Aggregate Entity Authentication Identifying Invalid Entities with Group Testing
Abstract
1. Introduction
1.1. Background
1.2. Our Contribution
1.3. Related Work
1.4. Organization
2. Preliminaries
2.1. Notation
2.2. MAC Function and Pseudorandom Function
2.3. Cryptographic Hash Function
2.4. Group Testing
- (1)
- .
- (2)
- For , do the followings: (a) ; (b) For , if the result of is negative, then .
- (3)
- Output .
3. Aggregate MAC
3.1. Syntax
- is a key-generation algorithm such that , where is a security parameter and . Each entity is assigned a secret key independently generated by .
- is a tagging algorithm such that , where and .
- is an aggregate algorithm such that where for and . ’s are required to be distinct from each other. It is often the case that T depends only on .
- is a verification algorithm such that , where and for , if and otherwise, and . ’s are required to be distinct from each other. With respect to , the pair and T are valid if and invalid otherwise.
3.2. Security Requirement
3.2.1. Unforgeability
- is called a tagging oracle. It returns in response to a query , where is the key of the entity .
- is called a key-disclosure oracle. It accepts a query and returns .
- is called a verification oracle. It accepts a query and returns
3.2.2. Soundness
- for ,
- , and
- .
3.3. Aggregate MAC Scheme by Katz and Lindell
- Each entity is given a secret key .
- The tagging algorithm returns a tag in response to .
- The aggregate algorithm returns an aggregate tag in response to .
- Taking and as input, the verification algorithm outputs 1 iff .
3.4. Aggregate MAC Scheme Using Hashing
- The key generation and tagging algorithms are identical to those of .
- For , the aggregate algorithm returns . For the uniqueness of the aggregate tag T, are assumed to be ordered in a lexicographic order.
- Taking and as input, the verification algorithm outputs 1 if and 0 otherwise.
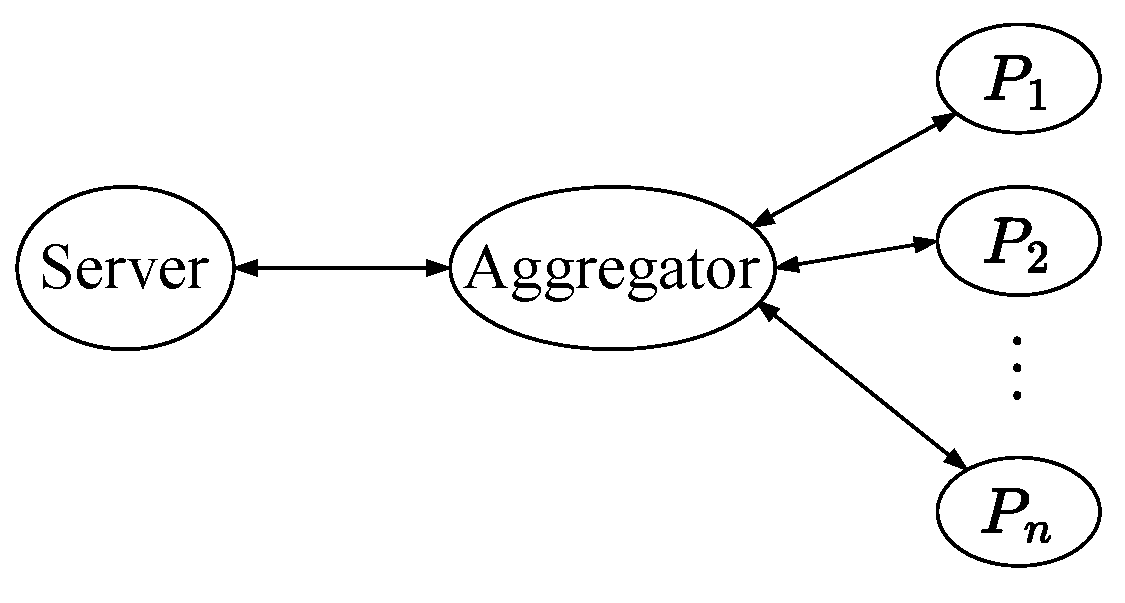
4. Group-Testing Aggregate Entity Authentication
4.1. Scheme
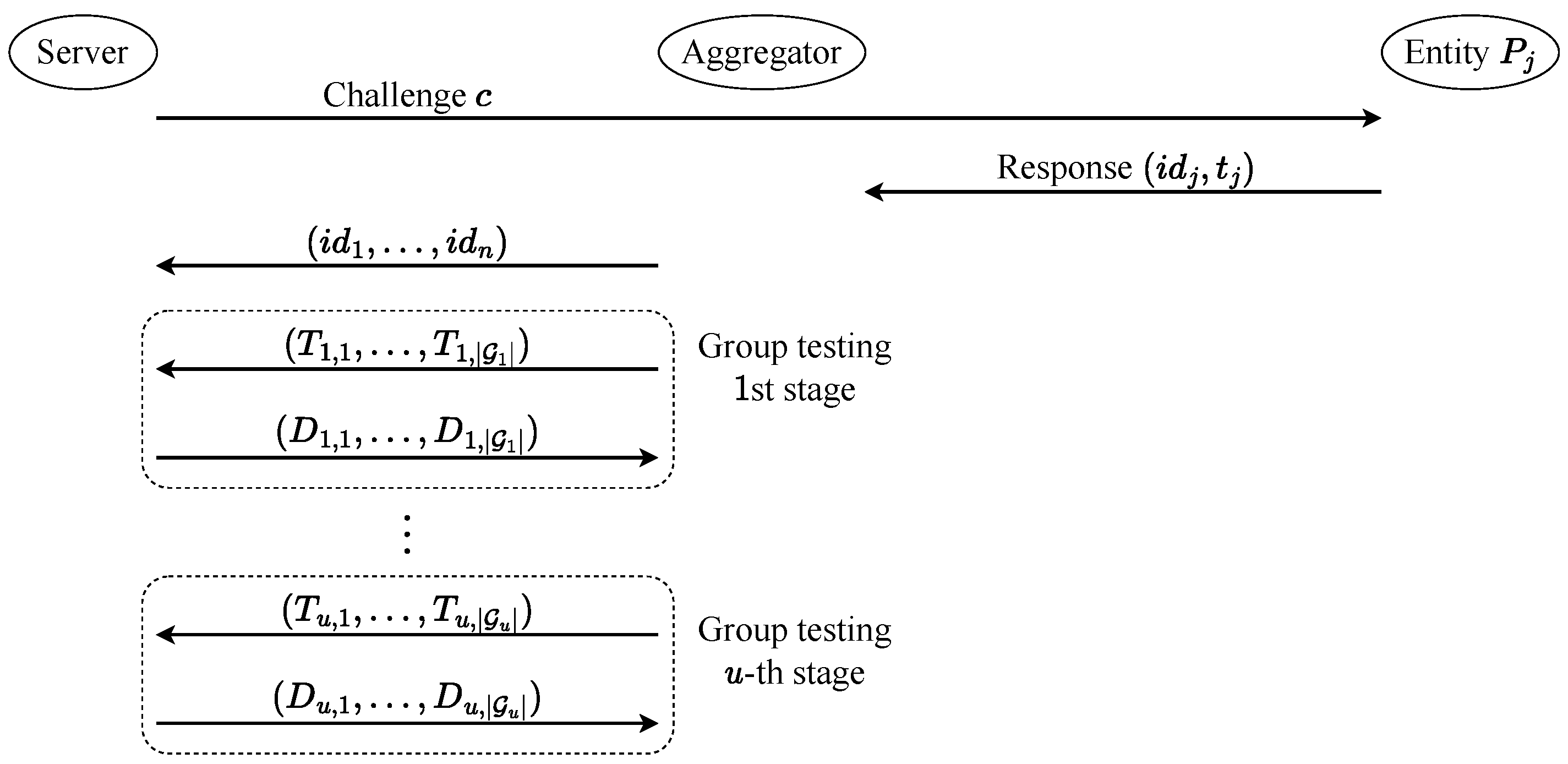
- Step 1:
- The server sends a challenge to the aggregator, which broadcasts it to the entities.
