A Survey on MAC-Based Physical Layer Security over Wireless Sensor Network
Abstract
:1. Introduction
2. Related Work
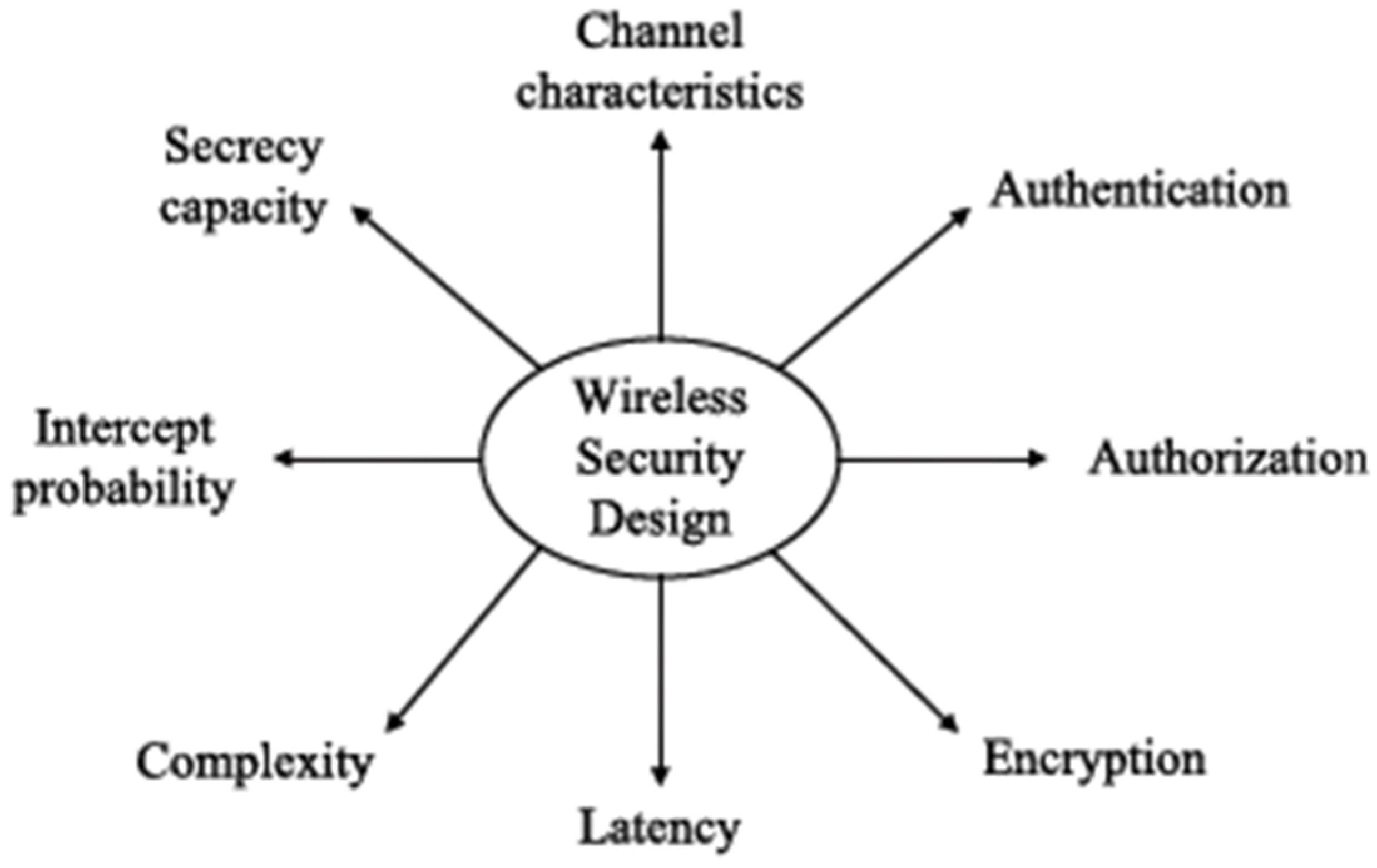
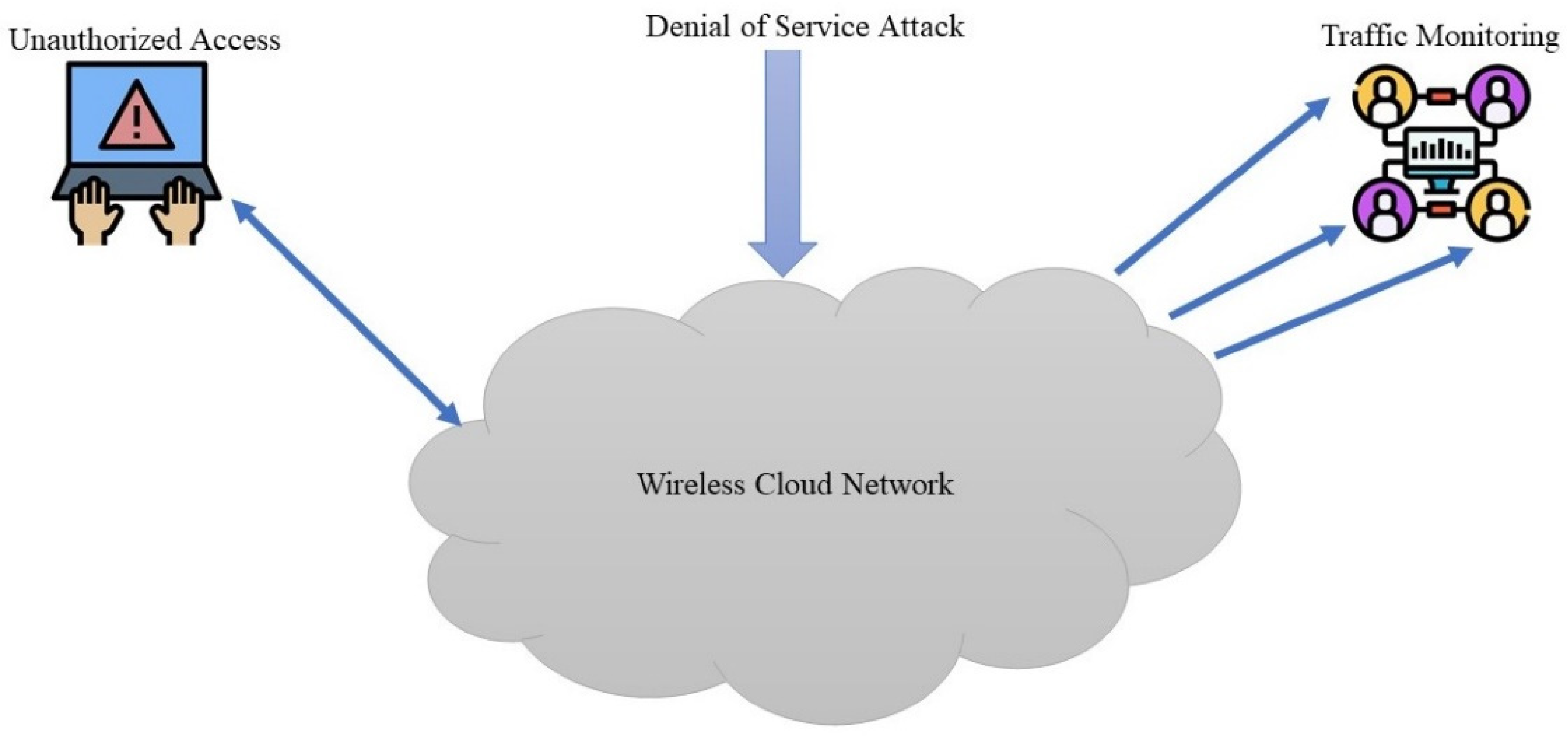
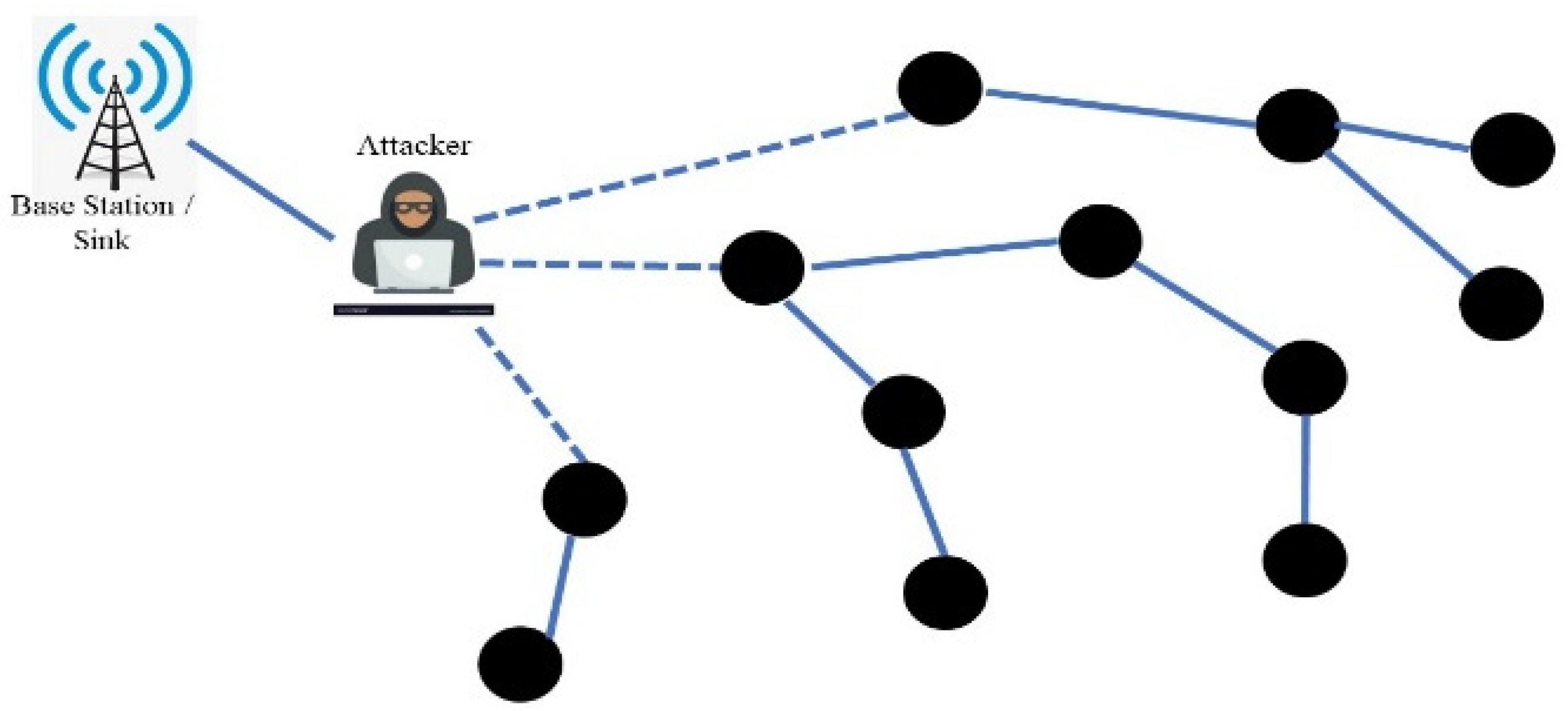
3. Attacks on Wireless Security
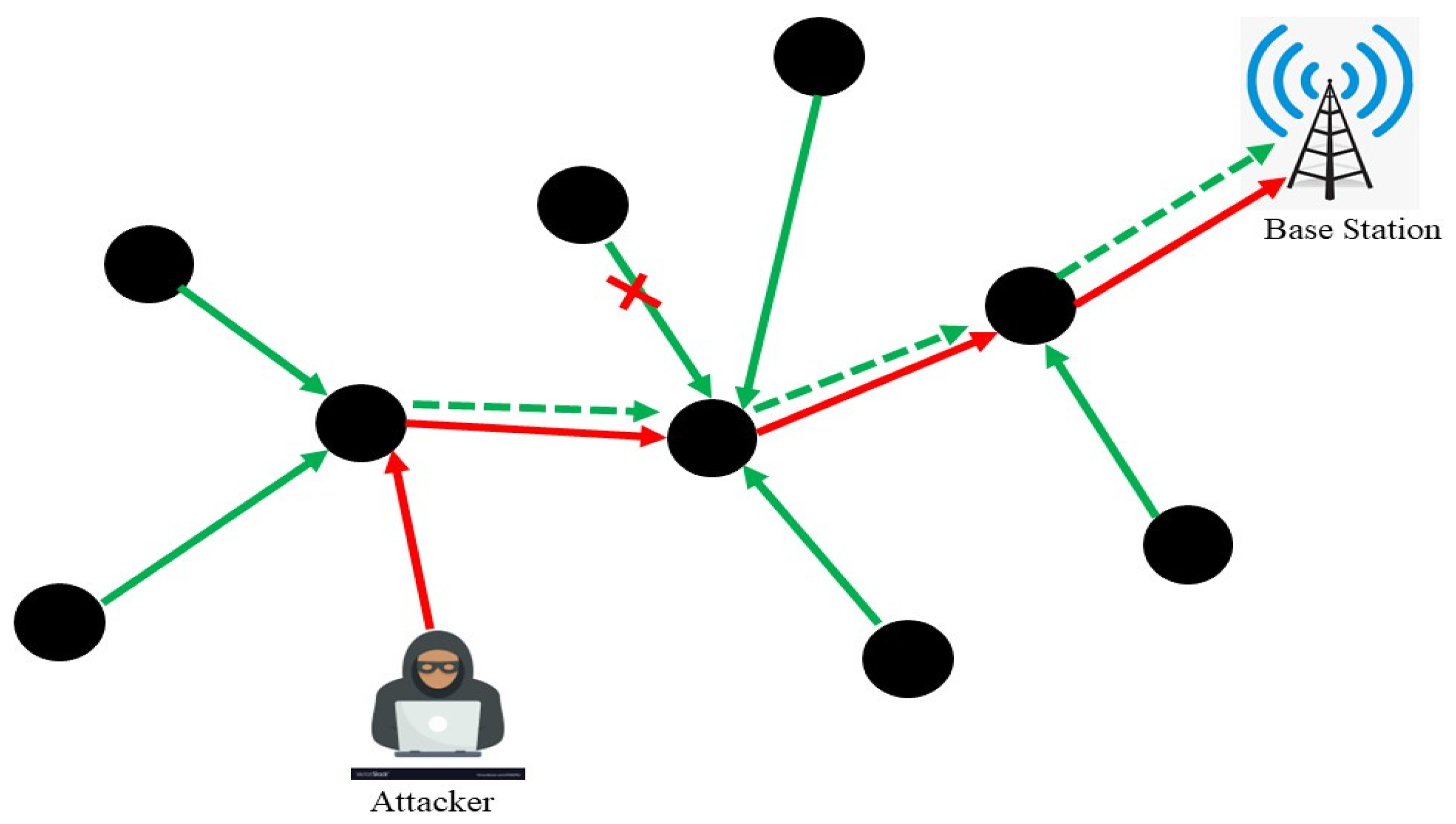
3.1. Packet Injection-Based Attacks
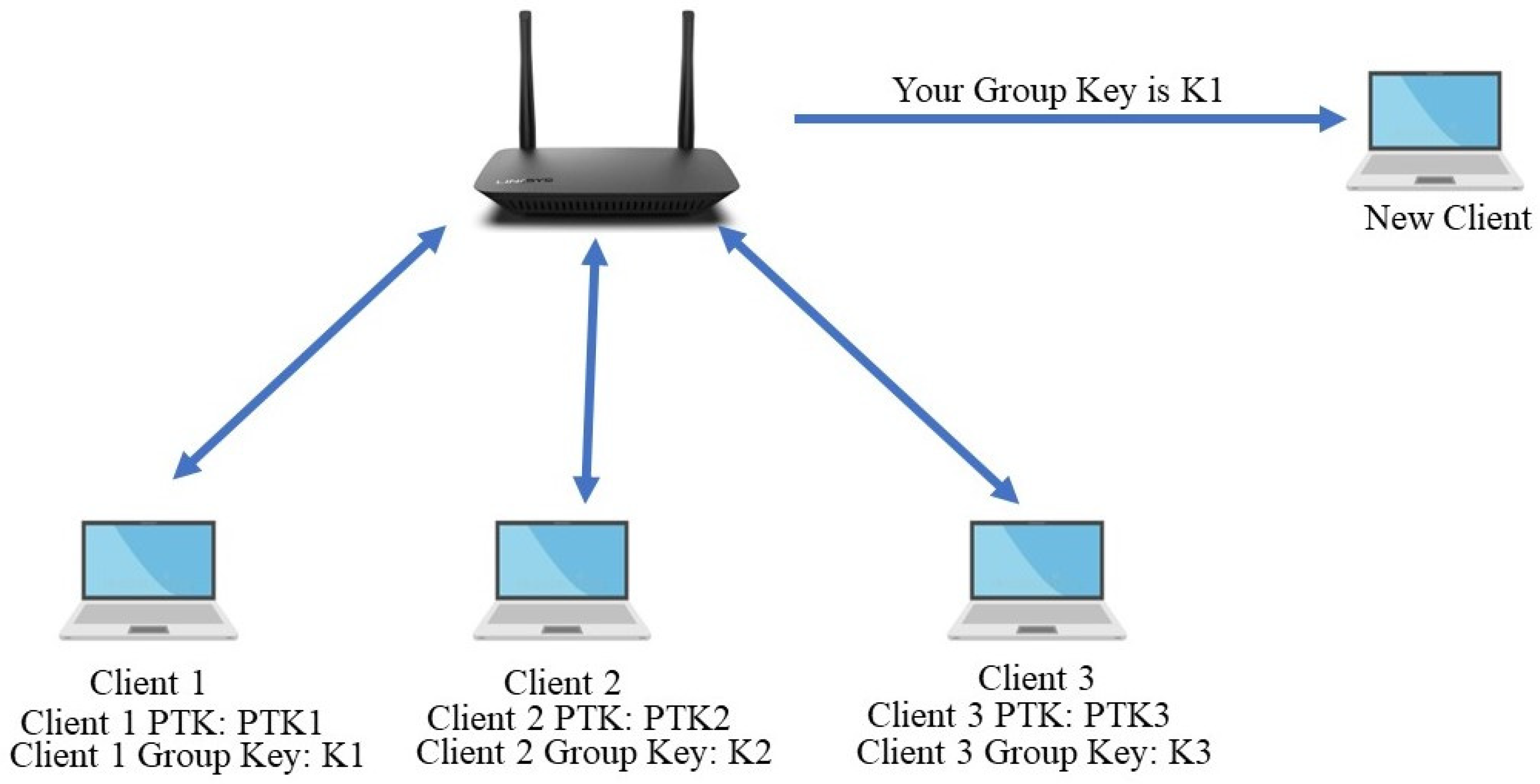
3.2. Fake Authentication-Based Attacks
- Open system authentication: in this type of authentication, the user can access the system without any kind of user verification by the network [66]. It is also referred to as null verification because no kind of authentication takes place between the devices, and it is an exchange of frames (hellos) between the client and the AP.
