Fog-Computing-Based Cyber–Physical System for Secure Food Traceability through the Twofish Algorithm
Abstract
:1. Introduction
- The integration of novel fog modules with the CPS-based food traceability system for the identification of poor-quality products from the supply chain by maintaining reliable product information to increase the trust level;
- The utilization of novel sensing features along with monitoring and interface layer to gather product information from different layers to maintain the product’s actual information;
- To maintain the integrity, the details captured by the sensors along with the distribution of the information collected from the monitoring layers and stored in the fog;
- The utilization of a hybrid authentication mechanism with the integrated modification ability wherein the system can select users’ authentication criteria.
2. Related Work
3. Proposed Traceability System
3.1. Requirements, Identification, and Tracking
- Requirements: The food product traceability solution is based on three basic requirements, i.e., place identification, food product identification, and tracking movement;
- Food place identification: During the production process in the food supply chain, it is important to trace every involved phase uniquely. As we know that food products start from raw materials and then move step-by-step to completion, this should be traceable by anyone. In the supply chain, a food product changes its location time-to-time till completion; therefore, the location needs to be identified;
- Food product identification: It is also important to track and trace a food product throughout the supply chain. From the raw materials, i.e., from the initial phase till finishing, it must be distinctively identified;
- Movement tacking: The movement of food is very important to track and trace. It is the actual key element in the supply chain to be monitored during its production [40].
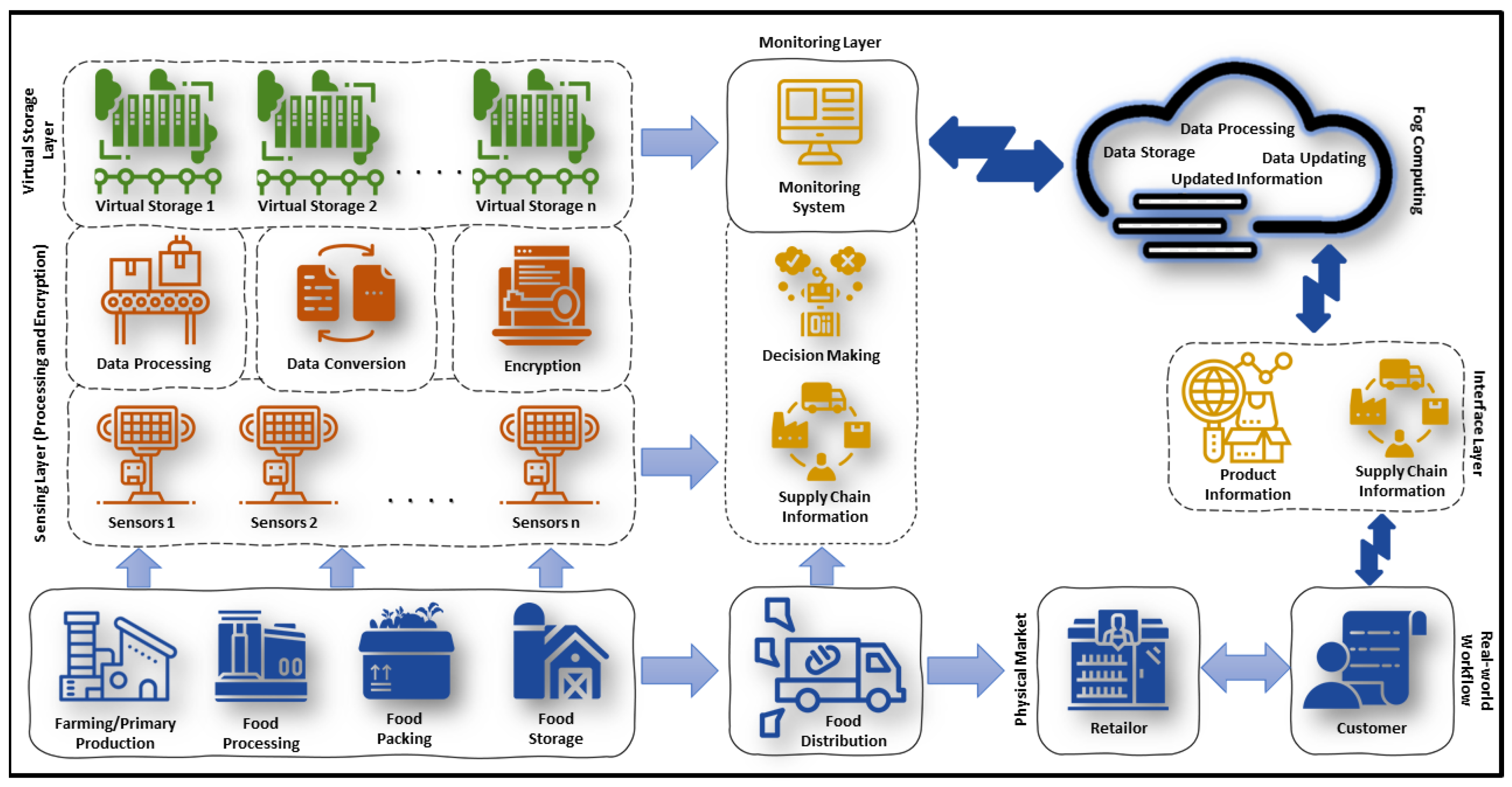
3.2. CPS-Based Secure Food Traceability Architecture
- Real-world layer: This is the ground or physical-world layer where the actual processes are performed physically. These processes consist of farming production where farmers produce the products, followed by the food processing layer, food packaging, and food storage. After this, the food is distributed to the retailer where customers can buy and are also able to obtain the product information from the intermediate layer;
