Decentralized Blockchain Network for Resisting Side-Channel Attacks in Mobility-Based IoT
Abstract
1. Introduction
- The proposed method introduces multiple stages of secure network implementation in IoT, where a novel communication model is built over mobile IoT devices;
- A novel blockchain network is constructed to verify and authorize data related to mobile IoT devices, access points, and smart agreements;
- The mobile IoT devices are configured to play the role of the requestor, worker, and supporter in the blockchain network in a branched form for facilitating a faster transaction with the least overhead and higher scalability;
- The complete operation of the proposed blockchain network is carried out by constructing an algorithm for permission rights, verification of adjacent nodes, data transmission, and assessment of candidate IoT nodes;
- Ethereum blockchain is implemented with an extensive test environment benchmarked by comparing with frequently used blockchain models to exhibit a better balance between securing multiple variants of side-channel attacks and communication efficiency.
2. Existing Approaches
3. Research Problem
- Narrowed focus on side-channel attack—All the variants of side-channel attacks are potentially linked. Hence, addressing one security problem will leave another set of related issues unsolved. A minor vulnerability in the secret key will affect both power and differential attacks and, to some extent, other variants of side-channel attacks. Hence, existing approaches offer a local solution that is not applicable when exposed to an extensive and distributed network;
- Less novelty in blockchain network—The majority of existing approaches are more focused on block formation than formulating a secure network. Encrypting with sophisticated secret keys will only increase delay and significantly affect the quality of service, especially in extensive networks like IoT. Even if it is deployed over many transactions, it will give rise to scalability issues that have not been addressed;
- Non-inclusion of mobility—Existing studies do not report the possible impact of mobile nodes on blockchains in extensive networks. Constructing the block, performing authentication, and updating data are challenging in a vast network with many connected devices. Even if a blockchain network is developed, authenticating all the mobile nodes joining and leaving the network will require dependency on many network devices and increased computational resources;
- Lack of realization of adversary strength—A side-channel attack can adopt a varied strategy to initiate an attack. A closer look into existing studies shows increasing adoption of the learning-based model for identifying the adversary. However, none of these schemes have reported a secure learning model that could be compromised by such an attacker and thereby grows more intelligent capabilities to introduce attackers;
- Lack of adoption of scalability—In the presence of a vast network, there will be an increasing demand for identifiers of mobile devices as well as certificates associated with network authentication. Further, adopting public key encryption makes the adversary formulate a more straightforward strategy to intrude into the network. Hence, existing encryption-based blockchains are also vulnerable to side-channel attacks.
4. Materials and Methods
4.1. Primary Stage
- msga—This control message is forwarded by the mobile IoT node to the LAP, where the prime fields of the message consist of a random nonce and identification number of the mobile IoT device;
- msgb—This control message is generated by the cloud server when the LAP either accepts or denies the identity of the mobile IoT device based on a physical unclonable function. The denial flag is generated only when the identity information of the mobile IoT device is not found within the device’s memory by LAP. Using another random number, this message is further ciphered in case of its presence. A unique code is appended with this message to ensure integrity;
- msgc—With the aid of a physical unclonable function, a response is generated by the mobile IoT device. A secret arbitrary integer value is obtained by this mobile IoT device using its response to verify the integrity and freshness of the message. The consecutive iteration of the random secret number is further used in increasing the count to generate a set of challenges by the mobile IoT device. This message is therefore used to ensure that the newly generated response and the arbitrary number are forwarded to the cloud server using the first random number. The computation of the received information is carried out by a cloud server using the first arbitrary secret number.
4.2. Secondary Stage
- Requestor—This mobile IoT node is responsible for understanding the task and placing a request to process a new task. To carry out this operation, the scalability is maintained by recommending multiple numbers of block allocation support by this node to the blockchain;
- Worker—This is a specific set of mobile IoT devices that receives the request for new tasks subjected to the blockchain process. Hence, such a node whose details are managed and updated by a distributed ledger accepts all the transaction blocks. The ledger stores the copy of the block of transaction that is altered by the other mobile IoT device after being authenticated;
- Supporter—This is the third role of the mobile IoT device, which is essentially meant to support services for all transactions using Smart Agreement (SA). The details of this SA are digitally signed with an encryption signature by the supporter node and transmitted to the original client.
