Multi-Hop Routing Protocols for Oil Pipeline Leak Detection Systems
Abstract
:1. Introduction
1.1. Wireless Communication for Linear-Based Topology Applications
- RFID and NFC
- Bluetooth
- Zigbee
- Wi-Fi
- Sigfox
- DASH 7
- LoRa
1.2. Routing in Wireless Sensor Networks
- Flat routing is a simple structure. The node senses the data and acts as a relay node. It reduces the communication overhead but consumes a large amount of power. In a flat topology, examples of the routing protocols are AODV, DSDV, OLSR, STAR, and ETSP [22]. This type of routing consumes energy.
- In hierarchical routing, the area is divided into sub-areas or clusters. Each one has a cluster head (CH). The sensors send the data to the CH, and CH sends it to the destination. Hierarchical topology is efficient and increases scalability [23].
- In static routing, the network administrator generates the static routing protocols. The routing table is built before the communication takes place, and it is fixed. Hence, it requires low energy. The IPv4 protocol uses static routing. Static routing is not suitable if the network changes [24].
- The dynamic routing protocol is used in environmental applications. The nodes know the routes and the paths from their neighbors. It uses two ways to discover the route: proactive and reactive [24]. Proactive routing, also known as table-driven routing, is one in which all routing information is stored in a table. To discover the paths, each node sends a broadcasting message to all nodes. These paths are stored in the routing table, which is continually updated [24]. There are many proactive protocols, such as DSDV, STAR, OLSR, HOLSR, and RPL. Reactive protocols discover the route on demand. Unlike proactive routing, reactive routing reduces the communication overhead. AODV, DSR, and TORA are examples of reactive protocols [24]. The dynamic protocol is adaptable and scalable. However, it needs more energy because of the routing process and additional resources like bandwidth, memory, and CPU, which may decrease network performance [24].
- Hybrid routing combines both static and dynamic routing, such as link-state routing (LSR). It has a low overhead. These protocols do not work well in large-scale networks [24].
2. Related Work
