Abstract
Next-generation wireless communication networks demand high spectrum efficiency to serve the requirements of an enormous number of devices over a limited available frequency spectrum. Device-to-device (D2D) communication with spectrum reuse offers a potential solution to spectrum scarcity. On the other hand, non-orthogonal multiple access (NOMA) as a multiple-access approach has emerged as a key technology to re-use a spectrum among multiple users. A cellular users (CUs) can share their spectrum with D2D users (DUs) and in response, the D2D network can help relay the CU signal to achieve better secrecy from an eavesdropper. Power optimization is known to be a promising technique to enhance system performance in challenging communication environments. This work aimed to enhance the secrecy rate of the CUs where the D2D transmitter (DT) helps in relaying the CU’s message under the amplify and forward (AF) protocol. A power optimization problem is considered under the quality of service constraints in terms of minimum rate requirements at the receivers and maximum power budgets at the transmitters. The problem is a non-convex complex optimization. A deep learning-based solution is proposed and promising results are obtained in terms of the secrecy rate of CU and the rate of D2D users.
1. Introduction
To fulfill the exigent spectrum efficiency and capacity requirements of the fifth generation (5G) wireless communication, device-to-device (D2D) communication, which shares cellular users (CUs)’ spectrum resources, is proposed [1]. To achieve maximum throughput, the D2D communication includes several operational modes, including dedicated mode, reuse mode, and cellular mode [2]. The authors in [3] minimize the total power while satisfying the D2D communication rate requirements through the formation of a coalition game among the D2D links for mode selection. In [4], while satisfying the quality of service (QoS) requirements of CUs, the sum rate of D2D communication is maximized as well.
In addition, spectrum efficiency can be further enhanced using multiple access techniques, i.e., non-orthogonal multiple access (NOMA) [5]. In contrast to orthogonal multiple access (OMA), NOMA technology uses power allocation and successive interference cancellation (SIC) to allow numerous users to send their messages simultaneously over the same spectrum resources [6,7]. A base station (BS) transmitter sends a mixed signal to numerous users in downlink transmission under NOMA, and each user uses SIC technology to identify and decode its signal [8].
Spectrum-efficient technologies can be integrated to reap their associated benefits. Kazmi et al. [9] obtained an enhanced average sum rate with D2D users (DUs) under the NOMA scheme through optimal user clustering and power control. Although the implementation of integrated technologies has its associated advantages, it faces security issues due to the broadcast nature of wireless communication causing malicious over-hearing attacks (e.g., financial statements and patients’ data related to healthcare) [10,11]. Furthermore, the complex network architecture of 5G makes high-level encryption approaches ineffective. Hence, there is a need for less complicated security techniques based on wireless channels’ physical features [12]. The work in [13] considered an underlay D2D communication network modeled as a Poisson cluster process (PCP) with random eavesdroppers’ distribution and derived the expressions for secrecy outage probabilities (SOPs) and coverage outage probabilities (COPs). Furthermore, solutions based on Tabus Search (TS) approach and Coalition Game (CG) formation utilizing interference between DUs and CUs to minimize eavesdropping and to ensure the minimum data rate for both DUs and CUs are presented in [14,15], respectively. Furthermore, in [16], mutual interference amongst CUs and DUs is employed to distract malicious user wiretapping CUs from downlink communication as well as D2D communication.
1.1. Literature Review
With their respective communication reliability assurance, DUs can help in securing CUs’ communication. In [17], mode selection and spectrum partitioning were explored concerning the trade-off between the security of CUs and the reliability of DUs. Furthermore, the work in [18] designates multiple D2D pairs for spectrum sharing to protect CUs’ security. Furthermore, the authors in [19] considered uncertainties in the channel gains of OFDMA for several CUs and DUs, where DUs act as a friendly jammer to protect CUs from eavesdropping.
Although the detrimental interference between DUs and CUs is beneficial with regard to security, increasing the diversity gain of CU links can protect them from eavesdroppers. Based on the information theoretic method, cooperative communication (CC) can improve CUs’ secrecy, utilizing relay to form virtual multiple inputs and multiple outputs (MIMO) [20]. The authors in [21] investigated two different sequential relay selection schemes to ameliorate the CUs’ security and DUs’ throughput. Furthermore, employing CC through untrustable full duplex D2D relay uplink communication is secured. Meanwhile, confidential information and interference are sent towards the relay [22].
In underlay D2D communication, the PLS and sum rate, with minimum processing delay, interference and noise can be augmented with the introduction of the successive interference cancellation (SIC) technique for NOMA in D2D pairs [23]. The author in [24] proposed D2D to act as a relay while employing NOMA for sending CUs’ as well its own signals; however, an eavesdropper can wiretap both CUs’ and DUs’ data. The DT ensures reliability and the full duplex cellular receiver (CR) ensures the security of NOMA transmission through AN injection. Similarly, the work in [25] used a corresponding model, which utilized beamforming to protect the legitimate user from a jamming signal.
