Abstract
Securing communication in vehicular ad hoc networks (VANETs) is hampered by numerous constraints, making it more difficult. First, traditional security schemes cannot be directly applied in VANET because they consider fixed topology. Second, VANET enables dynamic spectrum access where nodes constantly change frequencies due to their high degree of mobility, resulting in severe consequences on network performance. Third, an effective security scheme in VANET needs local and continual knowledge of nodes. Last, the presence of malicious nodes and their misbehaving activities impair the safety of the drivers since they might alter the content of the sent safety alerts. With these constraints in mind, this paper presents a unique security strategy that utilizes node behaviour during message exchange as a security metric to address these issues. Through the message alert exchange phase, node behaviour is measured through the fuzzy logic framework to generate a rank for each node called trust level (BL), which describes the node’s reliability in exchanging safety messages correctly. Moreover, all messages in VANET are encrypted using the existing cryptography techniques. The proposed scheme is developed to enhance communication security in VANET, minimize the effects of malicious nodes, and improve resource utilization in VANET. Evaluation of the proposed scheme shows that it improves the performance of VANET in terms of end-to-end delay, packet delivery ratio, and packet loss ratio. According to the results, our scheme improves throughput by up to 23% and reduces end-to-end delay by up to 60%.
Keywords:
malicious node; security; vehicular ad hoc networks; road safety; fuzzy logic; trust level 1. Introduction
Nowadays, the exponential rise of vehicular communication deployment and application is intrinsically related to the rapid population growth. Fortunately, advancements in wireless communication technology inspire the creation of new communication paradigms in which vehicles can communicate with one another, i.e., VANET. Numerous safety-related and non-safety-related applications are supported by VANET. However, these applications require low latency, high reliability, and an appropriate data rate. Safety applications that employ VANET are primarily concerned with security. In VANET, multiple nodes are allowed to dynamically access the frequency bands due to the mobile nature of vehicles [1,2,3,4,5,6,7]. Due to the unique characteristics of VANET, security is a challenge that must be handled. These characteristics include security, unpredictable growth and decrease of nodes, random topology, high node mobility, and fluctuating interference. Unfortunately, the dynamic nature and flexibility of accessing VANET’s spectrum have attracted malicious nodes’ attention, making VANET a target of malicious operations [8]. As a result, typical wireless network security schemes cannot be directly applied in VANET since they result in poor network performance regarding data accuracy, delay, packet delivery ratio, and throughput.
VANETs, like any other type of short-distance wireless network, are exposed to a wide range of security threats [9,10]. Unfortunately, any radio frequency can be blocked or jammed if a transmitter broadcasts a signal simultaneously and with sufficient power. There is no way to supervise the behaviour of unknown nodes, which jeopardizes the security of the VANET connection. All packets intended to be sent in a VANET may be delayed, changed, or dropped by a malicious node. As a result, in order to avoid malicious behaviours, the security of VANETs must be assessed in two ways. The first method is to encrypt the data provided over VANET. The second method is to monitor node activity and exclude malicious nodes while selecting trustworthy nodes to join VANET. VANETs have not been secured by combining both approaches to the best of our knowledge.
In addition to encrypting data in the VANET, our scheme removes malicious nodes based on their behavior in order to secure the VANET. In our trust-based security scheme, decisions are made based on specific node behaviour, which introduces uncertainty. Fuzzy logic handles uncertainty and tolerates imperfect data with great precision. A fuzzy logic-based multi-attribute trust model is proposed in this paper. Emulation attack attempt, collaboration degree, and RSU assessment are trust measures in the proposed trust paradigm. After calculating the three trust values, fuzzy computational theory is used to compute the final trust value of each node, which can be low (1), medium (2), or high (3). In our security scheme, a fuzzy logic module is used to deal with ambiguity in decision-making. In order to distinguish malicious nodes from others, it makes a decision based on multivariate attributes per node.
There are a variety of factors that should be taken into account when assessing a node’s trustworthiness. However, the process of assessing a node’s trustworthiness sometimes requires trade-offs among conflicting criteria. As a result, we often have to prioritize one criterion above another. To solve the trust assessment dilemma, we need to establish a middle ground between conflicting criteria. We begin by investigating the criteria that are in direct opposition to one another (i.e., the emulation attack attempt, the level of collaboration, and the RSU evaluation). Then, an aggregator operator takes into account multiple factors to establish a node’s credibility. In our research, we use fuzzy logic as an aggregation operator to resolve the issue of new nodes’ trust ratings being inconsistent due to conflicting criteria.
