Abstract
Radio frequency (RF) fingerprints have been an emerging research topic for the last decade. Numerous algorithms for recognition have been proposed. However, very few algorithms for the accurate extraction of IQI and PA nonlinearity are available, especially when multiple paths are considered. In this study, we present a scheme that uses the transmitter in-phase/quadrature-phase imbalance (IQI) and the power amplifier (PA) nonlinearity as RF fingerprint features in time-division duplexing (TDD) OFDM systems, which are always considered to be harmful to data transmission. The scheme consists of two round trips with four steps for two cases: in the first, the IQI and PA nonlinearity are unknown at the terminal; in the second, they are known at the terminal. A channel state information (CSI)-tracking algorithm based on the sliding-window least squares method is first adopted at the terminal. In case A, the obtained CSI is sent to the base station (BS) to remove its impact there; in case B, this removal is conducted directly by using pre-equalization at the terminal. Then, by following a sequential iterative approach, the IQI and nonlinearity are individually calculated. Theoretical analyses reveal how CSI estimation errors influence subsequent estimates at the BS in these two cases. Furthermore, the approximate unbiasedness is verified. The theoretical variance and Cramer–Rao lower bound (CRLB) are also given. It is indicated that the theoretical minimum variance in case B is lower than that in case A from the perspective of the CRLB. The numerical results demonstrate the efficiency of the scheme in comparison with existing techniques in the literature.
1. Introduction
With the development of B5G and 6G communication technologies, the physical-layer security of communication is becoming increasingly important, not only for future mobile communication systems but also for the internet of things (IoT) [1,2,3]. Security mechanisms that do not need to be built by using cryptography-based means in the upper layers and that rely solely on inherent physical-layer characteristics have their own unique characteristics, such as the inherent fingerprints of electronic components in transmitters, design defects or vulnerabilities in components in circuits, and the open propagation of electromagnetic waves in wireless communications [4]. In-phase/quadrature-phase imbalance (IQI) and power amplifier (PA) nonlinearity are two key transmitter characteristics that are relatively stable over the long term and vary from device to device [5,6]. They are harmful for data transmission, but are unique to each transmitter for use as a radio frequency (RF) fingerprint. Therefore, it is intuitive to use the transmitter IQI and PA nonlinearity as the RF fingerprint of a transmitter.
IQI estimation is always found in the field of channel equalization and is used to compensate for the distortion of the received signal generated by the IQI. A large number of methods based on linear technology have already been extensively discussed. In [7,8], Alireza Tarighat proposed the least squares (LS) and adaptive equalization method for estimating the combination of transmitter and receiver IQI and channel state information (CSI) to compensate for the resulting transceiver performance degradation. The CSI and IQI were independently estimated based on the pilot by using linear estimation technology in a multiuser single-input–multiple-output (MU-SIMO) system; first, the linear minimum mean squared error (LMMSE) was used to estimate the CSI, and then LS was used to estimate the IQI, thus achieving the separation of the CSI and IQI parameters due to the assumption of IQI at the receiver only [9]. The transmitter (TX) and receiver (RX) IQI compensation problem in differential space–time block-coded orthogonal frequency division multiplexing (STBC-OFDM) systems was studied in [10] and developed further in [11]; the TX and RX IQIs were extracted by employing an algorithm based on a widely linear estimation. An iterative decision feedback (DFB) receiver was proposed to compensate for the IQI due to imperfections in the transceiver RF link for a single carrier with a frequency-domain equalization (SC-FDE) system [12]. This method was a nonlinear compensation method that could greatly improve the equalization performance of an SC-FDE system under IQI compared to the above-mentioned approaches. The authors of [13] used an iterative nonlinear least squares (NLS) method to jointly estimate the IQI in the TX, RX, and channels for generalized orthogonal frequency-division multiplexing (GFDM) systems. Ayse Elif Canbilen [14] investigated the impact of the IQI under generalized Beckmann fading channels for SM-MIMO systems, and both TX and RX IQIs were involved. A performance analysis of the effective channel estimation (e.g., the joint effect of the IQI and channel) and MMSE-based estimation was conducted in [15,16], where the RX IQI was considered in uplink MIMO-OFDM systems. Xiantao Cheng addressed two similar algorithms for estimating the IQI and CSI. One was a sequential estimation algorithm for determining the transmitter IQI and CSI [17], and the other was an EM-based estimation algorithm for determining the transceiver IQI and CSI [18]. Unlike previous methods, they were able to obtain separate estimates of the IQI and CSI. However, our simulation studies showed that these algorithms tended to fall into local minima.
The various methods mentioned above are able to effectively combat performance degradation due to IQI in direct conversion systems, but none of them take the PA nonlinearity of the transmitter into account. PA nonlinearity exists at the front-end of an RF link, and it distorts digitally modulated signals in wireless communications [19,20]. In addition to in-band distortion, the spectral regrowth of digitally modulated signals and adjacent channel interference are also produced by PA nonlinearity [19,20]. PA nonlinearity and IQI are always exploited in specific emitter identification (SEI) (also known as RF-distinct native attribute (RF-DNA) fingerprints) due to their uniqueness and long-term invariant nature [4].
In [21], Ming-Wei Liu extracted PA nonlinearity by using an alternate iterative LS estimation of the channel coefficients and distorted baseband signal to obtain this reliable characteristic in a transmitter based on a training sequence. However, this algorithm required a certain number of samples with a low-enough amplitude in the sequence; otherwise, severe performance degradation would be inevitable. Recently, many works have employed machine learning technology, such as classification algorithms and deep learning technology, to cope with SEI [5,6,22,23]. In such works, a number of simulated and practical trials were conducted, thus verifying the efficiency and reliability of their proposed methods. Nevertheless, unlike traditional approaches [7,8,9,10,11,12,13,14,15,16,17,18], machine learning is powerless in environments without samples, due to its requirements for learning.
