Time Series Network Data Enabling Distributed Intelligence—A Holistic IoT Security Platform Solution
Abstract
:1. Introduction
1.1. Rationale
1.2. Related Work
1.2.1. Previous Work in Anomaly Detection Techniques
1.2.2. Previous Work in the Mitigation of Anomalies
1.2.3. Previous Work in Verification Techniques
1.2.4. Previous Work in Visual Analytics Systems
1.2.5. Novel Contributions
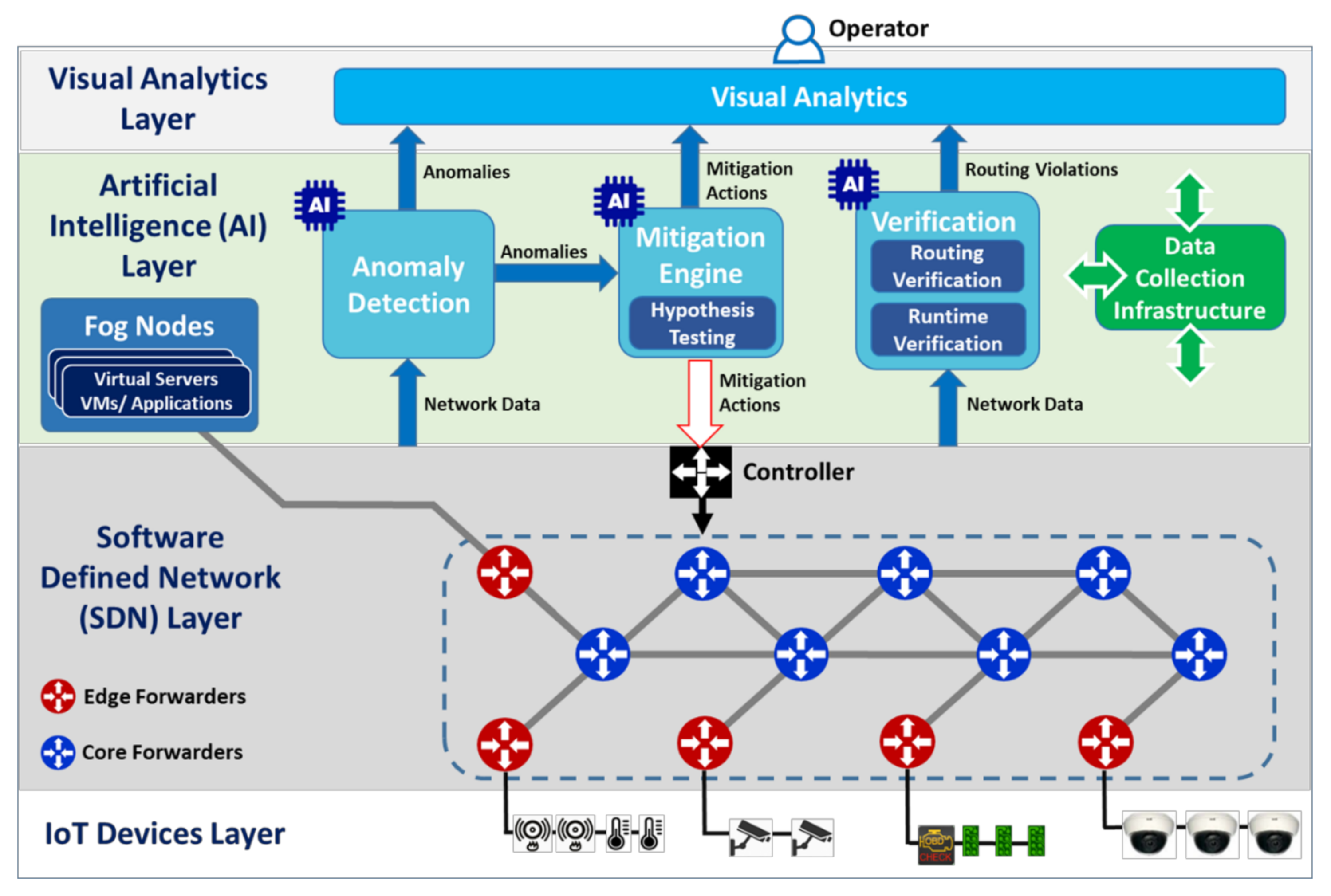
2. Design Methodology and System Architecture
2.1. Research Design
- The anomaly detection (AD) component, which utilizes a decentralized multi-agent approach based on a graph neural network (GNN) algorithm to discover anomalous traffic that might threaten network operation;
- The mitigation engine, i.e., the component that allows for the mitigation of any discovered threat by using multi-objective deep reinforcement learning to reach an optimal decision. This includes the hypothesis testing submodule;
- The routing verification component, which aims to verify that SDN routing decisions are optimal regarding energy, QoS and security properties through the multi-objective optimization employing evolutionary algorithms;
- The runtime verification component is a supplementary, heuristic tool used for early warnings about new types of attacks (i.e., types assaulting the system for the first time). It monitors network and resource statistics and reports deviations when exceeding predefined limits.