- Shared key authentication; this is the same as open system authentication but it includes a challenge (requires WEP keys to be matched) and response between AP and the user [67,68]. In this method, the key is delivered to wireless clients with the help of a secured and protected channel which is independent of any standard and protocols being used. The client or user just has to simply log in by submitting their credentials and can access the network [69].
3.3. Fluhrrer, Mantin and Shamir Attacks
3.4. Wi-Fi Protected Access (WPA) Attacks
3.4.1. Back and Tew’s Improved Attack
3.4.2. Ohigashi-Morii Attack
3.4.3. Michael Attack
3.5. Wi-Fi Protected Access 2 (WPA2) Attacks
3.5.1. KRACK Attack
3.5.2. PMKID Attack
- The attacker might be able to have direct communication with the access point, and therefore, it is a client-less attack as it does not need to have a regular user for its deployment [82].
- This attack is less time consuming because of the fact that the unauthorized person does not have to wait for the four-way handshaking process [86].
- They are faster because it does not require replaying of counter values.
- One of the key benefits is that the final data or result will not be shown in different format, but it will appear to be in regular hexadecimal format [67].
- There is no loss of EAPOL frames, since the AP and client are too far away from the attacker.
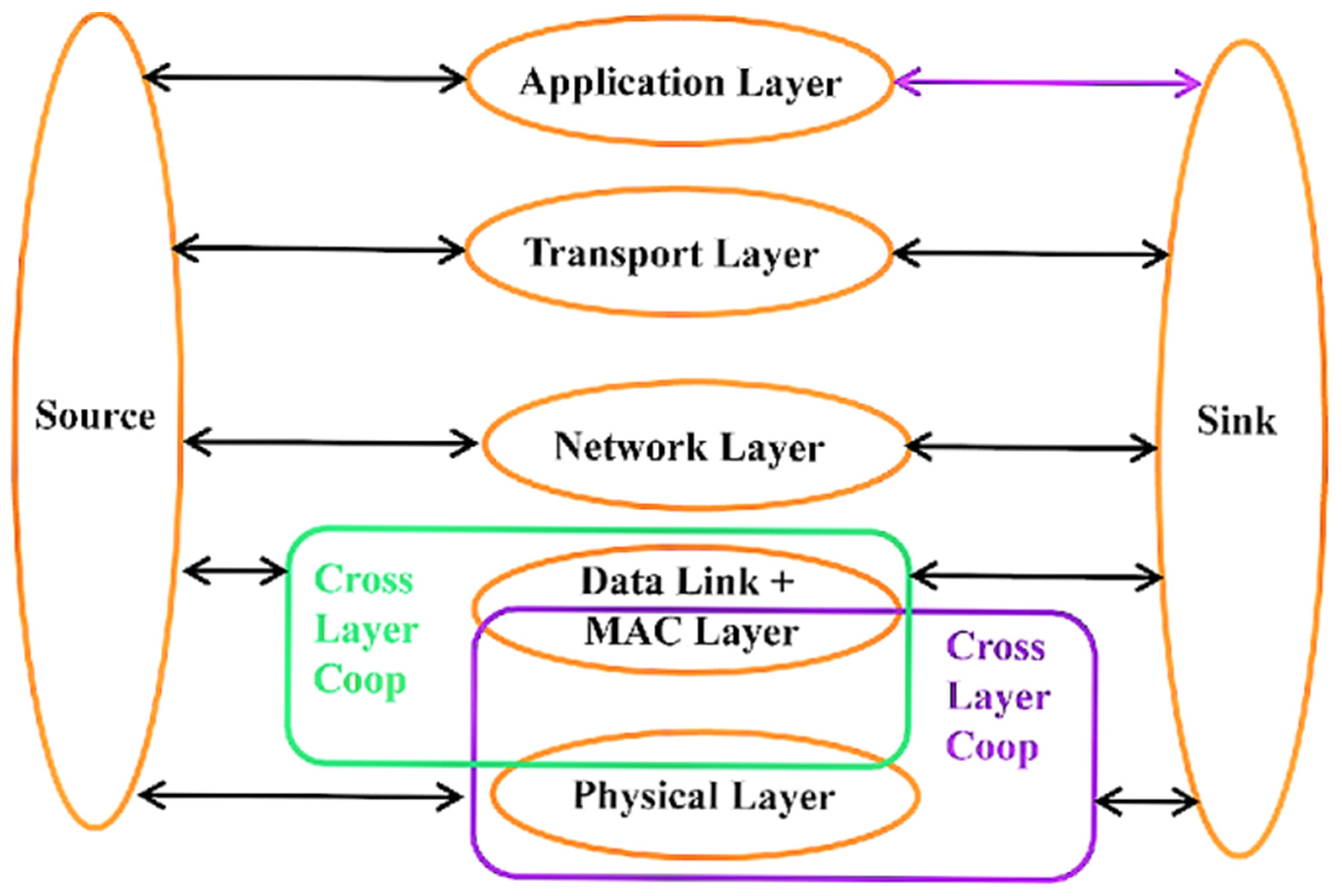
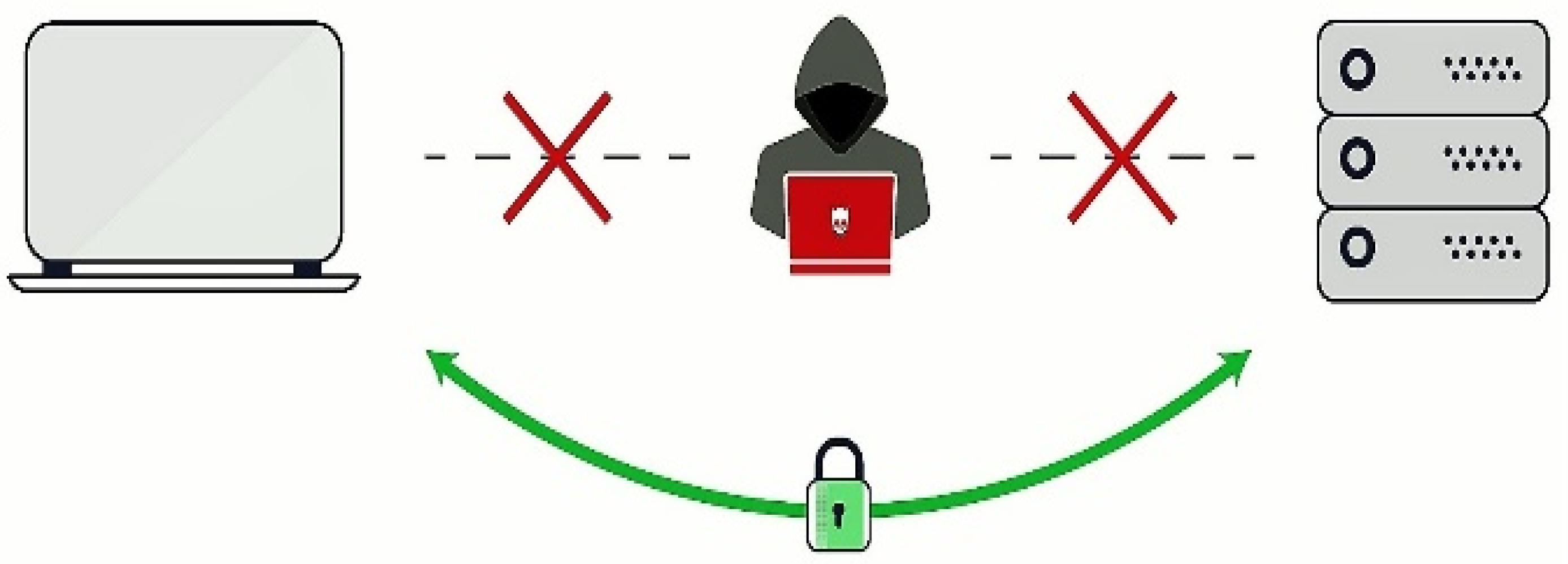
4. TCP/IP Model Layers Attacks
4.1. Physical Layer Attacks
4.2. MAC Layer Attacks
4.3. Network Layer Attacks
