Addressing the Effectiveness of DDoS-Attack Detection Methods Based on the Clustering Method Using an Ensemble Method
Abstract
:1. Introduction
Problem Statement
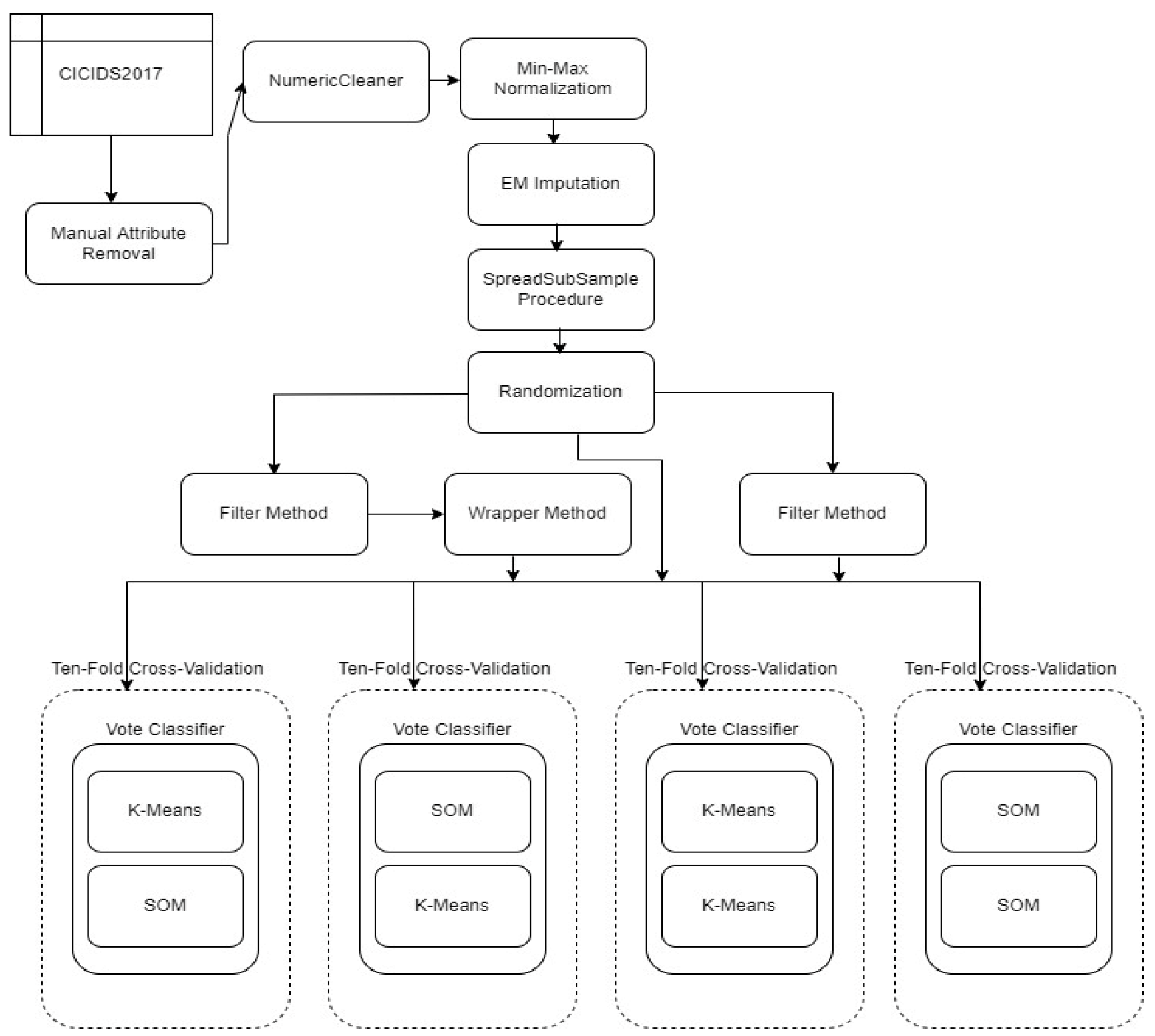
2. Materials and Methods
3. Literature Review
3.1. DDoS Attacks
3.2. Application of Clustering Algorithms in DDoS-Attack Detection
3.3. Application of CRISP-DM to Applied IT Problem
4. Data Analysis of the Experimentation
5. Study Validity
6. Results
6.1. Statistical Analysis Using One-Way ANOVA
6.2. Addition of the Filter Method in the B Phase and Comparison with the a Phase
6.3. Addition of the Wrapper Method in the BC Phase and Comparison with the a Phase
6.4. Comparison of Results across All DDoS-Attack Detection Methods
7. Discussion
8. Limitations and Implications
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Table of Independent Variables
| Independent Variable | Procedures |
|---|---|
| Combined Clustering Algorithms | Vote(SelfOrganizingMap & SimpleKMeans) Vote(SimpleKMeans & SelfOrganizingMap) Vote(SelfOrganizingMap & SelfOrganizingMap) Vote(SimpleKMeans & SimpleKMeans) |
| Filter Method | ChiSquaredAttributeEval InfoGainAttributeEval |
| Wrapper Method | WrapperSubsetEval(J48) WrapperSubsetEval(NaïveBayes) |
Appendix B. Experimental Results
| Applied Procedure in DDoS-Attack Detection Method | False-Positive Rates in DDoS-Attack Identification |
|---|---|
| Vote(SelfOrganizingMap & SimpleKMeans) | 0.062 |
| Vote(SimpleKMeans & SelfOrganizingMap) | 0.062 |
| Vote(SimpleKMeans & SimpleKMeans) | 0.172 |
| Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.191 |
| Applied Procedure in DDoS-Attack Detection Method | False-Positive Rates in DDoS-Attack Identification |
|---|---|
| InfoGainAttributeEval and Vote(SelfOrganizingMap & SimpleKMeans) | 0.093 |
| ChiSquaredAttributeEval and Vote(SelfOrganizingMap & SimpleKMeans) | 0.062 |
| InfoGainAttributeEval and Vote(SimpleKMeans & SelfOrganizingMap) | 0.093 |
| ChiSquaredAttributeEval and Vote(SimpleKMeans & SelfOrganizingMap) | 0.062 |
| InfoGainAttributeEval and Vote(SimpleKMeans & SimpleKMeans) | 0.180 |
| ChiSquaredAttributeEval and Vote(SimpleKMeans & SimpleKMeans) | 0.172 |
| InfoGainAttributeEval and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.139 |
| ChiSquaredAttributeEval and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.191 |
| Applied Procedure in DDoS-Attack Detection Methods | False-Positive Rates in DDoS-Attack Identification |
|---|---|
| InfoGainAttributeEval, Naïve Bayes, and Vote(SelfOrganizingMap & SimpleKMeans) | 0.013 |
| InfoGainAttributeEval, J48, and Vote(SelfOrganizingMap & SimpleKMeans) | 0.169 |
| ChiSquaredAttributeEval, Naïve Bayes, and Vote(SelfOrganizingMap & SimpleKMeans) | 0.013 |
