Image Encryption Algorithm Combining Chaotic Image Encryption and Convolutional Neural Network
Abstract
1. Introduction
- 1.
- This paper proposes an image encryption algorithm that combines chaotic image encryption with a CNN. It ensures image security and confidentiality while extracting high-level image features with improved robustness and generalization ability.
- 2.
- The effectiveness and superiority of the algorithm are demonstrated through experiments comparing it with other image encryption algorithms: traditional chaotic image encryption, CNN image encryption, and algorithms that combine them. The results show that the proposed algorithm achieves a higher encryption efficiency and image reconstruction quality while ensuring security, thereby providing a new approach for image encryption research.
- 3.
- The paper discusses the optimization and future development of the algorithm, including improving encryption efficiency and performance, and applying it to other fields. The proposed algorithm has valuable application not only in image encryption but also in areas such as video and voice encryption.
2. Related Work
3. Method
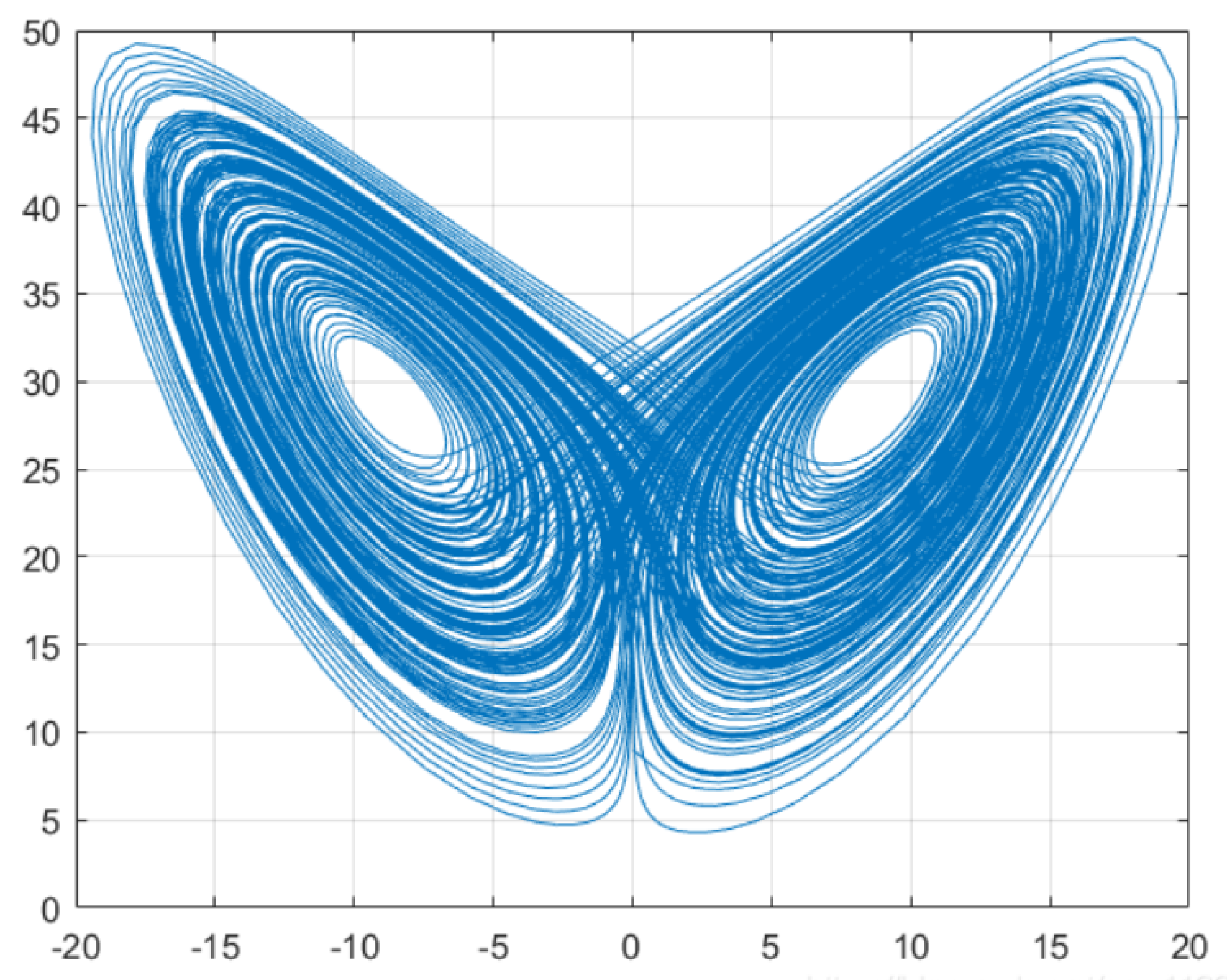
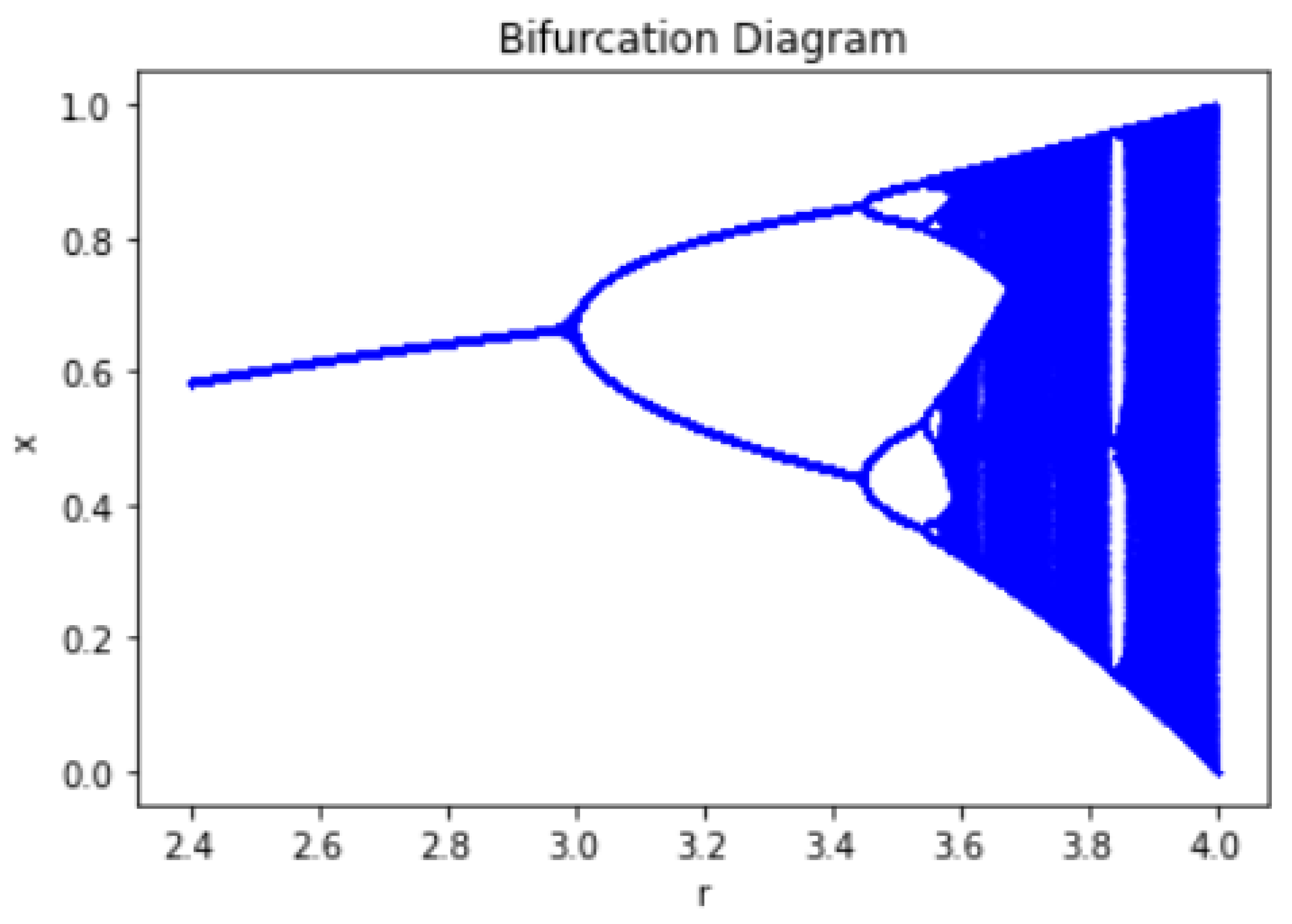
3.1. Chaotic Image Encryption
3.2. Convolutional Neural Networks
| Algorithm 1: Convolutional Neural Network (CNN) Training |
| 1: procedure CNN-TRAIN |
| 2: Initialize CNN parameters |
| 3: for to do |
| 4: for all training examples do |
| 5: Forward propagation: |
| 6: Compute the activations for each layer |
| 7: Backward propagation: |
| 8: Compute the gradients for each layer |
