN. In Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization (SDN-NFV Sec’18), Tempe, AZ, USA, 19–21 March 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Baldwin, J.; Dehghantanha, A. Leveraging Support Vector Machine for Opcode Density Based Detection of Crypto-Ransomware. In Cyber Threat Intelligence; Advances in Information Security; Dehghantanha, A., Conti, M., Dargahi, T., Eds.; Springer: Cham, Switzerland, 2018; Volume 70. [Google Scholar] [CrossRef]
- Manavi, F.; Hamzeh, A. A New Method for Ransomware Detection Based on PE Header Using Convolutional Neural Networks. In Proceedings of the 17th International ISC Conference on Information Security and Cryptology (ISCISC), Tehran, Iran, 9–10 September 2020; pp. 82–87. [Google Scholar] [CrossRef]
- Poudyal, S.; Subedi, K.P.; Dasgupta, D. A Framework for Analyzing Ransomware using Machine Learning. In Proceedings of the IEEE Symposium Series on Computational Intelligence (SSCI), Bangalore, India, 18–21 November 2018; pp. 1692–1699. [Google Scholar] [CrossRef]
- Poudyal, S.; Dasgupta, D.; Akhtar, Z.; Gupta, K. A multi-level ransomware detection framework using natural language processing and machine learning. In Proceedings of the 14th International Conference on Malicious and Unwanted Software—MALCON, Nantucket, MA, USA, 11–14 October 2019. [Google Scholar]
- Fernández Maimó, L.; Huertas Celdrán, A.; Perales Gómez, A.L.; García Clemente, F.J.; Weimer, J.; Lee, I. Intelligent and Dynamic Ransomware Spread Detection and Mitigation in Integrated Clinical Environments. Sensors 2019, 19, 1114. [Google Scholar] [CrossRef] [PubMed]
- Sanvito, D.; Siracusano, G.; González, R.; Bifulco, R. MUSTARD - Adaptive Behavioral Analysis for Ransomware Detection. In Proceedings of the ACM SIGSAC Conference on Computer and Communications (CCS), Poster, New York, NY, USA, 7 November 2022. [Google Scholar] [CrossRef]
- Sendner, C.; Iffländer, L.; Schindler, S.; Jobst, M.; Dmitrienko, A.; Kounev, S. Ransomware Detection in Databases through Dynamic Analysis of Query Sequences. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Austin, TX, USA, 3–5 October 2022. [Google Scholar] [CrossRef]
- Li, Z.; González Ríos, A.L.; Trajkovic, L. Machine Learning for Detecting the WestRock Ransomware Attack using BGP Routing Records. IEEE Commun. Mag. 2022, 61, 21–26. [Google Scholar] [CrossRef]
- Hossain, M.S.; Hasan, N.; Samad, M.A.; Hossain, M.S.; Karmoker, J.; Ahmed, F.; Fuad, K.F.M.N.; Choi, K. Android Ransomware Detection From Traffic Analysis Using Metaheuristic Feature Selection. IEEE Access 2022, 10, 128754–128763. [Google Scholar] [CrossRef]
- Karbab, E.B.; Debbabi, M.; Derhab, A. SwiftR: Cross-Platform Ransomware Fingerprinting using Hierarchical Neural Networks on Hybrid Features. Expert Syst. Appl. 2023, 225, 120017. [Google Scholar] [CrossRef]
- Phuangtong, T.; Jaroonchaipipat, N.; Thanundonsuk, N.; Sakda, P.; Fugkeaw, S. RANDES: A Ransomware Detection System based on Machine Learning. In Proceedings of the 2023 15th International Conference on Knowledge and Smart Technology (KST), Phuket, Thailand, 21–24 February 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Coglio, F.; Lekssays, A.; Carminati, B.; Ferrari, E. Early-Stage Ransomware Detection Based on Pre-attack Internal API Calls. In Advanced Information Networking and Applications. AINA 2023; Lecture Notes in Networks and Systems; Barolli, L., Ed.; Springer: Cham, Switzerland, 2023; Volume 654. [Google Scholar] [CrossRef]
- John, T.C.; Abbasi, M.S.; Al-Sahaf, H.; Welch, I.; Jang-Jaccard, J. Evolving malice scoring models for ransomware detection: An automated approach by utilising genetic programming and cooperative coevolution. Comput. Secur. 2023, 129, 103215. [Google Scholar] [CrossRef]
- NIST. Contingency Planning Guide for Federal Information Systems. Available online: https://csrc.nist.gov/publications/detail/sp/800-34/rev-1/final (accessed on 25 October 2023).
