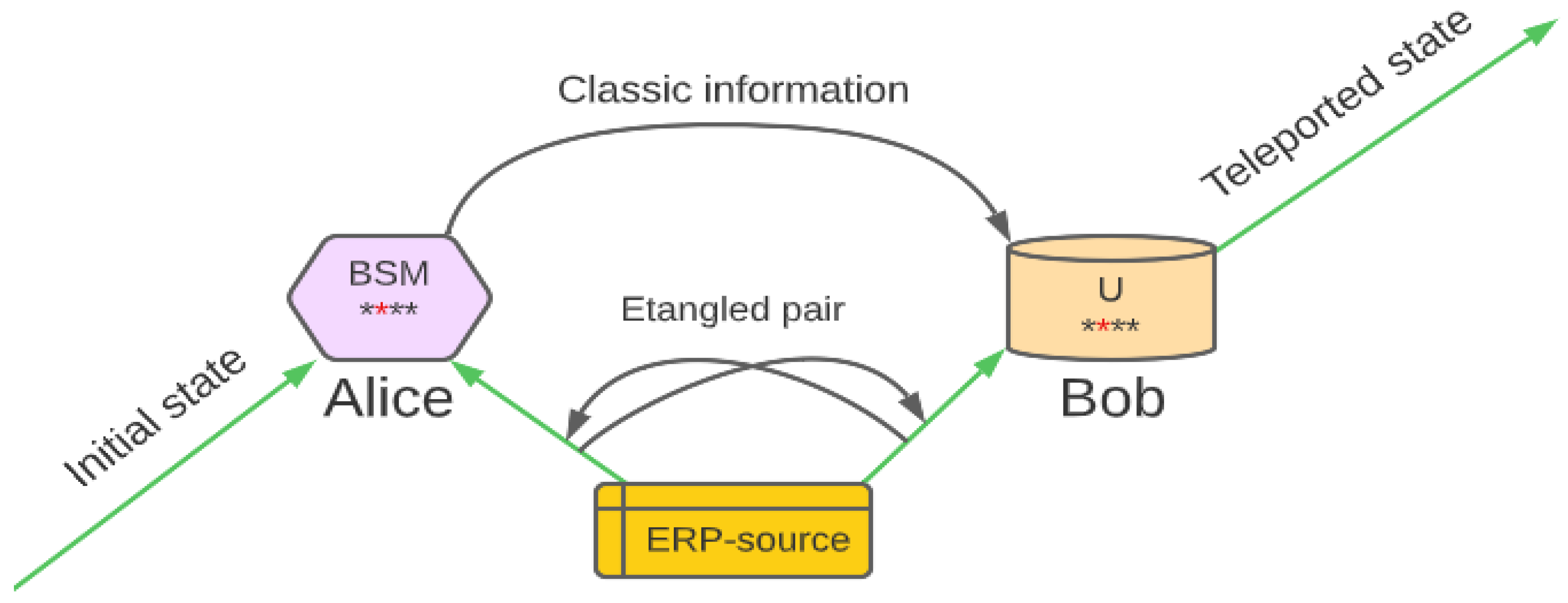
1. Introduction
The article is devoted to quantum cryptography. It particularly concerns quantum cryptographic protocols, which scientists have been investigating for almost forty years. Quantum cryptography is considered technology capable of adding to the new, unique look of telecommunication networks of the future.
However, no one can predict with full confidence what the formed quantum infrastructure will look like, and to what outcome it may lead. Today, quantum cryptography allows us not only to provide increased protection against unauthorized access to transmitted information, but also to reveal the very existence of such attempt with higher probability. In modern information-based society, this aspect is extremely important, since humanity is striving to achieve, in fact, complete digitalization.
In parallel with this process, the global modernization of technological equipment, computer software and hardware is rapidly taking place; load on telecommunications networks is increasing. Volumes of secret data, confidential information, and personal data of users are increasing. At the same time, the number of computer security incidents is inevitably increasing. Attackers are modernizing the types of threats and ways to implement them, causing serious problems with information security and data protection.
Maintaining the reliability and operability of technical equipment in communication networks is becoming an increasingly difficult task. Recent cyberattacks in various countries of the world have partially paralyzed the public activity of citizens and caused serious problems in government apparatus. Many countries face similar incidents of computer security every day, and in some cases, users become practically helpless. National governments are extremely concerned about this situation, which threatens their critical infrastructure.
The moment is not far off when the process of modernization of the available means of information protection will come to a standstill, and then the transition to safer quantum technologies will become the ubiquitous inevitability.
Therefore, many countries of the world are optimistic for quantum cryptography technologies. In this regard, the process of transition to quantum technologies seems inevitable, and the attitude to scientific research in this area has become much more serious.
The article proposed by the authors is aimed at analyzing the foundations of quantum cryptography protocols, comparing their cryptographic strength, and the possibilities for their modification. Two well–known quantum protocols are taken as examples: the outdated, but still competitive BB84, and its modification BB84 Info-Z, which has its own distinctive features. Understanding the grounds and principles of quantum protocol functioning is becoming a necessity for many information security specialists. The priority directions of the development of quantum key distribution systems are demonstrated, and the construction of safe and secure data transmission protocols grounded on quantum mechanics laws is shown.
