Empirical Analysis of Extended QX-MAC for IOT-Based WSNS
Abstract
:1. Introduction
- We identify several malfunctions in the original X-MAC design and propose alternative solutions to them.
- We model and simulate the extended QX-MAC protocol that integrates the proposed solutions to X-MAC design flaws as well as incorporates data acknowledgment and retransmission mechanisms to resolve the reliability issue of X-MAC.
- We perform an in-depth empirical analysis of the extended QX-MAC protocol compared with other reference MAC protocols considering two different communication models: single-hop scenario and multi-hop scenario.
- We emphasize QX-MAC performance gains in terms of energy consumption, and QoS metrics, such as packet loss, end-to-end packet delivery delay, and throughput.
2. Design Considerations for WSN MAC Protocols
2.1. Energy Efficiency
2.2. Traffic Adaptivity
2.3. Delay
2.4. Throughput
2.5. Reliability
3. Related Work
4. The QX-MAC Protocol
4.1. Problem Formulation
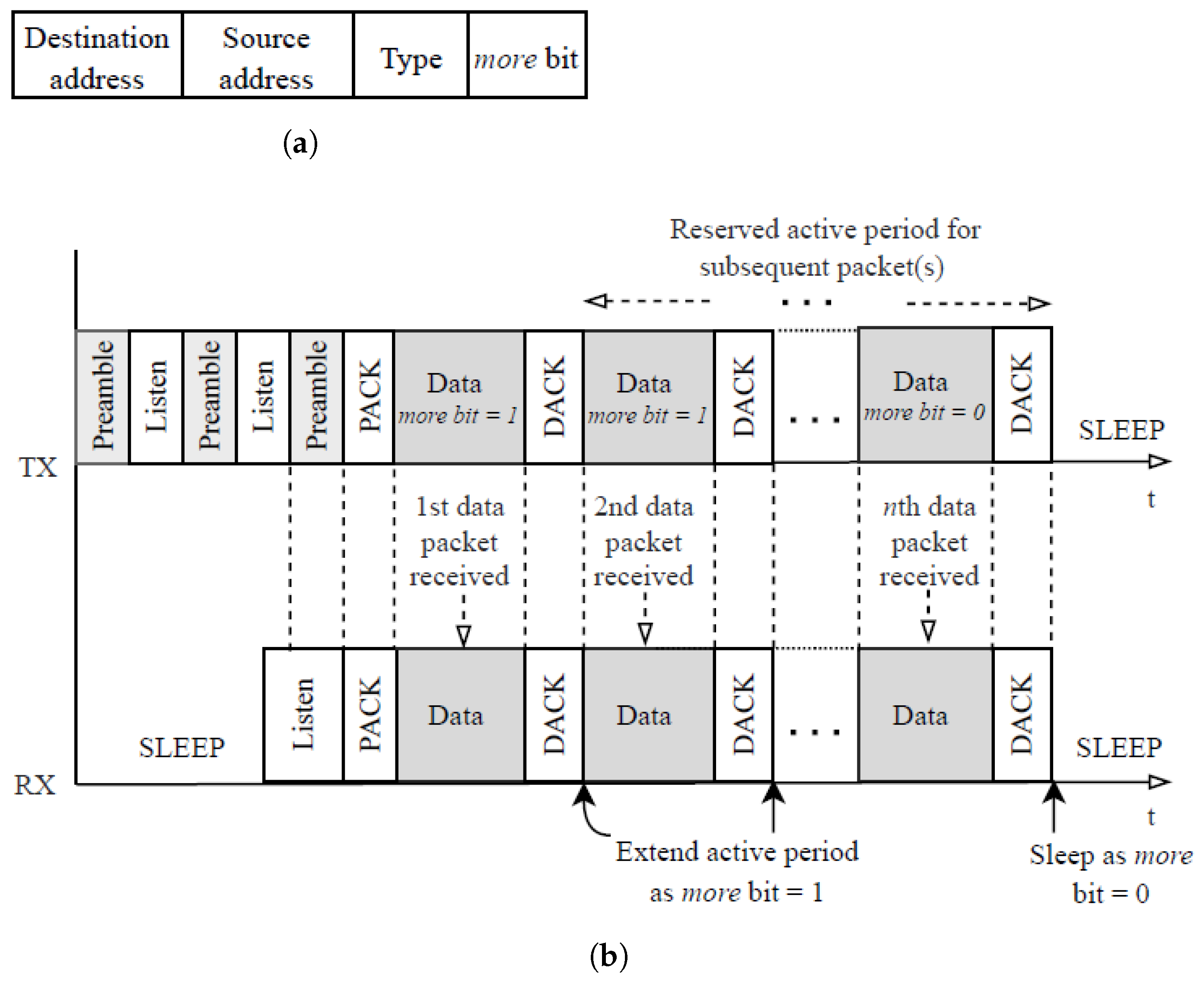
- High overhead and latencyOne problem associated with X-MAC is that it incurs high per-packet overhead and extra delay under heavy traffic conditions. This problem mainly arises because X-MAC operates only in unsynchronized state where the intended receiver returns to sleep after receiving each data packet irrespective of whether its most recent sender has more packets destined to it or not. In X-MAC, for each data packet transmission, the sender follows the state transition cycle:CCA➝SEND_PREAMBLE➝SEND_DATA➝WAIT_TX_DATA_OVER➝SLEEP; and the target receiver follows the cycle:CCA➝SEND_ACK➝WAIT_ACK_TX➝WAIT_DATA➝SLEEP.Since the receiver switches to sleep mode upon receiving a data packet, the same operational cycle is repeated for transmitting each data packet even after the sender has more packets in its queue for the same receiver. This way, resources in terms of energy and time are consumed in transmitting preamble bursts to transfer the subsequent data packet(s).QX-MAC addresses this issue by implementing an adaptive duty-cycled technique where the sender reserves its active period based on its queue status using Q-learning and the receiver adjusts its duty cycle following the more bit scheme.
- Reliability issueX-MAC does not implement data acknowledgments. Therefore, a sending node is not aware of whether a transmitted frame has been received successfully.QX-MAC ensures reliability by incorporating data acknowledgments and retransmissions.