In a word, in the previous literature, there are almost no algorithms that directly extract these two transmitter features separately, especially in the presence of multiple paths. The contributions of this study are summarized as follows:
- We establish a feature model of the IQI and PA nonlinearity at the transmitter with multiple paths. Following a brief analysis, we reveal that it is not possible to separately extract the parameters from just one transmission. However, separately extracting IQI and PA nonlinearity under the impact of the CSI is necessary for robust feature extraction. To this end, we propose a scheme for separately estimating the IQI and PA nonlinearity, which involves two round trips with four steps.
- The CSI is estimated/tracked via a sliding-window LS algorithm based on previously depicted training sequences in the first round trip. Then, the IQI and PA nonlinearity of the transmitter are obtained by utilizing a sequential iterative approach after removing the impact of the CSI in the second round trip. The scheme includes two cases: A: IQI and PA nonlinearity are unknown at the terminal; B: IQI and PA nonlinearity are known at the terminal. These have different procedures in steps 3 and 4. The terminal needs to send the coded CSI to the base station (BS) in order to eliminate the channel effect at the BS for case A. The latter deals with the channel effect directly via pre-equalization in step 3 so as to estimate the IQI and PA nonlinearity more simply at the BS for case B.
- We also derive the performance expressions for the two cases and indicate the influence of CSI estimation/tracking. The results of the theoretical analysis show that the theoretical minimum variance in case B is lower than that in case A from the perspective of the Cramer–Rao lower bound (CRLB). In addition, the results of a numerical simulation verify the efficiency of the proposed scheme.
The rest of this study is organized as follows: We first describe the system model and give a CSI tracking algorithm based on the sliding-window LS (CTA_SWLS) with the IQI at the receiver of a terminal in Section 2. In Section 3, we propose an efficient scheme, with four steps, for eliminating the channel impact, and a sequential iterative approach for simultaneously and separately estimating the TX IQI and nonlinear coefficient at the BS is given. This is followed by a performance analysis and an analysis of the CRLB and complexity of the proposed scheme with the two cases in Section 4. Section 5 demonstrates the simulation results. Finally, conclusions are given in Section 6.
Notation: , , and denote the complex conjugate, transpose, and complex conjugate transpose, respectively. ⊙ denotes element-by-element multiplication. ∗ represents circular convolution. DFT{x} and IDFT{X} denote the discrete Fourier transform of x and the inverse discrete Fourier transform of X, respectively. X mod Y refers to taking the remainder after the division of X by Y. Imaginary units are represented by j. Re{X} and Im{X} denotes taking the real part and imaginary part of X, respectively. indicates element-by-element division. The subscript or superscript i or k indicates the index of a variable, vector, or matrix in its context. refers to taking the partial derivative of ℑ with respect to x when .
2. System Model and Analysis
Here, we consider a direct upconversion transmitter in which the carrier frequency from an oscillation source is , the phase difference between the I-branch and Q-branch is 90 degrees, and the amplitude coefficients are equal under ideal conditions. However, due to imperfections in the components of the analog circuits in the transmitter RF link and the diversity in manufacturing, the phases of the two branches do not have a difference of strictly 90 degrees, and the amplitude coefficients are not strictly the same, resulting in errors in the demodulated data on the receiver side if there is no countermeasure. On the other hand, the nonlinearity of the transmitter PA also leads to performance degradation at the receiver.
We assume here that no IQI and PA linearity are maintained across the operating range at the BS. Generally speaking, the BS has a more powerful function and can use higher-cost wide-linearity-region PA- and IQI-free devices; IQI and nonlinearity are even present in the RF link, which can also be pre-corrected to achieve more perfect IQ balance and PA linearity, while this is more difficult to achieve at the terminals due to the relatively low cost and performance of the devices, as well as the relatively large number of terminals.
2.1. TX IQI at the Terminal Only
Let denote the ideal baseband equivalence symbol of the transmitter link at the terminal OFDM system. Because of the impact of the TX IQI at the terminal, this signal is distorted into the following form:
where u and v are the TX IQI coefficients, which are defined by the following two equations:
where and are the amplitude imbalance and the phase imbalance, respectively, generated by the same local oscillator; this is called a symmetric IQI model. As shown in Figure 1a, under conditions of no IQI, and .
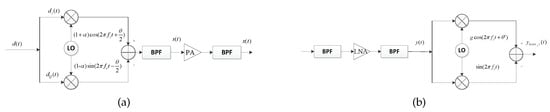
Figure 1.
TX and RX block diagrams with IQI at the terminal. (a) Block diagram of the TX IQI at the terminal. (b) Block diagram of the RX IQI at the terminal.
Considering that the OFDM system consists of N subcarriers, the symbol period is T, , the cyclic prefix is , and denotes the sampling period. The discrete signal expressions in the following parts of this study are all normalized by the sampling period unless specifically stated. The uplink signal received by the BS is
where is the multipath channel length of L, and is additional white Gaussian noise (AWGN).