| ChiSquaredAttributeEval, J48, and Vote(SelfOrganizingMap & SimpleKMeans) | 0.012 |
| InfoGainAttributeEval, Naïve Bayes, and Vote(SimpleKMeans & SelfOrganizingMap) | 0.013 |
| InfoGainAttributeEval, J48, and Vote(SimpleKMeans & SelfOrganizingMap) | 0.169 |
| ChiSquaredAttributeEval, Naïve Bayes, and Vote(SimpleKMeans & SelfOrganizingMap) | 0.013 |
| ChiSquaredAttributeEval, J48, and Vote(SimpleKMeans & SelfOrganizingMap) | 0.012 |
| InfoGainAttributeEval, Naïve Bayes, and Vote(SimpleKMeans & SimpleKMeans) | 0.014 |
| InfoGainAttributeEval, J48, and Vote(SimpleKMeans & SimpleKMeans) | 0.173 |
| ChiSquaredAttributeEval, Naïve Bayes, and Vote(SimpleKMeans & SimpleKMeans) | 0.211 |
| ChiSquaredAttributeEval, J48, and Vote(SimpleKMeans & SimpleKMeans) | 0.108 |
| InfoGainAttributeEval, Naïve Bayes, and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.014 |
| InfoGainAttributeEval, J48, and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.214 |
| ChiSquaredAttributeEval, Naïve Bayes, and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.013 |
| ChiSquaredAttributeEval, J48, and Vote(SelfOrganizingMap & SelfOrganizingMap) | 0.016 |
References
- Zeinalpour, A. Addressing High False Positive Rates of DDoS Attack Detection Methods. Ph.D. Thesis, Walden University, Minneapolis, MN, USA, 2021. [Google Scholar]
- Idhammad, M.; Afdel, K.; Belouch, M. Semi-supervised machine learning approach for DDoS detection. Appl. Intell. 2018, 48, 3193–3208. [Google Scholar] [CrossRef]
- Gahar, R.M.; Arfaoui, O.; Hidri, M.S.; Hadj-Alouane, N.B. A distributed approach for high-dimensionality heterogeneous data reduction. IEEE Access 2019, 7, 151006–151022. [Google Scholar] [CrossRef]
- Salimi, A.; Ziaii, M.; Amiri, A.; Hosseinjani Zadeh, M.; Karimpouli, S.; Moradkhani, M. Using a Feature Subset Selection method and Support Vector Machine to address curse of dimensionality and redundancy in Hyperion hyperspectral data classification. Egypt. J. Remote Sens. Space Sci. 2018, 21, 27–36. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, L.; Wang, B.; Li, F.; Zhang, Z. Feature clustering based support vector machine recursive feature elimination for gene selection. Appl. Intell. 2018, 48, 594–607. [Google Scholar] [CrossRef]
- Xiang, Y.; Wenchao, Y.; Shudong, L.; Xianfei, Y.; Ying, C.; Hui, L. Web DDoS attack detection method based on semisupervised learning. Secur. Commun. Netw. 2021, 2021, 1–10. [Google Scholar] [CrossRef]
- Mittal, M.; Kumar, K.; Behal, S. Deep learning approaches for detecting DDoS attacks: A systematic review. Soft Comput. 2022. [Google Scholar] [CrossRef]