The remainder of this article is organized as follows. First, related work and our contributions to the paper are introduced in Section 2. Next, VANET is presented in Section 3. We describe the proposed security scheme in Section 4. Then, we present some of the performed tests and show the performance of the VANET under different conditions with our scheme in Section 5. Finally, the article is concluded in Section 6.
2. Related Works
VANETs have a number of special features that make developing a solid trust model difficult. Long-term vehicle engagement is impractical because of the high movement of vehicles. Most of the time, only a few bits of information will be sent back and forth between two cars. The topology of the VANET, on the other hand, is dynamic. As a result, a solid trust model should be able to handle both dense and sparse settings. The trust model has to withstand many threats while also maintaining the privacy of the vehicles.
In [11], the authors suggested a trust-based authentication method for grouped vehicle ad hoc networks. The main goal of the proposed method is to create trustworthy and stable clusters that lead to the stability of the whole network. Messages are digitally signed by the sender, encrypted with a public/private key from a trusted authority (TA), and decrypted by the recipient. This gives each message a certificate from a trusted authority.
In [12], the authors suggest a trust management system that is based on hybrid cryptography (TMHC). The goal of this scheme is to increase the level of security that is present in VANET. Asymmetric identity-based (ID-based) digital signature and symmetric hash message authentication code are components of the technique proposed here (HMAC). Extensive simulations were used to achieve these results, which were then used to validate the suggested scheme.
In [13], The research aims to determine how much each vehicle in VANET can be trusted and to weaken rogue nodes. The data trust module evaluates a vehicle’s trustworthiness using trust evaluation and reputation calculation models. The vehicle trust authority uses a collaborative technique to aggregate several node trust evaluations. The recommended method sends high-priority signals with a higher rate of true positives and a lower rate of false positives than existing methods such as the Dempster–Shafer evidence theory and Bayesian inference. Experiments show that the Gaussian kernel function is best for our model. Proposed models are more energetic, according to positive rates.
Paper [7] presents a novel scheme for minimizing the invalidity ratio of VANET packet transmissions. The proposed scheme combines evidence from the current and past behaviour to detect unusual traffic to evaluate the trustworthiness of both data and nodes. A new intrusion detection scheme is accomplished through four phases: rule-based security filter, Dempster–Shafer adder, node history database, and Bayesian learner. The proposed solution is validated through extensive simulations. The results confirm that the fusion of different evidence has a significant positive impact on the performance of the security scheme compared to other counterparts.
Gazdar et al. [14] used a method of analysis based on layers. The vehicle is always figuring out how reliable the data it gets is based on what it knows from its own experience. The main goal of this TM is to determine which vehicles can be trusted and which cannot by looking at the data they send and judging how trustworthy each participating vehicle is. Each vehicle’s neighbours have a trust table. When messages come from trusted cars, their trustworthiness goes up, while the trustworthiness of messages from less trusted cars goes down. This system effectively detects hostile vehicles because it relies exclusively on vehicle input.
Nodes in VANETs (vehicular ad hoc networks) are mobile and dynamic. Managing privacy, trust, and data security has become more challenging. There are several ways to target data in these networks, but distributing misleading information is the most harmful [7]. As a result, in [7], they propose an authentication system that enables RSUs to communicate with automobiles without disclosing their identities. A vehicle’s nearest RSU can verify whether or not a fault occurred by utilizing the trust model. This technique was implemented to ensure that RSUs only send event notifications that have been checked. Finally, RSUs help to maintain and record the trust values of cars on the blockchain.
In VANETs, vehicles share content with other vehicles and roadside devices (RSU). However, RSUs and vehicles are not always reliable [15].To address these security concerns [16] proposed a blockchain-based content-sharing management method. They employ a consensus process known as practical Byzantine fault tolerance (PBFT), based on the frequency with which RSUs and automobiles interact. The frequency of interactions improves the possibility that the RSU will gain the right to package the block. So, RSUs and autos actively participate in the network, resulting in effective and honest content sharing. The authors conducted extensive testing to demonstrate that the proposed techniques can be implemented.
The author introduced the concept of mobile social networking in [17]. The study’s findings prompted the authors to conclude that the mobile social networking (MSN) mechanism might potentially replace existing VANET collaboration methods to encourage node cooperation. The MSN approach lacks an acceptable way of dealing with latency and packet loss issues. A social networking strategy is insufficient when there are a limited number of paths and high mobility of autos [16].