The resource allocation decisions made using conventional optimization techniques perform satisfactorily in terms of quality of service (QoS). To guarantee rigorous latency requirements, however, future generations of communication systems look for more advantageous alternatives with minimum computational complexity. Recently, the deep neural network (DNN) has gained significant attention in various engineering areas such as speech recognition [26], image processing [27], etc.
Likewise, DNN is utilized in various modern communication systems [28,29]. The study in [28] covers the use of deep learning (DL) in communication systems for modulation recognition, channel decoding, and detection. A DNN-based technique is reviewed in [29] for receiver design and channel information retrieval. An approach employing DNN that is range-based is described in [30] for the localization of wireless sensor networks submerged in water. The author of [31] suggested a distributed intelligent-agent technique using belief–desire intention (BDI) intelligent agents to manage the development of D2D networks. For underlay D2D communication, transmit power control with the weighted sum rate maximization loss function is suggested in [32]. Similarly, to minimize the co-channel interference between DUs and CUs, the work in [33] uses deep reinforcement learning (DRL) for the selection of available power and channel to maximize spectrum efficiency and system capacity while minimizing interference with CUs. However, in [34], the authors use deep q learning (DQL) to achieve a high D2D throughput. Furthermore, [35] employed a convolution neural network (CNN) for downlink communication to allocate power and beamforming to maximize the spectrum efficiency of D2D within QoS and interference constraints. For a multi-hop D2D communication scenario, the work in [36] developed a DNN framework to find an outage probability (OP) with a small execution time. Similarly, D2D communication in mmWave DNN-based relay selection was proposed in [37]. In their study of conventional downlink OMA transmission, the authors of [38] examined power allocation for sum-rate maximization. According to the research in [39], DL is used to increase the total rate of a NOMA-based relay-aided D2D connection. The work in [40] employed DL to jointly optimize the mode selection and allocate the transmission power among D2D pairs in cellular networks underlaid by D2D communication. These works have created DNN-based algorithms for power distribution issues based on system models.
A few works have been reported for the PLS of wireless communication in the literature using DL. Under the constraint of available power and energy harvesting, the authors in [41] maximized the minimum secrecy rate for legitimate users for a simultaneous wireless information and power transfer (SWIPT) system. A cognitive radio (CR) network’s secrecy rate was also optimized in [42] while being constrained by power and interference leakage.
1.2. Motivation and Problem Statement
In the previous section, for the PLS of cooperative D2D networks, most works utilized traditional optimization techniques for decisions on resource allocation. However, Future wireless networks seek out better options with the least amount of computational complexity. Furthermore, the maximization of the secrecy rate of a legitimate user, while maintaining the reliability of NOMA-enabled cooperative D2D networks underpinning the BS’s downlink communication have not been further researched. Most previous works have employed AN against eavesdroppers, which can improve secrecy performance. However, dedicated power must be allocated for AN injection, which is detrimental concerning the energy efficiency requirements of future wireless networks.
In this research, we discuss the issue of preserving the quality of service (QoS) of the D2D user (DU) and enhancing the secrecy performance of the cellular user (CU) in NOMA-based cooperative D2D communications. The D2D relay passes information from the base station (BS) to the CU, whereas a direct link between the BS and CU already exists in our mobile network. However, there is an outside eavesdropper that wishes to wiretap the data that the BS sends to the CU. On the other hand, CU and D2D receivers (DR) use SIC technology to decipher their respective data. Consequently, the following are our key contributions:
- A novel solution based on DNN for optimizing the SC of NOMA-enhanced cooperative D2D communication network is presented. As compared to [41,42], we employed the DNN framework which considers the total power budget and a minimum rate of DT along with the channel coefficients to act as input. Hence, the power allocation decisions are dependent on the power budget of the BS as well as the minimum rate requirement for D2D communication, making it more practical. Furthermore, the implementation of BN in the hidden layer provides novelty in the framework of DNN to accelerate the training time as well as improves the accuracy without using regularization techniques.
- Previous works have considered the optimization of the secrecy rate of D2D communication through relay selection or jamming employing artificial noise injection while only considering the security of D2D communication. However, none focused on the security of the CU’s downlink communication from BS, which is more vulnerable to eavesdropping. Contrary to existing works [24,25], we employed the DT working in spectrum reuse mode, as a NOMA-enhanced relay to maximize the SC of a cellular user (CU) through diversity gain for downlink communication, in exchange for the reliability of D2D transmission making the solution more practical.
2. System Model
A NOMA-enhanced cooperative D2D communication network is considered, as shown in Figure 1.
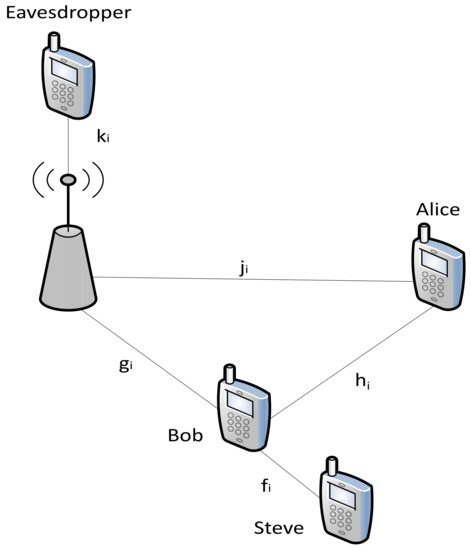
Figure 1.