- Alguliyev, R.M.; Aliguliyev, R.M.; Abdullayeva, F.J. PSO+K-means algorithm for anomaly detection in big data. Stat. Optim. Inf. Comput. 2019, 7, 348–359. [Google Scholar] [CrossRef]
- Akhter, M.P.; Zheng, J.; Afzal, F.; Lin, H.; Riaz, S.; Mehmood, A. Supervised ensemble learning methods towards automatically filtering Urdu fake news within social media. PeerJ Comput. Sci. 2021, 7, e425. [Google Scholar] [CrossRef]
- Ambusaidi, M.A.; He, X.; Nanda, P.; Tan, Z. Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Trans. Comput. 2016, 65, 2986–2998. [Google Scholar] [CrossRef]
- Kiranmai, S.A.; Laxmi, A.J. Data mining for classification of power quality problems using WEKA and the effect of attributes on classification accuracy. Prot. Control Mod. Power Syst. 2018, 3, 29. [Google Scholar] [CrossRef]
- Aksu, G.; Doğan, N. An analysis program used in data mining: WEKA. J. Meas. Eval. Educ. Psychol. 2019, 10, 80–95. [Google Scholar] [CrossRef]
- Moslehi, F.; Haeri, A.; Moini, A. Analyzing and investigating the use of electronic payment tools in Iran using data mining techniques. J. AI Data Min. 2018, 6, 417–437. [Google Scholar] [CrossRef]
- Cazacu, M.; Titan, E. Adapting CRISP-DM for social sciences. BRAIN Broad Res. Artif. Intell. Neurosci. 2020, 11, 99–106. [Google Scholar] [CrossRef]
- Contreras, Y.; Vera, M.; Huérfano, Y.; Valbuena, O.; Salazar, W.; Vera, M.I.; Borrero, M.; Barrera, D.; Hernández, C.; Molina, Á.V. Digital processing of medical images: Application in synthetic cardiac datasets using the CRISP_DM methodology. Rev. Latinoam. Hipertens. 2018, 13, 310–315. [Google Scholar]
- Groggert, S.; Elser, H.; Ngo, Q.H.; Schmitt, R.H. Scenario-based manufacturing data analytics with the example of order tracing through BLE-beacons. Procedia Manuf. 2018, 24, 243–249. [Google Scholar] [CrossRef]
- Douligeris, C.; Mitrokotsa, A. DDoS attacks and defense mechanisms: Classification and state-of-the-art. Comput. Netw. 2004, 44, 643–666. [Google Scholar] [CrossRef]
- Snehi, M.; Bhandari, A. Vulnerability retrospection of security solutions for software-defined Cyber–Physical System against DDoS and IoT-DDoS attacks. Comput. Sci. Rev. 2021, 40, 100371. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Mangat, V.; Vig, R.; Halder, S.; Conti, M. Distributed denial of service attacks in cloud: State-of-the-art of scientific and commercial solutions. Comput. Sci. Rev. 2021, 39, 100332. [Google Scholar] [CrossRef]
- Mishra, A.; Gupta, N.; Gupta, B.B. Defense mechanisms against DDoS attack based on entropy in SDN-cloud using POX controller. Telecommun. Syst. 2021, 77, 47–62. [Google Scholar] [CrossRef]
- Banitalebi Dehkordi, A.; Soltanaghaei, M.; Boroujeni, F.Z. The DDoS attacks detection through machine learning and statistical methods in SDN. J. Supercomput. 2021, 77, 2383–2415. [Google Scholar] [CrossRef]