The detection models based on the trust evaluation process in VANET garner considerable interest due to their potential to preserve network stability and meet service application requirements’ quality [17]. The network, which is periodically contacted by certification and traffic control organizations, is used to validate the vehicles’ behaviour and determine their reputation levels. The receiver vehicles’ decision-making systems use the reputation of the communication nodes to assess the veracity or untruth of the communications. A novel architecture that protects data security and privacy has reduced the severity of many VANET attacks. In [18], authors propose new security scheme for early detection of a black hole attack during the route discovery process. After computing the dynamic threshold value, the scheme generates a forged route request (RREQ) packet. A new security scheme was proposed in [19] to allow nodes to determine the legitimacy of messages. To combine direct and indirect reputation reports, the uncertain deductive technique was used. In addition, game theory was employed to encourage nodes to cooperate. In [20], the authors proposed a scheme for detecting malicious nodes. The trust for each node is calculated by gathering data about the node and feeding it into a fuzzy logic model that evaluates the node’s trust level. In [21], the authors suggested a new approach for detecting Sybil attackers in VANET. The detecting parameters are signal strength measurements and Euclidean distance. The reward for each vehicle is determined by gathering RSU feedback on the vehicle’s behavior.
Some of the proposed schemes are distributed in which the vehicle’s trust is evaluated through the trust information interaction between the vehicles in the VANET without regard for central authorization. Although this technique addresses the scalability issue of VANET, it cannot ensure correct information from nodes. Many nodes join and leave the VANET in a short period of time. Furthermore, complete trust information cannot be ensured. These schemes suffer from communication overhead because of trust evaluation. The majority of distributed schemes take no action against malicious nodes. On the other hand, RSU evaluates trust and manages security for all nodes in its range. However, most of these approaches presume that RSU communications are always safe and that no node attempts to replicate RSU. Additionally, several of these techniques do not address message diffusion. Furthermore, they take no action after detecting malicious nodes.
3. Network Overview
On each road, roadside units (RSUs) are regularly distributed. Every vehicle has an onboard unit (OBU). Specifically, there are stationary roadside units (RSUs) and moving vehicles equipped with OBUs in our proposed system model. RSU takes charge of managing vehicles and securing communication in VANET. In order to secure data in VANET and ensure a secure driving environment, RSU has a powerful and computational competence to control an indefinite number of vehicles.
RSU examines each new node that joins VANET before allowing it to communicate data with the rest of the network. Secure wireless connections are used to link all of the nodes together in VANET. Vehicles receive alert messages via RSUs. In order to ensure that the vehicles can update their information while driving on the roads, RSUs are strategically placed along the roadways to cover the entire area.
Since they are all outfitted with OBUs, the vehicles form a network of highly mobile nodes that can communicate with one another and with remote sensing units, or RSUs. When passing RSUs, a vehicle communicates with the RSU and updates its travel information or uploads data. In our work, vehicles are divided into clusters. Clustering architecture is one of the most widely used strategies to handle security in VANETs. Vehicles in a cluster-based VANET are divided into small zones depending on specified regulations, and vehicles in each cluster are managed by the RSU, which is in charge of the entire communication operation in the cluster, as well as security management. The architecture has a number of advantages over other architectures. These are some examples:
- Data aggregation: RSU collects data from all vehicles in a zone in order to identify malicious nodes and provide the final road status and conditions.
- Reduced communication overhead: each node must only communicate with RSU.
- Simple to maintain: each road is divided into zones, with a separate RSU assigned to control security in each zone.
4. Trust Evaluation in VANET
A VANET is a network with nodes and M remote service units (RSUs). RSU is in charge of overseeing and controlling traffic on VANET as well as the nodes within its jurisdiction. Each new node is given a trust level value by RSU. The range of TL is [22,23,24]. The key element that determines the existence of a node in a VANET is . Nodes with a lower will be removed from the VANET.
All the messages sent via VANET are secured by encrypting them using symmetric key cryptography. Symmetric key cryptography has many advantages that include:
- Highly secure when it employs a secure algorithm.
- Relatively fast and efficient for large amounts of data.
- Requires low computer resources
- Straightforwardness.
