Extending the Frontiers of Electronic Commerce Knowledge through Cybersecurity
Abstract
:1. Introduction
2. Materials and Methods
2.1. Data Collection
2.2. Project Configuration
2.3. Analysis Method
3. Results
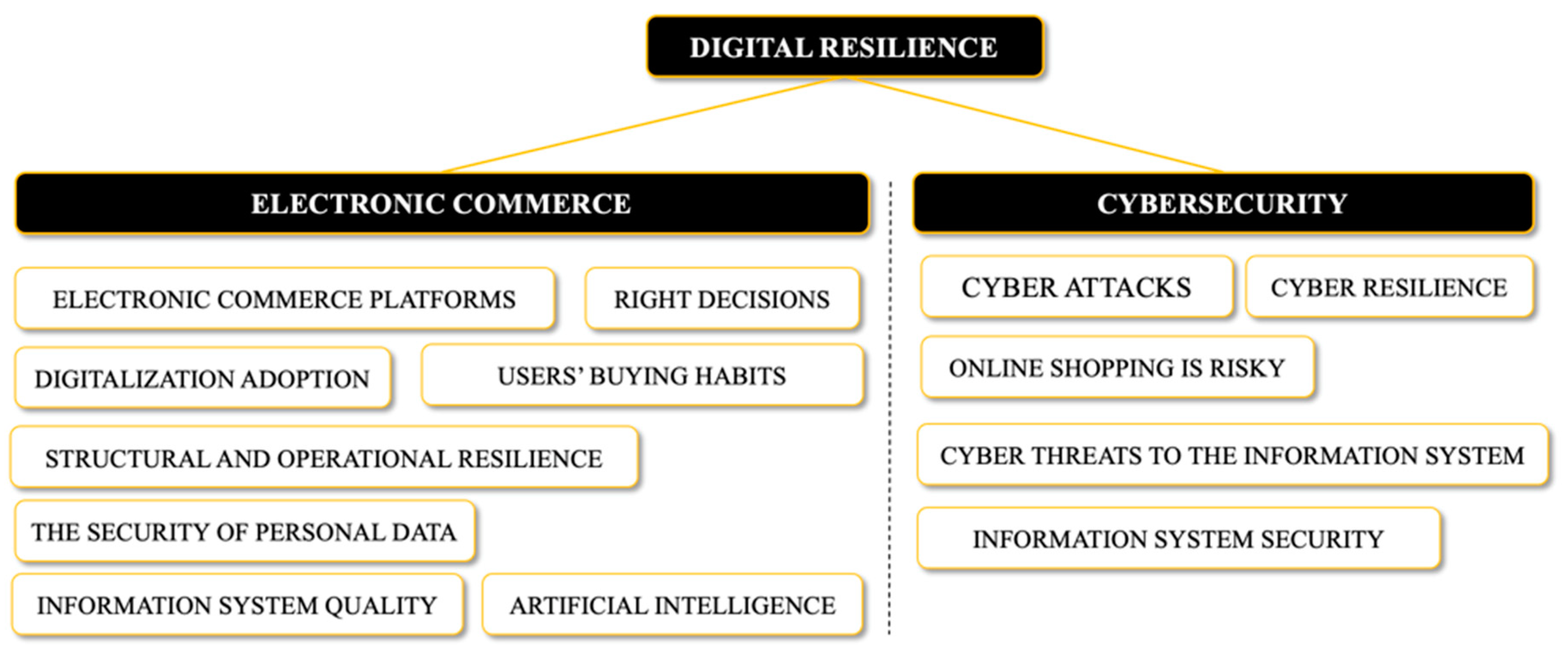
3.1. Electronic Commerce
3.2. Cybersecurity
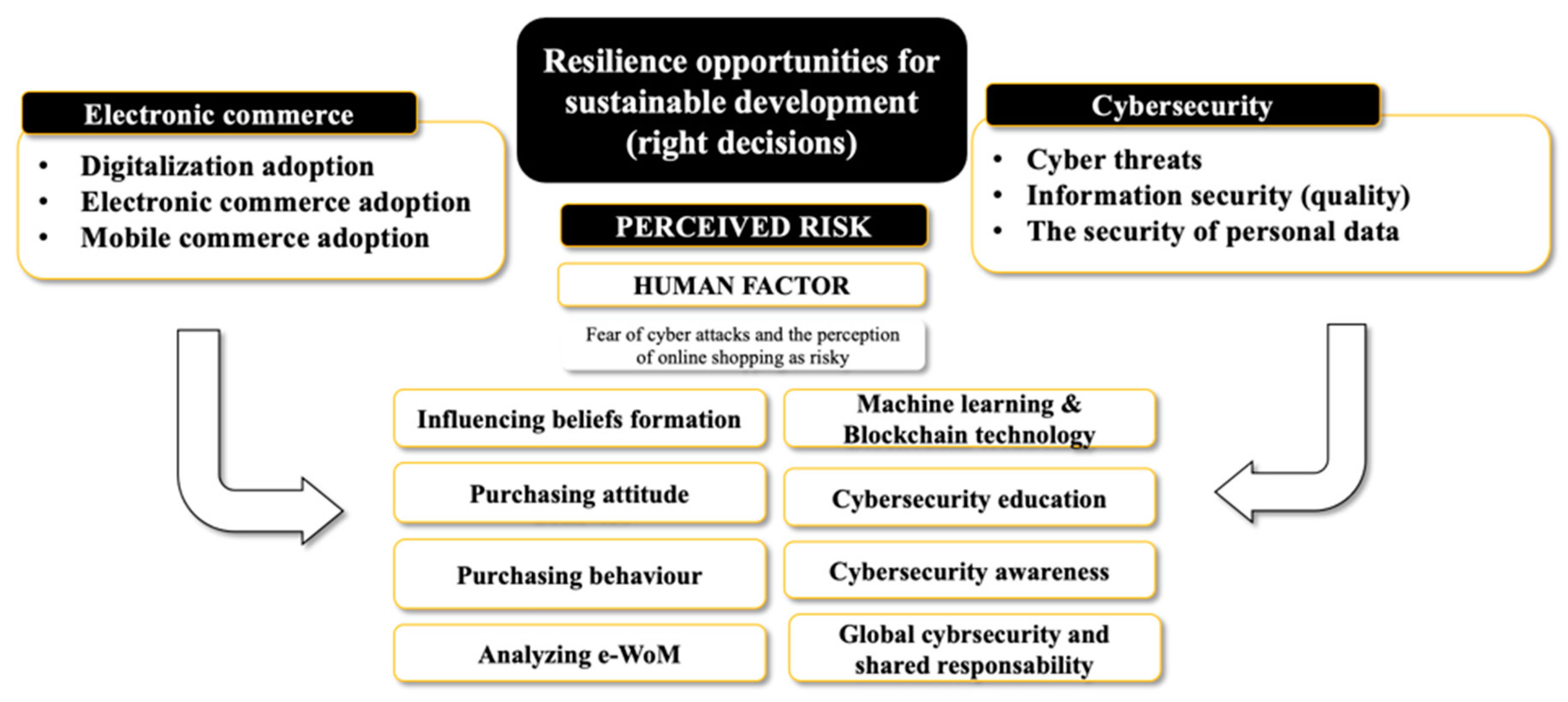
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Scutariu, A.-L.; Șuşu, Ș.; Huidumac-Petrescu, C.-E.; Gogonea, R.-M. A Cluster Analysis Concerning the Behavior of Enterprises with E-Commerce Activity in the Context of the COVID-19 Pandemic. J. Theor. Appl. Electron. Commer. Res. 2021, 17, 47–68. [Google Scholar] [CrossRef]
- CSA Singapore. Ransomware Incidents, Online Scams, and COVID-19-Related Phishing Activities Dominated Cyber Landscape in 2020. Available online: https://www.csa.gov.sg/News/Press-Releases/ransomware-incidents-online-scams-and-covid19-related-phishing-activities-dominated-cyber-landscape-in-2020 (accessed on 10 February 2022).
- D’Adamo, I.; González-Sánchez, R.; Medina-Salgado, M.S.; Settembre-Blundo, D. E-Commerce Calls for Cyber-Security and Sustainability: How European Citizens Look for a Trusted Online Environment. Sustainability 2021, 13, 6752. [Google Scholar] [CrossRef]
- Craigen, D.; Diakun-Thibault, N.; Purse, R. Defining Cybersecurity. Technol. Innov. Manag. Rev. 2014, 4, 13–21. [Google Scholar] [CrossRef]
- Ukhanova, E. Cybersecurity and cyber defence strategies of Japan. SHS Web Conf. 2022, 134, 00159. [Google Scholar] [CrossRef]
- Uniunea Europeana. Next Generation EU. Available online: https://europa.eu/next-generation-eu/index_ro (accessed on 10 February 2022).
- Dirgantari, P.D.; Hidayat, Y.M.; Mahphoth, M.H.; Nugraheni, R. Level of Use and Satisfaction of E-Commerce Customers in Covid-19 Pandemic Period: An Information System Success Model (ISSM) Approach. Indones. J. Sci. Technol. 2020, 5, 261–270. [Google Scholar] [CrossRef]
- Hailu, T. The Impact of Information System (IS) on Organziational Performace: With Special Refernce to Ethio-Telecom Southern Region, Hawassa. Eur. J. Bus. Manag. 2014, 6, 331–338. [Google Scholar]
