Identity and Access Management Resilience against Intentional Risk for Blockchain-Based IOT Platforms
Abstract
1. Introduction
1.1. Internet of Things
1.2. Blockchain Can Contribute to a Secure IoT World
1.3. Complex Networks Analysis: A Useful Tool to Feature Systems
1.4. Intentional Risk Management Via Complex Networks Analysis
1.4.1. Intentional Risk Management in IoT
1.4.2. Structure of the Paper
2. Related Works
2.1. Security Requirements for IoT
2.2. Blockchain. The Internet of Value Applied to IoT
2.3. IOTA
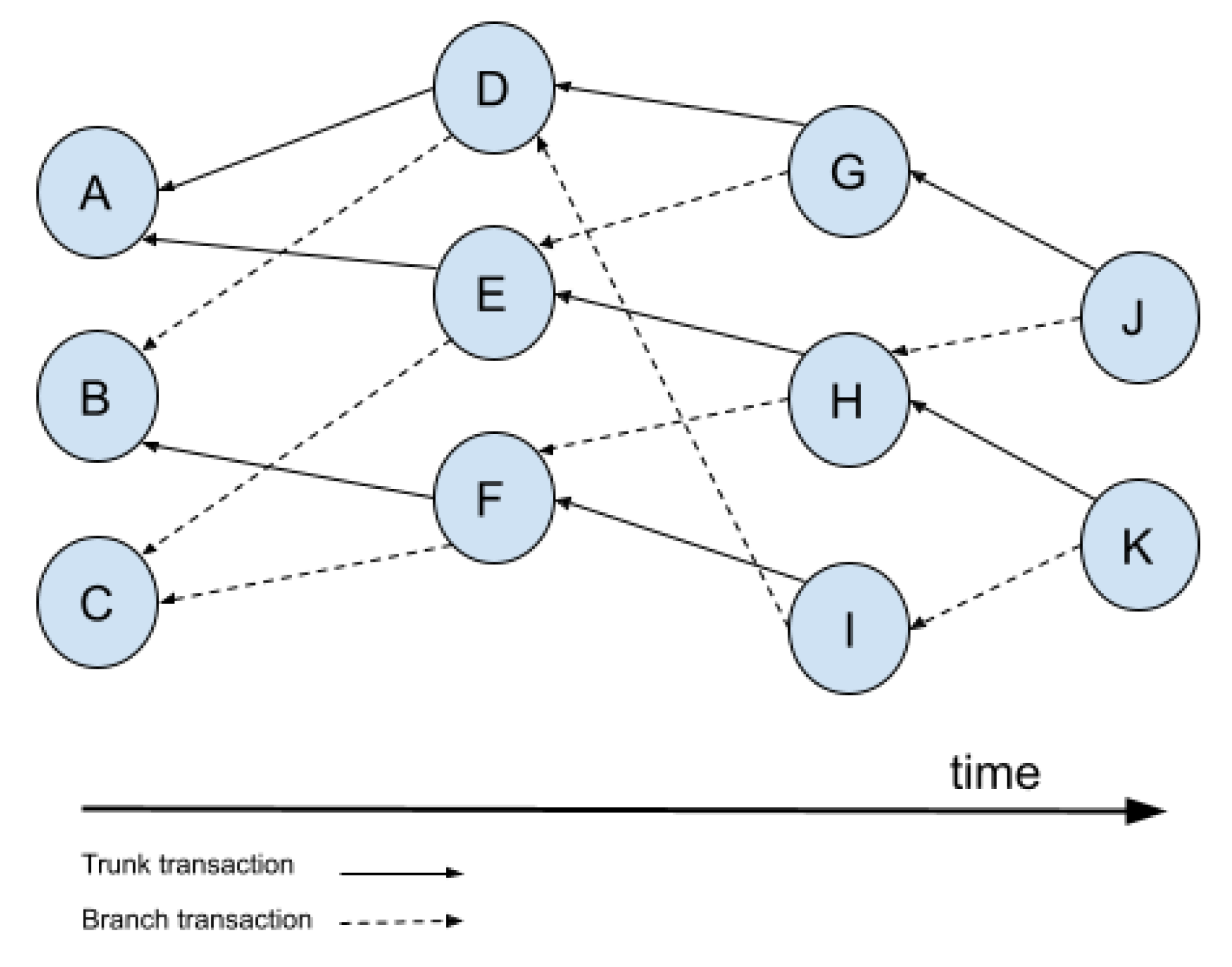
2.3.1. IOTA DAG. The Tangle
2.3.2. The Coordinator of the Tangle
2.3.3. The Coordicide Preparing IOTA Consolidation
- Global node identities: Using off-tangle non-post-quantum public key cryptography to identify nodes. Every node would then add its public key to every signed message.
- Sybil attack protection via a reputation system: Providing a reputation value (called mana) to every node, equivalent to the total number of funds transferred by that node. This is a specific kind of proof of ownership. They distinguish between pending mana (based on the tokens the node holds) and mana (spent tokens by that node in its transactions). Both pending mana and mana decay at a rate proportional to the stake they hold.
- Autopeering: Nodes in IOTA keep a copy of the ledger state, i.e., the tangle. Nodes share information on transactions with the neighbour nodes. This is called peering. This process is currently done manually by the node operator, and hence, could be subject to an ill-intentioned actor controlling all peering neighbours of a node. This is called the eclipse attack. IOTA designers propose the use of public-key-based cryptography to automate this node information exchange process (called autopeering). In order to do that, a regular transfer of nodes’ public keys will be required.
- Rate control: Many blockchain implementations, Bitcoin and Ethereum included, use proof of work. Proof of work is a consensus mechanism that act as a built-in network congestion limitation mechanism and deters attacks to a network by requiring the execution of a computationally demanding process for a network participant to get the service it requests confirmed. In the case of blockchains, the service is mainly transaction confirmation. A proof of work consensus mechanism favours the blockchain that has taken the most energy to be built (chainwork), in other words, “the longest chain wins.” This is measured by the number of hashes required to produce the current chain [42]. For a blockchain to be trustful, honest participants in the network need to control the majority of the network’s hashing power. The challenge of proof of work in IOTA is the limited computing capacity of most of their participants since IOTA positions itself as the distributed ledger for IoT devices. IOTA designers of Coordicide are studying adaptive (to the computing power of the device) proof of work (POW) algorithms.
- Decoupling of conflict resolution and transaction validation: These are the two hardest actions to solve. Regarding the consensus mechanism, the Coordicide proposes the use of a mana-based fast probabilistic consensus (FPC) [39,40,41] or “cellular automata” (CA, also known as majority dynamics). On tip selection, the initial biased random walk used to select transactions to validate transforms into an “almost” uniformly random tip selection among non-lazy, i.e., active nodes.
2.3.4. The Path to Coordicide
2.3.5. Reuse or Not of Addresses
2.3.6. IOTA Use Cases
2.4. Security Incidents in IOTA
2.5. IoTeX
2.5.1. IoTeX Rootchain and Subchains Fast Consensus with Instant Finality
2.5.2. Privacy in IoTeX Rootchain
- (a)
- The relayable payment code (on top of the stealth address technique) uses hashed timelock contracts (HTLCs) to offer receiver privacy [56].
- (b)
- The use of a secure multi-party computation protocol (SMCP) among bootstrapping blockchain nodes facilitates the use of a ring signature to preserve sender privacy [51].
- (c)
- The use of Pedersen cryptographic commitments provides transaction value privacy [51].
2.5.3. IoTeX Use Cases
2.5.4. IOTA vs. IoTeX
2.6. Security Incidents in Public Blockchains
2.7. Identity and Access Management in IoT
2.7.1. A Set of Technologies to Solve a Complex Security Problem: Cloud and Edge Computing
2.7.2. DIoTA: A Decentralised Ledger-Based Framework for Data Authenticity Protection in IoT Systems
- (a)
- The ledgers in DIoTA are permissioned and decentralised. Reading data could be granted to the public, but any node running ledgers supporting IoT data-producing devices need to hold a public key certificate from a trusted public key infrastructure (PKI).
- (b)
- Device authentication is a prerequisite for data authenticity protection.
- (c)
- The edge ledger maintains the data authenticity protection schema rather than the IoT devices.
- (d)
- The IoT device only needs to store a private key, crypto parameters such as a certificate and a list of edge ledger nodes.
- (e)
- IoT data authenticity protection is based on a number of cryptographic keys. Those keys are stored in blocks within a blockchain, a distributed edge or global ledger, which runs on top of the corresponding edge or cloud servers.
- (f)
- Reading blockchain data to look for keys and certificates is not resource-intensive. Low energy consumption in IoT devices is a functional requirement. Proposals on caching and scheduling policies to reduce transmission delays and power consumption, such as [71] and a dynamic routing algorithm based on energy-efficient relay selection [72], confirm the need to keep computing operations in the IoT device lightweight.
2.8. Complex Network Analysis: From Graphs to Networks
2.9. Intentional Risk Management
2.9.1. Static Risk and Dynamic Risk
2.9.2. Attackers’ Expected Profit
- -
- Expected income, i.e., the value for them.
- -
- The expenses they run (depending on the accessibility).
