Network Intelligent Control and Traffic Optimization Based on SDN and Artificial Intelligence
Abstract
1. Introduction
2. Scenarios and Requirements
2.1. The Carrying of 5G Services
2.2. MPLS Network
2.3. Cloudification of Services and IP Backbone Network
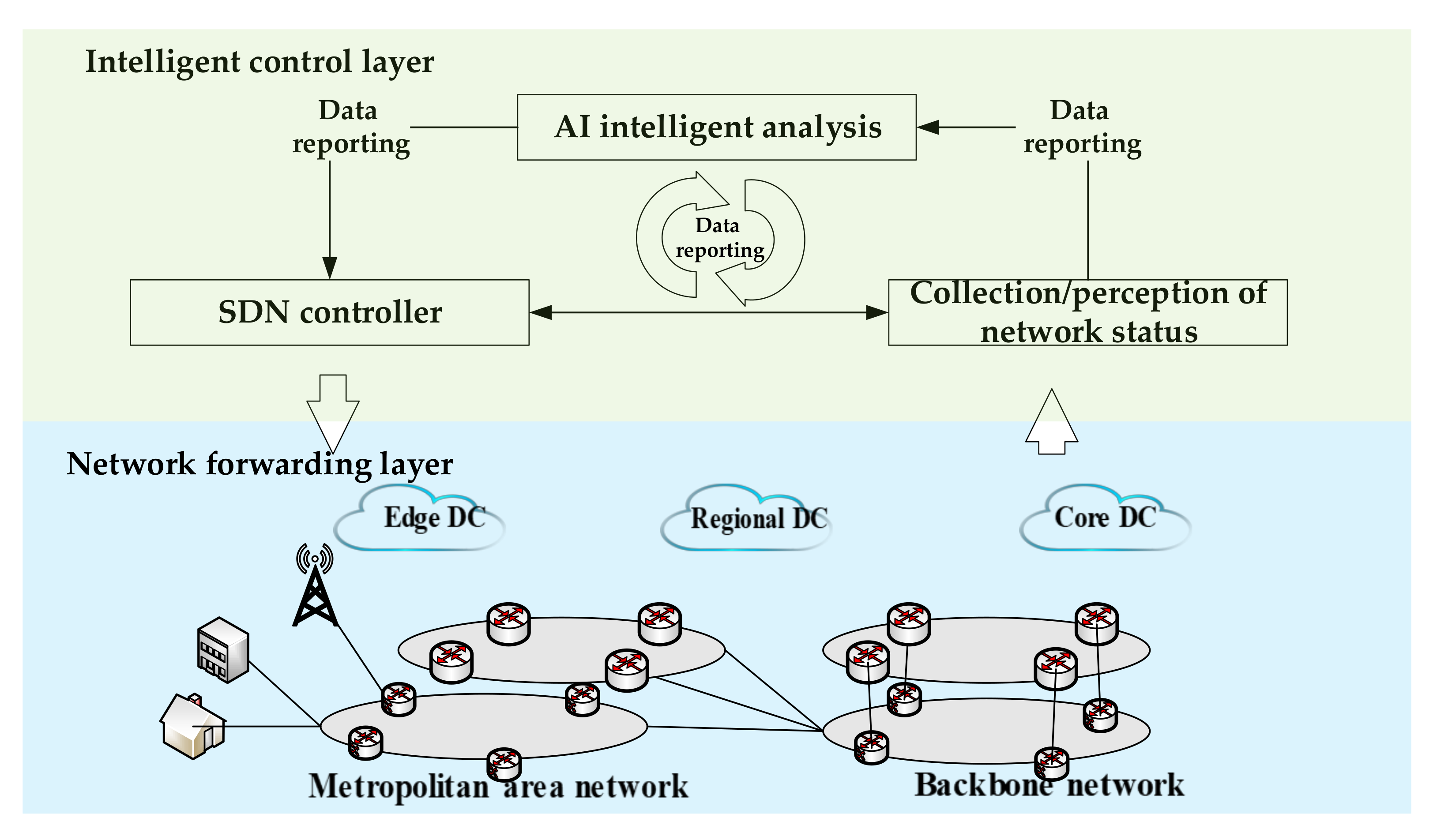
3. Architecture of Intelligent Network Control
3.1. Collection/Perception of Network Status Module
3.2. AI Intelligent Analysis Module
3.3. SDN Controller Module
4. Research Methods and Solutions
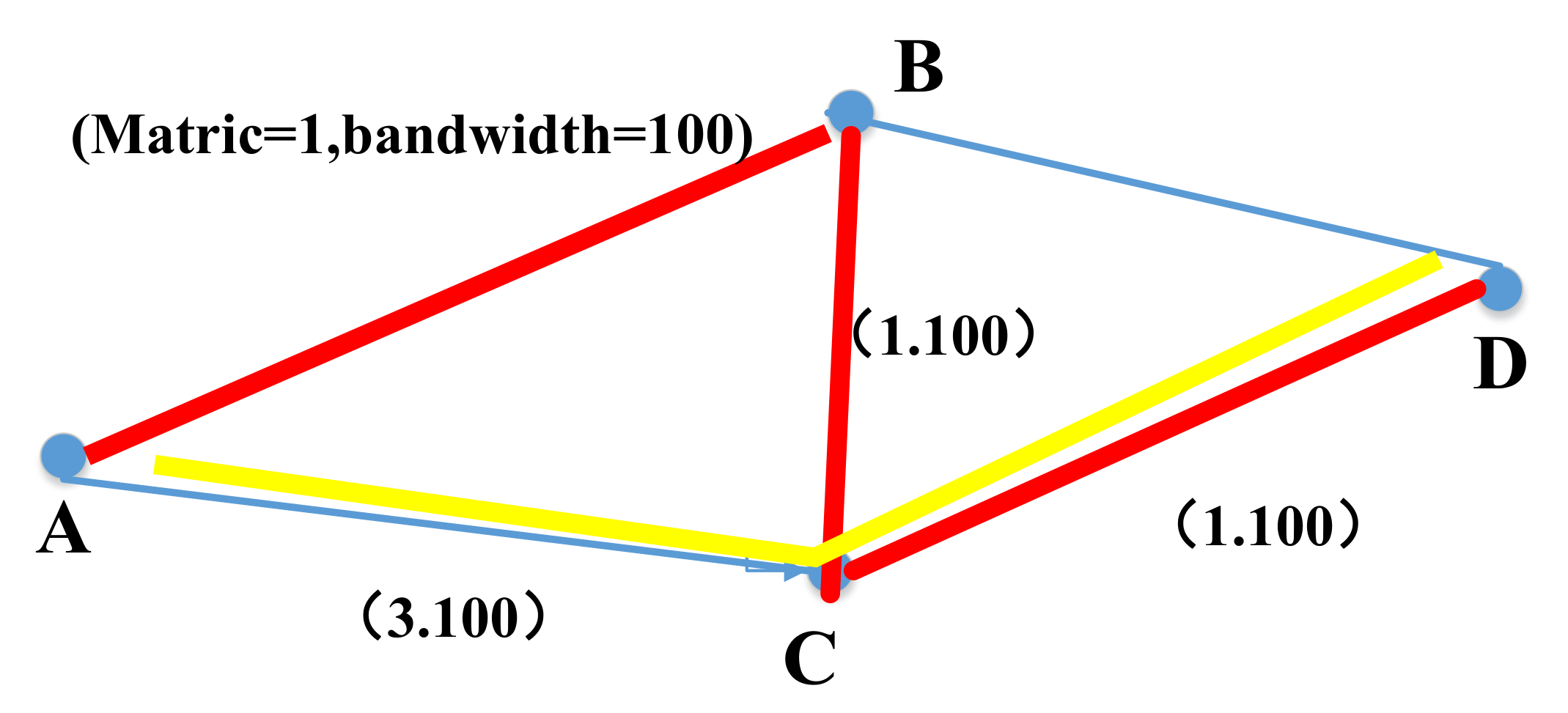
4.1. Object of Flow Optimization
4.2. Routing Calculation Algorithm
4.2.1. GREEDY Algorithm
4.2.2. KSP Algorithm
4.3. Path Optimization Algorithm