- Amaizu, G.C.; Nwakanma, C.I.; Bhardwaj, S.; Lee, J.M.; Kim, D.S. Composite and efficient DDoS attack detection framework for B5G networks. Comput. Netw. 2021, 188, 107871. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4112. [Google Scholar] [CrossRef]
- Shohani, R.B.; Mostafavi, S.; Hakami, V. A statistical model for early detection of DDoS attacks on random targets in SDN. Wirel. Pers. Commun. 2021, 120, 379–400. [Google Scholar] [CrossRef]
- Gadallah, W.G.; Omar, N.M.; Ibrahim, H.M. Machine learning-based distributed denial of service attacks detection technique using new features in software-defined networks. Int. J. Comput. Netw. Inf. Secur. 2021, 13, 15–27. [Google Scholar] [CrossRef]
- Smys, S.; Bestak, R.; Palanisamy, R.; Kotuliak, I. (Eds.) Computer Networks and Inventive Communication Technologies: Proceedings of Fourth ICCNCT 2021; Springer: Singapore, 2021. [Google Scholar]
- Xu, Y.; Yu, Y.; Hong, H.; Sun, Z. DDoS detection using a cloud-edge collaboration method based on entropy-measuring SOM and KD-tree in SDN. Secur. Commun. Netw. 2021, 2021, 5594468. [Google Scholar] [CrossRef]
- Chio, C.; Freeman, D. Machine Learning and Security: Protecting Systems with Data and Algorithms; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2018. [Google Scholar]
- Aamir, M.; Ali Zaidi, S.M. Clustering based semi-supervised machine learning for DDoS attack classification. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 436–446. [Google Scholar] [CrossRef]
- Das, S. Detection and Explanation of Distributed Denial of Service (DDoS) Attack through Interpretable Machine Learning. Ph.D. Thesis, The University of Memphis, Memphis, TN, USA, 2021. [Google Scholar]
- Chen, Y.; Qin, B.; Liu, T.; Liu, Y.; Li, S. The comparison of SOM and k-means for text clustering. Comput. Inf. Sci. 2010, 3, 268–274. [Google Scholar] [CrossRef]
- Qazdar, A.; Er-Raha, B.; Cherkaoui, C.; Mammass, D. A machine learning algorithm framework for predicting students performance: A case study of baccalaureate students in Morocco. Educ. Inf. Technol. 2019, 24, 3577–3589. [Google Scholar] [CrossRef]
- Prasad, M.; Tripathi, S.; Dahal, K. An efficient feature selection based Bayesian and Rough set approach for intrusion detection. Appl. Soft Comput. 2020, 87, 105980. [Google Scholar] [CrossRef]
- Chiba, Z.; Abghour, N.; Moussaid, K.; El omri, A.; Rida, M. Intelligent approach to build a Deep Neural Network based IDS for cloud environment using combination of machine learning algorithms. Comput. Secur. 2019, 86, 291–317. [Google Scholar] [CrossRef]