System model of NOMA-enhanced cooperative D2D communication network.
A BS broadcasts a confidential message to a CU (Alice). However, an eavesdropper tries to wiretap the downlink communication. Aiming to hit two birds with one stone, Alice SC is maximized whereas Bob underlays the spectrum for D2D communication. We assume that all the nodes only have a single antenna each. The private information transmitted by BS is received by Bob and Alice during the first hop. Then, in the second hop, Bob amplifies and forwards the received signal to the D2D receiver (Steve) through superposition coding, and sends it to Alice and Steve using NOMA. The channel coefficients between Alice and BS, Bob and BS, eavesdropper and BS, Bob and Alice, and Bob and Steve are denoted by , , , , and , respectively, for i = 1, 2, …, N.
Under NOMA, Steve is the strong user due to being closer to Bob and Alice is the weak user due to being at a larger distance from Bob. In the first time slot, the broadcast signal received by Bob and Alice is given as:
where is the power allocated by BS on the channel. is a broadcast signal, which is sent by BS and received by Alice and Bob. Furthermore, represents the additive white Gaussian noise (AWGN) having zero mean and variance. Furthermore, represents the AWGN having zero mean and variance . In the second time slot, the broadcast signal destined for Alice is amplified by Bob using AF protocol. To satisfy Alice’s QoS requirements, the power allocation coefficient is set so that ensures that the weak user is allocated more power than the strong user. Then, the received signal at Alice is
where represents the amplification factor given by . According to the NOMA scheme in [43], represents the interference signal of the strong user Bob. Where is the channel between Bob and Alice, represents AWGN. Meanwhile, the eavesdropper also receives a copy of the signal broadcast by BS to Alice in the first time slot. The signal received at eavesdropper is given by
where represents the channel gain from BS to eavesdropper and is the additive white Gaussian noise having a mean value equal to zero and variance. The transmitted signals are and , respectively. Therefore, the rates at Alice [44], Steve, and eavesdropper can be written as
where
denotes the signal-to-noise ratio (SNR) of Alice, while and denote received the SNRs by Steve and Eve, respectively. With (4) and (6), the secrecy rate [45] of AF-based NOMA system for Alice is given by
where
We aim to obtain optimal power allocation to BS and Bob to maximize the sum secrecy rate of Alice subject to the total power budget and NOMA power allocation constraints. Moreover, the Steve rate is guaranteed through constraints in the optimization.
The optimization problem can be formulated as P1:
The first two power allocation constraints make sure that the total power allocated over all channels is within the maximum available power budget of the corresponding nodes. The third constraint ensures successful NOMA transmission. The fourth constraint guarantees that Steve should achieve a data rate as per its minimum requirements .
3. Proposed Solution
The aforementioned problem P1 is non-convex and, hence, standard convex optimization techniques are unable to provide a solution. Traditional non-convex optimization algorithms take a long time to converge [40]. This in turn is not suitable for 5G communication systems with fast-changing conditions of channels. To determine an efficient solution for the problem P1, we appoint a deep learning-based approach.
A feed-forward DNN represents a function whose input and output vectors are, respectively, and . Furthermore, the parameters of the neural network are defined by . More precisely, for a neuron consists of where and are the respective weight and bias value of the neuron. The architecture of DNN is composed of an input layer, a hidden layer, and an output layer, as shown in Figure 2. The values of the BS power budget, the D2D receiver’s threshold rate , and the instantaneous channel gains are given to the input layer as vectors following the suggested DNN framework. Hence, the output vector (i.e., allocated power) is obtained at the output layer, where represents the parameters for the neural network. More specifically, for the neuron, parameter is characterized as , where the weight is and the bias of the neuron is .
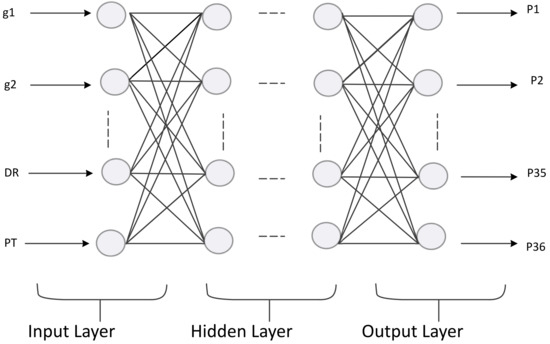
Figure 2.
DNN model.
A three-DNN model is shown in Figure 2, with an input layer, hidden layer, and output layer. Each node of the hidden and output layer consists of a sigmoid activation function given by:
where the activation function’s input is x. Owing to the nonlinearity of the sigmoid function, the neural network can be tailored to the objective P1 function’s nonlinearity [46].