As a result of allowing only trusted nodes to participate in VANET and access the network, VANET’s resources are better managed and utilized. Public key cryptography is utilized until the nodes and the RSU share a symmetric key. Each node utilizes a symmetric key during the node’s authentication process [20]. VANET utilizes a single encryption key for both encoding and decoding communications. The symmetric key is used to encrypt each communication. The received messages are decrypted with the same key. If each node is aware of RSU signal information, we presume it uses this information to detect and avoid malicious nodes that mimic RSUs. If the received signal does not match the expected RSU signal, the node notifies RSU of an emulation attack, i.e., a malicious node emulates RSU. The RSU receives data about the road from each node. RSU compares each vector of data received. The RSU determines a malicious node if the node’s vector does not match.
RSU makes the final decision regarding the road status based on the data sent by different nodes and their . After processing the data, RSU delivers the final decision to trustworthy nodes. A specific rule is followed to process these reports to determine the final road status. The common rule is the K-out-of-N rule, wherein K nodes out of N nodes have the same opinion to evaluate their opinion. In case 50 percent K-rule is employed, K is equal to N/1.5. We suggest a novel K-rule where K indicates the number of votes wherein we assign each user a distinct voting weight based on its value. We apply the following criteria in order to obtain the value of K:
- A node with a value of 3 counts as three votes.
- A node with a value of 2 counts as 1.5 votes.
- A node with a value of 1 counts as zero votes.
4.1. Reward Trust Level Computation
In our scheme, each node examines the behaviour/actions of the other nodes and sends feedback to RSU. Based on the feedback, the RSU updates the for vehicles. Incorrect feedback from nodes adversely harms the safety of drivers dramatically. Periodically, RSU broadcasts a message containing its position as well as the MAC addresses of all nodes in its zone. When a node receives this message, it creates a neighbor table. Each node maintains the behaviour of every participating node in the table for each transaction. When RSU requests recommendation for a certain node, the data in the database is used to assess the node’s trustworthiness. If no information is available, the node will apologize. The architecture of our proposed model is illustrated in Figure 1. In our model, the following criteria are considered for computing the trust level for a node in VANET:
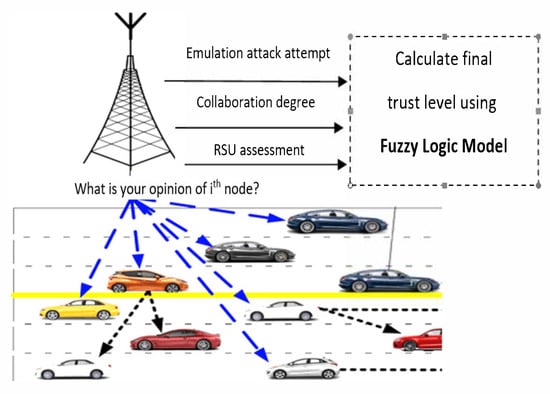
Figure 1.
The architecture of the proposed trust mode.
- Emulation attack attempt.
- Collaboration degree.
- RSU assessment.
4.1.1. Emulation Attack Attempt
The position of RSU is known to all nodes in VANET. Each node , upon receiving the message from RSU, computes the received signal strength and compares it with estimated signal strength From RSU. After comparing the signal strengths, the ith node decides whether the received signal is received from RSU or not, as follows:
The ith node considers the jth who transmitted the signal to be a malicious node if the signal difference is greater than the threshold β. In addition, to compare signal strength, ith node checks a vector of RSU known properties, such as message length, message time stamp, etc. The jth node’s MAC address and location are reported to RSU by ith node.
4.1.2. Collaboration Degree
RSU assigns 2 as the initially expected trust level for the new node in VANET. This value is adjusted based on positive “good behaviour” or negative “negative behaviour” evidence. For each node, is computed as follows:
where is the number of positive actions, is the number of the bad evidence, and is the maximum trust level (i.e., 3). RSU counts the number of transactions that jth node accepts to perform among all transactions . RSU computes the degree of collaboration for jth node as follows:
RSU rewards jth node for each executed transaction successfully according to a value called the reward factor and each it penalizes jth node by decreasing the expected according to a value called . At time the expected is adjusted by factor that is calculated as follows:
where is the set of nodes which decide that jth node is good, is the set of the node that the believe jth node is bad, and Trust level computed by node jth node about ith node using Equation (2). This factor is normalized as follows:
The expected trust level is adjusted at time as follows:
where is the expected trust value at time . Each reporting node’s is critical in calculating the trustworthiness of each node.