4.4. Transport Layer Attacks
4.5. Application Layer Attacks
Active Attacks
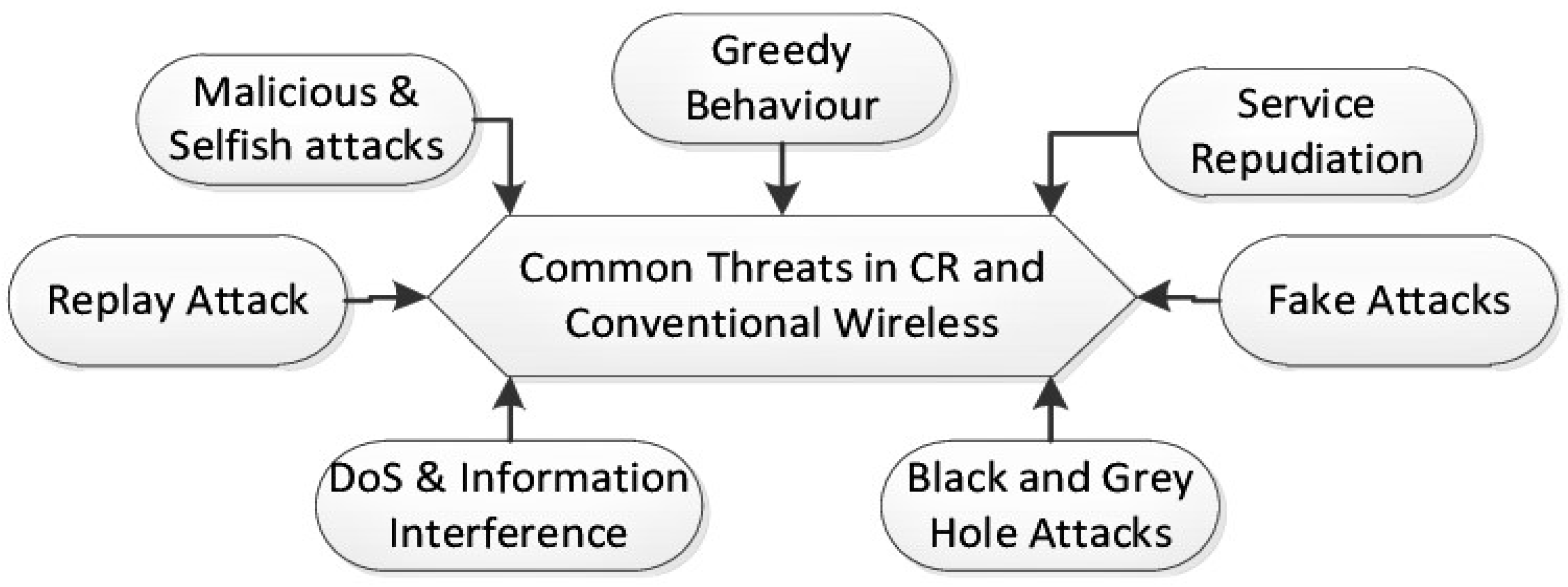
5. Security Threats in Real Life
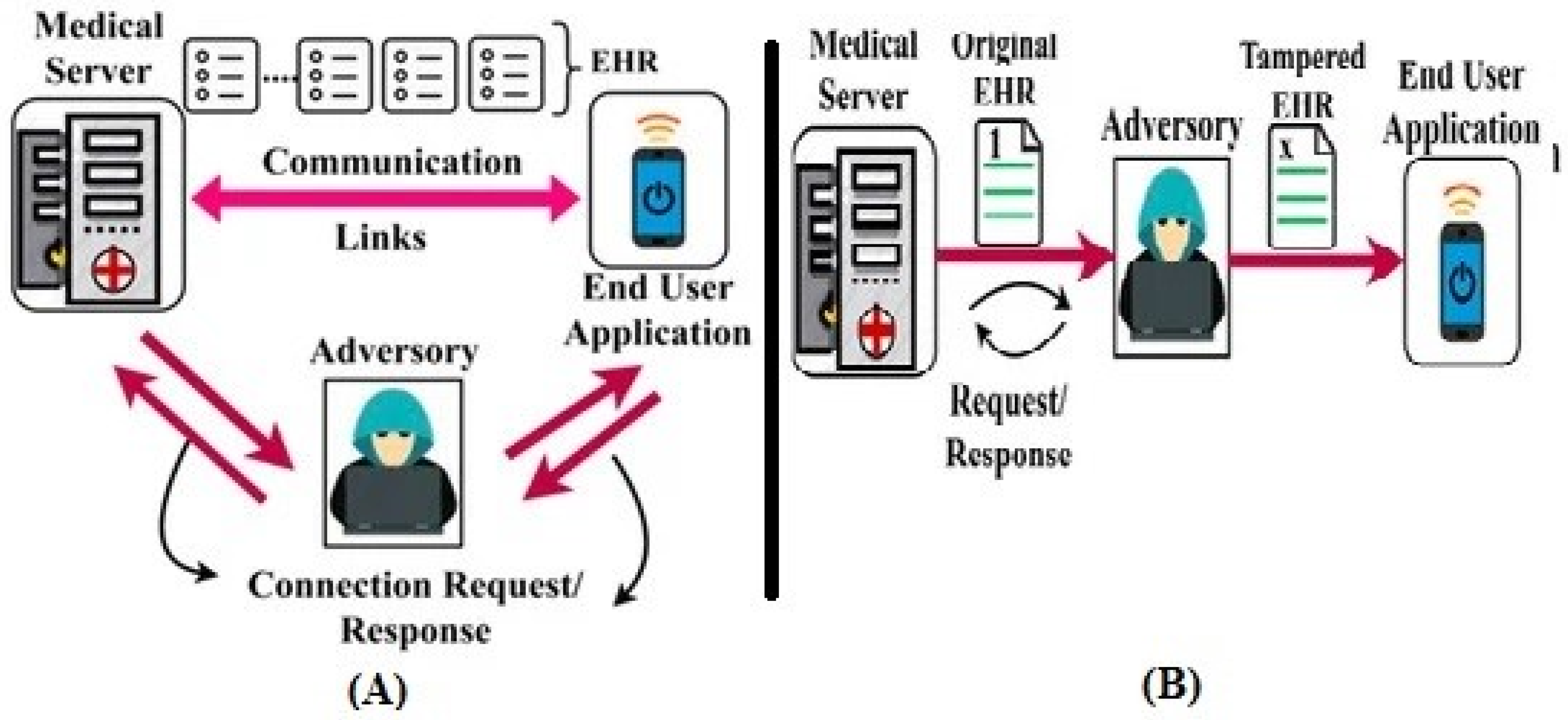
5.1. Healthcare Field
5.2. Oil and Gas Industries
5.3. Military Information Integration
6. Proposed Solution to Enhance Security of Wireless Sensor Networks
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Dwiputriane, D.B.; Heng, S.H. No. 3. Authentication for 5G Mobile Wireless Networks. J. Eng. Technol. Appl. Phys. 2022, 4, 16–24. [Google Scholar] [CrossRef]
- Masher, N.; ul Mahjoob, K. IOT SECURITY THREATS AND CHALLENGES. Available online: https://www.irjmets.com/uploadedfiles/paper/issue_2_february_2022/19081/final/fin_irjmets1644942131.pdf (accessed on 24 June 2022).