- Other flaws in X-MAC design
4.2. Flaws in X-MAC Design
4.2.1. Preambles from Multiple Senders
4.2.2. Preambles End without Being Acknowledged
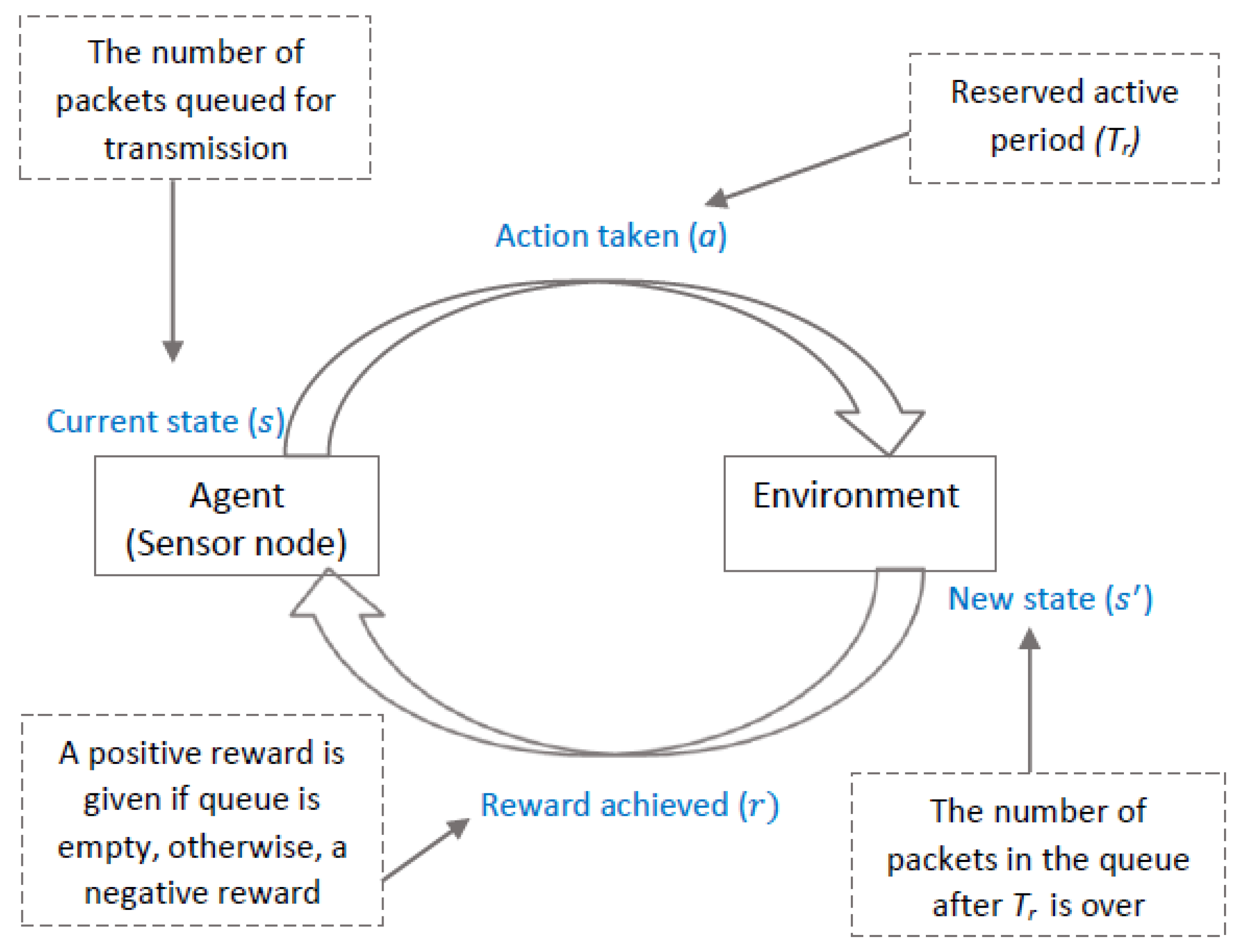
4.3. Q-Learning
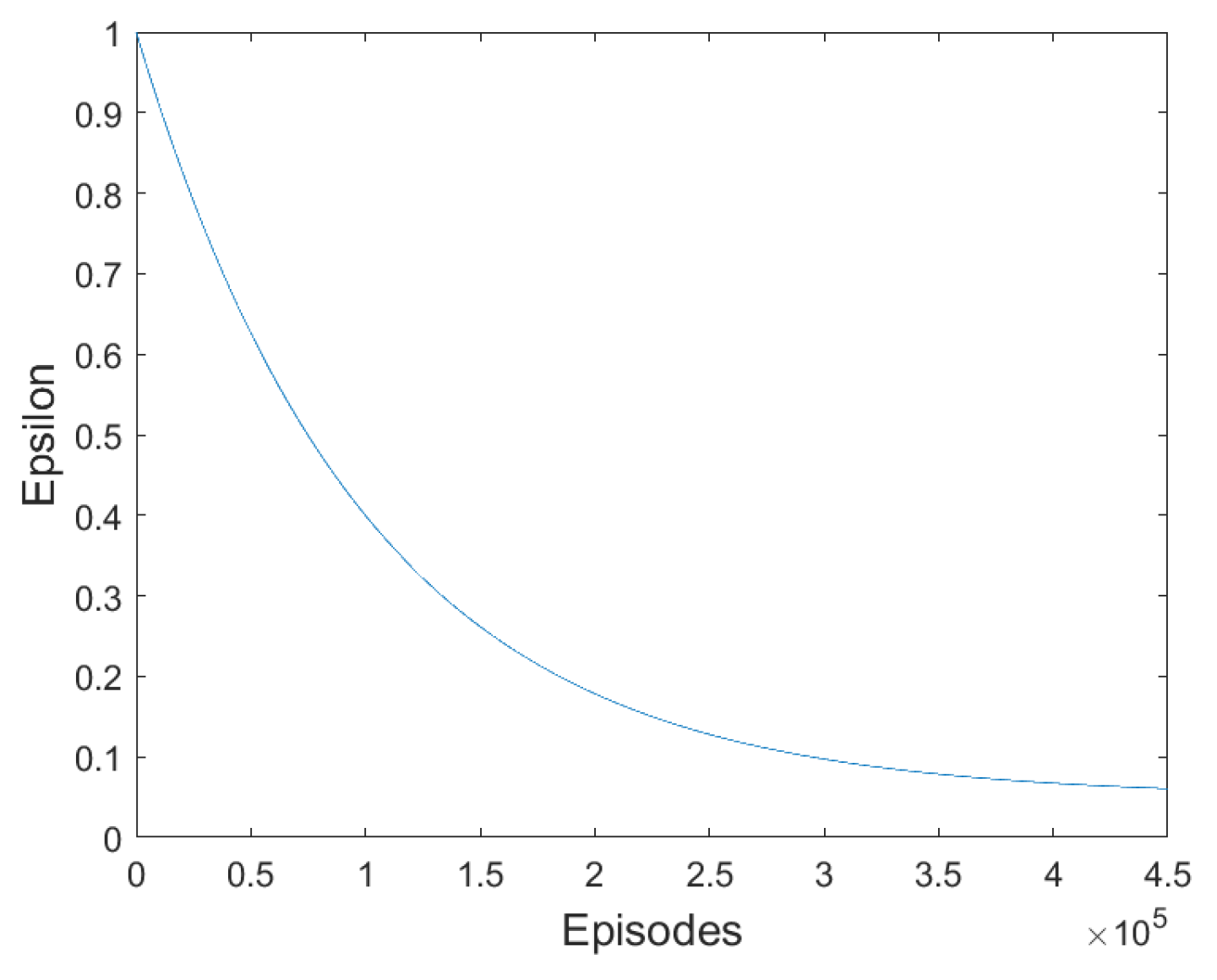
Epsilon-Greedy Method
