Abstract
Due to the broadcast nature of wireless communication, it is vulnerable to malicious jamming attacks. Meanwhile, multiple users need to share the limited spectrum resources to enhance the spectrum utilization efficiency because of the scarcity of wireless spectrum resources. Therefore, wireless communication systems need to deal with the malicious jamming attacks and mutual interference among different users. In this paper, a multi-user anti-jamming grouping approach based on a coalition formation game is studied. The proposed approach can maximize users’ transmission rate while avoiding channel jamming through optimization of the coalition formation strategy under the influence of malicious jamming. With the help of the exact potential energy game, we demonstrate that the proposed game model can obtain stable Nash equilibrium solutions. Lastly, the effectiveness of the proposed algorithm is demonstrated through numerical.
1. Introduction
Due to the shared and open nature of its propagation medium, wireless communication is extremely vulnerable to malicious interference attacks, which will significantly reduce the reliability and effectiveness of information transmission; in extreme cases, the communication may be interrupted [1]. Traditional communication anti-jamming technologies mainly include direct sequence spread spectrum technology (DSSS) and frequency hopping spread spectrum technology (FHSS). These technologies were proven to be effective for certain anti-jamming solutions. However, with the development of user-dense complicated electromagnetic environments, the requirements of reliable communication are becoming harder and harder to be guaranteed by simply using those direct expansion and frequency hopping technologies. Therefore, considering the behavior of both communication and jamming, and then improving the communication strategy and improving the communication reliability in the jamming environment have become urgent problems to be solved.
The communication anti-jamming process is actually a game process between the wireless communication system and the jammer; therefore, the game theory used in anti-jamming technologies has attracted wide research interest [2,3,4]. In the existing literature, methods such as Stackelberg game [5], stochastic learning theory [6], and reinforcement learning [7,8,9] have been studied, from the aspects of frequency and power By building a game model between communication and jamming, and by implementing a continuous trial-and-error method to avoid jamming, the optimal communication anti-jamming strategy was determined. In ref. [10], the Stackelberg game was applied to obtain the optimal hopping speed and the optimal transmitting power for a legal transmitter. In ref. [6], using the potential game model and random learning theory, a kind of anti-jamming channel selection algorithm was proposed to reduce the effects of external and internal entangled malicious interference. In ref. [11], a joint channel and power allocation algorithm based on the Stackelberg game was proposed to improve the transmission performance of other users by sacrificing the transmission performance of some users in order to deceive the interferer. In ref. [12], a stochastic zero-sum game was applied using a maximum–minimum Q learning algorithm to obtain the optimal spectrum policy The authors of ref. [13] used the transfer knowledge of the dual game phase to accelerate the learning process and improve the performance of channel selection. The authors of refs. [14,15] studied the joint anti-jamming problem of routing, channel assignment, and power control using reinforcement learning and the Stackelberg game. In ref. [16], a multidomain joint anti-jamming intelligent decision algorithm was proposed to derive the optimal transmit power of the system by considering the anti-jamming in both the frequency and the power domains. However, as a branch of game theory, the coalition formation game has rarely been applied in this field. In a coalition game, a coalition is a group of independent agents or players who can cooperate to increase their respective benefits. The authors of refs. [17,18,19] showed that the coalition formation game can be an applicable solution to realize reliable communication in UAV swarm scenarios, but its application in the field of anti-jamming in the multi-user frequency scenario remains rare.
In order to improve the effectiveness and reliability of multi-user transmission in a jammed environment, and effectively deal with the external malicious jamming threat and the frequency mutual interference problem within the multi-user scenario, a multi-user distributed anti-jamming coalition formation algorithm is proposed. The proposed algorithm can maximize the user’s transmission rate by avoiding the disturbed channel, as well as reduce the users’ mutual interference within the coalition by optimizing the coalition grouping strategy. At the same time, the proposed algorithm can realize efficient and intelligent anti-jamming decision making for multi-user networks in a low-complexity and distributed manner.
The remainder of this article is organized as follows: the system model and problem formulation are shown in Section 2. Section 3 illustrates the proposed game framework. The multi-user distributed anti-jamming coalition formation algorithm is studied in Section 4. Section 5 gives the simulation results and an analysis of the proposed game model. Lastly, the conclusions are given in Section 6. In addition, some key notations are shown in Table 1.