This article puts forward new assumptions about the possibility of universal improvement of quantum protocols on the example of modification of the quantum protocol BB84. The application of the idea put forward by the authors is based on the theory of man-made reconstruction of photons and their further use, which allows significantly reducing the danger of potential threats, and in some cases, to avoid situations related to vulnerabilities of quantum protocols. This method is combined; together with the application of false photon states and the creation of many traps, in order to increase the computing resources spent on cyberattacks by hackers, in the end, it nullifies this attack, making it useless. An attacker, or “eavesdropper”, will find a much smaller opportunity to guess the desired data transfer qubit, as well as the photon polarization state. The simulated copies, in addition to their main task, will become good bait for hackers, capable of driving him into the trap, thereby confirming his presence in the communication channel. In this case, the process of disconnecting the communication channel will not be mandatory.
2. Protocol BB84
This quantum protocol is named after the first letters of the surnames of its creators and the year of its publication [
1]. The BB84 protocol is designed to transmit secret information encoded in binary.
Figure 1 shows how, in the BB84 protocol, one bit can be encoded in the polarization state of photon. Binary 0 is defined as the polarization of 0° in the rectilinear coordinate basis, or 45° on a diagonal basis. Binary 1 can also be equal to 90° on a rectilinear coordinate basis, or 135° on a diagonal basis. Thereby, one bit can be represented by the polarization of a photon in one of two coordinate bases.
Currently, the participants in the transmission of the data process, Alice and Bob, agree to approve some big number n, the threshold of error pa and the linear correction code of error C, with the parity check matrix PC of the order r × n.
The linear key generation function (to enhance confidentiality), represented by PK matrix of order m × n, is also agreed upon. Both matrices can be known in advance or can be determined during the execution of the protocol, and then can be sent via the classical channel. In turn, the matrix (r + m) × n, the rows of which are the rows PC and PK, if taken together, must have the rank r + m. Alice randomly selects the sequences of bits: strings i from 2n – bit, b ∈ F22n, where F2 defines the field of 2 elements {0; 1}, that is, field of integer numbers modulo 2. Then, the state is encoded. For each bit, the coordinate basis is randomly selected, rectilinear or diagonal, with which the bit will be encoded. When transmitting the photon from Alice, Bob will inform her about the photon receiving, but will not measure it.
For each photon that Bob receives, he will measure the polarization of the photon on the randomly selected coordinate basis, applying it to his own state. If Bob chose the same coordinate basis of his state for particular photon as Alice did, when he performed the transformation , he switches to the state . Bob should measure the same polarization in the line iB, and thus output the bit that Alice sent correctly, in the case of absence of noise and signs of eavesdropping on the communication line from the side of an attacker.
To detect eavesdropping, Alice will randomly select n bits that will be used to detect the presence of attackers. By selecting a 2n–bit string containing n units exactly, Alice must ensure that equality |s| = n was fulfilled. Alice sends to Bob s bits publicly, such, that , which are applicated for testing, and the rest of the bits are employed for generating of the final key. Let us denote the corresponding substrings, appropriate for testing process values i and b, while the substrings appropriate for the generation of a key will be defined as is and bs. For every , such, that the value sj = 0, the participants of the data transfer process Alice and Bob publish the value of the bit with jth number.
If Bob chose the incorrect basis of coordinates, then his outcome and, consequently, the bit that he received will be random. It is worth noting that if the mismatch of the bits determined in the published values of the jth bit by comparison exceeds the npa, then they interrupt the protocol execution. The preliminarily fixed parameter pa of the protocol, in fact, is the relationship of permitted bit flips, intended for the testing process.
Alice and Bob save the values of the residue n bits in the strict confidence. The string of Alice is designated as and is called the information string. The appropriate string of bits on the side Bob is determined as xB.
At the second stage, Bob must inform Alice, via any unprotected channel of communication, what coordinate basis he has used to measure every photon. Then, Alice informs Bob if he chose the proper coordinate basis for each photon. At this stage, Alice and Bob throw out the bits appropriating the photons that Bob has measured with another coordinate basis. On the condition that no errors occurred, or no one managed the photons, Alice and Bob now should possess the same string of bits, which is named the sifted key.
The example demonstrated below (
Figure 2) illustrates the bits that Alice selected; the coordinate bases in which she encoded her bits; and the coordinate bases that Bob applicated for his dimension. In addition,
Figure 2 shows the resulting
sifted key, after the stage when Bob and Alice rejected their bits, as indicated above. However, Alice and Bob, before they finish, have to approve a subset of random bits for the comparison of the provision of the consistency of their actions. For verification, Alice sends Bob an
r–bit string of error correction. Bob will use ξ to compare or rectify his string
xB as necessary. String
is named the
syndrome of
string x (relative to
PC). If bits correspond, then they are rejected, and other bits create the common secret
m–bit key.