- Sensing layer: The sensing layer is the primary layer equipped with the CPS sensors placed at different geographical locations of the supply chain. The CPS sensors consist of three main components, i.e., communication, computation, and control. The major functions performed at this layer are data processing, data conversion into operations, and encryption. The encryption and decryption are performed through the Twofish algorithm using a 256 bit key. In every phase of the supply chain, sensors are placed at different locations, which can sense the actual product information in an explicit form. This layer is further connected to the virtual storage layer;
- Virtual storage layer: The encrypted data transmitted by the sensing layer are sent to the virtual storage devices, and a copy of the information is forwarded to the parallel layer for monitoring purposes. Furthermore, the sensing layer is connected to virtual storage and communication devices to exchange content between the below and above layers. A virtual storage layer can also be utilized for collecting food product data. The key responsibility of the virtual layer provides services to the top layer for decision-making in addition to providing the facility to monitor the supply chain during the production process;
- Monitoring layer: The monitoring layer is the most significant one for food traceability because it is connected to the sensing layer and virtual storage layer and also gathers the information directly from food distribution vehicles. The monitoring layer has two significant components, i.e., decision-making and supply chain information. The incoming information from the sensing, virtual storage, and food distribution layers is integrated using supply chain components and forwarded to the decision-making components to evaluate the accuracy of the product information. The collection of information from different layers for evaluation purposes makes the proposed mechanism robust against modification attacks;