2.1. Related Leak Detection Systems
2.2. Multi-Hop Routing Protocols for Leak Detection Systems
2.3. LoRa Multi-Hop
3. System Architecture, Scenarios of Multi-Hop LoRa, and Results
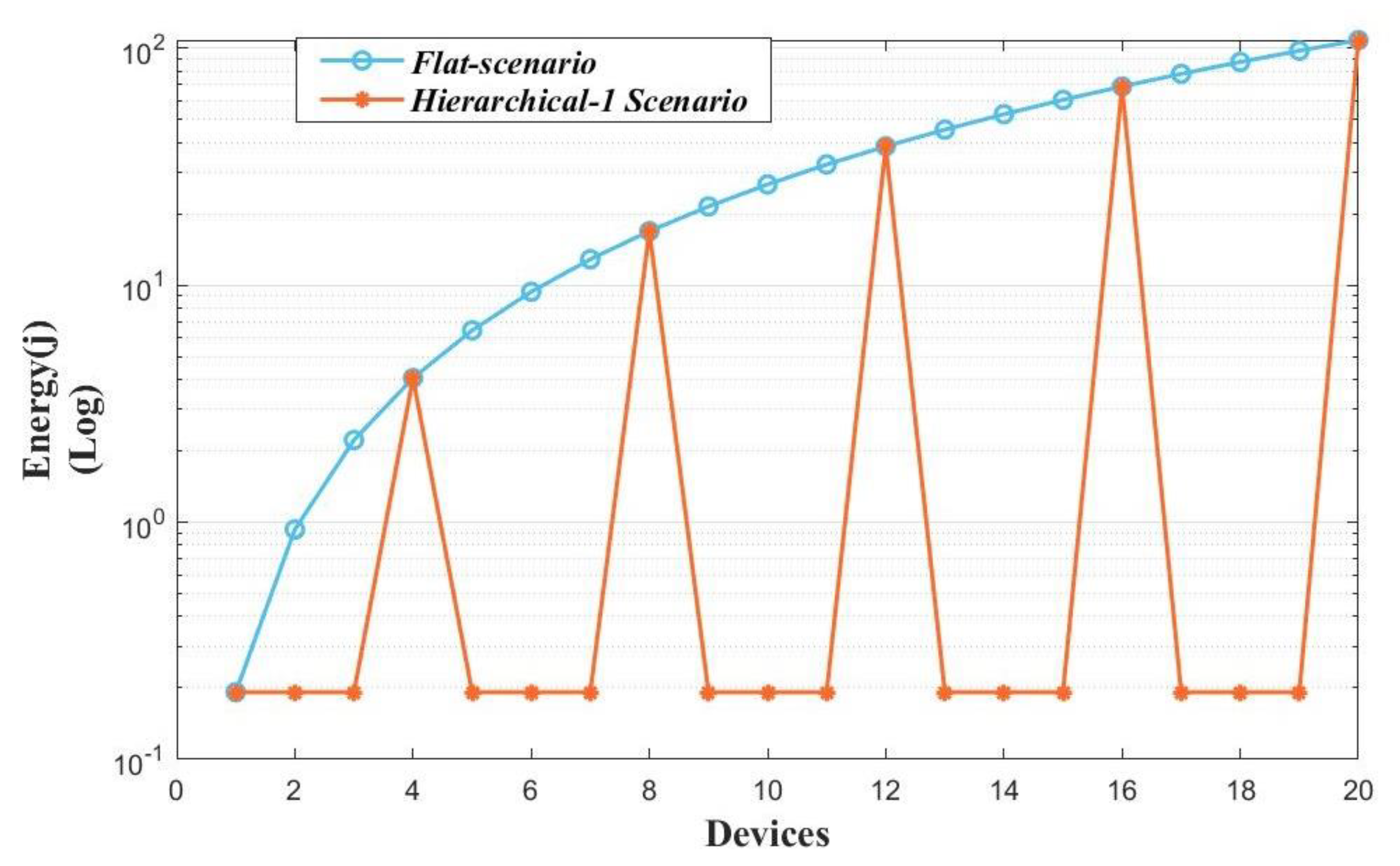
3.1. Flat Topology Calculations
3.1.1. Measurement Ranges and Traffic Size Calculations
3.1.2. The Energy Consumption of LoRa Nodes Calculations
3.1.3. Temperature and Pressure Sensor Calculations
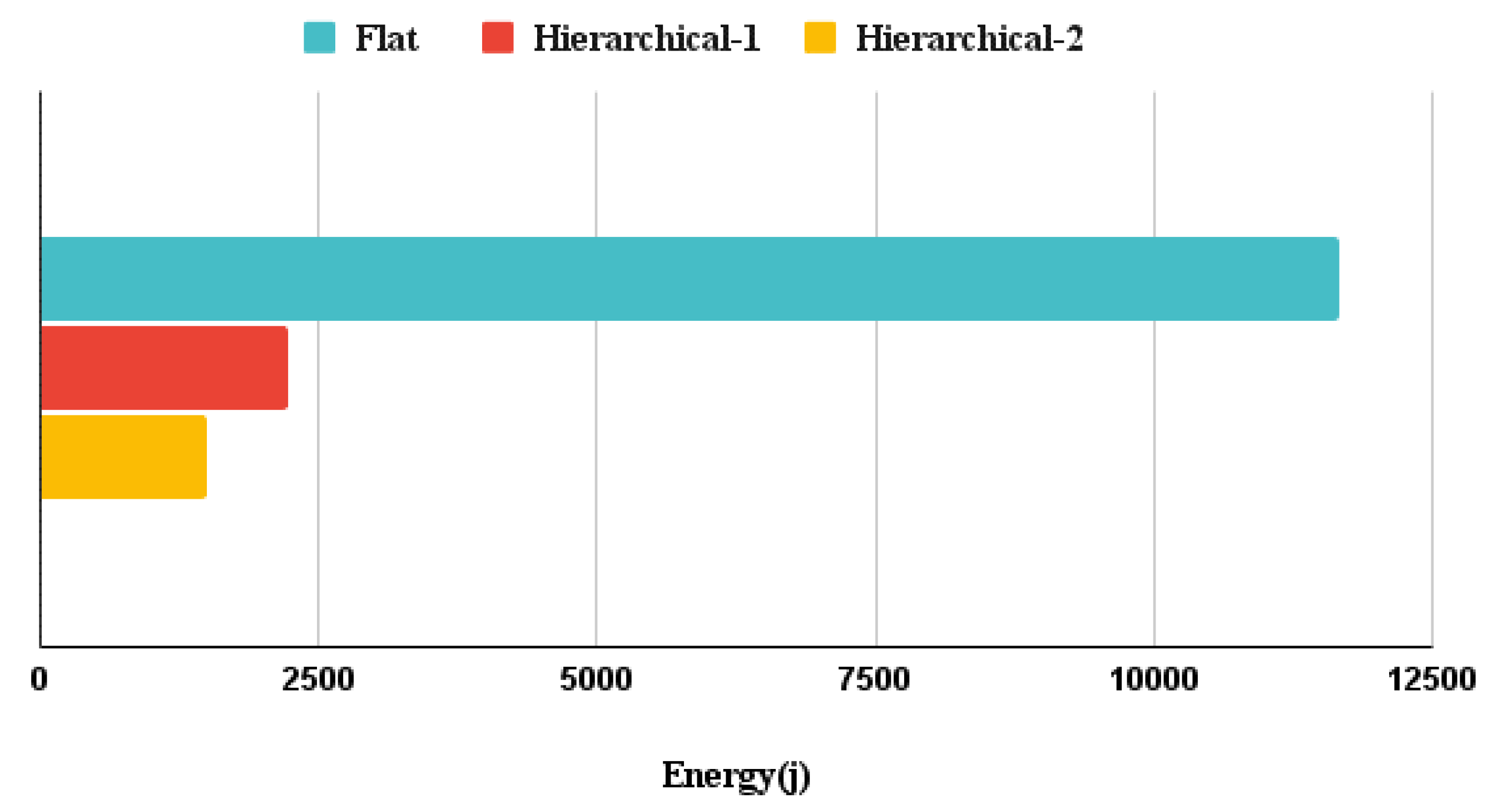
3.2. Hierarchical Topology calculations
4. Conclusions—Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Midani, M.; Technologies, P.; Arabia, S. Pipeline Leak Detection Technologies and Selection Criteria. In Proceedings of the Pipeline Technology Conference 2019, Berlin, Germany, 18–21 March 2019; pp. 1–12. [Google Scholar]
- Yu, H.; Guo, M. An efficient oil and gas pipeline monitoring systems based on wireless sensor networks. In Proceedings of the 3rd International Conference on Information Security & Intelligent Control, ISIC 2012, Yunlin, Taiwan, 14–16 August 2012; pp. 178–181. [Google Scholar] [CrossRef]
- Al-Ahmari, S.A. Saudi Aramco Experience towards Establishing Pipelines Integrity Management System (PIMS); Rio Pipeline Conference and Exposition, Technical Papers, Energy Technology Data Exchange (ETDEWEB): Washington, DC, USA, 2009; pp. 1–6. [Google Scholar]
- Anupama, K.R.; Kamdar, N.; Kamalampet, S.K.; Vyas, D.; Sahu, S.; Shah, S. A wireless sensor network based pipeline monitoring system. In Proceedings of the 2014 International Conference on Signal Processing and Integrated Networks, SPIN 2014, Delhi, India, 20–21 February 2014; pp. 412–419. [Google Scholar] [CrossRef]
- Subramaniam, S.K. Novel Design of Reliable Static Routing Algorithm For Multi-hop Linear Networks. Ph.D. Thesis, Brunel University London, London, UK, 2017. [Google Scholar]
- Sun, X.; He, J.; Chen, Y.; Ma, S.; Zhang, Z. A new routing algorithm for linear wireless sensor networks. In Proceedings of the 2011 6th International Conference on Pervasive Computing and Communications, ICPCA 2011, Pisa, Italy, 21–25 March 2011; pp. 497–501. [Google Scholar] [CrossRef]
- He, B.; Li, G. PUAR: Performance and Usage Aware Routing Algorithm for Long and Linear Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2014. [CrossRef] [Green Version]