4.3.1. Particle Swarm Optimization
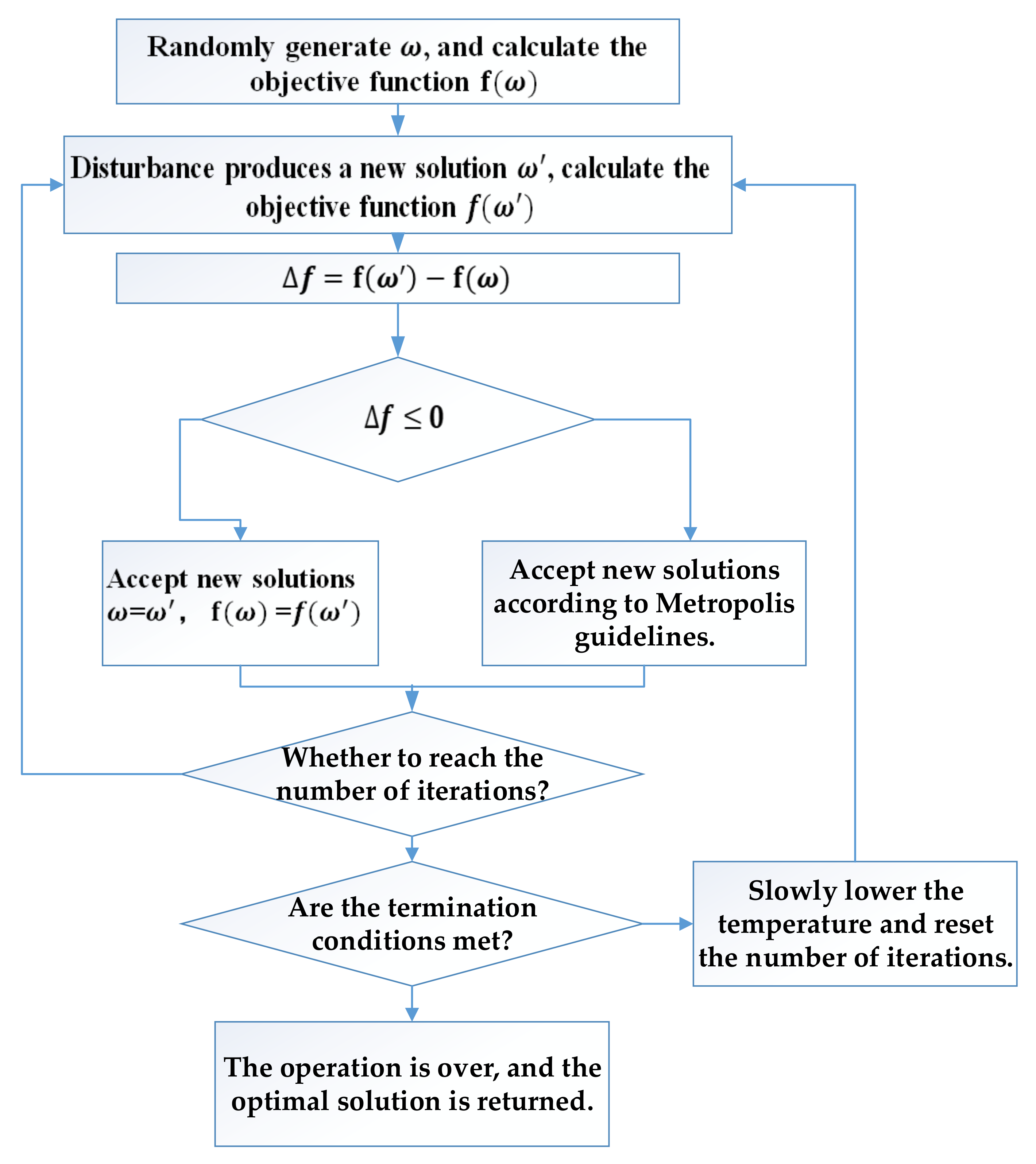
4.3.2. Simulated Annealing
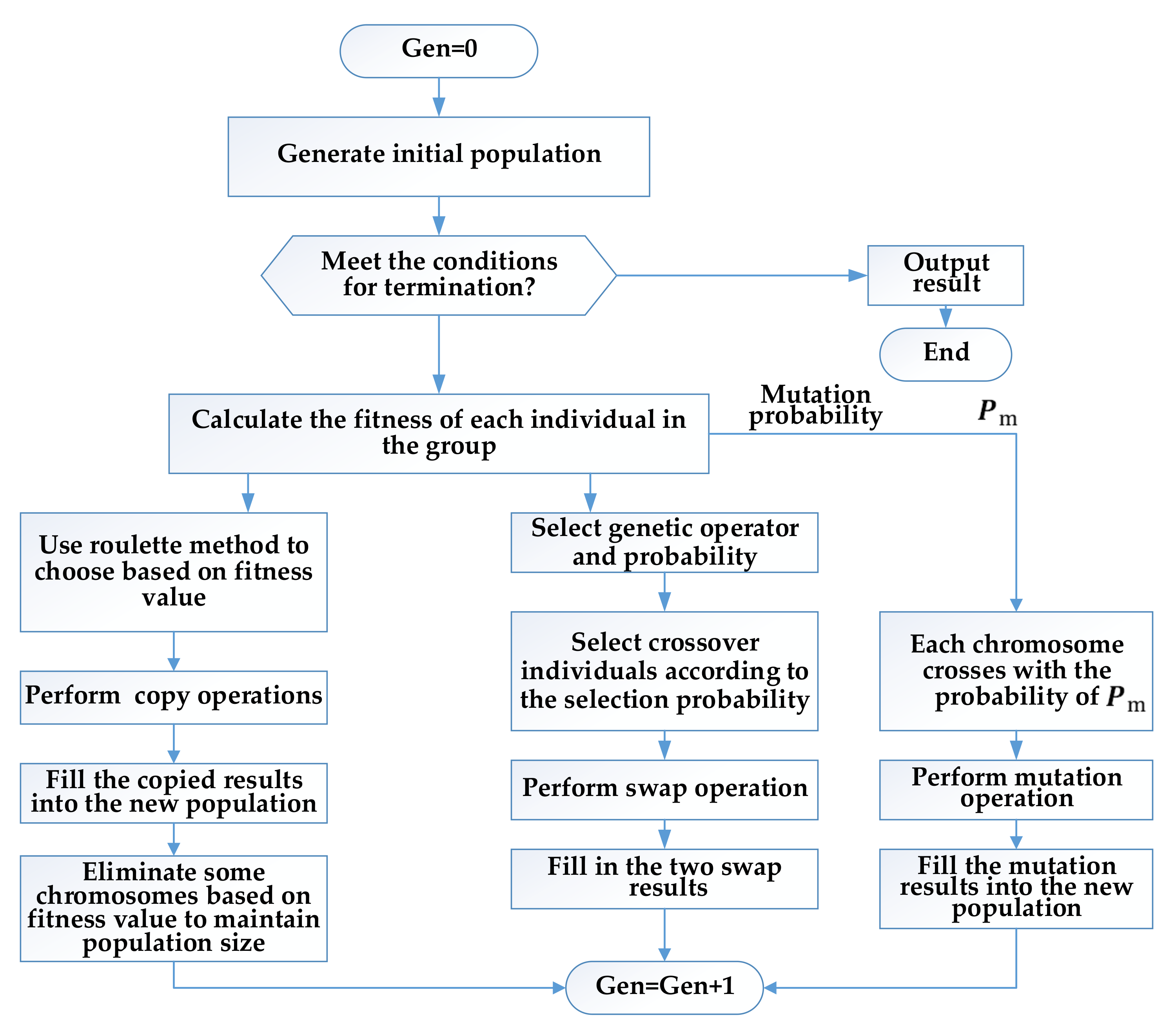
4.3.3. Genetic Algorithm
4.4. Network Congestion Control and Prevention Algorithm
- The number of service adjustments is the least. The genetic algorithm population always chooses the standard solution that has less disturbance with the offspring's inheritance and cross mutation. After several iterations, we chose the solution with the least disturbance to return and deploy.
- The link utilization rate is the most balanced after adjustment. The genetic algorithm population always chooses a solution with lower link utilization rate for offspring genetic and cross mutation. After several iterations, choose the solution with the lower maximum utilization rate to return and deploy.
- After adjustment, the link utilization is the most balanced, and the number of adjusted services is the least. The genetic algorithm population always selects the solution with the smallest maximum utilization and less disturbance for offspring inheritance and cross mutation. Then, the solution with the smaller maximum utilization and smaller disturbance is selected as the return deployment plan.
4.5. Resource Preemption Algorithm
- The number of disturbed services is the least during preemption. We select the low-priority request to be dismantled, optimize it with a heuristic algorithm and set the minimum number of dismantlement request services as the optimization goal. We iterate the algorithm until the algorithm converges and finally return the collection of low priority requests to be dismantled.
- Preempt low-priority services. We select the low-priority requests to be removed, optimize them with heuristic algorithms and set the minimum sum of low-priority requests to be removed as the optimization goal. We iterate the algorithm until the algorithm converges and finally return the collection of low priority requests for removal.