During the training phase, as shown in Figure 3, an appropriate response is learned by the DNN in a supervised fashion from the input and output vectors with a minimizing cost function of DNN using the Adam optimizer (a variant of stochastic gradient descent), i.e.,
in which denotes the number of samples. With a large number of samples, deep learning can approximate an actual solution.
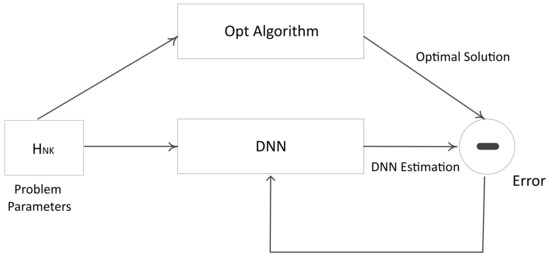
Figure 3.
Training of DNN.
The genetic algorithm (GA) (Algorithm 1) was first employed to solve the optimization problem P1. For this, initially, the limits of the 36 genes of the chromosome are set according to the constraints of the optimization problem, and the number of generations is set to . Following this, a parent population P is randomly generated with chromosomes. Furthermore, for cross-over, following the cross-over rate, parents are randomly selected from P, whereas chromosomes whose values depend on the mutation rate have the random gene per pair of parent chromosomes exchanged. Additionally, the best current solution p(1) is locally searched for an optimal solution with a decrease in step size per generation. Furthermore, the offspring generated thus far are merged in P, and top chromosomes are arranged in descending order for the selection of the best solution . Finally, after generations, the optimal solution is saved for the maximization of secrecy capacity under the power budget and NOMA power allocation fairness constraints.
| Algorithm 1 GA-based power allocation algorithm |
Randomly create the parent population P with size where each member has 36 variables having a set limit; for it = 1 to MaxIT do Select pairs from P; (n); Select and individuals from P; Decrease step-size for local search (it); (P); Sort individuals in descending order of fitness score; Find the best solution in the end for Save the best found solution; Return |
The training process for DNN is provided in depth by Algorithm 2. First, the input and output of the DNN are applied to the samples produced by GA simulations. The settings of the DNN parameters, namely the learning, epochs, weights, and biases, are then initialized. After that, each activation of k hidden layers is subjected to batch normalization (BN). The Algorithm 3 shows the step for normalization of the mini-batch B using the mean and variance of the activation along with the scaling and shifting of activation. Furthermore, is included in mini-batch variance as a constant for stability. On the other hand, in the DNN, tuning parameters and are optimized during the training to ensure that the inputs to activation functions are not constrained in a linear regime of nonlinearity.
Furthermore, BN is applied to activations in the form of mini-batches. For a given mini batch, the parameters of DNN are frozen for inference. Utilizing the mean and variances of activation in the mini-batch is part of the back-propagation process. This process is repeated for all mini-batches and the mean and variance values used in back-propagation for the minimization of the mean square error are averaged over all mini-batches. The advantage of the inclusion of BN in the training process is to remove overfitting without considering the setting of the learning rate and parameter initialization. Furthermore, the training of DNN has a guarantee of fast convergence. In the testing phase, input parameters are given to the DNN while maintaining a constant bias and weight value, to recover a roughly optimal output.
| Algorithm 2 Training of DNN |
Obtain values of system parameters and the resultant optimal solutions for i = 1, …, 64 from a search heuristic genetic algorithm-based solution. Initialize epoch value, weights , biases , learning rate , number of hidden layers and number of nodes per hidden layer. Input Network N with trainable parameters and ; subset of activations Output: Batch Normalized network for inference, for j = 1 to epoch value do ←N //Training BN network for k = 1…K do Add transformation to (Algorithm 3) Modify each layer in with input to take instead end for Train to optimize parameters and //Inference BN network with frozen parameters for k = 1 … K do for clarity, , , process multiple training mini batches B each of size m and average over them; in , replace the transform with end for end for Save the trained DNN |
| Algorithm 3 Batch normalization transform applied to activation x over a mini batch |
Input: Values of x over a mini-batch: Parameters to be learned , Output: //mini-batch mean //mini batch variance //normalize //scale and shift |
4. Results and Discussion
In this section, we assess the results of the proposed DNN-based solution. Using GA, the secrecy rate maximization problem, which takes into account independently and identically distributed Rayleigh fading channels, is addressed. For finding an approximate optimal solution, the cross-over, mutation rate, and the number of generations were attuned using the trial-and-error approach [47]. Unless otherwise stated, DNN was trained for 10,000 samples, split into a train and test set, with a ratio of 4:1, where the value of the learning rate is set to be for the corresponding 10,000 epochs. Furthermore, every sample consists of input features, i.e., channel gains, the BS’s power budget, and the minimum data rate requirement for D2D communication, i.e., . For training and testing, we employed the jupyter notebook 6.4.6 accompanied by python 3.9.7 and the tensor flow 2.6.0 library. Additionally, a core i7 computer with a 2.7 GHz processor and 32 GB of RAM was used to perform the simulations. Finally, the DNN-based power optimization solution is evaluated against the GA-based opt solution generated in Section 3. Without sacrificing generality, we assume that has a value of 0.01.