Table 1.
Summation of notations.
2. System Model and Problem Formulation
2.1. System Model
Figure 1 presents the system model. In this model, we assume that the wireless communication network consists of legitimate users, and all users share L channels, where channels have a bandwidth of B. The users can continuously sense the channel where the jammer is located, and each user is also equipped with a positioning device to obtain the location information of other users.

Figure 1.
Schematic diagram of system model.
Under the threat of jamming, some of the channels may be affected. When a user selects a jammed channel, its transmission rate can be severely reduced. On the other hand, if multiple users select the same channel at the same time, their mutual interference will increase. Therefore, in order to improve the transmission performance under a jamming environment, a few users can form a group and select the same channel. This group needs to reasonably select a channel, which can improve the overall transmission rate. The group formation, however, is limited by the channel selection. The group of users can be represented as
where is the n-th coalition, and is the potential of the set.
2.2. Problem Formulation
According to the analysis of the system model, the transmission rate of the user is defined as
where , , and are the user’s transmission power, channel bandwidth, and channel noise, respectively. is the channel gain, where is the instantaneous random quantity, and . is the jamming power, and the jamming channel gain is , where is the distance between the jammer and the user . is the mutual interference between users using the same channels.
As stated previously, under the jamming environment, spectrum resources are even more limited; if each user selects a channel, this may lead to the waste of spectrum resources. On the other hand, if a group of users selects the same channel for transmission, it will increase the mutual interference between them. Thus, the key issue here is choosing the best group strategy to maximize the users’ transmission rate while minimizing the mutual interference among the users in the group.
This problem can be formulated as follows:
where is the number of coalitions, is the sum rate of , and is the sum rate of all users.
3. Users Coalition Formation Game
On the basis of the system model presented in Section 2, we modeled the group formation problem of users as a coalition formation game [20]. In order to define the problem clearly, we propose some definitions.
Definition 1.
(Coalition formation game): The set of userscan be divided into multiple nonoverlapping coalitions,
. Each user has its own coalition preference profile, ,
denoting the preference relation of userchoosing to join a coalition; thus, the strategyconsists of the coalition formation game.
The set of users is divided into some groups according to the number of channels, i.e., users who choose the same channel for transmission make up a group. In other words, users within the same group form a coalition. The maximum sum rate of the coalition is defined as
In a network with jamming, a user expects to improve the transmission rate by forming a coalition with other users. In this paper, we take the transmission rate of the user after joining the coalition and the total transmission rate of the coalition as the metrics to evaluate the proposed scheme and the algorithm. The user selects the coalition utility, which can be defined as
where is the total sum rate of the coalition after joining the coalition . is used to describe the increase in the total transmission rate of the coalition due to the user selecting the coalition .
During the coalition formation, its preference order and the rules for the change of criterion can affect the performance of the coalition formation game based on the algorithm. The preference order represents the preference of each user for each coalition, and the rules for the change in coalition represent the rules adopted by the users to change their current coalition to explore other coalitions for better transmission rate.
(1) Coalition preference order: For , each user can choose to join or leave the coalition according to their preference. That is, given two coalitions and , if the utility of a user joining is higher than that of joining , then indicates a preference for joining coalition . The Pareto order is the commonly used coalition preference criterion.
If the coalition adopts the Pareto order, the user and the coalition formations satisfy the following equation:
where is the utility of coalition , and is the utility of all the users except for .
According to the Pareto order, the coalition choice of each user cannot harm the utility of any other user. Therefore, the coalition change of any user cannot harm the utility of other users, and the transmission rate of all users will not be further increased by the coalition change of each user.
(2) Coalition change rule: When the user can achieve higher utility, they will leave the current coalition and join a new coalition to get higher benefits. The reciprocity order is proposed here.
Definition 2.
(Reciprocity order): Users select a coalition according to the reciprocity order. If the coalition of a user, the selection is changed tofrom, and then the sum utility of the other users in the original coalitionand the users in the new coalition increases to, thereby establishing the coalition change.
where is the sum rate of .
Definition 3.
(Stable coalition formation): A coalition formation schemeis said to be stable if no user can improve their own game utility by changing their coalition formation strategy unilaterally.
where represents the coalition selections of other users except .
Theorem 1.