4.3. Ternary Stage
5. Algorithm Implementation
5.1. Permission Rights for Mobile IoT
| Algorithm 1 Permission Rights for Mobile IoT Device |
| Input: m (mobile IoT device) Output: Declaration of Accept/Reject Start 1. Obtain ((‘beacon’||Cnon), C) 2. For Kdis = 1 3. Obtain (IDm, IDreq, nonc, nonm, Kdis) 4. Obtain (non, Kses[], Kdis)C 5. Else 6. Obtain (IDm, IDreq, nonc, nonm, Kc) 7. Obtain (non, Kses[], Kdis)C 8. Obtain (Kdis, Kc, Km)C 9. Config(Kses[m] = 1, C) 10. lu(IDcreq, IDsk(m), nonc, nonm, Kdis) 11. If IDcreq = 1 12. Obtain (nonc, nonm, Kses[]) 13. Declare Accept 14. Else 15. Declare Reject End |
5.2. Verification of Adjacent Node in Blockchain
| Algorithm 2 Verifying Adjacent Nodes |
| Input: m (regular node of blockchain) Output: β (verified adjacent nodes) Start 1. For i = 1:m 2. Construct β(i) = [] 3. For j = 1:m 4. Compute dα(i, j) 5. If dα(i, j)= dαmax(i, j) && Dγi = =Dγj 6. Prob(d)i,j = 1 7. j→βi 8. Probθi= Probθj 9. Dij = Di-1,j-1 10. Else 11. Probβij(d) = 0 12. Probθi = Probθi 13. Dβij = Dβi-1,j-1 14. Return β(m) 15. End 16. End End |
5.3. Data Transmission and Inheritor Assessment
| Algorithm 3 Data Transmission |
| Input: m1 (transmitting node), m2 (receiving node) Output: ψ (blockchain) Start 1. For i = 1: s 2. init D, ψ 3. For j = 1: D 4. For k = 1: ψ 5. m1→m2 6. ψ(k)→ ψup 7. End 8. End 9. Verify ψup on m2 10. Assign ψup from m2 to ψ 11. End End |
| Algorithm 4 Assessing Inheritor |
| Input: ID (identity attribute) Output: σ (inheritor) Start 1. For i = 1:s 2. If ID⊆(m, σ) 3. Return σ 4. Else 5. For j = mo:1 6. If string[j]⊆(m, ID) 7. Return string[j], m 8. End 9. End 10. End End |
6. Results
6.1. Simulation Environment
6.2. Accomplished Outcome
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hassanien, A.E.; Dey, N.; Mahalle, P.N.; Shafi, P.M.; Kimabahune, V.V. Internet of Things, Smart Computing and Technology: A Roadmap Ahead; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- Kumar, A.; Balamurugan, B.; Chatterjee, J.M.; Raj, P. Internet of Things Use Cases for the Healthcare Industry; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- Murugesan, S.; Jain, S. Smart Connected World-Technologies and Applications Shaping the Future; Springer International Publishing: Cham, Switzerland, 2021. [Google Scholar]
- Ismail, Y. Internet of Things (IoT) for Automated and Smart Applications; IntechOpen: London, UK, 2019. [Google Scholar]
- Sun, J.; Han, G.; Wang, Y.; Liu, P. Memristor-based neural network circuit of emotion congruent memory with mental fatigue and emotion inhibition. IEEE Trans. Biomed. Circuits Syst. 2021, 15, 606–616. [Google Scholar] [CrossRef] [PubMed]
