A Blockchain-Based and SGX-Enabled Access Control Framework for IoT
Abstract
:1. Introduction
- The performance of the existing public blockchain cannot meet the massive terminal nodes of the Internet of Things; to solve this issue, we designed a blockchain framework of the permissioned blockchain on Quorum, based on the Ethereum protocol, to break the practical bottleneck. The framework saved the valuable storage space of the blockchain by distributing attribute signatures for clients off the chain. Specifically, it dramatically improves data-carrying capacity and transmission efficiency.
- We have designed an attribute-based access control contract to manage the access control strategy of IoT data resources in a fine-grained manner. It can effectively complete the process of client access verification on the blockchain. At the same time, the on-chain access control policy can be updated dynamically. We use a set of attributes to describe the client’s identity and grant it access through an off-chain attribute signature distribution mechanism. Therefore, our control access framework decouples access policy on the blockchain from client identity, which is more flexible than previous work [10,11].
- In data processing and the transmission of edge nodes, we use the Enclave security zone provided by Intel SGX as a trusted execution environment to process sensitive data. We use the remote attestation mechanism provided by Intel SGX to build a secure communication channel from the edge server to the client to ensure the credibility of data in the remote processing process and the security of the transmission process.
- We implemented a prototype of the proposed framework on Quorum. We conducted many experiments and compared them with previous work. Finally, we demonstrated the superiority of the proposed scheme with excellent performance data.
2. Related Technologies
2.1. Quorum and Smart Contract
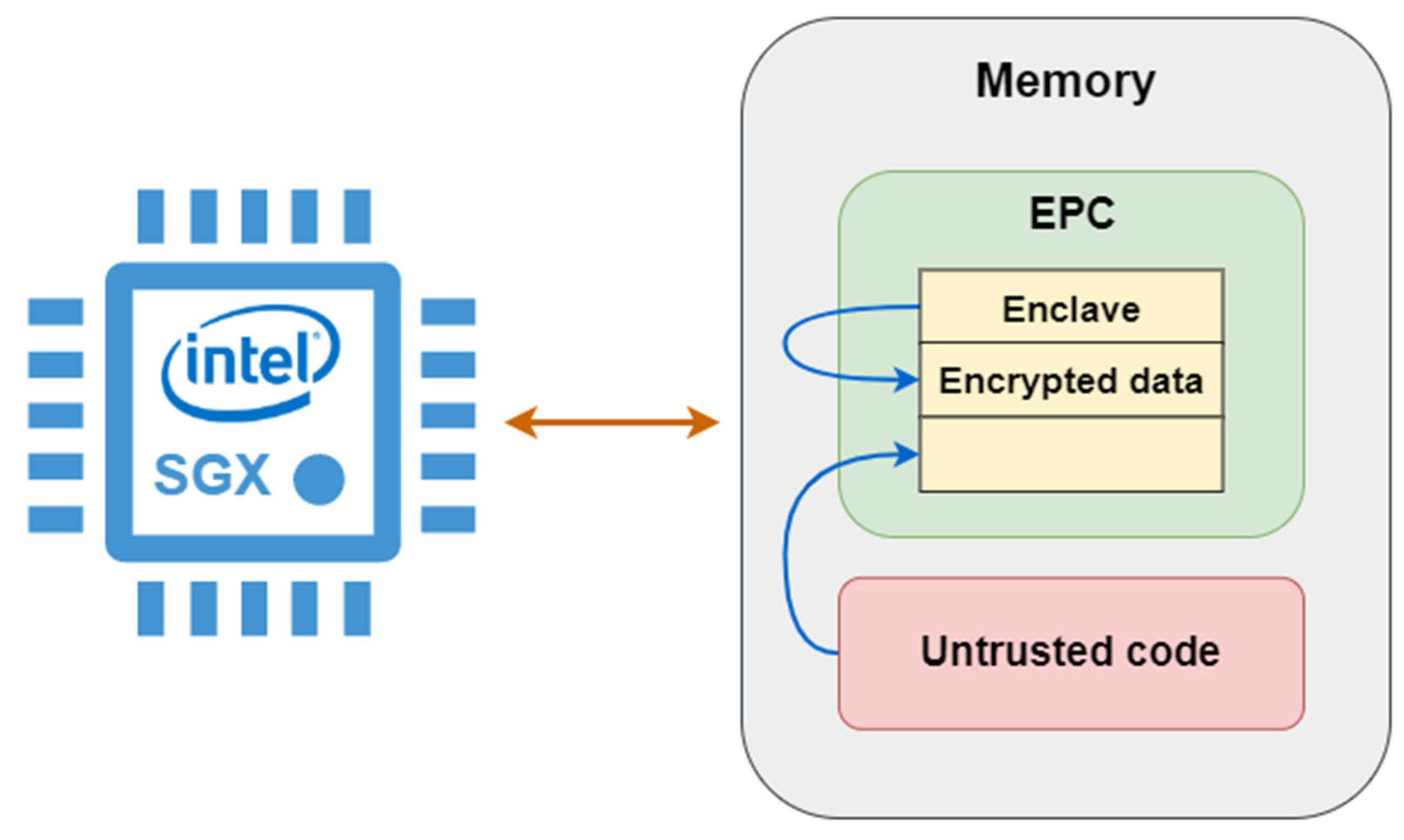
2.2. Intel SGX
2.2.1. Isolated Execution
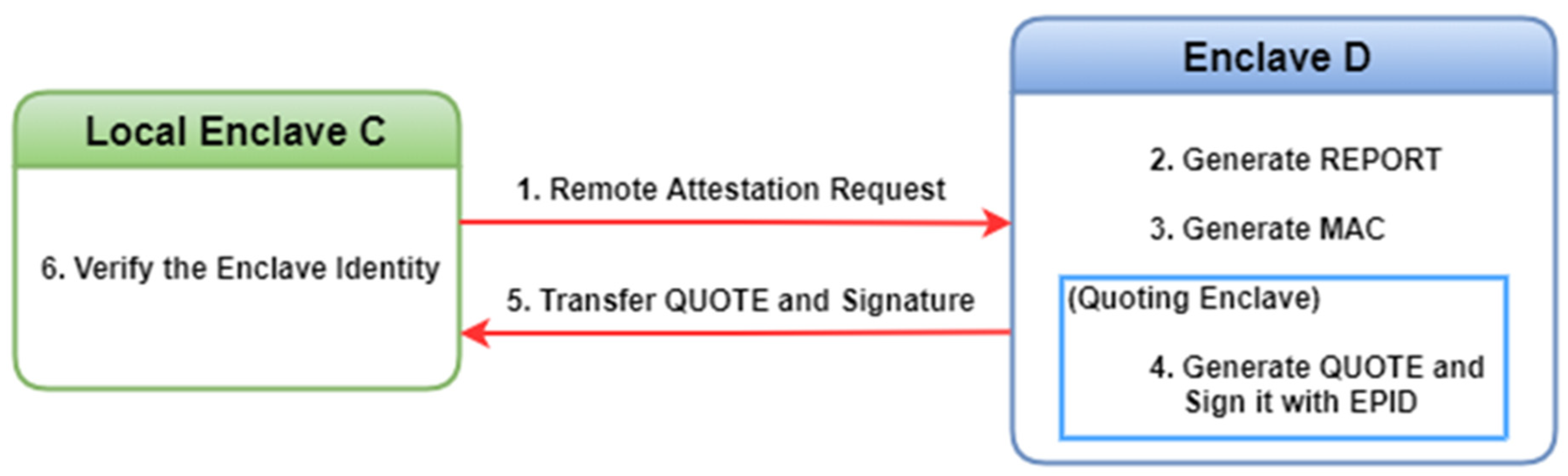
2.2.2. SGX Attestation
2.3. Access Control
3. Related Work
4. Design and Implementation
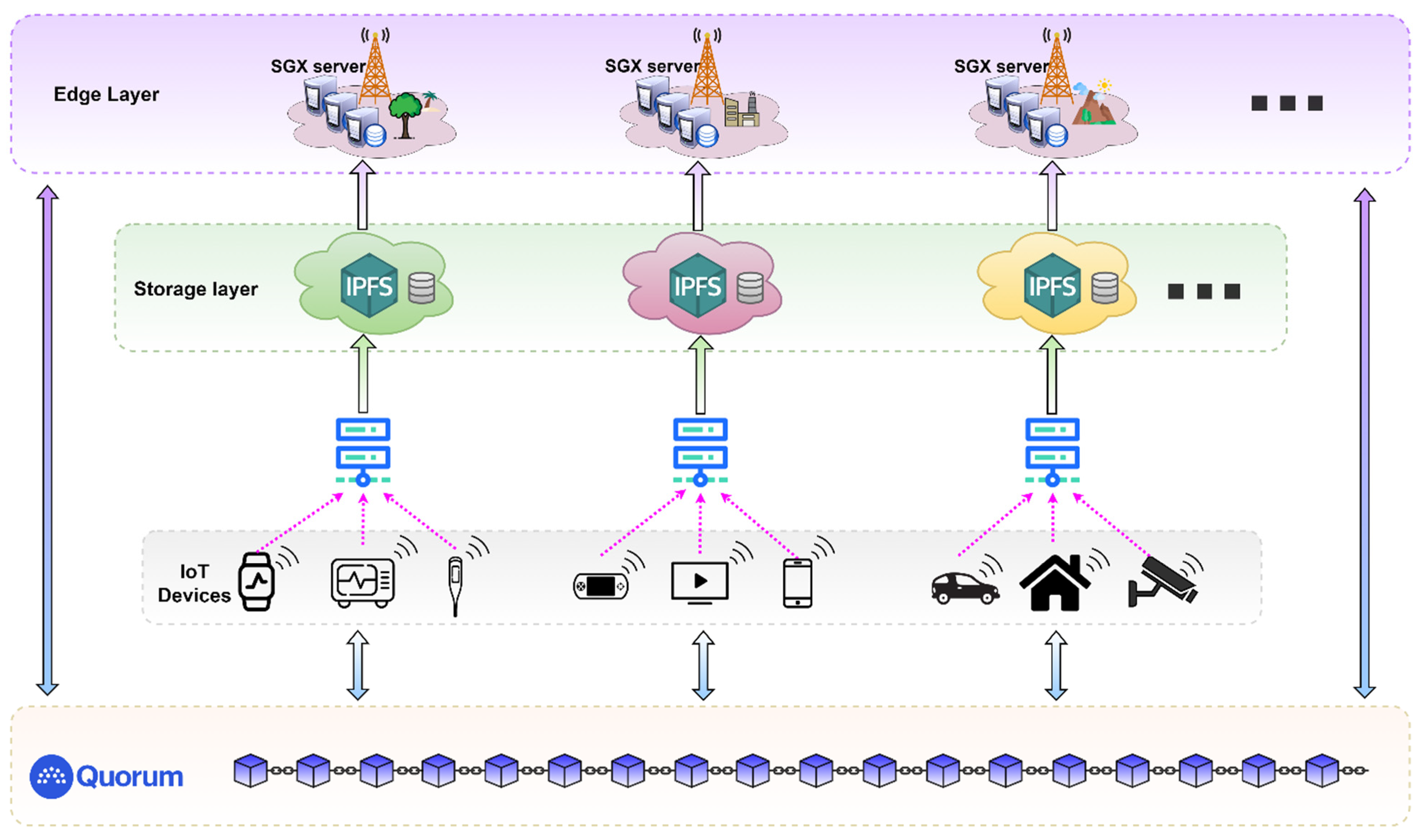
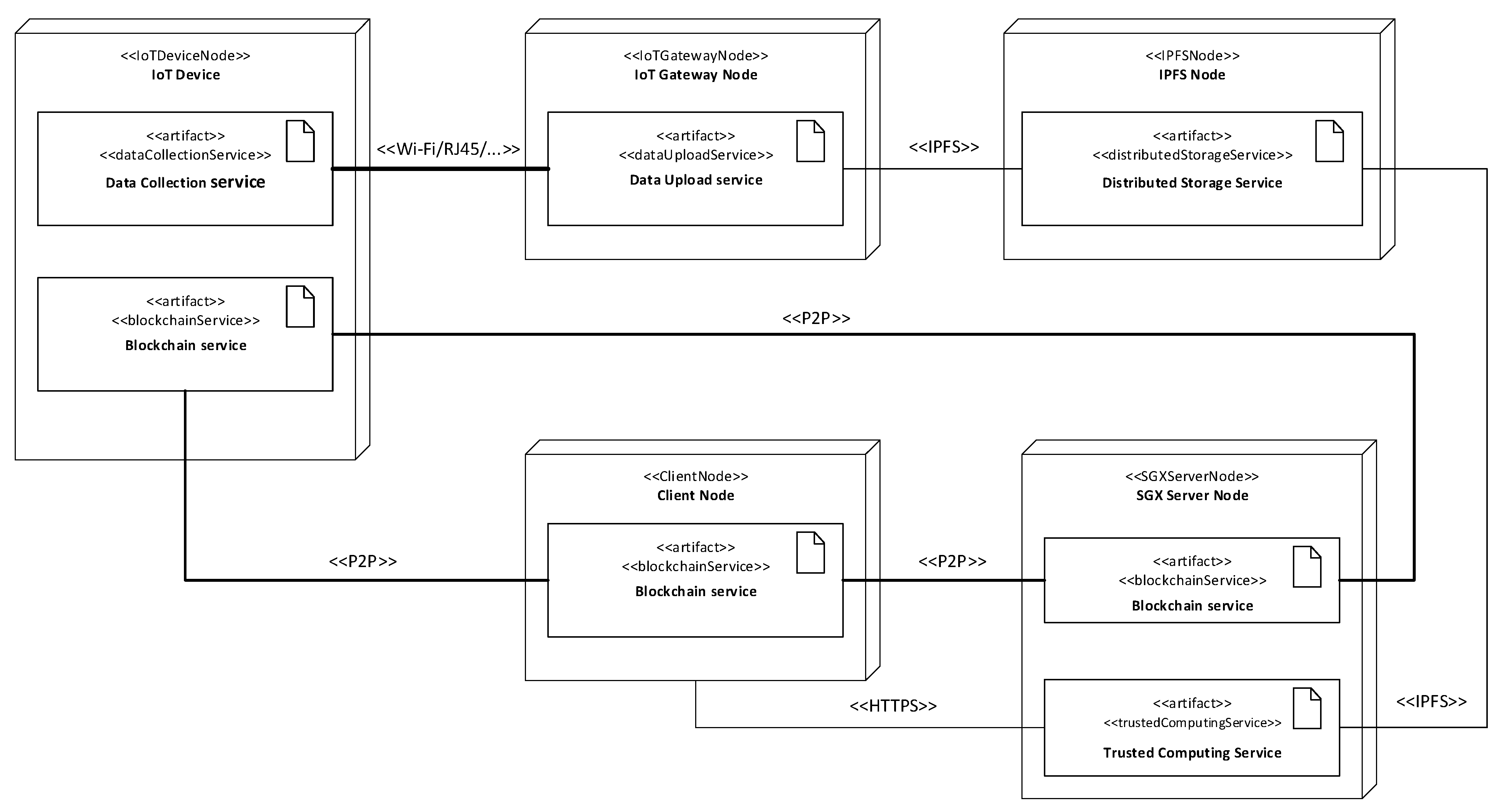
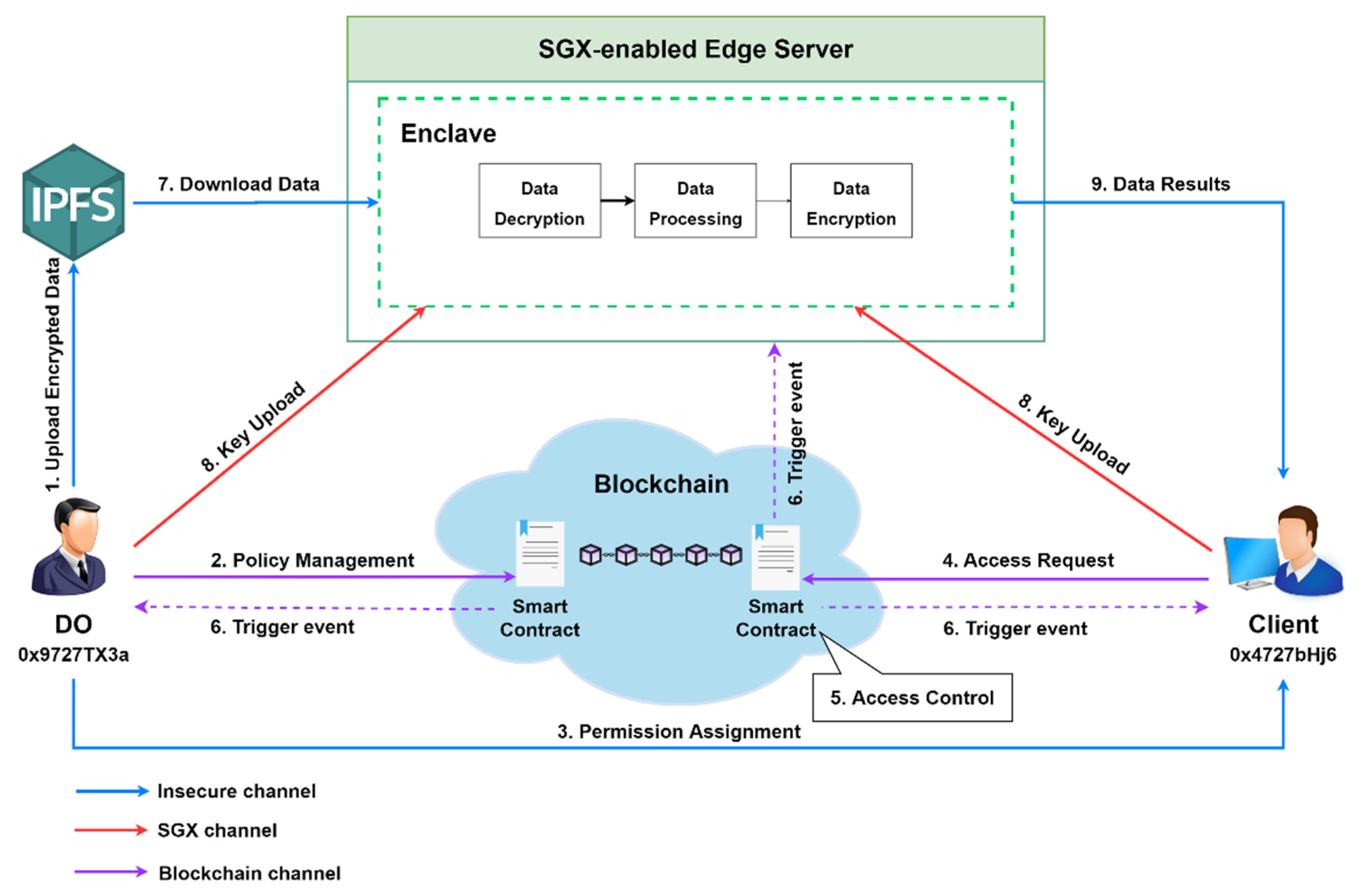
4.1. System Framework
4.2. Access Control of IoT Based on Blockchain
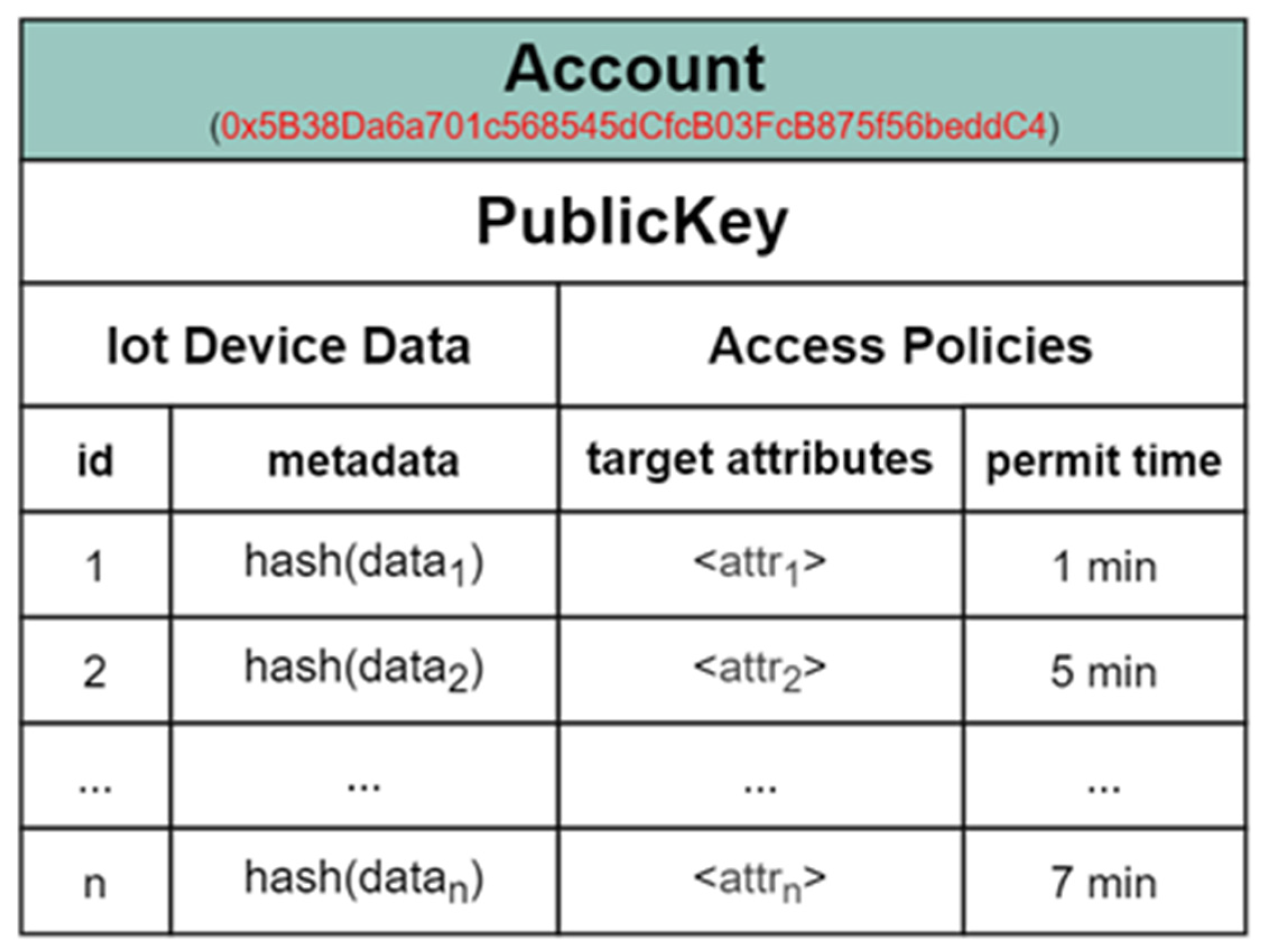
4.2.1. Initialization of Blockchain
4.2.2. Attribute-Based Access Control Contract
- Initialization of the Contract
| Algorithm 1. Initialization of the Contract | |
| 1: | address |
| 2: | enum{, , , } |
| 3: | mapping(=> ) |