- ISO 22301:2019; Security and Resilience—Business Continuity Management Systems—Requirements. ISO: Geneva, Switzerland, 2019. Available online: https://www.iso.org/standard/75106.html (accessed on 25 October 2023).
- Department of the Treasury. Advisory on Potential Sanction Risk for Facilitating Ransomware Payments. 2020. Available online: https://home.treasury.gov/system/files/126/ofac_ransomware_advisory_10012020_1.pdf (accessed on 30 October 2022).
- Ahnert, T.; Brolley, M.; Cimon, D.A.; Riordan, R. Cyber Security and Ransomware in Financial Markets. SSRN 2022. [Google Scholar] [CrossRef]
- Mierzwa, S.J.; Drylie, J.J.; Ho, C.; Bogdan, D.; Watson, K. Ransomware Incident Preparations With Ethical Considerations and Command System Framework Proposal. J. Leadership, Account. Ethics 2022, 19. [Google Scholar] [CrossRef]
- Sophos. Paying Ransom Doubles the Cost of Ransomware Attack, According to Sophos. 2020. Available online: https://www.sophos.com/en-us/press-office/press-releases/2020/05/paying-the-ransom-doubles-cost-of-recovering-from-a-ransomware-attack-according-to-sophos (accessed on 25 October 2023).
- Chen, P.H.; Bodak, R.; Gandhi, N.S. Ransomware Recovery and Imaging Operations: Lessons Learned and Planning Considerations. J. Digit Imaging 2021, 34, 731–740. [Google Scholar] [CrossRef]
- Crystaldiskmark. Available online: https://crystalmark.info/en/software/crystaldiskmark (accessed on 25 October 2023).
- Geekbench5. Available online: https://www.geekbench.com (accessed on 25 October 2023).
- PCMark10. Available online: https://benchmarks.ul.com/pcmark10 (accessed on 25 October 2023).
- Yaseen, Q.M. The Effect of the Ransomware Dataset Age on the Detection Accuracy of Machine Learning Models. Information 2023, 14, 193. [Google Scholar] [CrossRef]
- Gupta, A.; Prakash, A.; Scaife, N. Prognosis Negative: Evaluating Real-Time Behavioral Ransomware Detectors. In Proceedings of the IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–10 September 2021; pp. 353–368. [Google Scholar] [CrossRef]
- Berrueta, E.; Morato, D.; Magaña, E.; Izal, M. Open Repository for the Evaluation of Ransomware Detection Tools. IEEE Access 2020, 8, 65658–65669. [Google Scholar] [CrossRef]
- ISOT Research Lab. Ransomware Dataset. 2020. Available online: https://www.uvic.ca/ecs/ece/isot/datasets/botnet-ransomware/index.php (accessed on 25 October 2023).
- Resilient Information Systems Security. Ransomware Dataset. Available online: https://rissgroup.org/category/contributions/ (accessed on 25 October 2023).
- Rege, A. Critical Infrastructure Ransomware Incident Dataset. Version 11.8. Temple University. 2022. Available online: https://sites.temple.edu/care/cira/ (accessed on 30 October 2022).
- Rege, A.; Bleiman, R. A Free and Community-Driven Critical Infrastructure Ransomware Dataset. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media, Wales, UK, 20–21 June 2022; Springer: Singapore, 2023. [Google Scholar] [CrossRef]
- CiberSecurity-Insiders. 2022 Ransomware & Malware Report [BitGlass]. Report. Available online: https://www.cybersecurity-insiders.com/portfolio/2022-ransomeware-malware-report-bitglass/ (accessed on 25 October 2023).