4.1.3. RSU Assessment
A node’s trustworthiness can be evaluated using RSU’s cost and reward functions. Each node gets a fixed amount of reward after letting it connect to the VANET for the first time. RSU increases the reward for each successful transaction based on various parameters, including the information’s significance and the transaction’s correctness. The reward that is assigned for ith node after executing a required transaction is calculated as follows:
where is the reword for executing transaction , and is the weight for transaction . The node in VANET can send and receive a message if it has a reward. For ith node, the cost for acting badly at time is calculated as follows:
where is the cost of acting bad, and is the weight for behaviour . RSU evaluates the trust for ith node at time as follows:
RSU computes the trust level for each new node based on history. Each node is evicted if the reward is minus. The normalized reward is calculated as follows:
Any node with a minus reward will be evicted from VANET.
4.2. Fuzzy Logic for Trust Evaluation
The fuzzy logic model is used to extract the trust for each node. Firstly, the fuzzy model extracts the boundaries for trust level. The final trust level for ith node is calculated as follows:
where is the weight for RSU assessment, is the weight for collaboration degree, and is the weight for emulation attack attempt. After calculating the final trust level, the RSU evicts the nodes with the lowest trust level. Each vague trust value in the fuzzy set has a single membership value between 1 and 3.
Definition 1.
Let X = {, …, } Y = {, …, } be the conflict values. A fuzzy membership interval in X, Y, respectively, is determined as follows:
Definition 2.
Two membership functions characterize X and Y:
- (1)
- A truth membership min function : X ∈ [1,2,3]
- (2)
- A false membership max function B: Y ∈ [0,1,2]
Where () is a lower bound value of membership , and () is a high bound value of membership
Definition 3.
The fuzzy logic interval is written as follows:
where is the mean value after iteration; in our work, we calculate the mean r times, where r represents the tolerance with the boundaries of interval membership. The mean values cannot exceed 3, that is, [] ≤ 3. The rank boundaries in this work are three levels, respectively, low, moderate, and high. The trust level interval is represented as follows:
The lowest and highest boundaries of the priority rank interval are computed respectively as follows:
For malicious node eviction, we use Algorithm 1. RSU uses a security scheme to remove malicious nodes from its zone. When a new node requests to join the VANET, the algorithm is started. RSU notifies all nodes to provide their recommendation for a new node. After gathering the necessary data, it is fed into a fuzzy logic algorithm that classifies the node. If the trust level is less than 2, the node is evicted, and RSU broadcasts a message informing all nodes in its region not to collaborate with this node.
| Algorithm 1: Malicious node eviction |
| 1: For each new node i in VANET |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: if (T==low) |
| 8: Broadcast-Exclude(i); |
| 9: if |
| 10: end for |
5. Performance Evaluation
The simulation model is built using MatLab R2019a. We compare our proposed security scheme (FS) with unsecured VANET, where no scheme is used to secure data over VANET. Four performance measures are used in the comparison: throughput, average end-to-end delay, packet delivery ratio, and packet loss ratio. We evaluate the performance of our scheme by examining its ability to improve the performance of VANET. The results are averaged over enough independent runs so that the confidence level is 95% and the relative errors do not exceed 5%. We examine the performance under different parameter settings. Table 1 shows the parameters utilized to assess the proposed scheme. The settings of the input parameters are chosen to reflect a portion of the reality of wireless applications, such as phone call traffic.

Table 1.
Simulation Parameters.
Our scheme excludes malicious nodes that keep acting badly in the VANET. Whilst some malicious nodes attempt to make the connectivity in VANET very slow, others continually modify the alarm messages in VANET. Other nodes claim they cannot rely on some messages in VANET. As a result of these undesirable behaviours, the throughput of VANET is degraded dramatically. Figure 1 depicts the effect of malicious nodes on the performance of VANET in terms of throughput. The figure displayed the results of our method and unprotected VANET (UV) without any security mechanism. In the experiment, we took the throughput of VANET at various malicious nodes. Clearly, as the number of malicious nodes increases in the VANET, the throughput decreases considerably. Fortunately, our technique eliminates malicious nodes that enable VANET to deliver good service for drivers. However, UV scheme does not take any action regarding malicious nodes that continually drop packets and discard some packets. Figure 2 shows that our scheme enhances throughput by up to 23%.