- Bhuvaneswari, V.; Porkodi, R. The internet of things (IOT) applications and communication enabling technology standards: An overview. In Proceedings of the 2014 International Conference on Intelligent Computing, ICICA 2014, Nanchang, China, 3–6 August 2014; pp. 324–329. [Google Scholar] [CrossRef]
- Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M.S. Internet of Things (IoT) Communication Protocols: Review. In Proceedings of the 2017 8th International Conference on Information Technology, Singapore, 27–29 December 2017; pp. 685–690. [Google Scholar] [CrossRef]
- Coskun, V.; Ok, K. A Survey on Near Field Communication (NFC) Technology. Wirel. Pers. Commun. 2014, 71, 2259–2294. [Google Scholar] [CrossRef]
- Gomez, C.; Oller, J.; Paradells, J. Overview and evaluation of bluetooth low energy: An emerging low-power wireless technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Čolaković, A.; Hadžialić, M. Internet of Things (IoT): A review of enabling technologies, challenges, and open research issues. Comput. Netw. 2018, 144, 17–39. [Google Scholar] [CrossRef]
- Jawhar, I.; Mohamed, N.; Shuaib, K. A framework for pipeline infrastructure monitoring using wireless sensor networks. In Proceedings of the 2007 Wireless Telecommunications Symposium, WTS 2007, Pomona, CA, USA, 26–28 April 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Bhoyar, P.; Sahare, P.; Dhok, S.B.; Deshmukh, R.B. Communication technologies and security challenges for internet of things: A comprehensive review. AEU Int. J. Electron. Commun. 2019, 99, 81–99. [Google Scholar] [CrossRef]
- Durand, T.G.; Visagie, L.; Booysen, M.J. Evaluation of next-generation low-power communication technology to replace GSM in IoT-applications. IET Commun. 2019, 13, 2533–2540. [Google Scholar] [CrossRef]
- Stoynov, V.; Poulkov, V.; Valkova-Jarvis, Z. Low Power Wide Area Networks Operating in the ISM Band—Overview and Unresolved Challenges; Springer: Berlin, Germany, 2019; Volume 283. [Google Scholar]
- Ismail, D.; Rahman, M.; Saifullah, A. Low-Power Wide-Area Networks: Opportunities, Challenges, and Directions. In Proceedings of the International Conference on Distributed Computing and Networking, Varanasi, India, 4–7 January 2018; pp. 1–6. [Google Scholar]