4.4. QX-MAC Operation
QX-MAC Energy Consumption
5. Simulation Results and Analysis
5.1. Single-Hop Scenario
5.1.1. Effects of Packet Arrival Rate
Packet Loss
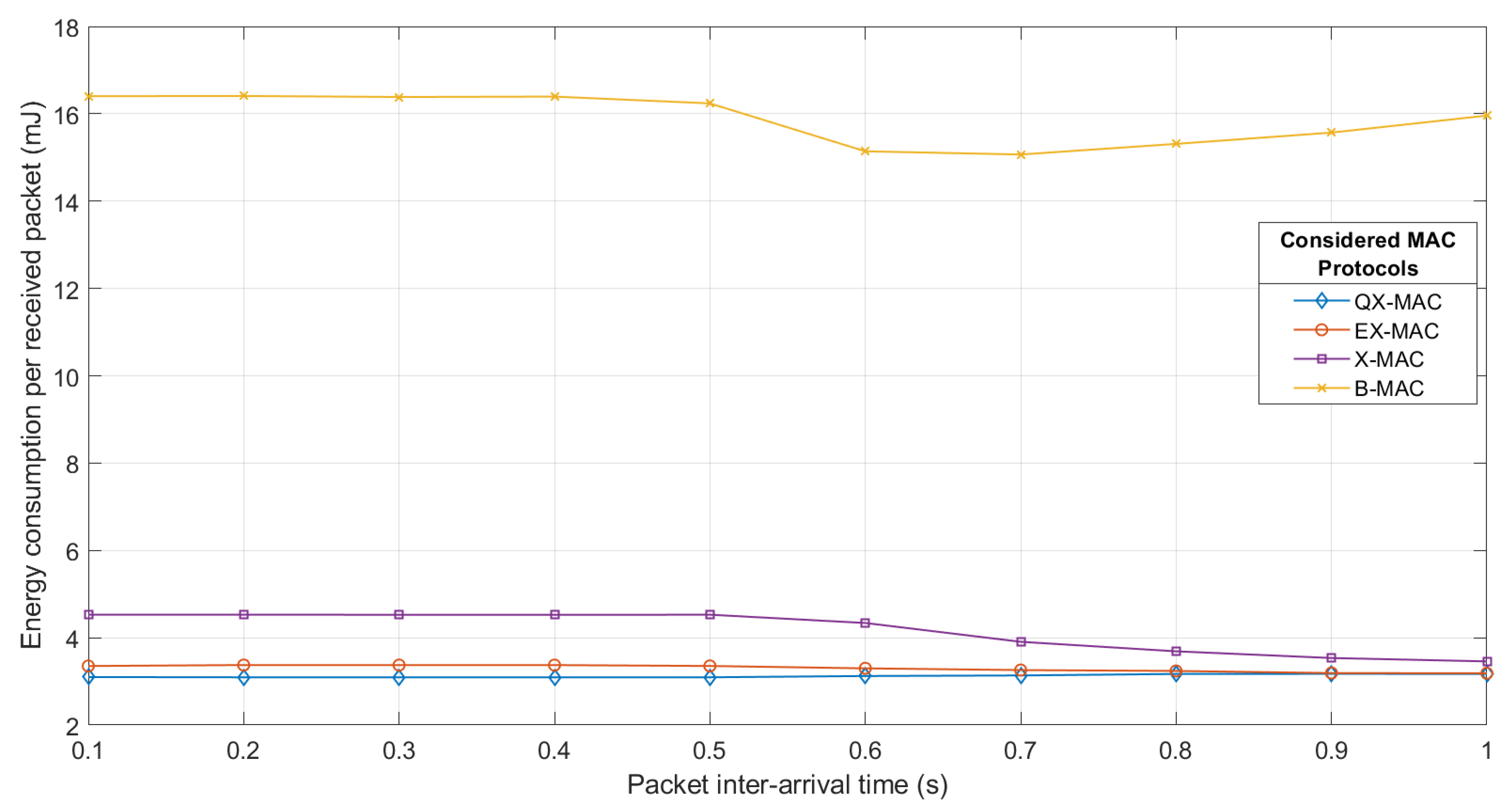
Energy Consumption
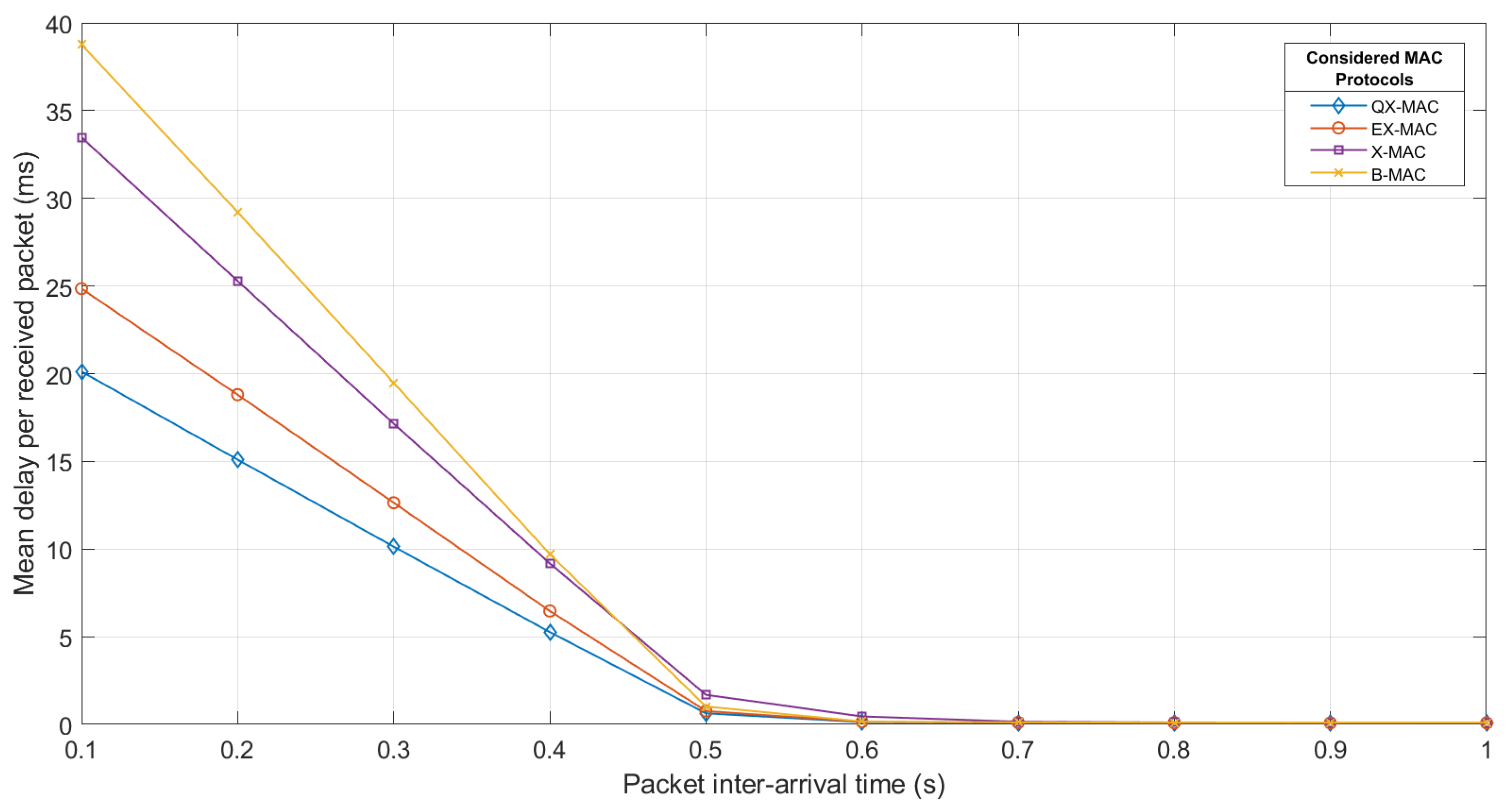