- The balance between the number of preempted services and the priority of preempted services. We select the low-priority request to be removed, optimize it with a heuristic algorithm and assign different weight coefficients to the number and priority of the removed service. Then, we take the smallest sum as the optimization goal. We iterate the algorithm until the algorithm converges and finally return the collection of low priority requests to be removed.
4.6. Balance of the Entire Network Traffic Algorithm
- Occupies the smallest bandwidth. We adopt the open corporate strategy and program framework (Open-CSPF) in the calculation of the service path, set the weight reader as the hop reader, and the path calculation for each service is carried out according to the principle of the smallest hop. We perform path calculations for the services in step (a) one by one and deploy them into the network to obtain a better solution. On the basis of this solution, we introduce a heuristic algorithm, multiply the bandwidth of the network by the number of hops and sum them. The sum is used to measure the performance of the solution. We look for a better solution until the algorithm converges and return to the final solution.
- Minimal cost: We adopt the Open-CSPF in the calculation of the service path, set the weight reader as the cost reader, and the path calculation for each service is performed according to the principle of minimum cost. We calculate the paths of the services in step (a) one by one and deploy them into the network to obtain a better solution. On the basis of this solution, we introduce a heuristic algorithm to multiply the network bandwidth by the cost and sum it up; the sum is used to measure the performance of the solution. We look for a better solution until the algorithm converges and return the final solution.
- Minimal delay: We adopt the Open-CSPF in the calculation of the services path, set the weight reader as the delay reader, and the path calculation for each service is performed according to the principle of minimum delay. We calculate the paths of the services in step (a) one by one and deploy them into the network to obtain a better solution. On the basis of this solution, we introduce a heuristic algorithm to multiply the network bandwidth by the delay and sum; the sum is used to measure the performance of the solution. We look for a better solution until the algorithm converges and return to the final solution.
5. Experimental Validation
5.1. Traffic Optimization Case Analysis
5.1.1. Maximum Utilization of Network Resources
5.1.2. Congestion Control and Prevention
5.1.3. Resource Load Sharing
5.2. Traffic Optimization Verification
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Valadarsky, A.; Schapira, M.; Shahaf, D.; Tamar, A. Learning to Route. In Proceedings of the 16th ACM Workshop on Hot Topics in Networks (HotNets-XVI), Palo Alto, CA, USA, 30 November–1 December 2017; ACM: New York, NY, USA, 2017; pp. 185–191. [Google Scholar]
- Bai, H. A Survey on Artificial Intelligence for Network Routing Problems; University of New Mexico: Albuquerque, NM, USA, 2007. [Google Scholar]
- Fortz, B.; Rexford, J.; Thorup, M. Traffic engineering with traditional IP routing protocols. Comm. Mag. 2002, 40, 118–124. [Google Scholar] [CrossRef]
- Kandula, S.; Katabi, D.; Davie, B.; Charny, A. Walking the tightrope. ACM SIGCOMM Comput. Commun. Rev. 2005, 35, 253–264. [Google Scholar] [CrossRef]
- Kumar, P.; Yuan, Y.; Yu, C.; Foster, N.; Kleinberg, R.D.; Soulé, R. Kulfi: Robust Traffic Engineering Using Semi-Oblivious Routing. Available online: https://arxiv.org/pdf/1603.01203.pdf (accessed on 3 March 2016).
- Yousaf, F.Z.; Bredel, M.; Schaller, S.; Schneider, F. NFV and SDN—Key technology enablers for 5G networks. IEEE J. Sel. Areas Commun. 2017, 35, 2468–2478. [Google Scholar] [CrossRef]
- Wang, S.Y. Comparison of SDN OpenFlow network simulator and emulators: EstiNet vs. Mininet. In Proceedings of the IEEE Symposium on Computers and Communications, Funchal, Portugal, 23–26 June 2014; pp. 1–6. [Google Scholar]
- Mostafaei, H.; Lospoto, G.; di Lallo, R.; Rimondini, M.; di Battista, G. A framework for multi-provider virtual private networks in software-defined federated networks. Int. J. Netw. Manag. 2020, 30, e2116. [Google Scholar] [CrossRef]
- Gouveia, R.; Aparício, J.; Soares, J.; Parreira, B.; Sargento, S.; Carapinha, J. SDN framework for connectivity services. In Proceedings of the IEEE International Conference on Communications, Sydney, Australia, 10–14 June 2014; pp. 3058–3063. [Google Scholar]
- Benzekki, K.; El Fergougui, A.; Elbelrhiti Elalaoui, A. Software-defined networking (SDN): A survey. Secur. Commun. Netw. 2016, 9, 5803–5833. [Google Scholar] [CrossRef]
- Khan, S.; Gani, A.; Wahab, A.W.A.; Guizani, M.; Khan, M.K. Topology discovery in software defined networks: Threats, taxonomy, and state-of-the-art. IEEE Commun. Surv. Tutor. 2017, 19, 303–324. [Google Scholar] [CrossRef]
- SDN White Paper. Available online: https://www.opennetworking.org/download-after/sdn-transport-api-interoperability-demonstration-executive-overview-technical-white-paper-download/ (accessed on 28 November 2019).