- Manimekalai, K.; Kavitha, A. Missing value imputation and normalization techniques in myocardial infarction. ICTACT J. Soft Comput. 2018, 8, 1655–1662. [Google Scholar] [CrossRef]
- Nguyen, G.; Dlugolinsky, S.; Bobák, M.; Tran, V.; López García, Á.; Heredia, I.; Malík, P.; Hluchý, L. Machine learning and deep learning frameworks and libraries for large-scale data mining: A survey. Artif. Intell. Rev. 2019, 52, 77–124. [Google Scholar] [CrossRef]
- Cerón, J.D.; López, D.M.; Eskofier, B.M. Human activity recognition using binary sensors, BLE beacons, an intelligent floor and acceleration data: A machine learning approach. In Proceedings of the 12th International Conference on Ubiquitous Computing and Ambient Intelligence (UCAmI 2018), Punta Cana, Dominican Republic, 4–7 December 2018; p. 1265. [Google Scholar]
- Chengxiang, S.; Xiaoqing, L. Research on clustering algorithm based on improved SOM neural network. Comput. Intell. Neurosci. 2022, 2022, 1482250. [Google Scholar] [CrossRef]
- Miniak-Górecka, A.; Podlaski, K.; Gwizdałła, T. Using k-means clustering in python with periodic boundary conditions. Symmetry 2022, 14, 1237. [Google Scholar] [CrossRef]
- Khalaf, B.A.; Mostafa, S.A.; Mustapha, A.; Mohammed, M.A.; Abduallah, W.M. Comprehensive review of artificial intelligence and statistical approaches in distributed denial of service attack and defense methods. IEEE Access 2019, 7, 51691–51713. [Google Scholar] [CrossRef]
- Gu, Y.; Li, K.; Guo, Z.; Wang, Y. Semi-supervised k-means DDoS detection method using hybrid feature selection algorithm. IEEE Access 2019, 7, 64351–64365. [Google Scholar] [CrossRef]
- Bopche, G.S.; Mehtre, B.M. Graph similarity metrics for assessing temporal changes in attack surface of dynamic networks. Comput. Secur. 2017, 64, 16–43. [Google Scholar] [CrossRef]
- Guo, J.; Chiang, S.; Liu, M.; Yang, C.-C.; Guo, K. Can machine learning algorithms associated with text mining from internet data improve housing price prediction performance? Int. J. Strateg. Prop. Manag. 2020, 24, 300–312. [Google Scholar] [CrossRef]
- Gayathri, S.; Krishna, A.K.; Gopi, V.P.; Palanisamy, P. Automated binary and multiclass classification of diabetic retinopathy using Haralick and multiresolution features. IEEE Access 2020, 8, 57497–57504. [Google Scholar] [CrossRef]
- Mouhamadou, T.S. Using Anova to examine the relationship between safety & security and human development. J. Int. Bus. Econ. 2014, 2, 101–106. [Google Scholar] [CrossRef]
- Pereira, J.; Peixoto, H.; Machado, J.; Abelha, A. A data mining approach for cardiovascular diagnosis. Open Comput. Sci. 2017, 7, 36–40. [Google Scholar] [CrossRef]
- Abdulraheem, M.H.; Ibraheem, N.B. A detailed analysis of new intrusion detection dataset. J. Theor. Appl. Inf. Technol. 2019, 97, 4519–4537. [Google Scholar]