- -
- Risk to the attacker (related to the degree of anonymity they can have and applicable deterrent legal, economic and social consequences). Calculated risk values should be intrinsic to the attributes of the network and require no expert estimates.
3. Methodology
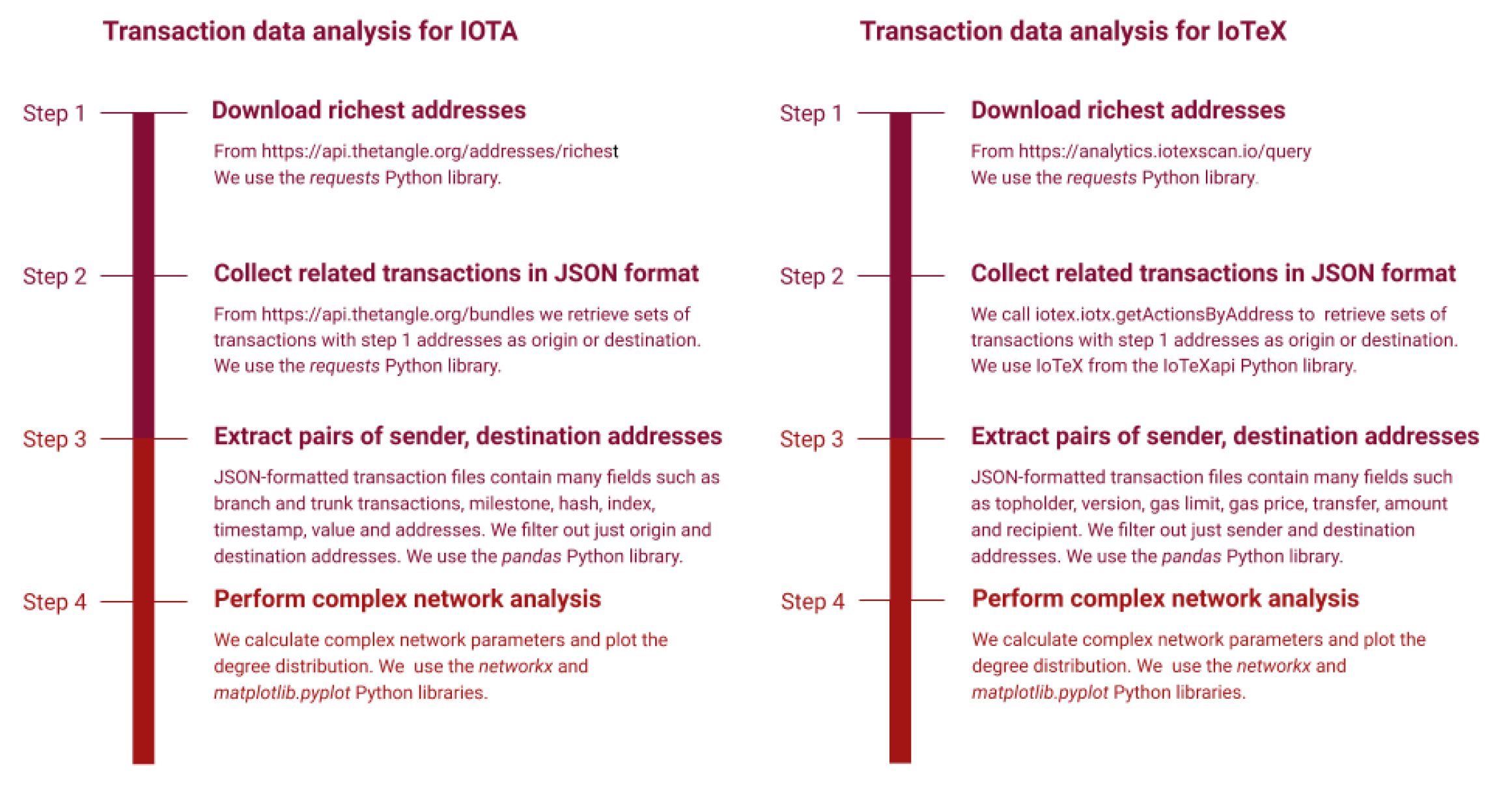
3.1. Transaction Data Collection
3.2. Transaction Data Preparation: Sender, Destination Pairs
3.3. Complex Network Analysis
4. Analysis and Results
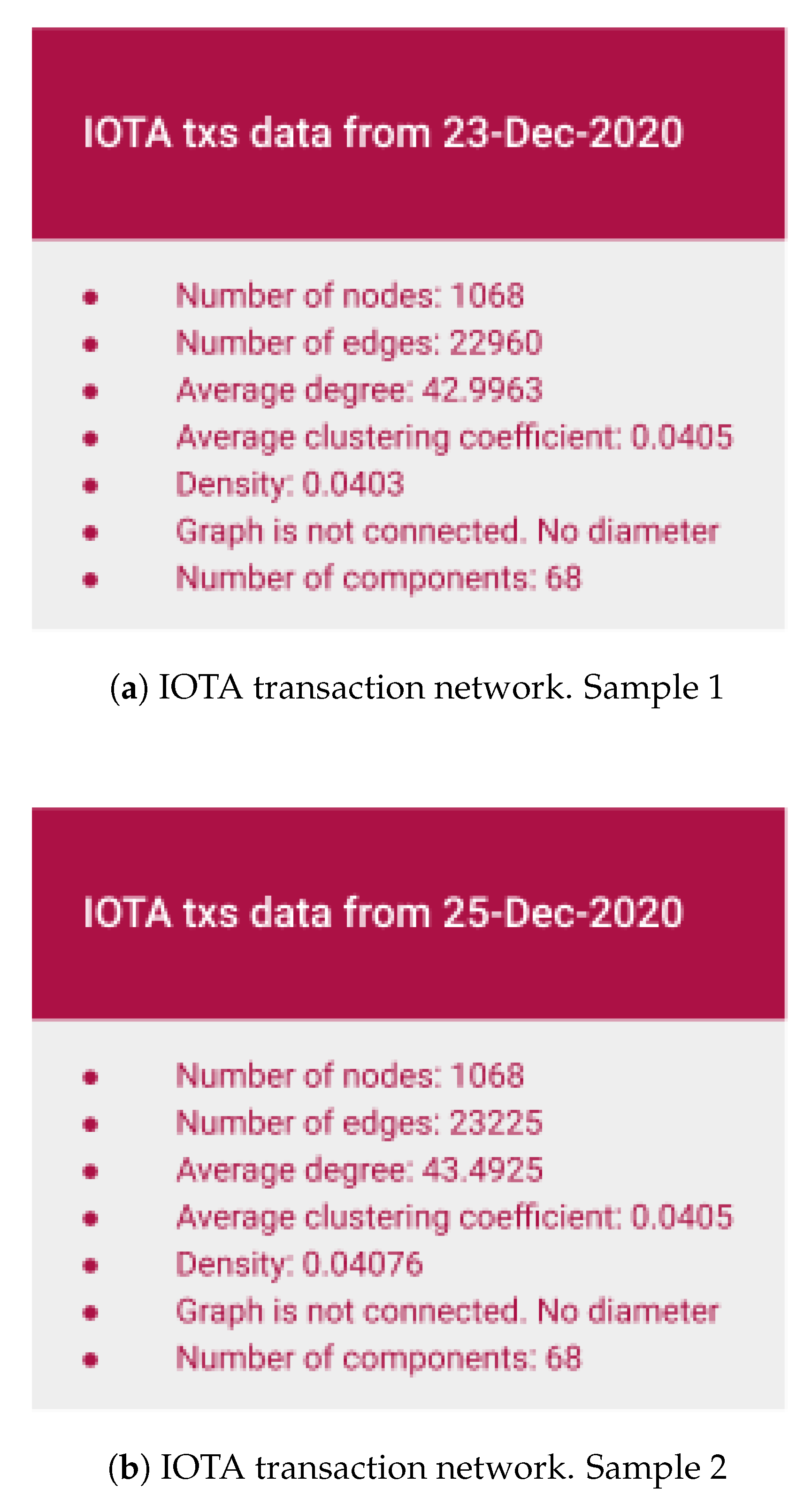
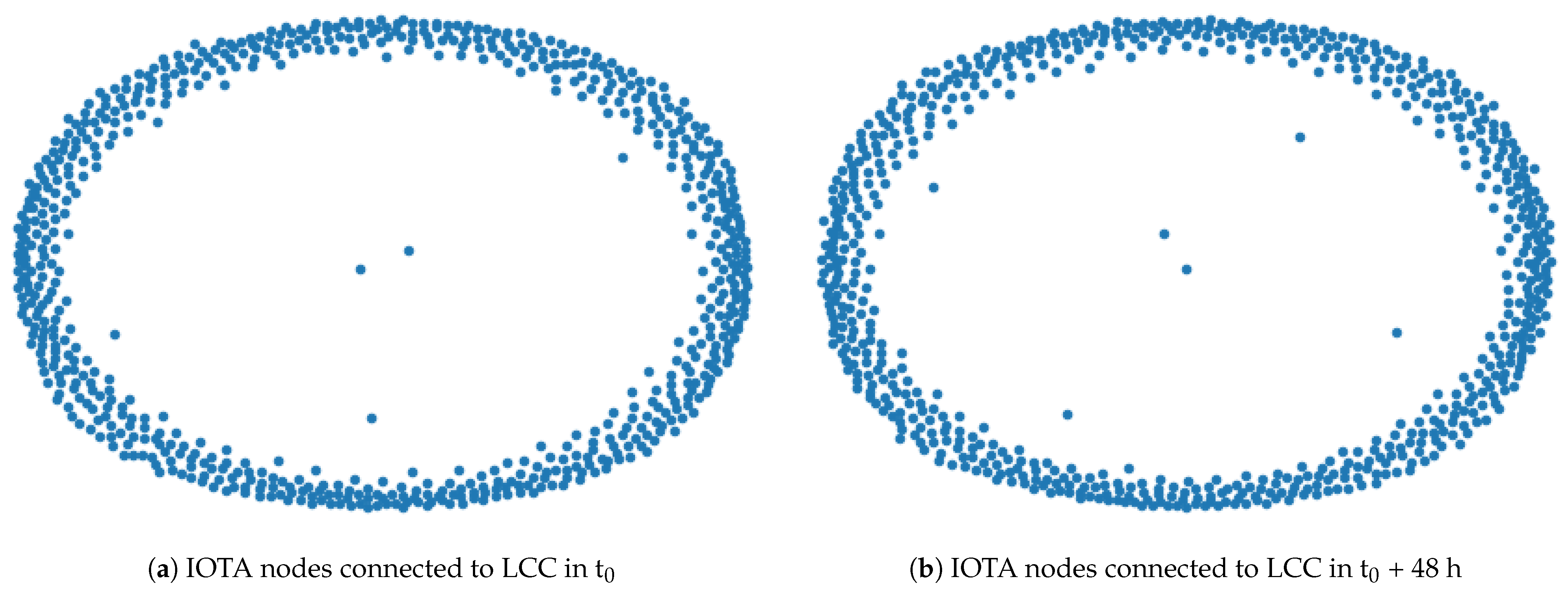
4.1. IOTA Complex Network Analysis
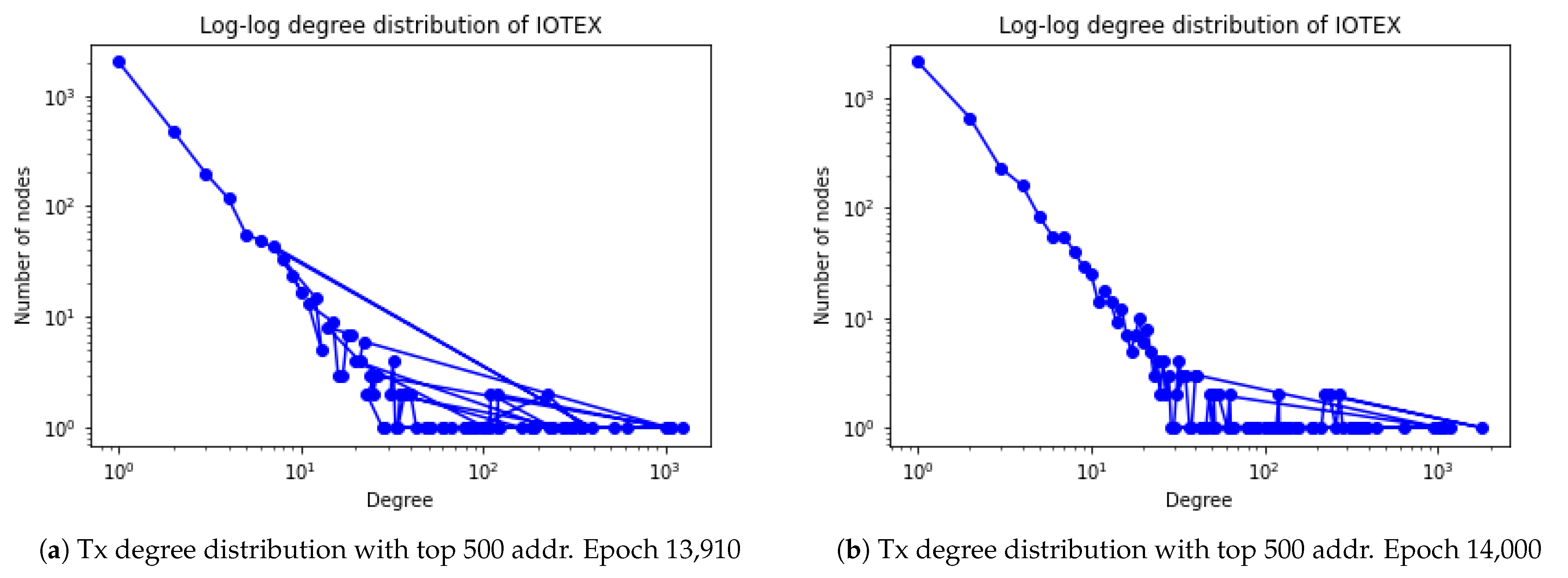
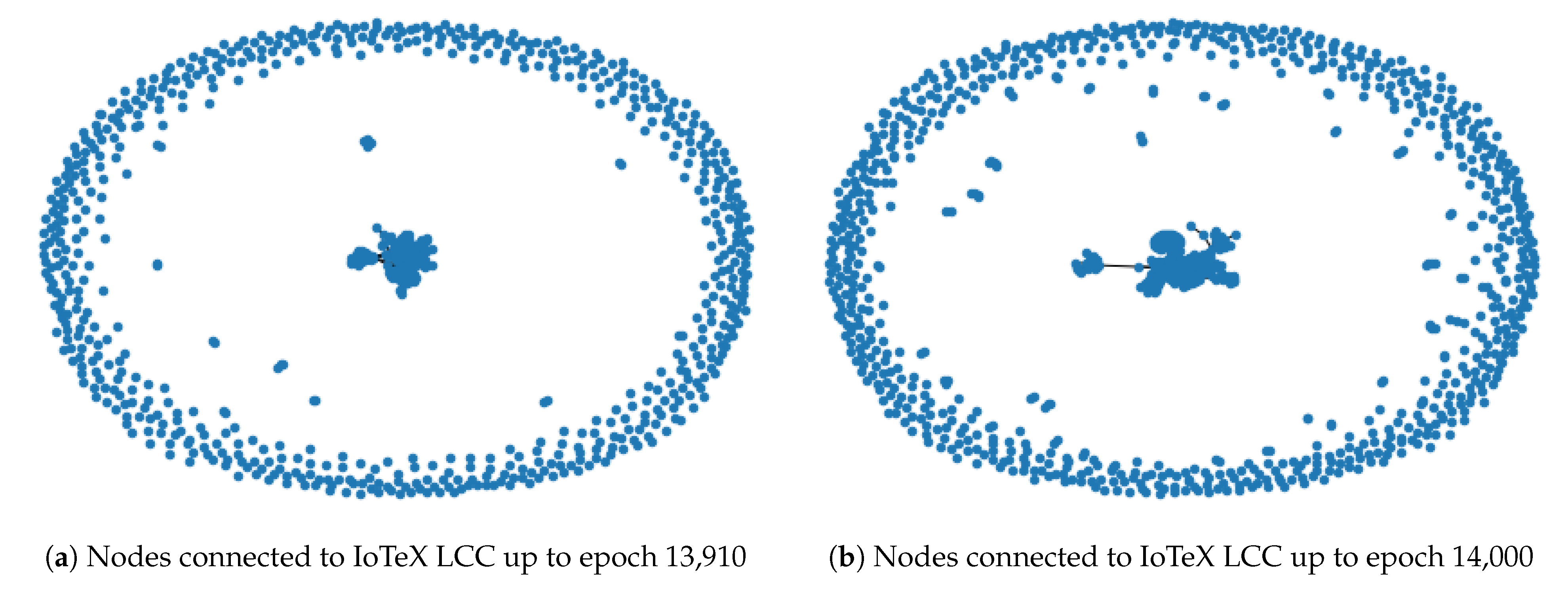
4.2. IoTeX Complex Network Analysis
4.3. Largest Connected Components in IOTA and IoTeX
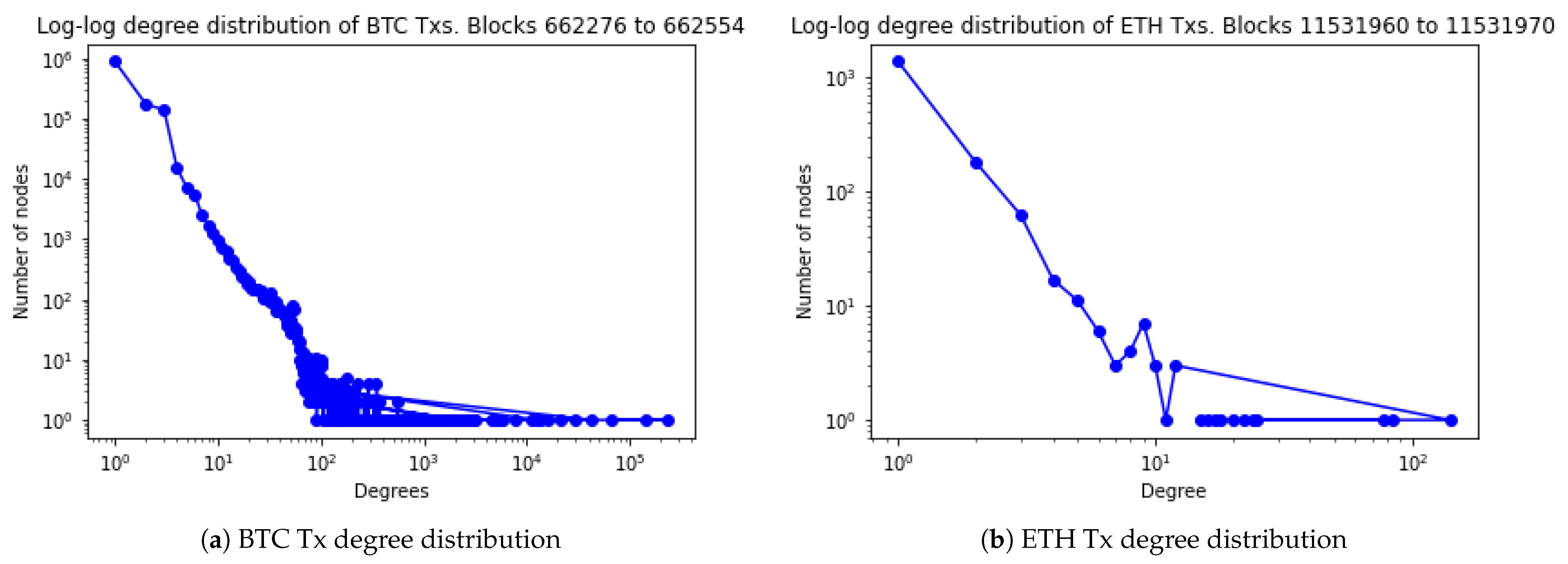
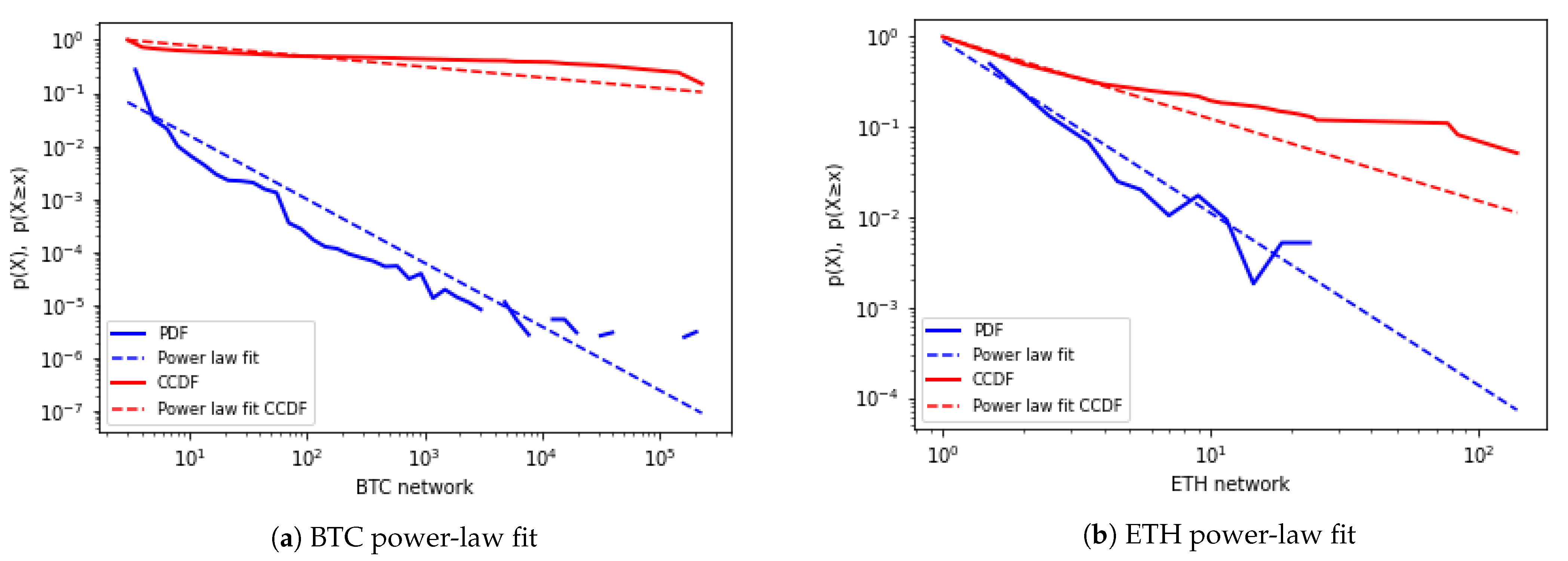
4.4. Comparison with Bitcoin and Ethereum Complex Network Analysis
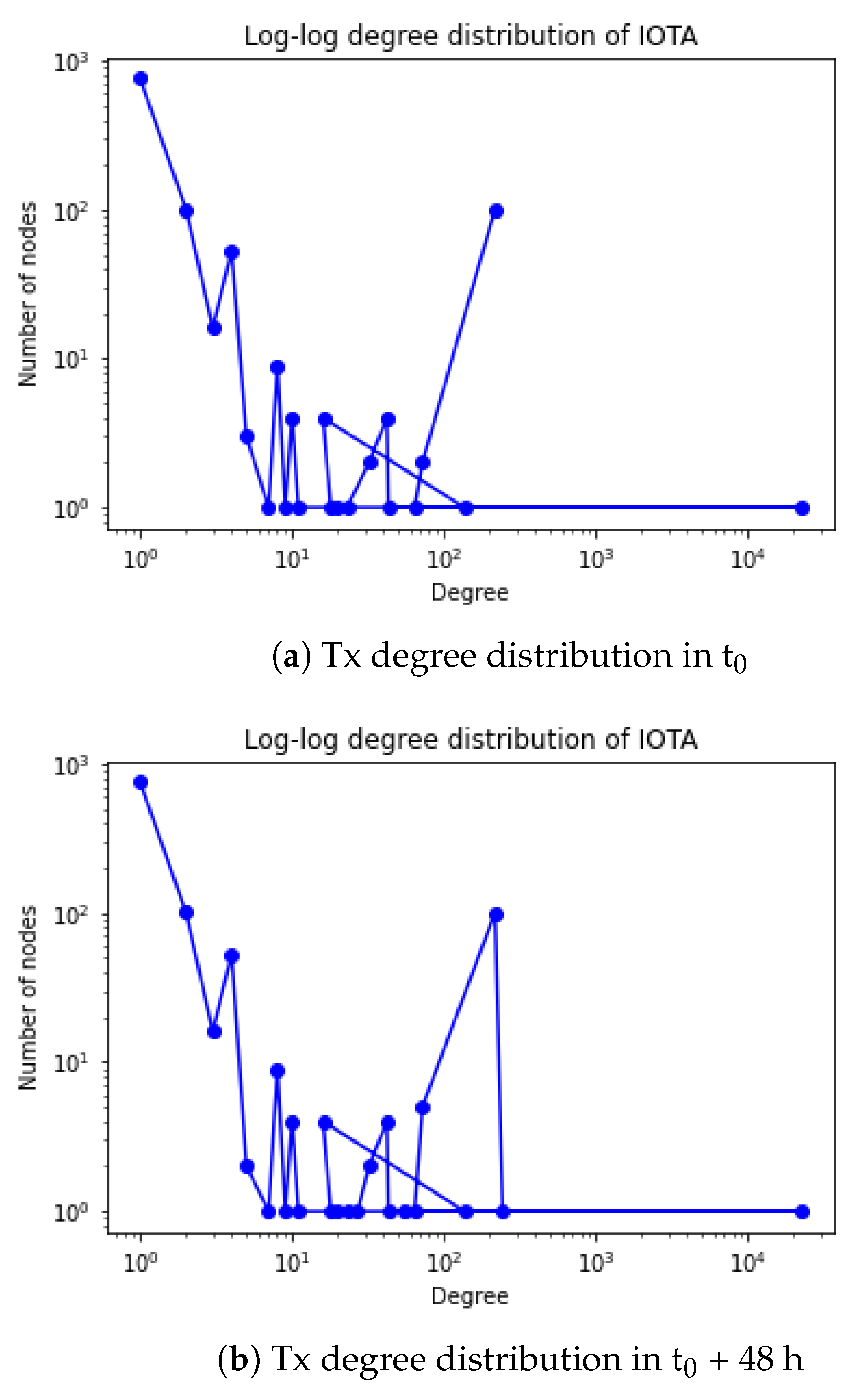
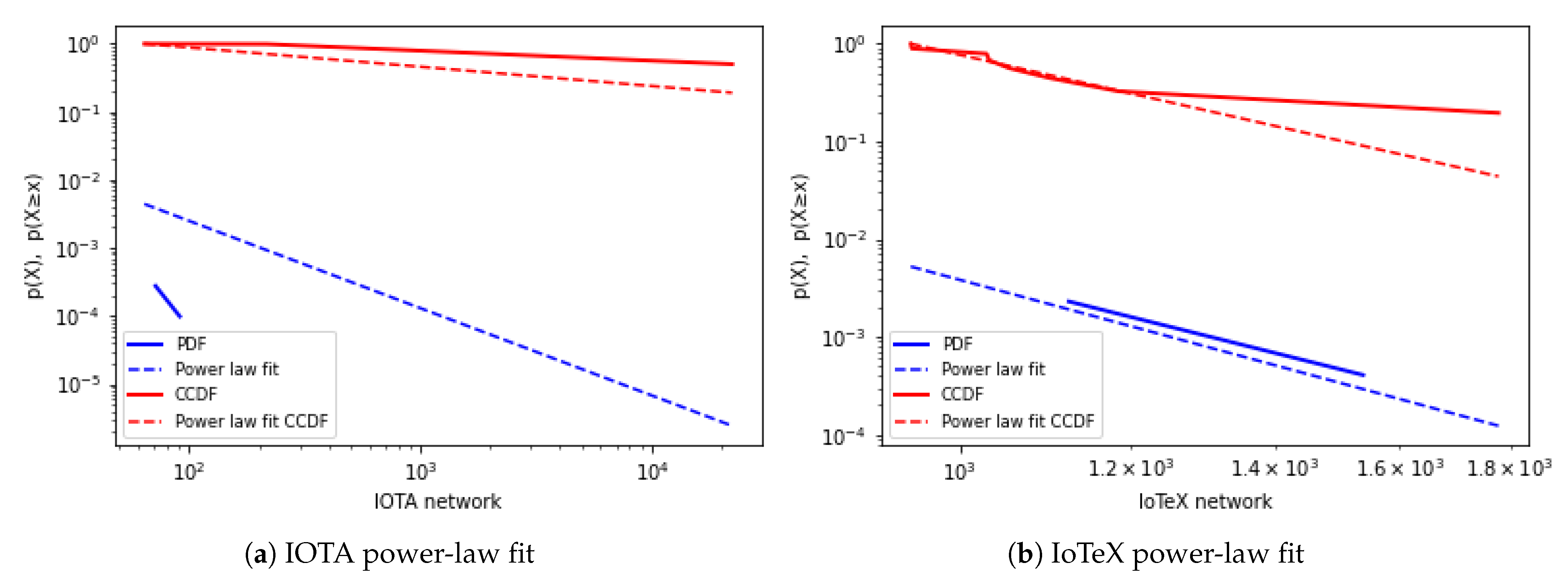
4.5. Analysis of Heavy-Tailed Distributions
5. Conclusions
5.1. Blockchain Answers a Subset of IoT Security Requirements
5.2. Identity and Access Management is a Key Security Requirement to Build Resilience against Intentional Risk
5.3. IoTeX and Possibly IOTA Networks Are Scale-Free. They Require Resilience against Intentional Risk
5.4. DIoTA Provides IoTex with Resilient Identity and Access Management
5.5. Resilience against Intentional Risk Requires an IAM Concept That Transcends a Single Blockchain
6. Future Work
- (a)
- Transforming the time series created by IOTA and IoTeX transactions into complex networks to go deeper into their analysis using the visibility graph proposed by Lacasa et al. [88].
- (b)
- Studying whether DIoTA can be further extended using any of the artificial intelligence (AI) solutions to secure IoT services in edge computing surveyed by Xu et al. [89].