| 9: Update the CNN parameters using gradient descent |
| 10: end for |
| 11: end for |
| 12: end procedure |
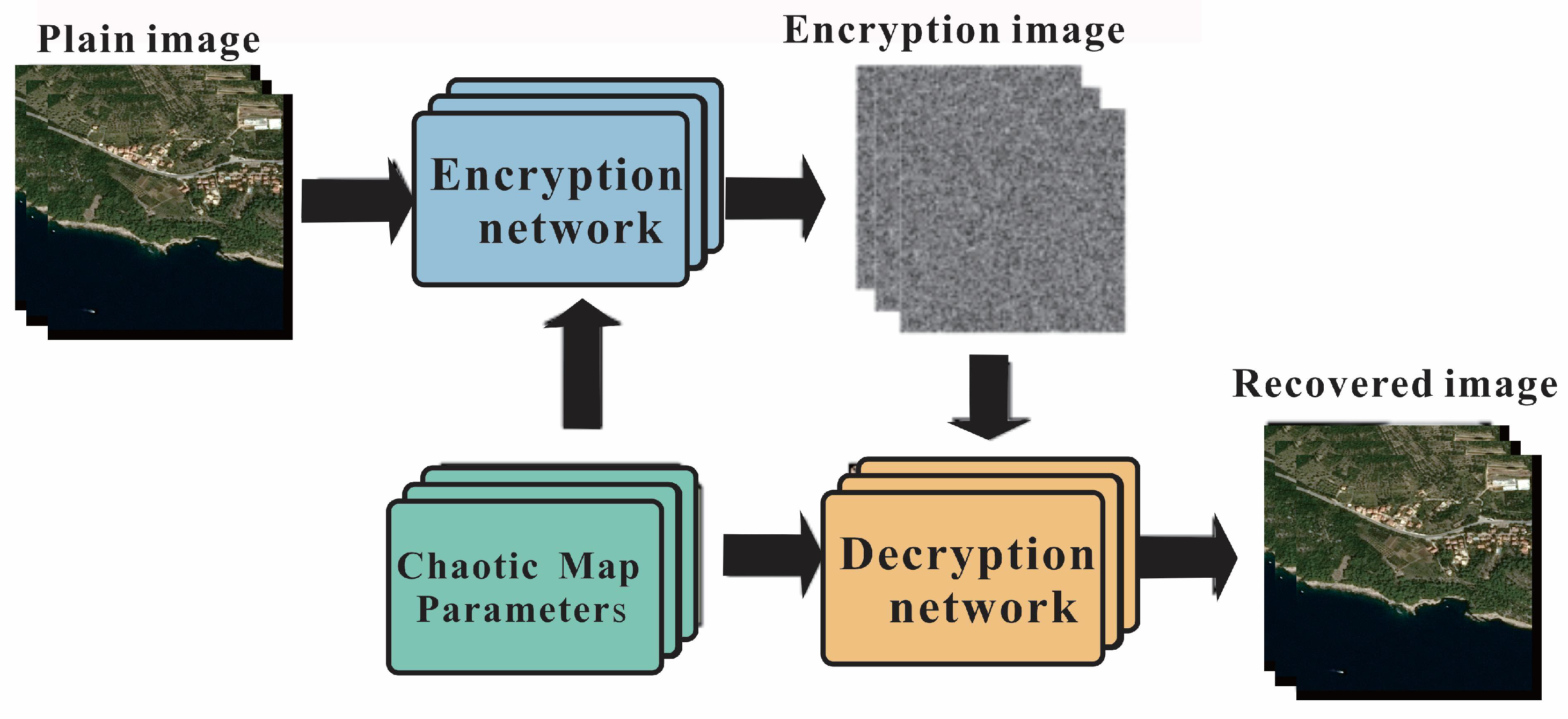
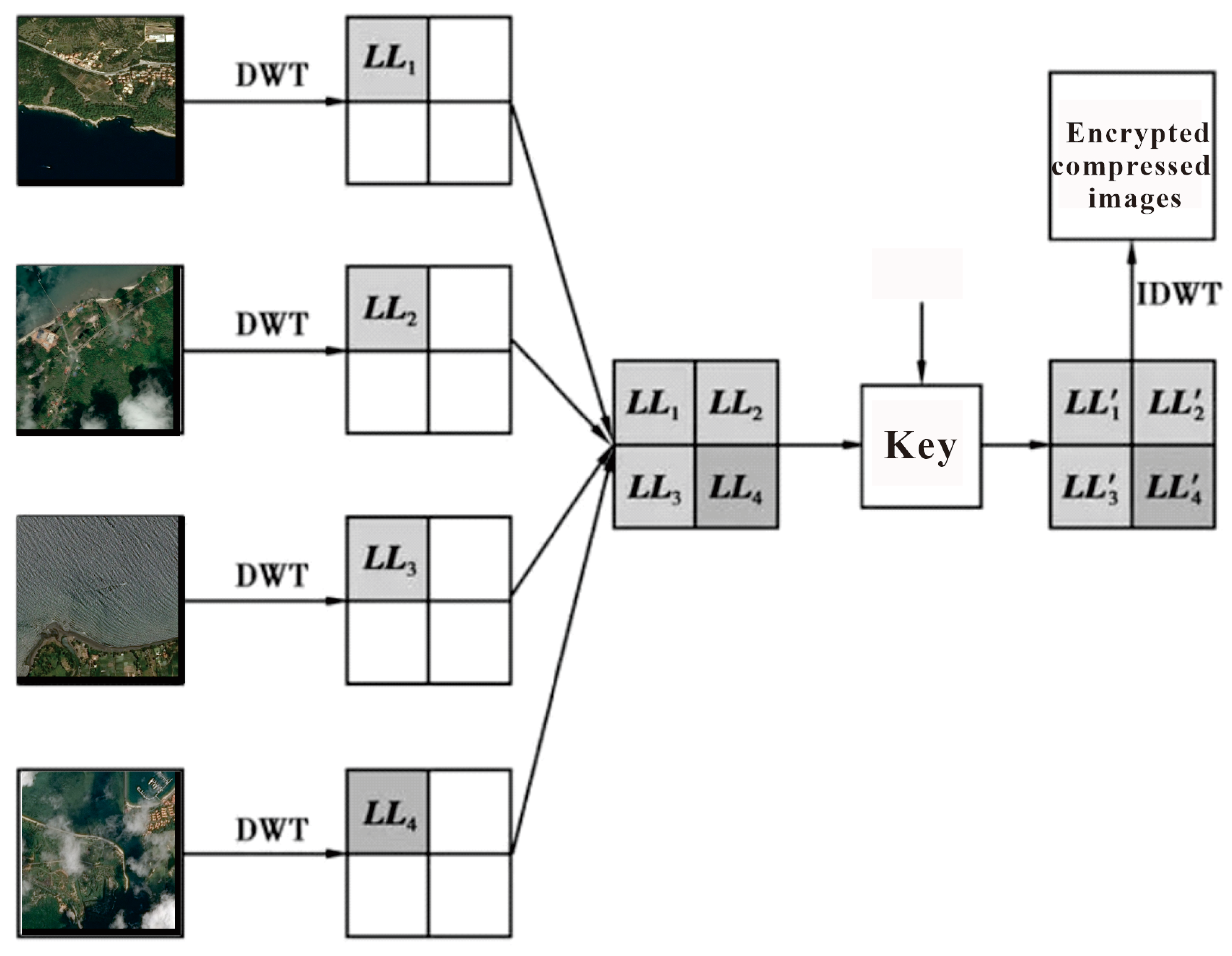
3.3. Chaotic Image Encryption Combined with a CNN
4. Experimental Platform
4.1. Data Set and Experimental Setup
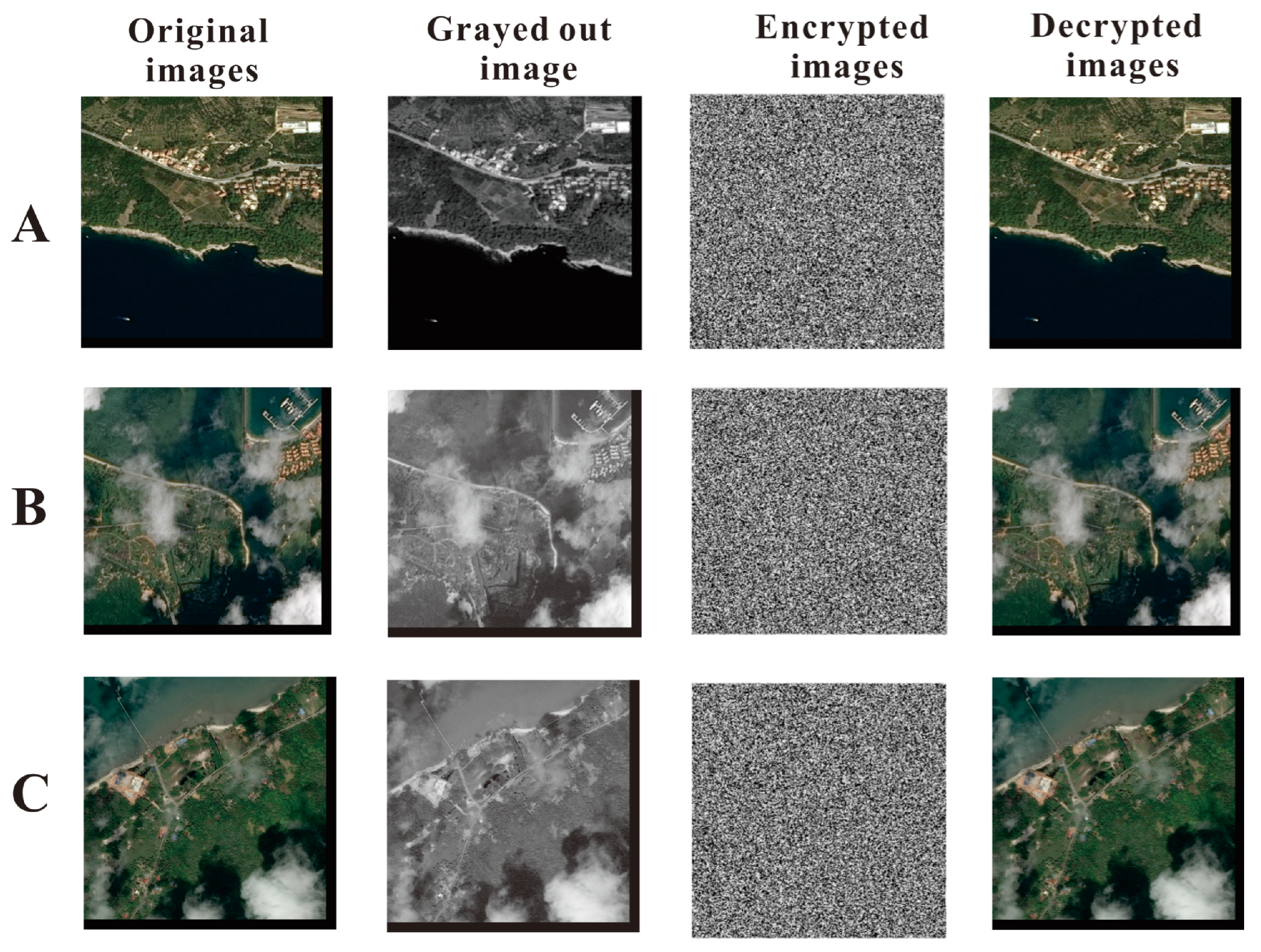
4.2. Experimental Results of Image Encryption and Decryption
5. Result
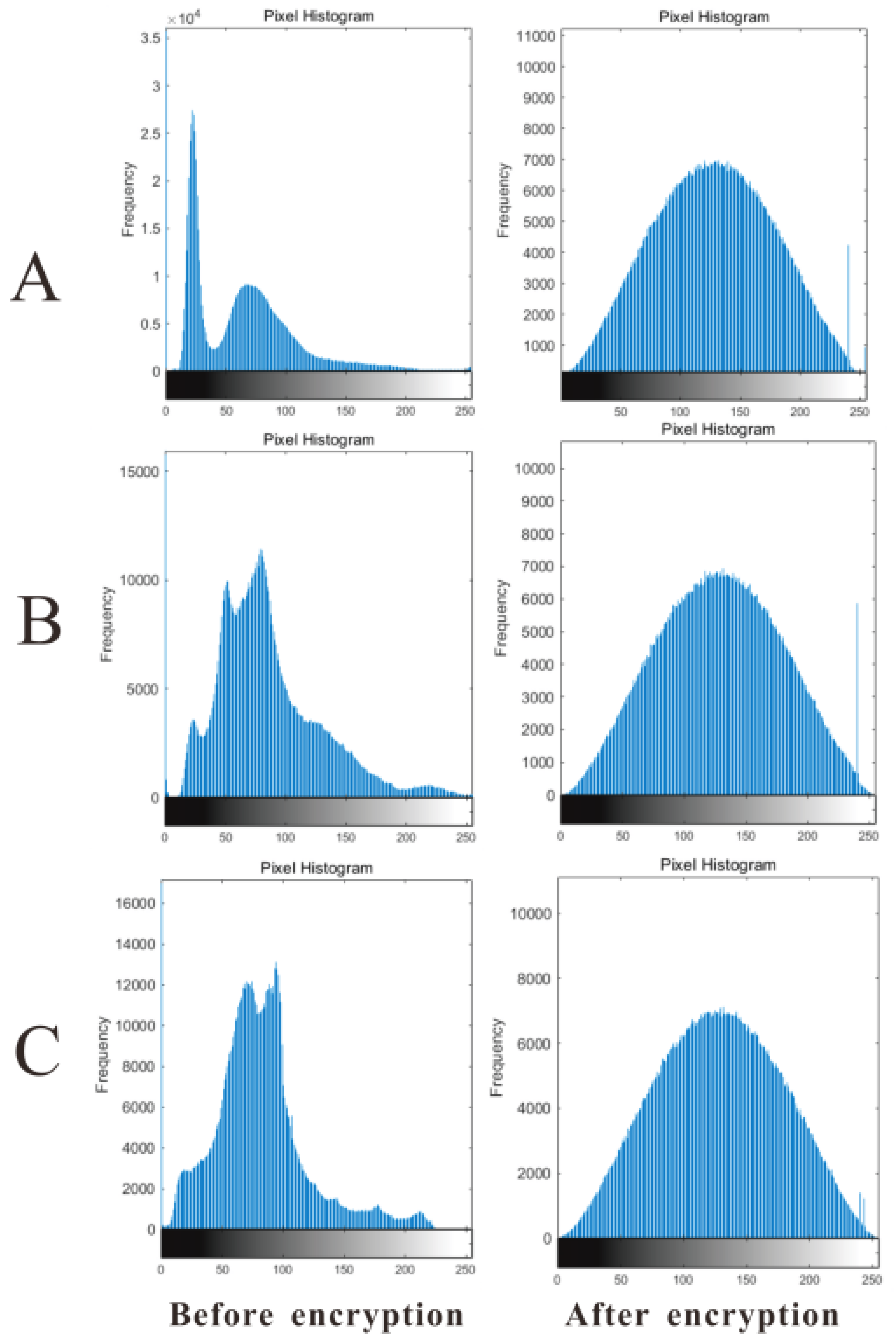
5.1. Encryption Quality and Security Assessment
5.2. Encryption Performance Improvement Evaluation
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hashem, I.A.T.; Yaqoob, I.; Anuar, N.B.; Mokhtar, S.; Gani, A.; Khan, S.U. The rise of “big data” on cloud computing: Review and open research issues. Inf. Syst. 2015, 47, 98–115. [Google Scholar] [CrossRef]
- Garfinkel, S.; Farrell, P.; Roussev, V.; Dinolt, G. Bringing science to digital forensics with standardized forensic corpora. Digit. Investig. 2009, 6, S2–S11. [Google Scholar] [CrossRef]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Foxe, J.J.; Doniger, G.M.; Javitt, D.C. Early visual processing deficits in schizophrenia: Impaired p1 generation revealed by high-density electrical mapping. Neuroreport 2001, 12, 3815–3820. [Google Scholar] [CrossRef]
- Li, J.-P.O.; Liu, H.; Ting, D.S.; Jeon, S.; Chan, R.P.; Kim, J.E.; Sim, D.A.; Thomas, P.B.; Lin, H.; Chen, Y.; et al. Digital technology, tele-medicine and artificial intelligence in ophthalmology: A global perspective. Prog. Retin. Eye Res. 2021, 82, 100900. [Google Scholar] [CrossRef]