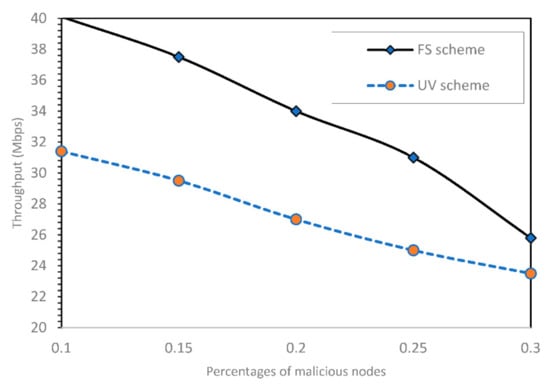
Figure 2.
Throughput at various percentages of malicious nodes.
Figure 3 illustrates the end-to-end delay in our proposed approach compared to UV scheme. As the number of malicious nodes increases, the end-to-end delay increases in both schemes. Some nodes attempt to postpone relaying packets. Our scheme excludes these nodes by punishing them according to the cost function in equation (8). Nodes that act bad are excluded from VANET by our scheme. Figure 3 shows that our proposed scheme outperforms the UV scheme, i.e., the end-to-end delay is improved by up to 60%.
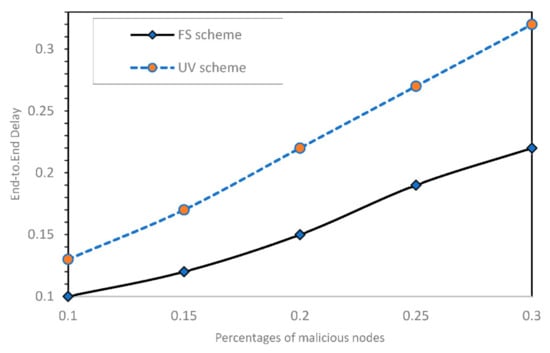
Figure 3.
End-to-end delay (proposed approach vs. UV).
The packet delivery ratio is compared in our proposed scheme and UV scheme, as shown in Figure 4. The packet delivery ratio decreases with the increment of the number of malicious nodes in the network. It can reach up to 95% for our scheme. The accuracy of relying on packets is essential in allowing nodes to join VANET. Nodes that keep dropping packets are evicted from VANET using our scheme.
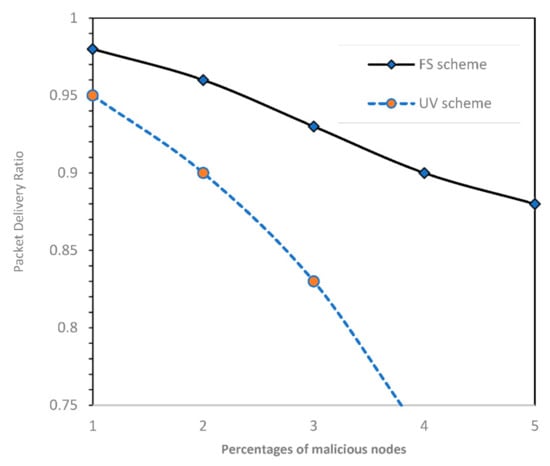
Figure 4.
Packet delivery ratio (proposed approach vs. UV scheme).
On the other hand, in Figure 5, we compare the packet loss rate in our proposed scheme and the UV scheme. Under the simulation used to measure the packet loss ratio of the two methods, the packet loss ratio drops quickly when fewer malicious nodes are relaying packets over the network. Our approach succeeds in having the minimum packet loss ratio, which outperforms the UV. Figure 4 illustrates that our scheme reduces packet loss ratio by over 50%.
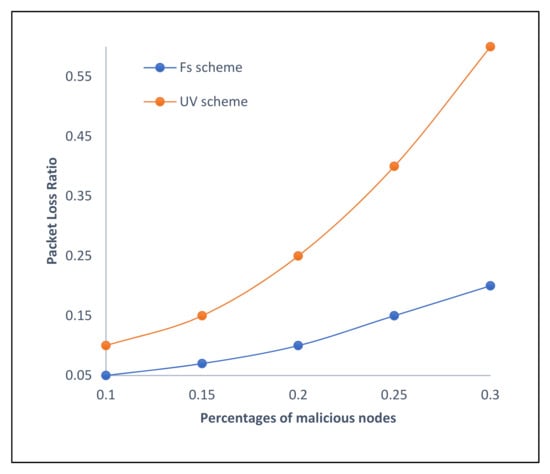
Figure 5.