- Bor, M.; Vidler, J.; Roedig, U. LoRa for the Internet of Things. In Proceedings of the 2016 International Conference on Embedded Wireless Systems and Networks, Graz, Austria, 15–17 February 2016; pp. 361–366. [Google Scholar]
- De Poorter, E.; Hoebeke, J.; Strobbe, M.; Moerman, I.; Latré, S.; Weyn, M.; Lannoo, B.; Famaey, J. Sub-GHz LPWAN Network Coexistence, Management and Virtualization: An Overview and Open Research Challenges. Wirel. Pers. Commun. 2017, 95, 187–213. [Google Scholar] [CrossRef] [Green Version]
- Zhou, Q.; Zheng, K.; Hou, L.; Xing, J.; Xu, R. Design and Implementation of Open LoRa for IoT. arXiv 2018, arXiv:1812.09012. [Google Scholar] [CrossRef]
- Toor, A.S.; Jain, A.K. A survey of routing protocols in Wireless Sensor Networks: Hierarchical routing. In Proceedings of the 2016 International Conference on Recent Advances and Innovations in Engineering, ICRAIE 2016, Jaipur, India, 23–25 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Randhawa, S.; Verma, A.K. Comparative analysis of flat routing protocols in wireless sensor networks: Which one is better? In Proceedings of the 2017 International Conference on Intelligent Computing and Control, Madurai, India, 15–16 June 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Mehta, D.; Saxena, S. A Comparative Analysis of Energy Efficient Hierarchical Routing Protocols for Wireless Sensor Networks. In Proceedings of the 4th International Conference on Computer Science, ICCS 2018, Wuxi, China, 11–13 June 2018; pp. 53–58. [Google Scholar] [CrossRef]
- Marietta, J.; Mohan, B.C. A Review on Routing in Internet of Things. Wirel. Pers. Commun. 2020, 111, 209–233. [Google Scholar] [CrossRef]
- Yoon, S.; Ye, W.; Heidemann, J.; Littlefield, B.; Shahabi, C. SWATS: Wireless sensor networks for steamflood and waterflood pipeline monitoring. IEEE Netw. 2011, 25, 50–56. [Google Scholar] [CrossRef] [Green Version]
- Basagni, S.; Petrioli, C.; Petroccia, R.; Spaccini, D. CARP: A Channel-aware routing protocol for underwater acoustic wireless networks. Ad Hoc Netw. 2015, 34, 92–104. [Google Scholar] [CrossRef]
- Jawhar, I.; Mohamed, N.; Mohamed, M.M.; Aziz, J. A routing protocol and addressing scheme for oil, gas, and water pipeline monitoring using wireless sensor networks. In Proceedings of the 5th IFIP International Conference on Wireless and Optical Communications Networks, WOCN 2008, Surabaya, Indonesia, 5–7 May 2008. [Google Scholar] [CrossRef]