- Han, J.; Lin, Z.; Porter, D.E. On the Effectiveness of Behavior-Based Ransomware Detection. In Security and Privacy in Communication Networks. SecureComm; Park, N., Sun, K., Foresti, S., Butler, K., Saxena, N., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer: Cham, Switzerland, 2020; Volume 336, pp. 120–140. [Google Scholar] [CrossRef]
- Loman, M. LockFile Ransomware’s Box of Tricks: Intermittent Encryption and Evasion. Sophos News, August 2021. Available online: https://news.sophos.com/en-us/2021/08/27/lockfile-ransomwares-box-of-tricks-intermittent-encryption-and-evasion/ (accessed on 25 October 2023).
- Palmer, D. Ransomware Warning: Now Attacks are Stealing Data as Well as Encrypting It. ZDNET Report. Available online: https://www.zdnet.com/article/ransomware-warning-now-attacks-are-stealing-data-as-well-as-encrypting-it/ (accessed on 25 October 2023).
- Purnama, B.; Stiawan, D.; Hanapi, D.; Idris, M.Y.; Afifah, N.; Sharipuddin, S.; Budiarto, R. Time Efficiency on Computational Performance of PCA, FA and TSVD on Ransomware Detection. Indones. J. Electr. Eng. Inform. (IJEEI) 2022, 10, 102–111. [Google Scholar] [CrossRef]
- Masum, M.; Faruk, M.J.H.; Shahriar, H.; Qian, K.; Lo, D.; Adnan, M.I. Ransomware Classification and Detection With Machine Learning Algorithms. In Proceedings of the IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; pp. 0316–0322. [Google Scholar] [CrossRef]
- Urooj, U.; Al-rimy, B.A.S.; Zainal, A.; Ghaleb, F.A.; Rassam, M.A. Ransomware Detection Using the Dynamic Analysis and Machine Learning: A Survey and Research Directions. Appl. Sci. 2022, 12, 172. [Google Scholar] [CrossRef]
- Bello, I.; Chiroma, H.; Abdullahi, U.A.; Gital, A.Y.; Jauro, F.; Khan, A.; Okesola, J.O.; Abdulhamid, S.M. Detecting ransomware attacks using intelligent algorithms: Recent development and next direction from deep learning and big data perspectives. J. Ambient. Intell. Human Comput. 2021, 12, 8699–8717. [Google Scholar] [CrossRef]
- Kok, S.H.; Zbdullah, A.; Jhanjhi, N.Z.; Supramaniam, M. Ransomware, Threat and Detection Techniques: A Review. Int. J. Comput. Sci. Netw. Secur. (IJCSNS) 2019, 19, 136–146. [Google Scholar]
- Camacho, J.; Therón, R.; García-Giménez, J.M.; Maciá-Fernández, G.; García-Teodoro, P. Group-Wise Principal Component Analysis for Exploratory Intrusion Detection. IEEE Access 2019, 7, 31–37. [Google Scholar] [CrossRef]
- De Gaspari, F.; Hitaj, D.; Pagnotta, G.; De Carli, L.; Mancini, L.V. Evading behavioral classifiers: A comprehensive analysis on evading ransomware detection techniques. Neural Comput. Appl. 2022, 34, 12077–12096. [Google Scholar] [CrossRef]
- Malik, S.; Shanmugam, B.; Kannorpatti, K.; Azam, S. Critical Feature Selection for Machine Learning Approaches to Detect Ransomware. Int. J. Comput. Digit. Syst. 2022, 11, 1167–1176. [Google Scholar] [CrossRef]
- Chainalysis. As Ransomware Payments Continue to Grow, So Too Does RAnsomware’s Role in Geopolitical Conflict. February 2022. Available online: https://blog.chainalysis.com/reports/2022-crypto-crime-report-preview-ransomware/ (accessed on 25 October 2023).
- Wang, K.; Pang, J.; Chen, D.; Zhao, Y.; Huang, D.; Chen, C.; Han, W. A Large-scale Empirical Analysis of Ransomware Activities in Bitcoin. ACM Trans. Web 2022, 16, 1–29. [Google Scholar] [CrossRef]
- Robles-Carrillo, M.; García-Teodoro, P. Ransomware: An Interdisciplinary Technical and Legal Approach. Secur. Commun. Netw. 2022, 2022, 2806605. [Google Scholar] [CrossRef]
- Blessing, J.; Drean, J.; Radway, S. Survey and analysis of U.S. policies to address ransomware. MIT Sci. Policy Rev. 2022, 3, 38–46. [Google Scholar] [CrossRef]
- Hacquebord, F.; Hilt, S.; Sancho, D. The Near and Far Future of Ransomware Business Models. Trend Micro Research. 2022. Available online: https://www.trendmicro.com/vinfo/es/security/news/cybercrime-and-digital-threats/the-future-of-ransomware (accessed on 25 October 2023).