Figure 4 shows the curves of the secrecy rate vs the power budget of the BS for GA-based solutions under different D2D minimum rate requirements. The average results are plotted with the GA tuning parameter mutation rate, cross-over rate, and the number of generations set to the values of 10, 30, and 400, respectively. As per the anticipation, the secrecy rate curve increases for larger values of . Furthermore, the secrecy rate curve for has the best performance concerning the rest of the curves with higher values of . However, it can also be observed that the increase in leads to a decline in secrecy rate performance. This is due to a subsequent decrease in allocated power by on the OFDM subchannels between and CU.
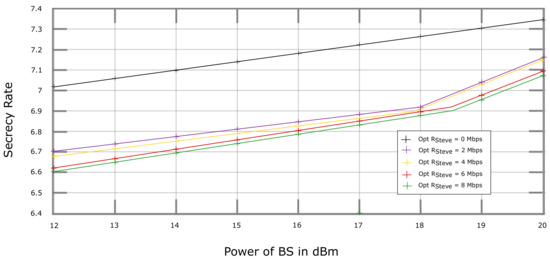
Figure 4.
Secrecy Rate vs. Total Power Budget of BS: GA-based solution.
We implemented the BN technique in Section 3, as mentioned previously, between the hidden layer and the output layer. This technique is well known for accelerating the training of DNN while overcoming the overfitting caused by a large number of neurons in the hidden layer [48]. Figure 5 shows the graphs of the secrecy rate vs. the of the BS with and without the implementation of BN in a DNN with one hidden layer consisting of six neurons. It can be observed that DNN with BN had a closer performance to that of opt as compared to without it.
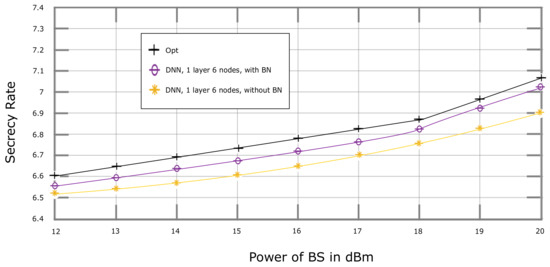
Figure 5.
Performance comparison of DNN algorithm with and without batch normalization.
Furthermore, Figure 6 depicts the convergence of the loss function of DNN, with and without the implementation of BN. It can be seen that the mean square error (mse) in each epoch converges much faster towards a value of 0 with the inclusion of BN as compared to without it.
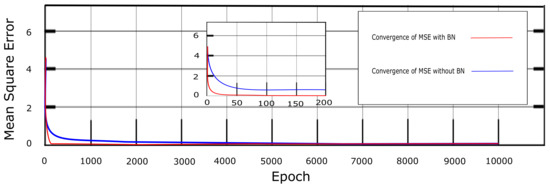
Figure 6.
Convergence.
Figure 7 depicts secrecy rate vs. plots obtained through the simulation of our proposed DNN-based solution, where . As expected, it has the best secrecy rate performance for the different numbers of neurons in the hidden layer. An increase in the number of neurons leads to a secrecy rate performance closer to Opt. In Figure 8, while keeping all the parameters similar to Figure 7, the value of is increased to 4 Mbps, which results in a trade-off in-between the secrecy rate and . However, in Figure 9, an increase in the value of to 8 Mbps leads to the worst secrecy rate performance as compared to the previously mentioned figures.
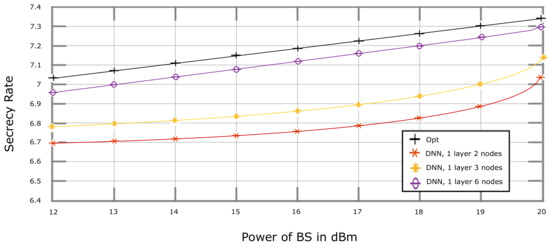
Figure 7.
Secrecy Rate vs. Power Budget of BS, performance of DNN Algorithm with different numbers of nodes, where D2D communication threshold rate, 0 Mbps.
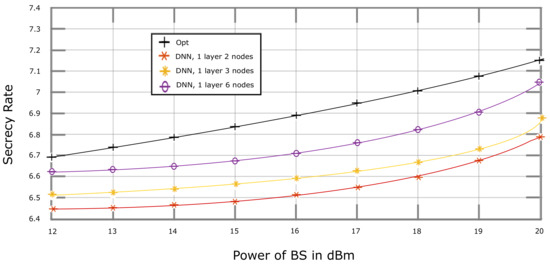
Figure 8.
Secrecy Rate vs. Power Budget of BS, performance of DNN algorithm with different number of nodes, where D2D communication threshold rate, 4 Mbps.