- Step 2:
- In response to c, each entity returns to the aggregator, where .
- Step 3:
- The aggregator sends to the server.
- Step 4:
- With the help of the aggregator, the server identifies the valid entities using , , and in the following way:
- 1.
- .
- 2.
- Let u be the number of stages of . For ,
- (a)
- According to , both the server and the aggregator determine the set of tests .
- (b)
- The aggregator computes for and sends to the server.
- (c)
- The server first sets . Then, for , it computesand if . Finally, it sends to the aggregator.
- 3.
- Output .
4.2. Security Requirement
4.2.1. Impersonation Resistance
4.2.2. Completeness and Soundness
5. Discussion on Security
5.1. Impersonation Resistance
- There exists some such that the challenge of the -th run of collides with some previous challenge () or c in a previous tagging query.
- There exists some and such that, for some test with during the -th run of , , and does not ask to and to any .
5.2. Completeness and Soundness
5.3. Enhancing the Generic Construction
- Steps 1 to 3:
- Identical to those of .
- Step 4:
- for .
- Step 5:
- Identical to Step 4 of .
6. Performance Evaluation
7. Concluding Remark
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| MAC | Message authentication code |
| IoT | Internet of things |
| XOR | Exclusive or |
| PRF | Pseudorandom function |
| STD | Shifted transversal design |
References
- Katz, J.; Lindell, A.Y. Aggregate Message Authentication Codes. In Proceedings of the Topics in Cryptology—CT-RSA 2008, The Cryptographers’ Track at the RSA Conference 2008, San Francisco, CA, USA, 8–11 April 2008; Malkin, T., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2008; Volume 4964, pp. 155–169. [Google Scholar] [CrossRef]
- Dorfman, R. The Detection of Defective Members of Large Populations. Ann. Math. Stat. 1943, 14, 436–440. [Google Scholar] [CrossRef]
- Du, D.Z.; Hwang, F.K. Combinatorial Group Testing and Its Applications, 2nd ed.; Series on Applied Mathematics; World Scientific: Singapore, 2000; Volume 12. [Google Scholar]
- FIPS PUB 180-4; Secure Hash Standard (SHS). National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015.
- FIPS PUB 198-1; The Keyed-Hash Message Authentication Code (HMAC). National Institute of Standards and Technology: Gaithersburg, MD, USA, 2008.
- Eikemeier, O.; Fischlin, M.; Götzmann, J.; Lehmann, A.; Schröder, D.; Schröder, P.; Wagner, D. History-Free Aggregate Message Authentication Codes. In Proceedings of the Security and Cryptography for Networks, 7th International Conference, SCN 2010, Amalfi, Italy, 13–15 September 2010; Garay, J.A., Prisco, R.D., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2010; Volume 6280, pp. 309–328. [Google Scholar] [CrossRef]