- Stoianov, I.; Nachman, L.; Madden, S.; Tokmouline, T. PIPENETa wireless sensor network for pipeline monitoring. In Proceedings of the Sixth International Symposium on Information Processing in Sensor Networks, IPSN 2007, Cambridge, MA, USA, 25–27 April 2007; pp. 264–273. [Google Scholar] [CrossRef]
- Sun, Z.; Wang, P.; Vuran, M.C.; Al-Rodhaan, M.A.; Al-Dhelaan, A.M.; Akyildiz, I.F. MISE-PIPE: Magnetic induction-based wireless sensor networks for underground pipeline monitoring. Ad Hoc Netw. 2011, 9, 218–227. [Google Scholar] [CrossRef]
- Sadeghioon, A.M.; Metje, N.; Chapman, D.N.; Anthony, C.J. SmartPipes: Smart wireless sensor networks for leak detection in water pipelines. J. Sens. Actuator Netw. 2014, 3, 64–78. [Google Scholar] [CrossRef]
- Kim, J.H.; Sharma, G.; Boudriga, N.; Iyengar, S.S. SPAMMS: A sensor-based pipeline autonomous monitoring and maintenance system. In Proceedings of the 2010 2nd International Conference on COMmunication Systems & NETworkS, COMSNETS 2010, Bangalore, India, 5–9 January 2010. [Google Scholar] [CrossRef]
- Saeed, H.; Ali, S.; Rashid, S.; Qaisar, S.; Felemban, E. Reliable monitoring of oil and gas pipelines using wireless sensor network (WSN)—REMONG. In Proceedings of the 9th International Conference on System of Systems Engineering, SoSE 2014, Glenelg, Australia, 9–13 June 2014; pp. 230–235. [Google Scholar] [CrossRef]
- Faragó, A. Network topology models for multihop wireless networks. Int. Sch. Res. Not. 2012. [CrossRef] [Green Version]
- Marhoon, H.A.; Mahmuddin, M.; Nor, S.A. Chain-based routing protocols in wireless sensor networks: A survey. ARPN J. Eng. Appl. Sci. 2015, 10, 1389–1398. [Google Scholar]
- Hadjila, M.; Guyennet, H.; Feham, M. A chain-based routing protocol to maximize the lifetime of wireless sensor networks. Wireless Sensor Network 2013, 5, 116–120. [Google Scholar] [CrossRef] [Green Version]
- Taghikhaki, Z.; Meratnia, N.; Havinga, P.J.M. A reliable and energy-efficient chain-cluster based routing protocol for Wireless Sensor Networks. In Proceedings of the 2013 IEEE Eighth International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Singapore, 21–24 April 2013; pp. 248–253. [Google Scholar]