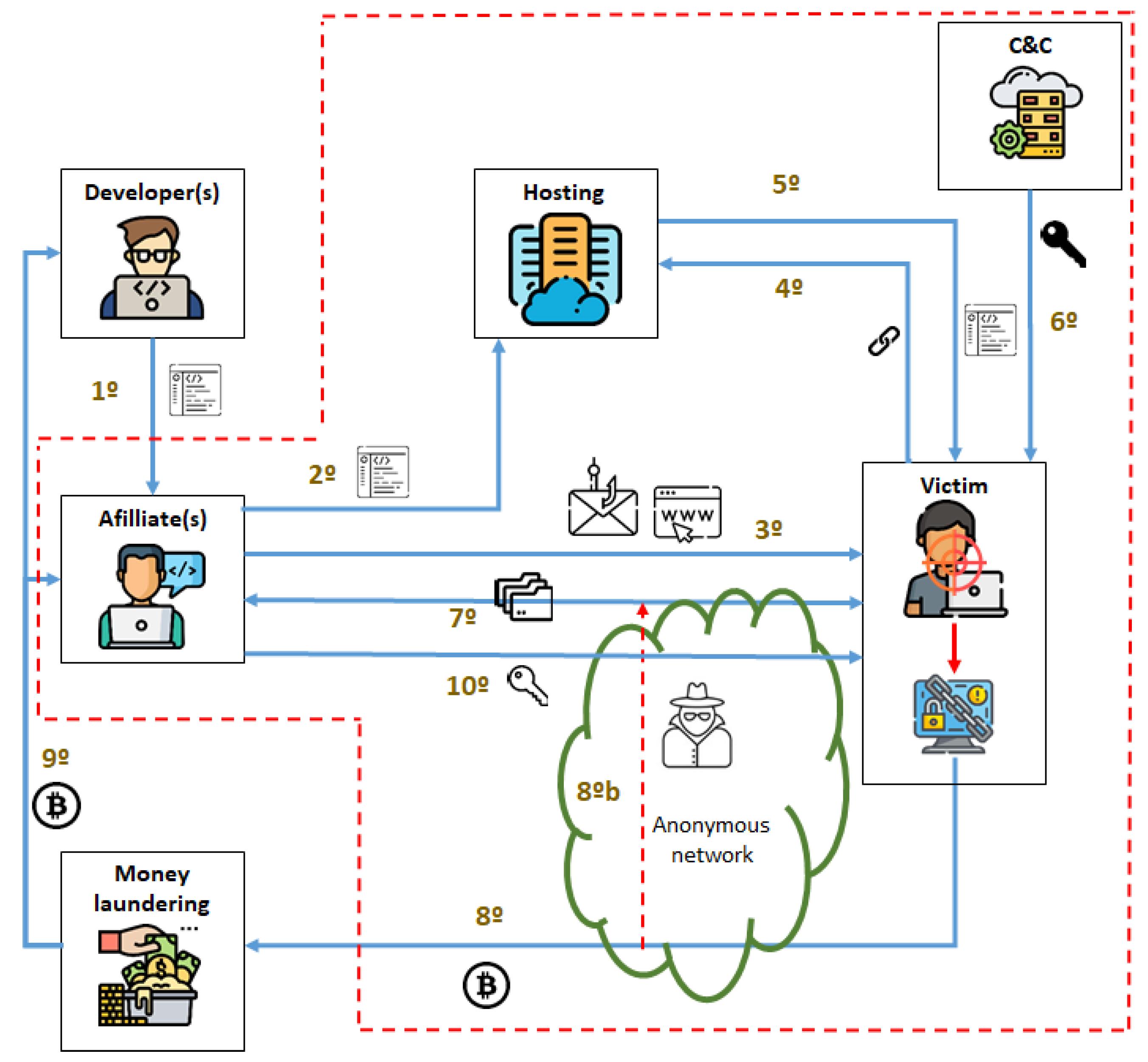


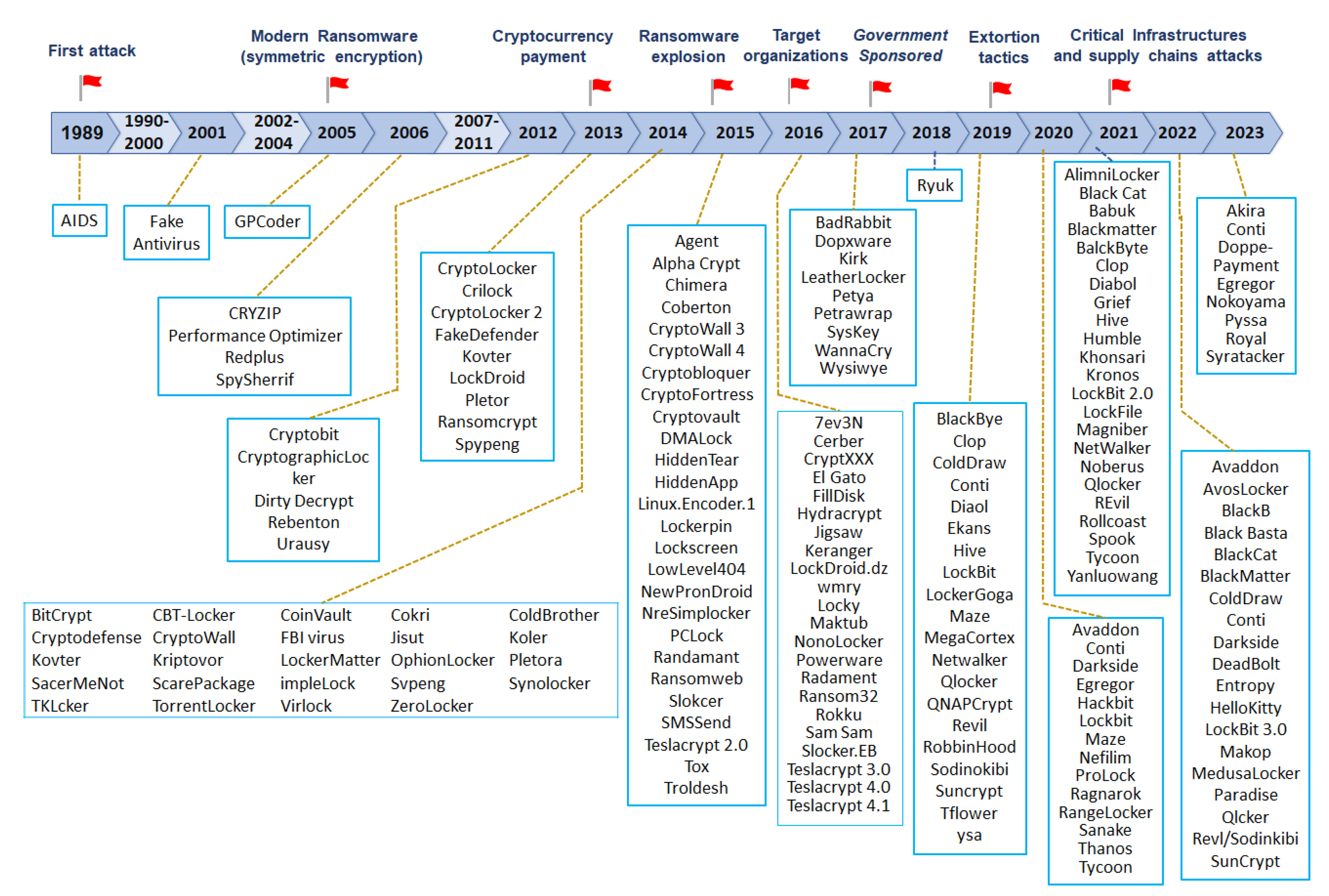

| Delivery Method | Usage % | Protocol | Usage % |
|---|---|---|---|
| Spam email | 60 | SMTP | 45 |
| Remote Desktop | 21 | IMAP | 26.5 |
| Trojan | 20 | Web-browsing | 22.3 |
| Vulnerability exploitation | 15 | POP3 | 3.8 |
| Botnet/Downloader | 11 | FTP | 2.3 |
| Malicious advertising | 8 | Other | 3.3 |
| Endpoint | 7 | ||
| External server | 7 | ||
| Removable media | 6 | ||
| Social media | 5 | ||
| Insider | 3 | ||
| Unfair administration | 2 | ||
| SMS | 1 | ||
| Affiliate scheme | 1 |
| Family | Cyber Kill Chain Stage | |||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Weaponization | Delivery | Exploit | Installation | C&C | Action | |||||||||||||||||
| Scripting | Payload | FAP | Encryption | Evasion | Social | Engineering | Malvertising | TDS | Exploit Kit | Custom Exploit | Host | Net | Hardcoded IP | DG | Botnet | |||||||
| T | D | C | N | P | S | AD | BE | RD | BMS | |||||||||||||
| Avaddon [50,51] | ✓ | 3 9 | ✓ | ✓ | ✓ | ✓ | ✓ | I | ||||||||||||||
| BlackByte [52,53] | ✓ | 1 | ✓ | ✓ | ✓ | ✓ | ✓ | I | ||||||||||||||
| BlackCat [54,55] | ✓ | ✓ | 1 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | o | |||||||||||
| Cerber [56,57,58] | ✓ | ✓ | 7 8 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||