- (c)
Author Contributions
Funding
Conflicts of Interest
References
- Number of Internet of Things (IoT) Connected Devices Worldwide in 2018, 2025 and 2030. Available online: https://www.statista.com/statistics/617136/digital-population-worldwide/ (accessed on 21 December 2020).
- Sallaba, M.; Siegel, D.; Becker, S. Deloitte Blockchain Institute. IoT Powered by Blockchain. How Blockchains Facilitate the Application of Digital Twins in IoT. May 2018. Available online: https://www2.deloitte.com/content/dam/Deloitte/de/Documents/Innovation/IoT-powered-by-Blockchain-Deloitte.pdf (accessed on 21 December 2020).
- Number of Internet of Things (IoT) Connected Devices Worldwide in 2018, 2025 and 2030. Available online: https://www.statista.com/statistics/802690/worldwide-connected-devices-by-access-technology/ (accessed on 21 December 2020).
- NIST. Creating a Profile Using the IoT Core Baseline and Non-Technical Baseline. NIST Interagency or Internal Report 8259C. December 2020. Available online: https://doi.org/10.6028/NIST.IR.8259C-draft (accessed on 21 December 2020).
- ETSI. Technical Specification. Cyber Security for Consumer Internet of Things. ETSI TS 103 645 V1.1.1 (2019-02). February 2019. Available online: https://www.etsi.org/deliver/etsi_ts/103600_103699/103645/01.01.01_60/ts_103645v010101p.pdf (accessed on 21 December 2020).
- NIST. Profile Using the IoT Core Baseline and Non-Technical Baseline for the Federal Government. NIST Interagency or Internal Report 8259D. December 2020. Available online: https://doi.org/10.6028/NIST.IR.8259D-draft (accessed on 21 December 2020).
- Newman, M.E.J. The Structure and Function of Complex Networks. SIAM Rev. 2003, 45, 167–257. [Google Scholar] [CrossRef]
- Newman, M.E.J. The Connected World. Santa Fe Institute, 2011. Available online: https://www.youtube.com/watch?v=yAtsm5xkb5c (accessed on 21 December 2020).