2.2. CSI Estimation with the RX IQI at the Terminal
If we consider the RX IQI at the terminal, a high-frequency (HF) signal that is received passes through a bandpass filter (BPF) and enters a low-noise amplifier (LNA), whose function is mainly to increase the output signal-to-noise ratio (SNR) (unlike the PA), so it can be considered linear over the entire operation range, as shown in Figure 1b. To facilitate the illustration of estimating the CSI at the terminal, we use an asymmetric model to describe the received signal in this section [9,24]. Thus, the signal received at the terminal in the time-division duplexing (TDD) system is
where represents a training sequence sent by the BS to the terminal, is AWGN, and . and are the RX IQI coefficients. Their complementary property is , and this can be exploited to separate the received signal and the RX IQI. By taking the conjugate to (4) and adding it, we obtain
Let , which satisfies the conjugate symmetry . Taking the DFT of (5) and using conjugate symmetry and the complementary property results in
It can be seen in (6) that when sending different training sequences, we can obtain independent linear equations; each equation can estimate two variables of the CSI via the LS. However, considering the time-varying nature of wireless channels, P sequences are required to be no longer than the channel coherence time [25].
where is the Doppler shift. For better tracking performance within the channel coherence time, we can send P consecutive but different training sequences circularly, herein utilizing the sliding-window LS algorithm to estimate the CSI for each symbol period. We introduce the symbol period index i and rewrite (6) in matrix form, resulting in
where
It is easy to obtain the CSI estimate as follows:
Since interchanges of rows or columns of a matrix do not change its singular values, is a fixed value. Let
Thus,
where denotes row of , as well as . To avoid large estimation errors, it is necessary to design the training sequences with a small condition number for . The CSI tracking algorithm based on the sliding window LS (CTA_SWLS) is given in the form of Algorithm 1 and is shown in Figure 2.
| Algorithm 1 CSI tracking algorithm based on the sliding-window LS (CTA_SWLS). |
|

Figure 2.
Block diagram of CSI tracking based on the sliding-window LS (CTA_SWLS) at the terminal.
2.3. TX Link with Nonlinear PA Only at the Terminal
Considering a memoryless PA, via Taylor expansions, a complex power-series expansion can be used to model the effect of a digital baseband signal passing through a transmitter front-end PA [20,21]. Accordingly, the even terms of the expanded series are discarded, leaving only the odd items, such that the baseband signal becomes
In (17), x denotes the signal after the baseband signal d passes the nonlinear PA, and is a complex coefficient of odd items. Equation (17) shows that the items of form the linear component of the PA. To facilitate analysis, herein, let be normalized to , so . We rewrite (17) in matrix form as follows:
where , , and .
2.4. Coexistence of the TX IQI and PA Nonlinearity in the Terminal Transmitter Link
By combining the IQ imbalance and PA nonlinearity and considering multipath channels and noise, the following received signals can be obtained at the BS:
where is the first column of , and is a matrix whose columns are composed of the last columns of . is an additional white Gaussian noise (AWGN) vector, and . Thus, matrix becomes .
It can be seen from that the IQI coefficients u and v are in each element of , as well as in the nonlinearity coefficient vector ; all of these are the transmitter features that need to be extracted. If the CSI is unknown at the BS, an arbitrary set of values of u and v can be used to determine the matrix by combining arbitrary values of , provided that takes an appropriate value; this can make (19) consistent whether there is error or not. Hence, the parameters in this model cannot be determined if the CSI is unknown at the BS. With special cases in which , , which is a scenario that has been extensively studied in many previous papers [7,8,9,10,11,12,13,14,15,16,17,18]. However, for transmitter feature extraction, the requirement of obtaining independent estimates of the transmitter IQ imbalance and PA nonlinearity from multiple paths is necessary. Therefore, we need to seek a new approach to deal with this issue.
The situation will be different under the condition that the CSI is known according to (19). If a set of values of u and v are available, by using LS estimation, an estimate of can be obtained; the closer the values of u and v are to their true values in all estimates, the more accurate the estimate of is in the sense of the LS. Note that the LS algorithm requires that the column rank of be equal to the number of non-zero terms in ; otherwise, it will be ill conditioned, leading to large errors. Since can be written as
where is a Vandermonde matrix, is equal to a non-zero number, and the rank of is equal to the number of different non-zero values. In other words, the number of different non-zero values in the training sequence is greater than the number of non-zero elements of . has an LS solution for the existence of IQI. Nevertheless, for IQI-free cases, the rank of is determined by the number of different non-zero values. It is, therefore, necessary that the number of different amplitudes is not less than M.
3. The Proposed Scheme
The above analysis shows that when the CSI is unknown at the BS, the model has no deterministic solution. Therefore, we propose a scheme for the joint and independent extraction of the IQI and nonlinear parameters in the terminal transmitter, and this scheme has two cases, which are shown in Figure 3.
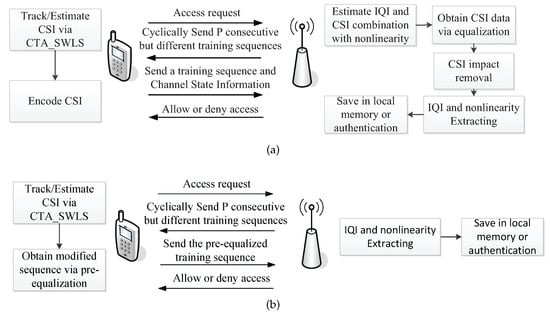
Figure 3.
Block diagram of the proposed scheme. (a) Case A: IQI and PA nonlinearity are unknown at the terminal. (b) Case B: IQI and PA nonlinearity are known at the terminal.
3.1. Case A: IQI and PA Nonlinearity Are Unknown at the Terminal
In this case, transmitter feature extraction and authentication are conducted via two round trips with four steps in TDD systems.