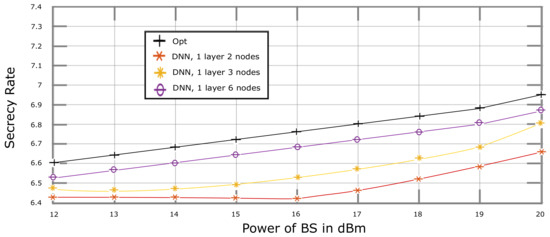
Figure 9.
Secrecy Rate vs. Power Budget of BS, performance of DNN algorithm with a different number of nodes, where D2D communication threshold rate, 8 Mbps.
As far as the prediction time of DNNs with 2, 3, and 6 neurons and one hidden layer is concerned, Table 1 enlists the corresponding values. Similarly, their respective training times are 1539.5 s, 1682 s, and 1728.4 s. Hence, considering both the training and testing time, the average computational times are 1.545 s, 1.7 s, and 1.8 s, individually. The following equation is used for computational time calculations. [39]. Where is the time taken for the DNN to train, represents the training time of the sample, and the number of samples is represented by . In practical communication systems, the value is large and the term on the left side of the equation will become 0. Hence, will converge to the values mentioned in Table 1.

Table 1.
Average simulation time for different numbers of neurons in the hidden layer.
5. Conclusions
In this work, we studied the power optimization problem for a NOMA-enhanced cooperative D2D communication network. The power is allocated at the BS in the first hop and at the DT in the second hop for the downlink communication from BS to the CU, where DT acts as an AF relay. The secrecy rate maximization problem under the constraint of minimum rate assurance for D2D communication and the power budget of BS and DT resulted in a non-convex problem. We presented a novel BN-DNN-based supervised learning algorithm with data samples obtained from a GA-based solution. Extensive simulations were performed to test the performance of the proposed algorithm. The simulation results demonstrated that the BN-DNN-based solution was able to have a performance almost near to the approximate optimal results obtained through GA with low computational time. It is also observed that the implementation of BN in the hidden layers greatly enhanced the performance of the proposed solution.
Author Contributions
Conceptualization, N.A.; Methodology, N.A.; Software, N.A.; Validation, G.A.S.S.; Formal analysis, N.A.; Investigation, N.A.; Data curation, N.A.; Writing—original draft, N.A.; Writing—review & editing, W.U.K.; Visualization, G.A.S.S.; Supervision, G.A.S.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- ElSawy, H.; Hossain, E.; Alouini, M.S. Analytical modeling of mode selection and power control for underlay D2D communication in cellular networks. IEEE Trans. Commun. 2014, 62, 4147–4161. [Google Scholar] [CrossRef]
- Gandotra, P.; Jha, R.K. Device-to-device communication in cellular networks: A survey. J. Netw. Comput. Appl. 2016, 71, 99–117. [Google Scholar] [CrossRef]
- Akkarajitsakul, K.; Phunchongharn, P.; Hossain, E.; Bhargava, V.K. Mode selection for energy-efficient D2D communications in LTE-advanced networks: A coalitional game approach. In Proceedings of the 2012 IEEE International Conference on Communication Systems (ICCS), Singapore, 21–23 November 2012; pp. 488–492. [Google Scholar]
- Zhu, D.; Wang, J.; Swindlehurst, A.L.; Zhao, C. Downlink resource reuse for device-to-device communications underlaying cellular networks. IEEE Signal Process. Lett. 2014, 21, 531–534. [Google Scholar] [CrossRef]
- Zuo, Y.; Zhu, X.; Jiang, Y.; Wei, Z.; Zeng, H.; Wang, T. Energy efficiency and spectral efficiency tradeoff for multicarrier NOMA systems with user fairness. In Proceedings of the 2018 IEEE/CIC International Conference on Communications in China (ICCC), Beijing, China, 16–18 August 2018; pp. 666–670. [Google Scholar]
- Wang, B.; Dai, L.; Wang, Z.; Ge, N.; Zhou, S. Spectrum and energy-efficient beamspace MIMO-NOMA for millimeter-wave communications using lens antenna array. IEEE J. Sel. Areas Commun. 2017, 35, 2370–2382. [Google Scholar] [CrossRef]
- Chraiti, M.; Ghrayeb, A.; Assi, C. A NOMA scheme exploiting partial similarity among users bit sequences. IEEE Trans. Commun. 2018, 66, 4923–4935. [Google Scholar] [CrossRef]
- Ali, M.S.; Tabassum, H.; Hossain, E. Dynamic user clustering and power allocation for uplink and downlink non-orthogonal multiple access (NOMA) systems. IEEE Access 2016, 4, 6325–6343. [Google Scholar] [CrossRef]