- Newman, M.E.J. Using Networks to Make Predictions. Santa Fe Institute. 2011. Available online: https://www.youtube.com/watch?v=rwA-y-XwjuU (accessed on 21 December 2020).
- Newman, M.E.J. What Networks Can Tell Us about the World. Santa Fe Institute. 2011. Available online: https://www.youtube.com/watch?v=lETt7IcDWLI (accessed on 21 December 2020).
- Chapela, V.; Criado, R.; Moral, S.; Romance, M. Intentional Risk Management through Complex Networks Analysis; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Boccaletti, S.; Latora, V.; Moreno, Y.; Chavez, M.; Hwang, D. Complex Networks: Structure and Dynamics. Phys. Rep. 2006, 175–308. [Google Scholar] [CrossRef]
- Boccaletti, S.; Buldú, J.; Criado, R.; Flores, J.; Latora, V.; Pello, J.; Romance, M. Multiscale Vulnerability of Complex Networks. Chaos Interdiscip. J. Nonlinear Sci. 2007, 175–308. [Google Scholar] [CrossRef]
- Alberto, P. Secure IT Up! In Cyber Insurance Due Diligence; Kroll Inc.: New York, NY, USA, 2012; pp. 6–7. ISBN 9781478314752. [Google Scholar]
- Andina, D.; Partida, A. IT Security Management: IT Securiteers—Setting up an IT Security Function. In Lecture Notes in Electrical Engineering; Springer: Berlin/Heidelberg, Germany, 2010; ISBN 9789048188819. [Google Scholar]
- ETSI. ETSI Releases First Globally Applicable Standard for Consumer IoT Security. February 2019. Available online: https://www.etsi.org/newsroom/press-releases/1549-2019-02-etsi-releases-first-globally-applicable-standard-for-consumer-iot-security (accessed on 21 December 2020).
- Fruhlinger, J. CSO Online. The Mirai Botnet Explained: How Teen Scammers and CCTV Cameras Almost Brought Down the Internet. 2018. Available online: https://www.csoonline.com/article/3258748/the-mirai-botnet-explained-how-teen-scammers-and-cctv-cameras-almost-brought-down-the-internet.html (accessed on 21 December 2020).
