Analyzing Miners’ Dynamic Equilibrium in Blockchain Networks under DDoS Attacks
Abstract
:1. Introduction
- To the best of our knowledge, this paper is the first to use a dynamic method to study the selection of the profitable optimal strategy for miners under DDoS attacks.
- We construct the miners’ profits tables and dynamic replication equation based on a DDoS attack.
- We obtain the optimal strategy in different cases by analyzing various attack situations on the dynamic replication equation.
- By comparing static and dynamic games, the experimental results show that dynamic games have the advantages of allowing multiple games and a better game evolution when miners face attacks. To be clear, the better the network environment is, the more the miners will choose to launch an attack to obtain the best profit when facing DDoS attacks.
2. Related Work
2.1. DDoS Attacks in Blockchain Systems
2.2. The DDoS-Based Combination Attacks in Blockchain Systems
2.3. Defense and Mitigation Methods for DDoS Attacks
2.4. Challenges in Current Research
3. The Proposed Evolutionary Game Theory Model and Solutions
3.1. Problem Description and Hypothesis
3.2. Design and Implementation of DDoS Attacks’ Evolutionary Game Model for Miners
3.3. Steady-State Solutions
4. Experiment and Results
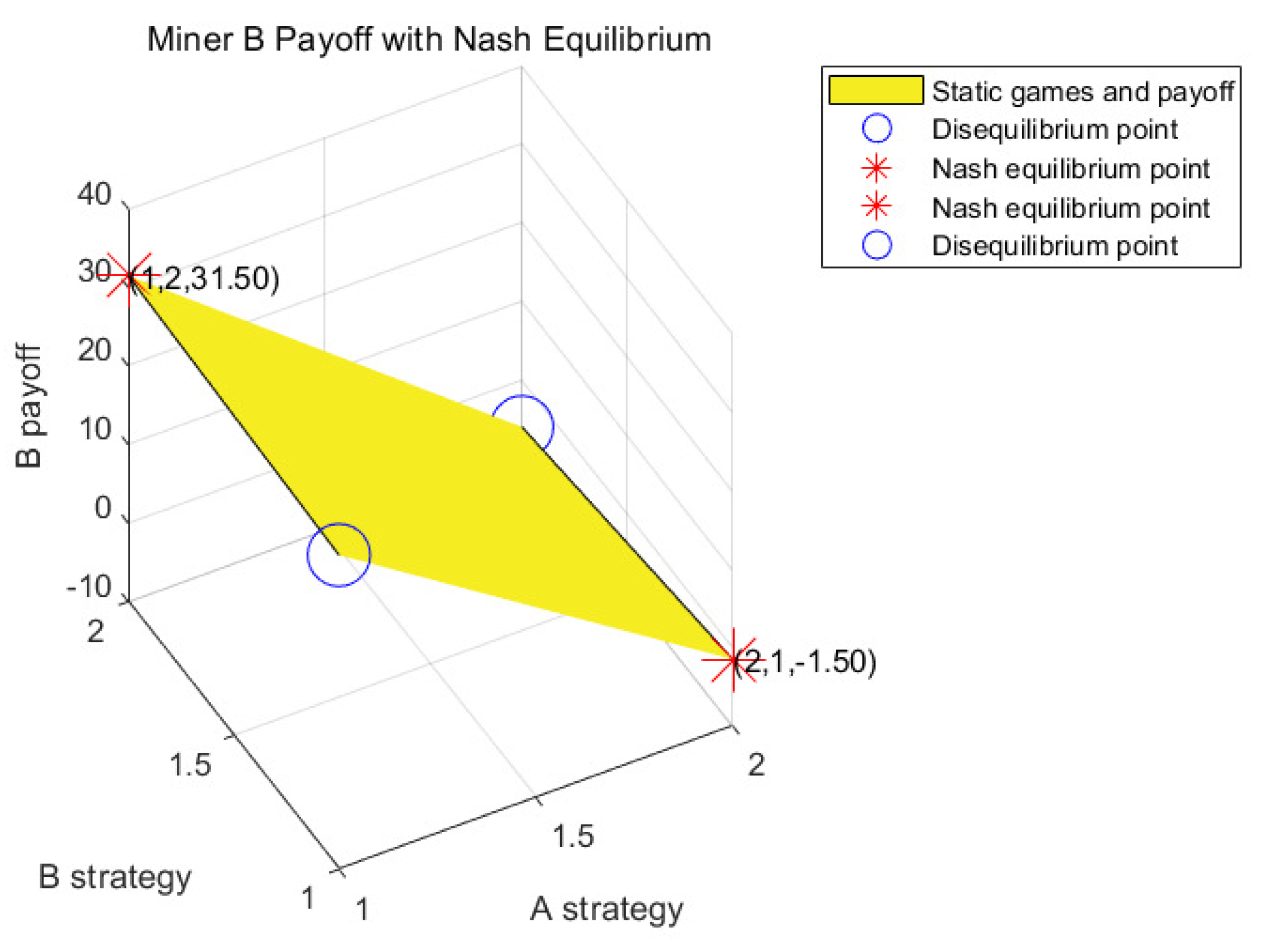
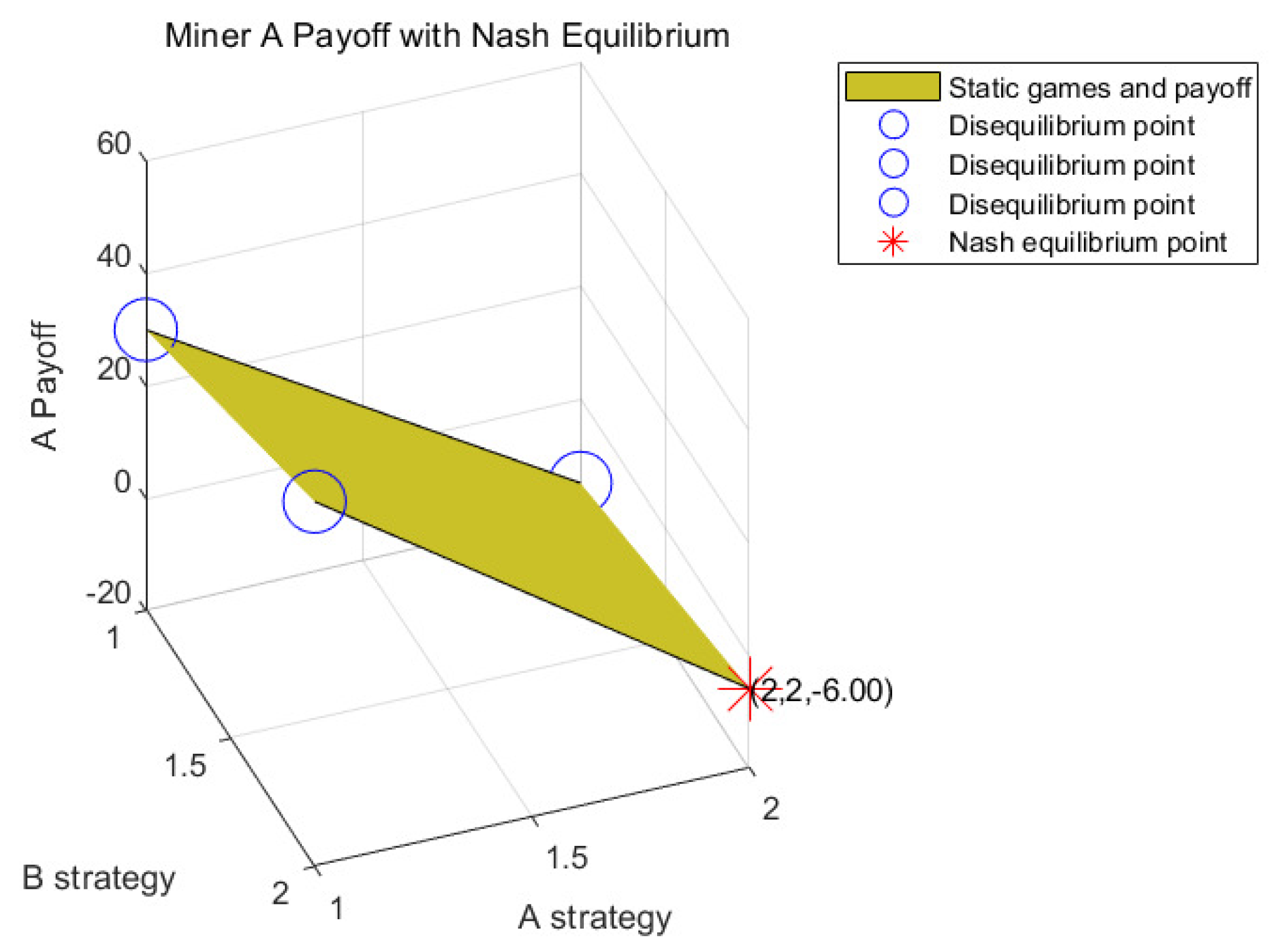
4.1. Static Game Experiment
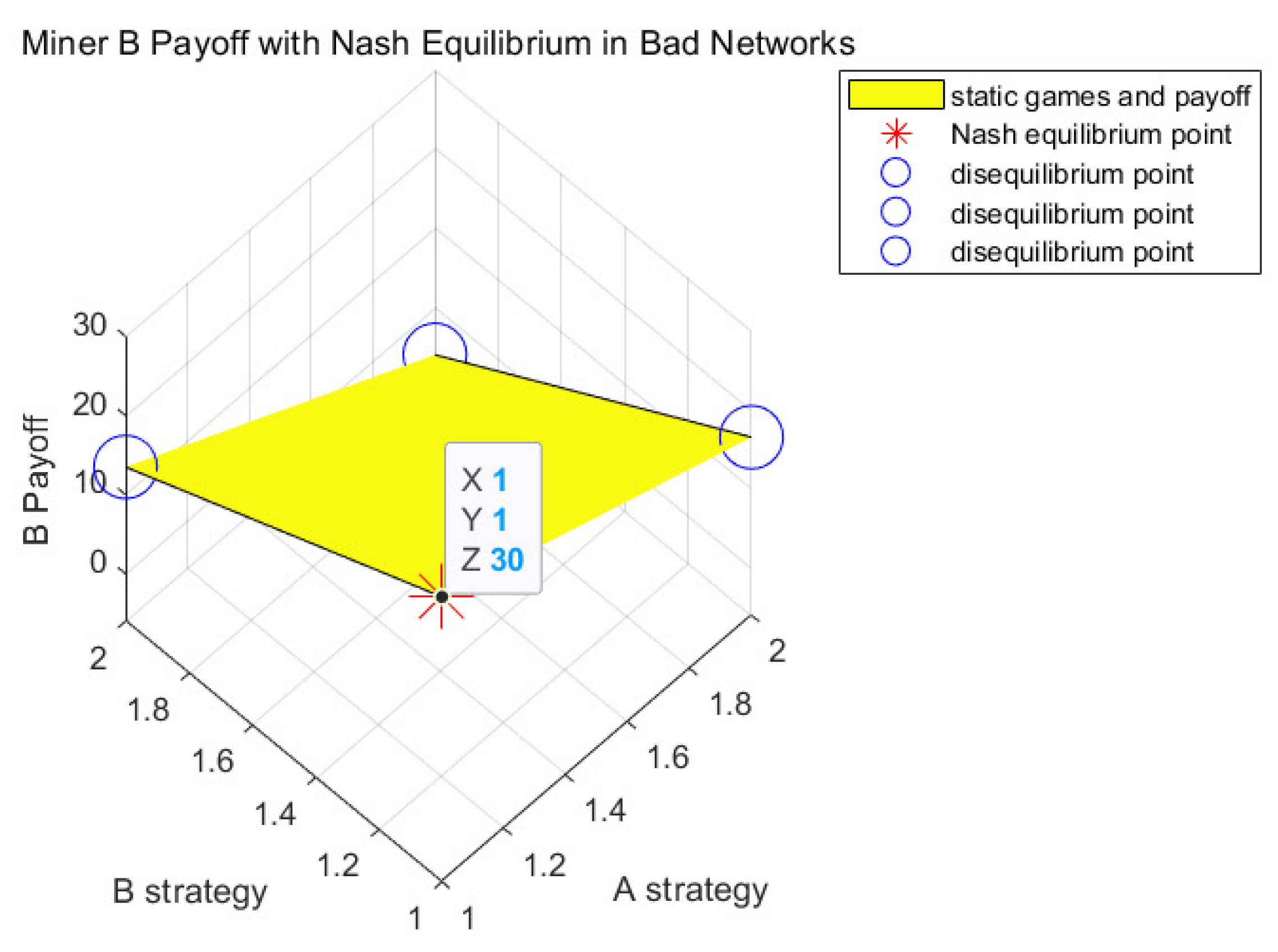
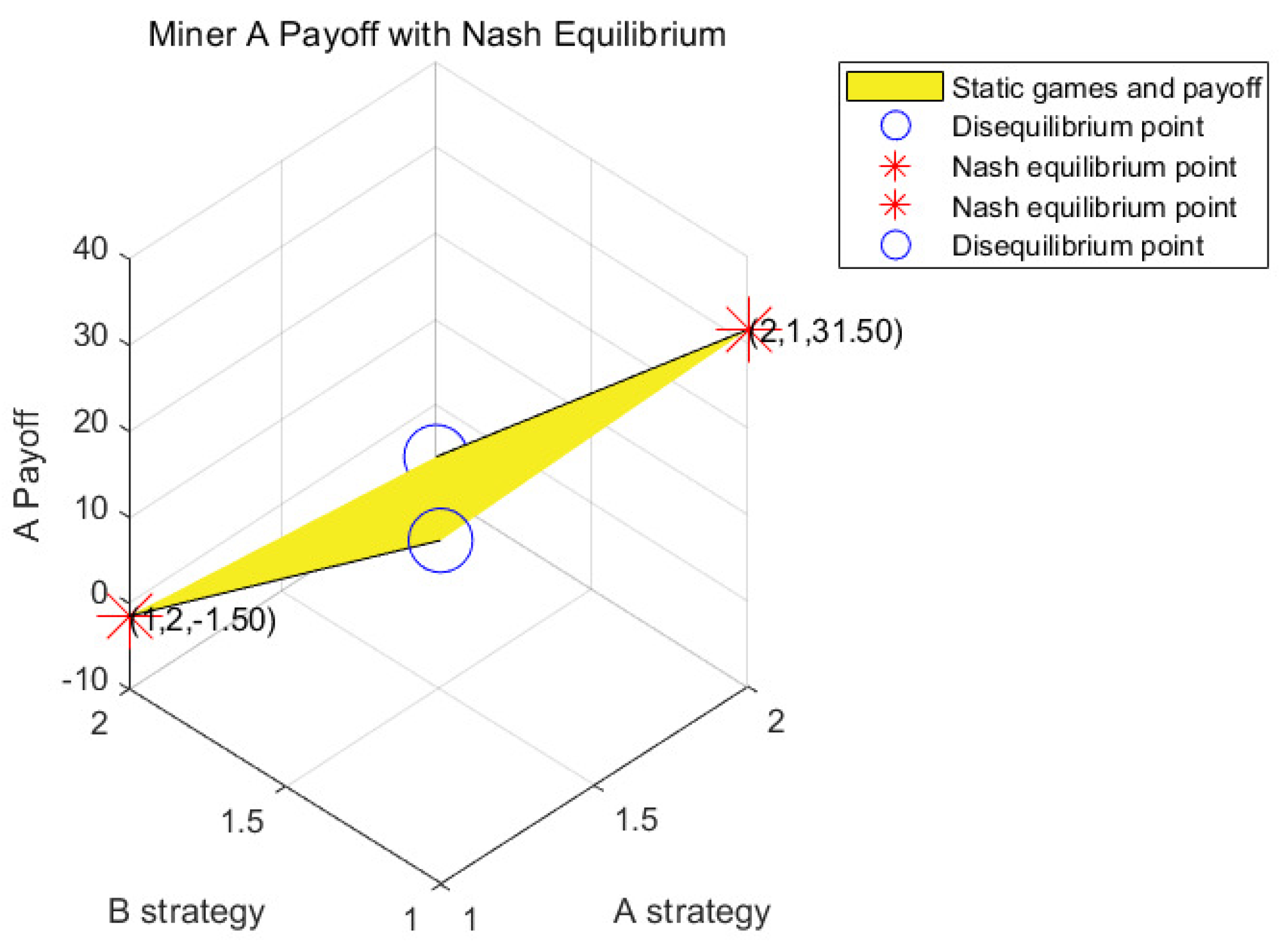
4.1.1. Analysis of Game Strategy under the Bad Network Environment
4.1.2. Analysis of Game Strategy under the Medium Network Environment
4.1.3. Analysis of Game Strategy under the Good Network Environment
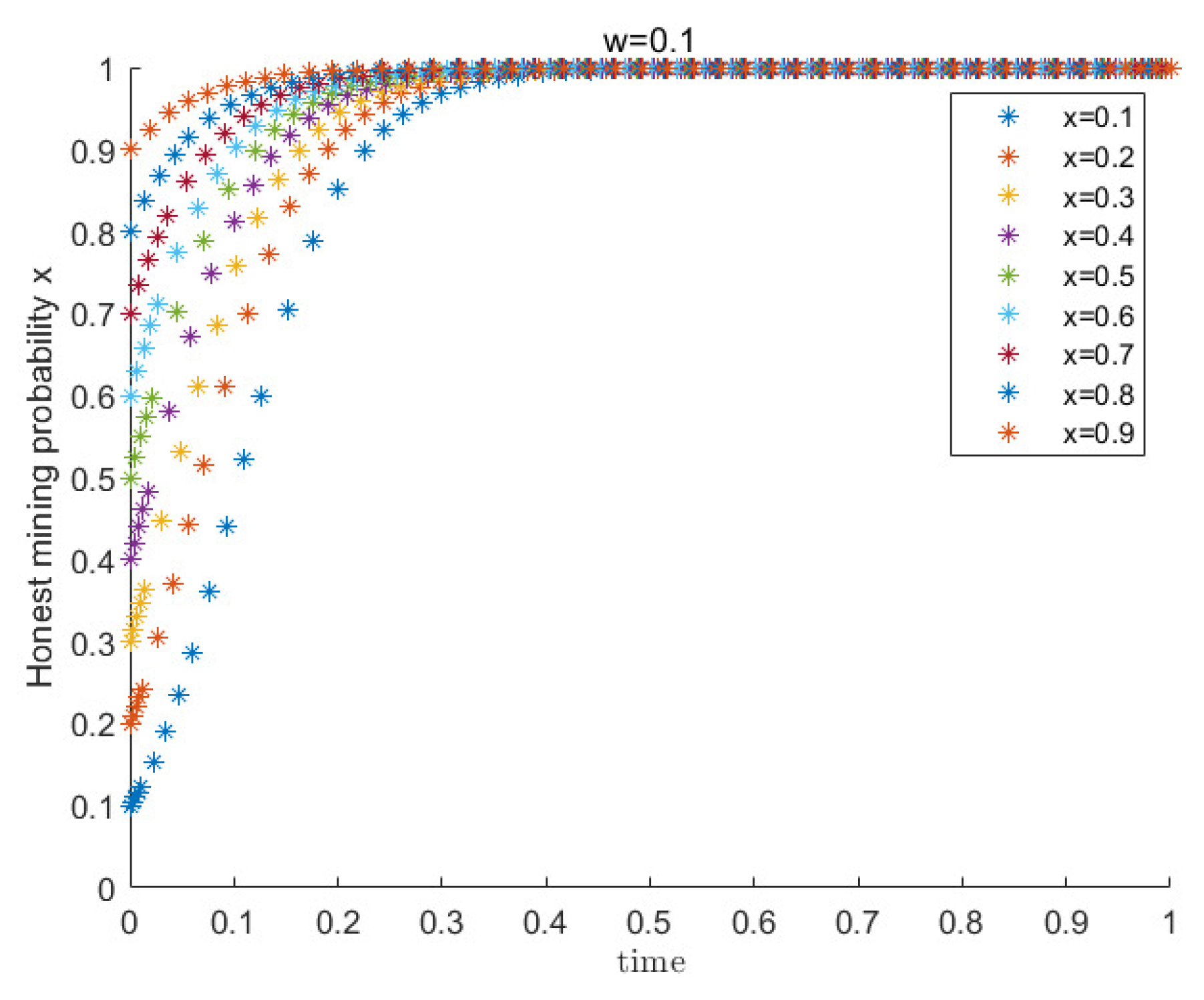
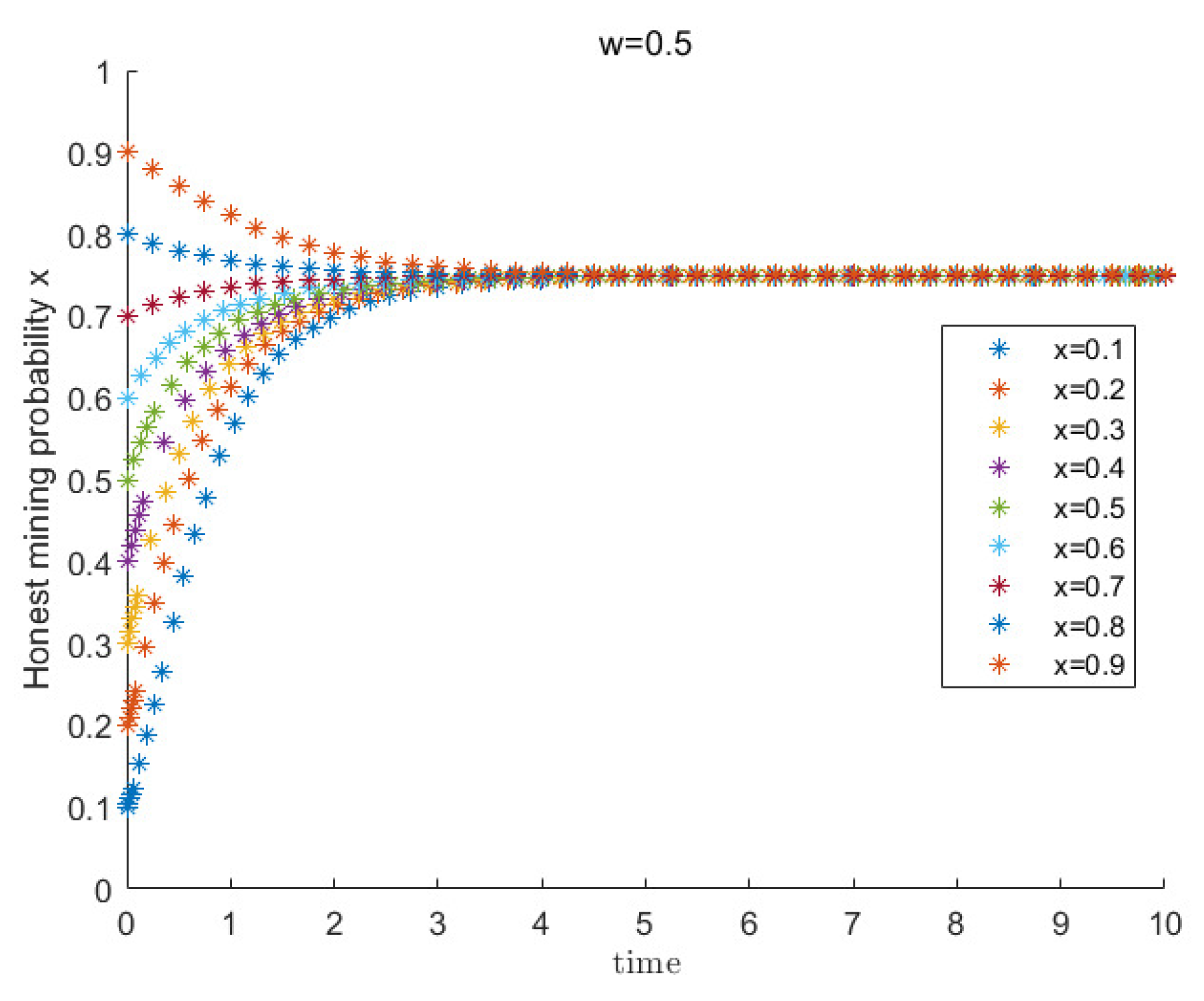
4.2. Evolutionary Game Experiment
4.2.1. Analysis of Game Strategy under a Harsh Network Environment
4.2.2. Analysis of Game Strategy under a Medium Network Environment