Packet loss ratio (proposed approach vs. UV scheme).
6. Conclusions
Because VANETs are susceptible to various attacks, security must be considered while creating new policies to keep malicious nodes out. We proposed a security scheme to find and remove malicious nodes from VANET. In our scheme, the eviction of untrusted nodes prevents future attacks in VANET. Our scheme encourages cooperation among the network’s nodes by rewarding selfish nodes. The final trust level for each node is computed using fuzzy logic. Emulation attack attempt, degree of collaboration, and RSU assessment are some criteria used to evaluate the node. Currently, node behaviour is not employed in security schemes to exclude untrustworthy nodes. These approaches stress the significance of merely encrypting messages. Our scheme uses node behaviour as a metric to filter out malicious nodes and prevent them from attacking networks. The simulation results demonstrate that our scheme improves network performance metrics, boosting network security, improving spectrum utilization, and network throughput. Our scheme improves throughput by up to 23% and reduces end-to-end delay by up to 60%, according to the results. Despite the improved performance of the proposed solution, this study was still bound by several research limitations. To begin, the proposed method solely considered VANET nodes when evaluating the trust of the new node. However, IoT devices and other RSUs can be consulted about new node. Future works should include deployment of the proposed solution in autonomous vehicles where one of them act as RSU. Furthermore, machine learning methods can be used to classify nodes in VANET. In the future, we intend to compute the proposed approach’s time complexity and compare it to other security schemes in terms of additional performance metrics such as network speed and latency. Furthermore, we will validate our technique using a verification tool to test its robustness against various threats and to demonstrate that it discovers the optimum secure path over the VANET.
Author Contributions
Conceptualization, B.I., A.A. (Ayoub Alsarhan) and A.A.-Q.; Formal analysis, I.A.-K.; Funding acquisition, A.A. (Amjad Aldweesh); Methodology, B.I., A.A. (Ayoub Alsarhan) and A.A. (Amjad Aldweesh); Project administration, I.A.-K.; Validation, A.A.-Q.; Writing–review & editing, A.A.-Q. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Acknowledgments
The authors would like to thank the Deanship of Scientific Research at Shaqra University (KSA) and The Hashemite University (Jordan) for supporting this work.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zeadally, S.; Hunt, R.; Chen, Y.-S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Su, J.; Ren, R.; Li, Y.; Lau, R.Y.; Shi, Y. Trusted Blockchain-Based Signcryption Protocol and Data Management for Authentication and Authorization in VANETs. Wirel. Commun. Mob. Comput. 2022, 2022, 9572992. [Google Scholar]
- Karopoulos, G.; Kambourakis, G.; Chatzoglou, E.; Hernández-Ramos, J.L.; Kouliaridis, V. Demystifying In-Vehicle Intrusion Detection Systems: A Survey of Surveys and a Meta-Taxonomy. Electronics 2022, 11, 1072. [Google Scholar] [CrossRef]
- Alsarhan, A.; Al-Ghuwairi, A.-R.; Alshdaifat, E.; Idhaim, H.; Alkhawaldeh, O. A Novel Scheme for Malicious Nodes Detection in Cloud Markets Based on Fuzzy Logic Technique. Int. J. Interact. Mob. Technol. 2022, 16, 102–191. [Google Scholar] [CrossRef]
- Almalkawi, I.; Halloush, R.; Alsarhan, A.; Al-Dubai, A.; Al-Karaki, J. A lightweight and efficient digital image encryption using hybrid chaotic systems for wireless network applications. J. Inf. Secur. Appl. 2022, 49, 102384. [Google Scholar] [CrossRef]
- Alsarhan, A.; Alauthman, M.; Alshdaifat, E.A.; Al-Ghuwairi, A.-R.; Al-Dubai, A. Machine Learning-driven optimization for SVM-based intrusion detection system in vehicular ad hoc networks. J. Ambient. Intell. Humaniz. Comput. 2021, 13, 1–10. [Google Scholar] [CrossRef]