- Garibay, O.O.; Winslow, B.; Andolina, S.; Antona, M.; Bodenschatz, A.; Coursaris, C.; Falco, G.; Fiore, S.M.; Garibay, I.; Grieman, K.; et al. Six human-centered artificial intelligence grand challenges. Int. J. Hum.-Comput. Interact. 2023, 39, 391–437. [Google Scholar] [CrossRef]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Fairaccess: A new blockchain-based access control framework for the internet of things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Cheddad, A.; Condell, J.; Curran, K.; Kevitt, P.M. Digital image steganography: Survey and analysis of current methods. Signal Process. 2010, 90, 727–752. [Google Scholar] [CrossRef]
- Dichtl, M.; Golić, J.D. High-speed true random number generation with logic gates only. In Cryptographic Hardware and Embedded Systems-CHES 2007, Proceedings of the 9th International Workshop, Vienna, Austria, 10–13 September 2007; Proceedings 9; Springer: Berlin/Heidelberg, Germany, 2007; pp. 45–62. [Google Scholar]
- Ullah, S.; Zheng, J.; Din, N.; Hussain, M.T.; Ullah, F.; Yousaf, M. Elliptic curve cryptography; applications, challenges, recent advances, and future trends: A comprehensive survey. Comput. Sci. Rev. 2023, 47, 100530. [Google Scholar] [CrossRef]
- Jahanshahi, H.; Yousefpour, A.; Munoz-Pacheco, J.M.; Moroz, I.; Wei, Z.; Castillo, O. A new multi-stable fractional-order four-dimensional system with self-excited and hidden chaotic attractors: Dynamic analysis and adaptive synchronization using a novel fuzzy adaptive sliding mode control method. Appl. Soft Comput. 2020, 87, 105943. [Google Scholar] [CrossRef]
- Kengne, J.; Njitacke, Z.; Fotsin, H. Dynamical analysis of a simple autonomous jerk system with multiple attractors. Nonlinear Dyn. 2016, 83, 751–765. [Google Scholar] [CrossRef]