- Interface layer: This layer provides an interface to consumers, which contains food supply chain information regarding the product quality, name, manufacturing date, expiry, and weight. If customers find all information on the Internet and the same product is delivered to them, then it increases the trust and reliability among them. If there is any ambiguity in the object information, then it will cause a negative impression for the consumers and markets, which may ultimately reduce the trust.
3.3. Twofish-Algorithm-Based Data Encryption
| Algorithm 1 Hybrid user authentication process. |
|
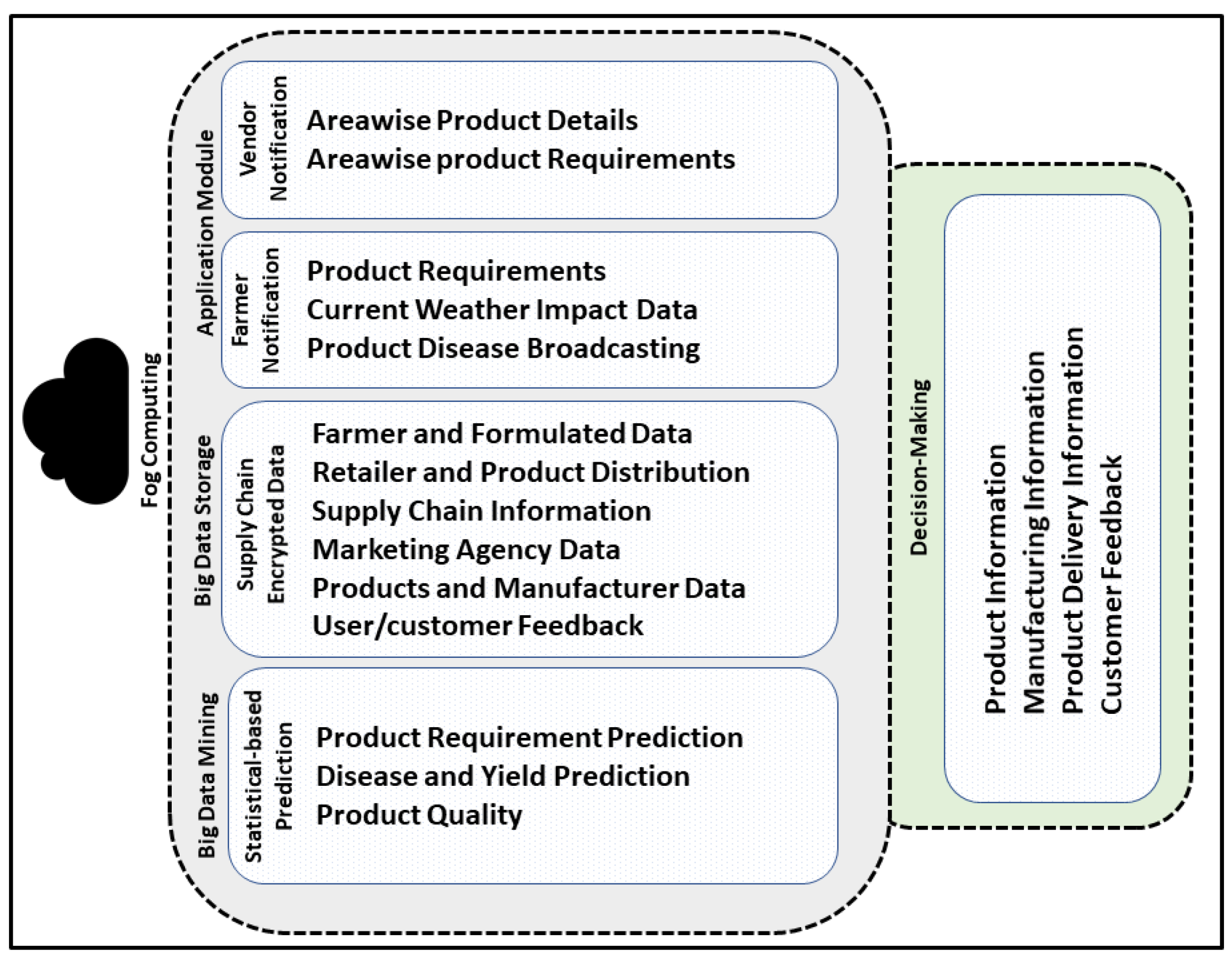
3.4. Utilization of Fog Computing in the Proposed CPS
4. Simulation Environment
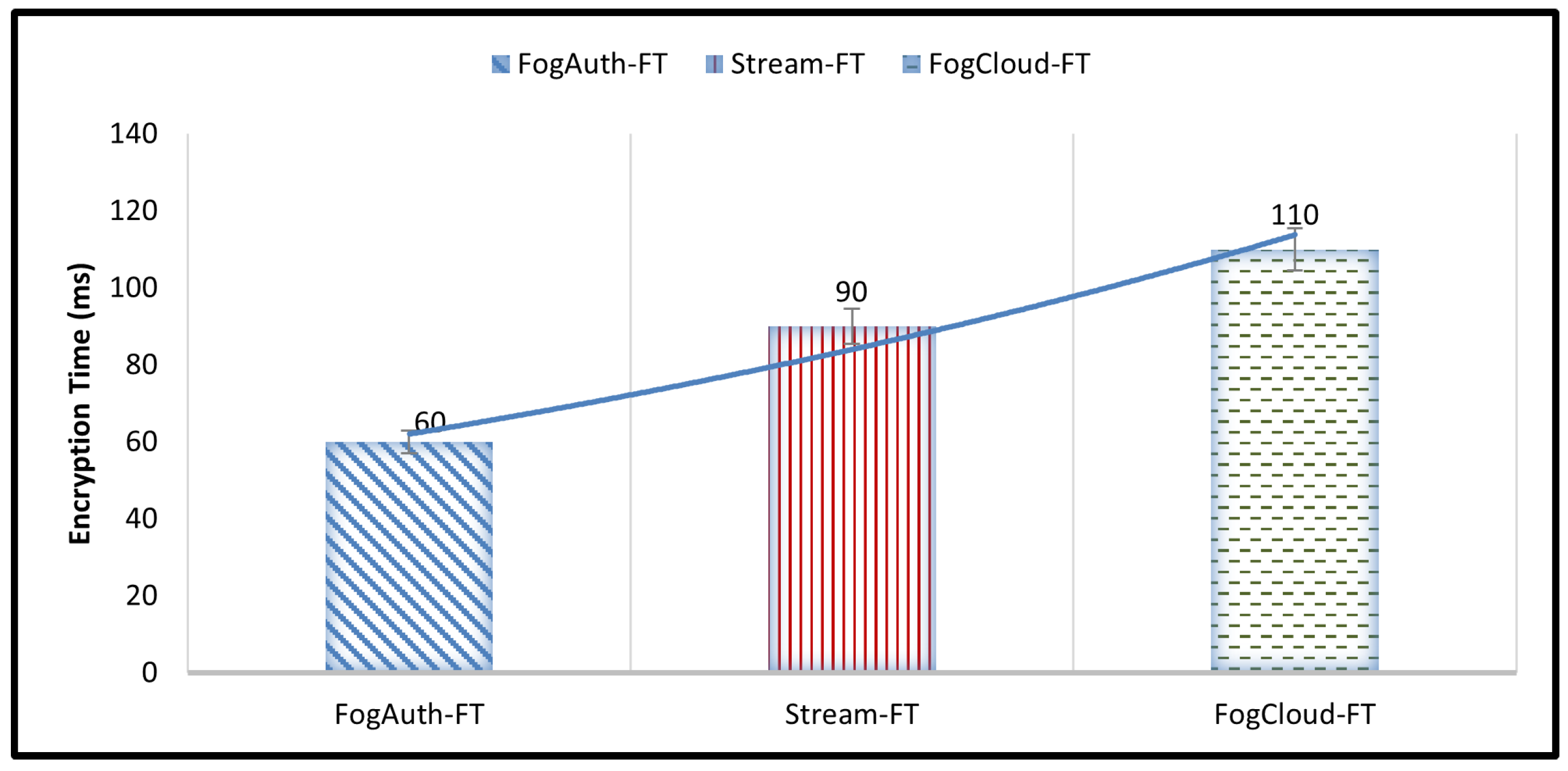
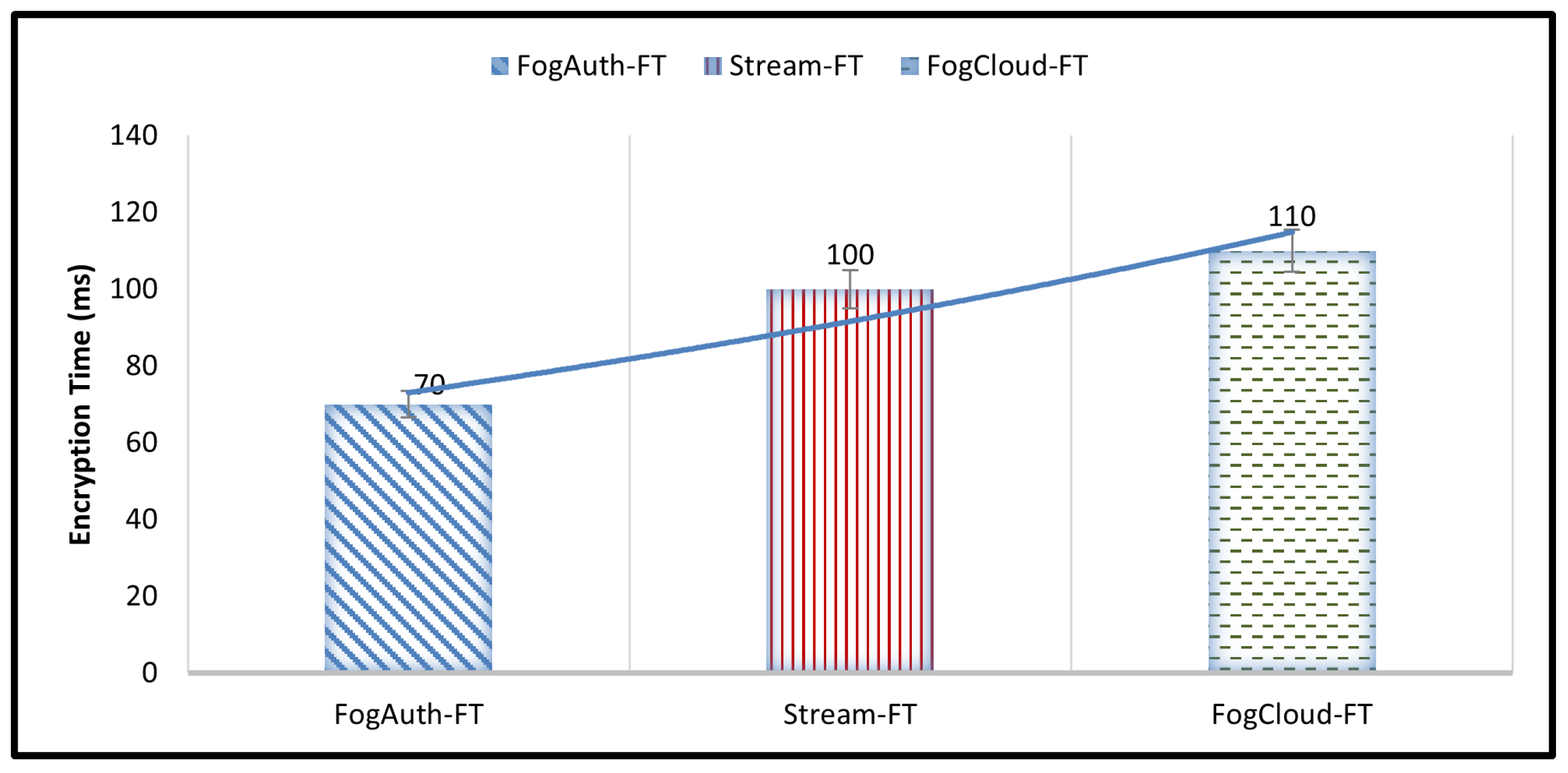
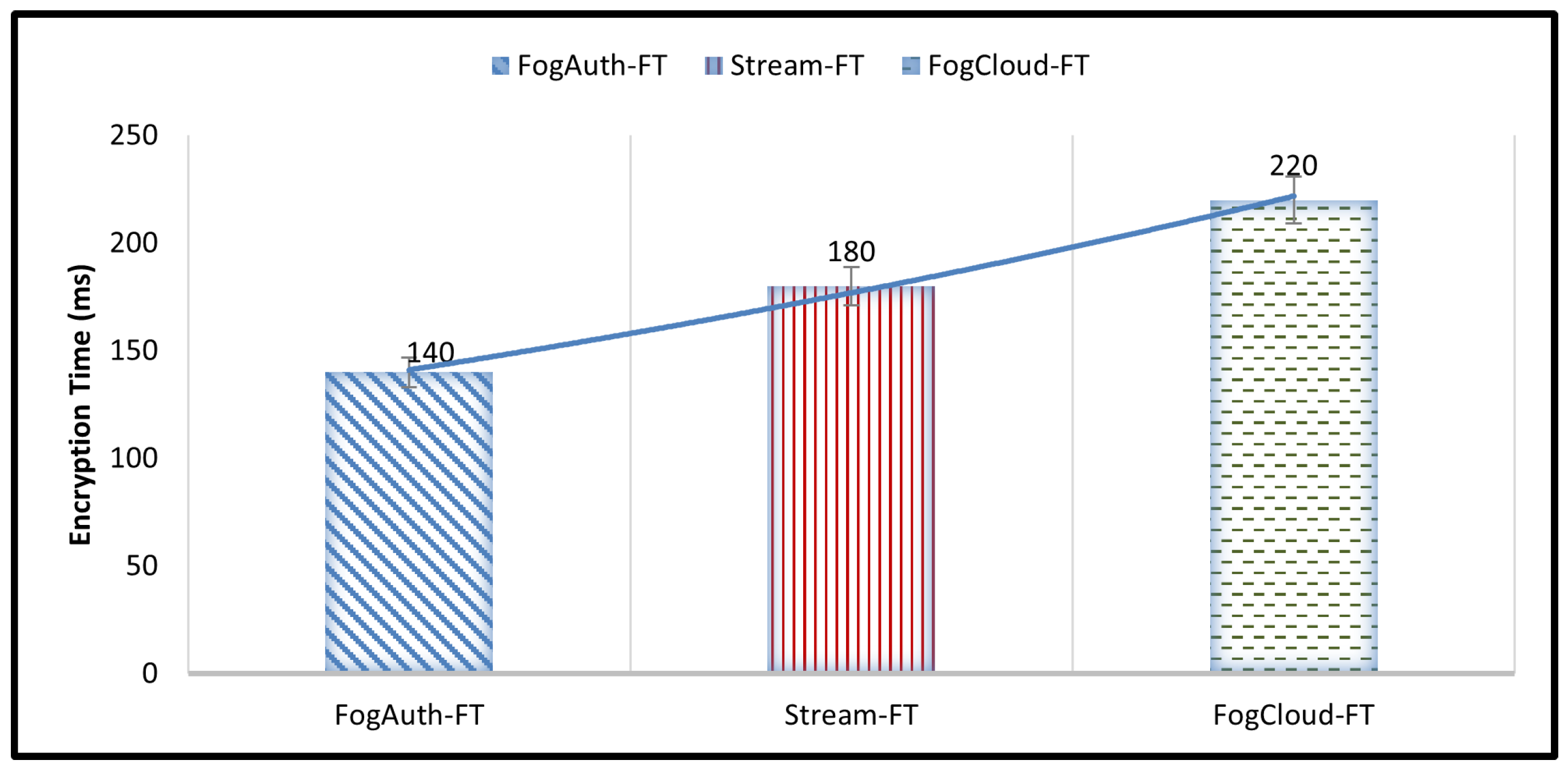
4.1. Encryption Time
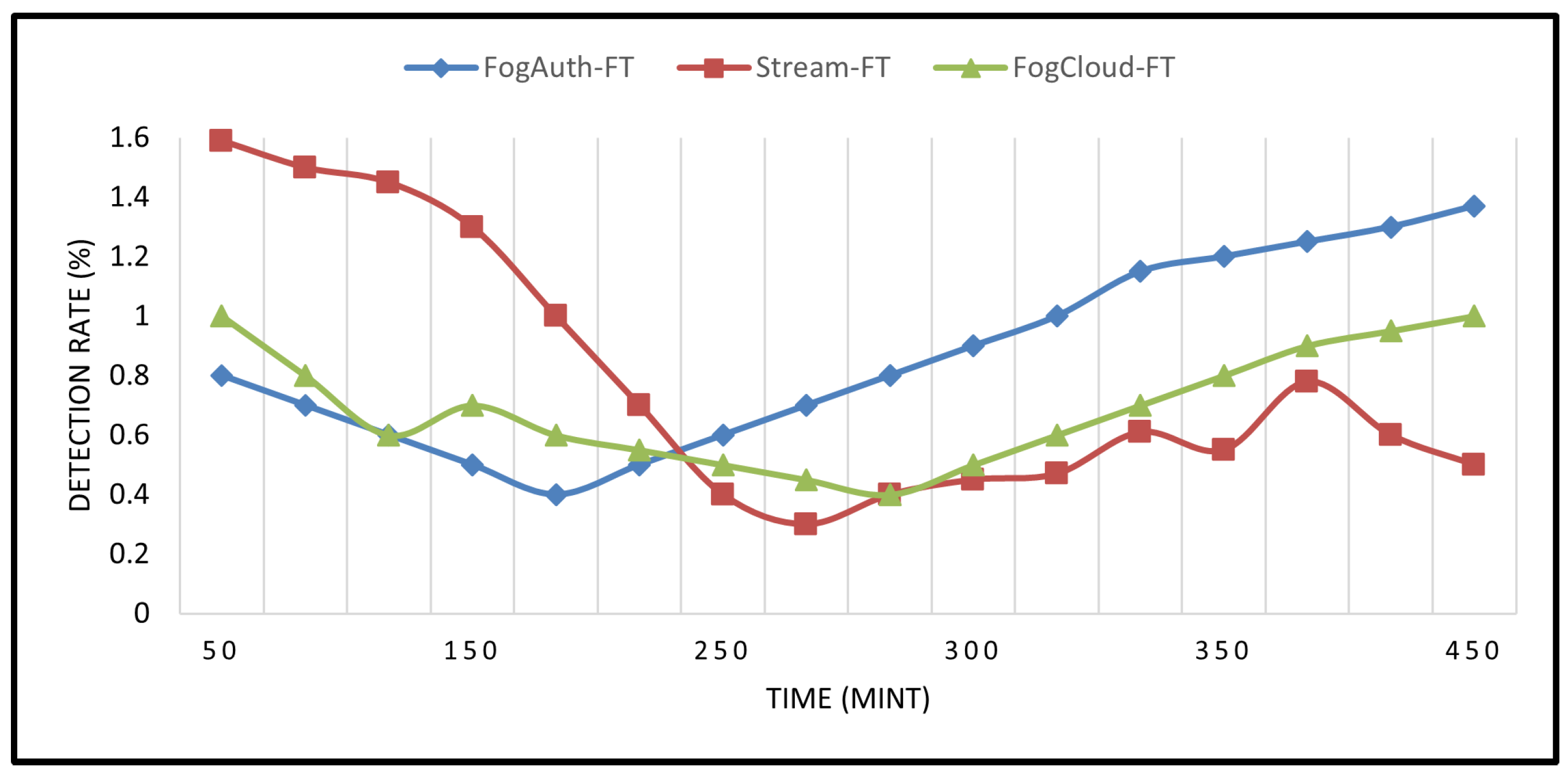
4.2. Trusted Data Identification and Error Estimation
4.3. Computational Cost
4.4. Modification Attack
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Khattak, H.A.; Tehreem, K.; Almogren, A.; Ameer, Z.; Din, I.U.; Adnan, M. Dynamic pricing in industrial internet of things: Blockchain application for energy management in smart cities. J. Inf. Secur. Appl. 2020, 55, 102615. [Google Scholar] [CrossRef]
- Smetana, S.; Aganovic, K.; Heinz, V. Food Supply Chains as Cyber-Physical Systems: A Path for More Sustainable Personalized Nutrition. Food Eng. Rev. 2021, 13, 92–103. [Google Scholar] [CrossRef]
- Kim, T.; Yoo, S.E.; Kim, Y. Edge/Fog Computing Technologies for IoT Infrastructure. Sensors 2021, 21, 3001. [Google Scholar] [CrossRef]
- Binti Azram, N.A.; binti Atan, R. SPL-based traceability model for food document tracing. In Proceedings of the IEEE 2015 9th Malaysian Software Engineering Conference (MySEC), Kuala Lumpur, Malaysia, 16–17 December 2015; pp. 212–216. [Google Scholar]
- Asuncion, H.U.; François, F.; Taylor, R.N. An end-to-end industrial software traceability tool. In Proceedings of the 6th Joint Meeting of the European Software Engineering Conference and the ACM SIGSOFT Symposium on The Foundations of Software Engineering, Dubrovnik, Croatia, 17 September 2007; pp. 115–124. [Google Scholar]
- Young, G. Synthetic Structure of Industrial Plastics, in Plastics; Peters, J., Ed.; McGraw-Hill: New York, NY, USA, 1964; Volume 3. [Google Scholar]