| 4: | event ResultEvent(, , ) |
| 5: | mapping( => ) |
| 6: | function Constructor(): ▷only invoked once by |
| 7: | = |
| 8: | end function |
- Management of Access Policy
| Algorithm 2. Management of Access Policy | |
| Input: | : the target data’ID : IPFS address index :the access policy |
| 1: | function AddDataPol(, , ) : ▷only invoked by |
| 2: | policy_all[] = (, ) |
| 3: | end function |
| 4: | function DelDataPol() ▷only invoked by |
| 5: | |
| 6: | end function |
| 7: | function QueryData() ▷only invoked by |
| 8: | (==) |
| 9: | return |
| 10: | end function |
- Assignment of Client Permission
- Access Control
| Algorithm 3. Assignment of Client Permission | |
| Input: | : the target data’ID : the attribute set : a message signed by |
| 1: | function AccessControl(, , ): ▷only invoked by |
| 2: | (==) |
| 3: | if ! = 1: |
| 4: | ResultEvent(, , ) |
| 5: | elif SignVerify(, ) == : |
| 6: | ResultEvent(, , ) |
| 7: | elif PolicyVerify(, ) == : |
| 8: | ResultEvent(, , ) |
| 9: | else: |
| 10: | ResultEvent(, ,,) |
| 11: | end if |
| 12 | end function |
| 13: | function SignVerify(, ): ▷only invoked internally |
| 14: | msgHash = |
| 15: | if == : |
| 16: | return |
| 17: | else |
| 18: | return |
| 19: | end if |
| 20: | end function |
| 21: | function PolicyVerify(, ): ▷only invoked internally |
| 22: | = |
| 23: | if is satisfied by : |
| 24: | return |
| 25: | else |
| 26: | return |
| 27: | end if |
| 28: | end function |
- Deregistration and Recovery of Client
| Algorithm 4. Deregistration of Client | |
| Input: | : the account address |
| 1: | function DeregisterClient() : ▷only invoked by |
| 2: | ++ |
| 3: | end function |
4.3. Trusted Processing of IoT Data Based on SGX-Enabled Edge Computing