- Pecora, L.M.; Carroll, T.L.; Johnson, G.A.; Mar, D.J.; Heagy, J.F. Fundamentals of synchronization in chaotic systems, concepts, and applications. Chaos Interdiscip. J. Nonlinear Sci. 1997, 7, 520–543. [Google Scholar] [CrossRef] [PubMed]
- Qiu, H.; Xu, X.; Jiang, Z.; Sun, K.; Cao, C. Dynamical behaviors, circuit design, and synchronization of a novel symmetric chaotic system with coexisting attractors. Sci. Rep. 2023, 13, 1893. [Google Scholar] [CrossRef] [PubMed]
- Farhan, A.K.; Al-Saidi, N.M.; Maolood, A.T.; Nazarimehr, F.; Hussain, I. Entropy analysis and image encryption application based on a new chaotic system crossing a cylinder. Entropy 2019, 21, 958. [Google Scholar] [CrossRef]
- Pulliam, T.H.; Vastano, J.A. Transition to chaos in an open unforced 2d flow. J. Comput. Phys. 1993, 105, 133–149. [Google Scholar] [CrossRef]
- Huhn, F.; Magri, L. Stability, sensitivity and optimisation of chaotic acoustic oscillations. J. Fluid Mech. 2020, 882, A24. [Google Scholar] [CrossRef]
- Toral, R.; Mirasso, C.R.; Hernández-Garcıa, E.; Piro, O. Analytical and numerical studies of noise-induced synchronization of chaotic systems. Chaos Interdiscip. J. Nonlinear Sci. 2001, 11, 665–673. [Google Scholar] [CrossRef]
- Stolova, N.I. Cognitive Linguistics and Lexical Change; John Benjamins: Amsterdam, The Netherlands; Philadelphia, PA, USA, 2015; pp. 1–269. [Google Scholar]
- Brindha, M.; Gounden, N.A. A chaos based image encryption and lossless compression algorithm using hash table and chinese remainder theorem. Appl. Soft Comput. 2016, 40, 379–390. [Google Scholar] [CrossRef]