Step 1: The terminal sends an access request to the BS.
Step 2: Upon receipt of the request by the BS, P consecutive but different training sequences are cyclically sent to the terminal.
Step 3: The CTA_SWLS algorithm is employed to track the CSI after P training sequences are received at the terminal. When is satisfied ( denotes a threshold), an FFT is performed on to obtain the time-domain CSI . The first L ( is the max delay spread) values of are retained. Then, a training sequence is sent, and the CSI is truncated to the BS. It is assumed that the CSI remains constant during the last symbol period in step 2 and step 3. Note that to maintain the relevance of the CSI, the training sequence needs to be sent to the BS before the CSI.
Step 4: The BS estimates the combination of the CSI and transmitter IQI based on the training sequence in step 3 by using the LS or MMSE with PA nonlinearity; then, it demodulates the data, which are also known as the CSI. Followed by the removal of the effect of the CSI in the received signal, the BS then estimates the terminal IQI and PA nonlinearity coefficients. The features are stored in a local database either directly or after processing. It is also possible to compare data in the database by using pattern recognition so that the resulting signal to accept or reject the transmitter’s access can be given.
Considering the effects of PA nonlinearity and noise, in step 3, when the terminal encodes and modulates the estimated CSI, it should use a lower-order modulation method, such as BPSK or QPSK, on each OFDM subcarrier. For example, the number of effective paths is generally within 10 for a frequency-selective channel; when using 10 bits (1024-level uniform quantization) and BPSK modulation, a total of 100 bits are required. As long as the number of subcarriers satisfies , this requirement is met. After the BS receives the CSI and removes the impact of the channel, Equation (19) becomes
where and . is a Fourier matrix. This problem now turns into
Let . Since u and v in are to be estimated, is also to be estimated; we use a sequential iterative approach to estimate these quantities.
Setting the initial values to and , first, we calculate
where . Next, by utilizing the gradient descent method, the estimate of v can be iteratively obtained as follows:
where is a small positive value for controlling the step size. In addition,
where
After a finite number of iterations, the temporary suboptimal values of and can be obtained. Then, and are substituted into (23), and the iterative process is repeated until the stopping criteria are met. We summarize the estimation procedure in Algorithm 2.
| Algorithm 2 IQI and nonlinearity sequential estimation algorithm (IQINSEA) |
3.2. Case B: IQI and PA Nonlinearity Are Known at the Terminal
Figure 3b demonstrates the procedure for case B. Here, prior knowledge is given at the terminal, and the corresponding processing is different to that in case A. The differences between case a and case B are as follows.
Step 3: The CTA_SWLS algorithm is employed to track the CSI after P training sequences are received at the terminal. When is satisfied, a modified sequence is directly obtained via a pre-equalization operation and sent to the BS instead of step 3 in case A.
Step 4: The BS receives and estimates the terminal IQI and nonlinear coefficients via Algorithm 2. The subsequent actions are the same as those in case A.
Since we only need to send a pre-equalization training sequence to the BS, case B is more suitable for faster-varying channels. With no CSI effect, the signal received by the BS should be shown as follows:
The matrix is known at both the terminal and the BS, but due to the CSI there is no unique solution, as described in the previous section. Therefore, we are able to send a pre-equalized training sequence to the BS after the CSI is estimated, and a signal with no CSI effect is equivalently received at the BS. To satisfy
that is,
Equation (30) can be written as N independent equations for :
or
where
Equation (31) is a binary nonlinear system of equations with respect to and , and the solution can be obtained via the Newton–Raphson method. We omit the subscript i and let so that we can obtain the following solution:
where is a Jacobian matrix. In addition,
in which and can be simultaneously replaced with and . can be replaced with .
It is also possible to use nonlinear least squares to find the solution for the following optimization problem:
It is given as
where , and is a small positive value for controlling the step size.
This is a system of N independent binary nonlinear equations that can be calculated in parallel at the transmitter side and implemented very quickly. The received signal that is transmitted to the BS can be eliminated from the CSI beforehand to facilitate subsequent processing at the BS. Once it is received by the BS, Algorithm 2 is used to directly estimate the IQI and nonlinear coefficients.
4. Performance Analysis
4.1. Performance Analysis of CTA_SWLS
Let represent the true value of . Thus, the estimated CSI with k and subcarriers is
Taking the expectation to yields
It can be seen from (37) that the unbiasedness of Algorithm 1 depends on the means of the past true CSI. If the CSI is a stationary process over P symbol periods, then , that is, Algorithm 1 is unbiased. It is assumed here that the channel is independent and identically distributed (IID), and for each path; thus, , where and denote the true CSI time-domain and frequency-domain vectors, respectively. and denote their respective means.
4.2. Error Propagation
In this subsection, the performance of Algorithm 2 in Step 4 is described. CSI estimation and quantization errors and demodulation errors in case A, as well as errors arising from pre-equalization in case B, are ignored. Before that, consideration of error propagation
is necessary. In the scheme, error propagation affects the estimation of the terminal IQI and
nonlinear parameters at the BS.
4.2.1. Case A
The received signal at the BS is
After removing the impact of the CSI, is now turned into in the estimated version of (21). Then, an FFT is implemented on both sides:
where .
4.2.2. Case B
The pre-equalization effect satisfies
Then,
An FFT is implemented on both sides of the estimated version of (29):
It can be seen that apart from the noise items, the two received signals at the BS are equivalent to the convolution of the received signal and after removing the CSI in both case A and case B. The factor vector is determined by the CSI estimation error of CTA_SWLS and the true CSI value. Note that the pre-equalization does not introduce new errors in case B, it just propagates the estimation error of the CSI. The only difference between the two cases is the noise effect.