If there is no noise and there are no other dimension errors, a mismatch in any of the compared bits would specify the availability of an interceptor presenting in the quantum channel. The reason for this is that if attacker Eve was trying to define the key value, then she would not have any other choice but to measure the photons dispatched by Alice before transmitting these photons to Bob.
Therefore, Eve should attach the separate quantum probe (at quantum sensing [
2,
3,
4,
5,
6]), which, as she assumed, is in a pure state, and apply the unitary transformation
Uj to the composite system. This is true because the theorem on prohibition of cloning (anti–cloning theorem) [
7] guarantees that it is impracticable to reproduce a particle of an unknown state.
In view of the fact that Eve will not know which coordinate bases Alice have applicated to encode the bit while she discussed her measurements with Bob, she will be forced to guess. If she measures the states of photons in the wrong coordinate bases, then, as the uncertainty principle of Heisenberg guarantees, the information that was encoded in another coordinate basis will be lost.
Therefore, when a photon reaches Bob, his dimension will be random, and he will receive incorrect information in 50% of cases. Taking into account that the interceptor Eve will choose the basis of measurement incorrectly in 50% cases, on average, then 25% the bits measured by Bob will discern from the bits of Alice. If interceptor Eve captures all possible bits, then, after comparisons of n–bit by Alice and Bob, they would decrease the possibility that attacker Eve can remain unnoticed by a value of .
Therefore, the probability that the interceptor–attacker Eve has investigated the secret is insignificant if relatively long bit sequences are compared and identified.
3. Protocol BB84–Info–Z
Modification of BB84 and the considered quantum protocol BB84–Info–Z, is analogous to BB84 [
8], except that it applies the following differences:
- –
Generalized numbers of bits n, nz and nx (n–the numbers of informational bits, where Z and X are the test bits, accordingly);
- –
Section P = (s, z, b) to divide n–bit string i into three non–overlapping sets (I, TZ и TX);
- –
Two special thresholds, which are separate (pA,z and pA,x) in place of one threshold (pA).
Before starting the quantum protocol functioning, Alice and Bob must select some general parameters or public parameters:
- –
numbers denoted as n, nz and nX (specified as the relationship N = n + nz + nx);
- –
thresholds of errors denoted as PA,Z and PA,X, r × n (which correspond to the linear code of error correction C);
- –
matrices of privacy enhancement m × n (representing the linear key of generation function).
It is important that all rows R + M of the previously considered PC and PK matrices are assembled as linearly independent.
Alice randomly selects the section
of the
N–bit strings, randomly choosing
N–bit strings denoted as,
, which satisfy the conditions:
Thereby, the section splits the set of indexes denoted as {1, 2, …, N} into three non-overlapping and disjointed sets:
- –
I (information bits, where sj = 1) size n;
- –
TZ (test bits Z, where zj = 1) with size nz;
- –
TX (test bits X, where bj = 1) with size nx.
Alice selects N–bit strings randomly, where , and performs the dispatch of N qubits , one by one, through the quantum information channel. At the same time, Alice uses coordinate basis Z to send the information of test Z–bits, as well as X coordinate basis to send X–bits. Initially, Bob stores every qubit he has received in the quantum memory, without measuring this qubits.
Next, Alice dispatches the string of bits b = b1…bN via the classical channel to Bob. Bob gauges and measures every qubit that he has received and saved. When measuring ith qubit, Bob measures it in the Z–coordinate basis if bi = 0, and measures it in the X–coordinate basis if bi = 1. This string of bits that Bob measured is designated as iB. If noise and eavesdropping are absent, then the bit string is equal to iB = i.
After that, Alice sends Bob the string of bits, designated as s. The information bits (which will be applied for the final key generating) are n bits sj = 1, while test Z and X bits (which will be applied for testing) are nZ + nX with sj = 0. Substrings are denoted by i and b, and correspond to information bits iS and bS, accordingly.
Next, Alice and Bob publish together the values of bits, which they obtain for all test bits Z and X, and then the bit values are compared. If, for Alice and Bob, more than nZ · pa,Z test Z–bits are, or more than nX · pa,X test X–bits between them are different, then they interrupt this protocol, where pa,Z and pa,X are preliminarily coordinated thresholds of errors. Alice and Bob keep values of residual n bits (information bits where sj = 1) a strict secret. The bit chain of Alice is designated as x = is, and the bit string of Bob is denoted as xB.
Then, the syndrome x should be dispatched from Alice to Bob (regarding code C correction of errors and its check on parity of the PC matrix), which includes r bits and is determined as . Using the value ξ, Bob rectifies the errors in his string of bits xB (it is similarly x). The final key is m–bit sequence and is determined as . Alice and Bob, together, calculate it. It is obvious that the protocols are very similar.
Let us consider their security against collective attacks [
9,
10], which are one of the most powerful theoretical cyberattacks.