- Open Networking Foundation (ONF). Available online: https://www.opennetworking.org/ (accessed on 28 November 2019).
- Feamster, N.; Rexford, J.; Zegura, E. The road to SDN. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 87–98. [Google Scholar] [CrossRef]
- Oloduowo, A.; Babalola, A.H.; Daniel, A.K. Solving Network Routing Problem Using Artificial Intelligent Techniques. Br. J. Math. Comput. Sci. 2016, 17, 1–9. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Tang, F.; Mao, B.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems. IEEE Commun. Surv. Tutor. 2017, 19, 2432–2455. [Google Scholar] [CrossRef]
- Qadir, J. Artificial intelligence based cognitive routing for cognitive radio networks. Artif. Intell. Rev. 2016, 45, 25–96. [Google Scholar] [CrossRef]
- Wu, Y.-J.; Hwang, P.-C.; Hwang, W.-S.; Cheng, M.-H. Artificial Intelligence Enabled Routing in Software Defined Networking. Appl. Sci. 2020, 10, 6564. [Google Scholar] [CrossRef]
- Mata, J.; de Miguel, I.; Durán, R.J.; Merayo, N.; Singh, S.K.; Jukan, A.; Chamania, M. Artificial intelligence (AI) methods in optical networks: A comprehensive survey. Opt. Switch. Netw. 2018, 28, 43–57. [Google Scholar] [CrossRef]
- Mao, B.; Fadlullah, Z.M.; Tang, F.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. Routing or computing? The paradigm shifts towards intelligent computer network packet transmission based on deep learning. IEEE Trans. Comput. 2017, 66, 1946–1960. [Google Scholar] [CrossRef]
- Al-Fares, M.; Radhakrishnan, S.; Raghavan, B.; Huang, N.; Vahdat, A. Hedera: Dynamic Flow Scheduling for Data Center Networks. In Proceedings of the 7th USENIX Conference on Networked Systems Design and Implementation, San Jose, CA, USA, 28–30 April 2010. [Google Scholar]
- Barbancho, J.; León, C.; Molina, F.J.; Barbancho, A. Using artificial intelligence in routing schemes for wireless networks. Comput. Commun. 2007, 30, 2802–2811. [Google Scholar] [CrossRef]
- Panno, D.; Riolo, S. An enhanced joint scheduling scheme for GBR and non-GBR services in 5G RAN. Wirel. Netw. 2020, 26, 3033–3052. [Google Scholar] [CrossRef]
- Ye, Y.; Fang, H.; Nie, D. Optimization and application of 5G bearer network backhaul bandwidth estimation model. Telecommun. Sci. 2020, 36, 138–143. [Google Scholar]
- Black, P.E. Dictionary of Algorithms and Data Structures; U.S. National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2012. [Google Scholar]
- Bang-Jensen, J.; Gutin, G.; Yeo, A. When the greedy algorithm fails. Discret. Optim. 2004, 1, 121–127. [Google Scholar] [CrossRef]
- Yen, J.Y. An algorithm for finding shortest routes from all source nodes to a given destination in general networks. Q. Appl. Math. 1970, 27, 526–530. [Google Scholar] [CrossRef]
- Zungeru, A.M.; Ang, L.; Seng, K.P. Classical and swarm intelligence based routing protocols for wireless sensor networks: A survey and comparison. J. Netw. Comput. Appl. 2012, 35, 1508–1536. [Google Scholar] [CrossRef]
- Willmott, S.; Faltings, B.; Frei, C.; Calisti, M. Organization and Coordination for On-Line Routing in Communications Networks. In Software Agents for Future Communication Systems; Hayzelden, A.L.G., Bigham, J., Eds.; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Dorigo, M. Particle swarm optimization. Scholarpedia 2008, 3, 1486. [Google Scholar] [CrossRef]