Each element of the factor vector follows a reciprocal normal distribution, with obeying a gaussian distribution. Its expectation exists and is a scaled Faddeeva function whose exact expression depends on the sign of the imaginary part [26]. Accordingly, the precise analysis of the factor vector’s impact on the estimation error in Algorithm 2 is intractable. Here, we consider a moderate condition, ; then, .
4.3. Performance Analysis of Algorithm 2
A detailed mathematical analysis of the performance of Algorithm 2 in case A and case B can be found in Appendix A.
4.4. Complexity Analysis
Here, we consider a time-complexity analysis based on the number of multiplications. In Step 3, the FFTs of P training sequences and are calculated offline. A total of P FFTs are required during the coherence time, and multiplications are acquired per FFT. There are parallel calculations, with each requiring multiplications.
However, during each symbol period, only is needed for online calculation. Then, the iterations in Algorithm 1 are executed in parallel. Lastly, an IFFT is implemented for . Therefore, a total of multiplications are required online.
In case B, pre-equalization is a parallel calculation of a system of N equations. Each equation requires only complex multiplications, where K is the number of iterations of the Newton–Raphson method. For the implementation of Algorithm 2 in Step 4, complex multiplications are needed. and denote the numbers of internal and external iterations in Algorithm 2, respectively.
5. Simulation and Analysis
In this section, simulations, analysis, and confirmation of the effectiveness of the proposed scheme are provided. The following simulation configuration was used: OFDM signals were sent at the BS and terminal, the number of subcarriers was , , MHz, and 64-QAM modulation was adopted in each subcarrier. The carrier frequency was GHz, the relative movement velocity was 300 km/h, and satisfied . In step 3 of case A, quantification errors were ignored, and the CSI was coded by using BPSK modulation for each subcarrier. Therefore, the BS demodulation error was not considered here. The time-varying channels were set up as independent Gaussian processes, and . The SNR was defined as follows:
The MSE was used as a performance indicator:
The proposed scheme is labeled as 1 in subscript, the method from [17] is labeled as 2, and the method from [21] is labeled as 3. A total of 1000 independent trials were implemented per setting.
5.1. CSI Tracking via CTA_SWLS in Step 3
In this subsection, we simulate cyclically sending P consecutive but different training sequences to the terminal. , , .
In Figure 4, one can see that the SNR difference did not significantly change the tracking performance. This performance was relatively more affected by the jitter of the channel itself. The reason for this was that the smoothing effect of RLS brought the tracking curve closer to the steady-state value of the channel, and the additive noise was effectively suppressed by using P training sequences to track the channel. Meanwhile, the time-varying nature of the P training sequences themselves had a larger cumulative impact on the tracking accuracy of the current symbol period. Thereby, the jitter of the channel had a greater impact on the tracking performance compared to the noise effect.
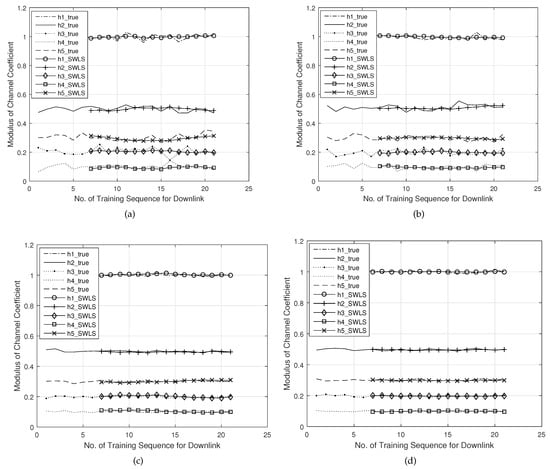
Figure 4.
Tracking performance of CTA_SWLS for each channel tap. (a) , SNR = 5 dB. (b) , SNR = 20 dB. (c) , SNR = 5 dB. (d) , SNR = 20 dB.
Figure 5 demonstrates the tracking performance of CTA_SWLS according to the MSE. Different noise levels only affected the mean value of the deviation, as shown by, for example, the fixed distance between the two curves at the top and bottom of Figure 5a,b, which was consistent with III in (38). However, the magnitude of the deviation was only affected by the channel jitter, which agreed with I and II in (38). In addition, the curves exhibited a cyclic pattern of the downlink with respect to the number of training sequences due to the cyclical sending of P sequences, which was in agreement with II of (38). Therefore, the theoretical variance of CTA_SWLS given by (38) was confirmed through this simulation.
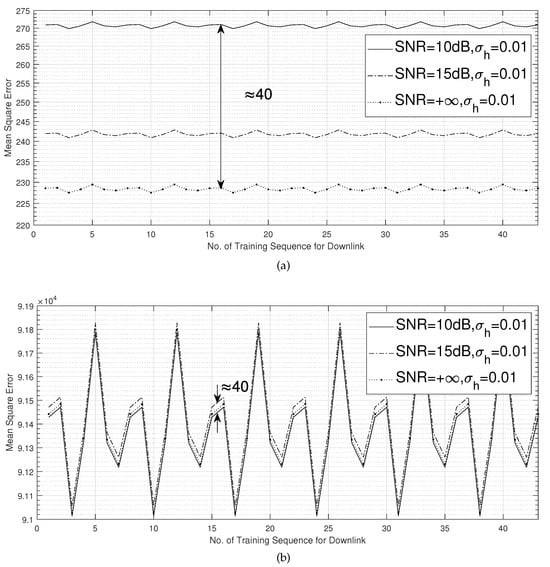
Figure 5.