- Sun, J.; Han, G.; Zeng, Z.; Wang, Y. Memristor-based neural network circuit of full-function Pavlov associative memory with time delay and variable learning rate. IEEE Trans. Cybern. 2020, 50, 2935–2945. [Google Scholar] [CrossRef] [PubMed]
- Sun, J.; Wang, Y.; Liu, P.; Wen, S.; Wang, Y. Memristor-based neural network circuit with multimode generalization and differentiation on Pavlov associative memory. IEEE Trans. Cybern. 2022, 1–12. [Google Scholar] [CrossRef] [PubMed]
- Ghazal, T.M.; Hasan, M.K.; Alshurideh, M.T.; Alzoubi, H.M.; Ahmad, M.; Akbar, S.S.; Al Kurdi, B.; Akour, I.A. IoT for smart cities: Machine learning approaches in smart healthcare—A review. Future Internet 2021, 13, 218. [Google Scholar] [CrossRef]
- Staddon, E.; Loscri, V.; Mitton, N. Attack categorisation for IoT applications in critical infrastructures, a survey. Appl. Sci. 2021, 11, 7228. [Google Scholar] [CrossRef]
- Balogh, S.; Gallo, O.; PLoSzek, R.; Špaček, P.; Zajac, P. IoT security challenges: Cloud and blockchain, postquantum cryptography, and evolutionary techniques. Electronics 2021, 10, 2647. [Google Scholar] [CrossRef]
- Sharma, G.; Vidalis, S.; Anand, N.; Menon, C.; Kumar, S. A survey on layer-wise security attacks in IoT: Attacks, countermeasures, and open-issues. Electronics 2021, 10, 2365. [Google Scholar] [CrossRef]
- Tsiknas, K.; Taketzis, D.; Demertzis, K.; Skianis, C. Cyber threats to industrial IoT: A survey on attacks and countermeasures. IoT 2021, 2, 9. [Google Scholar] [CrossRef]
- Méndez Real, M.; Salvador, R. Physical side-channel attacks on embedded neural networks: A survey. Appl. Sci. 2021, 11, 6790. [Google Scholar] [CrossRef]
- Hong, S. Side Channel Attacks; MDPI Books: Basel, Switzerland, 2019. [Google Scholar]
- Dogruluk, E.; Macedo, J.; Costa, A. A countermeasure approach for Brute-Force timing attacks on cache privacy in named data networking architectures. Electronics 2022, 11, 1265. [Google Scholar] [CrossRef]
- Randolph, M.; Diehl, W. Power side-channel attack analysis: A review of 20 years of study for the layman. Cryptography 2020, 4, 15. [Google Scholar] [CrossRef]
- Lo, O.; Buchanan, W.J.; Carson, D. Power analysis attacks on the AES-128 S-box using differential power analysis (DPA) and correlation power analysis (CPA). J. Cyber Secur. Technol. 2016, 1, 88–107. [Google Scholar] [CrossRef]
- Azizi, N.; Malekzadeh, H.; Akhavan, P.; Haass, O.; Saremi, S.; Mirjalili, S. IoT–Blockchain: Harnessing the power of Internet of Thing and blockchain for smart supply chain. Sensors 2021, 21, 6048. [Google Scholar] [CrossRef] [PubMed]