- Salem, A.M.; Yaser, H.; Shamsuddin, A.; Aziati, A. The Role of Different Types of Information Systems in Business Organization: A Review. Int. J. Res. 2014, 1, 1279–1286. [Google Scholar]
- Setyowati, W.; Widayanti, R.; Supriyanti, D. Implementation Of E-Business Information System in Indonesia: Prospects And Challenges. Int. J. Cyber IT Serv. Manag. (IJCITSM) 2021, 1, 180–188. [Google Scholar] [CrossRef]
- Spagnoletti, P.; Ceci, F.; Bygstad, B. Online Black-Markets: An Investigation of a Digital Infrastructure in the Dark. Inf. Syst. Front. 2021, 9, 10187. [Google Scholar] [CrossRef]
- Carias, J.F.; Borges, M.R.S.; Labaka, L.; Arrizabalaga, S.; Hernantes, J. Systematic Approach to Cyber Resilience Operationalization in SMEs. IEEE Access 2020, 8, 174200–174221. [Google Scholar] [CrossRef]
- van Haastrecht, M.; Ozkan, B.Y.; Brinkhuis, M.; Spruit, M. Respite for SMEs: A Systematic Review of Socio-Technical Cybersecurity Metrics. Appl. Sci. 2021, 11, 6909. [Google Scholar] [CrossRef]
- Modgil, S.; Singh, R.K.; Hannibal, C. Artificial intelligence for supply chain resilience: Learning from Covid-19. Int. J. Logist. Manag. 2021. ahead-of-print. [Google Scholar] [CrossRef]
- Dobson, S.; Hutchison, D.; Mauthe, A.; Schaeffer-Filho, A.; Smith, P.; Sterbenz, J.P.G. Self-Organization and Resilience for Networked Systems: Design Principles and Open Research Issues. Proc. IEEE 2019, 107, 819–834. [Google Scholar] [CrossRef] [Green Version]
- Lezzi, M.; Lazoi, M.; Corallo, A. Cybersecurity for Industry 4.0 in the current literature: A reference framework. Comput. Ind. 2018, 103, 97–110. [Google Scholar] [CrossRef]
- Jbair, M.; Ahmad, B.; Maple, C.; Harrison, R. Threat modelling for industrial cyber physical systems in the era of smart manufacturing. Comput. Ind. 2022, 137, 103611. [Google Scholar] [CrossRef]
- Cavallo, C.; Sacchi, G.; Carfora, V. Resilience effects in food consumption behaviour at the time of Covid-19: Perspectives from Italy. Heliyon 2020, 6, e05676. [Google Scholar] [CrossRef]
- Guthrie, C.; Fosso-Wamba, S.; Arnaud, J.B. Online consumer resilience during a pandemic: An exploratory study of e-commerce behavior before, during and after a COVID-19 lockdown. J. Retail. Consum. Serv. 2021, 61, 102570. [Google Scholar] [CrossRef]