5. Performance Evaluation
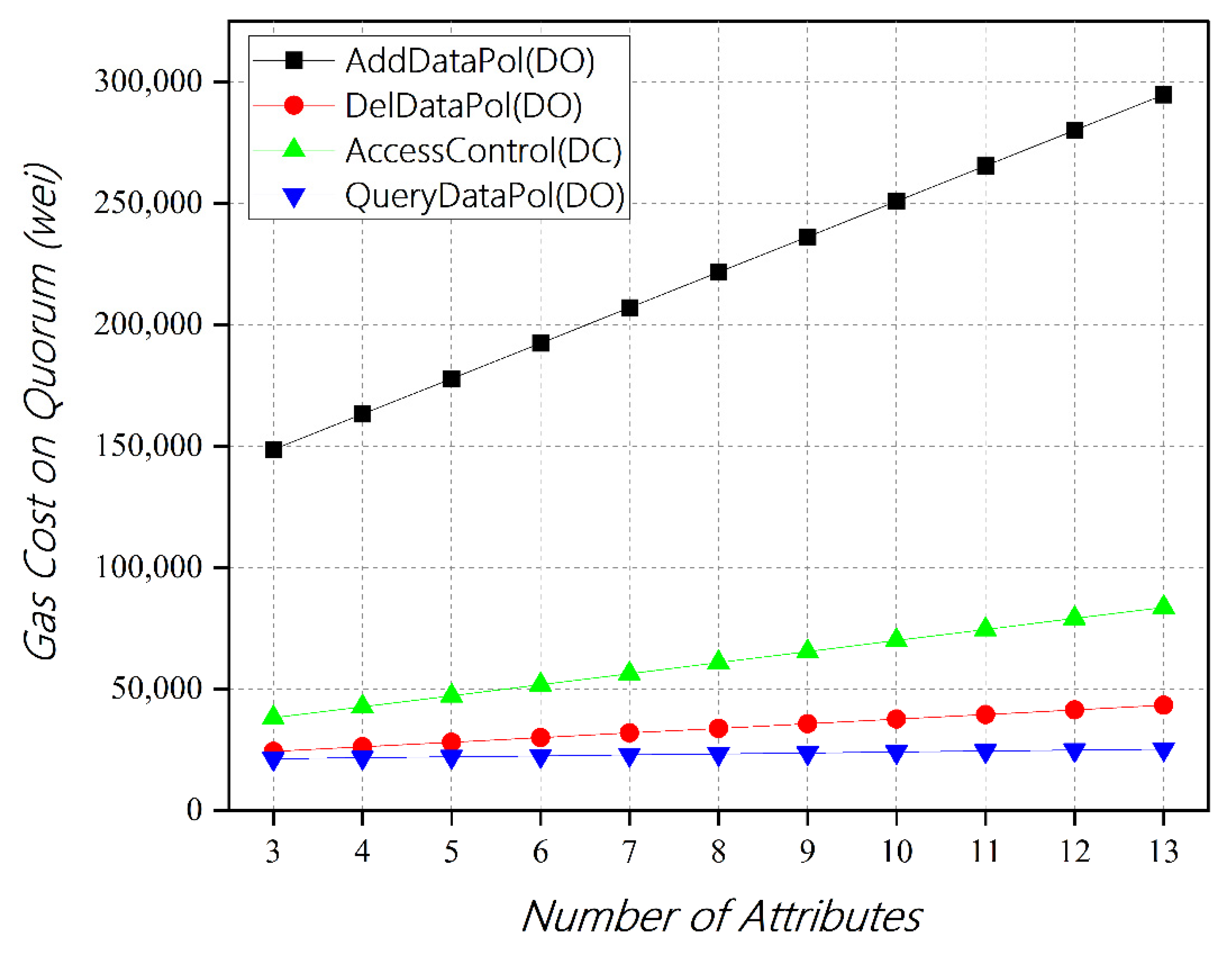
5.1. Performance of Access Control Contract
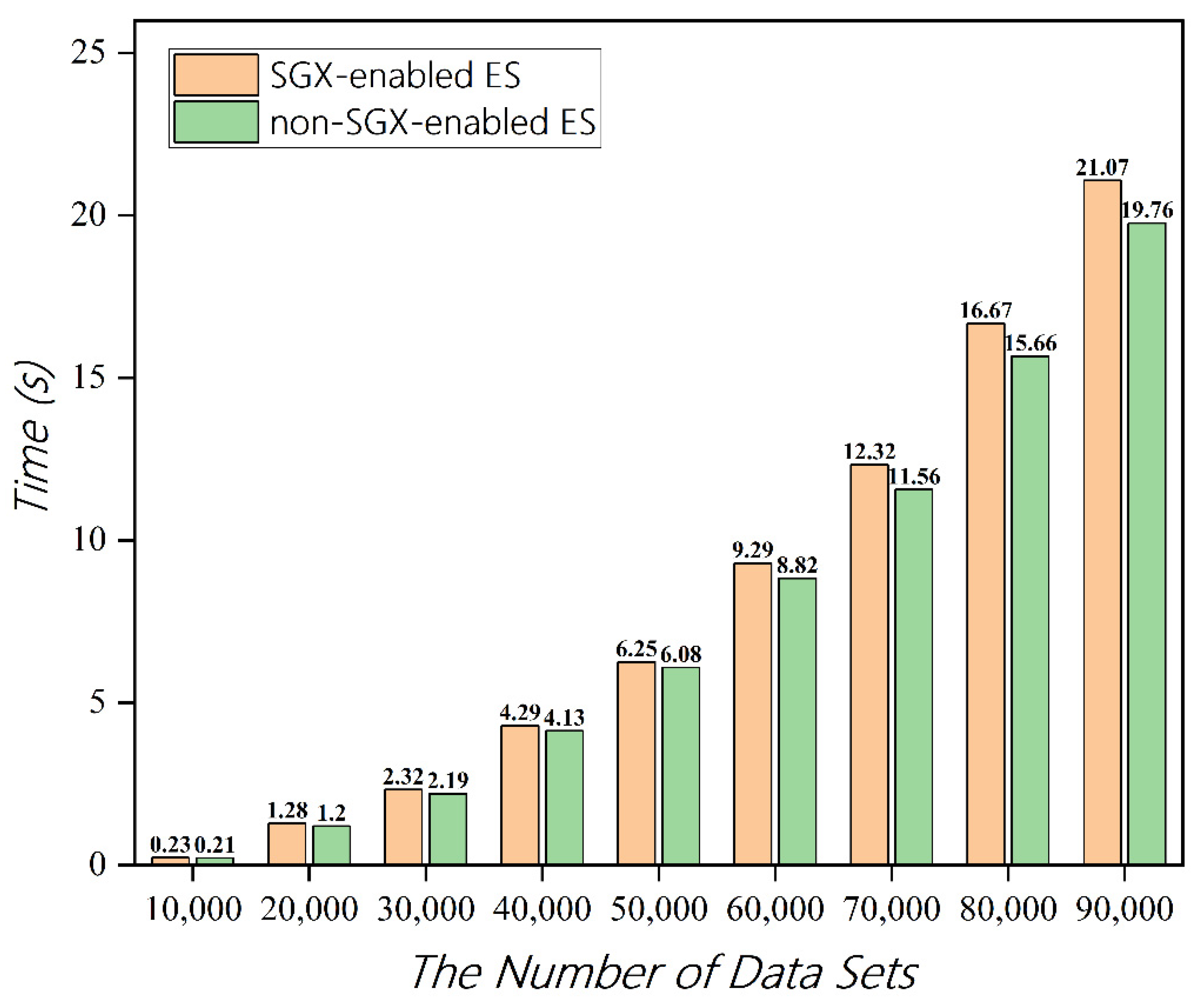
5.2. Performance of Trusted Data Processing Based on SGX
6. Discussion and Limitations
- (1)
- Auditability
- (2)
- Flexibility
- (3)
- Authenticity
- (4)
- IoT Data Confidentiality
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A Qualitative Cross-Comparison of Emerging Technologies for Software-Defined Systems. In Proceedings of the 2019 Sixth International Conference on Software Defined Systems (SDS), Rome, Italy, 10–13 June 2019; pp. 138–145. [Google Scholar] [CrossRef]
- Lionel Sujay Vailshery. IoT Connected Devices Worldwide 2030. Available online: https://www.statista.com/statistics/802690/worldwide-connected-devices-by-access-technology/ (accessed on 22 January 2021).