The proposed coalition formation game yields a stable coalition formation result which is a Nash equilibrium solution.
Proof of Theorem 1.
From the definition of the reciprocity order, it follows that, each time a user changes the chosen coalition, this further increases the total sum rate of the old and new coalitions, thus further increasing the total sum rate of all users. Since the number of users and channels is finite, the sum rates of all users eventually converge to a great value, and a stable coalition formation strategy is obtained. □
Definition 4.
(Exact potential game): A game is an exact potential game if there exists a potential functionfor a userthat satisfies the below equation when the user’s strategy changes, i.e., when the coalition chosen to joinchanges from to. The exact potential game model has at least one pure strategy Nash equilibrium solution.
Next, it is shown that the obtained stable coalition formation strategy is a Nash equilibrium solution. Starting from the definition of the exact potential game, the potential function is defined as the sum rate of all coalitions in total.
When the user choice of coalition changes from to , the change in utility function is
Since the change in the user’s coalition only affects and , and has no effect on other coalitions, the following expression can be easily obtained:
The change in users’ potential function is expressed as
Since , the proposed coalition formation game is an exact potential game; thus, it has at least one stable Nash equilibrium solution.
4. Distributed Federation Formation Algorithm for Multiple Users
According to the analysis results in Section 3, the group formation problem of users is modeled as a coalition formation game. Considering the jamming from the jammer and the mutual interference between users, the coalition group formation among users minimizes the selection of the channel subject to jamming by users, while coordinating the mutual interference between users in the coalition, so as to further improve the transmission rate of users and reduce the impact of interference on the transmission rate of users.
“Merge” and “split” rules are proposed to construct distributed coalition formation algorithms [21].
- Merge rule: when the user prefers to merge, then any set of coalitions is merged, where and then .
- Split rules: when a user preference splits, any coalition is split, , and then .
Considering the coalition utility and reciprocity order defined in Section 3, as well as the “merge” and “split” rules, a multi-user distributed anti-jamming coalition formation algorithm (MDACF) suited for the proposed game is constructed in Algorithm 1, in which each user makes a coalition selection as a function of the defined coalition utility and order. According to the MDACF algorithm, the user selects the better coalition from the set of available channels. Specifically, according to the “merge” and “split” rules, the user chooses whether to join other neighboring coalition. On the basis of the reciprocity order, the user calculates the utility and decides whether to change the current coalition.
The steps of the MDACF are shown below.
| Algorithm 1 Multi-user distributed anti-jamming coalition formation algorithm (MDACF) |
| Input: the current position of each user and the position of the jammer Initialize the coalition grouping. Each user randomly selects a channel for transmission to obtain the user’s coalition grouping. For do Randomly select a user, calculate the total transmission rate of its coalition, and the coalition utility of that user is calculated according to Equation (6). Choose to join other nearby coalitions according to the “Merge” and “Split” rules, and calculate the new coalition utility. According to the reciprocity order, if Equation (8) is satisfied, the user can obtain higher coalition utility; then, change the coalition; otherwise, maintain the current coalition. end for Output: coalition grouping results for users |
The computational complexity of the MDACF algorithm is analyzed below. Assuming that a stable user partition is achieved after iterations, i.e., a stable coalition formation, the computational complexity mainly lies in the process of each user selecting a coalition, whose scalar multiplication cost is , where is the number of coalitions that the user u can select.
5. Simulation Result and Analysis
5.1. Parameter Settings
In this section, simulations were carried out to investigate the performance of the proposed scheme using the MATLAB platform. We set the parameters related to simulation as shown in Table 2.

Table 2.
Settings of model-related parameters.
5.2. Analysis of Simulation
The red curve in Figure 2 shows the change in user transmission rate during the coalition formation game. As the iteration proceeds, the user’s sum rate increases significantly and eventually converges to a stable value, and the obtained results are consistent with the results of the game analysis in Section 3. The performance is significantly better than that of the direct transmission algorithm. The black curve in Figure 2 is the optimal solution obtained by the traversal method, which shows that the proposed algorithm is close to the optimal solution.