- Kirk, C.P.; Rifkin, L.S. I’ll trade you diamonds for toilet paper: Consumer reacting, coping and adapting behaviors in the COVID-19 pandemic. J. Bus. Res. 2020, 117, 124–131. [Google Scholar] [CrossRef]
- Hamilton, R.W.; Mittal, C.; Shah, A.; Thompson, D.V.; Griskevicius, V. How Financial Constraints Influence Consumer Behavior: An Integrative Framework. J. Consum. Psychol. 2018, 29, 285–305. [Google Scholar] [CrossRef]
- Weller, M.; Anderson, T. Digital resilience in higher education. Eur. J. Open Distance e-Learn. 2013, 16, 53. [Google Scholar]
- IDC. Digital Resiliency. Redefining Resiliency. 2020. Available online: https://www.idc.com/eu/research/key-trends/digital-resiliency (accessed on 27 June 2022).
- European Central Bank. What is Cyber Resilience? Available online: https://www.ecb.europa.eu/paym/cyber-resilience/html/index.en.html (accessed on 27 June 2022).
- Han, B.R.; Sun, T.; Chu, L.Y.; Wu, L. COVID-19 and E-Commerce Operations: Evidence from Alibaba. Manuf. Serv. Oper. Manag. 2022, 24, 1388–1405. [Google Scholar] [CrossRef]
- Weber, A.N. Responding to supply chain disruptions caused by the COVID-19 pandemic: A Black Swan event for omnichannel retailers. J. Transp. Supply Chain Manag. 2021, 15, 16. [Google Scholar] [CrossRef]
- Presto, M.M. Evaluating the Significant Role of E-Commerce to the Resiliency of MSMEs During the COVID-19 Pandemic. Ascendens Asia J. Multidiscip. Res. Conf. Proc. 2021, 4. Available online: https://ojs.aaresearchindex.com/index.php/aajmrcp/article/view/533 (accessed on 27 June 2022).
- Costa, J.; Castro, R. SMEs Must Go Online—E-Commerce as an Escape Hatch for Resilience and Survivability. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 3043–3062. [Google Scholar] [CrossRef]
- Appel, A.; Hardaker, S. Strategies in Times of Pandemic Crisis—Retailers and Regional Resilience in Würzburg, Germany. Sustainability 2021, 13, 2643. [Google Scholar] [CrossRef]
- Anatan, L. A review on MSMEs resilience: Strategies and policies post covid-19 pandemic. Rev. Integr. Bus. Econ. Res. 2021, 10, 386–394. [Google Scholar]