- Alsarhan, A.; Al-Ghuwairi, A.-R.; Almalkawi, I.T.; Alauthman, M.; Al-Dubai, A. Machine Learning-Driven Optimization for Intrusion Detection in Smart Vehicular Networks. Wirel. Pers. Commun. 2021, 117, 3129–3152. [Google Scholar] [CrossRef]
- Sultan, S.; Javaid, Q.; Rehman, E.; Alahmadi, A.-A.; Ullah, N.; Khan, W. Incentive-Driven Approach for Misbehavior Avoidance in Vehicular Networks. Comput. Mater. Contin. 2022, 70, 6089–6106. [Google Scholar] [CrossRef]
- Hamza, M.-A.; Alshahrani, H.-M.; Al-Wesabi, F.-N.; Duhayyim, M.-A.; Hilal, A.-M.; Mahgoub, H. Artificial Intelligence Based Clustering with Routing Protocol for Internet of Vehicles. Comput. Mater. Contin. 2022, 70, 5835–5853. [Google Scholar]
- Nayak, R.-P.; Sethi, S.; Bhoi, S.-K.; Sahoo, K.-S.; Jhanjhi, N.; Tabbakh, T.-A.; Almusaylim, Z.-A. TBDDoSA-MD: Trust-Based DDoS Misbehave Detection Approach in Software-defined Vehicular Network (SDVN). Comput. Mater. Contin. 2021, 69, 3513–3529. [Google Scholar]
- Mirsadeghi, F.; Rafsanjani, M.K.; Gupta, B.B. A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-Peer Netw. Appl. 2021, 14, 2537–2553. [Google Scholar] [CrossRef]
- Tangade, S.; Manvi, S.S.; Lorenz, P. Trust Management Scheme Based on Hybrid Cryptography for Secure Communications in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 5232–5243. [Google Scholar] [CrossRef]
- Sultan, S.; Javaid, Q.; Malik, A.J.; Al-Turjman, F.; Attique, M. Collaborative-trust approach toward malicious node detection in vehicular ad hoc networks. Environ. Dev. Sustain. 2022, 24, 7532–7550. [Google Scholar] [CrossRef]
- Gazdar, T.; Belghith, A.; Abutair, H. An Enhanced Distributed Trust Computing Protocol for VANETs. IEEE Access 2018, 6, 380–392. [Google Scholar] [CrossRef]
- Lin, F.; Peng, Y.; Cui, T.; Huang, X.; Chen, Q. Blockchain based Content Sharing Management in VANETs. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), Helsinki, Finland, 25–28 April 2021; pp. 1–5. [Google Scholar]
- Hua, L.C.; Anisi, M.H.; Yee, L.; Alam, M. Social networking-based cooperation mechanisms in vehicular ad-hoc network—A survey. Veh. Commun. 2017, 10, 57–73. [Google Scholar] [CrossRef]
- Lu, T.; Chang, S.; Li, W. Fog computing enabling geographic routing for urban area vehicular network. Peer-Peer Netw. Appl. 2018, 11, 749–755. [Google Scholar] [CrossRef]
- Karim, A. Development of secure Internet of Vehicle Things (IoVT) for smart transportation system. Comput. Electr. Eng. 2022, 102, 108101. [Google Scholar] [CrossRef]
- Malik, A.; Khan, M.Z.; Faisal, M.; Khan, F.; Seo, J.-T. An Efficient Dynamic Solution for the Detection and Prevention of Black Hole Attack in VANETs. Sensors 2022, 22, 1897. [Google Scholar] [CrossRef]
- Na, F.; Wu, C.Q. On trust models for communication security in VANETs 2019, Ad Hoc Networks. Ad Hoc Netw. 2019, 90, 101740. [Google Scholar] [CrossRef]
- Alkhalidy, M.; Al-Serhan, A.F.; Alsarhan, A.; Igried, B. A New Scheme for Detecting Malicious Nodes in Vehicular Ad Hoc Networks Based on Monitoring Node Behavior. Future Internet 2022, 14, 223. [Google Scholar] [CrossRef]
- Krishnan, R.P.; Kumar, A.R.P. A collaborative strategy for detection and eviction of Sybil attacker and Sybil nodes in VANET. Int. J. Commun. Syst. 2021, 34, 3. [Google Scholar] [CrossRef]
- Wang, Y.; Ding, Y.; Wu, Q.; Wei, Y.; Qin, B.; Wang, H. Privacy-preserving cloud-based road condition monitoring with source authentication in VANETs. IEEE Trans. Inf. Forensics Security 2018, 14, 1779–1790. [Google Scholar] [CrossRef]
- Mishra, R.; Singh, A.; Kumar, R. VANET security: Issues, challenges and solutions. In Proceedings of the 2016 International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016; pp. 1050–1055. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).