4.2.3. Analysis of Game Strategy under a Good Network Environment
4.3. Analysis of Experimental Results
5. Discussion
6. Conclusions
7. Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Meneghetti, A.; Sala, M.; Taufer, D. A Survey on PoW-based Consensus. AETiC 2020, 4, 8–18. [Google Scholar] [CrossRef]
- Lepore, C.; Ceria, M.; Visconti, A.; Rao, U.P.; Shah, K.A.; Zanolini, L. A Survey on Blockchain Consensus with a Performance Comparison of PoW, PoS and Pure PoS. Mathematics 2020, 8, 1782. [Google Scholar] [CrossRef]
- Xu, J.; Wang, C.; Jia, X. A Survey of Blockchain Consensus Protocols. ACM Comput. Surv. 2023, 55, 278. [Google Scholar] [CrossRef]
- Yadav, A.K.; Singh, K.; Amin, A.H.; Almutairi, L.; Alsenani, T.R.; Ahmadian, A. A Comparative Study on Consensus Mechanism with Security Threats and Future Scopes: Blockchain. Comput. Commun. 2023, 12, 102–115. [Google Scholar] [CrossRef]
- Liu, X.; Huang, Z.; Wang, Q.; Wan, B. An Evolutionary Game Theory-Based Method to Mitigate Block Withholding Attack in Blockchain System. Electronics 2023, 12, 2808. [Google Scholar] [CrossRef]
- Huang, Z.; Wang, Q. A PUF-based Unified Identity Verification Framework for Secure IoT Hardware via Device Authentication. World Wide Web 2020, 2, 1057–1088. [Google Scholar] [CrossRef]
- Kumari, P.; Jain, A.K. A Comprehensive Study of DDoS Attacks over IoT Network and Their Countermeasures. Comput. Secur. 2023, 127, 103096. [Google Scholar] [CrossRef]
- Mittal, M.; Kumar, K.; Behal, S. Deep learning approaches for detecting DDoS attacks: A systematic review. Soft Comput. 2023, 27, 13039–13075. [Google Scholar] [CrossRef]
- Waseem, M.; Adnan Khan, M.; Goudarzi, A.; Fahad, S.; Sajjad, I.A.; Siano, P. Incorporation of Blockchain Technology for Different Smart Grid Applications: Architecture, Prospects, and Challenges. Energies 2023, 16, 820. [Google Scholar] [CrossRef]