- Aslam, M.; Javaid, N.; Rahim, A.; Nazir, U.; Bibi, A.; Khan, Z.A. Survey of extended LEACH-based clustering routing protocols for wireless sensor networks. In Proceedings of the 2012 IEEE 14th International Conference on High Performance Computing and Communication & 2012 IEEE 9th International Conference on Embedded Software and Systems, Liverpool, UK, 25–27 June 2012; pp. 1232–1238. [Google Scholar] [CrossRef] [Green Version]
- Kaur, A.; Grover, A. LEACH and Extended LEACH Protocols in Wireless Sensor Network—A Survey. Int. J. Comput. Appl. 2015, 116, 1–5. [Google Scholar] [CrossRef]
- Neto, J.H.B.; Rego, A.; Cardoso, A.R.; Celestino, J. MH-LEACH: A distributed algorithm for multi-hop communication in wireless sensor networks. In Proceedings of the 1st ACM conference on Information-centric Networking (ICN 2014), Paris, France, 24–26 September 2014; pp. 55–61. [Google Scholar]
- Centelles, R.P.; Freitag, F.; Meseguer, R.; Navarro, L. Beyond the Star of Stars: An Introduction to Multihop and Mesh for LoRa and LoRaWAN. IEEE Pervasive Comput. 2021, 20, 63–72. [Google Scholar] [CrossRef]
- Cotrim, J.R.; Kleinschmidt, J.H. LoRaWAN Mesh networks: A review and classification of multihop communication. Sensors 2020, 20, 4273. [Google Scholar] [CrossRef]
- Farooq, M.O. Multi-hop communication protocol for LoRa with software-defined networking extension. Internet Things 2021, 14. [Google Scholar] [CrossRef]
- Aslam, M.S.; Khan, A.; Atif, A.; Hassan, S.A.; Mahmood, A.; Qureshi, H.K.; Gidlund, M. Exploring Multi-Hop LoRa for Green Smart Cities. IEEE Netw. 2020, 34, 225–231. [Google Scholar] [CrossRef] [Green Version]
- Lee, H.C.; Ke, K.H. Monitoring of Large-Area IoT Sensors Using a LoRa Wireless Mesh Network System: Design and Evaluation. IEEE Trans. Instrum. Meas. 2018, 67, 2177–2187. [Google Scholar] [CrossRef]
- Mai, D.L.; Kim, M.K. Multi-hop LOra network protocol with minimized latency. Energies 2020, 13, 1368. [Google Scholar] [CrossRef] [Green Version]
- Triwidyastuti, Y.; Musayyanah, M.; Ernawati, F.; Affandi, C.D. Multi-hop Communication between LoRa End Devices. Sci. J. Inform. 2020, 7, 125–135. [Google Scholar] [CrossRef]