4. Description of Cyberattack of Eve and the Properties of It
To every
j qubit
shipped by Alice
, Eve attaches the separate quantum probe (at quantum sensing), which, as it assumed, is in pure state, and applies the unitary transformation
Uj to the composite system. Then, she stores her quantum probes in the quantum memory for the subsequent measurements, and dispatches to Bob his part of the system [
11].
Therefore, for every qubit there is a certain trial Hilbert space and a certain unitary transformation Uj; they are determined by Eve in advance and, thus, are corrected and fixed for all feasible variants and options of i, b and s.
4.1. Cyberattack of Eve on the Separate Qubit
Because the cyberattack is bitwise, it is possible to focus the analysis on some selected fixed qubit, temporarily discarding subindex
j and expressing the general impact of the actions of Eve on the concrete qubit relative to the coordinate basis
where
,
,
and
represent the vectors, or non–normalized states, in the trial Hilbert space of Eve, respective to this concrete qubit. Because the transformation
U is unitary, then
and
have norm 1 and are orthogonal. This means that
4.2. Spreading the Cyberattack to the Several Qubits–Collective Cyberattack
For every qubit ∈ [1 … 2
n] Eve uses the transformation
Uj in the space
, where
is Eve’s trial space,
– is the space of qubits. The coordinate basis bj, expressed relative to Eve’s point of view, is obtained by tracking Bob from the
and
, resulting in the following density matrices:
If Alice dispatches the string
i applying the coordinate basis
b, then the global state of Eve is the tensor product of these states
. After revealing the test bits [
12], Eve requires only those values
, or which
sj = 1. The set
has
n elements and is global. The global corresponding values
s, b,
x can now be saved as:
4.3. Probability of Errors
Supposing that the qubit is under cyberattack by transformation U, as determined in (1) and (2), then an error emerges if Alice dispatches 0 and Bob measures 1, or if Alice dispatches 1 and Bob measures 0. Let k be the value Bob has measured, i the value dispatched by Alice for the concrete qubit, and b the coordinate basis applied by Alice for encoding i.
Then, the possibility of Bob measuring the error is expressed as:
4.4. Probability of Errors Occurrence in the Conjugate Basis
Now we study the expression , where (when , ), which responds to the basis, conjugating to the basis that was given and specified as b.
Cyberattack U is described usually by formulas (1) and (2), in the coordinate basis b.
To compute the probability of error when Alice encodes
as
instead
, it is necessary to represent
U in the coordinate basis
. From the Equation (10), it is known that in this circumstance, the probability of errors is determined by the expression:
Using the fact that
and using linearity
U, expressions are derived from (1) and (2):
Replacing
and
in the right parts of expressions on their magnitudes from the positions
and
|, i.e.,
and
|, we receive
where components for
and
are enclosed in parentheses, we can easily see that:
Let us distribute this result applying Equalities
and
for
(where the complex conjugation is denoted above the line [
13]). Using the Equalities (3) and (4), we obtain the following expressions:
This expression will be applied to relate the perturbation caused by Eve while Alice is encoding bits in the coordinate basis , so , with the information which Eve obtains, while Alice will encode it in this coordinate basis.
According to the principle of «Information against perturbation» [
14], the more information Eve receives while the encoding is carried out in the coordinate basis b, the more interference it causes while the bits are encoding and checking in conjugate coordinate basis. Therefore, it is possible to limit Eve’s knowledge about the key by limiting the allowable rate (frequency) of errors in this quantum protocol.
5. Security Confirmation of Classical Protocol BB84 against the Collective Cyberattacks
Proof of Security
Let us choose such code , or some small value ; then the expression will be less than value , which by itself is exponentially small in n.
We can apply Heffding’s selection from [
8] (the theorem) for every specific row
c1 … c2n, appropriate to all qubit measurements in some valid coordinate basis
b. Let
be the average value of selection respective to incorrect bits of information;
–is the mathematical expectation , which is equal to the expression , or is identical to inequality .
To the rows
and
we will rewrite the conditions as:
whence it follows that using Heffding’s theorem [
15], the relation is obtained:
It is necessary to make sure that the rate of errors in the bits of information is less than the maximum speed at which the error correction code can process.
This condition is necessary for the key to be reliable.
6. Security Proof for the Protocol BB84–Info–Z against the Collective Cyberattacks
6.1. General Collective Cyberattack of Eve
Let us assume that, before executing the quantum key distribution (QKD) protocol, Eve chooses to carry out a collective cyberattack [
8]. Let the
jth qubit be given, sent by Alice to Bob. Eve attaches the quantum probe state (at quantum sensing) and applies some unitary operator
Uj to the composite system. Then, Eve holds in her quantum memory subsystem
Ej, which is the state of her quantum probe; next, she dispatches to Bob the subsystem
Tj. This subsystem is the qubit dispatched from Alice to Bob (it may be modified by Eve’s cyberattack
Uj).
The biggest common collective cyberattack
Uj of Eve is directed on the
jth qubit, presented by orthonormal coordinate basis. The cyberattack described as:
where
,
,
, and
are non–normalized states in Eve’s quantum probe of system
Ej, that was fastened and fixed to
jth qubit.