- Waqas, M.; Tu, S.; Halim, Z.; Rehman, S.; Abbas, G.; Abbas, Z.H. The Role of Artificial Intelligence and Machine Learning in Wireless Networks Security: Principle, Practice and Challenges; Springer: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Li, J.; Ma, H.; Li, K.; Cui, L.; Sun, L.; Zhao, Z.; Wang, X. Wireless Sensor Networks. In Proceedings of the 12th China Conference, CWSN 2018, Kunming, China, 21–23 September 2018. [Google Scholar]
- Yadav, R.; Varma, S.; Malaviya, N. A survey of MAC protocols for wireless sensor networks. UbiCC J. 2009, 4, 827–833. [Google Scholar]
- Ismail, A.S.; Wang, X.F.; Hawbani, A.; Alsamhi, S.; Abdel Aziz, S. Routing protocols classification for underwater wireless sensor networks based on localization and mobility. Wirel. Netw. 2022, 28, 797–826. [Google Scholar] [CrossRef]
- Raja Basha, A. A Review on Wireless Sensor Networks: Routing. Wirel. Pers. Commun. 2022, 1–41. [Google Scholar] [CrossRef]
- Moessner, K.; Majid, M.; Habib, S.; Rehman Javed, A.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.-W. Applications of wireless sensor networks and internet of things frameworks in the industry revolution 4.0: A systematic literature review. Sensors 2022, 22, 2087. [Google Scholar] [CrossRef]
- Temene, N.; Sergiou, C.; Georgiou, C.; Vassiliou, V.; Sergiou, C. A survey on mobility in Wireless Sensor Networks. Ad Hoc Netw. 2022, 125, 102726. [Google Scholar] [CrossRef]
- Zhu, L.; Xiang, H.; Zhang, K. A Light and Anonymous Three-Factor Authentication Protocol for Wireless Sensor Networks. Symmetry 2022, 14, 46. [Google Scholar] [CrossRef]
- Cao, L.; Wang, Z.; Yue, Y. Analysis and Prospect of the Application of Wireless Sensor Networks in Ubiquitous Power Internet of Things. Comput. Intell. Neurosci. 2022, 2022, 9004942. [Google Scholar] [CrossRef]
- El Khediri, S. Wireless sensor networks: A survey, categorization, main issues, and future orientations for clustering protocols. Wirel. Pers. Commun. 2022, 104, 1775–1837. [Google Scholar] [CrossRef]
- Mezrag, F.; Bitam, S.; Mellouk, A. An efficient and lightweight identity-based scheme for secure communication in clustered wireless sensor networks. J. Netw. Comput. Appl. 2022, 200. [Google Scholar] [CrossRef]
- Choi, J.; Ha, J.; Personal, H.J. Physical Layer Security for Wireless Sensor Networks. Available online: https://ieeexplore.ieee.org/document/6666094?arnumber=6666094 (accessed on 25 June 2022).
- Engineering, F.A. Energy-efficient collision avoidance MAC protocols for underwater sensor networks: Survey and challenges. J. Mar. Sci. Eng. 2021, 9, 741. [Google Scholar] [CrossRef]
- Gulati, K.; Sarath Kumar Boddu, R.; Kumar Boddu, S.; Kapila, D.; Bangare, S.L.; Chandnani, N.; Saravanan, G. A review paper on wireless sensor network techniques in Internet of Things (IoT). Mater. Today 2022, 51, 161–165. [Google Scholar] [CrossRef]
- Rajasoundaran, S.; Prabu, A.V.; Kumar, G.S.; Malla, P.P.; Routray, S. Secure Opportunistic Watchdog Production in Wireless Sensor Networks: A Review. Wirel. Pers. Commun. 2021, 120, 1895–1919. [Google Scholar] [CrossRef]
- Daanoune, I.; Abdennaceur, B.; Ballouk, A. A comprehensive survey on LEACH-based clustering routing protocols in Wireless Sensor Networks. Ad. Hoc. Netw. 2021, 114, 102409. [Google Scholar] [CrossRef]
- Chander, B.; Gopalakrishnan, K. Secure, Efficient, Lightweight Authentication in Wireless Sensor Networks. Lect. Notes Electr. Eng. 2021, 749, 303–312. [Google Scholar] [CrossRef]
- Shiu, Y.; Chang, S.; Wu, H.C.; Huang, S.C.H.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Ahmad, A.; Rathore, M.; Paul, A.; Chen, B.W. Data transmission scheme using mobile sink in static wireless sensor network. J. Sens. 2015, 2015, 279304. [Google Scholar] [CrossRef]
- Jabbar, S.; Paul, A.; Rho, S.; Minhas, A.A. Multilayer cluster designing algorithm for lifetime improvement of wireless sensor networks. J. Supercomput. 2014, 70, 104–132. [Google Scholar] [CrossRef]
- Pinto, A.; Farooq, M.S.; Idrees, M.; Rehman, A.U.; Khan, M.Z.; Abunadi, I.; Assam, M.; Althobaiti, M.M.; Al-Wesabi, F.N. Formal Modeling and Improvement in the Random Path Routing Network Scheme Using Colored Petri Nets. Appl. Sci. 2022, 12, 1426. [Google Scholar] [CrossRef]
- Din, S.; Paul, A.; Ahmad, A.; Kim, J.H. Energy efficient topology management scheme based on clustering technique for software defined wireless sensor network. Peer-Peer Netw. Appl. 2019, 12, 348–356. [Google Scholar] [CrossRef]
- Jabbar, S.; Minhas, A.A.; Gohar, M.; Paul, A.; Rho, S. E-MCDA: Extended-multilayer cluster designing algorithm for network lifetime improvement of homogenous wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 902581. [Google Scholar] [CrossRef]
- Tropea, M.; Spina, M.; De Rango, F.; Gentile, A. Security in Wireless Sensor Networks: A Cryptography Performance Analysis at MAC Layer. Future Internet 2022, 14, 145. [Google Scholar] [CrossRef]
- Meshram, C.; Imoize, A.L.; Jamal, S.S.; Aljaedi, A.; Alharbi, A.R. SBOOSP for Massive Devices in 5G WSNs Using Conformable Chaotic Maps. Comput. Mater. Contin. 2022, 71, 4591–4608. [Google Scholar] [CrossRef]
- Ahmad, I.; Rahman, T.; Zeb, A.; Khan, I.; Ullah, I.; Hamam, H.; Cheikhrouhou, O. Analysis of security attacks and taxonomy in underwater wireless sensor networks. Wirel. Commun. Mob. Comput. 2021, 2021, 1444024. [Google Scholar] [CrossRef]
- Singh, S.; Saurabh, R.; Maitra, T.; Giri, D. Security in Communication for Intelligent Wireless Sensor Networks: Issues and Challenges. Comput. Intell. Wirel. Sens. Netw. 2022, 1, 175–192. [Google Scholar]
- Yu, D.; Kang, J.; Dong, J. Service attack improvement in wireless sensor network based on machine learning. Microprocess. Microsyst. 2021, 80, 103637. [Google Scholar] [CrossRef]