- Wang, X.-Y.; Li, P.; Zhang, Y.-Q.; Liu, L.-Y.; Zhang, H.; Wang, X. A novel color image encryption scheme using dna permutation based on the lorenz system. Multimed. Tools Appl. 2018, 77, 6243–6265. [Google Scholar] [CrossRef]
- Tang, M.; Zeng, G.; Yang, Y.; Chen, J. A hyperchaotic image encryption scheme based on the triple dislocation of the liu and lorenz system. Optik 2022, 261, 169133. [Google Scholar] [CrossRef]
- Zhao, Z.; Wang, S.; Wang, S.; Zhang, X.; Ma, S.; Yang, J. Enhanced bi-prediction with convolutional neural network for high-efficiency video coding. IEEE Trans. Circuits Syst. Video Technol. 2018, 29, 3291–3301. [Google Scholar] [CrossRef]
- Wu, Y.; Zhang, L.; Berretti, S.; Wan, S. Medical image encryption by content-aware dna computing for secure healthcare. IEEE Trans. Ind. Inform. 2022, 19, 2089–2098. [Google Scholar] [CrossRef]
- Liu, Y.; Li, Q.; Sun, Z. Attribute-aware face aging with wavelet-based generative adversarial networks. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, LA, USA, 18–24 June 2019; pp. 11877–11886. [Google Scholar]
- Cheng, G.; Wang, C.; Chen, H. A novel color image encryption algorithm based on hyperchaotic system and permutation-diffusion architecture. Int. J. Bifurc. Chaos 2019, 29, 1950115. [Google Scholar] [CrossRef]
- Li, C.; Zhang, X. Abnormal signal recognition method of wearable sensor based on machine learning. In IoT and Big Data Technologies for Health Care; Springer: Berlin/Heidelberg, Germany, 2022; pp. 322–338. [Google Scholar]
- Man, Z.; Li, J.; Di, X.; Sheng, Y.; Liu, Z. Double image encryption algorithm based on neural network and chaos. Chaos Solitons Fractals 2021, 152, 111318. [Google Scholar] [CrossRef]