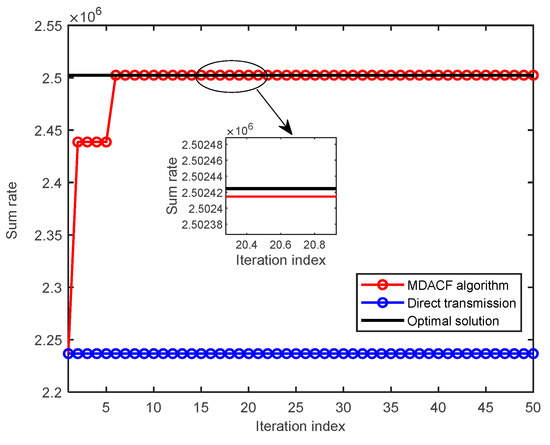
Figure 2.
Schematic diagram of the comparison of different algorithms.
In order to maximize the transmission rate of users, cooperative transmission is implemented among users through coalition groups. The users forming a coalition use the same channel for transmission. The jammer is located at the origin of the coordinates. Assuming that the initialized coalitions are , where , , and , and coalition 1 is the channel 1 subject to jamming.
Figure 3 shows the selection results after the formation of the users’ coalition group. It can be seen that most of the users in channel 1 subject to jamming during initialization leave coalition 1 and join other coalitions, thus avoiding jamming. Furthermore, adopting the coalition strategy reduces the mutual interference among users.

Figure 3.
Schematic diagram of the change in coalition before and after using the MDACF algorithm: (a) before using MDACF algorithm; (b) after using MDACF algorithm.
Figure 4 compares the sum rates under different coalition preference orders. From the figure, it can be seen that the convergence rate under the reciprocity order proposed in this paper is faster than the Pareto order and the selfish order, and the sum rate is also significantly higher. This is because, when forming a coalition according to the Pareto order, each user’s order choice cannot harm the utility of any other user, while users under the selfish order make coalition choices only concerned with their own utility. Thus, it has a higher probability of obtaining better utility compared to the Pareto order.
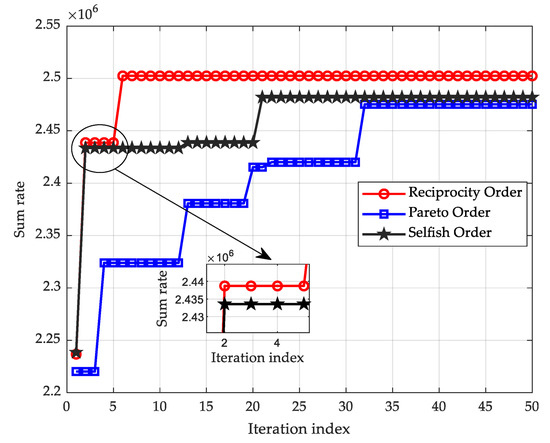
Figure 4.
Schematic representation of the performance comparison of different coalition preference orders.
Figure 5 shows the effect of jamming power on the proposed algorithm. It is clear from the figure that, as the jamming power increases, the user’s sum rate is reduced. Compared with the Pareto order, the degradation of the MDACF algorithm is smaller than the Pareto order as the jamming power increases, indicating that the proposed MDACF algorithm can still obtain a higher transmission rate at a higher jamming power, thus achieving a better performance.

Figure 5.
Schematic representation of the effect of interference power on the proposed algorithm.
Figure 6 shows the sum utilities of different coalition preference orders when the number of users increases from 10 to 20. As shown in Figure 6, on the one hand, the sum utility of the proposed reciprocity order is greater than the Pareto order and the selfish order; on the other hand, the sum utility increases with the number of users. Since each additional user within the coalition increases the transmission rate of that user, the sum utility increases with the number of users.
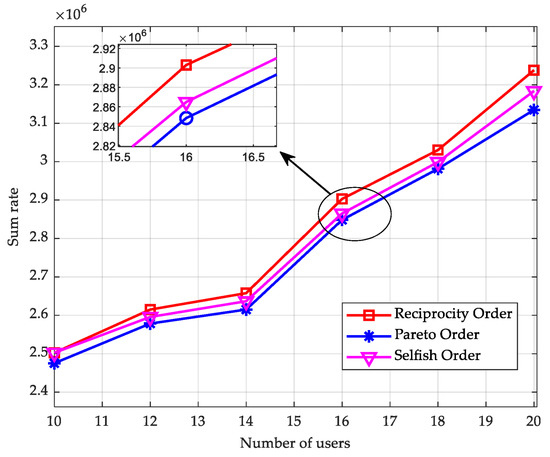
Figure 6.