Tracking performance of CTA_SWLS according to the MSE. (a) , SNR = 10 dB/15 dB/+∞. (b) , SNR = 10 dB/15 dB/+∞.
5.2. IQI and PA Nonlinearity Estimation Performance via IQINSEA in Case A and Case B
Figure 6, Figure 7 and Figure 8 show the MSE performance curves versus the SNR for IQINSEA in the two cases. The IQI and PA nonlinearity parameters were configured as follows: strong IQI and strong PA nonlinearity in Figure 6, strong IQI and weak PA nonlinearity in Figure 7, and weak IQI and strong PA nonlinearity in Figure 8. It was considered that the proposed scheme had to estimate the CSI first for both cases before the IQI and PA nonlinearity could be estimated by using IQINSEA. To facilitate fair comparisons, the ideal CSI was provided for method 2 and method 3; otherwise, the estimation performance of these two algorithms would be worse. Under this condition, since method 2 did not have the ability to estimate the PA nonlinearity and method 3 could not estimate the IQI, method 2 was only involved in the estimation of the IQI, and method 3 was only involved in the estimation of the PA nonlinearity.
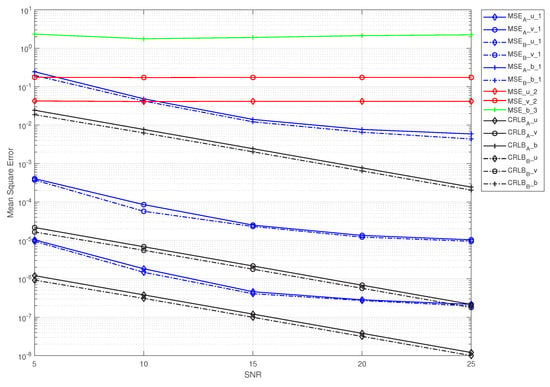
Figure 6.
MSE curves for the three methods, as well as the CRLB. . was set as follows: .
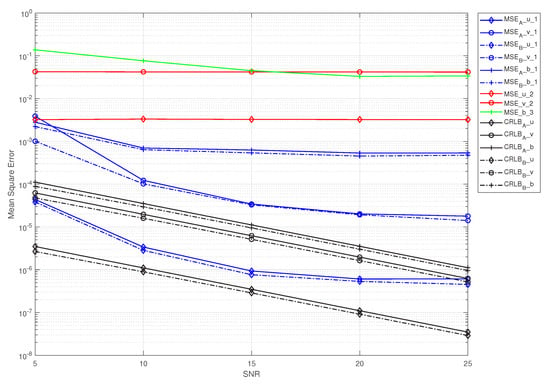
Figure 7.
MSE curves for the three methods, as well as the CRLB. . was set as follows: .
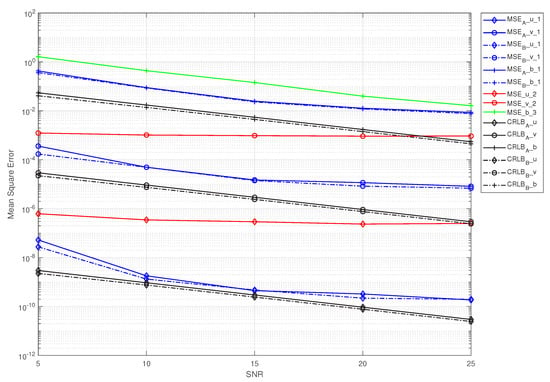
Figure 8.
MSE curves for the three methods, as well as the CRLB. . was set as follows: .
In Figure 6, it can be observed that, in the strong IQI scenarios, the PA nonlinearity estimation with method 3 hardly improved as the SNR grew (Figure 6 and Figure 7) because this method did not take the IQI into account, although there was some improvement in the weak IQI scenario (Figure 8). Accordingly, it can be seen that the effect of the IQI on the estimation performance of method 3 was relatively large. Note that the MSE performance of method 2 hardly varied with the SNR in all of the scenarios because this method is prone to local minima and does not consider the PA nonlinearity. These results were obtained with the assumption that the CSI was known at the BS for methods 2 and 3. Otherwise, the estimated errors would be even larger.
Nevertheless, of all of the scenarios, our proposed scheme was the most efficient among the three methods, i.e., it had a lower MSE and was closer to the CRLB. Another noteworthy aspect is that the MSE curves slowly decreased as the SNR grew, especially in the high-SNR regime. Note that the MSEs in case B were slightly lower than those in case A, especially with a low SNR, which verified the conclusion given in Section 4. This is because when the CSI was estimated, it was placed at the transmitter to directly remove the effect of the CSI on the system; then, the signal without the impact of the CSI was transmitted, i.e., case B. On the contrary, the CSI was further distorted in transmission, resulting in the removal of the impact of the CSI on the system at the receiver, thus making the error of the system larger, i.e., case A.
6. Conclusions
In this study, two important features of a transmitter, i.e., IQI and PA nonlinearity, were utilized, and these are generated by the nonlinear circuit of the RF front-end at the terminal. They are detrimental to the efficiency of data transmission, but due to their uniqueness and long-term invariance, they can be used as RF fingerprints of a transmitter for terminal identification. This study focuses on the problem of extracting the IQI and PA nonlinearity of a transmitter efficiently and separately in the presence of multiple paths for TDD OFDM systems.