- Clerc, M. Particle Swarm Optimization; ISTE: London, UK, 2006. [Google Scholar]
- Clerc, M.; Kennedy, J. The particle swarm-explosion, stability and convergence in a multidimensional complex space. IEEE Trans. Evol. Comput. 2002, 6, 58–73. [Google Scholar] [CrossRef]
- Engelbrecht, A.P. Fundamentals of Computational Swarm Intelligence; John Wiley & Sons: Chichester, UK, 2005. [Google Scholar]
- Henderson, D.; Jacobson, S.H.; Johnson, A.W. The Theory and Practice of Simulated Annealing. In Handbook of Metaheuristics; International Series in Operations Research & Management, Science; Glover, F., Kochenberger, G.A., Eds.; Springer: Boston, MA, USA, 2003; Volume 57. [Google Scholar]
- Laarhoven, P.; Aarts, E. Simulated Annealing: Theory and Applications; Springer: Dordrecht, The Netherlands, 1987. [Google Scholar]
- Ledesma, S.; Ruiz, J.; Garcia, G. Simulated Annealing Evolution, Simulated Annealing—Advances, Applications and Hybridizations, Marcos de Sales Guerra Tsuzuki; IntechOpen: London, UK, 2012; Available online: https://www.intechopen.com/books/simulated-annealing-advances-applications-and-hybridizations/simulated-annealing-evolution (accessed on 29 August 2012).
- Askarzadeh, A.; Coelho, L.d.S.; Klein, C.E.; Mariani, V.C. A population-based simulated annealing algorithm for global optimization. In Proceedings of the 2016 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Budapest, Hungary, 9–12 October 2016; pp. 4626–4633. [Google Scholar]
- Jennings, P.C.; Lysgaard, S.; Hummelshøj, J.S.; Vegge, T.; Bligaard, T. Genetic algorithms for computational materials discovery accelerated by machine learning. Npj Comput. Mater. 2019, 5, 46. [Google Scholar] [CrossRef]
- Katoch, S.; Chauhan, S.S.; Kumar, V. A review on genetic algorithm: Past, present, and future. Multimedia Tools Appl. 2021, 80, 8091–8126. [Google Scholar] [CrossRef] [PubMed]
- Ohn, H. Holland: Genetic algorithms. Scholarpedia 2012, 7, 1482. [Google Scholar]




| Path 1 | S1 -> A -> B -> C -> E1 |
| Path 2 | S1 -> A -> C -> E1 |
| Path 3 | S2 -> A -> B -> C -> E2 |
| Path 4 | S2 -> A -> C -> E2 |
| Path 5 | S3 -> A -> B -> C -> E3 |
| Path 6 | S3 -> A -> C -> E3 |
| Service | Start Point | End Point | Size |
|---|---|---|---|
| Service 1 | S1 | E1 | 40 M |
| Service 2 | S2 | E2 | 30 M |
| Service 3 | S3 | E3 | 20 M |
| Scheme | Path 1 | Path 2 | Path 3 | Path 4 | Path 5 | Path 6 | Maximum Link Utilization |
|---|---|---|---|---|---|---|---|
| Service 1 | √ | 60% | |||||
| Service 2 | √ | ||||||
| Service 3 | √ |
| Service | Path 1 | Path 2 | Path 3 | Path 4 | Path 5 | Path 6 | Maximum Link Utilization |
|---|---|---|---|---|---|---|---|
| Service 1 | √ | 33.3% | |||||
| Service 2 | √ | ||||||
| Service 3 | √ |
| Service | Path 1 | Path 2 | Path 3 | Path 4 | Path 5 | Path 6 | Maximum Link Utilization |
|---|---|---|---|---|---|---|---|
| Service 1 | √ | 80% | |||||
| Service 2 | √ | ||||||
| Service 3 | √ | ||||||
| Service 4 | √ |
| Service | Path 1 | Path 2 | Path 3 | Path 4 | Path 5 | Path 6 | Maximum Link Utilization |
|---|---|---|---|---|---|---|---|
| Service 1 | √ | 80% | |||||
| Service 2 | √ | ||||||
| Service 3 | √ | ||||||
| Service 5 | √ | ||||||
| Service 6 | √ |