- Velimirovic, J.D.; Janjic, A.; Velimirovic, L.Z. Modelling electronic trust using bayesian networks. In Proceedings of the International May Conference on Strategic Management—IMCSM18, Bor, Serbia, 25–27 May 2018; Volume XIV, pp. 460–465. [Google Scholar]
- Charandabi, S.; Ghanadiof, O. Evaluation of Online Markets Considering Trust and Resilience: A Framework for Predicting Customer Behavior in E-Commerce. J. Bus. Manag. Stud. 2022, 4, 23–33. [Google Scholar] [CrossRef]
- Treiblmaier, H.; Mirkovski, K.; Lowry, P.B.; Zacharia, Z.G. The physical internet as a new supply chain paradigm: A systematic literature review and a comprehensive framework. Int. J. Logist. Manag. 2020, 31, 239–287. [Google Scholar] [CrossRef]
- Eslamkhah, M.; Seno, S.A.H. Identifying and Ranking Knowledge Management Tools and Techniques Affecting Organizational Information Security Improvement. Knowl. Manag. Res. Pract. 2019, 17, 276–305. [Google Scholar] [CrossRef]
- Mukherjee, D.; Lim, W.M.; Kumar, S.; Donthu, N. Guidelines for advancing theory and practice through bibliometric research. J. Bus. Res. 2022, 148, 101–115. [Google Scholar] [CrossRef]
- Donthu, N.; Kumar, S.; Mukherjee, D.; Pandey, N.; Lim, W.M. How to conduct a bibliometric analysis: An overview and guidelines. J. Bus. Res. 2021, 133, 285–296. [Google Scholar] [CrossRef]
- Chen, C.; Ibekwe-SanJuan, F.; Hou, J. The structure and dynamics of cocitation clusters: A multiple-perspective cocitation analysis. J. Am. Soc. Inf. Sci. Technol. 2010, 61, 1386–1409. [Google Scholar] [CrossRef] [Green Version]
- Chen, C. CiteSpace: A Practical Guide for Mapping Scientific Literature; Nova Science Publishers: New York, NY, USA, 2016; pp. 41–44. [Google Scholar]
- Molla, A.; Licker, P.S. eCommerce adoption in developing countries: A model and instrument. Inf. Manag. 2005, 42, 877–899. [Google Scholar] [CrossRef]
- Bordonaba-Juste, V.; Cambra-Fierro, J.J. Managing supply chain in the context of SMEs: A collaborative and customized partnership with the suppliers as the key for success. Supply Chain Manag. Int. J. 2009, 14, 393–402. [Google Scholar] [CrossRef]
- Putra, P.O.H.; Santoso, H.B. Contextual factors and performance impact of e-business use in Indonesian small and medium enterprises (SMEs). Heliyon 2020, 6, e03568. [Google Scholar] [CrossRef] [PubMed]