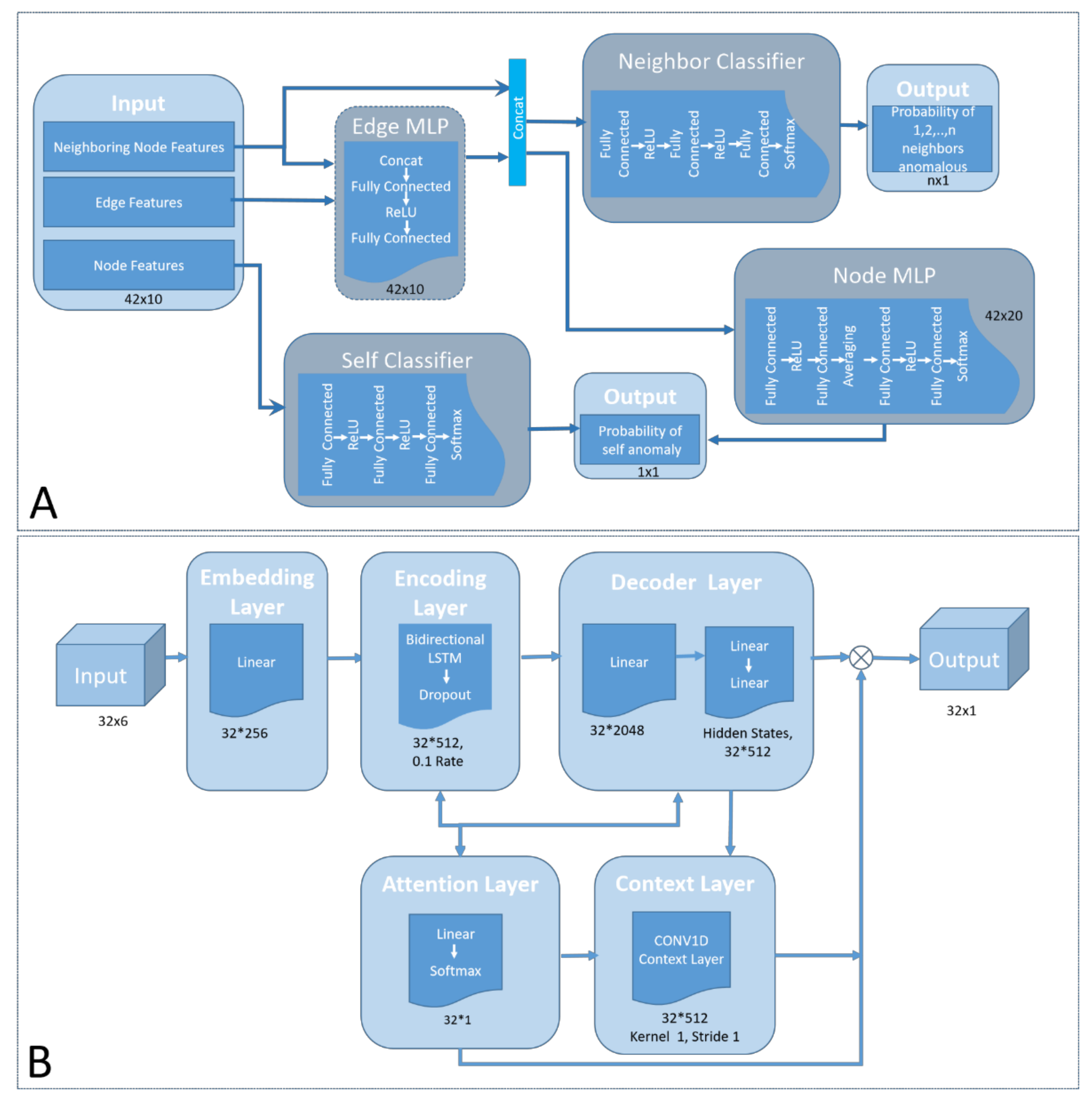
2.2. Multi-Agent Anomaly Detection
2.2.1. Multi-Agent Anomaly Detection Model Architecture
2.2.2. Network Identifiers Extraction
2.3. Threat Management and Mitigation
2.3.1. Mitigation Engine Module
2.3.2. Hypothesis Testing Submodule
2.4. Routing Verification
2.5. Runtime Verification