- Shahid, A.; Almogren, A.; Javaid, N.; Al-Zahrani, F.A.; Zuair, M.; Alam, M. Blockchain-based agri-food supply chain: A complete solution. IEEE Access 2020, 8, 69230–69243. [Google Scholar] [CrossRef]
- Antonides, G.; Hovestadt, L. Product attributes, evaluability, and consumer satisfaction. Sustainability 2021, 13, 12393. [Google Scholar] [CrossRef]
- Hidayat, A.; Wijaya, T.; Ishak, A.; Endi Catyanadika, P. Consumer Trust as the Antecedent of Online Consumer Purchase Decision. Information 2021, 12, 145. [Google Scholar] [CrossRef]
- Janjua, K.; Shah, M.A.; Almogren, A.; Khattak, H.A.; Maple, C.; Din, I.U. Proactive forensics in IoT: Privacy-aware log-preservation architecture in fog-enabled-cloud using holochain and containerization technologies. Electronics 2020, 9, 1172. [Google Scholar] [CrossRef]
- Vidmar, D.; Marolt, M.; Pucihar, A. Information Technology for Business Sustainability: A Literature Review with Automated Content Analysis. Sustainability 2021, 13, 1192. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Shu, Y.; Cui, X.; Shi, K.; Wei, C.; Shia, Z. Efficient Fault-tolerant Information Barrier Coverage in Internet of Things. IEEE Trans. Wirel. Commun. 2021, 20, 7963–7976. [Google Scholar] [CrossRef]
- León-Bravo, V.; Caniato, F.; Caridi, M. Sustainability assessment in the food supply chain: Study of a certified product in Italy. Prod. Plan. Control 2021, 32, 567–584. [Google Scholar] [CrossRef] [Green Version]
- Badia-Melis, R.; Mishra, P.; Ruiz-García, L. Food traceability: New trends and recent advances. A review. Food Control 2015, 57, 393–401. [Google Scholar] [CrossRef]
- Poltavtseva, M.; Shelupanov, A.; Bragin, D.; Zegzhda, D.; Alexandrova, E. Key Concepts of Systemological Approach to CPS Adaptive Information Security Monitoring. Symmetry 2021, 13, 2425. [Google Scholar] [CrossRef]
- Morella, P.; Lambán, M.P.; Royo, J.A.; Sánchez, J.C. The Importance of Implementing Cyber Physical Systems to Acquire Real-Time Data and Indicators. J 2021, 4, 147–153. [Google Scholar] [CrossRef]
- Hammoudeh, M.; Watters, P.; Epiphaniou, G.; Kayes, A.; Pinto, P. Special Issue “Security Threats and Countermeasures in Cyber-Physical Systems”. J. Sens. Actuator Netw. 2021, 10, 54. [Google Scholar] [CrossRef]