Via system modeling, it was found that only a single transmission could not yield a unique solution due to the coexistence of the IQI, PA nonlinearity, and multiple paths. To address this intractable problem, we proposed a scheme for independently estimating the IQI and nonlinearity, and this involved two round trips with four steps.
Once the training sequences from the BS were received, the real-time CSI was first estimated/tracked at the terminal by using the CTA_SWLS algorithm. The procedures were then divided into different parts for the two cases. In case A, the IQI and PA nonlinearity were unknown at the terminal; in case B, the IQI and PA nonlinearity were known at the terminal. In the two cases, the treatments for removing the impact of the CSI were distinct. Finally, the IQI and PA nonlinearity were estimated at the receiver by using IQINSEA.
With the theoretical analysis, the CSI tracking performance of CTA_SWLS was given. The influence of error propagation on further processing stages was given for both cases. Then, the approximate unbiasedness of the estimation algorithm was theoretically proven, and the variances of IQINSEA were given with the CRLB for both cases. The numerical results show the efficiency of the scheme in comparison with existing techniques in the literature.
Author Contributions
Conceptualization, Y.H. and A.H.; methodology, Y.H.; software, J.F.; validation, Y.H., X.L. and Y.Z.; formal analysis, Y.H. and H.T.; investigation, Y.H. and J.F.; resources, H.T.; data curation, Y.H. and H.T.; writing—original draft preparation, Y.H.; writing—review and editing, A.H.; visualization, X.L. and Y.Z.; supervision, A.H.; project administration, Y.H.; funding acquisition, A.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported in part by Jiangsu Provincial Key Laboratory of Network and Information Security (No. BM2003201), Natural Science Foundation of Jiangsu Province, China (Grant No. BK20201199).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Performance Analysis of Algorithm 2
Appendix A.1. Case A
To facilitate the analysis of unbiasedness and efficiency, we analyze an estimator under the condition that the others are known. In practice, the parameters interact with each other, and the results of this analysis will have some errors with respect to its real performance. However, if the effects of interaction are considered, the analysis will be intractable due to its complexity. Considering the unbiasedness of , it is first provided that , u, and are known. Once the iterations converge to the optimal value, it is required that
Substituting (21) into (A1), the following is given:
Since the presence of nonlinear components in the matrix () leads to the presence of higher-order quantities that cannot be easily and directly calculated, we use the Taylor approximation and retain the linear and quadratic terms.
where . Let , , , and to simplify the derivation, and (A2) becomes (A5).
Ignoring higher-order infinitesimals and taking the expectation on both sides of (A5), the following is obtained:
This holds for any , and is obtained. So, under weak nonlinearity, the estimate of is approximately unbiased. Similarly to the above derivation, , u, and are also evidently unbiased. That is, Algorithm 2 is approximately unbiased in case A.
Let , . Ignoring higher-order infinitesimals and taking the variance on both sides of (A5), and are substituted. and are independent. We obtain the variance of through (A7).
where and are given by
where and are given in (A10) and (A11), respectively.
Here,
and in (A8) and (A9) are given as in (A14) and (A15), respectively.
Similarly, the variance of is given by (A16):
where and are similar to and , respectively. So, the mean square error (MSE) of is given by
where is similar to .
From (23) and (A2), it follows that
The expectation is taken on both sides of
Accordingly, the autocorrelation matrix of is given as in (A20).
Note that, actually, the MSE will be larger than the above result if interactions are considered.
The variance of any unbiased estimator can only approximate the CRLB without restriction and not go below it; thus, we derive the CRLB of the model for comparative analyses here. The conditional probability density function (CPDF) of is shown as in (A21).
Let . It can be seen in (A21) that the CPDF satisfies the regularity conditions among all of the available estimates. Accordingly, a minimum-variance unbiased estimator is attained, that is, the CRLB. The Fisher information matrix is obtained as
where
So, the CRLB in case A is equal to . Straightforwardly, the minimum variances of v and in case A are given by
Appendix A.2. Case B
Here, Equation (A2) becomes
In a similar derivation to that for case A, we find that Algorithm 2 is also approximately unbiased in case B.
where is similar to .
The CPDF of is given as
Let . After a similar derivation, this yields
Straightforwardly, the CRLB in case B is achieved as in (A28).
Obviously, , where the notation ≺ means that is a positive-definite matrix. consists of elements that satisfy . Straightforwardly, . The reason for this is that any prior knowledge at the transceivers should achieve the performance gain illustrated in case B.