| Diavol [59,60] | ✓ | ✓ | 8 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | E | ||||||||||||
| Ekans [61,62] | ✓ | 3 9 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | I | |||||||||||||
| Entropy [63,64] | ✓ | ✓ | 7 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||||
| Hive [65] | ✓ | ✓ | 8 | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||||||||
| Khonsari [66] | ✓ | ✓ | 2 4 | ✓ | ✓ | ✓ | ||||||||||||||||
| Locky [27] [67,68,69] | ✓ | ✓ | ✓ | 21 5 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||||
| Megacortex [70] | ✓ | ✓ | 23 10 11 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||||||||
| REvil [71] | ✓ | 7 | ✓ | ✓ | ✓ | ✓ | ✓ | E | ||||||||||||||
| Ruyk [72,73] | 1 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | E | ||||||||||||||
| Sabbath [74] | ✓ | ✓ | 1 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | E | ||||||||||||
| Sodinokibi [75] | ✓ | ✓ | 1 6 11 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Z | ||||||||||
| TFLower [76,77] | ✓ | 8 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||||||||
| WannaCry [78,79] | ✓ | 1 8 | ✓ | ✓ | ✓ | ✓ | I | |||||||||||||||
| Detection | Recovery | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Source | ML | Processing | Actions | Sources | Processing | Actions | |||||||||||||