- Kazmi, S.M.A.; Tran, N.H.; Ho, T.M.; Manzoor, A.; Niyato, D.; Hong, C.S. Coordinated Device-to-Device Communication With Non-Orthogonal Multiple Access in Future Wireless Cellular Networks. IEEE Access 2018, 6, 39860–39875. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Chu, Z.; Zhang, Y. Secure transmission for heterogeneous cellular networks with wireless information and power transfer. IEEE Syst. J. 2018, 12, 3755–3766. [Google Scholar] [CrossRef]
- Zhong, Y.; Ge, X.; Han, T.; Li, Q.; Zhang, J. Tradeoff between delay and physical layer security in wireless networks. IEEE J. Sel. Areas Commun. 2018, 36, 1635–1647. [Google Scholar] [CrossRef]
- Wang, W.; Teh, K.C.; Luo, S.; Li, K.H. Physical layer security in heterogeneous networks with pilot attack: A stochastic geometry approach. IEEE Trans. Commun. 2018, 66, 6437–6449. [Google Scholar] [CrossRef]
- Lyu, J.; Zheng, T.X.; Huang, K.W.; Feng, Y.; Wang, H.M. Secure transmissions of D2D underlay cellular networks with Poisson cluster process. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Ahmed, M.; Shi, H.; Chen, X.; Li, Y.; Waqas, M.; Jin, D. Socially aware secrecy-ensured resource allocation in D2D underlay communication: An overlapping coalitional game scheme. IEEE Trans. Wirel. Commun. 2018, 17, 4118–4133. [Google Scholar] [CrossRef]
- Ashtiani, A.F.; Pierre, S. Power allocation and resource assignment for secure D2D communication underlaying cellular networks: A Tabu search approach. Comput. Netw. 2020, 178, 107350. [Google Scholar] [CrossRef]
- Javan, M.R.; Mokari, N. Resource Allocation in Secure Full-Duplex D2D Communications Using Zero Forcing Beamforming. In Proceedings of the Electrical Engineering (ICEE), Iranian Conference on Electrical Engineering, Mashhad, Iran, 8–10 May 2018; pp. 586–591. [Google Scholar]
- Zhang, Y.; Shen, Y.; Jiang, X.; Kasahara, S. Mode selection and spectrum partition for D2D inband communications: A physical layer security perspective. IEEE Trans. Commun. 2018, 67, 623–638. [Google Scholar] [CrossRef]
- Wang, L.; Liu, J.; Chen, M.; Gui, G.; Sari, H. Optimization-based access assignment scheme for physical-layer security in D2D communications underlaying a cellular network. IEEE Trans. Veh. Technol. 2018, 67, 5766–5777. [Google Scholar] [CrossRef]
- Arian, F.; Javan, M.R.; Yamchi, N.M. Secure green D2D communication in OFDMA based networks with imperfect channel knowledge. Wirel. Netw. 2021, 27, 3147–3164. [Google Scholar] [CrossRef]
- Liu, K.R.; Sadek, A.K.; Su, W.; Kwasinski, A. Cooperative Communications and Networking; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar]
- Moualeu, J.M.; Ngatched, T.M. Relay selection strategies for physical-layer security in D2D-assisted cellular networks. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–7. [Google Scholar]
- Song, X.; Xia, L.; Xu, S.; Wang, Y. Secure Communication for Uplink Cellular Networks Assisted with Full-Duplex Device-to-Device User. Future Internet 2020, 12, 175. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Kumar, N. Secrecy-ensured NOMA-based cooperative D2D-aided fog computing under imperfect CSI. J. Inf. Secur. Appl. 2021, 59, 102812. [Google Scholar] [CrossRef]
- Li, Q.; Ren, P.; Xu, D. Security enhancement and QoS provisioning for NOMA-based cooperative D2D networks. IEEE Access 2019, 7, 129387–129401. [Google Scholar] [CrossRef]
- Li, Q.; Ren, P.; Du, Q.; Xu, D.; Xie, Y. Safeguarding NOMA enhanced cooperative D2D communications via friendly jamming. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–5. [Google Scholar]
- Dominguez-Morales, J.P.; Liu, Q.; James, R.; Gutierrez-Galan, D.; Jimenez-Fernandez, A.; Davidson, S.; Furber, S. Deep spiking neural network model for time-variant signals classification: A real-time speech recognition approach. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–8. [Google Scholar]
- Salman, M. Hiperspektral ve Lidar Verilerinin Öznitelik Ve Karar Seviyelerinde Tümleştirilmesi Ve Derin Evrişimli Sinir Ağlarıyla Sınıflandırılması. Master Thesis, Hacettepe University, Ankara, Turkey, 18 April 2018. [Google Scholar]
- Wang, T.; Wen, C.K.; Wang, H.; Gao, F.; Jiang, T.; Jin, S. Deep learning for wireless physical layer: Opportunities and challenges. China Commun. 2017, 14, 92–111. [Google Scholar] [CrossRef]
- He, H.; Jin, S.; Wen, C.K.; Gao, F.; Li, G.Y.; Xu, Z. Model-driven deep learning for physical layer communications. IEEE Wirel. Commun. 2019, 26, 77–83. [Google Scholar] [CrossRef]