- Guru, A.; Mohanta, B.K.; Mohapatra, H.; Al-Turjman, F.; Altrjman, C.; Yadav, A. A Survey on Consensus Protocols and Attacks on Blockchain Technology. Appl. Sci. 2023, 13, 2604. [Google Scholar] [CrossRef]
- Hayat, R.F.; Aurangzeb, S.; Aleem, M.; Srivastava, G.; Lin, J.C.-W. ML-DDoS: A Blockchain-Based Multilevel DDoS Mitigation Mechanism for IoT Environments. IEEE Trans. Eng. Manag. 2022, 2022, 1–14. [Google Scholar] [CrossRef]
- Wang, Q.; Xia, T.; Wang, D.; Ren, Y.; Miao, G.; Choo, K.-K.R. SDoS: Selfish Mining-Based Denial-of-Service Attack. IEEE Trans. Inform. Forensic Secur. 2022, 17, 3335–3349. [Google Scholar] [CrossRef]
- Mirkin, M.; Ji, Y.; Pang, J.; Klages-Mundt, A.; Eyal, I.; Juels, A. BDoS: Blockchain Denial-of-Service. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020; pp. 601–619. [Google Scholar] [CrossRef]
- Liu, J.; Wang, X.; Shen, S.; Yue, G.; Yu, S.; Li, M. A Bayesian Q -Learning Game for Dependable Task Offloading Against DDoS Attacks in Sensor Edge Cloud. IEEE Internet Things J. 2021, 8, 7546–7561. [Google Scholar] [CrossRef]
- Baek, U.-J.; Ji, S.-H.; Park, J.T.; Lee, M.-S.; Park, J.-S.; Kim, M.-S. DDoS Attack Detection on Bitcoin Ecosystem Using Deep-Learning. In Proceedings of the 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS), Matsue, Japan, 18–20 September 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Jiang, S.; Yang, L.; Gao, X.; Zhou, Y.; Feng, T.; Song, Y.; Liu, K.; Cheng, G. BSD-Guard: A Collaborative Blockchain-Based Approach for Detection and Mitigation of SDN-Targeted DDoS Attacks. Secur. Commun. Netw. 2022, 2022, 1608689. [Google Scholar] [CrossRef]
- Zhang, Y.; Gai, K.; Zhu, L.; Qiu, M. An Auxiliary Classifier GAN-Based DDoS Defense Solution in Blockchain-Based Software Defined Industrial Network. In Smart Computing and Communication; Qiu, M., Lu, Z., Zhang, C., Eds.; Lecture Notes in Computer Science; Springer Nature: Cham, Switzerland, 2023; Volume 13828, pp. 319–328. [Google Scholar] [CrossRef]