- NIST. IoT Device Cybersecurity Guidance for the Federal Government: Establishing IoT Device Cybersecurity Requirements. Draft NIST Special Publication 800-213. December 2020. Available online: https://doi.org/10.6028/NIST.SP.800-213-draft (accessed on 21 December 2020).
- Anthony, L. A Gentle Introduction to Blockchain Technology. Bitsonblocks.com. 2015. Available online: http://bitsonblocks.net/2015/09/09/a-gentle-introduction-to-blockchain-technology (accessed on 21 December 2020).
- Satoshi, N. Bitcoin: A Peer-to-Peer Electronic Cash System. Nakamotoinstitute.org. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 21 December 2020).
- ETH Corporate Site. Available online: https://www.ethereum.org/ (accessed on 21 December 2020).
- Coinmarketcap. Cryptocurrencies Market Capitalisation in Real Time. Available online: https://coinmarketcap.com/all/views/all/ (accessed on 21 December 2020).
- Papadodimas, G.; Palaiokrasas, G.; Litke, A.; Varvarigou, T. Implementation of Smart Contracts for Blockchain Based IoT Applications. Electrical and Computer Engineering Department National Technical University of Athens. November 2018. Available online: http://bloomen.io/wp-content/uploads/2018/11/ICCS-nof2018.pdf (accessed on 21 December 2020).
- Kurt Peker, Y.; Rodriguez, X.; Ericsson, Y.; Lee, S.; Perez, A. A Cost Analysis of Internet of Things Sensor Data Storage on Blockchain via Smart Contracts. Electronics 2020, 9, 244. [Google Scholar] [CrossRef]
- Zvi, S. k-Root-n: An Efficient Algorithm for Avoiding Short Term Double-Spending Alongside Distributed Ledger Technologies such as Blockchain. Information 2020, 11, 90. [Google Scholar]
- Blockchain.com. Transactions Per Second. Available online: https://www.blockchain.com/charts/transactions-per-second (accessed on 21 December 2020).