- Sato, S.; Hirose, S.; Shikata, J. Sequential Aggregate MACs from Any MACs: Aggregation and Detecting Functionality. J. Internet Serv. Inf. Secur. 2019, 9, 2–23. [Google Scholar] [CrossRef]
- Ishii, Y.; Tada, M. Structurally aggregate message authentication codes. In Proceedings of the International Symposium on Information Theory and Its Applications, ISITA 2020, Kapolei, HI, USA, 24–27 October 2020; pp. 339–343. [Google Scholar]
- Goodrich, M.T.; Atallah, M.J.; Tamassia, R. Indexing Information for Data Forensics. In Proceedings of the Applied Cryptography and Network Security, Third International Conference, ACNS 2005, New York, NY, USA, 7–10 June 2005; Ioannidis, J., Keromytis, A.D., Yung, M., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2005; Volume 3531, pp. 206–221. [Google Scholar] [CrossRef]
- Minematsu, K. Efficient Message Authentication Codes with Combinatorial Group Testing. In Proceedings of the Computer Security—ESORICS 2015—20th European Symposium on Research in Computer Security, Vienna, Austria, 21–25 September 2015; Proceedings, Part I. Pernul, G., Ryan, P.Y.A., Weippl, E.R., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2015; Volume 9326, pp. 185–202. [Google Scholar] [CrossRef]
- Black, J.; Rogaway, P. A Block-Cipher Mode of Operation for Parallelizable Message Authentication. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002, International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Knudsen, L.R., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2002; Volume 2332, pp. 384–397. [Google Scholar] [CrossRef]
- Minematsu, K.; Kamiya, N. Symmetric-Key Corruption Detection: When XOR-MACs Meet Combinatorial Group Testing. In Proceedings of the Computer Security—ESORICS 2019—24th European Symposium on Research in Computer Security, Luxembourg, 23–27 September 2019; Proceedings, Part I. Sako, K., Schneider, S., Ryan, P.Y.A., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2019; Volume 11735, pp. 595–615. [Google Scholar] [CrossRef]
- Hirose, S.; Shikata, J. Non-adaptive Group-Testing Aggregate MAC Scheme. In Proceedings of the Information Security Practice and Experience—14th International Conference, ISPEC 2018, Tokyo, Japan, 25–27 September 2018; Su, C., Kikuchi, H., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2018; Volume 11125, pp. 357–372. [Google Scholar] [CrossRef]
- Hirose, S.; Shikata, J. Aggregate Message Authentication Code Capable of Non-Adaptive Group-Testing. IEEE Access 2020, 8, 216116–216126. [Google Scholar] [CrossRef]