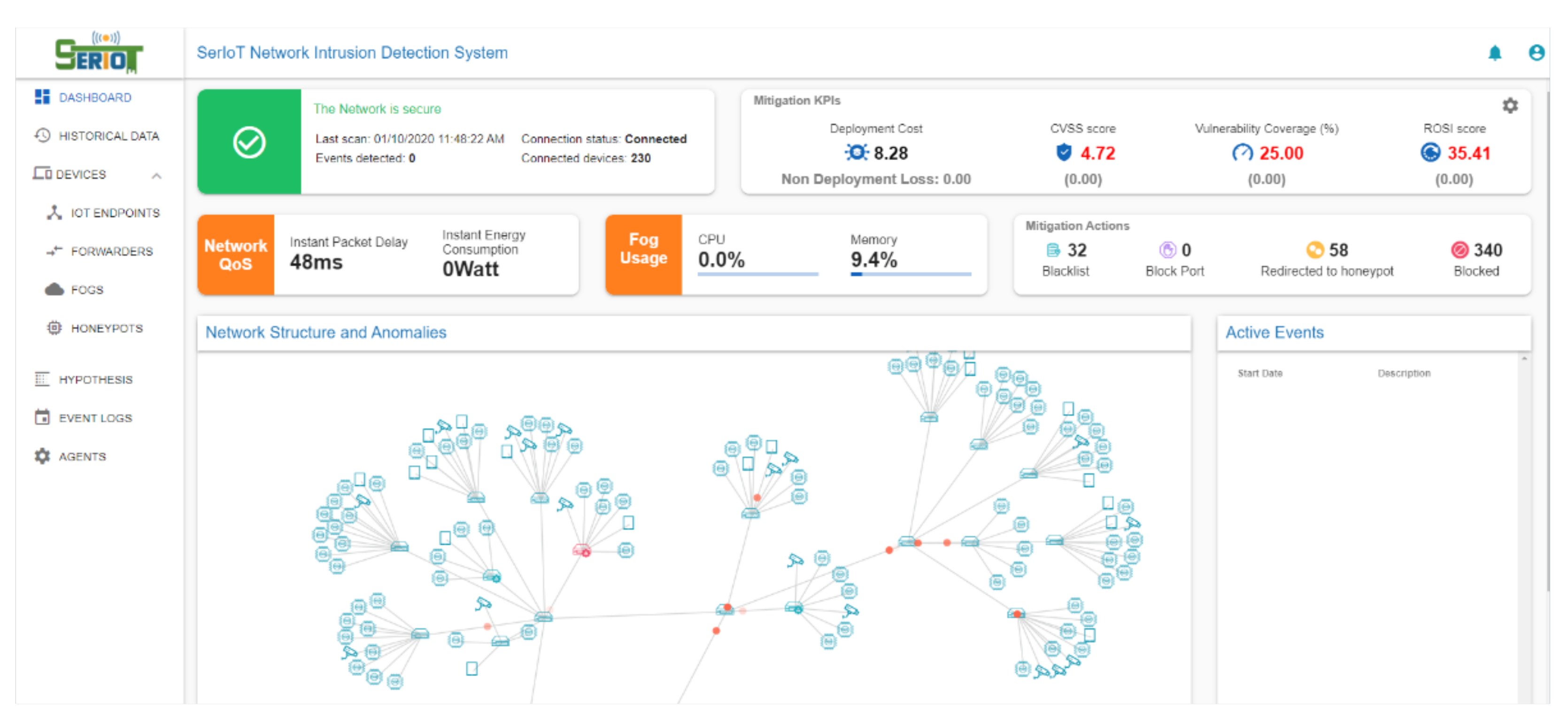
2.6. Visual Analytics
3. Experimental Results
3.1. Anomaly Detection Results
3.2. Mitigation Engine Results
4. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gartner Global Research and Advisory Company. Leading the IoT. Available online: https://www.gartner.com (accessed on 6 April 2021).