- Dong, Y.; Li, Z.; Wang, R.; Zhang, K. Range-based localization in underwater wireless sensor networks using deep neural network. In Proceedings of the 2017 16th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Pittsburgh, PA, USA, 18–21 April 2017; pp. 321–322. [Google Scholar]
- Ioannou, I.; Vassiliou, V.; Christophorou, C.; Pitsillides, A. Distributed artificial intelligence solution for D2D communication in 5G networks. IEEE Syst. J. 2020, 14, 4232–4241. [Google Scholar] [CrossRef]
- Lee, W.; Kim, M.; Cho, D.H. Deep learning based transmit power control in underlaid device-to-device communication. IEEE Syst. J. 2018, 13, 2551–2554. [Google Scholar] [CrossRef]
- Wang, D.; Qin, H.; Song, B.; Xu, K.; Du, X.; Guizani, M. Joint resource allocation and power control for D2D communication with deep reinforcement learning in MCC. Phys. Commun. 2021, 45, 101262. [Google Scholar] [CrossRef]
- Pires, L.B.; de Carvalho, P.H.P. Deep Q-Learning Framework for Improving Spectral Efficiency in D2D Communication. In Proceedings of the XXXVIII Simpósio Brasileiro de Telecomunicações e Processamento de Sinais, SBrT, Florianópolis, Brazil, 22–25 November 2020. [Google Scholar]
- Wang, Y.; Wang, S.; Liu, L. Joint beamforming and power allocation using deep learning for D2D communication in heterogeneous networks. IET Commun. 2020, 14, 3095–3101. [Google Scholar] [CrossRef]
- Nguyen, T.V.; Huynh-The, T.; Shim, K.; An, B. On the performance of multihop D2D communications in cognitive IoT networks with energy harvesting: A deep learning approach. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Seoul, Republic of Korea, 1–3 November 2020; pp. 1–4. [Google Scholar]
- Abdelreheem, A.; Omer, O.A.; Esmaiel, H.; Mohamed, U.S. Deep learning-based relay selection in D2D millimeter wave communications. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Beijing, China, 17–19 June 2019; pp. 1–5. [Google Scholar]
- Kim, J.; Park, J.; Noh, J.; Cho, S. Autonomous Power Allocation Based on Distributed Deep Learning for Device-to-Device Communication Underlaying Cellular Network. IEEE Access 2020, 8, 107853–107864. [Google Scholar] [CrossRef]
- Ali, Z.; Sidhu, G.A.S.; Gao, F.; Jiang, J.; Wang, X. Deep learning based power optimizing for noma based relay aided d2d transmissions. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 917–928. [Google Scholar] [CrossRef]
- Ron, D.; Lee, J.R. Learning-based joint optimization of mode selection and transmit power control for D2D communication underlaid cellular networks. Expert Syst. Appl. 2022, 198, 116725. [Google Scholar] [CrossRef]
- Li, J.; Zhao, H.; Huang, Y.; Zhang, M.; Lal, S.P. Deep learning driven physical layer security for a simultaneously wireless information and power transfer network. Alex. Eng. J. 2022, 61, 7429–7439. [Google Scholar] [CrossRef]
- Zhang, M.; Cumanan, K.; Thiyagalingam, J.; Tang, Y.; Wang, W.; Ding, Z.; Dobre, O.A. Exploiting deep learning for secure transmission in an underlay cognitive radio network. IEEE Trans. Veh. Technol. 2021, 70, 726–741. [Google Scholar] [CrossRef]
- Liang, X.; Wu, Y.; Ng, D.W.K.; Zuo, Y.; Jin, S.; Zhu, H. Outage Performance for Cooperative NOMA Transmission with an AF Relay. IEEE Commun. Lett. 2017, 21, 2428–2431. [Google Scholar] [CrossRef]
- Cheng, J.; Li, H.; Guo, Y.X.; Li, H.Y.; Xiao, K.X. Power Allocation and Receiver Design for D2D Assisted Cooperative Relaying Downlink System Using NOMA. IEEE Access 2020, 8, 210663–210677. [Google Scholar] [CrossRef]
- Liu, X. Outage Probability of Secrecy Capacity over Correlated Log-Normal Fading Channels. IEEE Commun. Lett. 2013, 17, 289–292. [Google Scholar] [CrossRef]
- Eisen, M.; Zhang, C.; Chamon, L.F.; Lee, D.D.; Ribeiro, A. Learning optimal resource allocations in wireless systems. IEEE Trans. Signal Process. 2019, 67, 2775–2790. [Google Scholar] [CrossRef]
- Črepinšek, M.; Liu, S.H.; Mernik, M. Exploration and exploitation in evolutionary algorithms: A survey. ACM Comput. Surv. 2013, 45, 1–33. [Google Scholar] [CrossRef]
- Ioffe, S.; Szegedy, C. Batch normalization: Accelerating deep network training by reducing internal covariate shift. In Proceedings of the International Conference on Machine Learning, Lille, France, 7–9 July 2015; pp. 448–456. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).