- Mao, Y.; Chen, G.; Lian, S. A novel fast image encryption scheme based on 3d chaotic baker maps. Int. J. Bifurc. Chaos 2004, 14, 3613–3624. [Google Scholar] [CrossRef]
- Lai, Q.; Hu, G.; Erkan, U.; Toktas, A. High-efficiency medical image encryption method based on 2d logistic-gaussian hyperchaotic map. Appl. Math. Comput. 2023, 442, 127738. [Google Scholar] [CrossRef]
- Zhang, M.; Xie, K.; Zhang, Y.-H.; Wen, C.; He, J.-B. Fine segmentation on faces with masks based on a multistep iterative segmentation algorithm. IEEE Access 2022, 10, 75742–75753. [Google Scholar] [CrossRef]
- Kumar, A.; Raghava, N. An efficient image encryption scheme using elementary cellular automata with novel permutation box. Multimed. Tools Appl. 2021, 80, 21727–21750. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Xian, Y. Image encryption algorithm based on a 2d-clss hyperchaotic map using simultaneous permutation and diffusion. Inf. Sci. 2022, 605, 71–85. [Google Scholar] [CrossRef]
- Cabán, C.C.T.; Yang, M.; Lai, C.; Yang, L.; Subach, F.V.; Smith, B.O.; Piatkevich, K.D.; Boyden, E.S. Tuning the sensitivity of genetically encoded fluorescent potassium indicators through structure-guided and genome mining strategies. ACS Sens. 2022, 7, 1336–1346. [Google Scholar] [CrossRef]
- Yao, W.; Gao, K.; Zhang, Z.; Cui, L.; Zhang, J. An image encryption algorithm based on a 3d chaotic hopfield neural network and random row–column permutation. Front. Phys. 2023, 11, 1162887. [Google Scholar] [CrossRef]