- Abrardo, A.; Pozzebon, A. A multi-hop lora linear sensor network for the monitoring of underground environments: The case of the medieval aqueducts in Siena, Italy. Sensors 2019, 19, 402. [Google Scholar] [CrossRef] [Green Version]
- Mikhaylov, K.; Petaejaejaervi, J.; Haenninen, T. Analysis of capacity and scalability of the LoRa low power wide area network technology. In Proceedings of the 22th European Wireless Conference, Lisbon, Portugal, 3–5 July 2016; pp. 1–6. [Google Scholar]
- Shirtliff, J.G.; Leid, M. Reliable and Efficient Information Forwarding and Traffic Engineering in Wireless Sensor Networks. In Wireless Sensor Networks and Applications; Springer: Berlin, Germany, 2009; Volume 3. [Google Scholar]







| Technology | Topology | Data Rate | Frequency Band | Power | Range |
|---|---|---|---|---|---|
| NFC | P2P | 4–8 kbps | 120–150 kHz | 50 mA | 10–20 cm |
| RFID | P2P | 40–640 Kbps | 3.11 GHz | N/A | Up to 200 m |
| Bluetooth | P2P | 24 Mbps | 2.4 GHz | 30 mA | Up to 100 m |
| BLE | P2P | 1 Mbps | 2.4 GHz | 15 mA | Up to 50 m |
| ZIGBEE | Star-mesh-tree | 250 kbps | 2.4 GHz | 30 mA | Up to 100 m |
| LoRa | Star -Mesh | Up to 50 kbps | 434–868 MHz | 12–40 mA | Up to 15 km |
| Sigfox | Star | 100 bps | 868 MHz | 45 mA | Up to 30 km |
| DASH7 | Star-Tree | Up to 200 kbps | 433–868–915 MHz | 31 mA | Up to 5 km |
| System | Fluid Type | Pipeline | Measurements Type | WSN Communication Technology | Routing Type |
|---|---|---|---|---|---|
| PIPENET | water | under-ground | hydraulic-acoustic/ vibration | Bluetooth Wi-Fi | Single-hop |
| CARP | oil | underwater | N/available | N/available | Multi-hop |
| ROLS [27] | water–gas–oil | N/available | N/available | Zigbee, Bluetooth Cellular, Wi-Max | Single-hop |
| SWATS | water-steam | above-ground | temperature pressure | Low Power WSN Wi-Fi | Multi-hop |
| SPAMMS | water | above-ground | pressure | RFID | Single-hop |
| MISE- PIPE | water–oil | under-ground | temperature, acoustic pressure | N/Available | Multi-hop |
| Smart- Pipe | water | under-ground | temperature pressure | N/Available | Multi-hop |
| RE- MONG | oil | above-ground | temperature-pressure | Zigbee | Multi-hop |
| Protocol | Intra/inter Cluster | Advantage | Disadvantage |
|---|---|---|---|
| Chain-based 1 | Multi-hop/Single-hop | Low delay | Unbalanced CH energy |