- Alves, R.; Oliveira, D.; Pereira, G.C.; Albertini, B.C.; Margi, C.B. WS3N: Wireless secure SDN-based communication for sensor networks. Secur. Commun. Netw. 2018, 2018, 8734389. [Google Scholar] [CrossRef]
- Abood, M.S.; Wang, H.; Mahdi, H.F.; Hamdi, M.M.; Abdullah, A.S. Review on secure data aggregation in Wireless Sensor Networks. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1076, 012053. [Google Scholar] [CrossRef]
- de Carvalho, J.A.R.P.; Veiga, H.; Ribeiro Pacheco, C.F. Extended performance research on IEEE 802.11a WPA2 multi-node laboratory links. IAENG Int. J. Comput. Sci. 2020, 47, 296–301. [Google Scholar] [CrossRef]
- Ali, J.; Roh, B.H. Quality of service improvement with optimal software-defined networking controller and control plane clustering. Comput. Mater. Contin. 2021, 67, 849–875. [Google Scholar] [CrossRef]
- Ali, J.; Roh, B.H.; Lee, S. QoS improvement with an optimum controller selection for software-defined networks. PLoS ONE 2019, 14, e0217631. [Google Scholar] [CrossRef] [PubMed]
- Ali, J.; Roh, B.H. A Novel Scheme for Controller Selection in Software-Defined Internet-of-Things (SD-IoT). Sensors 2022, 22, 3591. [Google Scholar] [CrossRef] [PubMed]
- Ali, J.; Lee, B.; Oh, J.; Lee, J.; Roh, B.H. A novel features prioritization mechanism for controllers in software-defined networking. Comput. Mater. Contin. 2021, 69, 267–282. [Google Scholar] [CrossRef]
- Ali, J.; Roh, B.H. An Effective Approach for Controller Placement in Software-Defined Internet-of-Things (SD-IoT). Sensors 2022, 22, 2992. [Google Scholar] [CrossRef]
- Ali, J.; Roh, B.H. An effective hierarchical control plane for software-defined networks leveraging TOPSIS for end-to-end QoS class-mapping. IEEE Access 2020, 8, 88990–89006. [Google Scholar] [CrossRef]
- Ali, J.; Lee, G.M.; Roh, B.H.; Ryu, D.K.; Park, G. Software-defined networking approaches for link failure recovery: A survey. Sustainability 2020, 12, 4255. [Google Scholar] [CrossRef]
- Ndiaye, M.; Hancke, G.P.; Abu-Mahfouz, A.M. Software defined networking for improved wireless sensor network management: A survey. Sensors 2017, 17, 1031. [Google Scholar] [CrossRef]
- Orozco-Santos, F.; Sempere-Payá, V.; Albero-Albero, T.; Silvestre-Blanes, J. Enhancing sdn wise with slicing over tsch. Sensors 2021, 21, 1075. [Google Scholar] [CrossRef]
- Mohammed, A.; Al-Dulaimi, K.; Khodayer, M.; Al-Dulaimi, H. Analysis for modulation and coding scheme with data rate traffic over IEEE 802.11 AC and 802.11 N in wireless multimedia. Int. J. Comput. 2021, 20, 2021–2109. [Google Scholar] [CrossRef]
- Badhwar, R. Next Gen Wi-Fi and Security. CISO’s Next Front. 2021, 213–218. [Google Scholar] [CrossRef]
- Ahmed, N.; De, D.; Barbhuiya, F.A.; Hussain, M.I. MAC Protocols for IEEE 802.11 ah-based Internet of Things: A Survey. IEEE Internet Things J. 2021, 9, 916–938. [Google Scholar] [CrossRef]
- Frontier, R.B. Next Gen Wi-Fi and Security; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Ahmed, N.; Roy, A.; Misra, S.; Tandur, D. Programmable IEEE 802.11 ah Network for Internet of Things. In Proceedings of the ICC 2021—IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021. [Google Scholar] [CrossRef]
- Butt, T.M.; Riaz, R.; Chakraborty, C.; Rizvi, S.S.; Paul, A. Cogent and energy efficient authentication protocol for wsn in iot. Comput. Mater. Contin. 2021, 68, 1877–1898. [Google Scholar]
- Reddy, S.N. Industrial Safety Applications Using Wireless Access Panels. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021, 12, 1573–1577. [Google Scholar]
- Carvalho, J.; Veiga, H.; Pacheco, C.F.; Reis, A.D. Extended Performance Research on IEEE 802.11 a WPA Multi-Node Laboratory Links; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Dunkels, A.; Alonso, J.; Voigt, T.; Ritter, H.; Schiller, J. Connecting wireless sensornets with TCP/IP networks. Lect. Notes Comput. Sci. (Incl. Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinform.) 2004, 2957, 143–152. [Google Scholar] [CrossRef]
- Paliwal, G.; Mudgal, A.P.; Taterh, S. A study on various attacks of TCP/IP and security challenges in MANET layer architecture. Adv. Intell. Syst. Comput. 2015, 336, 191–203. [Google Scholar] [CrossRef]
- Kwon, E.; Cho, Y.; Chae, K.J. Integrated Transport Layer Security: End-To-End Security Model between WTLS and TLS. Available online: https://ieeexplore.ieee.org/document/905331 (accessed on 24 June 2022).
- Fall, K.; Stevens, W. TCP/IP Illustrated, Volume 1: The Protocols; Addison-Wesley Professional: Boston, MA, USA, 2011. [Google Scholar]
- Zhang, Y. A multilayer IP security protocol for TCP performance enhancement in wireless networks. IEEE J. Sel. Areas Commun. 2004, 22, 767–776. [Google Scholar] [CrossRef]
- Fu, B.; Xiao, Y.; Deng, H.; Zeng, H. A survey of cross-layer designs in wireless networks. IEEE Commun. Surv. Tutor. 2013, 16, 110–126. [Google Scholar] [CrossRef]
- Farid, S.; Rehman, A.U. Enhancement in Quality of Services Using Integrated Services in 4G Cellular Network. Tech. J. 2018, 23, 82–93. [Google Scholar]
- Perkins, C.; Jagannadh, T. DHCP for mobile networking with TCP/IP. In Proceedings of the Proceedings IEEE Symposium on Computers and Communications, Alexandria, Egypt, 27–29 July 1995. [Google Scholar] [CrossRef]
- Ali, M.; Nadeem, M.; Siddique, A.; Ahmad, S.; Ijaz, A. Addressing Sinkhole Attacks in Wireless Sensor Networks—A Review. Int. J. Sci. Technol. Res. (IJSTR) 2020, 9, 406–411. [Google Scholar]
- Hussain, A.; Ali, M.; Razzaq, A.; Ijaz, A.; Saeed Khan, N. Development of an Adaptive Energy Aware Routing Scheme for Wireless Sensor Networks. Int. J.Emerg. Technol. 2020, 11, 381–388. [Google Scholar]
- Shang, W.; Yu, Y.; Droms, R.; Zhang, L. Challenges in IoT Networking via TCP/IP Architecture. NDN Project. 2016. Available online: https://named-data.net/publications/techreports/ndn-0038-1-challenges-iot/ (accessed on 24 June 2022).