So, it can be noticed that the quantum probe state can change the initial state of the composite system product,, to an entangled state. This implies that Eve’s cyberattack can cause the entangling of her quantum probe with Bob’s probe (at quantum sensing).
Firstly, this can clarify the situation, and bring some kind of information about the state of Bob; secondly, it is the reason for the disturbance, and can be discovered by him. The information received the day before and the disturbance that Eve caused, by their nature, are interrelated with their relationship—this is the main reason why the QKD protocols are secure and safe.
6.2. Proof of Security
As was mentioned earlier [
8], the random variable
matches the errors in the string of bits in information bits if they were encoded in the coordinate basis
X. Bits of TEST–
X are also encoded in basis
X. The
CTX random variable matches the string of bits of the errors, on these bits. Hence, it is possible to consider the choice of
n–bits indexes of information (Info) and
nx–bits TEST–
X as a random selection (after
n,
nz and
nx numbers; and bit indexes TEST–Z, which was selected already) and to apply the theorem of Heffding [
9].
Hence, for every string of bits
c1 … cn + nx, which consists of errors in the bits
n + nx Info and TEST–
X, if Info bits were coded in the coordinate basis
X, then we can use Heffding’s theorem: let us take the sample with size
n without changing from combination
c1, …, cn + nx. In the above discussion [
8], the following theorem is actually proven:
Theorem. Let the values δ > 0 and R > 0; for infinite number of values n, the vectors family is given, which is linearly independent, such, that, . Hence, for anyonesuch, that, and for anyand two final keys k, k’ that are the mn–bit keys, the distance between the states of Eve, appropriate to k and k’, meets the following requirements and boundaries:
6.3. Reliability
By itself, the security is insufficient; it is also necessary that the key be reliable. More specifically, it must be identical for Alice and Bob [
16]. It assumes it a need to ensure that quantity of errors in the Info bits was less than the maximum error number, which can be rectified by the error correction code. To do this, it is necessary that the code for error correction can really correct the errors. Consequently, the final key reliability, having exponentially low failure probability, is provided by the inequality below:
The choice of the Info bits indexes, and the bits of TEST–Z, is random separation of n + nZ bits into two subsets, with sizes n and nZ (provided that the bits indexes of TEST–X was already selected). Thus, it matches Heffding’s sample.
7. Protocol CSLOE–2022 (BB84–CSLOE–2022)
It is recommended to become acquainted with the new modification proposed by the authors and named CSLOE–2022, for the old but still effective quantum protocol using the quantum distribution of the key–BB84. For the protocol BB84, it is possible to modify significantly the cryptographic strength and degree of entanglement of the listener, which in their perspective will complicate the possibility of intercepting information from such an interceptor (or cryptanalyst) targeting confidential messages.
It is known that after coordination of the coordinate bases in the classic protocol BB84, an interceptor can receive accurate information about the transmitted state.
The final purpose of modification is to complicate eavesdropping process to the point of uselessness, in terms of spending time and resources, as well as to confirm the guesses about the real possibility of using such a method. The idea consists in the following: it is known that the process of replicating the quantum state, recorded as ψ → ψ⊗ψ, (cloning) can be performed perfectly, with probability of 1, then and only then if the coordinate basis to which ψ refers is understood and known [
17]. Otherwise, the ideal cloning is not possible, since the copies are not perfect. These are contents and consequences of the theorem prohibiting quantum information cloning. This circumstance will be useful.
If it is impossible to reproduce an exact clone of a photon, in order to obtain information from it, it is necessary to measure the characteristics of the original. The only way to measure the characteristics of the photon is to use a detector of single photons. However, as soon the photon reaches the detector, it transmits energy and disappears. That is, the measurement destroys the photon itself [
9]. It is worth considering that each photon is unique [
18]. However, it is possible to create some kind of photon (kind of similarity). It is known, thanks to quantum teleportation, that it is possible to obtain an exact copy of a photon [
17], which, in turn, can be used also to construct such a similarity. For simplicity, we call it a «pseudo-photon». The interceptor will perceive such a pseudo-photon either as a real photon with its own specific set of characteristics, or as some distortion in the channel.
To detect and recognize such a clone in the communication channel, it is necessary to make considerable efforts. In the theory, at the first stage, as in the classic protocol BB84, Alice will communicate with Bob via the quantum communication channel. In turn, Alice will transmit to Bob the modified sequence consisting of cloned pseudo–photons and forming a dictionary (glossary) for each bit with corresponding polarization.
As mentioned earlier, the pseudo-photon will be a kind of photon created artificially [
4]. In each concrete case, it is possible to form new sequences that generate the dynamic dictionary, thereby reducing the repetition during encryption.
Knowing that each photon is unique [
18], one pseudo-photon cannot be used for each bit, but the whole group with a certain range of values that will be corrected, rectified, adjusted, shifted or expanded can [
19].
Each bit, or their sequence, even if they are repeated, will have random pseudo-photons from a certain range of values that are attributed to the concrete bit or bit sequence. When sending the dictionary for decoding, it is possible to send it in parts, to maintain secrecy, and to avoid declassification.