- Papadaki, S.; Wang, X.; Wang, Y.; Zhang, H.; Jia, S.; Liu, S.; Yang, M.; Zhang, D.; Jia, J.-M.; Köster, R.W.; et al. Dual-expression system for blue fluorescent protein optimization. Sci. Rep. 2022, 12, 10190. [Google Scholar] [CrossRef]
- Wu, S.; Wang, J.; Ping, Y.; Zhang, X. Research on individual recognition and matching of whale and dolphin based on efficientnet model. In Proceedings of the 2022 3rd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Xi’an, China, 15–17 July 2022; pp. 635–638. [Google Scholar]
- Zhang, Y.-H.; Wen, C.; Zhang, M.; Xie, K.; He, J.-B. Fast 3d visualization of massive geological data based on clustering index fusion. IEEE Access 2022, 10, 28821–28831. [Google Scholar] [CrossRef]
- Zou, Z.; Careem, M.; Dutta, A.; Thawdar, N. Joint spatio-temporal precoding for practical non-stationary wireless channels. IEEE Trans. Commun. 2023, 71, 2396–2409. [Google Scholar] [CrossRef]
- Zou, Z.; Wei, X.; Saha, D.; Dutta, A.; Hellbourg, G. Scisrs: Signal cancellation using intelligent surfaces for radio astronomy services. In Proceedings of the GLOBECOM 2022–2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 4238–4243. [Google Scholar]
- Zhang, T.; Zhou, Y.; Chen, C.P. A new combined chaotic system for image encryption. In Proceedings of the 2012 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Zhangjiajie, China, 25–27 May 2012; Volume 2, pp. 331–335. [Google Scholar]
- Heron, S. Advanced encryption standard (aes). Netw. Secur. 2009, 2009, 8–12. [Google Scholar] [CrossRef]
- Singh, G. A study of encryption algorithms (rsa, des, 3des and aes) for information security. Int. J. Comput. Appl. 2013, 67, 19. [Google Scholar] [CrossRef]