- Thompson, D.R.; Rainwater, C.E.; Di, J.; Ricke, S.C. Student cross-training opportunities for combining food, transportation, and critical infrastructure cybersecurity into an academic food systems education program. In Food and Feed Safety Systems and Analysis; Elsevier: Amsterdam, The Netherlands, 2018; pp. 375–391. [Google Scholar]
- Rani, S.; Kataria, A.; Chauhan, M. Fog computing in industry 4.0: Applications and challenges—A research roadmap. In Energy Conservation Solutions for Fog-Edge Computing Paradigms; Springer: Berlin/Heidelberg, Germany, 2022; pp. 173–190. [Google Scholar]
- Keerthi, C.K.; Jabbar, M.; Seetharamulu, B. Cyber Physical Systems (CPS): Security Issues, Challenges and Solutions. In Proceedings of the 2017 IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), Coimbatore, India, 14–16 December 2017; pp. 1–4. [Google Scholar]
- Ali, W.; Din, I.U.; Almogren, A.; Guizani, M.; Zuair, M. A lightweight privacy-aware iot-based metering scheme for smart industrial ecosystems. IEEE Trans. Ind. Inform. 2020, 17, 6134–6143. [Google Scholar] [CrossRef]
- Tao, H.; Bhuiyan, M.Z.A.; Rahman, M.A.; Wang, T.; Wu, J.; Salih, S.Q.; Li, Y.; Hayajneh, T. TrustData: Trustworthy and secured data collection for event detection in industrial cyber-physical system. IEEE Trans. Ind. Inform. 2019, 16, 3311–3321. [Google Scholar] [CrossRef]
- Lv, C.; Hu, X.; Sangiovanni-Vincentelli, A.; Li, Y.; Martinez, C.M.; Cao, D. Driving-style-based codesign optimization of an automated electric vehicle: A cyber-physical system approach. IEEE Trans. Ind. Electron. 2018, 66, 2965–2975. [Google Scholar] [CrossRef] [Green Version]
- Deka, L.; Khan, S.M.; Chowdhury, M.; Ayres, N. Transportation cyber-physical system and its importance for future mobility. In Transportation Cyber-Physical Systems; Elsevier: Amsterdam, The Netherlands, 2018; pp. 1–20. [Google Scholar]
- Xu, J.; Wei, L.; Wu, W.; Wang, A.; Zhang, Y.; Zhou, F. Privacy-preserving data integrity verification by using lightweight streaming authenticated data structures for healthcare cyber–physical system. Future Gener. Comput. Syst. 2020, 108, 1287–1296. [Google Scholar] [CrossRef]