- Wu, S.; Chen, Y.; Li, M.; Luo, X.; Liu, Z.; Liu, L. Survive and Thrive: A Stochastic Game for DDoS Attacks in Bitcoin Mining Pools. IEEE/ACM Trans. Netw. 2020, 28, 874–887. [Google Scholar] [CrossRef]
- Johnson, B.; Laszka, A.; Grossklags, J.; Vasek, M.; Moore, T. Game-Theoretic Analysis of DDoS Attacks Against Bitcoin Mining Pools. In Financial Cryptography and Data Security; Böhme, R., Brenner, M., Moore, T., Smith, M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8438, pp. 72–86. [Google Scholar] [CrossRef]
- Boreiri, Z.; Azad, A.N. A Novel Consensus Protocol in Blockchain Network Based on Proof of Activity Protocol and Game Theory. In Proceedings of the 2022 8th International Conference on Web Research (ICWR), Tehran, Iran, 24–25 April 2022; pp. 82–87. [Google Scholar] [CrossRef]
- He, Q.; Wang, C.; Cui, G.; Li, B.; Zhou, R.; Zhou, Q.; Xiang, Y.; Jin, H.; Yang, Y. A Game-Theoretical Approach for Mitigating Edge DDoS Attack. IEEE Trans. Depend. Secur. Comput. 2022, 19, 2333–2348. [Google Scholar] [CrossRef]
- Amini, H.; Bichuch, M.; Feinstein, Z. Decentralized payment clearing using blockchain and optimal bidding. Eur. J. Oper. Res. 2022, 309, 409–420. [Google Scholar] [CrossRef]
- Khanum, S.; Mustafa, K. A Systematic Literature Review on Sensitive Data Protection in Blockchain Applications. Concurr. Comput. 2023, 35, e7422. [Google Scholar] [CrossRef]
- Saad, M.; Njilla, L.; Kamhoua, C.; Kim, J.; Nyang, D.; Mohaisen, A. Mempool Optimization for Defending Against DDoS Attacks in PoW-Based Blockchain Systems. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 285–292. [Google Scholar] [CrossRef]
- Tan, Y.; Huang, X.; Li, W. Does blockchain-based traceability system guarantee information authenticity? An evolutionary game approach. Int. J. Prod. Econ. 2023, 264, 108974. [Google Scholar] [CrossRef]