| Name | Kernel | User | DT | RF | ANN | Scoring | Monitoring | Statistical | Distance | Kill | Block | Isolation | Notify | I/O | Cache | API | Deletion | Restoration | |
| KRProtector | H | ✓ | ✓ | ||||||||||||||||
| RAPPER | AC | ✓ | ✓ | ✓ | ✓ | ||||||||||||||
| R-Killer | FS | N | ✓ | ✓ | ✓ | ✓ | |||||||||||||
| R-Locker | H | ✓ | ✓ | ✓ | ✓ | ||||||||||||||
| SSD-Insider | S | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||||||
| UShallNotPass | PR | ✓ | ✓ | ✓ | ✓ | ||||||||||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gómez Hernández, J.A.; García Teodoro, P.; Magán Carrión, R.; Rodríguez Gómez, R. Crypto-Ransomware: A Revision of the State of the Art, Advances and Challenges. Electronics 2023, 12, 4494. https://doi.org/10.3390/electronics12214494
Gómez Hernández JA, García Teodoro P, Magán Carrión R, Rodríguez Gómez R. Crypto-Ransomware: A Revision of the State of the Art, Advances and Challenges. Electronics. 2023; 12(21):4494. https://doi.org/10.3390/electronics12214494
Chicago/Turabian StyleGómez Hernández, José Antonio, Pedro García Teodoro, Roberto Magán Carrión, and Rafael Rodríguez Gómez. 2023. "Crypto-Ransomware: A Revision of the State of the Art, Advances and Challenges" Electronics 12, no. 21: 4494. https://doi.org/10.3390/electronics12214494