- Shahbazi, Z.; Byun, Y.C. Integration of blockchain, IoT and machine learning for multistage quality control and enhancing security in smart manufacturing. Sensors 2021, 21, 1467. [Google Scholar] [CrossRef]
- Gardas, B.B.; Heidari, A.; Navimipour, N.J.; Unal, M. A fuzzy-based method for objects selection in blockchain-enabled edge-IoT platforms using a hybrid multi-criteria decision-making model. Appl. Sci. 2022, 12, 8906. [Google Scholar] [CrossRef]
- Heidari, A.; Jabraeil Jamali, M.A.; Jafari Navimipour, N.; Akbarpour, S. Deep Q-learning technique for offloading offline/online computation in Blockchain-enabled green IoT-edge scenarios. Appl. Sci. 2022, 12, 8232. [Google Scholar] [CrossRef]
- Jafar, U.; Aziz, M.J.A.; Shukur, Z. Blockchain for electronic voting system—Review and open research challenges. Sensors 2021, 21, 5874. [Google Scholar] [CrossRef]
- Srinivasu, P.N.; Bhoi, A.K.; Nayak, S.R.; Bhutta, M.R.; Woźniak, M. Blockchain technology for secured healthcare data communication among the non-terminal nodes in IoT architecture in 5G network. Electronics 2021, 10, 1437. [Google Scholar] [CrossRef]
- Kwon, D.; Hong, S.; Kim, H. Optimizing implementations of non-profiled deep learning-based side-channel attacks. IEEE Access 2021, 10, 5957–5967. [Google Scholar] [CrossRef]
- Le, A.T.; Hoang, T.T.; Dao, B.A.; Tsukamoto, A.; Suzaki, K.; Pham, C.K. A real-time cache side-channel attack detection system on RISC-V out-of-order processor. IEEE Access 2021, 9, 164597–164612. [Google Scholar] [CrossRef]
- Mukhtar, N.; Fournaris, A.P.; Khan, T.M.; Dimopoulos, C.; Kong, Y. Improved hybrid approach for side-channel analysis using efficient convolutional neural network and dimensionality reduction. IEEE Access 2020, 8, 184298–184311. [Google Scholar] [CrossRef]
- Moini, S.; Tian, S.; Holcomb, D.; Szefer, J.; Tessier, R. Power side-channel attacks on BNN accelerators in remote FPGAs. IEEE J. Emerg. Sel. Top. Circuits Syst. 2021, 11, 357–370. [Google Scholar] [CrossRef]
- Ghandali, S.; Ghandali, S.; Tehranipoor, S. Deep K-TSVM: A novel profiled power side-channel attack on AES-128. IEEE Access 2021, 9, 136448–136458. [Google Scholar] [CrossRef]
- Ng, J.S.; Chen, J.; Chong, K.S.; Chang, J.S.; Gwee, B.H. A highly secure FPGA-based dual-hiding asynchronous-logic AES accelerator against side-channel attacks. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2022, 30, 1144–1157. [Google Scholar] [CrossRef]