- Chan, M.C.; Ramjee, R. Improving TCP/IP performance over third-generation wireless networks. IEEE Trans. Mob. Comput. 2008, 7, 430–443. [Google Scholar] [CrossRef]
- Poongodi, T.; Krishnamurthi, R.; Indrakumari, R.; Suresh, P.; Balusamy, B. Wearable devices and IoT. Intell. Syst. Ref. Libr. 2020, 165, 245–273. [Google Scholar] [CrossRef]
- Dunkels, A.; Alonso, J.; Voigt, T.; Ritter, H.; Schiller, J. Connecting wireless sensornets with TCP/IP networks. In International Conference on Wired/Wireless Internet Communications; Springer: Berlin, Heidelberg, 2004. [Google Scholar]
- Faria, D.B.; Cheriton, D.R. Detecting identity-based attacks in wireless networks using signalprints. In WiSE 2006—Proceedings 5th ACM Work Wireless Security; ACM: New York, NY, USA, 2006; Volume 2006, pp. 43–52. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Choudhary, K.; Hossain, M.S.; Alhamid, M.F.; Muhammad, G. Lightweight and Anonymity-Preserving User Authentication Scheme for IoT-Based Healthcare. IEEE Internet Things J. 2022, 9, 2649–2656. [Google Scholar] [CrossRef]
- Mahamune, A.A.; Chandane, M.M. TCP/IP Layerwise Taxonomy of Attacks and Defence Mechanisms in Mobile Ad Hoc Networks. J. Inst. Eng. Ser. B 2022, 103, 273–291. [Google Scholar] [CrossRef]
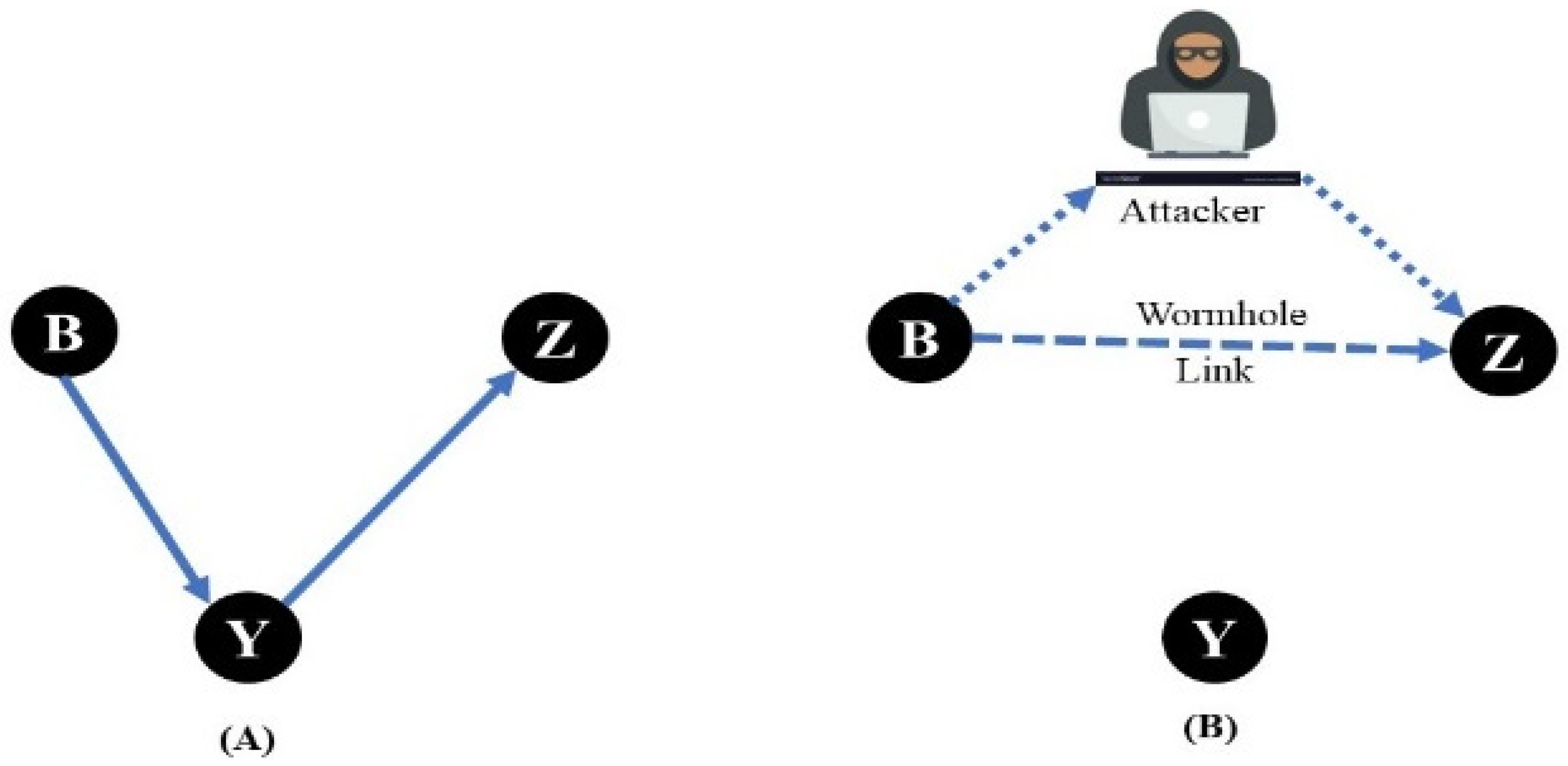
- Messai, M.-L. Classification of Attacks in Wireless Sensor Networks. arXiv 2014, arXiv:1406.4516. [Google Scholar]
- Hu, Y.; Perrig, A.; Johnson, D.B. Wormhole attacks in wireless networks. IEEE J. Sel. Areas Commun. 2006, 24, 370–380. [Google Scholar]
- Lupu, T.G. Main types of attacks in wireless sensor networks. In Proceedings of the 9th WSEAS International Conference on Signal, Speech and Image Processing, and 9th WSEAS International Conference on Multimedia, Internet & Video Technologies, Budapest, Hungary, 3–5 September 2009. [Google Scholar]
- Yu, B.; Xiao, B. Detecting selective forwarding attacks in wireless sensor networks. In Proceedings of the 20th IEEE International Parallel & Distributed Processing Symposium, Rhodes Island, 25–29 April 2006. [Google Scholar]
- Noman Riaz, M.; Buriro, A.; Mahboob, A. Classification of Attacks on Wireless Sensor Networks: A Survey. Int. J. Wirel. Microw. Technol. 2018, 8, 15–39. [Google Scholar] [CrossRef]
- Yang, J.; Chen, Y.; Trappe, W.; Cheng, J. Detecting mobile agents using identity fraud. SpringerBriefs Comput. Sci. 2014, 0, 43–66. [Google Scholar] [CrossRef]
- Shahzad, F.; Pasha, M.; Ahmad, A. A survey of active attacks on wireless sensor networks and their countermeasures. Int. J. Comput. Sci. Inf. Secur. 2017, 14, 12. [Google Scholar]
- Patel, M.; Aggarwal, A. Security attacks in wireless sensor networks: A survey. In Proceedings of the 2013 International Conference on Intelligent Systems and Signal Processing (ISSP), Vallabh Vidyanagar, India, 1–2 March 2013. [Google Scholar]
- Anwar, R.; Bakhtiari, M.; Zainal, A.; Abdullah, A.H.; Qureshi, K.N. Security issues and attacks in wireless sensor network. World Appl. Sci. J. 2014, 30, 1224–1227. [Google Scholar] [CrossRef]
- Yang, T.; Zhai, F.; Xu, H.Q.; Li, W. Design of a secure and efficient authentication protocol for real-time accesses of multiple users in PIoT-oriented multi-gateway WSNs. Energy Rep. 2022, 8, 1200–1211. [Google Scholar] [CrossRef]
- Sinha, P.; Jha, V.K.; Bhushan, B.; Rai, A.K.; Jha, V.K. A Review of Machine Learning Solutions to Denial-of-Services Attacks in Wireless Sensor Networks. In Proceedings of the 2017 International Conference on Signal Processing and Communication (ICSPC), Coimbatore, India, 28–29 July 2017. [Google Scholar] [CrossRef]
- Bouabdellah, M.; Kaabouch, N.; El Bouanani, F.; Ben-Azza, H. Network layer attacks and countermeasures in cognitive radio networks: A survey. J. Inf. Secur. Appl. 2018, 38, 40–49. [Google Scholar] [CrossRef]
- Proano, A.; Lazos, L. Selective jamming attacks in wireless networks. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010. [Google Scholar]
- Singh, R.; Prasad, A.; Moven, R.M.; Deva Sarma, H.K. Denial of service attack in wireless data network: A survey. In Proceedings of the 2017 Devices for Integrated Circuit (DevIC), Kalyani, India, 23–24 March 2017; pp. 354–359. [Google Scholar]
- Edigar, M.B.; Rao, P.V. Modeling of lightweight security framework for identifying efficient route for secure communication in WSN. Int. J. Intell. Unmanned Syst. 2022, 10, 129–144. [Google Scholar] [CrossRef]
- Isha, A.M.; Raj, G. Dos attacks on tcp/ip layers in wsn. Int. J. Comput. Netw. Commun. Secur. 2013, 1, 40–45. [Google Scholar]
- Zhang, L.; Restuccia, F.; Melodia, T.; Pudlewski, S.M. Taming cross-layer attacks in wireless networks: A Bayesian learning approach. IEEE Trans. Mob. Comput. 2018, 18, 1688–1702. [Google Scholar] [CrossRef]
- Wang, L.; Wyglinski, A.M. A combined approach for distinguishing different types of jamming attacks against wireless networks. In Proceedings of the 2011 IEEE Pacific Rim Conference on Communications, Computers and Signal Processing, Victoria, BC, Canada, 23–26 August 2011. [Google Scholar]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, S.V. Denial of service attacks in wireless networks: The case of jammers. IEEE Commun. Surv. Tutor. 2010, 13, 245–257. [Google Scholar] [CrossRef]
- Ali, M.; Siddique, A.; Hussain, A.; Hassan, F.; Ijaz, A.; Mehmood, A. A Sustainable Framework for Preventing IoT Systems from Zero Day DDoS Attacks by Machine Learning. Int. J. Emerg. Technol. 2021, 12, 116–121. [Google Scholar]
- Eriksson, J.; Krishnamurthy, S.V.; Faloutsos, M. Truelink: A practical countermeasure to the wormhole attack in wireless networks. In Proceedings of the 2006 IEEE International Conference on Network Protocols, Santa Barbara, CA, USA, 12–15 November 2006. [Google Scholar]
- Zhang, Z.; Wu, J.; Deng, J.; Qiu, M. Jamming ACK attack to wireless networks and a mitigation approach. In Proceedings of the IEEE GLOBECOM 2008–2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November 2008–4 December 2008. [Google Scholar]