Schematic representation of the impact of the number of users on the performance of the proposed algorithm.
Furthermore, we also compare the change in coalition utility when the number of coalitions increases with a constant number of users. As shown in Figure 7, as the number of coalitions increases, the sum utility of the coalition also increases. Because the number of coalitions increases for the same number of users, i.e., the number of channels increases, then the number of channels available for the same interference conditions also increases and the transmission rate increases. Moreover, due to the increase in the number of channels, the number of users using the same frequency band decreases, reducing the mutual interference between users, which also increases the transmission rate of users.
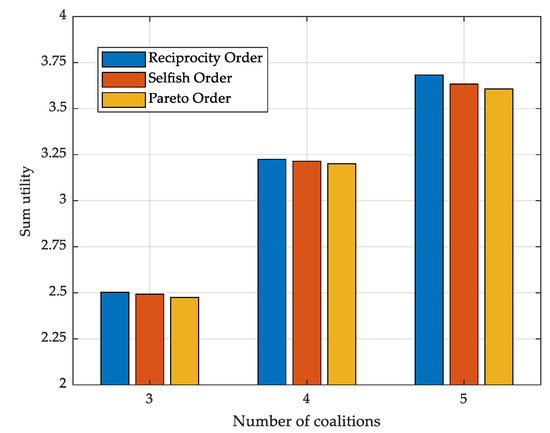
Figure 7.
Schematic representation of the impact of the number of coalitions on the performance of the proposed algorithm.
6. Conclusions
In this paper, we studied a multi-user anti-interference grouping method under the threat of the jamming and proposed a multi-user distributed anti-jamming coalition formation algorithm. By optimizing the grouping strategy of users, an efficient distributed cooperative spectrum decision was achieved, which reduced both the external malicious jamming threat and the co-channel mutual interference among users. With the help of potential game theory, it was demonstrated that the proposed anti-interference coalition formation game could achieve stable coalition grouping and could obtain Nash equilibrium solutions. Lastly, the simulation results indicated that the proposed algorithm performed better than the existing approaches in anti-interference communication decisions. In the future study, more intelligent jammers will implement multidomain cooperative jamming for the weak links of the communication network; in this scenario, the communication system also needs to realize multidomain cooperative resource scheduling and parameter optimization.
Author Contributions
Methodology, H.D. and C.H.; writing—original draft, H.D.; software, H.D.; supervision, Y.N.; writing—review and editing, H.D. and P.X.; validation, H.D. and C.H.; funding acquisition, Y.N.; project administration, Y.N. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Science Foundation of China (NSFC grant: U19B2014).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yao, F. Communication Anti-jamming Engineering and Practice; Electronic Industry Press: Beijing, China, 2012. (In Chinese) [Google Scholar]
- Jia, L.; Qi, N.; Chu, F.; Fang, S.; Wang, X.; Ma, S.; Feng, S. Game-Theoretic Learning Anti-Jamming Approaches in Wireless Networks. IEEE Commun. Mag. 2022, 60, 60–66. [Google Scholar] [CrossRef]
- Liang, X.; Xiao, Y. Game Theory for Network Security. IEEE Commun. Surv. Tutor. 2013, 15, 472–486. [Google Scholar] [CrossRef] [Green Version]
- Sun, Y.; Zhu, Y.; An, K.; Zheng, G.; Chatzinotas, S.; Wong, K.K.; Liu, P. Robust Design for RIS-Assisted Anti-Jamming Communications with Imperfect Angular Information: A Game-Theoretic Perspective. IEEE Trans. Veh. Technol. 2022, 71, 1–6. [Google Scholar] [CrossRef]
- Jia, L.; Yao, F.; Sun, Y.; Niu, Y.; Zhu, Y. Bayesian Stackelberg Game for Antijamming Transmission with Incomplete Information. IEEE Commun. Lett. 2016, 20, 1991–1994. [Google Scholar] [CrossRef]