- Ericsson. Cellular Networks for Massive IoT, White Paper. Available online: https://www.ericsson.com (accessed on 6 April 2021).
- McAfee. The Hidden Costs of Cybercrime. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-hidden-costs-of-cybercrime.pdf (accessed on 29 October 2021).
- Mobilio, M.; Orr‘u, M.; Riganelli, O.; Tundo, A.; Mariani, L. Anomaly detection as-a-service. In Proceedings of the IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Berlin, Germany, 27–30 October 2019; pp. 193–199. [Google Scholar]
- Hariharan, A.; Gupta, A.; Pal, Τ. Camlpad: Cybersecurity autonomous machine learning platform for anomaly detection. In Proceedings of the Future of Information and Communication Conference, San Francisco, CA, USA, 5–6 March 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 705–720. [Google Scholar]
- Sun, W.; Liu, J.; Yue, Y. AI-enhanced offloading in edge computing: When machine learning meets industrial IoT. IEEE Netw. 2019, 33, 68–74. [Google Scholar] [CrossRef]
- Roukounaki, A.; Efremidis, S.; Soldatos, J.; Neises, J.; Walloschke, T.; Kefalakis, N. Scalable and configurable end-to-end collection and analysis of IoT security data: Towards end-to-end security in IoT systems. In Proceedings of the IEEE Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [Google Scholar]
- Lasota, K.; Bazydło, P.; Kozakiewicz, A. Mobile platform for threat monitoring in wireless sensor networks. In Proceedings of the 3rd IEEE World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; pp. 106–110. [Google Scholar]
- Zhipeng, S.; Yuanming, Z.; Jiawei, L.; Jun, X.; Gang, X. A novel time series forecasting model with deep learning. Neurocomputing 2020, 396, 302–313. [Google Scholar] [CrossRef]
- Colò, G. Anomaly detection for Cyber Security: Time Series Forecasting and Deep Learning. Int. J. Sci. Res. Math. Stat. Sci. 2020, 7, 40–52. [Google Scholar]
- Li, D.; Chen, D.; Goh, J.; Ng, S. Anomaly Detection with Generative Adversarial Networks for Multivariate Time Series. In Proceedings of the 7th International Workshop on Big Data, Streams and Heterogeneous Source Mining: Algorithms, Systems, Programming Models and Applications on the ACM Knowledge Discovery and Data Mining Conference, London, UK, 20 August 2018. [Google Scholar]
- Wang, K.; Xiong, H.; Zhang, J.; Chen, H.; Dou, D.; Xu, C.Z. SenseMag: Enabling Low-Cost Traffic Monitoring using Non-invasive Magnetic Sensing. IEEE Internet Things J. 2021, 8, 16666–16679. [Google Scholar] [CrossRef]
- Ding, Z.; Shen, L.; Chen, H.; Yan, F.; Ansari, N. Energy-efficient relay-selection-based dynamic routing algorithm for IoT-oriented software-defined WSNs. IEEE Internet Things J. 2020, 7, 9050–9065. [Google Scholar] [CrossRef]
- Ding, Z.; Shen, L.; Chen, H.; Yan, F.; Ansari, N. Residual-Energy Aware Modeling and Analysis of Time-Varying Wireless Sensor Networks. IEEE Commun. Lett. 2021, 25, 2082–2086. [Google Scholar] [CrossRef]
- Bai, J.; Ding, B.; Xiao, Z.; Jiao, L.; Chen, H.; Regan, A.C. Hyperspectral Image Classification Based on Deep Attention Graph Convolutional Network. IEEE Trans. Geosci. Remote Sens. 2021, 60, 1–16. [Google Scholar] [CrossRef]
- Forestiero, A.; Papuzzo, G. Agents-based algorithm for a distributed information system in Internet of Things. IEEE Internet Things J. 2021, 8, 16548–16558. [Google Scholar] [CrossRef]