- Rachmawati, D.; Budiman, M.A. On using the first variant of dependent rsa encryption scheme to secure text: A tutorial. J. Phys. Conf. Ser. 2020, 1542, 012024. [Google Scholar] [CrossRef]




| Image | PSNR (dB) | SSIM | HU |
|---|---|---|---|
| Original Image | - | - | - |
| Traditional Chaotic Encryption [41] | 35.21 | 0.92 | 0.78 |
| AES Encryption [42] | 41.52 | 0.96 | 0.88 |
| DES Encryption [43] | 38.90 | 0.94 | 0.82 |
| RSA Encryption [44] | 37.45 | 0.93 | 0.75 |
| Chaotic + CNN Encryption | 41.78 | 0.95 | 0.92 |
| Method | Computational Performance | Encryption Speed | Decryption Speed |
|---|---|---|---|
| Traditional Chaotic Encryption | High | Moderate | Moderate |
| CNN + Chaotic Encryption | Excellent | Fast | Fast |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, L.; Du, J.; Fu, C.; Song, W. Image Encryption Algorithm Combining Chaotic Image Encryption and Convolutional Neural Network. Electronics 2023, 12, 3455. https://doi.org/10.3390/electronics12163455
Feng L, Du J, Fu C, Song W. Image Encryption Algorithm Combining Chaotic Image Encryption and Convolutional Neural Network. Electronics. 2023; 12(16):3455. https://doi.org/10.3390/electronics12163455
Chicago/Turabian StyleFeng, Luoyin, Jize Du, Chong Fu, and Wei Song. 2023. "Image Encryption Algorithm Combining Chaotic Image Encryption and Convolutional Neural Network" Electronics 12, no. 16: 3455. https://doi.org/10.3390/electronics12163455
APA StyleFeng, L., Du, J., Fu, C., & Song, W. (2023). Image Encryption Algorithm Combining Chaotic Image Encryption and Convolutional Neural Network. Electronics, 12(16), 3455. https://doi.org/10.3390/electronics12163455