- Nikolina Cveticanin. 30 Big Data Statistics Everybody’s Talking About. Available online: https://dataprot.net/statistics/data-statistics/ (accessed on 8 March 2022).
- Ning, Z.; Dong, P.; Wang, X.; Hu, X.; Guo, L.; Hu, B.; Guo, Y.; Qiu, T.; Kwok, R.Y.K. Mobile Edge Computing Enabled 5G Health Monitoring for Internet of Medical Things: A Decentralized Game Theoretic Approach. IEEE J. Sel. Areas Commun. 2020, 39, 463–478. [Google Scholar] [CrossRef]
- Kari, P. Dozens sue Amazon’s Ring after Camera Hack Leads to Threats and Racial Slurs. Available online: https://www.theguardian.com/technology/2020/dec/23/amazon-ring-camera-hack-lawsuit-threats (accessed on 23 December 2020).
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Futur. Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Hahn, W. Cynerio Research Finds Critical Medical Device Risks Continue to Threaten Hospital Security and Patient Safety. Available online: https://www.cynerio.com/blog/cynerio-research-finds-critical-medical-device-risks-continue-to-threaten-hospital-security-and-patient-safety (accessed on 19 January 2022).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. [Google Scholar] [CrossRef]
- Hoekstra, M.; Lal, R.; Pappachan, P.; Phegade, V.; Del Cuvillo, J. Using innovative instructions to create trustworthy software solutions. HASP@ISCA 2013, 11, 2487726–2488370. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef]
- Yutaka, M.; Zhang, Y.; Sasabe, M.; Kasahara, S. Using Ethereum Blockchain for Distributed Attribute-Based Access Control in the Internet of Things. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1809.03421. [Google Scholar] [CrossRef]
- Lin, D.; Wu, J.; Yuan, Q.; Zheng, Z. Modeling and Understanding Ethereum Transaction Records via a Complex Network Approach. IEEE Trans. Circuits Syst. II: Express Briefs 2020, 67, 2737–2741. [Google Scholar] [CrossRef]
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. HASP@ISCA 2013, 10, 1–8. [Google Scholar] [CrossRef] [Green Version]
- Anati, I.; Gueron, S.; Johnson, S.; Scarlata, V. Innovative technology for CPU based attestation and sealing. In Proceedings of the Proceedings of the 2nd International Workshop on Hardware and Architectural Support for Security and Privacy; ACM: New York, NY, USA, 2013; Volume 13. [Google Scholar]
- Intel Corporation. Intel Software Guard Extensions. Available online: https://software.intel.com/sgx (accessed on 23 December 2020).
- Sandhu, R.; Samarati, P. Access control: Principle and practice. IEEE Commun. Mag. 1994, 32, 40–48. [Google Scholar] [CrossRef]
- Sandhu, R.S. Role-based Access Control. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 1998; Volume 46, pp. 237–286. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F. Attribute-Based Access Control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Yang, W.; Liu, W.; Wei, X.; Guo, Z.; Yang, K.; Huang, H.; Qi, L. EdgeKeeper: A trusted edge computing framework for ubiquitous power Internet of Things. Front. Inf. Technol. Electron. Eng. 2021, 22, 374–399. [Google Scholar] [CrossRef]
- Li, X.; Li, D.; Wan, J.; Liu, C.; Imran, M. Adaptive Transmission Optimization in SDN-Based Industrial Internet of Things with Edge Computing. IEEE Internet Things J. 2018, 5, 1351–1360. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, N.; Zhang, Y.; Chen, X.; Wu, W.; Shen, X.S. Energy Efficient Dynamic Offloading in Mobile Edge Computing for Internet of Things. IEEE Trans. Cloud Comput. 2019, 9, 1050–1060. [Google Scholar] [CrossRef]
- Xu, S.; Li, Y.; Deng, R.H.; Zhang, Y.; Luo, X.; Liu, X. Lightweight and Expressive Fine-Grained Access Control for Healthcare Internet-of-Things. IEEE Trans. Cloud Comput. 2019, 10, 474–490. [Google Scholar] [CrossRef]
- Alkhresheh, A.; Elgazzar, K.; Hassanein, H.S. DACIoT: Dynamic Access Control Framework for IoT Deployments. IEEE Internet Things J. 2020, 7, 11401–11419. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Varadharajan, V.; Rabehaja, T. Policy-based access control for constrained healthcare resources in the context of the Internet of Things. J. Netw. Comput. Appl. 2019, 139, 57–74. [Google Scholar] [CrossRef]
- Mahmood, Z.; Jusas, V. Blockchain-Enabled: Multi-Layered Security Federated Learning Platform for Preserving Data Privacy. Electronics 2022, 11, 1624. [Google Scholar] [CrossRef]
- Han, J.; Li, Z.; Liu, J.; Wang, H.; Xian, M.; Zhang, Y.; Chen, Y. Attribute-Based Access Control Meets Blockchain-Enabled Searchable Encryption: A Flexible and Privacy-Preserving Framework for Multi-User Search. Electronics 2022, 11, 2536. [Google Scholar] [CrossRef]