- Li, B.; Yin, Z.; Ding, J.; Xu, S.; Zhang, B.; Ma, Y.; Zhang, L. Key influencing factors of consumers’ vegetable e-commerce adoption willingness, behavior, and willingness-behavior consistency in Beijing, China. Br. Food J. 2020, 122, 3741–3756. [Google Scholar] [CrossRef]
- Fesenmaier, D.R.; Xiang, Z.; Pan, B.; Law, C.H.R. A Framework of Search Engine Use for Travel Planning. J. Travel Res. 2010, 50, 587–601. [Google Scholar] [CrossRef]
- Chatterjee, S.; Goyal, D.; Prakash, A.; Sharma, J. Exploring healthcare/health-product ecommerce satisfaction: A text mining and machine learning application. J. Bus. Res. 2020, 131, 815–825. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Futur. Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Schmitt, M.N. Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Shi, L.; Mai, Y.; Wu, Y.J. Digital Transformation: A Bibliometric Analysis. J. Organ. End User Comput. 2022, 34, 1–20. [Google Scholar] [CrossRef]
- Sarfraz, M. Cybersecurity Threats with New Perspectives; IntechOpen: London, UK, 2021. [Google Scholar] [CrossRef]
- Rai, S.; Singh, K.; Varma, A.K. Global Research Trend on Cyber Security: A Scientometric Analysis. Libr. Philos. Pract. 2019, 3769. [Google Scholar]

| Abbreviation | Meaning |
|---|---|
| Q | Modularity metric |
| LLR | Log-likelihood ratio |
| S | Mean silhouette |
| Topic | Number of Results in Web of Science Core Collection | Citations of the Most Relevant Paper |
|---|---|---|
| Ecommerce | 1570 | 10 |
| Cybersecurity | 10,388 | 8 |
| Digital resilience | 2627 | 14 |
| Cluster ID | Size | Silhouette | Mean (Year) | Label (LLR) |
|---|---|---|---|---|
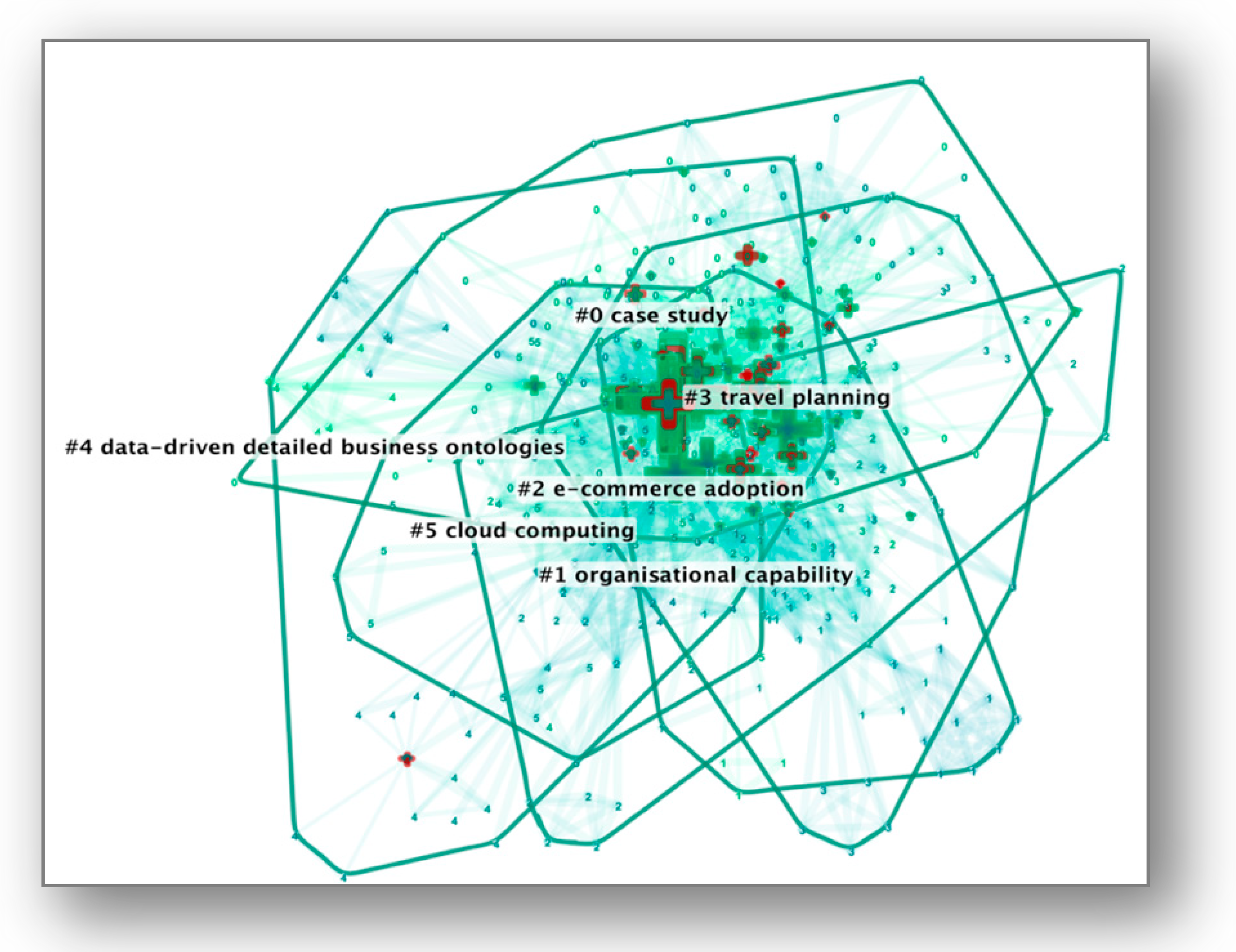
| 1 | 31 | 0.962 | 2016 | e-commerce adoption (18.1, 1.0 × 10−4); influencing beliefs formation (15.79, 1.0 × 10−4); social commerce (15.79, 1.0 × 10−4); SME travel agencies (15.79, 1.0 × 10−4); mobile commerce adoption (13.49, 0.001) |
| 2 | 28 | 1 | 2012 | social media (23.99, 1.0 × 10−4); latent transition analysis (23.99, 1.0 × 10−4); trip experience (23.99, 1.0 × 10−4); tourism design (19.05, 1.0 × 10−4); smart tourism development (14.18, 0.001) |