- Vuppala, S.; Mady, A.E.D.; Kuenzi, A. Moving target defense mechanism for side-channel attacks. IEEE Syst. J. 2019, 14, 1810–1819. [Google Scholar] [CrossRef]
- Ghosh, A.; Nath, M.; Das, D.; Ghosh, S.; Sen, S. Electromagnetic analysis of integrated on-chip sensing loop for side-channel and fault-injection attack detection. IEEE Microw. Wirel. Compon. Lett. 2022, 32, 784–787. [Google Scholar] [CrossRef]
- Jevtic, R.; Otero, M.G. Methodology for complete decorrelation of power supply EM side-channel signal and sensitive data. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 2256–2260. [Google Scholar] [CrossRef]
- Liu, W.; Wang, R.; Qi, X.; Jiang, L.; Jing, J. Multiclass classification-based side-channel hybrid attacks on strong PUFs. IEEE Trans. Inf. Forensics Secur. 2022, 17, 924–937. [Google Scholar] [CrossRef]
- Ensan, S.S.; Nagarajan, K.; Khan, M.N.I.; Ghosh, S. SCARE: Side Channel Attack on In-Memory Computing for Reverse Engineering. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 2040–2051. [Google Scholar] [CrossRef]
- Kim, T.; Shin, Y. ThermalBleed: A practical thermal side-channel attack. IEEE Access 2022, 10, 25718–25731. [Google Scholar] [CrossRef]
- Antognazza, F.; Barenghi, A.; Pelosi, G. Metis: An integrated morphing engine CPU to protect against side channel attacks. IEEE Access 2021, 9, 69210–69225. [Google Scholar] [CrossRef]
- Ha, G.; Chen, H.; Jia, C.; Li, M. Threat model and defense scheme for side-channel attacks in client-side deduplication. Tsinghua Sci. Technol. 2023, 28, 1–12. [Google Scholar] [CrossRef]
- Kulow, A.; Schamberger, T.; Tebelmann, L.; Sigl, G. Finding the needle in the haystack: Metrics for best trace selection in unsupervised side-channel attacks on blinded RSA. IEEE Trans. Inf. Forensics Secur. 2021, 16, 3254–3268. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Fabric-IoT: A blockchain-based access control system in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Hasan, H.R.; Salah, K.; Yaqoob, I.; Jayaraman, R.; Pesic, S.; Omar, M. Trustworthy IoT data streaming using blockchain and IPFS. IEEE Access 2022, 10, 17707–17721. [Google Scholar] [CrossRef]
- Rodrigues, C.K.D.S.; Rocha, V. Towards blockchain for suitable efficiency and data integrity of IoT ecosystem transactions. IEEE Lat. Am. Trans. 2021, 19, 1199–1206. [Google Scholar] [CrossRef]
- Zhou, J.; Feng, G.; Wang, Y. Optimal deployment mechanism of blockchain in resource-constrained IoT systems. IEEE Internet Things J. 2022, 9, 8168–8177. [Google Scholar] [CrossRef]