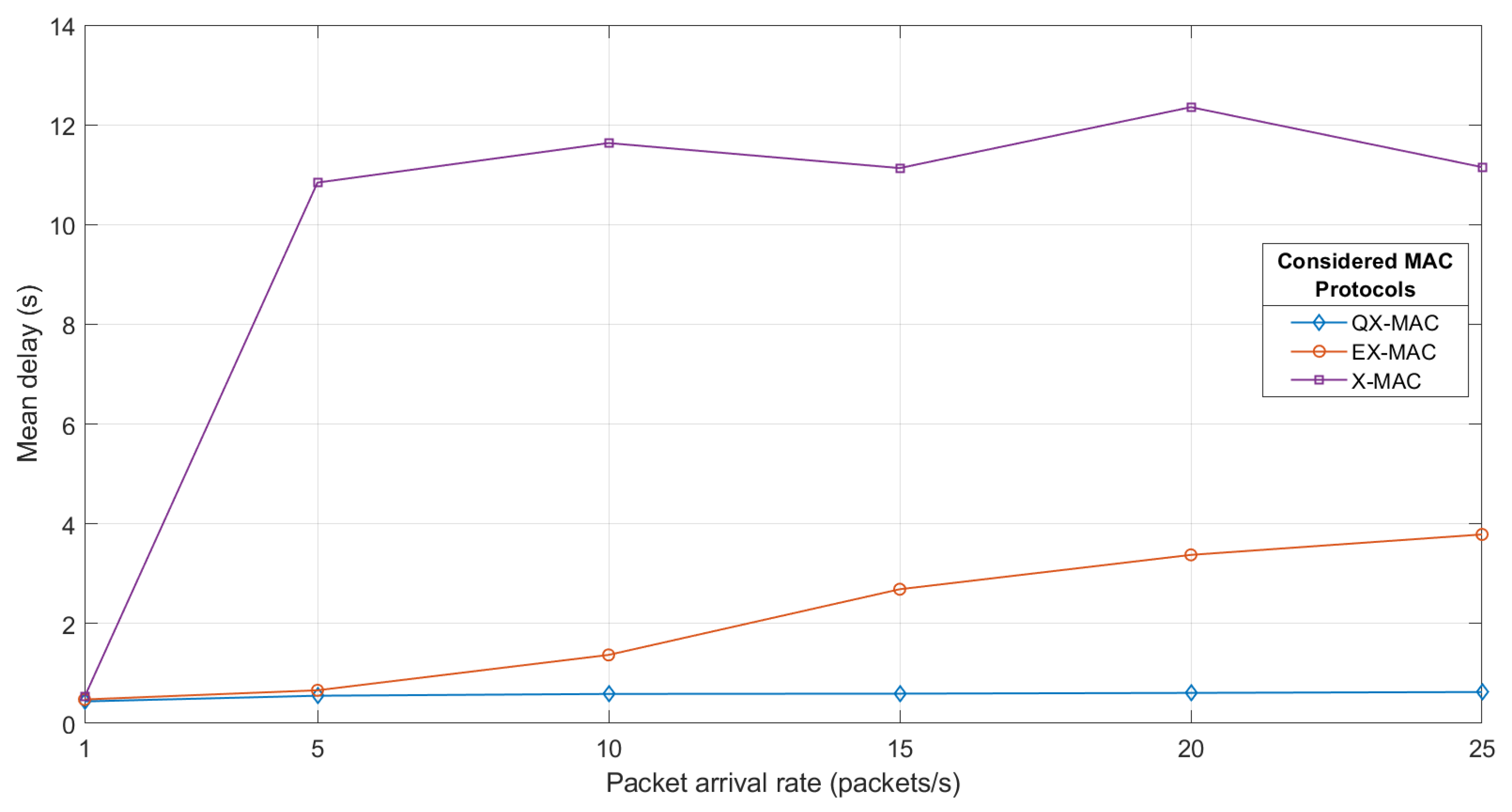
Delay
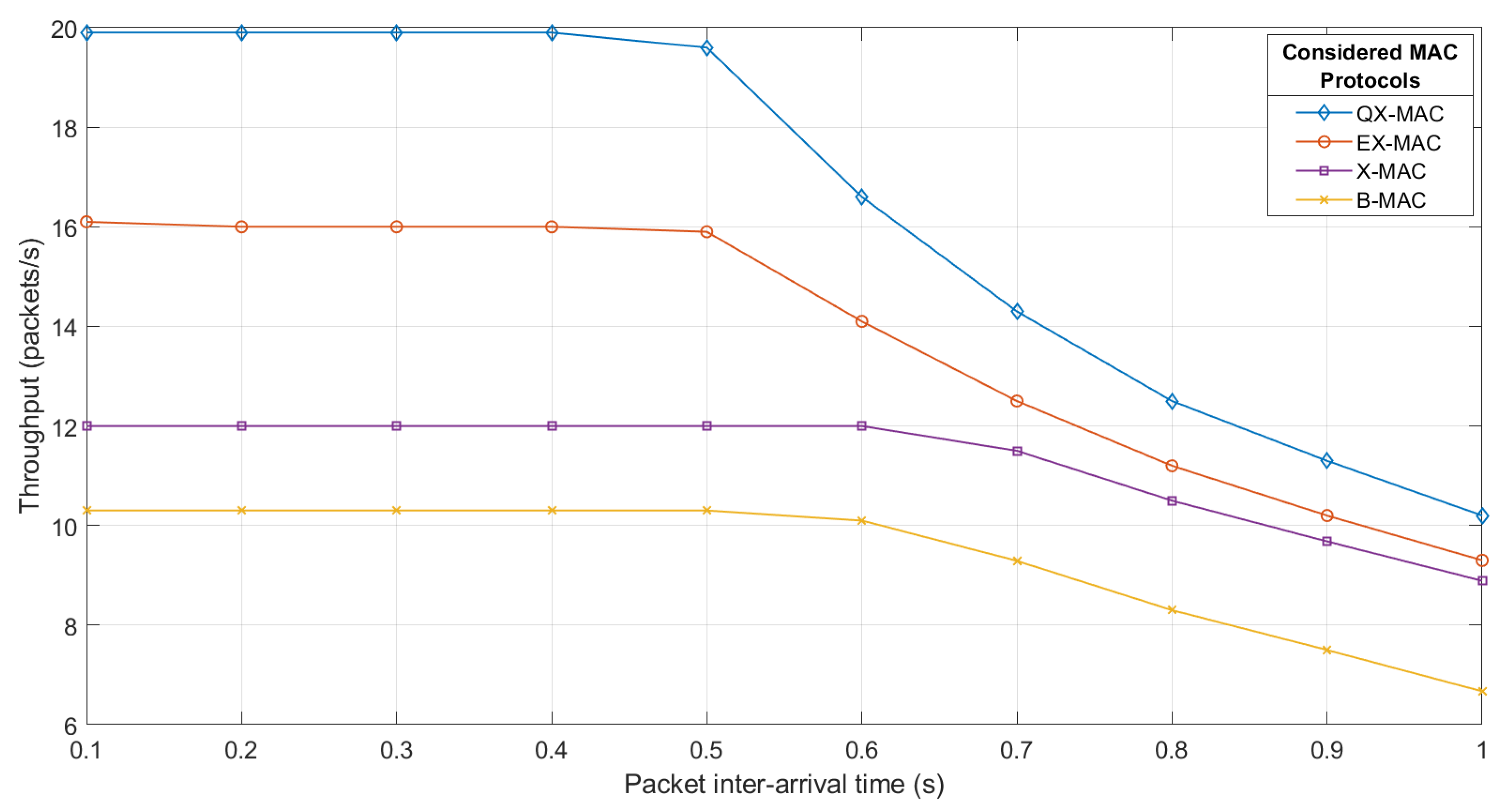
Throughput
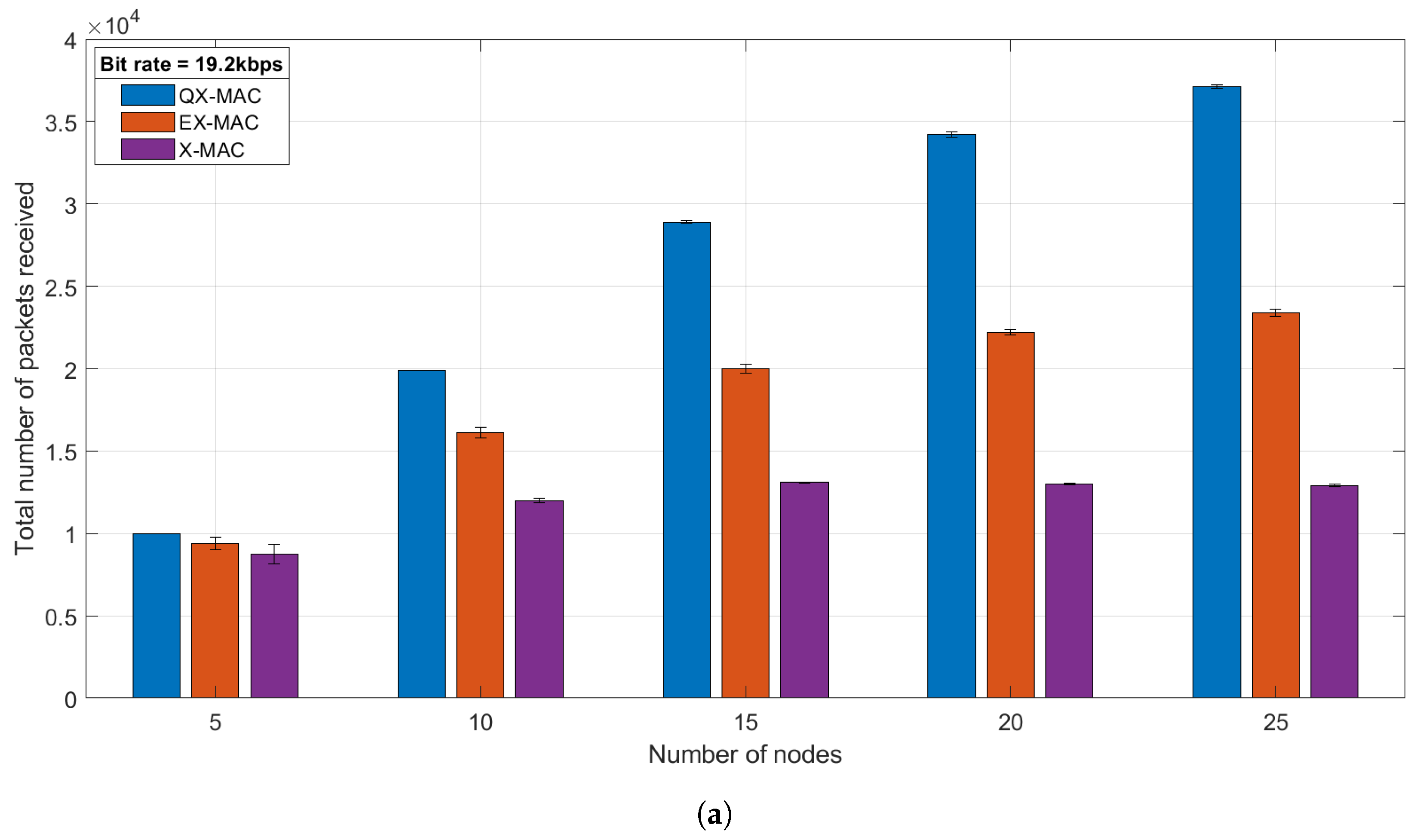
5.1.2. Effects of Number of Nodes
Packet Loss
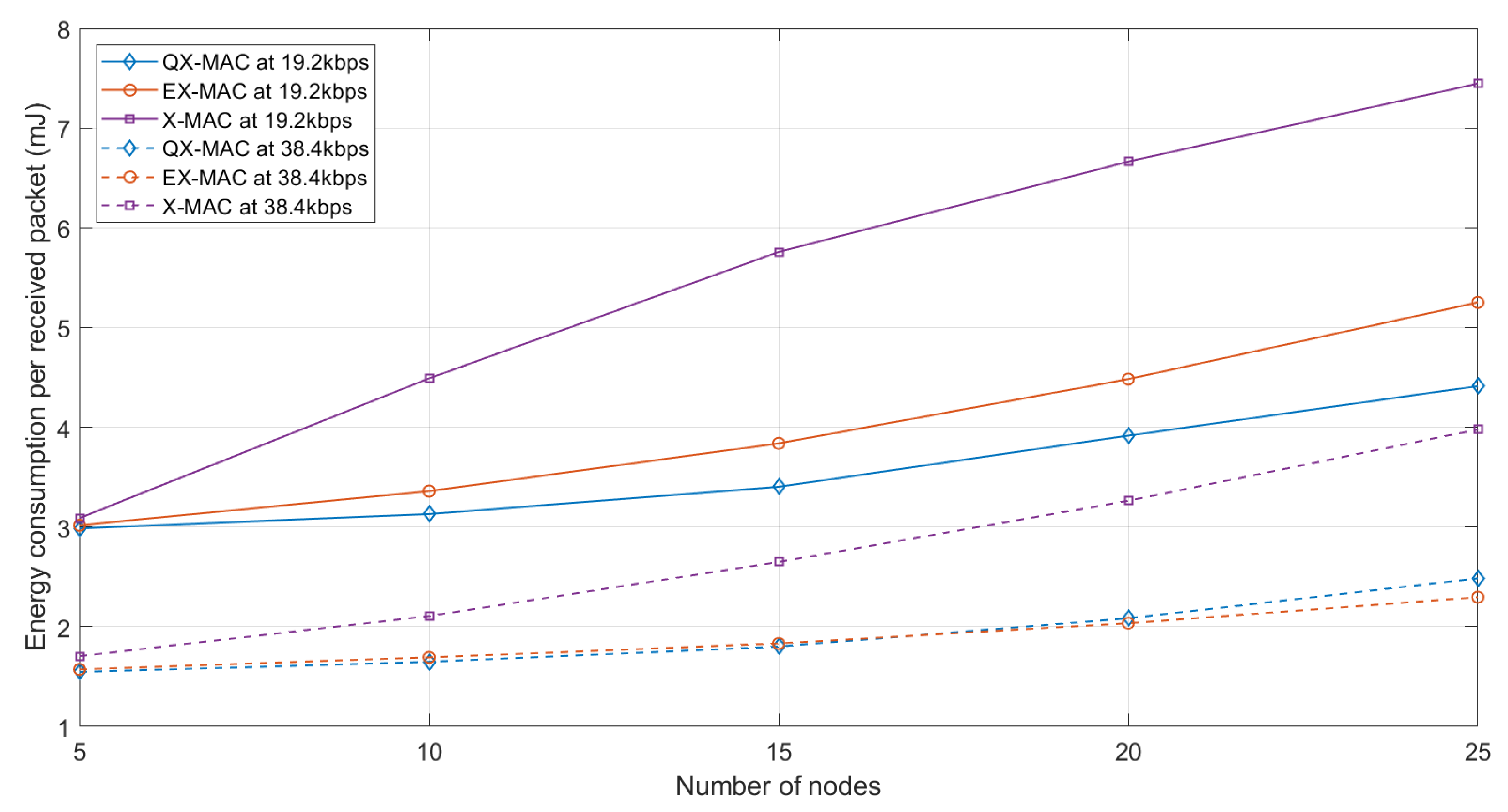
Energy Consumption