- Sato, S.; Shikata, J. Interactive Aggregate Message Authentication Scheme with Detecting Functionality. In Advanced Information Networking and Applications, Proceedings of the 33rd International Conference on Advanced Information Networking and Applications, AINA 2019, Matsue, Japan, 27–29 March 2019; Barolli, L., Takizawa, M., Xhafa, F., Enokido, T., Eds.; Advances in Intelligent Systems and Computing; Springer: Berlin/Heidelberg, Germany, 2019; Volume 926, pp. 1316–1328. [Google Scholar] [CrossRef]
- Anada, H.; Kamibayashi, D. Quantum Security and Implementation Evaluation of Non-adaptive Group-Testing Aggregate Message Authentication Codes. In Proceedings of the Eighth International Symposium on Computing and Networking Workshops, CANDAR 2020 Workshops, Naha, Japan, 24–27 November 2020; pp. 307–313. [Google Scholar] [CrossRef]
- Sato, S.; Shikata, J. Quantum-Secure (Non-)Sequential Aggregate Message Authentication Codes. In Proceedings of the Cryptography and Coding—17th IMA International Conference, IMACC 2019, Oxford, UK, 16–18 December 2019; Albrecht, M., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2019; Volume 11929, pp. 295–316. [Google Scholar] [CrossRef]
- Ogawa, Y.; Sato, S.; Shikata, J.; Imai, H. Aggregate Message Authentication Codes with Detecting Functionality from Biorthogonal Codes. In Proceedings of the IEEE International Symposium on Information Theory, ISIT 2020, Los Angeles, CA, USA, 21–26 June 2020; pp. 868–873. [Google Scholar] [CrossRef]
- Hirose, S.; Shikata, J. Group-Testing Aggregate Entity Authentication. In Proceedings of the IEEE Information Theory Workshop, ITW 2023, Saint-Malo, France, 23–24 April 2023. [Google Scholar]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Proceedings of the Advances in Cryptology—CRYPTO ’93, 13th Annual International Cryptology Conference, Santa Barbara, CA, USA, 22–26 August 1993; Stinson, D.R., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 1993; Volume 773, pp. 232–249. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Random Oracles are Practical: A Paradigm for Designing Efficient Protocols. In Proceedings of the CCS ’93, Proceedings of the 1st ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 November 1993; Denning, D.E., Pyle, R., Ganesan, R., Sandhu, R.S., Ashby, V., Eds.; ACM: New York, NY, USA, 1993; pp. 62–73. [Google Scholar] [CrossRef]
- Dýachkov, A.G.; Rashad, A.M.; Rykov, V.V. Superimposed distance codes. Probl. Control Inf. Theory 1989, 18, 237–250. [Google Scholar]
- Porat, E.; Rothschild, A. Explicit Non-adaptive Combinatorial Group Testing Schemes. In Proceedings of the Automata, Languages and Programming, 35th International Colloquium, ICALP 2008, Reykjavik, Iceland, 7–11 July 2008; Proceedings, Part I: Tack A: Algorithms, Automata, Complexity, and Games. Aceto, L., Damgård, I., Goldberg, L.A., Halldórsson, M.M., Ingólfsdóttir, A., Walukiewicz, I., Eds.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2008; Volume 5125, pp. 748–759. [Google Scholar] [CrossRef]