| 3 | 27 | 0.985 | 2018 | opinion mining (21.68, 1.0 × 10−4); fuzzy logic (21.68, 1.0 × 10−4); salient research topics (17.97, 1.0 × 10−4); analysing e-wom (14.31, 0.001); stochastic dominance (14.31, 0.001) |
| 6 | 22 | 0.978 | 2017 | attention-based item collaborative (21.02, 1.0 × 10−4); fast shipping ecommerce (18.33, 1.0 × 10−4); case study (18.33, 1.0 × 10−4); inbound logistics operation (18.33, 1.0 × 10−4); purchasing attitude (15.65, 1.0 × 10−4) |
| 10 | 18 | 0.978 | 2015 | empirical investigation (22.2, 1.0 × 10−4); big data perspective (22.2, 1.0 × 10−4); online review helpfulness (22.2, 1.0 × 10−4); specific word entropy (17.64, 1.0 × 10−4); purchasing behaviour (13.14, 0.001) |
| Keywords | Strengths | Begin | End | 2000–2022 |
|---|---|---|---|---|
| social media | 5.89 | 2016 | 2019 |  |
| online review | 5.82 | 2020 | 2022 |  |
| destination marketing | 5.59 | 2007 | 2011 |  |
| web service | 4.93 | 2001 | 2005 |  |
| e-commerce | 4.65 | 2011 | 2013 |  |
| social network | 4.64 | 2015 | 2017 |  |
| sentiment analysis | 4.58 | 2018 | 2022 |  |
| information search | 4.34 | 2009 | 2014 |  |
| service | 3.98 | 2019 | 2022 |  |
| web | 3.97 | 2011 | 2017 |  |
| perceived risk | 3.93 | 2018 | 2019 |  |
| data mining | 3.72 | 2012 | 2015 |  |
| purchase intention | 3.61 | 2019 | 2022 |  |
| online shopping | 3.49 | 2014 | 2019 |  |
| experience | 3.34 | 2017 | 2019 |  |
| electronic commerce | 3.28 | 2008 | 2013 |  |
| tourism | 3.18 | 2008 | 2017 |  |
| Cluster ID | Size | Silhouette | Label (LLR) | Year | The Most Relevant Topics |
|---|---|---|---|---|---|
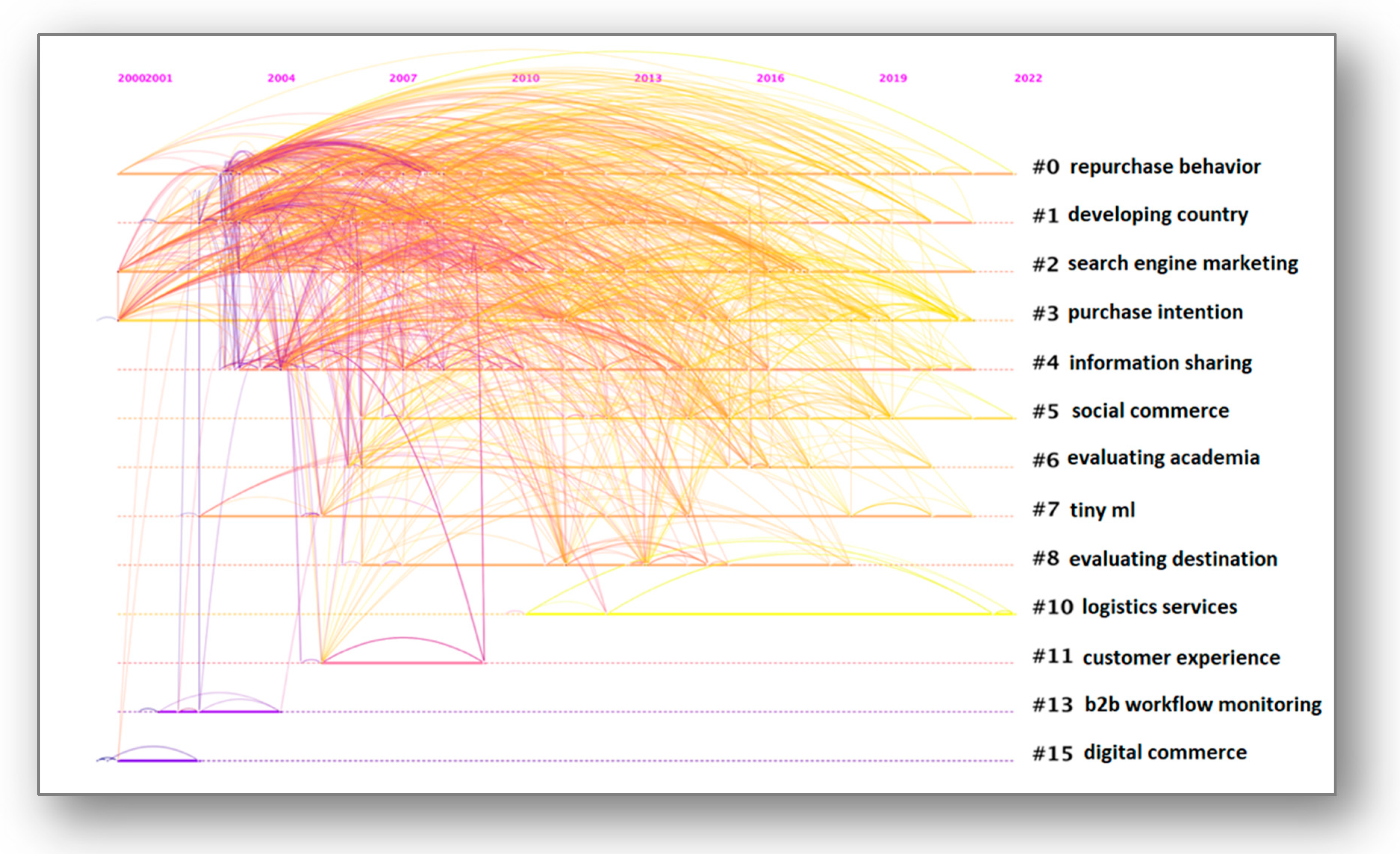
| 0 | 42 | 0.643 | repurchase behaviour (144.12, 1.0 × 10−4) | 2011 | factors and performance impact of electronic business [41] |
| 1 | 42 | 0.727 | a developing country (327.66, 1.0 × 10−4) | 2010 | Electronic commerce adoption willingness and behaviour [42] |
| 2 | 38 | 0.736 | search engine marketing (255.83, 1.0 × 10−4) | 2012 | search engine use [43] |
| 3 | 31 | 0.586 | purchase intention (194.09, 1.0 × 10−4) | 2015 | Electronic commerce satisfaction [44] |
| Cluster ID | Size | Silhouette | Mean (Year) | Label (LLR) |