- Ren, J.; Li, J.; Liu, H.; Qin, T. Task offloading strategy with emergency handling and blockchain security in SDN-empowered and fog-assisted healthcare IoT. Tsinghua Sci. Technol. 2022, 27, 760–776. [Google Scholar] [CrossRef]
- Xu, C.; Qu, Y.; Luan, T.H.; Eklund, P.W.; Xiang, Y.; Gao, L. A lightweight and attack-proof bidirectional blockchain paradigm for Internet of Things. IEEE Internet Things J. 2022, 9, 4371–4384. [Google Scholar] [CrossRef]
- Alrubei, S.M.; Ball, E.; Rigelsford, J.M. A secure blockchain platform for supporting AI-enabled IoT applications at the Edge layer. IEEE Access 2020, 10, 18583–18595. [Google Scholar] [CrossRef]
- Hao, X.; Yeoh, P.L.; Ji, Z.; Yu, Y.; Vucetic, B.; Li, Y. Stochastic analysis of double blockchain architecture in IoT communication networks. IEEE Internet Things J. 2022, 9, 9700–9711. [Google Scholar] [CrossRef]
- Whaiduzzaman, M.; Mahi, M.J.N.; Barros, A.; Khalil, M.I.; Fidge, C.; Buyya, R. BFIM: Performance measurement of a blockchain based hierarchical tree layered fog-IoT microservice architecture. IEEE Access 2021, 9, 106655–106674. [Google Scholar] [CrossRef]
- Ullah, Z.; Raza, B.; Shah, H.; Khan, S.; Waheed, A. Towards blockchain-based secure storage and trusted data sharing scheme for IoT environment. IEEE Access 2022, 10, 36978–36994. [Google Scholar] [CrossRef]
- Qu, Y.; Pokhrel, S.R.; Garg, S.; Gao, L.; Xiang, Y. A blockchained federated learning framework for cognitive computing in Industry 4.0 networks. IEEE Trans. Ind. Inform. 2020, 17, 2964–2973. [Google Scholar] [CrossRef]
- Qiu, C.; Wang, X.; Yao, H.; Du, J.; Yu, F.R.; Guo, S. Networking integrated cloud–edge–end in IoT: A blockchain-assisted collective Q-learning approach. IEEE Internet Things J. 2021, 8, 12694–12704. [Google Scholar] [CrossRef]
- Mothukuri, V.; Parizi, R.M.; Pouriyeh, S.; Dehghantanha, A.; Choo, K.K.R. FabricFL: Blockchain-in-the-Loop Federated Learning for trusted decentralized systems. IEEE Syst. J. 2022, 16, 3711–3722. [Google Scholar] [CrossRef]
- Miao, Y.; Liu, Z.; Li, H.; Choo, K.K.T.; Deng, R.H. Privacy-preserving Byzantine-robust federated learning via blockchain systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2848–2861. [Google Scholar] [CrossRef]
- Weng, J.; Weng, J.; Zhang, J.; Li, M.; Zhang, Y.; Luo, W. DeepChain: Auditable and privacy-preserving deep learning with blockchain-based incentive. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2438–2455. [Google Scholar] [CrossRef]
- Qin, Z.; Ye, J.; Meng, J.; Lu, B.; Wang, L. Privacy-preserving blockchain-based federated learning for marine Internet of Things. IEEE Trans. Comput. Soc. Syst. 2022, 9, 159–173. [Google Scholar] [CrossRef]