- Tran, M.C.; Heejeong, L.; Nakamura, Y. Abnormal web traffic detection using connection graph. Bull. Netw. Comput. Syst. Softw. 2014, 3, 57–62. [Google Scholar]
- Zheng, L.; Li, Z.; Li, J.; Li, Z.; Gao, J. AddGraph: Anomaly detection in dynamic graph using attention-based temporal GCN. In Proceedings of the 28th International Joint Conference on Artificial Intelligence, Macao, China, 10–16 August 2019; AAAI Press: Palo Alto, CA, USA, 2019; pp. 4419–4425. [Google Scholar]
- Yu, W.; Cheng, W.; Aggarwal, C.C.; Zhang, K.; Chen, H.; Wang, W. Netwalk: A flexible deep embedding approach for anomaly detection in dynamic networks. In Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, London, UK, 19–23 August 2018; pp. 2672–2681. [Google Scholar]
- Chaudhary, A.; Mittal, H.; Arora, A. Anomaly detection using graph neural networks. In Proceedings of the International Conference on Machine Learning, Big Data, Cloud and Parallel Computing COMITCon), Faridabad, India, 14–16 February 2019; IEEE: New York, NY, USA, 2019; pp. 346–350. [Google Scholar]
- Eswaran, D.; Faloutsos, C.; Guha, S.; Mishra, N. Spotlight: Detecting anomalies in streaming graphs. In Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, London, UK, 19–23 August 2018; pp. 1378–1386. [Google Scholar]
- Shin, K.; Hooi, B.; Faloutsos, C. M-zoom: Fast dense-block detection in tensors with quality guarantees. In Proceedings of the Joint European Conference on Machine Learning and Knowledge Discovery in Databases, Skopje, Macedonia, 18–22 September 2016; pp. 264–280. [Google Scholar]
- Le Bars, B.; Kalogeratos, A. A probabilistic framework to node-level anomaly detection in communication networks. arXiv 2019, arXiv:1902.04521. [Google Scholar]
- Wu, Z.; Pan, S.; Chen, F.; Long, G.; Zhang, C.; Yu, P.S. A comprehensive survey on graph neural networks. arXiv 2019, arXiv:1901.00596. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gelenbe, E.; Fröhlich, P.; Nowak, M.; Papadopoulos, S.; Protogerou, A.; Drosou, A.; Tzovaras, D. IoT network attack detection and mitigation. In Proceedings of the 9th Mediterranean Conference on Embedded computing, MECO 2020, Budva, Montenegro, 8–11 June 2020; IEEE: New York, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Protogerou, A.; Papadopoulos, S.; Drosou, A.; Tzovaras, D.; Refanidis, I. A graph neural network method for distributed anomaly detection in IoT. Evol. Syst. 2020, 12, 19–36. [Google Scholar] [CrossRef]
- Forestiero, A. Metaheuristic algorithm for anomaly detection in Internet of Things leveraging on a neural-driven multiagent system. Knowl. Based Syst. 2021, 228, 107241. [Google Scholar] [CrossRef]
- Ahemd, M.M.; Wahid, A. IoT Security: A Layered Approach for Attacks & Defenses. In Proceedings of the 2017 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 19–21 April 2017; IEEE: New York, NY, USA, 2017; pp. 104–110. [Google Scholar]
- Gonzalez-Granadillo, G.; Garcia-Alfaro, J.; Alvarez, E.; El-Barbori, M.; Debar, H. Selecting optimal countermeasures for attacks against critical systems using the attack volume model and the RORI index. Comput. Electr. Eng. 2015, 47, 13–34. [Google Scholar] [CrossRef]