- Transactions Per Second. Available online: https://etherscan.io/ (accessed on 21 December 2020).
- Transactions Per Second in Blockchains. Available online: https://blocktivity.info/ (accessed on 21 December 2020).
- EOSIO Reaches a New Transaction Per Second Record: 9656. Available online: https://www.eosgo.io/news/eosio-reaches-new-transaction-per-second-record (accessed on 21 December 2020).
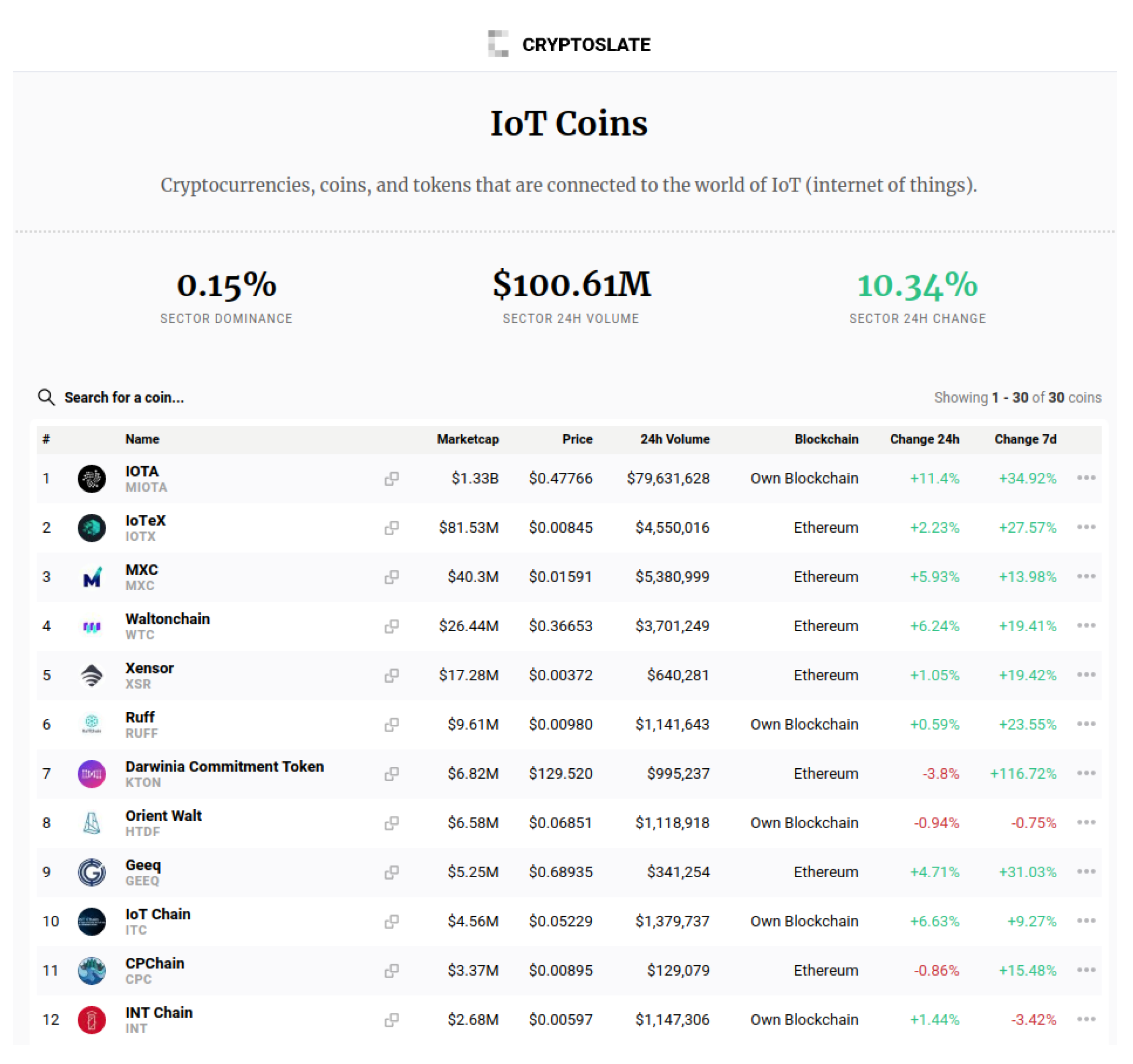
- IOT Crypto Coin Market Value. Available online: https://cryptoslate.com/cryptos/iot/ (accessed on 24 December 2020).
- IOTA. Introduction. Available online: https://www.iota.org/get-started/what-is-iota (accessed on 21 December 2020).
- Sun, F. UTXO vs Account/Balance Model. Available online: https://medium.com/@sunflora98/utxo-vs-account-balance-model-5e6470f4e0cf (accessed on 25 December 2020).
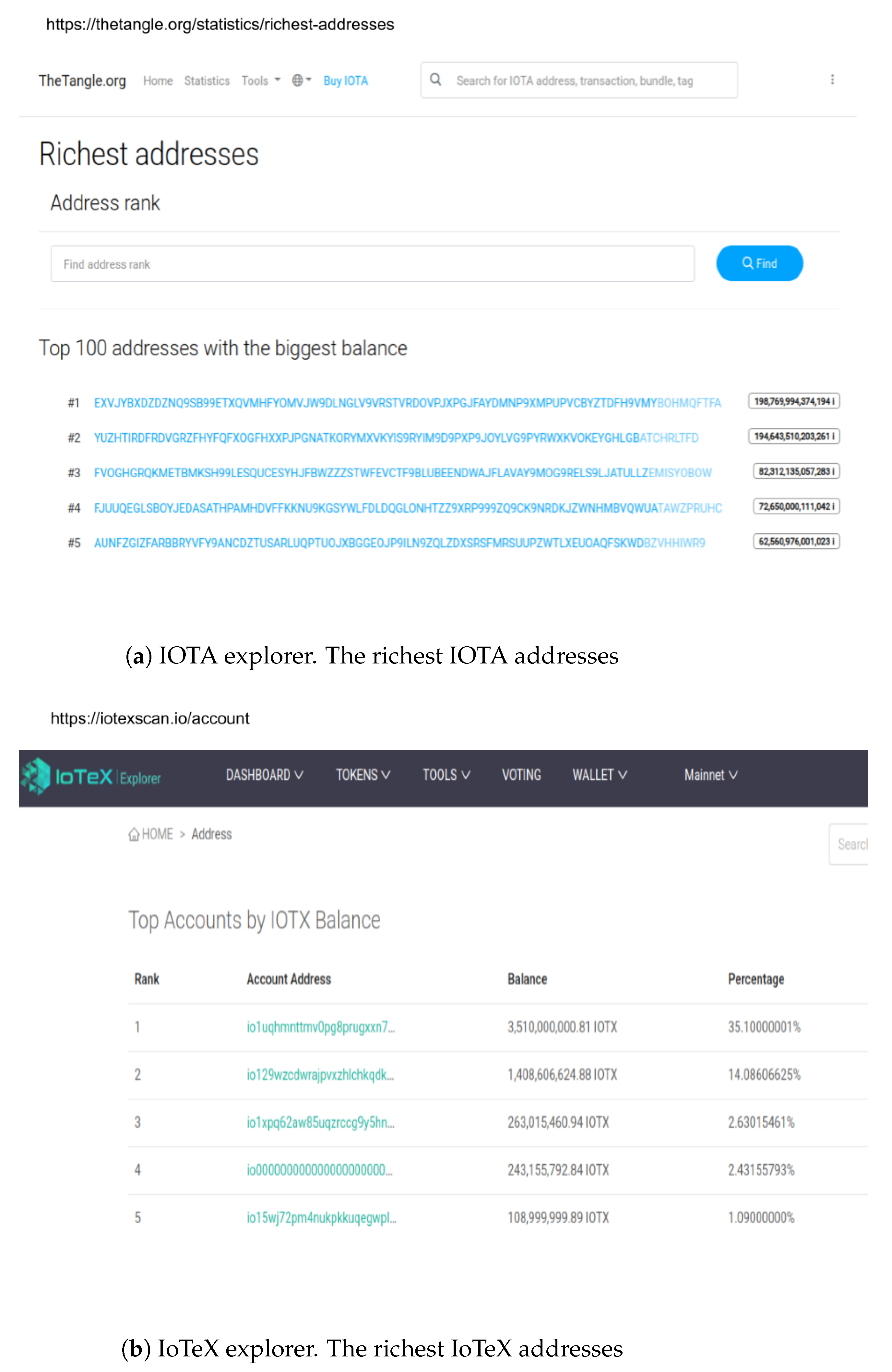
- IOTA Tangle Explorer. Available online: https://thetangle.org/ (accessed on 24 December 2020).
- IOTA Tangle Explorer. Available online: https://thetangle.org/nodes (accessed on 24 December 2020).
- Serguei, P. The Tangle. White Paper. Version 1.4.3. 2018. Available online: https://bit.ly/3e2edXo (accessed on 24 December 2020).