| Testing Scenarios | Congestion Threshold | Original Highest Link Utilization | Number of Congested Links | Number of Congested Services | Convergence Time (Less Than) | Disturbance is Not Considered: Reduce Link Utilization, Regardless of the Number of Services | ||||
|---|---|---|---|---|---|---|---|---|---|---|
| Maximum Link Utilization after Optimization | Number of Adjusted Services | Number of Adjusted Links | Remaining Congested Links | Number of Remaining Congested Services | ||||||
| case 1 | 50% | 56.32% | 6 | 431 | 10 s | 41.11% | 374 | 9088 | 0 | 0 |
| case 2 | 55% | 77.66% | 14 | 634 | 10 s | 53.59% | 592 | 12,055 | 0 | 0 |
| case 3 | 50% | 72.49% | 14 | 547 | 10 s | 42.92% | 444 | 12,658 | 0 | 0 |
| case 4 | 50% | 78.65% | 13 | 555 | 10 s | 44.91% | 463 | 12,640 | 0 | 0 |
| case 5 | 50% | 75.63% | 14 | 667 | 10 s | 48.14% | 504 | 12,859 | 0 | 0 |
| case 6 | 50% | 77.43% | 13 | 586 | 10 s | 44.39% | 462 | 12,619 | 0 | 0 |
| case 7 | 50% | 62.41% | 9 | 342 | 10 s | 42.57% | 340 | 9471 | 0 | 0 |
| case 8 | 50% | 76.18% | 16 | 541 | 10 s | 44.76% | 421 | 12,043 | 0 | 0 |
| case 9 | 50% | 91.76% | 10 | 472 | 10 s | 49.61% | 440 | 11,809 | 0 | 0 |
| case 10 | 50% | 72.66% | 18 | 606 | 10 s | 45.14% | 484 | 12,421 | 0 | 0 |
| Testing Scenarios | Congestion Threshold | Original Highest Link Utilization | Number of Congested Links | Number of Congested Services | Convergence Time (Less Than) | Consider Disturbance: Reduce Link Utilization and Fewer Service Adjustments | ||||
|---|---|---|---|---|---|---|---|---|---|---|
| Maximum Link Utilization after Optimization | Number of Adjusted Services | Number of Adjusted Links | Remaining Congested Links | Number of Remaining Congested Services | ||||||
| case 1 | 50% | 56.32% | 6 | 431 | 10 s | 44.70% | 123 | 3594 | 0 | 0 |
| case 2 | 55% | 77.66% | 14 | 634 | 10 s | 52.07% | 245 | 4932 | 0 | 0 |
| case 3 | 50% | 72.49% | 14 | 547 | 10 s | 46.09% | 219 | 5804 | 0 | 0 |
| case 4 | 50% | 78.65% | 13 | 555 | 10 s | 47.92% | 187 | 5109 | 0 | 0 |
| case 5 | 50% | 75.63% | 14 | 667 | 10 s | 49.30% | 273 | 6241 | 0 | 0 |
| case 6 | 50% | 77.43% | 13 | 586 | 10 s | 45.43% | 231 | 5931 | 0 | 0 |
| case 7 | 50% | 62.41% | 9 | 342 | 10 s | 44.41% | 110 | 3080 | 0 | 0 |
| case 8 | 50% | 76.18% | 16 | 541 | 10 s | 45.80% | 227 | 6002 | 0 | 0 |
| case 9 | 55% | 91.76% | 10 | 472 | 10 s | 55.00% | 187 | 5013 | 0 | 0 |
| case 10 | 50% | 72.66% | 18 | 606 | 10 s | 48.42% | 214 | 5849 | 0 | 0 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guo, A.; Yuan, C. Network Intelligent Control and Traffic Optimization Based on SDN and Artificial Intelligence. Electronics 2021, 10, 700. https://doi.org/10.3390/electronics10060700
Guo A, Yuan C. Network Intelligent Control and Traffic Optimization Based on SDN and Artificial Intelligence. Electronics. 2021; 10(6):700. https://doi.org/10.3390/electronics10060700
Chicago/Turabian StyleGuo, Aipeng, and Chunhui Yuan. 2021. "Network Intelligent Control and Traffic Optimization Based on SDN and Artificial Intelligence" Electronics 10, no. 6: 700. https://doi.org/10.3390/electronics10060700
APA StyleGuo, A., & Yuan, C. (2021). Network Intelligent Control and Traffic Optimization Based on SDN and Artificial Intelligence. Electronics, 10(6), 700. https://doi.org/10.3390/electronics10060700