- Bashir, K.; Li, T.; Yohannese, C.W. An empirical study for enhanced software defect prediction using a learning-based framework. Int. J. Comput. Intell. Syst. 2018, 12, 282–298. [Google Scholar] [CrossRef]
- de Rooij, M.; Weeda, W. Cross-validation: A method every psychologist should know. Adv. Methods Pract. Psychol. Sci. 2020, 3, 248–263. [Google Scholar] [CrossRef]
- Anjum, S.; Qaseem, N. Big data algorithms and prediction: Bingos and risky zones in sharia stock market index. J. Islamic Monet. Econ. Financ. 2019, 5, 475–490. [Google Scholar] [CrossRef]
- Li, C.; Shi, D.; Chen, Y.; Zhang, H.; Geng, H.; Wang, P. A prediction scheme for the precipitation of spr based on the data mining algorithm and circulation analysis. J. Trop. Meteorol. 2019, 25, 519–527. [Google Scholar] [CrossRef]
- Abdulhammed, R.; Musafer, H.; Alessa, A.; Faezipour, M.; Abuzneid, A. Features dimensionality reduction approaches for machine learning based network intrusion detection. Electronics 2019, 8, 322. [Google Scholar] [CrossRef]
- Lamba, M.; Munjal, G.; Gigras, Y. Feature Selection of micro-array expression data (FSM)—A review. Procedia Comput. Sci. 2018, 132, 1619–1625. [Google Scholar] [CrossRef]
- Xiaofei, Q.; Lin, Y.; Kai, G.; Linru, M.; Meng, S.; Mingxing, K.; Mu, L. A survey on the development of self-organizing maps for unsupervised intrusion detection. Mob. Netw. Appl. 2021, 26, 808–829. [Google Scholar] [CrossRef]
- Ning, H.; Zhihong, T.; Hui, L.; Xiaojiang, D.; Guizani, M. A multiple-kernel clustering based intrusion detection scheme for 5G and IoT networks. Int. J. Mach. Learn. Cybern. 2021, 12, 3129–3144. [Google Scholar] [CrossRef]
- Sakr, M.M.; Tawfeeq, M.A.; El-Sisi, A.B. An efficiency optimization for network intrusion detection system. Int. J. Comput. Netw. Inf. Secur. 2019, 11, 1–11. [Google Scholar] [CrossRef]
- Ellis, T.J.; Levy, Y. Towards a guide for novice researchers on research methodology: Review and proposed methods. J. Issues Inf. Sci. Inf. Technol. 2009, 6, 323–337. [Google Scholar] [CrossRef] [Green Version]
| Source | Type III Sum of Squares | df | Mean Square | F | Sig. | Partial Eta-Squared |
|---|---|---|---|---|---|---|
| Corrected Model | 0.017 a | 2 | 0.008 | 1.530 | 0.236 | 0.109 |
| Intercept | 0.233 | 1 | 0.233 | 42.081 | <0.001 | 0.627 |
| Class | 0.017 | 2 | 0.008 | 1.530 | 0.236 | 0.109 |
| Error | 0.138 | 25 | 0.006 | |||
| Total | 0.407 | 28 | ||||
| Corrected Total | 0.155 | 27 |
| Methods | Mean | Std. Deviation | N |
|---|---|---|---|
| Clustering Only | 0.12175 | 0.069428 | 4 |
| Filter Method | 0.12400 | 0.053136 | 8 |
| Wrapper Method | 0.07356 | 0.083359 | 16 |
| Total | 0.09486 | 0.075865 | 28 |