- Trifa, Z.; Khemakhem, M. Sybil Nodes as a Mitigation Strategy Against Sybil Attack. Procedia Comput. Sci. 2014, 32, 1135–1140. [Google Scholar] [CrossRef]
- Kusmierz, B.; Staupe, P.; Gal, A. Extracting Tangle Properties in Continuous Time via Large-Scale Simulations. 2018. Available online: https://tinyurl.com/yclxej5h (accessed on 26 December 2020).
- Popov, S.; Moog, H.; Camargo, D.; Capossele, A.; Dimitrov, V.; Gal, A.; Greve, A.; Kusmierz, B.; Mueller, S.; Penzkofer, A.; et al. The Coordicide. IOTA Foundation. 2020. Available online: https://files.iota.org/papers/20200120_Coordicide_WP.pdf (accessed on 24 December 2020).
- Capossele, A.; Mueller, S.; Penzkofer, A. Robustness and Efficiency of Leaderless Probabilistic Consensus Protocols within Byzantine Infrastructures. 2019. Available online: https://arxiv.org/abs/1911.08787 (accessed on 25 December 2020).
- Müller, S.; Penzkofer, A.; Kuśmierz, B.; Camargo, D.; Buchanan, W.J. Fast Probabilistic Consensus with Weighted Votes. In Proceedings of the Future Technologies Conference (FTC), Vancouver, BC, Canada, 5–6 November 2020; Arai, K., Kapoor, S., Bhatia, R., Eds.; Springer: Cham, Switzerland, 2020; Volume 1289. [Google Scholar] [CrossRef]
- Popov, S.; Buchanan, W.J. FPC-BI: Fast Probabilistic Consensus within Byzantine Infrastructures. J. Parallel Distrib. Comput. 2021, 147, 77–86. [Google Scholar] [CrossRef]
- Chain, L. Learn Me a Bitcoin. Available online: https://bit.ly/38uPTw0 (accessed on 24 December 2020).
- Release Strategy for Chrysalis. IOTA 1.5. Available online: https://blog.iota.org/release-strategy-for-chrysalis-iota-1-5-4ea8741ea3a1 (accessed on 24 December 2020).
- A Proposal for Reusable Addresses (Part 1). IOTA Blog. Available online: https://blog.iota.org/a-proposal-for-reusable-addresses-part1-bc6dbca84cbf (accessed on 7 July 2020).
- A Proposal for Reusable Addresses (Part 2). IOTA Blog. Available online: https://blog.iota.org/a-proposal-for-reusable-addresses-part-2-d83d328ff1b3 (accessed on 7 July 2020).
- A Proposal for Reusable Addresses (Part 3). IOTA Blog. Available online: https://blog.iota.org/a-proposal-for-reusable-addresses-part-3-9ec6fa1929d7 (accessed on 7 July 2020).
- IOTA Corporate Site. Explore IOTA Industries. Available online: https://www.iota.org/solutions/industries (accessed on 25 December 2020).
- Guo, F.; Xiao, X.; Hecker, A.; Dustdar, S. Characterizing IOTA Tangle with Empirical Data. 2020 IEEE Global Communications Conference. Taiwan Communications for Human and Machine Intelligence. Available online: https://globecom2020.ieee-globecom.org/program/symposia-tuesday (accessed on 26 December 2020).
- PSA. Do Not Use Online Seed Generators. Reddit. Available online: https://www.reddit.com/r/Iota/comments/7rmc55/psa_do_not_use_online_seed_generators/ (accessed on 28 December 2020).
- IOTA Foundation Suspends Network, Probes Fund Theft in Trinitytrinity Wallet. Coindesk. Available online: https://www.coindesk.com/iota-foundation-suspends-network-probes-fund-theft-in-trinity-wallet (accessed on 28 December 2020).
- IoTex Team and Introduction Portal. Available online: https://v1.iotex.io/ (accessed on 24 December 2020).
- IoTeX Team. IoTeX. A Decentralised Network for Internet of Things Powered by a Privacy-Centric Blockchain. White Paper. Version 1.5. 12 July 2018. Available online: https://v1.iotex.io/white-paper (accessed on 24 December 2020).
- Stafford, B. Decision and Control; Wiley: London, UK, 1966. [Google Scholar]
- Fan, X. Scalable Practical Byzantine Fault Tolerance with Short-Lived Signature Schemes. In Proceedings of the 28th Annual International Conference on Computer Science and Software Engineering, Markham, ON, Canada, 29–31 October 2018; pp. 245–256. [Google Scholar] [CrossRef]
- Fan, X.; Chai, Q. Roll-DPoS: A Randomized Delegated Proof of Stake Scheme for Scalable Blockchain-Based Internet of Things Systems. In Proceedings of the MobiQuitous’18: Proceedings of the 15th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York City, NY, USA, 5–7 November 2018; pp. 482–484. [Google Scholar] [CrossRef]
- Fan, X. Faster Dual-Key Stealth Address for Blockchain-Based Internet of Things Systems. 2018. Available online: https://link.springer.com/chapter/10.1007/978-3-319-94478-4_9 (accessed on 29 December 2020).
- Fan, X.; Zhong, Z.; Chai, Q.; Guo, D. Ucam: A User-Centric, Blockchain-Based and End-to-End Secure Home IP Camera System. In Security and Privacy in Communication Networks, Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Park, N., Sun, K., Foresti, S., Butler, K., Saxena, N., Eds.; Springer: Cham, Switzerland, 2020; Volume 336. [Google Scholar] [CrossRef]
- Xu, L.; Chen, L.; Gao, Z.; Carranco, L.; Fan, X.; Shah, N.; Diallo, N.; Shi, W. Supporting Blockchain-Based Cryptocurrency Mobile Payment With Smart Devices. IEEE Consum. Electron. Mag. 2020, 9, 26–33. [Google Scholar] [CrossRef]
- Blockchain News Site. Information Related to Incidents. Available online: https://www.coindesk.com (accessed on 28 December 2020).
- Nyamtiga, B.W.; Sicato, J.C.S.; Rathore, S.; Sung, Y.; Park, J.H. Blockchain-Based Secure Storage Management with Edge Computing for IoT. Electronics 2019, 8, 828. [Google Scholar] [CrossRef]
- Xiao, Z.; Dai, X.; Jiang, H.; Wang, D.; Chen, H.; Yang, L.; Zeng, F. Vehicular Task Offloading via Heat-Aware MEC Cooperation Using Game-Theoretic Method. IEEE Internet Things J. 2020, 7, 2038–2052. [Google Scholar] [CrossRef]
- Sittón-Candanedo, I.; Alonso, R.S.; García, Ó.; Gil, A.B.; Rodríguez-González, S. A Review on Edge Computing in Smart Energy by means of a Systematic Mapping Study. Electronics 2020, 9, 48. [Google Scholar] [CrossRef]
- Fan, X.; Chai, Q.; Li, Z.; Pan, T. Decentralized IoT Data Authorization with Pebble Tracker. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020. [Google Scholar] [CrossRef]
- Xu, L.; Chen, L.; Gao, Z.; Fan, X.; Suh, T.; Shi, W. DIoTA: Decentralized-Ledger-Based Framework for Data Authenticity Protection in IoT Systems. IEEE Netw. 2020, 34, 38–46. [Google Scholar] [CrossRef]
- Choi, Y.-J.; Kang, H.-J.; Lee, I.-G. Scalable and Secure Internet of Things Connectivity. Electronics 2019, 8, 752. [Google Scholar] [CrossRef]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Trust Management in Decentralized IoT Access Control System. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 4–7 May 2020; pp. 1–9. [Google Scholar] [CrossRef]
- Huang, Y.; Guan, X.; Chen, H.; Liang, Y.; Yuan, S.; Ohtsuki, T. Risk Assessment of Private Information Inference for Motion Sensor Embedded IoT Devices. IEEE Trans. Emerg. Top. Comput. Intell. 2020, 4, 265–275. [Google Scholar] [CrossRef]
- Wang, D.; Fan, J.; Xiao, Z.; Jiang, H.; Chen, H.; Zeng, F.; Li, K. Stop-and-Wait: Discover Aggregation Effect Based on Private Car Trajectory Data. IEEE Trans. Intell. Transp. Syst. 2019, 20, 3623–3633. [Google Scholar] [CrossRef]
- Chen, H.; Gao, F.; Martins, M.H.T.; Huang, P.; Liang, J. Accurate and Efficient Node Localization for Mobile Sensor Networks. Mob. Netw. Appl. 2013, 18, 141–147. [Google Scholar] [CrossRef]
- Chen, H.; Liu, B.; Huang, P.; Liang, J.; Gu, Y. Mobility-Assisted Node Localization Based on TOA Measurements without Time Synchronization in Wireless Sensor Networks. Mob. Netw. Appl. 2012, 17, 90–99. [Google Scholar] [CrossRef]
- Zhang, Z.; Chen, Z.; Hua, M.; Li, C.; Huang, Y.; Yang, L. Double Coded Caching in Ultra Dense Networks: Caching and Multicast Scheduling via Deep Reinforcement Learning. IEEE Trans. Commun. 2020, 68, 1071–1086. [Google Scholar] [CrossRef]
- Ding, Z.; Shen, L.; Chen, H.; Yan, F.; Ansari, N. Energy-Efficient Relay-Selection-Based Dynamic Routing Algorithm for IoT-Oriented Software-Defined WSNs. IEEE Internet Things J. 2020, 7, 9050–9065. [Google Scholar] [CrossRef]
- da Fontoura Costa, L.; Oliveira, O.N., Jr.; Travieso, G.; Aparecido Rodrigues, F.; Ribeiro Villas Boas, P.; Antiqueira, L.; Palhares Viana, M.; Correa Rocha, L.E. Analyzing and modeling real-world phenomena with complex networks: A survey of applications. Adv. Phys. 2011, 60, 329–412. [Google Scholar] [CrossRef]
- Beauguitte, L.; Ducruet, C. Scale-free and small-world networks in geographical research: A critical examination. In Proceedings of the 17th European Colloquium on Theoretical and Quantitative Geography, Athènes, Greece, 15 September 2019; pp. 663–671. Available online: https://halshs.archives-ouvertes.fr/halshs-00623927 (accessed on 21 December 2020).