- Shahbazi, Z.; Byun, Y.C. Blockchain-based event detection and trust verification using natural language processing and machine learning. IEEE Access 2022, 10, 5790–5800. [Google Scholar] [CrossRef]
- Peng, Z. VFChain: Enabling verifiable and auditable federated learning via blockchain systems. IEEE Trans. Netw. Sci. Eng. 2022, 9, 173–186. [Google Scholar] [CrossRef]
- Sun, J.; Wu, Y.; Wang, S.; Fu, Y.; Chang, X. Permissioned blockchain frame for secure federated learning. IEEE Commun. Lett. 2022, 26, 13–17. [Google Scholar] [CrossRef]
- Ayaz, F.; Sheng, Z.; Tian, D.; Guan, Y.L. A blockchain-based federated learning for message dissemination in vehicular networks. IEEE Trans. Veh. Technol. 2022, 71, 1927–1940. [Google Scholar] [CrossRef]
- Li, J.; Niyato, D.; Hong, C.S.; Park, K.-J.; Wang, L.; Han, Z. Cyber insurance design for validator rotation in sharded blockchain networks: A hierarchical game-based approach. IEEE Trans. Netw. Serv. Manag. 2021, 18, 3092–3106. [Google Scholar] [CrossRef]
- Feng, S.; Wang, W.; Xiong, Z.; Niyato, D.; Wang, P.; Wang, S.S. On cyber risk management of blockchain networks: A game theoretic approach. IEEE Trans. Serv. Comput. 2021, 14, 1492–1504. [Google Scholar] [CrossRef]
- Guo, S.; Dai, Y.; Guo, S.; Qiu, X.; Qi, F. Blockchain meets edge computing: Stackelberg game and double auction based task offloading for mobile blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5549–5561. [Google Scholar] [CrossRef]
- Kruminis, E.; Navaie, K. Game-theoretic analysis of an exclusively transaction-fee reward blockchain system. IEEE Access 2022, 10, 5002–5011. [Google Scholar] [CrossRef]
- Zhang, M.; Eliassen, F.; Taherkordi, A.; Jacobsen, H.A.; Chung, H.-M.; Zhang, Y. Demand–response games for peer-to-peer energy trading with the Hyperledger blockchain. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 19–31. [Google Scholar] [CrossRef]
- Jiang, S.; Li, X.; Wu, J. Multi-leader multi-follower Stackelberg game in mobile blockchain mining. IEEE Trans. Mob. Comput. 2022, 21, 2058–2071. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Ahn, J.; Kim, Y.Y.; Kim, R.Y. A novel WLAN Vehicle-To-Anything (V2X) channel access scheme for IEEE 802.11p-based next-generation connected car networks. Appl. Sci. 2018, 8, 2112. [Google Scholar] [CrossRef]
- Zanaj, E.; Caso, G.; Nardis, L.D.; Mohammadpour, A.; Alay, O.; Benedetto, M.G.D. Energy efficiency in short and wide-area IoT technologies—A survey. Technologies 2021, 9, 22. [Google Scholar] [CrossRef]