- Kotenko, I.; Doynikova, E. Dynamical Calculation of Security Metrics for Countermeasure Selection in Computer Networks. In Proceedings of the 24th Euromicro International Conference on Parallel, Distributed, and Network-Based Processing (PDP), Heraklion, Greece, 17–19 February 2016; pp. 558–565. [Google Scholar]
- Chehida, S.; Baouya, A.; Bozga, M.; Bensalem, S. Exploration of Impactful Countermeasures on IoT Attacks. In Proceedings of the 9th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 8–11 June 2020; pp. 1–4. [Google Scholar]
- Lee, Y.; Choi, T.J.; Ahn, C.W. Multi-objective evolutionary approach to select security solutions. CAAI Trans. Intell. Technol. 2017, 2, 64–67. [Google Scholar] [CrossRef]
- Enoch, S.Y.; Hong, J.B.; Ge, M.; Khan, K.M.; Kim, D.S. Multi-Objective Security Hardening Optimisation for Dynamic Networks. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Hyunjae, K.; Ahn, D.H.; Lee, G.M.; Yoo, J.D.; Park, K.H.; Kim, H.K. IoT network intrusion dataset. IEEE Dataport 2019. [Google Scholar] [CrossRef]
- Manasrah, A.M.; Gupta, B.B. An optimized service broker routing policy based on differential evolution algorithm in fog/cloud environment. Clust. Comput. 2019, 22, 1639–1653. [Google Scholar] [CrossRef]
- Naha, R.K.; Othman, M.M. Cost-aware service brokering and performance sentient load balancing algorithms in the cloud. J. Netw. Comput. Appl. 2016, 75, 47–57. [Google Scholar] [CrossRef]
- Gupte, P.; Bejgum, R.S.R.; Maes, S.H.; Hewlett Packard Enterprise Development LP. Policy Based Selection of Resources for a Cloud Service. U.S. Patent Application No. 14/914,297, 14 July 2016. [Google Scholar]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog computing: Platform and applications. In Proceedings of the 3rd IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; pp. 73–78. [Google Scholar]
- Arkian, H.R.; Diyanat, A.; Pourkhalili, A. MIST: Fog-based data analytics scheme with cost-efficient resource provisioning for IoT crowdsensing applications. J. Netw. Comput. Appl. 2017, 82, 152–165. [Google Scholar] [CrossRef]
- Angelini, M.; Blasilli, G.; Bonomi, S.; Lenti, S.; Palleschi, A.; Santucci, G.; Paoli, E. BUCEPHALUS: A BUsiness CEntric cybersecurity Platform for proActive anaLysis Using visual analyticS. In Proceedings of the IEEE Symposium on Visualization for Cyber Security (VizSec), New Orleans, LA, USA, 27 October 2021. [Google Scholar]
- Damaševičius, R.; Toldinas, J.; Venčkauskas, A.; Grigaliūnas, Š.; Morkevičius, N.; Jukavičius, V. Visual Analytics for Cyber Security Domain: State-of-the-Art and Challenges. In Information and Software Technologies. ICIST 2019; Communications in Computer and Information Science Series; Springer: Berlin/Heidelberg, Germany, 2019; Volume 1078, pp. 256–270. [Google Scholar]
- Radoglou Grammatikis, P.; Sarigiannidis, P.; Moscholios, I. Securing the Internet of Things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar] [CrossRef]
- Shiravi, H.; Shiravi, A.; Ghorbani, A. A Survey of Visualization Systems for Network Security. IEEE Trans. Vis. Comput. Graph. 2012, 18, 1313–1329. [Google Scholar] [CrossRef] [PubMed]
- Legg, P. Enhancing cyber situation awareness for Non-Expert Users using visual analytics. In Proceedings of the 2016 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), London, UK, 13–14 June 2016. [Google Scholar]