|---|---|---|---|---|
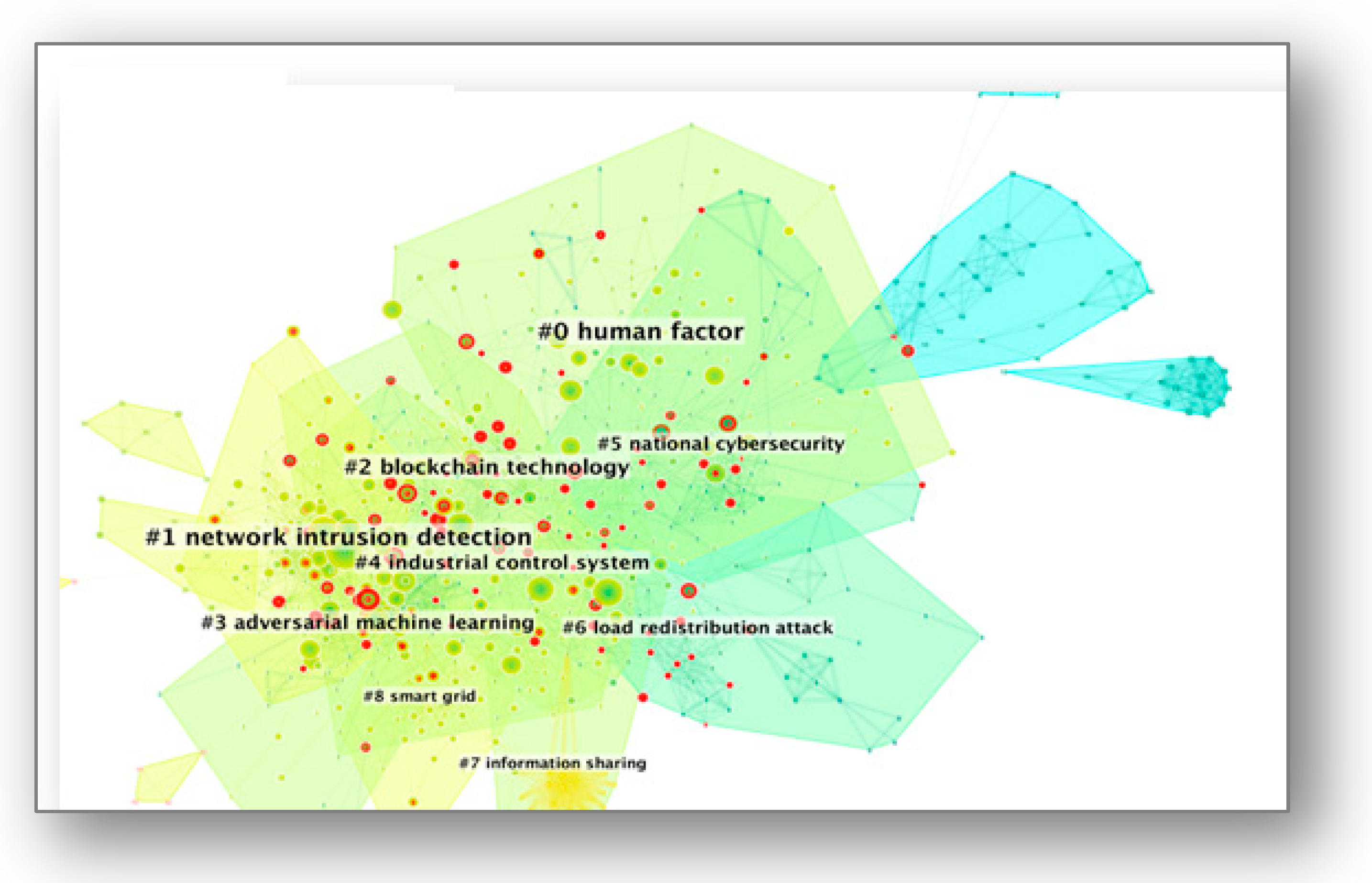
| 0 | 99 | 0.92 | 2016 | human factor (1038.26, 1.0 × 10−4); machine learning (760.94, 1.0 × 10−4); health care (678.93, 1.0 × 10−4); scoping review (601.43, 1.0 × 10−4); smart grid (593.5, 1.0 × 10−4) |
| 1 | 95 | 0.915 | 2017 | network intrusion detection (1797.74, 1.0 × 10−4); using machine (933.96, 1.0 × 10−4); objective comparison (863.01, 1.0 × 10−4); IoT network (829.85, 1.0 × 10−4); intrusion detection system (790.24, 1.0 × 10−4) |
| 2 | 78 | 0.873 | 2016 | blockchain technology (2099.46, 1.0 × 10−4); smart cities (1690.93, 1.0 × 10−4); blockchain technologies (928.62, 1.0 × 10−4); IoT device (826.53, 1.0 × 10−4); using blockchain (643.47, 1.0 × 10−4) |
| 3 | 69 | 0.914 | 2015 | adversarial machine learning (1756.66, 1.0 × 10−4); adversarial example (1053.93, 1.0 × 10−4); deep learning (861.22, 1.0 × 10−4); machine learning (854.89, 1.0 × 10−4); adversarial attack (660.04, 1.0 × 10−4) |
| 4 | 65 | 0.884 | 2016 | industrial control system (2556.12, 1.0 × 10−4); in-vehicle network (1172, 1.0 × 10−4); attack detection (894.82, 1.0 × 10−4); case study (782.27, 1.0 × 10−4); behavioural model (770.93, 1.0 × 10−4) |
| 5 | 61 | 0.944 | 2014 | national cybersecurity (682.86, 1.0 × 10−4); shared responsibility (610.77, 1.0 × 10−4); global cybersecurity (538.74, 1.0 × 10−4); political economy (472.75, 1.0 × 10−4); theorising cyber coercion (466.76, 1.0 × 10−4) |
| 6 | 54 | 0.949 | 2012 | load redistribution attack (1494.73, 1.0 × 10−4); advanced metering infrastructure (747.5, 1.0 × 10−4); power system adequacy assessment (741.01, 1.0 × 10−4); power grid (656.86, 1.0 × 10−4); 3d printing cybersecurity (656.86, 1.0 × 10−4) |
| Cluster ID | Size | Silhouette | Mean (Year) | Label (LLR) |
|---|---|---|---|---|
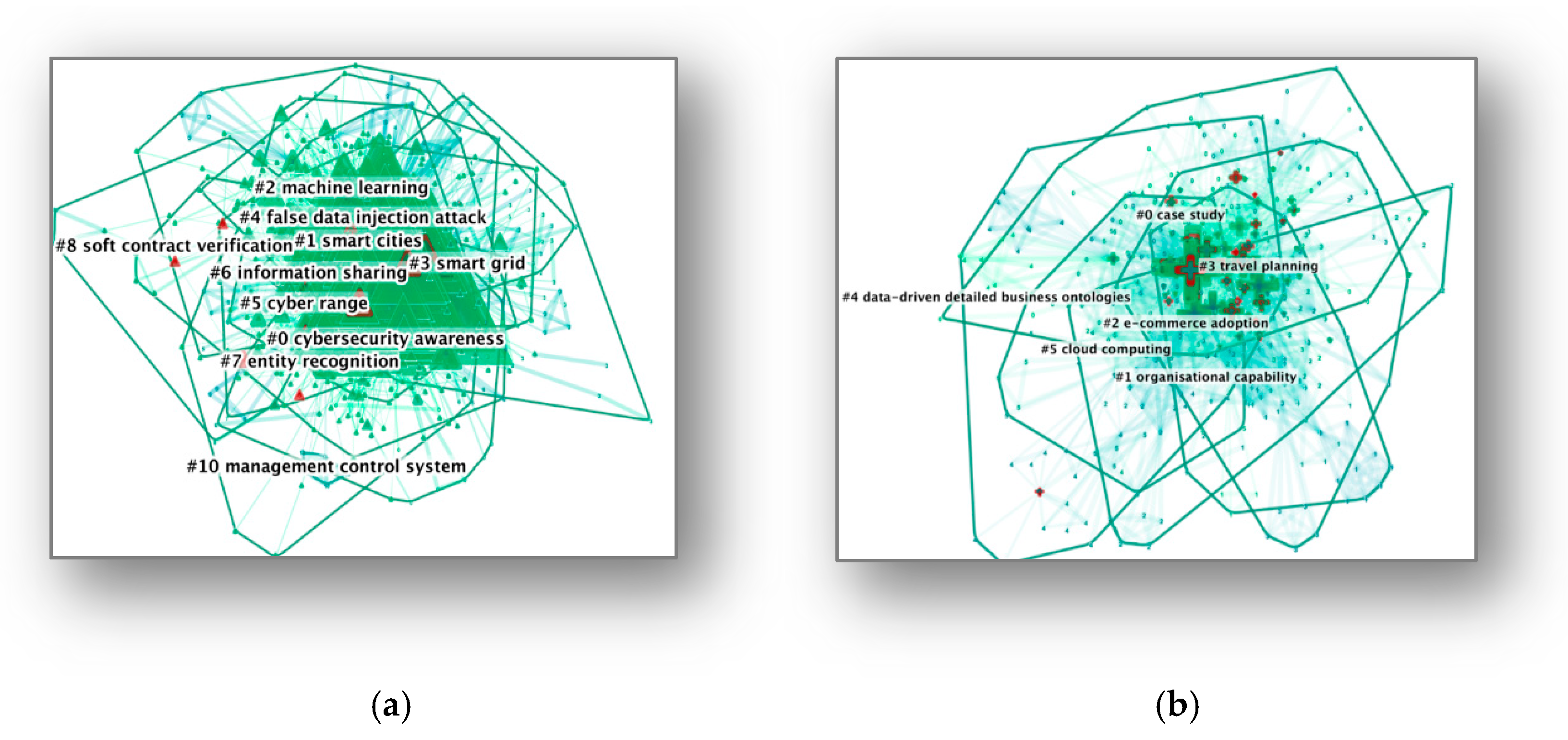
| 0 | 142 | 0.698 | 2017 | cybersecurity awareness (4192.79, 1.0 × 10−4) |
| 1 | 132 | 0.628 | 2017 | smart cities (5279.12, 1.0 × 10−4) |
| 2 | 105 | 0.725 | 2016 | machine learning (6747.1, 1.0 × 10−4) |
| Keywords | Strengths | Begin | End | 2000–2022 |
|---|---|---|---|---|
| cyber security | 19.22 | 2012 | 2017 |  |