If listening is detected at this first step, the dictionary can be expanded and the intercepted part discarded, as was described earlier [
20], or data transmitting can be stopped and a new dictionary created. After successful transmission of the dictionary, it is possible to start sending encoded messages via the communication channel in which real photons, as well as their created copies, will alternate and have absolutely random positions in the sequence. It is worth noting that the protocol can be further complicated. For example, four quantum states can be used to encode bits in two coordinate bases, which corresponds to the quantum protocol BB84 (4 + 2) [
21]. Further, such a protocol works according to the classical scenario, but using the dictionary–glossary.
Every time Bob receives a qubit, he reports it to Alice, but does not measure it. Subsequently, for each photon and pseudo-photon which Bob obtains, he will measure the value of polarization on the randomly selected coordinate basis, applying it to his state. If Bob has chosen the same coordinate basis of state for the particular photon, then when he performs transformation Hb, as Alice does, then he goes into the same state. Then, Bob must measure the same polarization in the string iB. Hence, he can output properly the bit that Alice was going to dispatch in that case, if there is no noise orsigns of eavesdropping in the communication channel.
On the second step, Bob must tell Alice, using any unsecured communication channel, which coordinate basis he applied to quantify and to measure every photon. Then, Alice informs Bob which photons were real by sending the encrypted ranges, and informs him whether he has chosen the right coordinate basis for every original photon.
On this step, Alice and Bob reject the bits corresponding to pseudo-photons and the bits that Bob have quantified and measured in other coordinate bases. If there were no errors and nobody manipulated the photons, Bob and Alice must acquire the same bits string that is named as the sifted key (
Table 1). The example below (
Figure 3) demonstrates the bits which Alice selected [
22]; the coordinate bases in which she encoded it; and bases that Bob used to measure them. In addition, the sifted key, obtained in the result, is demonstrated after Bob and Alice rejected their bits.
The principle of imperfect replication is not new, and it is used often in telecommunications practice. In fact, information transmitted in optical fibers is encoded in the light state; thus, this process is quantum coding [
23]. The information is strengthened several times on the way from source to receiver; hence, its quality must deteriorate. However, the telecommunication signal includes a large amount of photons being prepared in an identical quantum state. Strengthening in telecommunications boils down to creating several new copies of
ψ from
ψ ⊗ N.
That is, the theorem of prohibition of cloning is applied to the amplification of the telecommunication signals, due to the fact that spontaneous radiation is usually available in the amplifiers. Nevertheless, the copy is practically ideal, as the stimulated radiation is the dominant effect. In addition, the sensitivity of modern equipment is quite high, and at this stage is such that quantum limitation must be achieved in the nearest future. Thus, information encoding following the theorem of the prohibition of cloning can also be useful for quantum key distribution protocols [
24].
The impossibility of exact and accurate copying of quantum information cannot negate the whole conception of the quantum information. On the contrary, it serves as a demonstration and illustration of power. It is impossible to copy the state of a certain quantum system for intelligent information coding completely using a set of states which are non–orthogonal.
Therefore, if a similar system reaches the receiver undisturbed, that proves that no opponent has copied it. This means that, due to the theorem of the prohibition of cloning, quantum information supports the tools to complete such tasks, which are impossible to solve applying only familiar information. For example, the detection of any eavesdropping device on the communication channel is possible only with the application of the ideas of quantum cryptography.
7.1. Cloning Methods
Let us consider the possible methods of non–ideal cloning of discrete quantum systems, which are performed in the protocol BB84.
There are several variants of such machines:
- (1)
Optimal symmetric universal quantum copying machine (UQCM) proposed by Vladimir Bužek (Buzhek, in various sources is spelled differently)–Mark Hillery (BH) in 1996;
- (2)
Symmetric universal quantum copying machine (UQCM) proposed by Nickolas Gisin–Serge Massar and their scientific group in 1997;
- (3)
Asymmetric universal quantum copying machine (copier)–UQCM.
The symmetric UQCM qubits cloning for 1 → 2, developed by Buzhek and Hillery (BH) accepts the cloning qubit as input, and uses the separate qubit as an auxiliary qubit [
25]. The action of such a universal quantum–copying machine in the computational base of initial original qubit is described by the expression:
where
. By its linearity, these ratios cause the next action on the most common and general input state:
:
where
.
As can be seen from the Equation (23), α and β can swap their places. In addition, for all input states, this transformation has the similar shape .
Therefore, the quantum copying machine (QCM) is universal and symmetric. For the original and the copy, its partial states are expressed as:
The symmetric universal quantum copying machine for NM qubits was developed by Nickolas Gisin and Serge Massar in 1997. It generalizes the Buzhek–Hillery UQCM, and its correctness is determined by the following expression:
which reproduces
for
and
.