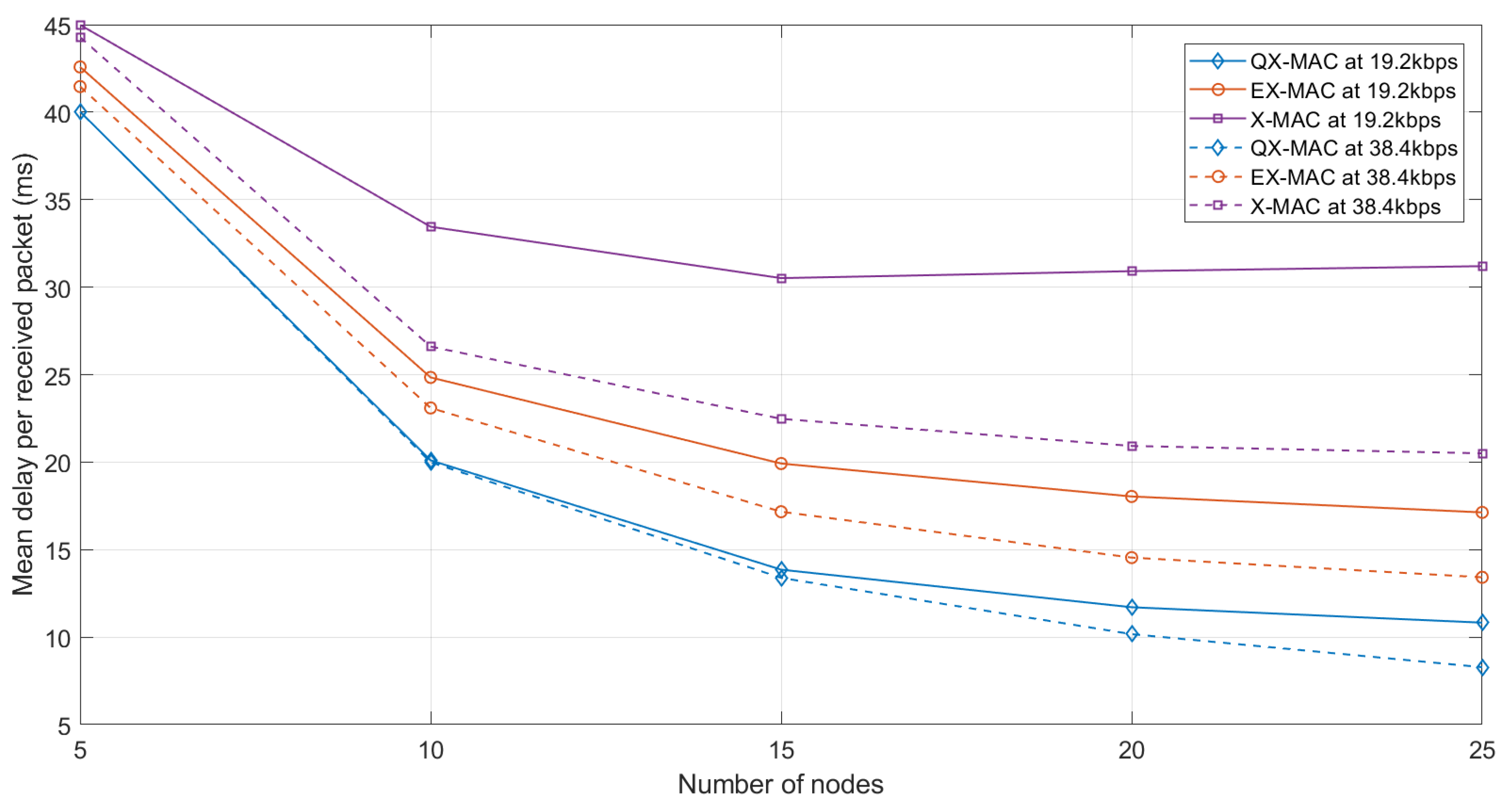
Delay
Throughput
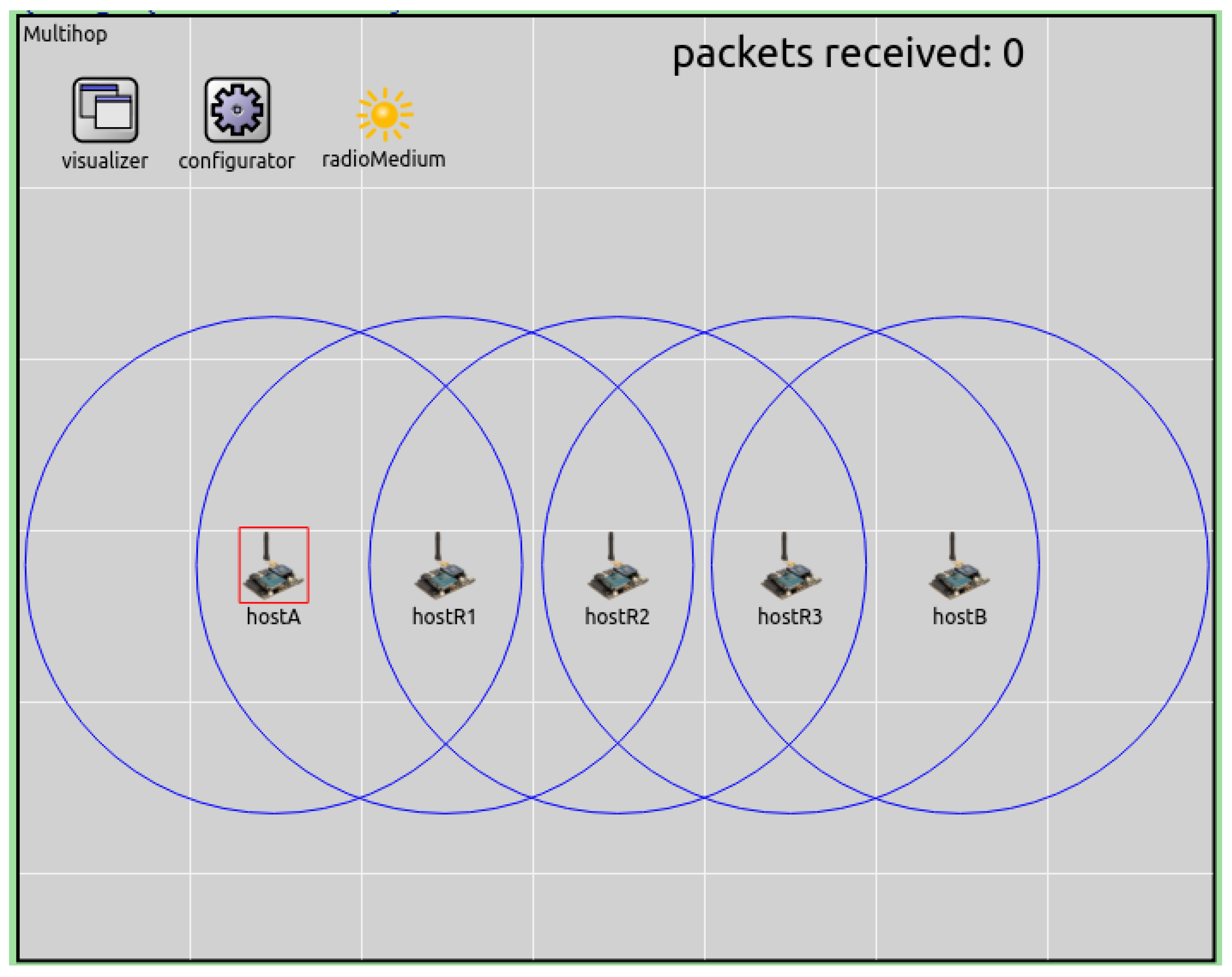
5.2. Multi-Hop Scenario
5.3. QoS and Energy Performance
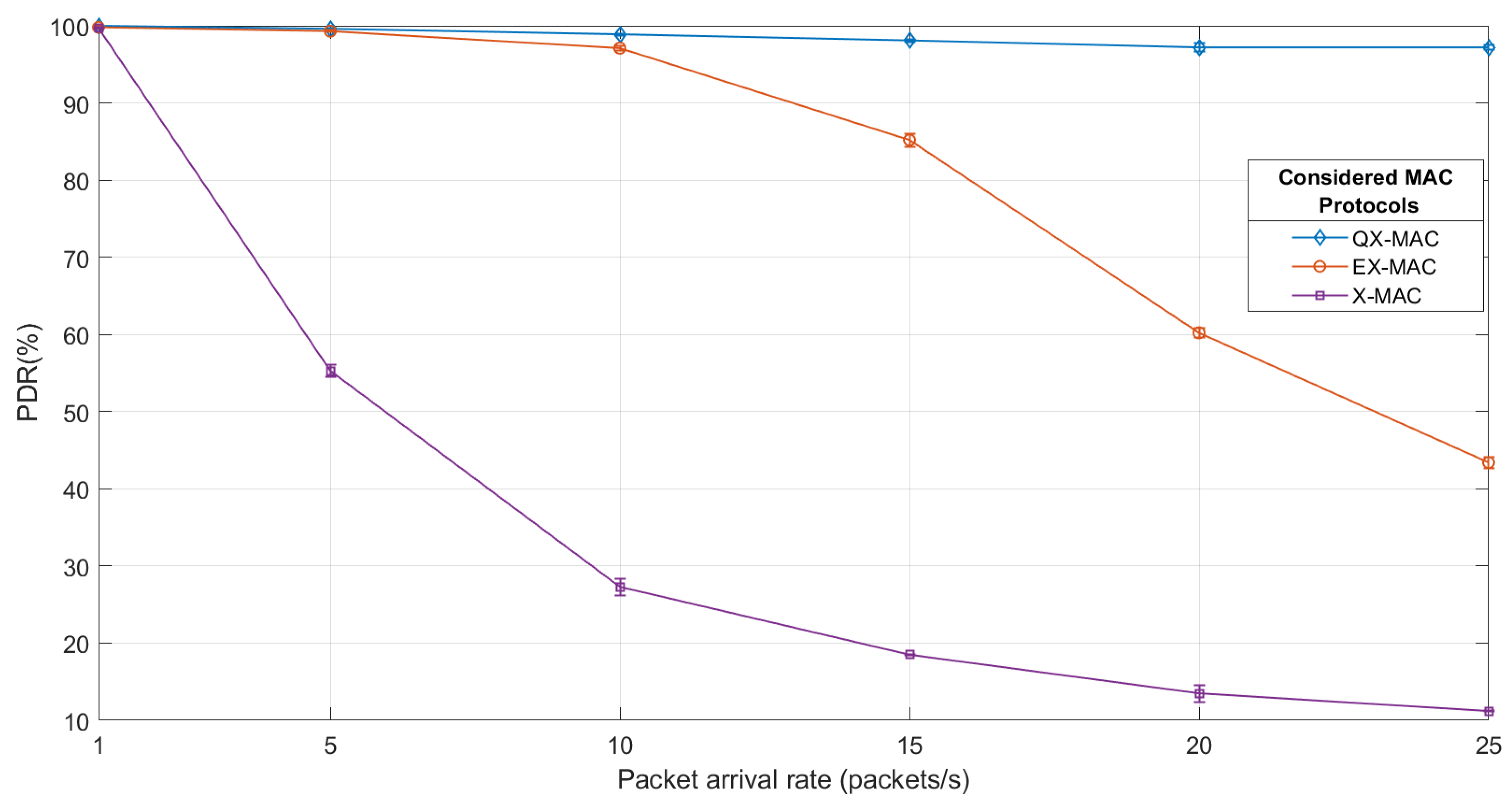
5.3.1. Packet Delivery Ratio (PDR)
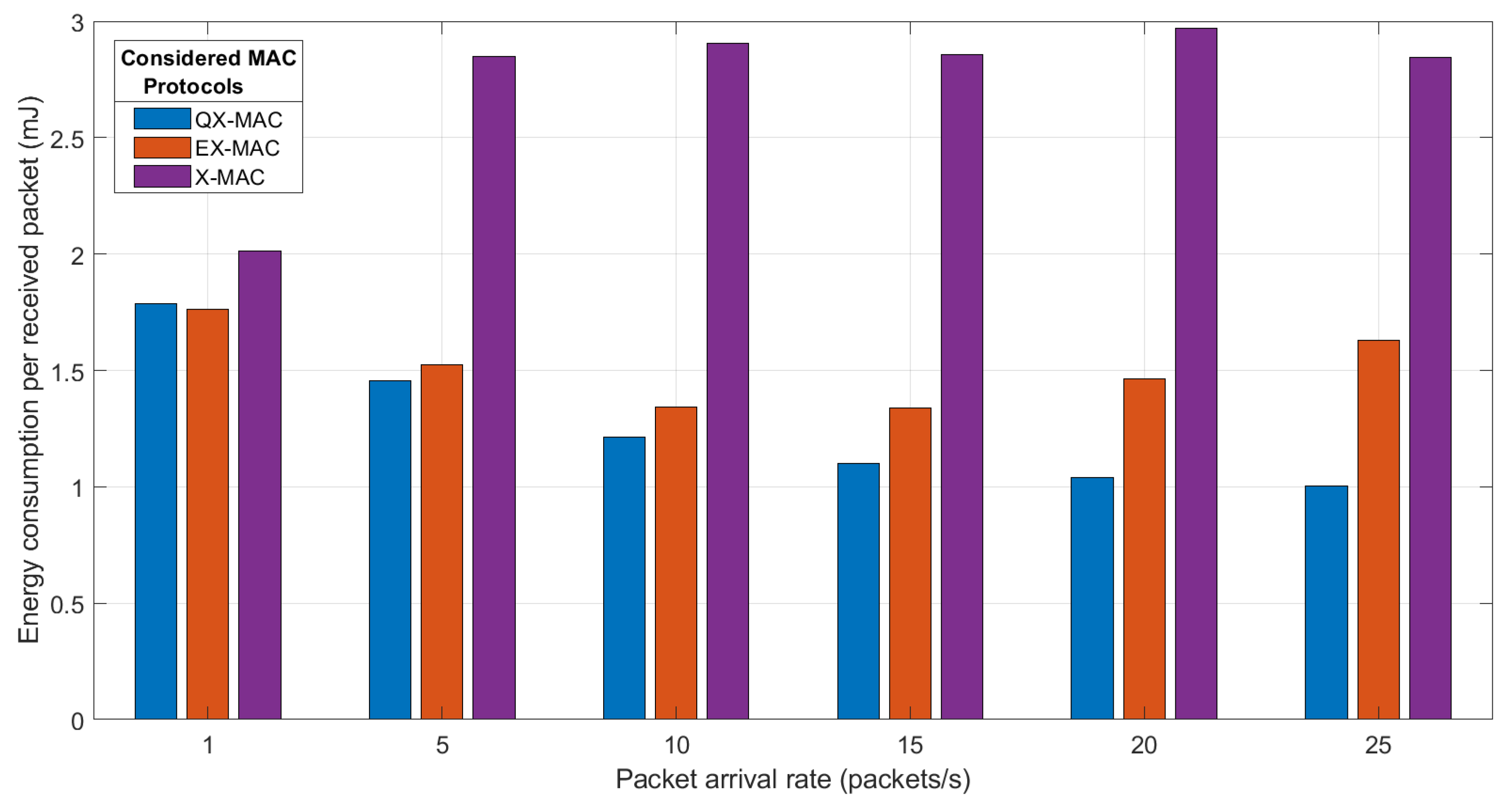
5.3.2. Energy Consumption
5.3.3. Delay
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A

References
- Internet of Things: Wireless Sensor Networks. Available online: https://www.iec.ch/basecamp/internet-things-wireless-sensor-networks (accessed on 20 December 2021).