- Bao, Q.; Li, B.; Hu, T.; Sun, X. A Survey of Blockchain Consensus Safety and Security: State-of-the-Art, Challenges, and Future Work. J. Syst. Softw. 2023, 196, 111555. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A Survey on Blockchain Technology and Its Security. Blockchain Res. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Shah, Z.; Ullah, I.; Li, H.; Levula, A.; Khurshid, K. Blockchain-Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey. Sensors 2022, 22, 1094. [Google Scholar] [CrossRef] [PubMed]
- Yaish, A.; Qin, K.; Zhou, L.; Zohar, A.; Gervais, A. Speculative Denial-of-Service Attacks in Ethereum. Cryptol. ePrint Arch. 2023, 2023, 1–24. [Google Scholar]
- Guo, T.; Han, Y.; Feng, C. A Survey on Attack and Defense of Block-chain System. J. Softw. 2021, 32, 1495–1525. [Google Scholar] [CrossRef]
- Ilyas, B.; Kumar, A.; Setitra, M.A.; Bensalem, Z.A.; Lei, H. Prevention of DDoS Attacks Using an Optimized Deep Learning Approach in Blockchain Technology. Trans. Emerg. Telecommun. Technol. 2023, 34, e4729. [Google Scholar] [CrossRef]
- Yakubu, B.M.; Khan, M.I.; Khan, A.; Jabeen, F.; Jeon, G. Blockchain-Based DDoS Attack Mitigation Protocol for Device-to-Device Interaction in Smart Home. Digit. Commun. Netw. 2023, 9, 383–392. [Google Scholar] [CrossRef]
- Houda, Z.A.E.; Hafid, A.S.; Khoukhi, L. MiTFed: A Privacy-Preserving Collaborative Network Attack Mitigation Framework Based on Federated Learning Using SDN and Blockchain. IEEE Trans. Netw. Sci. Eng. 2023, 2023, 1985–2001. [Google Scholar] [CrossRef]
- Jmal, R.; Ghabri, W.; Guesmi, R.; Alshammari, B.M.; Alshammari, A.S.; Alsaif, H. Distributed Blockchain-SDN Secure IoT System Based on ANN to Mitigate DDoS Attacks. Appl. Sci. 2023, 13, 4953. [Google Scholar] [CrossRef]
- Li, Q.; Huang, H.; Li, R.; Lv, J.; Yuan, Z.; Ma, L.; Han, Y.; Jiang, Y. A comprehensive survey on DDoS defense systems: New trends and challenges. Comput. Netw. 2023, 233, 109895. [Google Scholar] [CrossRef]