References
- Li, G.; Hu, L.; Staat, P.; Elders-Boll, H.; Zenger, C.; Paar, C.; Hu, A. Reconfigurable Intelligent Surface for Physical Layer Key Generation: Constructive or Destructive? IEEE Wirel. Commun. 2022, 29, 146–153. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Xu, W.; Renzo, M.D.; Hu, A. On Maximizing the Sum Secret Key Rate for Reconfigurable Intelligent Surface-Assisted Multiuser Systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 211–225. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Jorswieck, E.A.; Zhang, J.; Hu, A.; Chen, Y. Sum Secret Key Rate Maximization for TDD Multi-User Massive MIMO Wireless Networks. IEEE Trans. Inf. Forensics Secur. 2021, 16, 968–982. [Google Scholar] [CrossRef]
- Danev, B.; Zanetti, D.; Capkun, S. On physical-layer identification of wireless devices. ACM Comput. Surv. (CSUR) 2012, 45, 1–29. [Google Scholar] [CrossRef]
- Fadul, M.K.; Reising, D.R.; Sartipi, M. Identification of OFDM-based radios under rayleigh fading using RF-DNA and deep learning. IEEE Access 2021, 9, 17100–17113. [Google Scholar] [CrossRef]
- Zha, X.; Chen, H.; Li, T.; Qiu, Z.; Feng, Y. Specific emitter identification based on complex Fourier neural network. IEEE Commun. Lett. 2021, 26, 592–596. [Google Scholar] [CrossRef]
- Tarighat, A.; Bagheri, R.; Sayed, A.H. Compensation schemes and performance analysis of IQ imbalances in OFDM receivers. IEEE Trans. Signal Process. 2005, 53, 3257–3268. [Google Scholar] [CrossRef]
- Tarighat, A.; Sayed, A.H. Joint compensation of transmitter and receiver impairments in OFDM systems. IEEE Trans. Wirel. Commun. 2007, 6, 240–247. [Google Scholar] [CrossRef]
- Kolomvakis, N.; Matthaiou, M.; Coldrey, M. IQ imbalance in multiuser systems: Channel estimation and compensation. IEEE Trans. Commun. 2016, 64, 3039–3051. [Google Scholar] [CrossRef]
- Chen, L.; Helmy, A.G.; Yue, G.; Li, S.; Al-Dhahir, N. Performance analysis and compensation of joint TX/RX I/Q imbalance in differential STBC-OFDM. IEEE Trans. Veh. Technol. 2016, 66, 6184–6200. [Google Scholar] [CrossRef]
- Chen, L.; Helmy, A.G.; Yue, G.; Li, S.; Al-Dhahir, N. Performance and compensation of I/Q imbalance in differential STBC-OFDM. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; IEEE: Piscataway Township, NJ, USA, 2016; pp. 1–7. [Google Scholar]
- Zhang, X.; Li, H.; Liu, W.; Qiao, J. Iterative IQ imbalance compensation receiver for single carrier transmission. IEEE Trans. Veh. Technol. 2017, 66, 8238–8248. [Google Scholar] [CrossRef]
- Cheng, H.; Xia, Y.; Huang, Y.; Yang, L.; Mandic, D.P. Joint channel estimation and Tx/Rx I/Q imbalance compensation for GFDM systems. IEEE Trans. Wirel. Commun. 2019, 18, 1304–1317. [Google Scholar] [CrossRef]
- Canbilen, A.E.; Ikki, S.S.; Basar, E.; Gultekin, S.S.; Develi, I. Joint impact of I/Q imbalance and imperfect CSI on SM-MIMO systems over generalized Beckmann fading channels: Optimal detection and Cramer-Rao bound. IEEE Trans. Wirel. Commun. 2020, 19, 3034–3046. [Google Scholar] [CrossRef]
- Chen, Y.; You, L.; Lu, A.A.; Gao, X.; Xia, X.G. Channel estimation and robust detection for IQ imbalanced uplink massive MIMO-OFDM with adjustable phase shift pilots. IEEE Access 2021, 9, 35864–35878. [Google Scholar] [CrossRef]
- Chen, Y.; You, L.; Lu, A.A.; Gao, X. Widely-linear processing for the uplink of the massive MIMO with IQ imbalance: Channel estimation and data detection. IEEE Trans. Signal Process. 2021, 69, 4685–4698. [Google Scholar] [CrossRef]
- Cheng, X.; Luo, Z. Compensation of transmitter I/Q imbalance in millimeter-wave SC-FDE systems. IEEE Trans. Veh. Technol. 2016, 66, 4472–4476. [Google Scholar] [CrossRef]
- Cheng, X.; Yang, Y.; Li, S. Joint compensation of transmitter and receiver I/Q imbalances for SC-FDE systems. IEEE Trans. Veh. Technol. 2020, 69, 8483–8498. [Google Scholar] [CrossRef]
- Aparin, V. Analysis of CDMA signal spectral regrowth and waveform quality. IEEE Trans. Microw. Theory Tech. 2001, 49, 2306–2314. [Google Scholar] [CrossRef]
- Gard, K.G.; Larson, L.E.; Steer, M.B. The impact of RF front-end characteristics on the spectral regrowth of communications signals. IEEE Trans. Microw. Theory Tech. 2005, 53, 2179–2186. [Google Scholar] [CrossRef]
- Liu, M.W.; Doherty, J.F. Nonlinearity estimation for specific emitter identification in multipath channels. IEEE Trans. Inf. Forensics Secur. 2011, 6, 1076–1085. [Google Scholar]
- Pan, Y.; Yang, S.; Peng, H.; Li, T.; Wang, W. Specific emitter identification based on deep residual networks. IEEE Access 2019, 7, 54425–54434. [Google Scholar] [CrossRef]
- Liu, W.; Li, X.; Huang, Z.; Wang, X. Transmitter fingerprinting for VLC systems via deep feature separation network. IEEE Photonics J. 2021, 13, 1–7. [Google Scholar] [CrossRef]
- Li, J.; Matthaiou, M.; Svensson, T. I/Q imbalance in two-way AF relaying. IEEE Trans. Commun. 2014, 62, 2271–2285. [Google Scholar] [CrossRef]
- Rappaport, T.S. Wireless Communications: Principles and Practice, 2nd ed.; Pearson Education: Upper Saddle River, NJ, USA, 2010. [Google Scholar]
- Lecomte, C. Exact statistics of systems with uncertainties: An analytical theory of rank-one stochastic dynamic systems. J. Sound Vib. 2013, 332, 2750–2776. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).