| (I) Methods | (J) Methods | Mean Difference (I-J) | Std. Error | Sig. | 95% Confidence Interval | ||
|---|---|---|---|---|---|---|---|
| Lower Bound | Upper Bound | ||||||
| Tukey’s HSD | Clustering Only | Filter Method | −0.00225 | 0.045572 | 0.999 | −0.11576 | 0.11126 |
| Wrapper Method | 0.04819 | 0.041601 | 0.488 | −0.05543 | 0.15181 | ||
| Filter Method | Clustering Only | 0.00225 | 0.045572 | 0.999 | −0.11126 | 0.11576 | |
| Wrapper Method | 0.05044 | 0.032224 | 0.279 | −0.02983 | 0.13070 | ||
| Wrapper Method | Clustering Only | −0.04819 | 0.041601 | 0.488 | −0.15181 | 0.05543 | |
| Filter Method | −0.05044 | 0.032224 | 0.279 | −0.13070 | 0.02983 | ||
| Dunnett’s C | Clustering Only | Filter Method | −0.00225 | 0.039471 | −0.15616 | 0.15166 | |
| Wrapper Method | 0.04819 | 0.040489 | −0.10404 | 0.20042 | |||
| Filter Method | Clustering Only | 0.00225 | 0.039471 | −0.15166 | 0.15616 | ||
| Wrapper Method | 0.05044 | 0.028057 | −0.02681 | 0.12769 | |||
| Wrapper Method | Clustering Only | −0.04819 | 0.040489 | −0.20042 | 0.10404 | ||
| Filter Method | −0.05044 | 0.028057 | −0.12769 | 0.02681 | |||
| Levene’s Statistic | df1 | df2 | Sig. | ||
|---|---|---|---|---|---|
| False Positive Rates | Based on Mean | 3.539 | 2 | 25 | 0.044 |
| Based on Median | 0.133 | 2 | 25 | 0.876 | |
| Based on Median and with Adjusted df | 0.133 | 2 | 15.940 | 0.876 | |
| Based on Trimmed Mean | 2.758 | 2 | 25 | 0.083 | |
| Feature-Selection Methods | False-Positive Rates |
|---|---|
| CFS | 0.015 |
| IG | 0.068 |
| PCA | 0.020 |
| CFS-PSO | 0.015 |
| CFS-ABC | 0.014 |
| IG-PSO | 0.047 |
| IG-ABC | 0.086 |
| PCA-PSO | 0.035 |
| PCA-ABC | 0.022 |
| No Feature Selection | 0.015 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zeinalpour, A.; Ahmed, H.A. Addressing the Effectiveness of DDoS-Attack Detection Methods Based on the Clustering Method Using an Ensemble Method. Electronics 2022, 11, 2736. https://doi.org/10.3390/electronics11172736
Zeinalpour A, Ahmed HA. Addressing the Effectiveness of DDoS-Attack Detection Methods Based on the Clustering Method Using an Ensemble Method. Electronics. 2022; 11(17):2736. https://doi.org/10.3390/electronics11172736
Chicago/Turabian StyleZeinalpour, Alireza, and Hassan A. Ahmed. 2022. "Addressing the Effectiveness of DDoS-Attack Detection Methods Based on the Clustering Method Using an Ensemble Method" Electronics 11, no. 17: 2736. https://doi.org/10.3390/electronics11172736
APA StyleZeinalpour, A., & Ahmed, H. A. (2022). Addressing the Effectiveness of DDoS-Attack Detection Methods Based on the Clustering Method Using an Ensemble Method. Electronics, 11(17), 2736. https://doi.org/10.3390/electronics11172736