- Zheng, R.; Ying, C.; Shao, J.; Wei, G.; Yan, H.; Kong, J.; Ren, Y.; Zhang, H.; Hou, W. New Game-Theoretic Analysis of DDoS Attacks Against Bitcoin Mining Pools with Defence Cost. In Network and System Security; Liu, J.K., Huang, X., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2019; Volume 11928, pp. 567–580. [Google Scholar] [CrossRef]
- Chaganti, R.; Boppana, R.V.; Ravi, V.; Munir, K.; Almutairi, M.; Rustam, F.; Lee, E.; Ashraf, I. A Comprehensive Review of Denial of Service Attacks in Blockchain Ecosystem and Open Challenges. IEEE Access 2023, 10, 96538–96555. [Google Scholar] [CrossRef]
- Guo, W.; Xu, J.; Pei, Y.; Yin, L.; Jiang, C.; Ge, N. A Distributed Collaborative Entrance Defense Framework Against DDoS Attacks on Satellite Internet. IEEE Internet Things J. 2022, 9, 15497–15510. [Google Scholar] [CrossRef]
- Wang, C.; Chu, X.; Qin, Y. Dissecting Mining Pools of Bitcoin Network: Measurement, Analysis and Modeling. IEEE Trans. Netw. Sci. Eng. 2022, 10, 398–412. [Google Scholar] [CrossRef]
- Sood, A. DDOS Attacks Against Bitcoin Mining Pools: A New Game-Theoretic Analysis With Defense Cost. In Proceedings of the 2023 3rd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 12–13 May 2023; pp. 2398–2402. [Google Scholar] [CrossRef]
- Kesavan, R.; Pitchai, K.M. Modeling and Simulation of Selfish Mining Attacks in Blockchain Network using Evolutionary Game Theory. In Proceedings of the 2023 Third International Conference on Artificial Intelligence and Smart Energy (ICAIS), Coimbatore, India, 2–4 February 2023; pp. 1016–1021. [Google Scholar] [CrossRef]
- Mighan, S.N.; Mišić, J.; Mišić, V.B.; Chang, X. An In-Depth Look at Forking-Based Attacks in Ethereum with PoW Consensus. IEEE Trans. Netw. Serv. Manag. 2023, 2023, 1–11. [Google Scholar] [CrossRef]
- Sigmund, K.; Nowak, M.A. Evolutionary game theory. Curr. Biol. 1999, 9, 503–505. [Google Scholar] [CrossRef]
- Hofbauer, J.; Sigmund, K. Evolutionary Game Dynamics. Bull. Am. Math. Soc. 2003, 40, 479–519. [Google Scholar] [CrossRef]