- Aldridge, M.; Johnson, O.; Scarlett, J. Group Testing: An Information Theory Perspective. Found. Trends Commun. Inf. Theory 2019, 15, 196–392. [Google Scholar] [CrossRef]
- Erdös, P.; Frankl, P.; Füredi, Z. Families of Finite Sets in Which No Set Is Covered by the Union of r Others. Isr. J. Math. 1985, 51, 79–89. [Google Scholar] [CrossRef]
- Dýachkov, A.G.; Rykov, V.V. Bounds on the Length of Disjunctive Codes. Probl. Inf. Transm. 1982, 18, 7–13. [Google Scholar]
- Shangguan, C.; Ge, G. New Bounds on the Number of Tests for Disjunct Matrices. IEEE Trans. Inf. Theory 2016, 62, 7518–7521. [Google Scholar] [CrossRef]
- Li, C.H. A Sequential Method for Screening Experimental Variables. J. Am. Stat. Assoc. 1962, 57, 455–477. [Google Scholar] [CrossRef]
- Eppstein, D.; Goodrich, M.T.; Hirschberg, D.S. Improved Combinatorial Group Testing Algorithms for Real-World Problem Sizes. SIAM J. Comput. 2007, 36, 1360–1375. [Google Scholar] [CrossRef]
- Thierry-Mieg, N. A new pooling strategy for high-throughput screening: The Shifted Transversal Design. BMC Bioinform. 2006, 7, 28. [Google Scholar] [CrossRef] [PubMed]
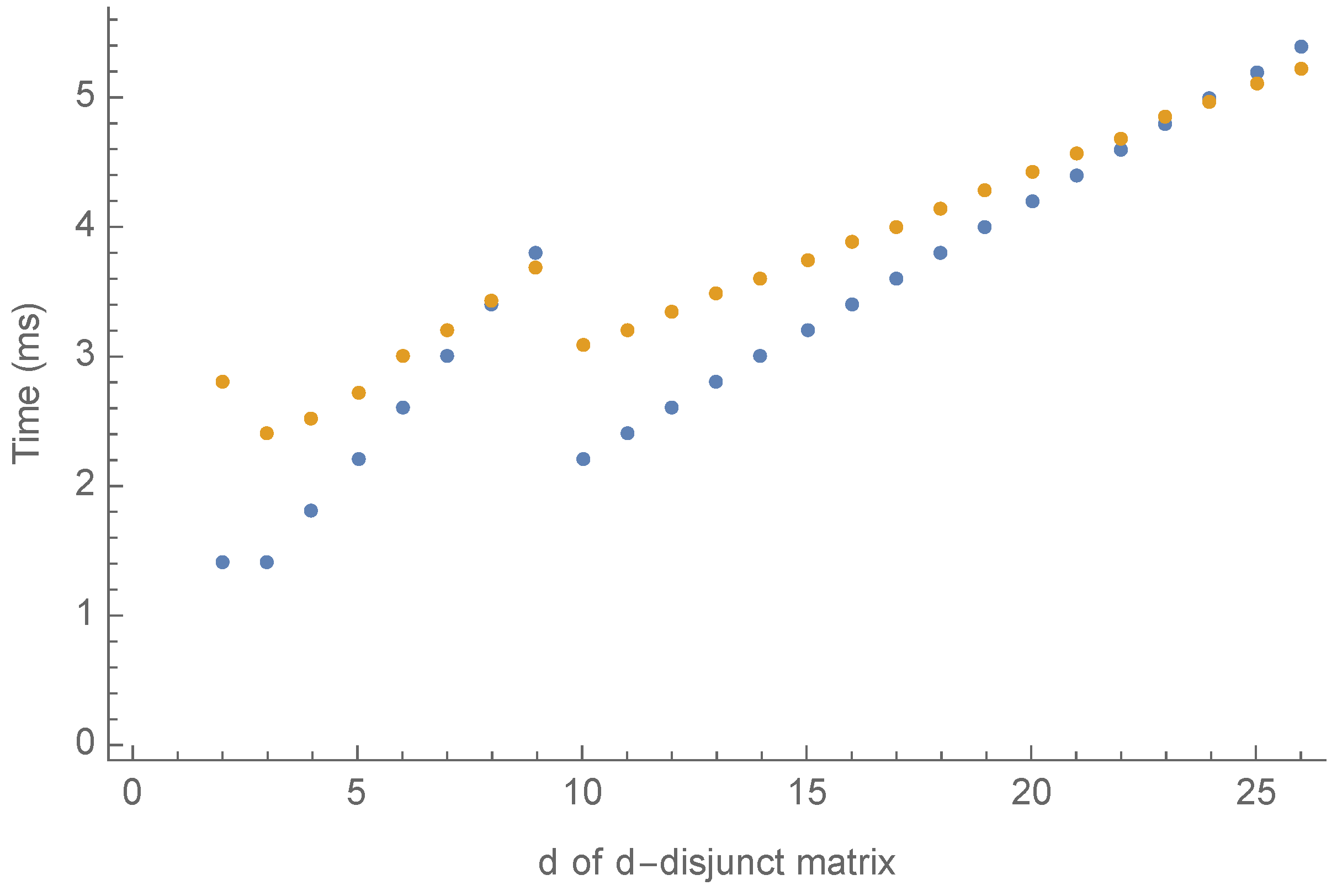
| Number of Entities | Tagging | Verification | ||
|---|---|---|---|---|
| 100 | ||||
| 1000 | ||||
| 10,000 | ||||
| d | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| # rows | 49 | 77 | 99 | 121 | 169 | 255 | 289 | 361 | 407 |
| # 1’s | 7000 | 7000 | 9000 | 11,000 | 13,000 | 15,000 | 17,000 | 19,000 | 11,000 |
| d | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| # rows | 444 | 481 | 518 | 555 | 592 | 629 | 666 | 703 | 740 |
| # 1’s | 12,000 | 13,000 | 14,000 | 15,000 | 16,000 | 17,000 | 18,000 | 19,000 | 20,000 |
| d | 20 | 21 | 22 | 23 | 24 | 25 | 26 | ||
| # rows | 777 | 814 | 851 | 888 | 925 | 962 | 999 | ||
| # 1’s | 21,000 | 22,000 | 23,000 | 24,000 | 25,000 | 26,000 | 27,000 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hirose, S.; Shikata, J. Aggregate Entity Authentication Identifying Invalid Entities with Group Testing. Electronics 2023, 12, 2479. https://doi.org/10.3390/electronics12112479
Hirose S, Shikata J. Aggregate Entity Authentication Identifying Invalid Entities with Group Testing. Electronics. 2023; 12(11):2479. https://doi.org/10.3390/electronics12112479
Chicago/Turabian StyleHirose, Shoichi, and Junji Shikata. 2023. "Aggregate Entity Authentication Identifying Invalid Entities with Group Testing" Electronics 12, no. 11: 2479. https://doi.org/10.3390/electronics12112479
APA StyleHirose, S., & Shikata, J. (2023). Aggregate Entity Authentication Identifying Invalid Entities with Group Testing. Electronics, 12(11), 2479. https://doi.org/10.3390/electronics12112479