- Jia, L.; Xu, Y.; Sun, Y.; Feng, S.; Yu, L.; Anpalagan, A. A Game-Theoretic Learning Approach for Anti-Jamming Dynamic Spectrum Access in Dense Wireless Networks. IEEE Trans. Veh. Technol. 2019, 68, 1646–1656. [Google Scholar] [CrossRef]
- Xiao, L.; Ding, Y.; Huang, J.; Liu, S.; Tang, Y.; Dai, H. UAV Anti-Jamming Video Transmissions with QoE Guarantee: A Reinforcement Learning-Based Approach. IEEE Trans. Commun. 2021, 69, 5933–5947. [Google Scholar] [CrossRef]
- Zhou, Q.; Li, Y.; Niu, Y. Intelligent Anti-Jamming Communication for Wireless Sensor Networks: A Multi-Agent Reinforcement Learning Approach. IEEE Open J. Commun. Soc. 2021, 2, 775–784. [Google Scholar] [CrossRef]
- Zhou, Q.; Li, Y.; Niu, Y. A Countermeasure Against Random Pulse Jamming in Time Domain Based on Reinforcement Learning. IEEE Access 2020, 8, 97164–97174. [Google Scholar] [CrossRef]
- Li, Y.; Bai, S.; Gao, Z. A Multi-Domain Anti-Jamming Strategy Using Stackelberg Game in Wireless Relay Networks. IEEE Access 2020, 8, 173609–173617. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, Y.; Xu, Y.; Yang, Y.; Luo, Y.; Wu, Q.; Liu, X. A Multi-Leader One-Follower Stackelberg Game Approach for Cooperative Anti-Jamming: No Pains, No Gains. IEEE Commun. Lett. 2018, 22, 1680–1683. [Google Scholar] [CrossRef]
- Wang, B.; Wu, Y.; Liu, K.R.; Clancy, T.C. An Anti-Jamming Stochastic Game for Cognitive Radio Networks. IEEE J. Sel. Areas Commun. 2011, 29, 877–889. [Google Scholar] [CrossRef] [Green Version]
- Thien, H.T.; Vu, V.; Koo, I. A Transfer Games Actor-Critic Learning Framework for Anti-Jamming in Multi-Channel Cognitive Radio Networks. IEEE Access 2021, 9, 47887–47900. [Google Scholar] [CrossRef]
- Han, C.; Niu, Y. Joint Anti-interference Algorithm Based Hierarchical Q-learning. Comput. Eng. 2019, 45, 279–284. [Google Scholar]
- Han, C.; Niu, Y. Cross-Layer Anti-Jamming Scheme: A Hierarchical Learning Approach. IEEE Access 2018, 6, 34874–34883. [Google Scholar] [CrossRef]
- Li, M.; Ren, Q.; Wu, J. UAV Multi-domain Joint Anti-interference Intelligent Decision Algorithm Research. J. Northwest. Polytech. Univ. 2021, 39, 367–374. [Google Scholar] [CrossRef]
- Han, C.; Liu, L.; An, K.; Tong, X.; Liang, X. A Game-theoretic-based Approach to UAV Swarm Deployment and Networking in a Jammed Environment. J. Electron. Inf. 2022, 44, 860–870. (In Chinese) [Google Scholar]
- Chen, J.; Wu, Q.; Xu, Y.; Qi, N.; Guan, X.; Zhang, Y.; Xue, Z. Joint Task Assignment and Spectrum Allocation in Heterogeneous UAV Communication Networks: A Coalition Formation Game-Theoretic Approach. IEEE Trans. Wirel. Commun. 2021, 20, 440–452. [Google Scholar] [CrossRef]
- Han, C.; Liu, A.; Wang, H.; Huo, L.; Liang, X. Dynamic Anti-Jamming Coalition for Satellite-Enabled Army IoT: A Distributed Game Approach. IEEE Internet Things J. 2020, 7, 10932–10944. [Google Scholar] [CrossRef]
- Saad, W.; Han, Z.; Debbah, M.; Hjorungnes, A.; Basar, T. Coalitional Game Theory for Communication Networks. IEEE Signal Process. Mag. 2009, 26, 77–97. [Google Scholar] [CrossRef] [Green Version]
- Saad, W.; Han, Z.; Debbah, M.; Hjorungnes, A.; Basar, T. Coalitional Games for Distributed Collaborative Spectrum Sensing in Cognitive Radio Networks. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2009, 9, 2114–2122. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).