- Kanawat, S.; Parihar, P. Attacks in wireless networks. Int. J. Smart Sens. Adhoc Netw. 2011, 1, 17. [Google Scholar] [CrossRef]
- Kadhim, A.N.; Sadkhan, S.B. Security Threats in Wireless Network Communication-Status, Challenges, and Future Trends. In Proceedings of the 2021 International Conference on Advanced Computer Applications (ACA), Maysan, Iraq, 25–26 July 2021. [Google Scholar]
- Sardar, R.; Anees, T. Web of things: Security challenges and mechanisms. IEEE Access 2021, 9, 31695–31711. [Google Scholar] [CrossRef]
- Taleb, H.; Nasser, A.; Andrieux, G.; Charara, N.; Motta Cruz, E. Wireless technologies, medical applications and future challenges in WBAN: A survey. Wirel. Netw. 2021, 27, 5271–5295. [Google Scholar] [CrossRef]
- Zaman, S.; Alhazmi, K.; Aseeri, M.A.; Ahmed, M.R.; Khan, R.T.; Kaiser, M.S.; Mahmud, M. Security threats and artificial intelligence based countermeasures for internet of things networks: A comprehensive survey. IEEE Access 2021, 9, 94668–94690. [Google Scholar] [CrossRef]
- Raza, M.; Bukht, T.; Ali, M.; Rehman, A.U.; Idrees, M. Analyzing the Behaviour of DDOS Cyber Attacks. Tech. J. 2021, 26, 46. [Google Scholar]
- Najmi, K.; AlZain, M.; Masud, M.; Jhanjhi, N.Z.; Al-Amri, J.; Baz, M. A Survey on Security Threats and Countermeasures in IoT to Achieve Users Confidentiality and Reliability. Available online: https://www.sciencedirect.com/science/article/pii/S221478532102469X (accessed on 24 June 2022).
- Khalid, L.; Ameen, S. Secure Iot integration in daily lives: A review. J. Inf. Technol. Inform. 2021, 1, 6–12. [Google Scholar]
- Hassija, V.; Chamola, V.; Bajpai, B.C.; Zeadally, S. Security issues in implantable medical devices: Fact or fiction? Sustain. Cities Soc. 2021, 66, 102552. [Google Scholar] [CrossRef]
- Ahmad, I.; Niazy, M.; Ziar, R.; Khan, S. Survey on IoT: Security threats and applications. J. Robot. Control 2021, 2. [Google Scholar] [CrossRef]
- Nayak, P.; Mohapatra, S.K.; Sharma, S.C.M. Privacy and Security Issues in IoT Cloud Convergence of Smart Health Care; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Chatterjee, U.; Ray, S. Security Issues on IoT Communication and Evolving Solutions. Stud. Comput. Intell. 2022, 988, 183–204. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Bayramov, S.; Kiani Kalejahi, B. Internet of Things Applications: Opportunities and Threats. Wirel. Pers. Commun. 2022, 122, 451–476. [Google Scholar] [CrossRef]
- Balogh, Z.; Francisti, J.; Fodor, K. Effectiveness of Selected Wireless Sensor Protocols and Their Security. Available online: https://www.researchgate.net/profile/Kristian_Fodor2/publication/361189368_Effectiveness_of_Selected_Wireless_Sensor_Protocols_and_Their_Security/links/62a1f80955273755ebe071b5/Effectiveness-of-Selected-Wireless-Sensor-Protocols-and-Their-Security.pdf (accessed on 24 June 2022).
- Kalra, V.; Rahi, S.; pawar, N.; Tanwar, P.; Sharma, M.S. A Tour Towards the Security Issues of Mobile Cloud Computing: A Survey. Lect. Notes Electr. Eng. 2022, 875, 577–589. [Google Scholar] [CrossRef]
- Chaudhary, M.M.; Biswas, S.S.; Nafis, M.T.; Tanweer, S. Study of Security Issues on Open Channel. Smart Sustain. Approaches Optim. Perform. Wirel. Netw. 2022, 279–282. [Google Scholar] [CrossRef]
- Chaudhary, M.; Biswas, S.; Nafis, M.; Tanweer, S. Study of Security Issues on Open Channel; Wiley Online Library: Hoboken, NJ, USA, 2022. [Google Scholar]
- Pico-Valencia, P.; Holgado-Terriza, J.A. Agentification of the Internet of Things: A systematic literature review. Int. J. Distrib. Sens. Netw. 2018, 14. [Google Scholar] [CrossRef]
- Neware, R.; Ulabhaje, K.; Karemore, G.; Lokhande, H.; Dandige, V. Survey on Security Issues in Mobile Cloud Computing and Preventive Measures. Adv. Intell. Syst. Comput. 2020, 767, 89–100. [Google Scholar] [CrossRef]
- Butun, I.; Osterberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutorials 2020, 22, 616–644. [Google Scholar] [CrossRef]
- Li, Y.; Yu, Y.; Susilo, W.; Hong, Z.; Guizani, M. Security and Privacy for Edge Intelligence in 5G and Beyond Networks: Challenges and Solutions. IEEE Wirel. Commun. 2021, 28, 63–69. [Google Scholar] [CrossRef]


| Network Attacks | Characteristics and Features |
|---|---|
| IP Spoofing | Falsification of IP address |
| IP Hijacking | Impersonation of a legitimate users IP address |
| Smurf Attack | Paralyzation of a network by launching a huge number of ICMP requests |
| Transport Attacks | Characteristics and Features |
|---|---|
| TCP Flooding | Sending a huge number of ping requests |
| UDP Flooding | Launching an overwhelming number of UDP Packets |
| TCP Sequence Prediction Attack | Fabrication of a legitimate users data packets using the predicted TCP sequence index. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, A.U.; Mahmood, M.S.; Zafar, S.; Raza, M.A.; Qaswar, F.; Aljameel, S.S.; Khan, I.U.; Aslam, N. A Survey on MAC-Based Physical Layer Security over Wireless Sensor Network. Electronics 2022, 11, 2529. https://doi.org/10.3390/electronics11162529
Rehman AU, Mahmood MS, Zafar S, Raza MA, Qaswar F, Aljameel SS, Khan IU, Aslam N. A Survey on MAC-Based Physical Layer Security over Wireless Sensor Network. Electronics. 2022; 11(16):2529. https://doi.org/10.3390/electronics11162529
Chicago/Turabian StyleRehman, Attique Ur, Muhammad Sajid Mahmood, Shoaib Zafar, Muhammad Ahsan Raza, Fahad Qaswar, Sumayh S. Aljameel, Irfan Ullah Khan, and Nida Aslam. 2022. "A Survey on MAC-Based Physical Layer Security over Wireless Sensor Network" Electronics 11, no. 16: 2529. https://doi.org/10.3390/electronics11162529
APA StyleRehman, A. U., Mahmood, M. S., Zafar, S., Raza, M. A., Qaswar, F., Aljameel, S. S., Khan, I. U., & Aslam, N. (2022). A Survey on MAC-Based Physical Layer Security over Wireless Sensor Network. Electronics, 11(16), 2529. https://doi.org/10.3390/electronics11162529