- Ye, M.; Han, Q.-L.; Ding, L.; Xu, S. Distributed Nash Equilibrium Seeking in Games With Partial Decision Information: A Survey. Proc. IEEE 2023, 111, 140–157. [Google Scholar] [CrossRef]
- Facchinei, F.; Kanzow, C. Generalized Nash equilibrium problems. Ann. Oper. Res. 2007, 5, 173–210. [Google Scholar] [CrossRef]
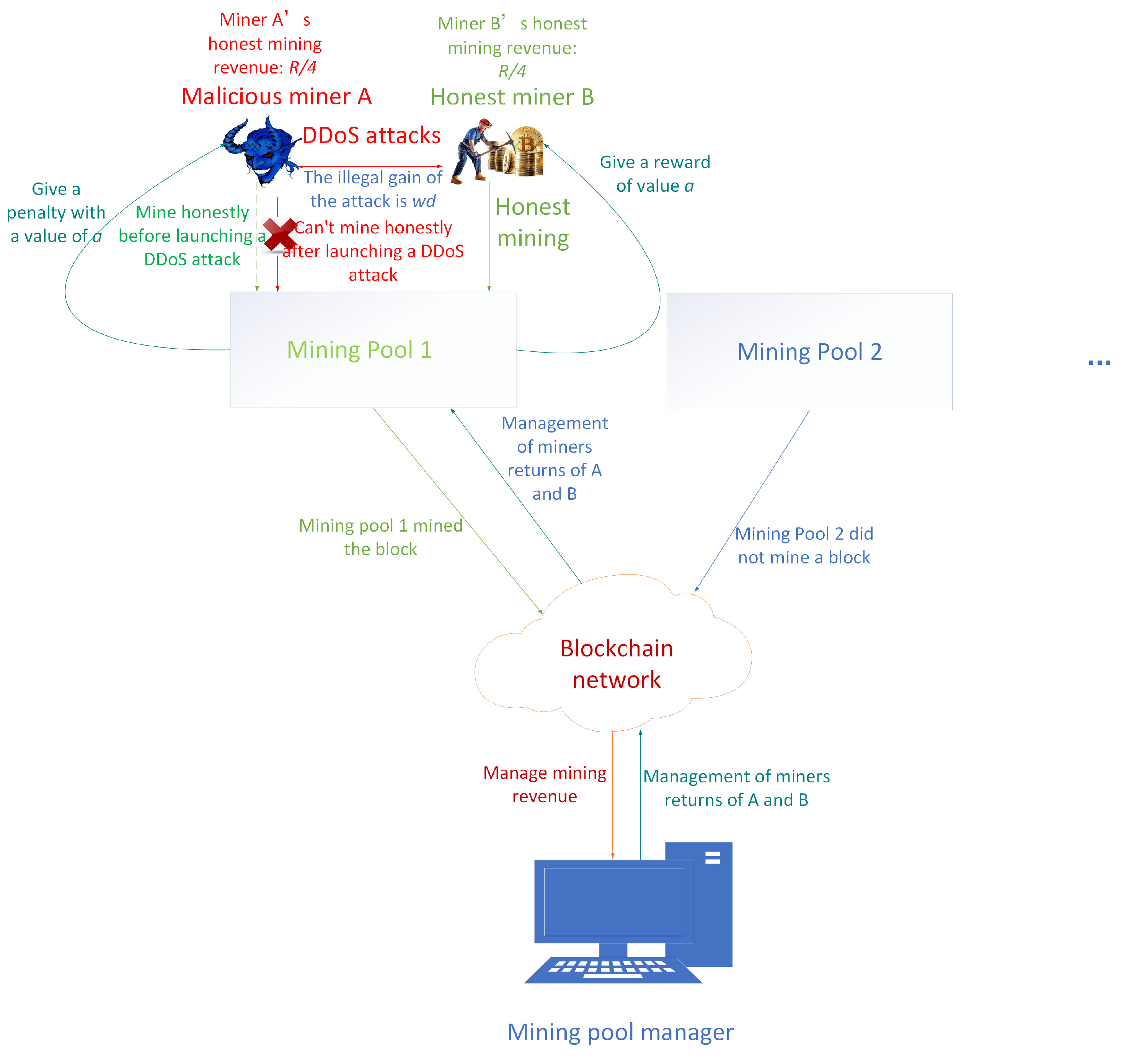
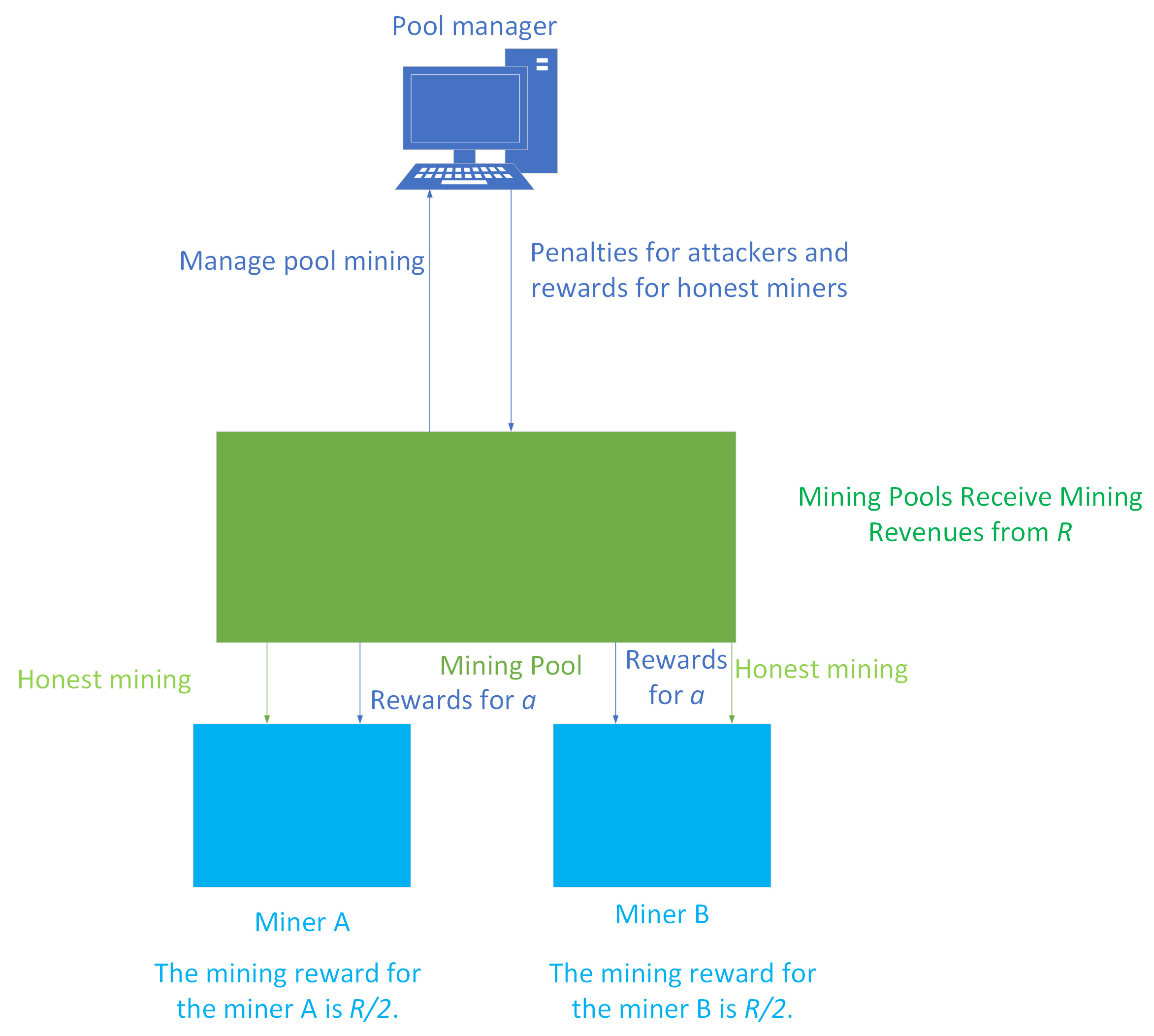
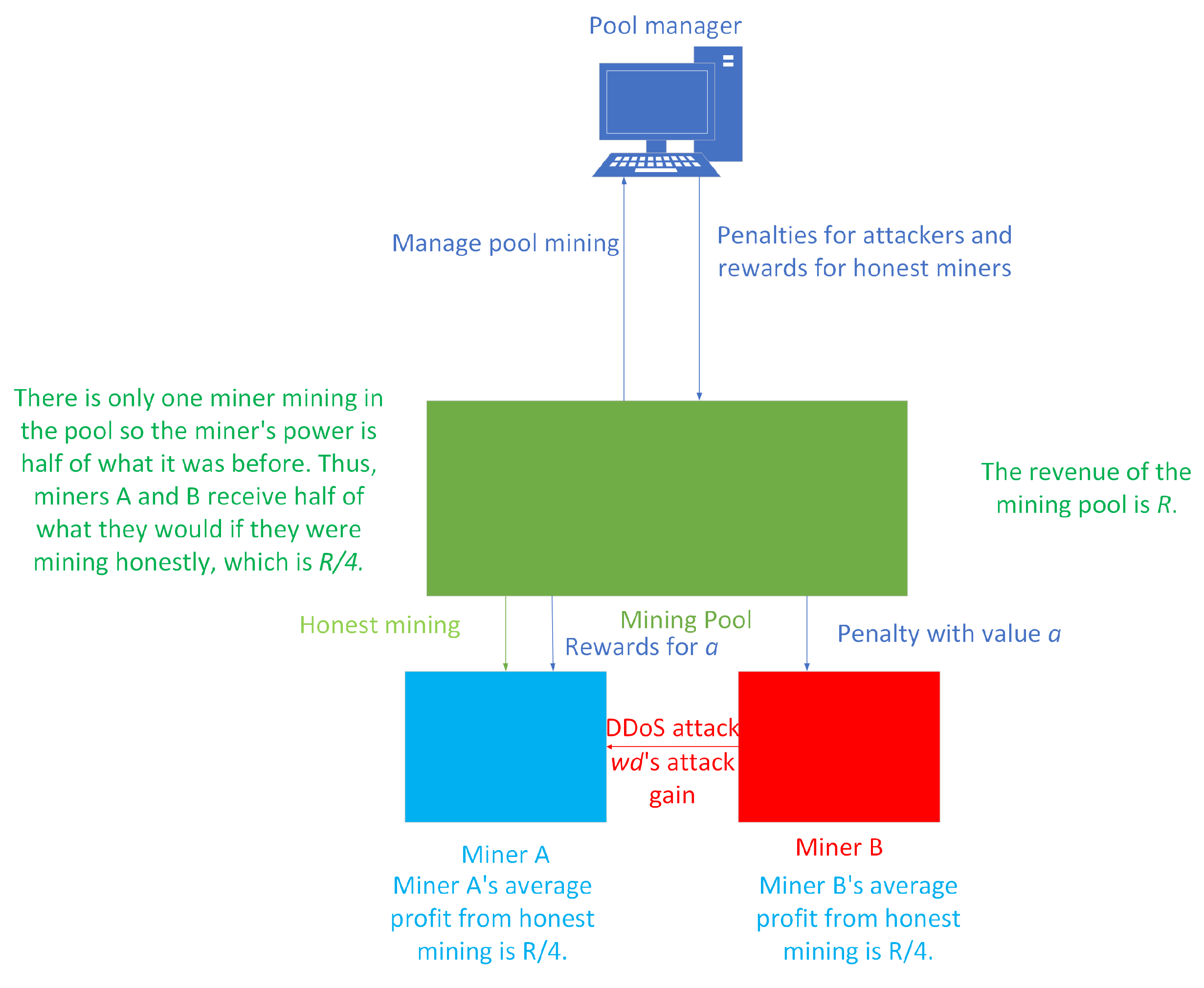

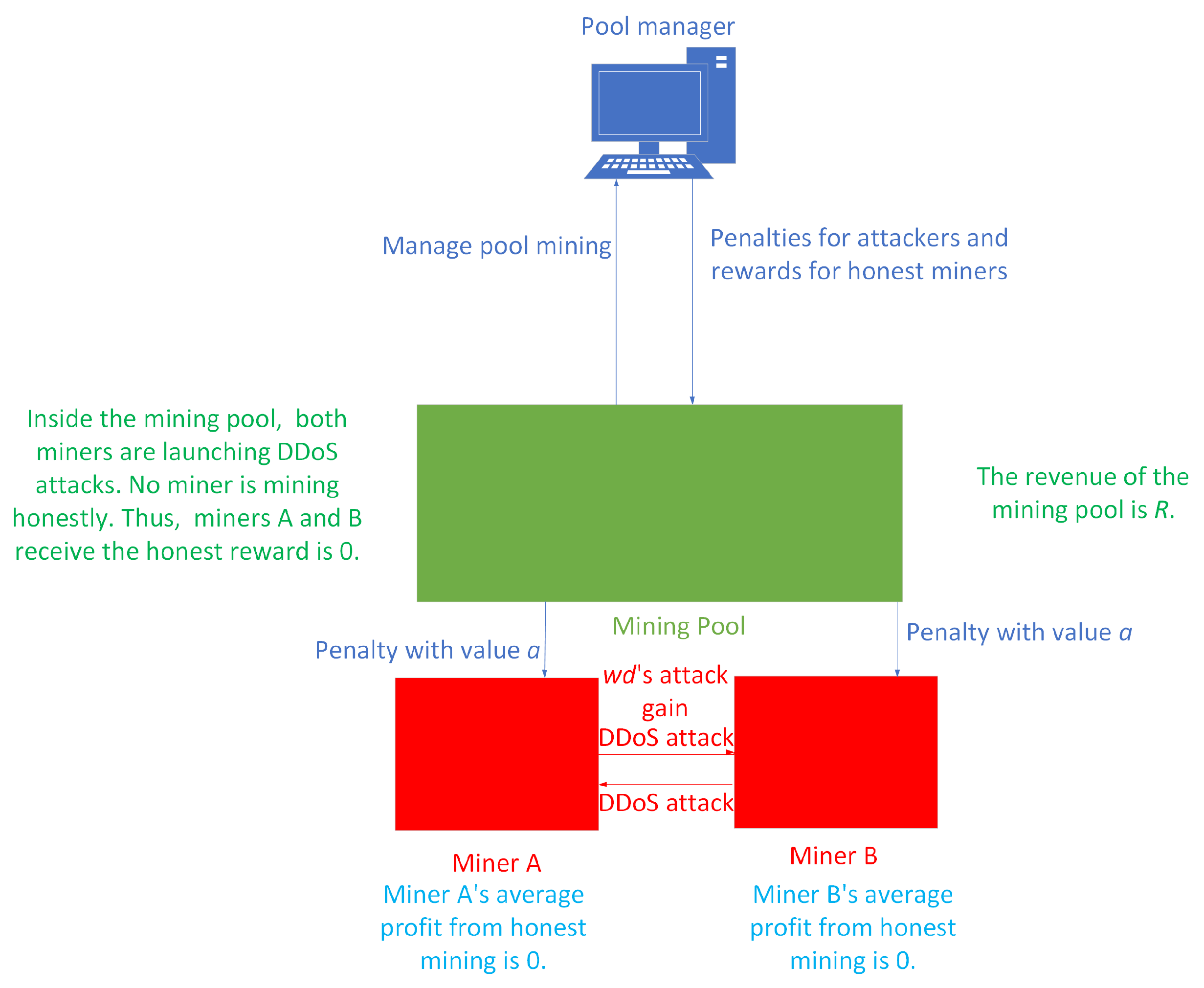
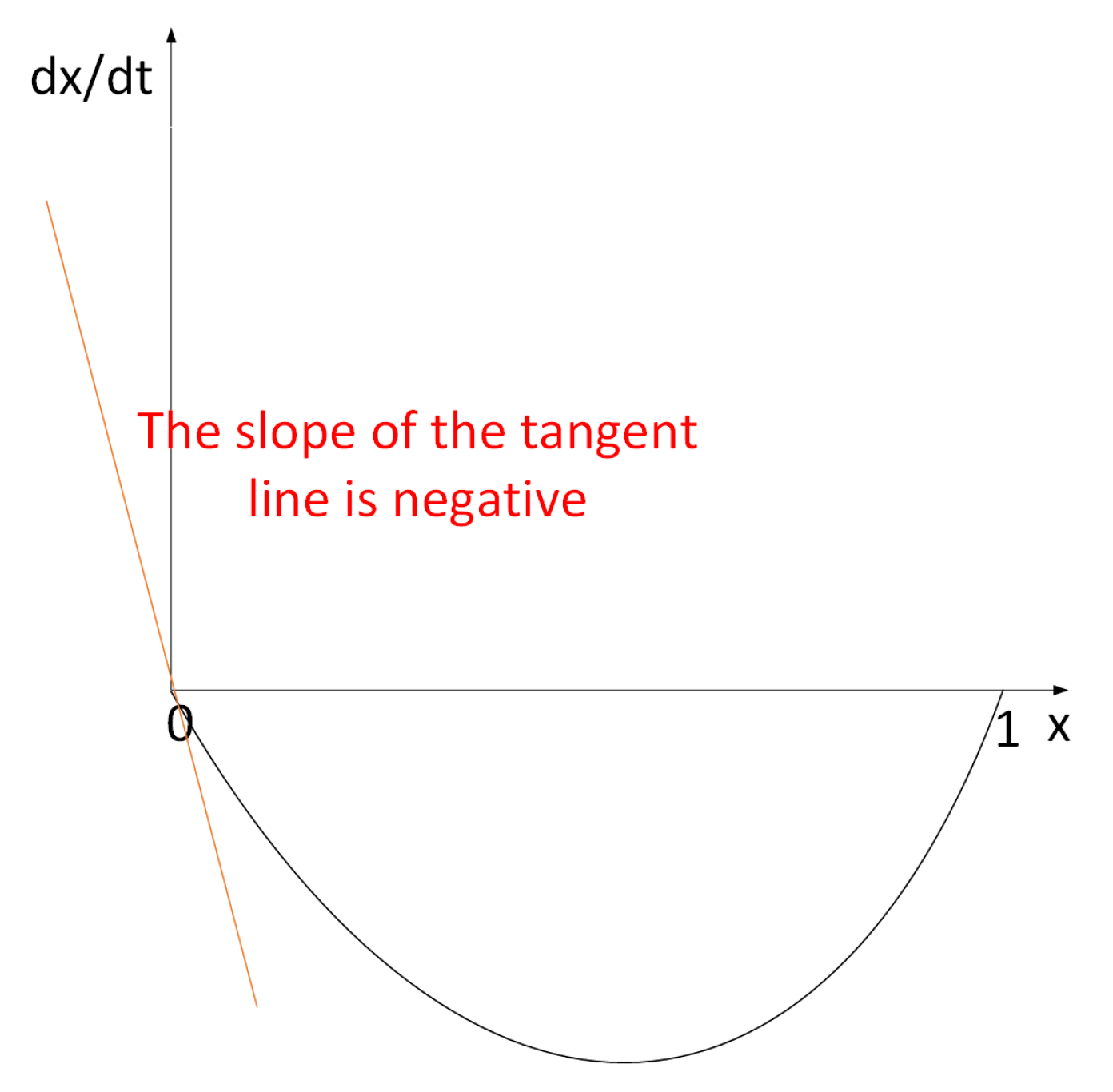
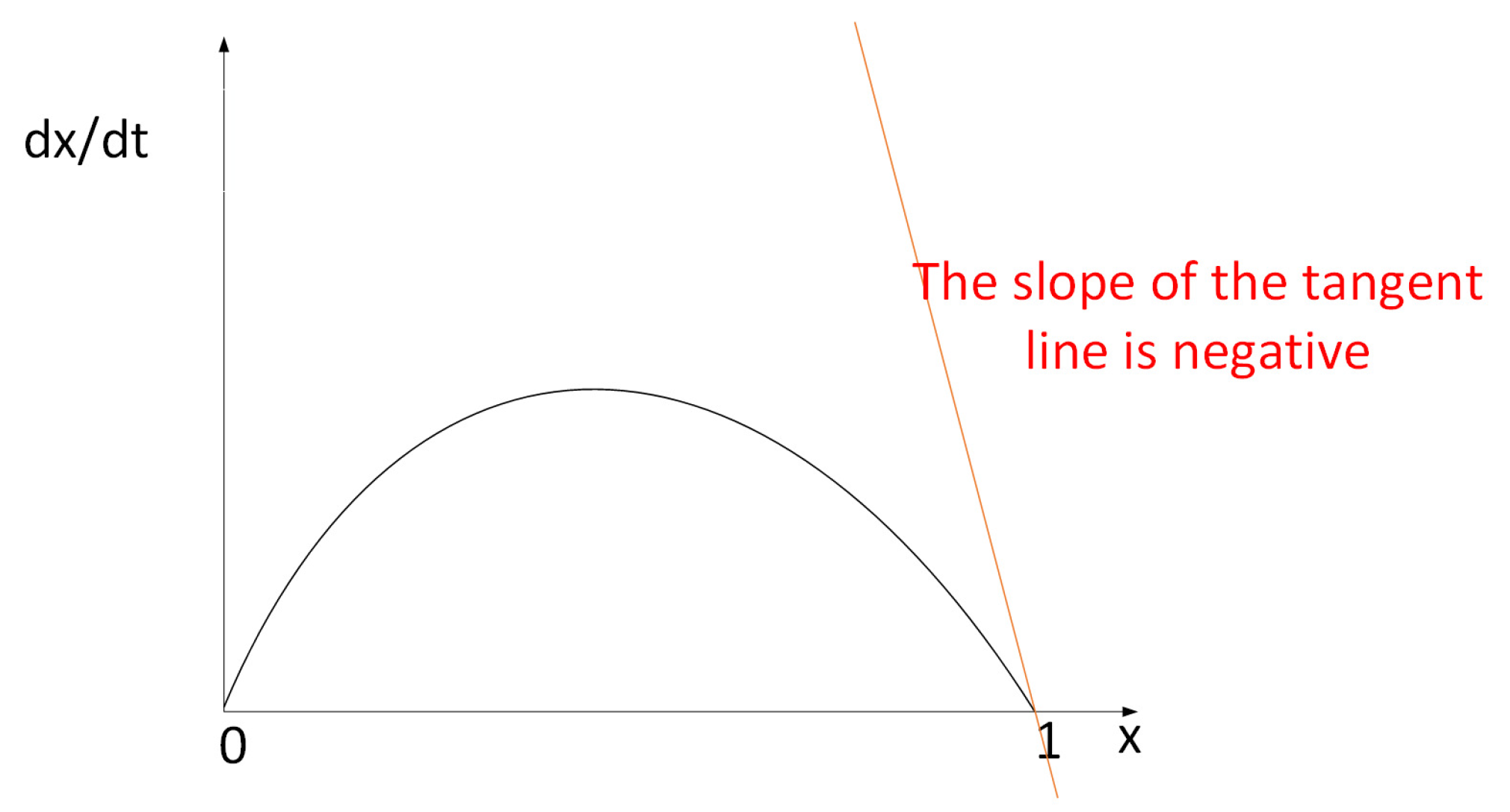




| Parameters | Description and Function of Parameters |
|---|---|
| R | The total profit allocated by the pool manager when a single mining pool mines in the blockchain system. |
| d | The illegal revenue gained by the attacker or the revenue lost by the attacked miner. |
| a | (1) When miners mine honestly with the same mining pool, the pool manager gives the reward to honest miners. (2) When a malicious miner launches a DDoS attack, the attacker is punished by the mining pool manager. |
| w | Network environment coefficient. |
| The miner returns from honest mining. | |
| The miner returns when launching DDoS attacks. | |
| Average returns for miners facing DDoS attacks. | |
| The dynamic equation of replication for x and time t. | |
| The first derivative of with respect to the probability x of honest mining. | |
| x | The probability that the miners mine honestly. |
| Solve the replicated dynamic equations to obtain the optimal policy values of multiple candidates that a miner may choose under the attack return model of this paper. | |
| Deterministic mining strategies under different degrees of network environment. |
| Pool B | Honest Mining (H) | DDoS Attacks (D) | |
|---|---|---|---|
| Pool A | |||
| Honest mining (H) | |||
| DDoS attacks (D) | |||
| Pool A | Honest Mining (H) | DDoS Attacks (D) | |
|---|---|---|---|
| Pool B | |||
| Honest mining (H) | |||
| DDoS attacks (D) | |||
| Network Environment Coefficient w | Evolutionary Steady-State Strategy | Analysis |