- Chen, R.Y. An intelligent value stream-based approach to collaboration of food traceability cyber–physical system by fog computing. Food Control 2017, 71, 124–136. [Google Scholar] [CrossRef]
- Feng, H.; Wang, X.; Duan, Y.; Zhang, J.; Zhang, X. Applying blockchain technology to improve agri-food traceability: A review of development methods, benefits and challenges. J. Clean. Prod. 2020, 260, 121031. [Google Scholar] [CrossRef]
- Adnan, M.; Lu, Y.; Jones, A.; Cheng, F.T. Application of the Fog Computing Paradigm to Additive Manufacturing Process Monitoring and Control. SSRN 3785854. 2021. Available online: https://ssrn.com/abstract=3785854 (accessed on 17 December 2021).
- Mao, B.; He, J.; Cao, J.; Bigger, S.W.; Vasiljevic, T. A framework for food traceability information extraction based on a video surveillance system. Procedia Comput. Sci. 2015, 55, 1285–1292. [Google Scholar] [CrossRef]
- Mao, B.; He, J.; Cao, J.; Gao, W.; Pan, D. Food traceability system based on 3d city models and deep learning. Ann. Data Sci. 2016, 3, 89–100. [Google Scholar] [CrossRef]
- Chen, R.Y. Fog computing-based intelligent inference performance evaluation system integrated internet of thing in food cold chain. In Proceedings of the IEEE 2015 12th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD), Zhangjiajie, China, 15–17 August 2015; pp. 879–886. [Google Scholar]
- Musa, Z.; Vidyasankar, K. A fog computing framework for blackberry supply chain management. Procedia Comput. Sci. 2017, 113, 178–185. [Google Scholar] [CrossRef]
- Mededjel, M.; Belalem, G.; Neki, A. Towards a traceability system based on cloud and fog computing. Multiagent Grid Syst. 2017, 13, 47–68. [Google Scholar] [CrossRef]
- Mededjel, M.; Belalem, G.; Neki, A. A cloud-fog architecture for physical-internet-enabled supply chain. Supply Chain. Forum Int. J. 2021, 32, 1–16. [Google Scholar] [CrossRef]
- Chen, R.Y. Intelligent predictive food traceability cyber–physical system in agriculture food supply chain. In Journal of Physics: Conference Series; IOP Publishing: Avid College, Maldives, 2018; Volume 1026, p. 012017. [Google Scholar]