- Barabási, A. Network Science. 2014. Creative Commons: CC BY-NC-SA 2.0. Available online: http://barabasi.com/book/network-science (accessed on 29 December 2020).
- Chapela, M.; Sekulic, V.; Ignjatovic, A.; Bertino, E.; Jha, S. Interdependent Security Risk Analysis of Hosts and Flows. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2325–2339. [Google Scholar] [CrossRef]
- Bitcoin Blockchain Explorer. Available online: https://www.blockchain.com/explorer (accessed on 28 December 2020).
- Ethereum Blockchain Explorer. Available online: https://etherscan.io/ (accessed on 28 December 2020).
- IOTA Blockchain Explorer. Available online: https://explorer.iota.org/mainnet (accessed on 28 December 2020).
- IoTeX Blockchain Explorer. Available online: https://iotexscan.io/ (accessed on 28 December 2020).
- Ethereum Blockchain Explorer API. Available online: https://infura.io/ (accessed on 28 December 2020).
- Liang, J.; Li, L.; Zeng, D. Evolutionary dynamics of cryptocurrency transaction networks: An empirical study. PLoS ONE 2018, 13, e0202202. [Google Scholar] [CrossRef]
- Javarone, M.A.; Wright, C.S. From Bitcoin to Bitcoin Cash: A network analysis. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 77–81. [Google Scholar] [CrossRef]
- Lischke, M.; Fabian, B. Analyzing the Bitcoin Network: The First Four Years. Future Internet 2016, 8, 7. [Google Scholar] [CrossRef]
- Goldstein, M.L.; Morris, S.A.; Yen, G. Problems with Fitting to the Power-Law Distribution. Phys. Condens. Matter 2004, 41. [Google Scholar] [CrossRef]
- Alstott, J.; Bullmore, E.; Plenz, D. Powerlaw: A Python Package for Analysis of Heavy-Tailed Distributions. PLoS ONE 2014, 9, e85777. [Google Scholar] [CrossRef]
- Lacasa, L.; Luque, B.; Ballesteros, F.; Luque, J.; Nuño, J. From time series to complex networks: The visibility graph. Proc. Natl. Acad. Sci. USA 2008, 105, 4972–4975. [Google Scholar] [CrossRef] [PubMed]
- Xu, Z.; Liu, W.; Huang, J.; Yang, C.; Lu, J.; Tan, H. Artificial Intelligence for Securing IoT Services in Edge Computing: A Survey. Hindawi. Secur. Commun. Netw. J. 2020, 8872586. [Google Scholar] [CrossRef]
- Wang, K.; Gou, C.; Duan, Y.; Lin, Y.; Zheng, X.; Wang, F. Generative adversarial networks: Introduction and outlook. IEEE/CAA J. Autom. Sin. 2017, 4, 588–598. [Google Scholar] [CrossRef]
- Wang, Y. A Mathematical Introduction to Generative Adversarial Nets (GAN). Available online: https://arxiv.org/abs/2009.00169 (accessed on 30 December 2020).
- Reid, F.; Harrigan, M. An Analysis of Anonymity in the Bitcoin System. In Proceedings of the IEEE Third International Conference on Privacy, Security, Risk and Trust, Boston, MA, USA, 9–11 October 2011; pp. 1318–1326. [Google Scholar] [CrossRef]

| Provision | Key Topic |
|---|---|
| 1 | No universal default passwords |
| 2 | Report vulnerabilities |
| 3 | Keep software updated |
| 4 | Securely store credentials and security-sensitive data |
| 5 | Communicate securely |
| 6 | Minimised exposed attack surfaces |
| 7 | Ensure software integrity |
| 8 | Protect personal data |
| 9 | Make systems resilient to outages |
| 10 | Examine system telemetry data |
| 11 | Make deletion of personal data easy |
| 12 | Facilitate installation and maintenance |
| 13 | Validate input data |
| Capability | Key Abilities |
|---|---|
| Device identity | Unique physical and digital device identifier |
| Device configuration | Display and device configuration control |
| Data protection | Cryptographic capabilities and secure storage |
| Logical access to interfaces | Authentication, authentication, use and interface control |
| Software update | Possibility to update code |
| Cybersecurity state awareness | Event logging and monitoring, audit trail protection |
| Device security | Secure operation and communication |
| Capability | Key Abilities |
|---|---|
| Documentation | Device acquisition and maintenance description during device lifetime |
| Information and query reception | Cybersecurity reports and queries |
| Information dissemination | Software maintenance and cybersecurity alerts |
| Education and awareness | Device and cybersecurity awareness |
| Processor | Architecture | Tps |
|---|---|---|
| Visa | Centralised | 5000 |
| Bitcoin | Distributed | 3 to 4, pikes of 7 |
| Ethereum | Distributed | 12 on average |
| IOTA | Distributed | below 10 |
| IoTeX | Distributed | f(chain) |
| EOS | Distributed | 36 |
| Blockchain Property | IoT Requirement |
|---|---|
| Decentralization | Scalability, privacy |
| Byzantine fault tolerance | Availability, security |
| Transparency & Immutability | Trust |
| Programmability | Extensibility |
| Criteria | IOTA | IoTeX |
|---|---|---|
| Year of creation | 2015 | 2017 |
| Market cap (USD) | 1.3 B | 81 M |
| Technology | public permissionless DAG | public permissionless root blockchain |
| Subchains | No | Yes (permissioned possible) |
| Balance model | UTXO | Balance |
| Transaction fees | No | Low |
| Consensus protocol | Proof of work | Proof of stake |
| Privacy | Not in the DAG | Possible in the rootchain |
| Known security incidents | 2 | 0 |
| Date | BLK | Incident | Root Cause |
|---|---|---|---|
| 2011 | BTC | Mt.Gox exchange hack1 | Admin laptop compromised |
| 2014 | BTC | Mt.Gox exchange hack2 | Leak in hot wallet and no security monitoring |
| 2016 | ETH | In a DAO. One Distributed Autonomous Organisation | Code errors in smart contract |
| 2016 | BTC | Bitfinex exchange | Flaw in multi-signature accounts and Bitgo wallet |
| 2017 | ETH | CoinDash Initial Coin Offering | Website hacked (ICO address changed) |
| 2017 | ETH | Parity wallet breach 1 and 2 | Vulnerable contract code |
| 2017 | ETH | Enigma project scam | Website, slack channel and mailing list compromised |
| 2017 | ETH and BTC | Tether tokens stolen | Vulnerable wallet |
| 2018 | NEM | Coincheck exchange hacked | Vulnerable hot non-multi signature wallet |
| Token | Time Window | Addresses | Transactions | #Rich Addresses |
|---|---|---|---|---|
| IOTA | 23-December-2020 | 1068 | 22,960 | 100 |
| IOTA | 25-December-2020 | 1068 | 23,225 | 100 |
| IoTeX | endepoch = 13,910 (in December-2020) | 3190 | 10,222 | 500 |
| IoTeX | endepoch = 14,000 (in December-2020) | 3709 | 13,935 | 500 |
| Token | Time Window | Blocks (Number) | Addresses | Transactions |
|---|---|---|---|---|
| BTC | 21–23-December-2020 | 662,276–662,554 (278) | 1,241,548 | 1,385,212 |
| ETH | 26-December-2020 | 11,531,960–11,531,970 (11) | 1677 | 1363 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Partida, A.; Criado, R.; Romance, M. Identity and Access Management Resilience against Intentional Risk for Blockchain-Based IOT Platforms. Electronics 2021, 10, 378. https://doi.org/10.3390/electronics10040378
Partida A, Criado R, Romance M. Identity and Access Management Resilience against Intentional Risk for Blockchain-Based IOT Platforms. Electronics. 2021; 10(4):378. https://doi.org/10.3390/electronics10040378
Chicago/Turabian StylePartida, Alberto, Regino Criado, and Miguel Romance. 2021. "Identity and Access Management Resilience against Intentional Risk for Blockchain-Based IOT Platforms" Electronics 10, no. 4: 378. https://doi.org/10.3390/electronics10040378
APA StylePartida, A., Criado, R., & Romance, M. (2021). Identity and Access Management Resilience against Intentional Risk for Blockchain-Based IOT Platforms. Electronics, 10(4), 378. https://doi.org/10.3390/electronics10040378