- Empl, P.; Pernul, G. A Flexible Security Analytics Service for the Industrial IoT. In Proceedings of the 2021 ACM Workshop on Secure and Trustworthy Cyber-Physical Systems, Virtual, 28 April 2021. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Breitenbacher, D.; Shabtai, A.; Elovici, Y. N-BaIoT-Network-based detection of IoT botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef] [Green Version]
- Battaglia, P.W.; Hamrick, J.B.; Bapst, V.; Sanchez-Gonzalez, A.; Zambaldi, V.; Malinowski, M.; Tacchetti, A.; Raposo, D.; Santoro, A.; Faulkner, R.; et al. Relational inductive biases, deep learning, and graph networks. arXiv 2018, arXiv:1806.01261. [Google Scholar]
- Mell, P.; Scarfone, K.; Romanosky, S. Common vulnerability scoring system. IEEE Secur. Priv. 2006, 4, 85–89. [Google Scholar] [CrossRef]
- Sonnenreich, W.; Albanese, J.; Stout, B. Return on security investment (rosi)-a practical quantitative model. J. Res. Pract. Inf. Technol. 2006, 38, 239–252. [Google Scholar]
- Karthick, R.R.; Hattiwale, V.P.; Ravindran, B. Adaptive network intrusion detection system using a hybrid approach. In Proceedings of the IEEE Fourth International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 3–7 January 2012; pp. 1–7. [Google Scholar]
- Vinyals, O.; Fortunato, M.; Jaitly, N. Pointer networks. Adv. Neural Inf. Process. Syst. 2015, 28, 2692–2700. [Google Scholar]
- Messac, A.; Ismail-Yahaya, A.; Mattson, C. The normalized normal constraint method for generating the pareto frontier. Struct. Multidiscip. Optim. 2003, 25, 86–98. [Google Scholar] [CrossRef]
- Mpatziakas, A.; Papadopoulos, S.; Drosou, A.; Tzovaras, D. A Hypothesis Testing tool for the comparison of different Cyber-Security Mitigation Strategies in IoT. In Proceedings of the 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021. [Google Scholar]
- Sood, K.; Karmakar, K.K.; Varadharajan, V.; Tupakula, U.; Yu, S. Analysis of policy-based security management system in software-defined networks. IEEE Commun. Lett. 2019, 23, 612–615. [Google Scholar] [CrossRef]
- Trivedi, A.; Srinivasan, D.; Sanyal, K.; Ghosh, A. A survey of multiobjective evolutionary algorithms based on decomposition. IEEE Trans. Evol. Comput. 2017, 21, 440–462. [Google Scholar] [CrossRef]
- Li, K.W.; Song, H.; Zeng, F. Policy-based secure and trustworthy sensing for internet of things in smart cities. IEEE Internet Things J. 2017, 5, 716–723. [Google Scholar] [CrossRef]
- Hidalgo, C.; Vaca, M.; Nowak, M.P.; Frölich, P.; Reed, M.; Al-Naday, M.; Tzovaras, D. Detection, control and mitigation system for secure vehicular communication. Veh. Commun. 2021, 2021, 100425. [Google Scholar] [CrossRef]




| Anomaly Detector Features | |
| Time-related entities | Start time, duration |
| Header-related entities | FIN/SYN/RST/PSH/ ACK/URG/CWE/ECE flag counts, Fwd Header Len |
| Flow-related identifiers | Src IP, Dst IP, Dir, Label |
| Payload-related entities | Tot Fwd Pkts, Init Fwd Win Byts, Subflow Fwd Byts, Flow Pkts/s, Flow Byts/s, TotLen Fwd Pkts, Fwd Pkts/s, Subflow Bwd Byts, Fwd IAT Tot |
| Mitigation Engine Features | |
| CVSS Score | Common Vulnerability Scoring System (CVSS) is an open-industry standard for assessing the severity of a cyber security vulnerability [48]. A CVSS score of 10 for a single vulnerability represents the highest severity: CVSS Score = 10−mean(CVSSalldetectedvulnerabilities) |