- Barenji, A.V.; Montreuil, B. Open Logistics: Blockchain-Enabled Trusted Hyperconnected Logistics Platform. Sensors 2022, 22, 4699. [Google Scholar] [CrossRef]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Harnessing the power of blockchain technology to solve IoT security & privacy issues. In Proceedings of the Second International Conference on Internet of Things, Data and Cloud Computing, Cambridge, UK, 22–23 March 2017; Volume 7. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Alansari, S.; Paci, F.; Sassone, V. A Distributed Access Control System for Cloud Federations. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2131–2136. [Google Scholar] [CrossRef]
- Maesa, D.D.F.; Mori, P.; Ricci, L. Blockchain Based Access Control. In Proceedings of the IFIP International Conference on Distributed Applications and Interoperable Systems; Springer: Berlin/Heidelberg, Germany, 2017; pp. 206–220. [Google Scholar] [CrossRef]
- Li, Z.; Hao, J.; Liu, J.; Wang, H.; Xian, M. An IoT-Applicable Access Control Model Under Double-Layer Blockchain. IEEE Trans. Circuits Syst. II: Express Briefs 2020, 68, 2102–2106. [Google Scholar] [CrossRef]
- Park, M.; Kim, J.; Kim, Y.; Cho, E.; Park, S.; Sohn, S.; Kang, M.; Kwon, T. An SGX-Based Key Management Framework for Data Centric Networking. In Proceedings of the International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2019; pp. 370–382. [Google Scholar] [CrossRef]
- Gao, Y.; Lin, H.; Chen, Y.; Liu, Y. Blockchain and SGX-Enabled Edge-Computing-Empowered Secure IoMT Data Analysis. IEEE Internet Things J. 2021, 8, 15785–15795. [Google Scholar] [CrossRef]
- Ayoade, G.; El-Ghamry, A.; Karande, V.; Khan, L.; Alrahmawy, M.; Rashad, M.Z. Secure data processing for IoT middleware systems. J. Supercomput. 2018, 75, 4684–4709. [Google Scholar] [CrossRef]
- Górski, T. The 1+5 Architectural Views Model in Designing Blockchain and IT System Integration Solutions. Symmetry 2021, 13, 2000. [Google Scholar] [CrossRef]
- Tran, N.K.; Babar, M.A.; Walters, A. A Framework for Automating Deployment and Evaluation of Blockchain Network. arXiv 2020, arXiv:2203.10647. [Google Scholar] [CrossRef]
- Górski, T. Continuous Delivery of Blockchain Distributed Applications. Sensors 2021, 22, 128. [Google Scholar] [CrossRef] [PubMed]


| Schemes | Basic Framework | Enable Blockchain | Enable SGX | Decision Maker |
|---|---|---|---|---|
| Xu [24] | ABAC | NO | NO | Edge Server |
| Zhang [10] | ACL | YES (Ethereum) | NO | Smart contract |
| Yutaka [11] | ABAC | YES (Ethereum) | NO | Smart contract |
| Gao [36] | ACL | YES (Hyperledger Fabric) | YES | Edge Server |
| Ours | ABAC | YES(Quorum) | YES | Smart contract |
| Name | Extended UML Element |
|---|---|
| Node | |
| Node | |
| Node | |
| Node | |
| Node | |
| Artifact | |
| Artifact | |
| Artifact | |
| Artifact | |
| Artifact | |
| Generic Connection | |
| Generic Connection | |
| Generic Connection | |
| Generic Connection |
| Notation | Description |
|---|---|
| The data owner | |
| Data owner’s account address | |
| The client | |
| Client’s account address | |
| The IoT device | |
| IoT device’s account address | |
| Attributes of the client | |
| Access policy | |
| Sign data with the data owner’s public key | |
| A label bound to the client deregister | |
| The ID of IoT data | |
| Encryption key of the data owner | |
| Encryption key of the client | |
| DH shared secret key between enclaves | |
| Data process program |
| Scheme | Deploying Contracts | Adding Attributes | Adding a Policy | Access Control | Total |
|---|---|---|---|---|---|
| [10] | 1,706,290 | - | 128,777 | 75,771 | 1,910,838 |
| [11] | 1,301,972 | 308,109 | 363,964 | 264,635 | 2,238,680 |
| ours | 871,268 | - | 163,284 | 42,764 | 1,077,316 |
| Scheme | Deploying Contracts | Access Control |
|---|---|---|
| [10] | ≈1 min | ≈30 s |
| [11] | ≈80 s | ≈36 s |
| Ours | ≈33 s | ≈2 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, J.; Zhang, Y.; Liu, J.; Li, Z.; Xian, M.; Wang, H.; Mao, F.; Chen, Y. A Blockchain-Based and SGX-Enabled Access Control Framework for IoT. Electronics 2022, 11, 2710. https://doi.org/10.3390/electronics11172710
Han J, Zhang Y, Liu J, Li Z, Xian M, Wang H, Mao F, Chen Y. A Blockchain-Based and SGX-Enabled Access Control Framework for IoT. Electronics. 2022; 11(17):2710. https://doi.org/10.3390/electronics11172710
Chicago/Turabian StyleHan, Jiujiang, Yuxiang Zhang, Jian Liu, Ziyuan Li, Ming Xian, Huimei Wang, Feilong Mao, and Yu Chen. 2022. "A Blockchain-Based and SGX-Enabled Access Control Framework for IoT" Electronics 11, no. 17: 2710. https://doi.org/10.3390/electronics11172710
APA StyleHan, J., Zhang, Y., Liu, J., Li, Z., Xian, M., Wang, H., Mao, F., & Chen, Y. (2022). A Blockchain-Based and SGX-Enabled Access Control Framework for IoT. Electronics, 11(17), 2710. https://doi.org/10.3390/electronics11172710