| Parameter | Values |
|---|---|
| Simulation area | 1000 × 1100 m2 |
| No. of Mobile IoT device (m) | 500–1000 |
| Communication range of m | 200 m |
| Communication range of LAP | 800 m |
| Speed of m | 10–40 kmph |
| Duration of simulation | 1200 s |
| Rate of data transmission | 27–54 Mbps |
| Channel capacity | 10–20 MHz |
| Initialized energy | 80 J |
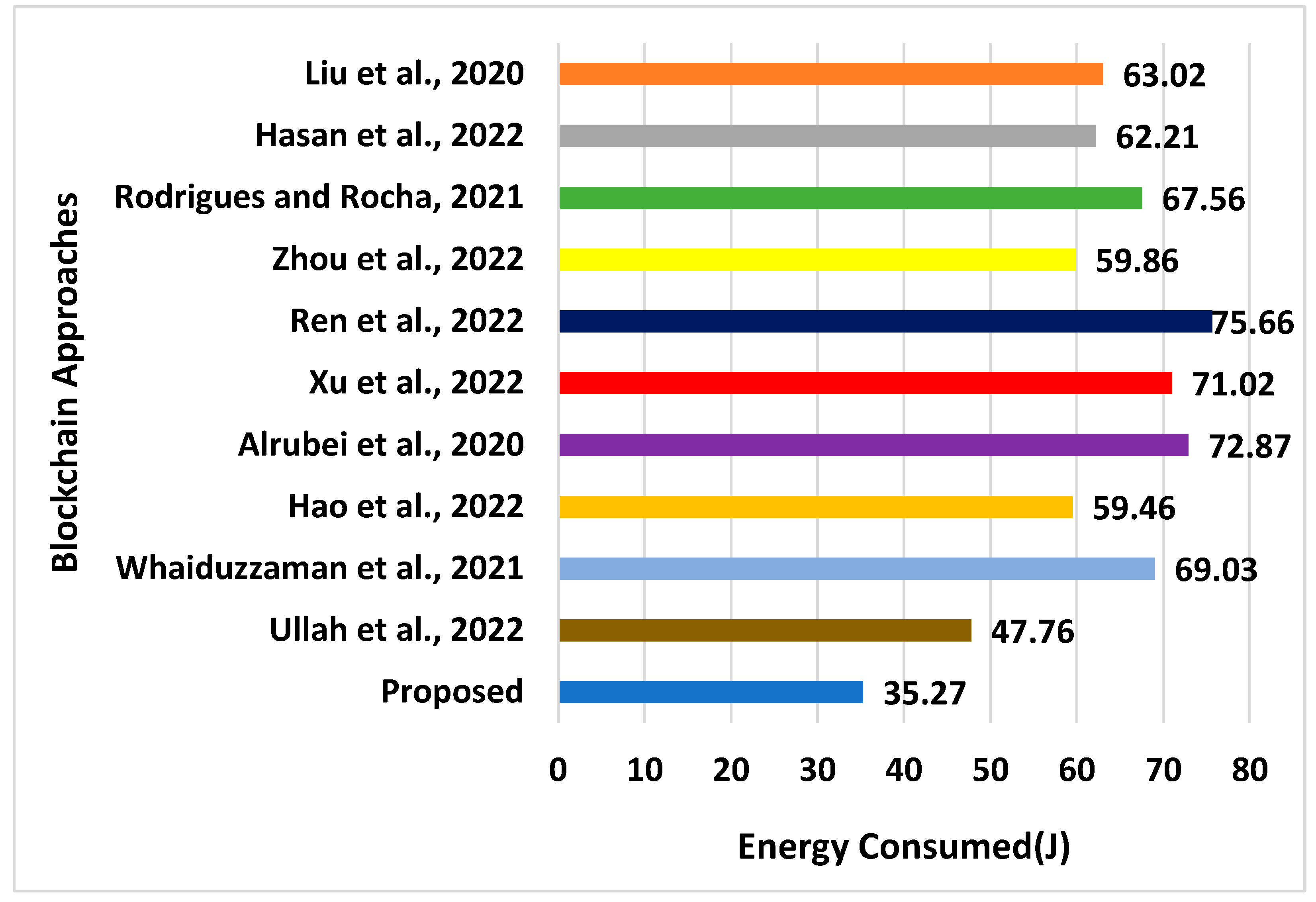
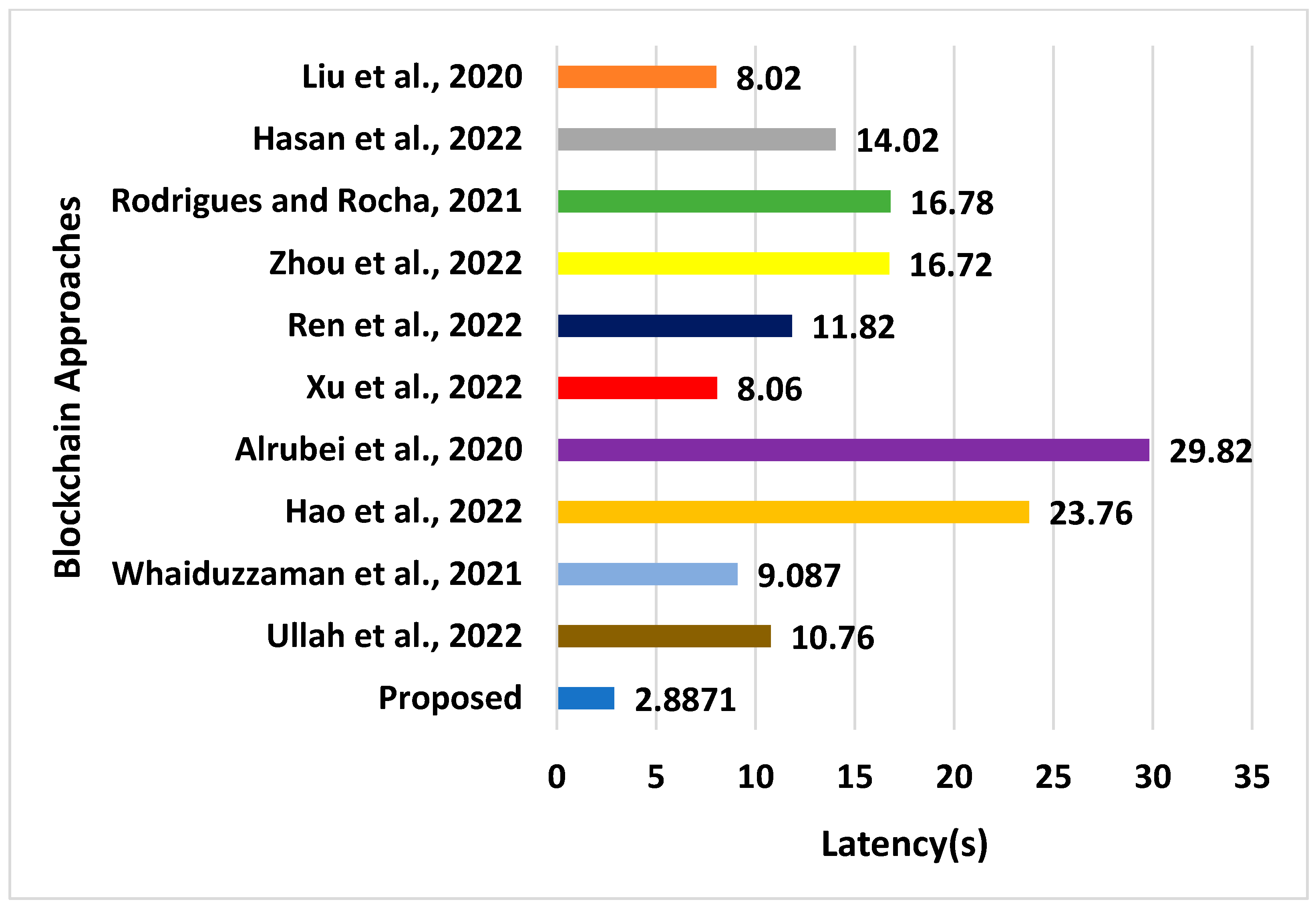
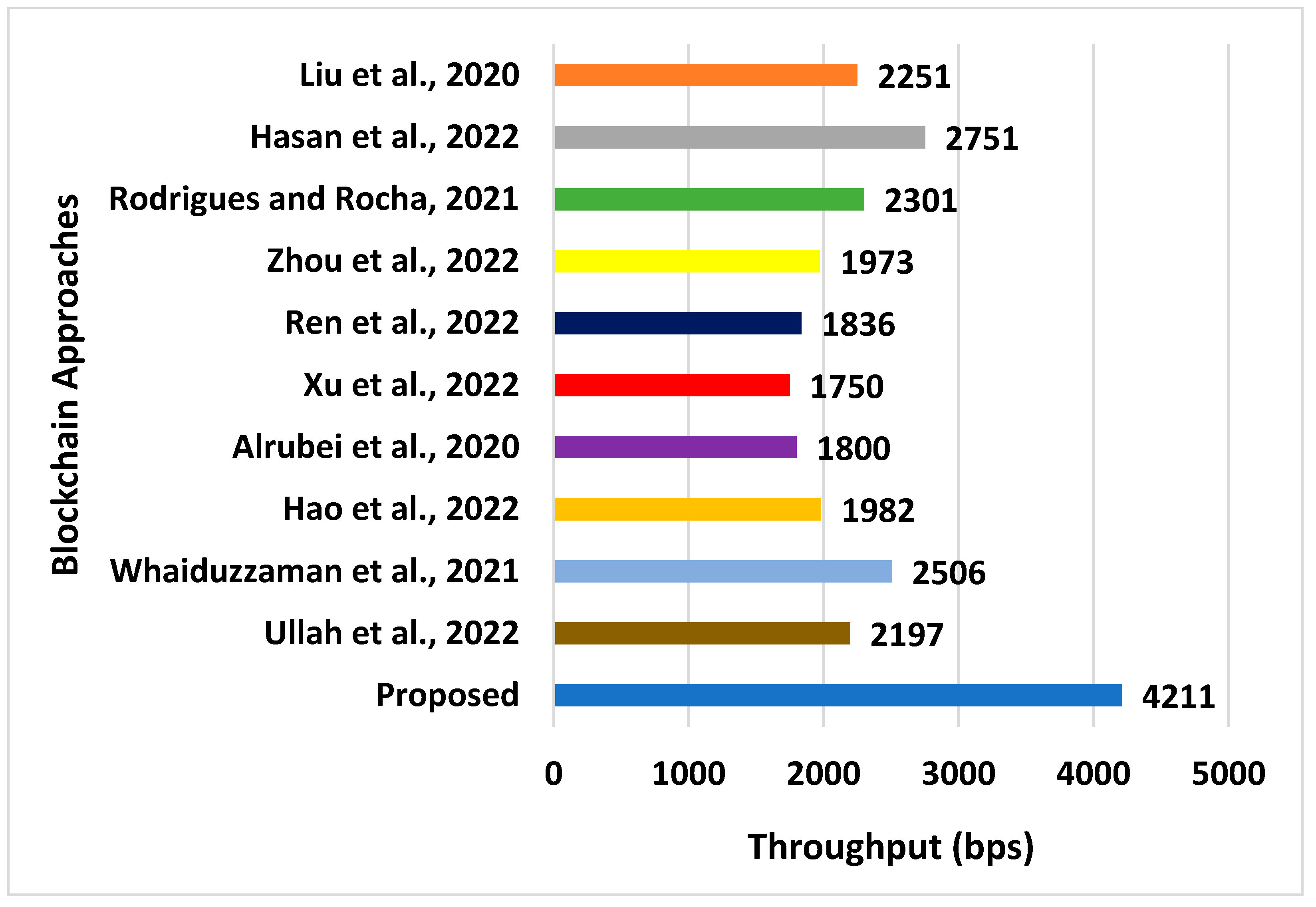
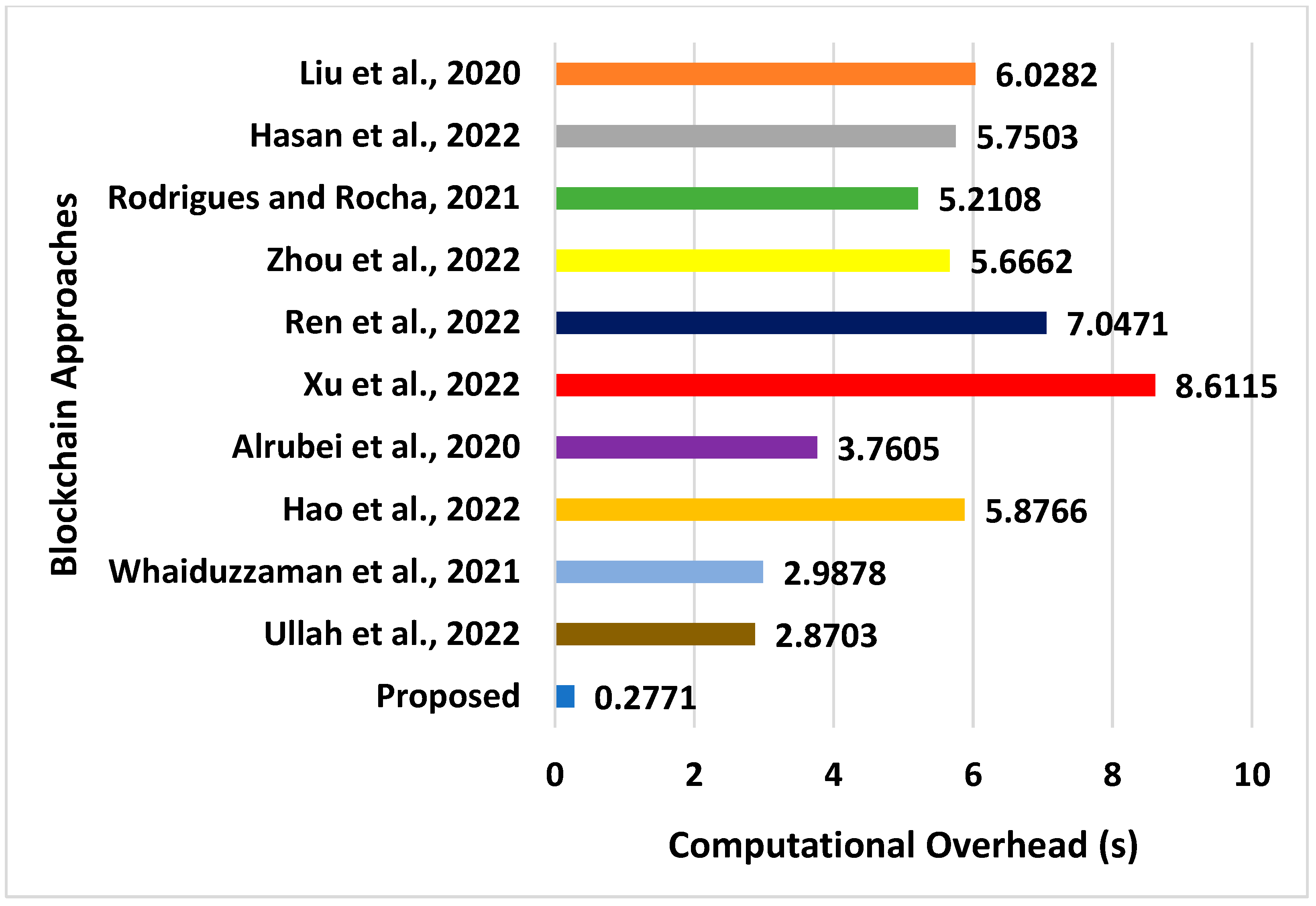
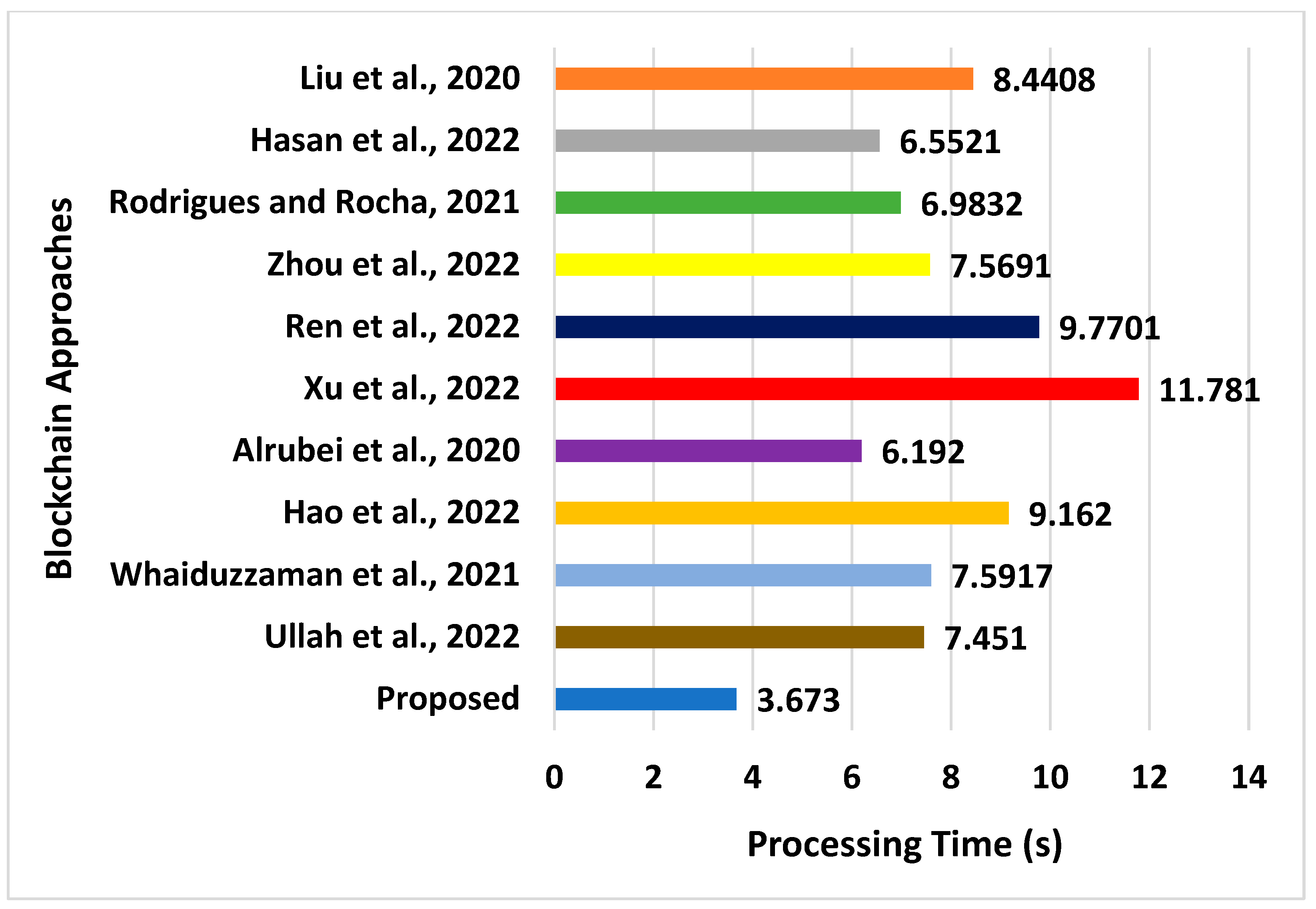
| Approaches | Energy (J) | Latency (s) | Throughput (bps) | Processing Time (s) | Computational Overhead (s) |
|---|---|---|---|---|---|
| Liu et al., 2020 [39] | 63.02 | 8.02 | 2251 | 8.4408 | 6.0282 |
| Hasan et al., 2022 [40] | 62.21 | 14.02 | 2751 | 6.5521 | 5.7503 |
| Rodrigues and Rocha, 2021 [41] | 67.56 | 16.78 | 2301 | 6.9832 | 5.2108 |
| Zhou et al., 2022 [42] | 59.86 | 16.72 | 1973 | 7.5691 | 5.6662 |
| Ren et al., 2022 [43] | 75.66 | 11.82 | 1836 | 9.7701 | 7.0471 |
| Xu et al., 2022 [44] | 71.02 | 8.06 | 1750 | 11.781 | 8.6115 |
| Alrubei et al., 2020 [45] | 72.87 | 29.82 | 1800 | 6.192 | 3.7605 |
| Hao et al., 2022 [46] | 59.46 | 23.76 | 1982 | 9.162 | 5.8766 |
| Whaiduzzaman et al., 2021 [47] | 69.03 | 9.087 | 2506 | 7.5917 | 2.9878 |
| Ullah et al., 2022 [48] | 47.76 | 10.76 | 2197 | 7.451 | 2.8703 |
| Proposed | 35.27 | 2.8871 | 4211 | 3.673 | 0.2771 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Olanrewaju, R.F.; Khan, B.U.I.; Kiah, M.L.M.; Abdullah, N.A.; Goh, K.W. Decentralized Blockchain Network for Resisting Side-Channel Attacks in Mobility-Based IoT. Electronics 2022, 11, 3982. https://doi.org/10.3390/electronics11233982
Olanrewaju RF, Khan BUI, Kiah MLM, Abdullah NA, Goh KW. Decentralized Blockchain Network for Resisting Side-Channel Attacks in Mobility-Based IoT. Electronics. 2022; 11(23):3982. https://doi.org/10.3390/electronics11233982
Chicago/Turabian StyleOlanrewaju, Rashidah Funke, Burhan Ul Islam Khan, Miss Laiha Mat Kiah, Nor Aniza Abdullah, and Khang Wen Goh. 2022. "Decentralized Blockchain Network for Resisting Side-Channel Attacks in Mobility-Based IoT" Electronics 11, no. 23: 3982. https://doi.org/10.3390/electronics11233982
APA StyleOlanrewaju, R. F., Khan, B. U. I., Kiah, M. L. M., Abdullah, N. A., & Goh, K. W. (2022). Decentralized Blockchain Network for Resisting Side-Channel Attacks in Mobility-Based IoT. Electronics, 11(23), 3982. https://doi.org/10.3390/electronics11233982