| smart grid | 12.36 | 2010 | 2017 |  |
| cybersecurity education | 7.76 | 2014 | 2018 |  |
| vulnerability assessment | 6.28 | 2005 | 2018 |  |
| information security | 6.21 | 2008 | 2014 |  |
| moving target defence | 5.88 | 2016 | 2018 |  |
| cloud computing | 5.82 | 2011 | 2017 |  |
| cyber defence | 5.42 | 2014 | 2018 |  |
| information sharing | 5.42 | 2015 | 2017 |  |
| static analysis | 5.17 | 2018 | 2019 |  |
| computer security | 5.09 | 2009 | 2015 |  |
| critical infrastructure | 5 | 2015 | 2017 |  |
| security | 4.99 | 2013 | 2015 |  |
| crime | 4.94 | 2017 | 2018 |  |
| attack graph | 4.93 | 2012 | 2018 |  |
| data protection | 4.89 | 2017 | 2018 |  |
| social network | 4.87 | 2016 | 2018 |  |
| big data | 4.83 | 2012 | 2018 |  |
| software security | 4.81 | 2016 | 2018 |  |
| game theory | 4.63 | 2014 | 2018 |  |
| situation awareness | 4.46 | 2016 | 2019 |  |
| smart home | 4.42 | 2019 | 2020 |  |
| critical infrastructure protection | 4.4 | 2015 | 2016 |  |
| malware | 4.16 | 2019 | 2020 |  |
| cybersecurity training | 4.13 | 2017 | 2018 |  |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vuță, D.R.; Nichifor, E.; Țierean, O.M.; Zamfirache, A.; Chițu, I.B.; Foris, T.; Brătucu, G. Extending the Frontiers of Electronic Commerce Knowledge through Cybersecurity. Electronics 2022, 11, 2223. https://doi.org/10.3390/electronics11142223
Vuță DR, Nichifor E, Țierean OM, Zamfirache A, Chițu IB, Foris T, Brătucu G. Extending the Frontiers of Electronic Commerce Knowledge through Cybersecurity. Electronics. 2022; 11(14):2223. https://doi.org/10.3390/electronics11142223
Chicago/Turabian StyleVuță, Daniela Roxana, Eliza Nichifor, Ovidiu Mircea Țierean, Alexandra Zamfirache, Ioana Bianca Chițu, Tiberiu Foris, and Gabriel Brătucu. 2022. "Extending the Frontiers of Electronic Commerce Knowledge through Cybersecurity" Electronics 11, no. 14: 2223. https://doi.org/10.3390/electronics11142223
APA StyleVuță, D. R., Nichifor, E., Țierean, O. M., Zamfirache, A., Chițu, I. B., Foris, T., & Brătucu, G. (2022). Extending the Frontiers of Electronic Commerce Knowledge through Cybersecurity. Electronics, 11(14), 2223. https://doi.org/10.3390/electronics11142223