- Matin, M.A.; Islam, M.M. Overview of wireless sensor network. In Wireless Sensor Networks-Technology and Protocols; Matin, M.A., Ed.; IntechOpen: Rijeka, Croatia, 2012. [Google Scholar]
- Guo, F.; Yu, F.R.; Zhang, H.; Li, X.; Ji, H.; Leung, V.C. Enabling massive IoT toward 6G: A comprehensive survey. IEEE Internet Things J. 2021, 8, 11891–11915. [Google Scholar] [CrossRef]
- Kumar, A.; Zhao, M.; Wong, K.J.; Guan, Y.L.; Chong, P.H.J. A comprehensive study of IoT and WSN MAC protocols: Research issues, challenges and opportunities. IEEE Access 2018, 6, 76228–76262. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Beaudaux, J.; Gallais, A.; Montavont, J.; Noel, T.; Roth, D.; Valentin, E. Thorough empirical analysis of X-MAC over a large scale internet of things testbed. IEEE Sens. J. 2013, 14, 383–392. [Google Scholar] [CrossRef]
- Oller, J.; Demirkol, I.; Casademont, J.; Paradells, J.; Gamm, G.U.; Reindl, L. Has Time Come to Switch from Duty-Cycled MAC Protocols to Wake-Up Radio for Wireless Sensor Networks? IEEE/ACM Trans. Netw. 2016, 24, 674–687. [Google Scholar] [CrossRef]
- Ye, W.; Heidemann, J.; Estrin, D. An energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 23–27 June 2002; Volume 3, pp. 1567–1576. [Google Scholar]
- Van Dam, T.; Langendoen, K. An adaptive energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 171–180. [Google Scholar]
- Lu, G.; Krishnamachari, B.; Raghavendra, C.S. An adaptive energy-efficient and low-latency MAC for data gathering in wireless sensor networks. In Proceedings of the 18th International Parallel and Distributed Processing Symposium, Santa Fe, NM, USA, 26–30 April 2004; pp. 224–231. [Google Scholar]
- Polastre, J.; Hill, J.; Culler, D. Versatile low power media access for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 95–107. [Google Scholar]
- El-Hoiydi, A.; Decotignie, J.D. Low power downlink MAC protocols for infrastructure wireless sensor networks. Mob. Netw. Appl. 2005, 10, 675–690. [Google Scholar] [CrossRef]
- Buettner, M.; Yee, G.V.; Anderson, E.; Han, R. X-MAC: A short preamble MAC protocol for duty-cycled wireless sensor networks. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems, Boulder, CO, USA, 31 October–3 November 2006; pp. 307–320. [Google Scholar]
- Afroz, F.; Braun, R.; Chaczko, Z. XX-MAC and EX-MAC: Two Variants of X-MAC Protocol for Low Power Wireless Sensor Networks. Adhoc Sens. Wirel. Netw. 2022, 51, 285–314. [Google Scholar]
- Afroz, F.; Braun, R. QX-MAC: Improving QoS and Energy Performance of IoT-based WSNs using Q-Learning. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4–7 October 2021; pp. 455–462. [Google Scholar]
- Anwander, M.; Wagenknecht, G.; Braun, T.; Dolfus, K. Beam: A burst-aware energy-efficient adaptive mac protocol for wireless sensor networks. In Proceedings of the 2010 Seventh International Conference on Networked Sensing Systems (INSS), Kassel, Germany, 15–18 June 2010; pp. 195–202. [Google Scholar]
- Yigitel, M.A.; Incel, O.D.; Ersoy, C. QoS-aware MAC protocols for wireless sensor networks: A survey. Comput. Netw. 2011, 55, 1982–2004. [Google Scholar] [CrossRef]
- Di Marco, P.; Park, P.; Fischione, C.; Johansson, K.H. TREnD: A timely, reliable, energy-efficient and dynamic wsn protocol for control applications. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; pp. 1–6. [Google Scholar]
- Djiroun, F.Z.; Djenouri, D. MAC protocols with wake-up radio for wireless sensor networks: A review. IEEE Commun. Surv. Tutor. 2016, 19, 587–618. [Google Scholar] [CrossRef]
- Buratti, C.; Martalò, M.; Verdone, R.; Ferrari, G. Sensor Networks with IEEE 802.15. 4 Systems: Distributed Processing, MAC, and Connectivity; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Afroz, F.; Braun, R. Energy-efficient MAC protocols for wireless sensor networks: A survey. Int. J. Sens. Netw. 2020, 32, 150–173. [Google Scholar] [CrossRef]
- Souil, M. Contribution to Quality of Service in Wireless Sensor Networks. Ph.D. Thesis, Université de Technologie de Compiègne, Compiègne, France, 2013. [Google Scholar]
- Quintero, V.; Estevez, C.; Orchard, M.; Pérez, A. Improvements of Energy-Efficient Techniques in WSNs: A MAC-Protocol Approach. IEEE Commun. Surv. Tutor. 2018, 21, 1188–1208. [Google Scholar] [CrossRef]
- Ketshabetswe, L.K.; Zungeru, A.M.; Mangwala, M.; Chuma, J.M.; Sigweni, B. Communication protocols for wireless sensor networks: A survey and comparison. Heliyon 2019, 5, e01591. [Google Scholar] [CrossRef] [PubMed]
- Sadeq, A.S.; Hassan, R.; Sallehudin, H.; Aman, A.H.M.; Ibrahim, A.H. Conceptual Framework for Future WSN-MAC Protocol to Achieve Energy Consumption Enhancement. Sensors 2022, 22, 2129. [Google Scholar] [CrossRef] [PubMed]
- Du, S.; Saha, A.K.; Johnson, D.B. RMAC: A routing-enhanced duty-cycle MAC protocol for wireless sensor networks. In Proceedings of the IEEE INFOCOM 2007-26th IEEE International Conference on Computer Communications, Anchorage, AK, USA, 6–12 May 2007; pp. 1478–1486. [Google Scholar]
- Liu, C.J.; Huang, P.; Xiao, L. TAS-MAC: A traffic-adaptive synchronous MAC protocol for wireless sensor networks. ACM Trans. Sens. Netw. (TOSN) 2016, 12, 1–30. [Google Scholar] [CrossRef]
- Sun, Y.; Gurewitz, O.; Johnson, D.B. RI-MAC: A receiver-initiated asynchronous duty cycle MAC protocol for dynamic traffic loads in wireless sensor networks. In Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, Raleigh, NC, USA, 5–7 November 2008; pp. 1–14. [Google Scholar]
- Morshed, S.; Heijenk, G. TR-MAC: An energy-efficient MAC protocol exploiting transmitted reference modulation for wireless sensor networks. In Proceedings of the 17th ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Montreal, QC, Canada, 21–26 September 2014; pp. 21–29. [Google Scholar]
- Henna, S. SA-RI-MAC: Sender-assisted receiver-initiated asynchronous duty cycle mac protocol for dynamic traffic loads in wireless sensor networks. In International Conference on Mobile Lightweight Wireless Systems; Springer: Berlin/Heidelberg, Germany, 2011; Volume 81, LNICST; pp. 120–135. [Google Scholar]
- Tang, L.; Sun, Y.; Gurewitz, O.; Johnson, D.B. PW-MAC: An energy-efficient predictive-wakeup MAC protocol for wireless sensor networks. In Proceedings of the 2011 IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1305–1313. [Google Scholar]
- Liu, Z.; Elhanany, I. RL-MAC: A QoS-Aware Reinforcement Learning based MAC Protocol for Wireless Sensor Networks. In Proceedings of the 2006 IEEE International Conference on Networking, Sensing and Control, Ft. Lauderdale, FL, USA, 23–25 April 2006; pp. 768–773. [Google Scholar]
- Kosunalp, S.; Chu, Y.; Mitchell, P.D.; Grace, D.; Clarke, T. Use of Q-learning approaches for practical medium access control in wireless sensor networks. Eng. Appl. Artif. Intell. 2016, 55, 146–154. [Google Scholar] [CrossRef]
- Jang, B.; Lim, J.B.; Sichitiu, M.L. An asynchronous scheduled MAC protocol for wireless sensor networks. Comput. Netw. 2013, 57, 85–98. [Google Scholar] [CrossRef]
- Aby, A.T.; Guitton, A.; Lafourcade, P.; Misson, M. SLACK-MAC: Adaptive MAC protocol for low duty-cycle wireless sensor networks. In International Conference on Ad Hoc Networks; Springer: Cham, Switzerlnad, 2015; pp. 69–81. [Google Scholar]
- INET Framework. Available online: https://inet.omnetpp.org/ (accessed on 21 December 2021).