Gisin and Massar provided numerical proofs of the optimality of their universal quantum copying machine. Later, Dagmar Bruss, Artur Eckert and Chiara Machiavelli gave analytical proof for this optimality in 1998. They suggested that the output state appertains to the
M qubits symmetric subspace. Further, Reinhard Werner generalized this outcome for the quantum systems of whatever dimension [
26].
The universal and asymmetric cloning relate to such a state of affairs where the resulting clones may have varying accuracy in reproduction.
We should concentrate on universal cloning 1 → 1 + 1. Several researchers studied cases that are more general in 2005. Let us look at some of these ideas with their experimental implementation. In the detailed research of cloning 1 → 1 + 1, Chi–Sheng Niu and Robert Griffiths, in 1998, obtained, in particular, the optimal asymmetric universal quantum copying machine 1 → 1 + 1. Nickolas Cerf in 1998 and 2000 independently obtained the same result. He used the algebraic method, along with Vladimir Bužek and Mark Hillery in 1998 [
27], who developed the method of quantum schemes, which was improved compared to the previous construction used for symmetric cloning.
Optimality is illustrated by confirming and proving the accuracy of reproduction of two clones,
FA and
FB, that confirms the inequality of non–cloning:
The authors managed to extend the development of their schemes far beyond the individual case of qubits. Based on the above, to improve the cryptographic strength of protocol BB84, the universal quantum copying machine (UQCM) of Bužek–Hillery is best suited, as it is the simplest quantum copier to implement all the concepts discussed above.
7.2. Comparison of Protocols
Since the protocols BB84, BB84–Info–Z and the CSLOE–2022 modification proposed by the authors have a lot in common, several parameters can be distinguished for their comparison. Let us start by comparing the threshold of errors.
This parameter is necessary to determine whether there was eavesdropping. In the practical implementation of the protocol of quantum keys distribution (QKD), the disadvantages of individual separate components will always show and manifest themselves, and some qubits will be unsuitable for the forming of a secret key.
In addition, listening to the quantum channel makes changes to the transmitted qubits, which also prevents them from being used when forming the secret key.
In the case of the classic protocol BB84, the threshold value of the error rate is 11% [
28]. For an ideal model, the number of bits received as the result, the final secret key (R) for the bit of the sifted key, is expressed by the relationship:
where the value
H is the binary entropy of Shannon and QBER is number of errors measured by Bob. The dependence of
R on QBER is demonstrated in the
Figure 4:
This may not always be the case. The quality of execution of the equipment implementing the protocol may allow reducing the threshold.
In the protocol BB84–Info–Z, in addition to the information qubits responsible for key generation, the test qubits X and Z are used [
7].
They are necessary for the eavesdropping check. The error threshold for this modification is slightly smaller, at 7.56% [
9] (
Figure 5).
For the modification proposed by the authors of CSLOE–2022, the threshold of errors is theoretically similar to the original one, since during key formation, imperfect copies of photons used to achieve the entanglement of a listener (eavesdropping interceptor) are discarded, and then the originals are checked, as in the classical protocol. On the other hand, when trying to listen, it is unlikely that the photons will be distorted, since their quantity is significantly lower than the number of copies.
From publication [
17] it is known that the code of Steane (CSS), otherwise known as Calderbank–Shor–Steane, is the tool of quantum error correction, introduced by Andrew Steane in 1996. Steane’s code uses the classical binary Hamming’s code to correct the errors of the qubit flip (
X–errors) and the double Hamming code to correct the errors of the phase flip (
Z–errors), in practice allowing:
qubits, where
δ–number of measured errors, and
n–length of qubits sequence.
If expression (28) would be written as:
, then the chart (graph) will intersect the axis
X at the point 0.11, which gave us the threshold of errors of 11% in the classical quantum protocol BB84 [
29].
For the protocol CSLOE–2022, the dependence of the number of bits of the final resulting secret key
R from the quantity of recorded and fixed errors QBER is preserved, as is shown in
Figure 6, since all photons, both the original and their copies in the form of pseudo-photons, will be distorted during transmission. Thus, the comparison of protocols by the threshold of errors can be observed in
Table 2:
The protocol BB84–Info–Z differs for the better from all the others, since a much smaller threshold of errors will allow the eavesdropping intruder to receive significantly less information about the secret key.
Another important parameter is the working distance. The protocols of quantum keys distribution (QKD) operate with single photons, which can be distorted during transmission. Therefore, the working distance is relatively small. For example, for protocol BB84, it is about 70 km [
30]. When implementing the protocols DPS and COW, it became possible to reach distances of 250 and 307 km, respectively, but their safety has not yet been proven.
Based on the findings of the research, it was suggested that in the case of using pseudo-photons, it is impossible to declare the numbers of photon losses correctly. If the losses occur from the number of pseudo-photons, and they are used as the trap and entanglement, they may have completely different behavior and completely different interactions, which can lead to both a decrease in losses, or an increase. To declare this confidently without conducting a series of experiments is incorrect and unpredictable. In the case of the protocols BB84 and BB84–Info-Z, the loss of photons is particularly significant. However, the feature of the CSLOE–2022 protocol is its modularity and application of pseudo-photons, which fundamentally distinguishes it from its predecessors.