- Bordel Sánchez, B.; Alcarria, R.; Martín, D.; Robles, T. TF4SM: A framework for developing traceability solutions in small manufacturing companies. Sensors 2015, 15, 29478–29510. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Huang, J.; Zhu, Y.; Cheng, B.; Lin, C.; Chen, J. A PetriNet-based approach for supporting traceability in cyber-physical manufacturing systems. Sensors 2016, 16, 382. [Google Scholar] [CrossRef] [Green Version]
- Sareen, S.; Gupta, S.K.; Sood, S.K. An intelligent and secure system for predicting and preventing Zika virus outbreak using Fog computing. Enterp. Inf. Syst. 2017, 11, 1436–1456. [Google Scholar] [CrossRef]
- Lin, Q.; Wang, H.; Pei, X.; Wang, J. Food safety traceability system based on blockchain and EPCIS. IEEE Access 2019, 7, 20698–20707. [Google Scholar] [CrossRef]
- Bhatt, T.; Buckley, G.; McEntire, J.C.; Lothian, P.; Sterling, B.; Hickey, C. Making traceability work across the entire food supply chain. J. Food Sci. 2013, 78, B21–B27. [Google Scholar] [CrossRef]
- Schneier, B.; Kelsey, J.; Whiting, D.; Wagner, D.; Hall, C.; Ferguson, N. Twofish: A 128-bit block cipher. AES Submiss. 1998, 15, 23–91. [Google Scholar]
- Herrera-Macías, J.A.; Legón-Pérez, C.M.; Suárez-Plasencia, L.; Piñeiro-Díaz, L.R.; Rojas, O.; Sosa-Gómez, G. Test for Detection of Weak Graphic Passwords in Passpoint Based on the Mean Distance between Points. Symmetry 2021, 13, 777. [Google Scholar] [CrossRef]
- Khan, M.A.; Din, I.U.; Jadoon, S.U.; Khan, M.K.; Guizani, M.; Awan, K.A. G-RAT|a novel graphical randomized authentication technique for consumer smart devices. IEEE Trans. Consum. Electron. 2019, 65, 215–223. [Google Scholar] [CrossRef]
- Awan, K.A.; Ud Din, I.; Almogren, A.; Kumar, N.; Almogren, A. A Taxonomy of Multimedia-based Graphical User Authentication for Green Internet of Things. ACM Trans. Internet Technol. (TOIT) 2021, 22, 1–28. [Google Scholar] [CrossRef]
- Gupta, H.; Vahid Dastjerdi, A.; Ghosh, S.K.; Buyya, R. iFogSim: A toolkit for modeling and simulation of resource management techniques in the Internet of Things, Edge and Fog computing environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef] [Green Version]






| Approach | Contribution | Limitation |
|---|---|---|
| [29] | Use of video surveillance cameras along with a novel dynamic background model for object monitoring. | Compression and decompression of stream data may take excessive time. |