- Sutton, R.S. Introduction: The challenge of reinforcement learning. In Reinforcement Learning; Springer: Boston, MA, USA, 1992; pp. 1–3. [Google Scholar]
- Kaelbling, L.P.; Littman, M.L.; Moore, A.W. Reinforcement learning: A survey. J. Artif. Intell. Res. 1996, 4, 237–285. [Google Scholar] [CrossRef]
- Sutton, R.S.; Barto, A.G. Reinforcement Learning: An Introduction; MIT Press: Cambridge, MA, USA, 2018. [Google Scholar]
- Watkins, C.J.C.H. Learning from Delayed Rewards. Ph.D. Thesis, King’s College, Cambridge, UK, 1989. [Google Scholar]
- Lim, S.; Yu, H.; Lee, H. Optimal Tethered-UAV Deployment in A2G Communication Networks: Multi-Agent Q-Learning Approach. IEEE Int. Things J. 2022. [Google Scholar] [CrossRef]
- Mathew, A.; Roy, A.; Mathew, J. Intelligent residential energy management system using deep reinforcement learning. IEEE Syst. J. 2020, 14, 5362–5372. [Google Scholar] [CrossRef]
- OMNeT++. Available online: https://omnetpp.org/ (accessed on 21 December 2021).





| Flaws in X-MAC | Interpretation | Potential Consequence |
|---|---|---|
| No evaluation for the scenario with preambles from multiple senders | One sender is sending preambles during the gaps while the other sender is listening for the preamble-ACK (PACK) from the receiver. | Packet loss Energy consumption |
| One sender starts sending preambles while the other sender is already in the SEND_PREAMBLE state. | ||
| Preambles end without being acknowledged | One sender starts sending preambles while the other sender has more packets in its queue is waiting for the data-ACK (DACK) from the receiver. | Packet loss Energy consumption |
| One sender receives data during the preamble gaps while sending preambles. |
| Approach | Parameter | Value |
|---|---|---|
| Common | Header length | 2 bytes |
| Message length | 10 bytes | |
| Preamble duration | 0.83 ms | |
| Bit rate | 19,200 bps | |
| Queue capacity | 20 packets | |
| Send interval | 0.5 s | |
| GW slot duration | 45 ms | |
| Transmit power | 2.24 mW | |
| Receiver sensitivity | −100 dBm | |
| Simulation time | 1000 s | |
| QX-MAC | Learning rate | 0.5 |
| Discount factor | 0.618 | |
| Decay rate | 0.00001 | |
| Maximum transmission attempts | 2 retries |
| Parameter | Value |
|---|---|
| Header length | 2 bytes |
| Message length | 10 bytes |
| Bit rate | 19.2 kbps and 38.4 kbps |
| Queue capacity | 30 packets |
| Packet generation interval | (0.1 s) |
| Send interval | 0.5 s |
| Slot duration | According to Table 4 |
| Number of nodes | 5, 10, 15, 20, 25 nodes |
| Transmit power | 2.24 mW |
| Receiver sensitivity | −100 dBm |
| Simulation time | 1000 s |
| MAC Protocol | Bit Rate (kbps) | Slot Duration (s) | Number of Sensor Nodes | ||||
|---|---|---|---|---|---|---|---|
| 5 | 10 | 15 | 20 | 25 | |||
| X-MAC | 19.2 | sink | 0.035 s | 0.045 s | 0.038 s | 0.038 s | 0.038 s |
| nodes | 0.194 s | 0.25 s | 0.25 s | 0.25 s | 0.25 s | ||
| 38.4 | sink | 0.04 s | 0.02 s | 0.02 s | 0.02 s | 0.02 s | |
| nodes | 0.222 s | 0.111 s | 0.111 s | 0.111 s | 0.111 s | ||
| EX-MAC | 19.2 | sink | 0.035 s | 0.045 s | 0.045 s | 0.045 s | 0.038 s |
| nodes | 0.194 s | 0.25 s | 0.25 s | 0.25 s | 0.25 s | ||
| 38.4 | sink | 0.045 s | 0.045 s | 0.038 s | 0.045 s | 0.038 s | |
| nodes | 0.25 s | 0.25 s | 0.25 s | 0.25 s | 0.25 s | ||
| QX-MAC | 19.2 | sink | 0.045 s | 0.045 s | 0.038 s | 0.038 s | 0.038 s |
| nodes | 0.25 s | 0.25 s | 0.25 s | 0.25 s | 0.25 s | ||
| 38.4 | sink | 0.085 s | 0.045 s | 0.038 s | 0.045 s | 0.038 s | |
| nodes | 0.472 s | 0.25 s | 0.25 s | 0.25 s | 0.25 s | ||
| Approach | Parameter | Value |
|---|---|---|
| Common | Header length | 2 bytes |
| Message length | 10 bytes | |
| Preamble duration | 0.83 ms | |
| Bit rate | 250 kbps | |
| Queue capacity | 30 packets | |
| Sink slot duration | 0.1 s | |
| Source/relay node’s slot duration | 0.2 s | |
| Transmit power | 0.7 mW | |
| Receiver sensitivity | −85 dBm | |
| Simulation time | 1000 s | |
| QX-MAC | Learning rate | 0.5 |
| Discount factor | 0.618 | |
| Decay rate | 0.00001 | |
| Maximum transmission attempts | 2 retries |
| MAC Protocol | Packet Arrival Rate (Packets/s) | |||||
|---|---|---|---|---|---|---|
| 1 | 5 | 10 | 15 | 20 | 25 | |
| X-MAC | 2.01 J | 7.94 J | 7.96 J | 7.94 J | 7.98 J | 7.94 J |
| EX-MAC | 1.75 J | 7.61 J | 13.19 J | 17.02 J | 17.73 J | 17.77 J |
| QX-MAC | 1.77 J | 7.22 J | 12.08 J | 16.28 J | 20.20 J | 24.33 J |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Afroz, F.; Braun, R. Empirical Analysis of Extended QX-MAC for IOT-Based WSNS. Electronics 2022, 11, 2543. https://doi.org/10.3390/electronics11162543
Afroz F, Braun R. Empirical Analysis of Extended QX-MAC for IOT-Based WSNS. Electronics. 2022; 11(16):2543. https://doi.org/10.3390/electronics11162543
Chicago/Turabian StyleAfroz, Farhana, and Robin Braun. 2022. "Empirical Analysis of Extended QX-MAC for IOT-Based WSNS" Electronics 11, no. 16: 2543. https://doi.org/10.3390/electronics11162543
APA StyleAfroz, F., & Braun, R. (2022). Empirical Analysis of Extended QX-MAC for IOT-Based WSNS. Electronics, 11(16), 2543. https://doi.org/10.3390/electronics11162543