Therefore, it is possible to make another hypothesis to rely on it, and refer to the fact that the method is based on the cloning of pseudo-photons. At large distances, the transmission of information with photons is carried out with large losses of (η ≃ 0), and this limitation can be exceeded only by using quantum repeaters. In turn, they will have to be used without limitation for the transmission of recreated pseudo-photons. In addition, it is necessary to be able to combine them with ordinary photons which can be transmitted without repeaters at all.
It is known that quantum communications guarantee the reliable transmission of quantum information and efficient distribution of entanglement, together with the generation of completely secure keys. However, it should be borne in mind that, at long distances, photon transmissions incur significant losses. Quantum repeaters can surpass this limitation. The article [
31] discusses the theoretical aspects of the possible limit for ensuring the transmission of information without repeaters.
Relying on this article is possible if the objective is to increase the distance between repeaters. However, the studies themselves given in [
31] are difficult to use for the clear practical application without conducting of series of experiments, and especially in combination of multi-qubit states, which is what some scientists are trying to practice now.
However, in the case considered by the authors, pseudo-photons are used (that is, recreated from real photons with clear differences), which, in turn, may display completely different, unpredictable behavior. This can lead to both a decrease in the losses or an increase in them. In the case of real photons, for the channel with losses, the article [
31] proves that
, where
η is the coefficient of transmission. In particular, the transmission capacity of the secret key of the channel with losses is the maximum speed achievable with any optical implementation of the quantum key distribution (QKD). At large distances, that is, with large losses,
η ≃ 0, finding the optimal scaling of losses and the speed of
K ≃ 1.44 η secret bits per channel use, the fundamental limitation is obtained, which, at this point in time, can be overcome, practically, only with repeaters.
A team of Chinese physicists succeeded in transmitting a secret quantum key at a distance of 511 km in real-world conditions [
20]. They were thus able to implement the quantum line of data transmission outside laboratory conditions.
Physicists continue to search for different ways to increase the distance to hundreds and thousands of kilometers, developing repeaters for existing protocols, as well as new ones. For example, the protocol of the twin fields TF (Twin Field). Unlike the standard protocol, for example, BB84, in which Alice directly sends photons to Bob, the protocol TF [
32] includes an additional Charlie node, which is located between Alice and Bob. In that case, Alice and Bob carry out the transfer and transmit their information on the weak coherent pulse to Charlie, who compares them and announces whether the received bits coincide or not.
However, Charlie has no information about the bits he has received; he can only compare them and declare whether they have coincided at the moment or not, so Charlie is considered to be an untrusted node.
This approach allows exceeding the known limit of the key generation rate without repeaters. It uses two photon sources, the phases of which, in addition to hundreds of kilometers of optical fiber between them, are not easy to stabilize.
Thus, we can summarize the comparison of protocols BB84, BB84–Info–Z and CSLOE–2022 by working distance and record the results in
Table 3:
8. Conclusions
The article shows that the quantum protocol BB84–Info–Z is protected completely from collective attacks—one of the most powerful cyberattacks.
It is found that the results of the quantum protocol BB84 have much in common with the BB84–Info–Z quantum protocol, with two significant exceptions:
The rate of errors should be checked separately so that it remains below the threshold values
and
for bits TEST–Z and TEST–X; accordingly, when in the quantum protocol BB84, the threshold value of error rate
pa is applied to all bits of TEST jointly [
7].
The indexes and information indicators of the interceptor Eve (in security terms) and probability of the error-correcting code failure (in reliability terms) differ from the indexes and indicators in the case of classical quantum protocol BB84 [
8].
It can be concluded that if the quantum protocol BB84 is modified so that the bits Info would be only at the coordinate basis
Z, this will not weaken its reliability and security (against the collective cyberattacks, at least). It will not even change the threshold of the asymptotic rate of errors [
8].
Protocol BB84–Info-Z can be applied safely to distribute the secret key; its security has ideal implementation, and it is protected against collective cyberattacks.
It is shown that modification of classical quantum protocol BB84 (CSLOE–2022) proposed by the authors could be used for quantum key distribution, since the applied principle of imperfect copying does not violate the laws of physics, but allows increasing the cryptographic strength of the protocol. So far, this modification is just an idea, and it needs to be proven by a series of practical experiments using specific equipment.
However, it is known that the principle of imperfect copying has already been applied experimentally in communication channels, as is mentioned in [
33,
34,
35,
36,
37,
38,
39,
40,
41,
42,
43,
44,
45,
46,
47], which makes it possible to transmit information over much longer distances.
Nevertheless, for quantum key distribution, there are other requirements for the quality of performance of individual components.
Therefore, these new ideas are being put forward, and engineers are given specific tasks in order to prove the correctness of the new hypotheses.
Further, the authors plan to research the optical quantum memory of photons and pseudo-photons for the possibility of recording information into them. Based on the data obtained, it is necessary to identify theoretical limitations as well as to find the ways to level and neutralize them, both for photons and for pseudo-photons recreated on their basis.