|---|---|---|
| A good network environment corresponds to Case A | ||
| A harsh network environment corresponds to Case B | ||
| A medium network environment corresponds to Case C |
| One Miner Honest Mining Profit in One Same Mining Pool R | Illegal Profits of Miners Launching DDoS Attacks d | Degree of Punishment or Reward by the Pool Manager a | Network Environment Coefficient w | Evolutionary Steady-State Strategy | Analysis |
|---|---|---|---|---|---|
| Nash equilibrium point for Experiment Section 4.1.1 of the static game and the solution obtained in experiment Section 4.2.1 correspond to case A in Section 3.3 | |||||
| Nash equilibrium point for Experiment Section 4.1.2 of the static game and the solution obtained in experiment Section 4.2.2 correspond to case C in Section 3.3 | |||||
| Nash equilibrium point for Experiment Section 4.1.3 of the static game and the solution obtained in experiment Section 4.2.3 correspond to case B in Section 3.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, X.; Huang, Z.; Wang, Q.; Jiang, X.; Chen, Y.; Wan, B. Analyzing Miners’ Dynamic Equilibrium in Blockchain Networks under DDoS Attacks. Electronics 2023, 12, 3903. https://doi.org/10.3390/electronics12183903
Liu X, Huang Z, Wang Q, Jiang X, Chen Y, Wan B. Analyzing Miners’ Dynamic Equilibrium in Blockchain Networks under DDoS Attacks. Electronics. 2023; 12(18):3903. https://doi.org/10.3390/electronics12183903
Chicago/Turabian StyleLiu, Xiao, Zhao Huang, Quan Wang, Xiaohong Jiang, Yin Chen, and Bo Wan. 2023. "Analyzing Miners’ Dynamic Equilibrium in Blockchain Networks under DDoS Attacks" Electronics 12, no. 18: 3903. https://doi.org/10.3390/electronics12183903
APA StyleLiu, X., Huang, Z., Wang, Q., Jiang, X., Chen, Y., & Wan, B. (2023). Analyzing Miners’ Dynamic Equilibrium in Blockchain Networks under DDoS Attacks. Electronics, 12(18), 3903. https://doi.org/10.3390/electronics12183903