| Chain-based 2 | Multi-hop/multi-hop | Low delay | Unbalanced energy |
| RFC+ | Multi-hop/multi-hop | Reduce the CH consumption energy | OverheadNot applicable |
| Multi-Hop LEACH | Single-hop/multi-hop | Scalability | Increase network traffic |
| MH-LEACH | Single-hop/multi-hop | Reduce the transmission energy | Increase network traffic |
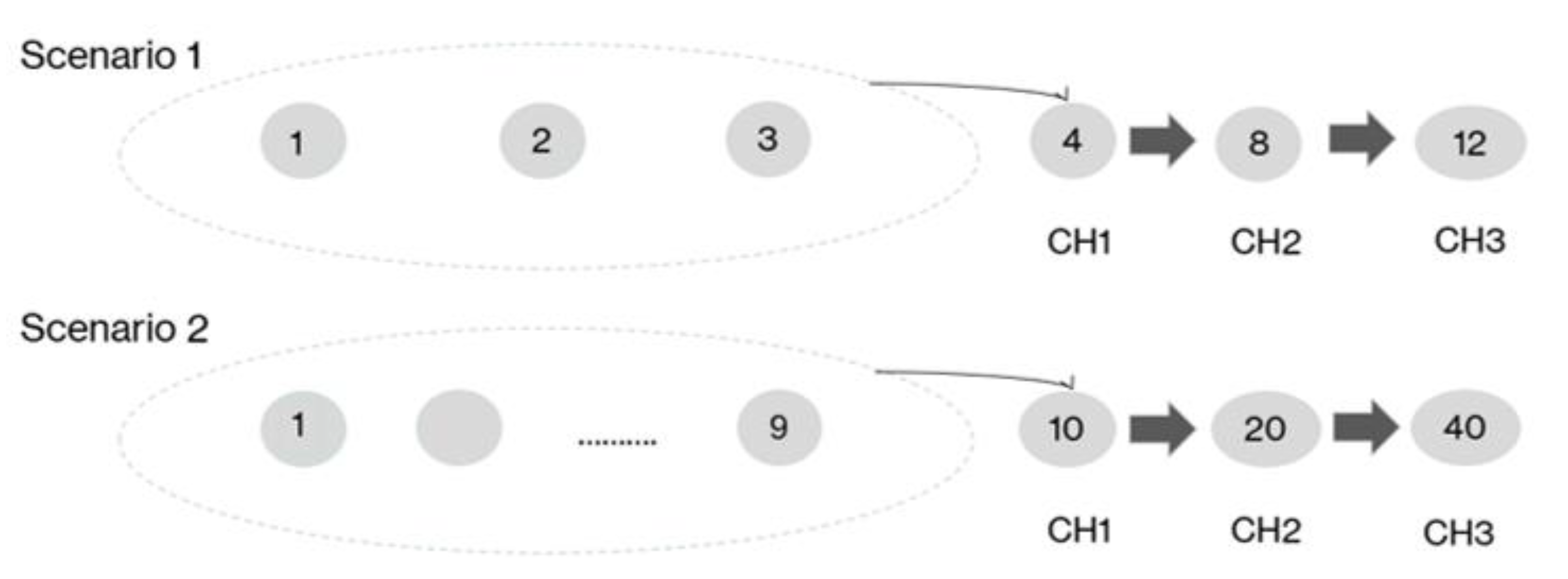
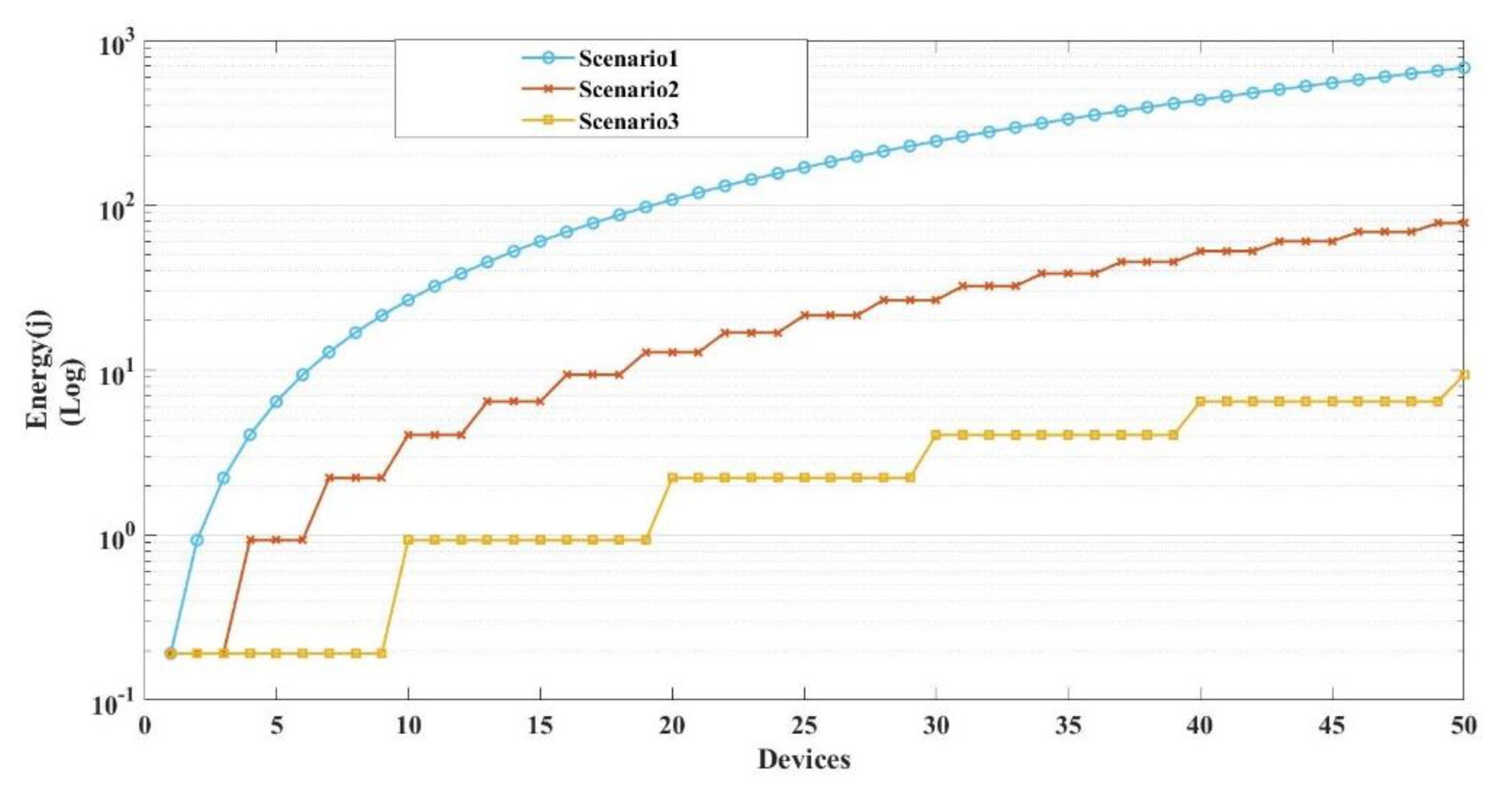
| Scenario 1 | Scenario 2 | Scenario 3 | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Pipeline length | 10 km | |||||||||||||||||
| Communication Scenarios | Hop-by-hop | The third neighbor | The ninth neighbor | |||||||||||||||
| Distances (m) | 10 | 50 | 100 | 150 | 200 | 500 | 10 | 50 | 100 | 150 | 200 | 500 | 10 | 50 | 100 | 1500 | 200 | 500 |
| Devices | 1000 | 200 | 100 | 67 | 50 | 20 | 1000 | 200 | 100 | 67 | 50 | 20 | 1000 | 200 | 100 | 67 | 50 | 20 |
| No. Hops | 1000 | 200 | 100 | 67 | 50 | 20 | 340 | 68 | 34 | 23 | 17 | 7 | 100 | 20 | 10 | 7 | 5 | 2 |
| Packets | 1 byte/ 255 bytes | |||||||||||||||||
| 98 mA | Drawing current of send mode |
| 66 mA | Drawing current of receive mode |
| 1 packet each 3 h | Packets |
| 1-day | Total assumed duration |
| 50 Node | Number of Nodes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alhomyani, H.; Fadel, M.; Dimitriou, N.; Bakhsh, H.; Aldabbagh, G.; Alkhuraiji, S. Multi-Hop Routing Protocols for Oil Pipeline Leak Detection Systems. Electronics 2022, 11, 2078. https://doi.org/10.3390/electronics11132078
Alhomyani H, Fadel M, Dimitriou N, Bakhsh H, Aldabbagh G, Alkhuraiji S. Multi-Hop Routing Protocols for Oil Pipeline Leak Detection Systems. Electronics. 2022; 11(13):2078. https://doi.org/10.3390/electronics11132078
Chicago/Turabian StyleAlhomyani, Haneen, Mai Fadel, Nikos Dimitriou, Helen Bakhsh, Ghadah Aldabbagh, and Samar Alkhuraiji. 2022. "Multi-Hop Routing Protocols for Oil Pipeline Leak Detection Systems" Electronics 11, no. 13: 2078. https://doi.org/10.3390/electronics11132078
APA StyleAlhomyani, H., Fadel, M., Dimitriou, N., Bakhsh, H., Aldabbagh, G., & Alkhuraiji, S. (2022). Multi-Hop Routing Protocols for Oil Pipeline Leak Detection Systems. Electronics, 11(13), 2078. https://doi.org/10.3390/electronics11132078