| [30] | Creation of a 3D city model and utilization of deep learning for object identification. | Requires abundant resources. |
| [26] | Stream monitoring with fuzzy rules and stream mapping. | Integrity challenges due to the traceability database. |
| [31] | Utilization of fog computing to reduce latency and communication cost. | T-S fuzzy and ANN-based fog increases the computational complexity. |
| [32] | Division of layers into monitored, control, and cloud servers. | Depending on the cellular network and GPRS, may cause transmission delay. |
| [33] | IoT later to capture information with the fog and cloud. | Increased latency and transmission cost. |
| [34] | Utilization of real-time processing for prompt decision-making. | The A* algorithm is a blind search algorithm that may increase time and waste resources. |
| Block Size | 192 bit | Average Percentage | ||
| Key Size | 128 bit | 192 bit | 256 bit | |
| FogAuth-FT | 60 | 90 | 110 | 86.67 |
| Stream-FT | 90 | 120 | 150 | 120 |
| FogCloud-FT | 110 | 145 | 120 | 125 |
| Block Size | 256 bit | Average Percentage | ||
| Key Size | 128 bit | 192 bit | 256 bit | |
| FogAuth-FT | 70 | 105 | 140 | 105 |
| Stream-FT | 100 | 130 | 180 | 136.67 |
| FogCloud-FT | 110 | 165 | 220 | 165 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Awan, K.A.; Din, I.U.; Almogren, A.; Kim, B.-S. Fog-Computing-Based Cyber–Physical System for Secure Food Traceability through the Twofish Algorithm. Electronics 2022, 11, 283. https://doi.org/10.3390/electronics11020283
Awan KA, Din IU, Almogren A, Kim B-S. Fog-Computing-Based Cyber–Physical System for Secure Food Traceability through the Twofish Algorithm. Electronics. 2022; 11(2):283. https://doi.org/10.3390/electronics11020283
Chicago/Turabian StyleAwan, Kamran Ahmad, Ikram Ud Din, Ahmad Almogren, and Byung-Seo Kim. 2022. "Fog-Computing-Based Cyber–Physical System for Secure Food Traceability through the Twofish Algorithm" Electronics 11, no. 2: 283. https://doi.org/10.3390/electronics11020283
APA StyleAwan, K. A., Din, I. U., Almogren, A., & Kim, B.-S. (2022). Fog-Computing-Based Cyber–Physical System for Secure Food Traceability through the Twofish Algorithm. Electronics, 11(2), 283. https://doi.org/10.3390/electronics11020283