| ROSI Score | Return on security investment score (ROSI) calculates an index to evaluate the trade-off between the efficiency and the cost of a mitigation plan [49]: ROSI Score = |
| Coverage Score | The coverage score of a mitigation action is calculated as the percentage of the number of vulnerabilities it covers to the number of the total active vulnerabilities. |
| Deployment Cost Score | This KPI evaluates the deployment costs of mitigation actions by taking into account the mitigation deployment time and the importance of the device (as assessed by the network security operator): Deployment cost = Deployment Time * Device importance |
| Anomaly Detection | ||||
|---|---|---|---|---|
| All Devices Online | Offline Devices | |||
| Detection Method | ROC Score | Accuracy | ROC Score | Accuracy |
| GNN | 98.90 | 99.00 | 98.90 | 99.00 |
| SVM | 87.26 | 87.26 | 85.02 | 85.02 |
| Decision Tree | 97.70 | 97.97 | 96.23 | 96.23 |
| Random Forest | 96.96 | 96.96 | 94.03 | 94.03 |
| Mitigation Engine | ||||
|---|---|---|---|---|
| Algorithm | CVSS Score (MIN) | Deployment Cost (MIN) | Coverage Score (MAX) | ROSI Score (MAX) |
| Pointer Networks | 1.47 | 7.07 | 100 | 2628 |
| NSGA—II | 2.86 | 12.03 | 76.09 | 2092 |
| MOEA/D | 2.61 | 11.65 | 92.39 | 3005 |
| Device | Vulnerability ID | Vulnerabilities Covered by Available Mitigations | ROSI Score (Percent) | Mitigation Deployment Cost |
|---|---|---|---|---|
| SDN Switch with Openvswitch | CVE-2017-9265 (CVSS 7.5), CVE-2018-17205 (CVSS 5) | 2 | 39 | Honeypot 25, Block 10, Blacklist 15, Block Port 18 |
| IP Camera | CVE-2018-19081 (CVSS 4.3), CVE-2018-19082 (CVSS 10), CVE-2018-19083 (CVSS 7.5) | 3 | 19 | Honeypot 12.5, Block 5, Blacklist 7.5, Block Port 9 |
| SDN Router with ONOS | CVE-2018-1000615 (CVSS 5), CVE-2018-12691 (CVSSS 4.3) | 2 | 39 | Honeypot 37.5, Block 15, Blacklist 22.5, Block Port 27 |
| Windows PC | CVE-2019-1368 (CVSS 2.1), CVE-2019-1359 (CVSS 9.3) | 2 | 59 | Honeypot 50, Block 20, Blacklist 30, Block Port 36 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Protogerou, A.; Kopsacheilis, E.V.; Mpatziakas, A.; Papachristou, K.; Theodorou, T.I.; Papadopoulos, S.; Drosou, A.; Tzovaras, D. Time Series Network Data Enabling Distributed Intelligence—A Holistic IoT Security Platform Solution. Electronics 2022, 11, 529. https://doi.org/10.3390/electronics11040529
Protogerou A, Kopsacheilis EV, Mpatziakas A, Papachristou K, Theodorou TI, Papadopoulos S, Drosou A, Tzovaras D. Time Series Network Data Enabling Distributed Intelligence—A Holistic IoT Security Platform Solution. Electronics. 2022; 11(4):529. https://doi.org/10.3390/electronics11040529
Chicago/Turabian StyleProtogerou, Aikaterini, Evangelos V. Kopsacheilis, Asterios Mpatziakas, Kostas Papachristou, Traianos Ioannis Theodorou, Stavros Papadopoulos, Anastasios Drosou, and Dimitrios Tzovaras. 2022. "Time Series Network Data Enabling Distributed Intelligence—A Holistic IoT Security Platform Solution" Electronics 11, no. 4: 529. https://doi.org/10.3390/electronics11040529
APA StyleProtogerou, A., Kopsacheilis, E. V., Mpatziakas, A., Papachristou, K., Theodorou, T. I., Papadopoulos, S., Drosou, A., & Tzovaras, D. (2022). Time Series Network Data Enabling Distributed Intelligence—A Holistic IoT Security Platform Solution. Electronics, 11(4), 529. https://doi.org/10.3390/electronics11040529






