Next-Generation Blockchain-Enabled Virtualized Cloud Security Solutions: Review and Open Challenges
Abstract
:1. Introduction
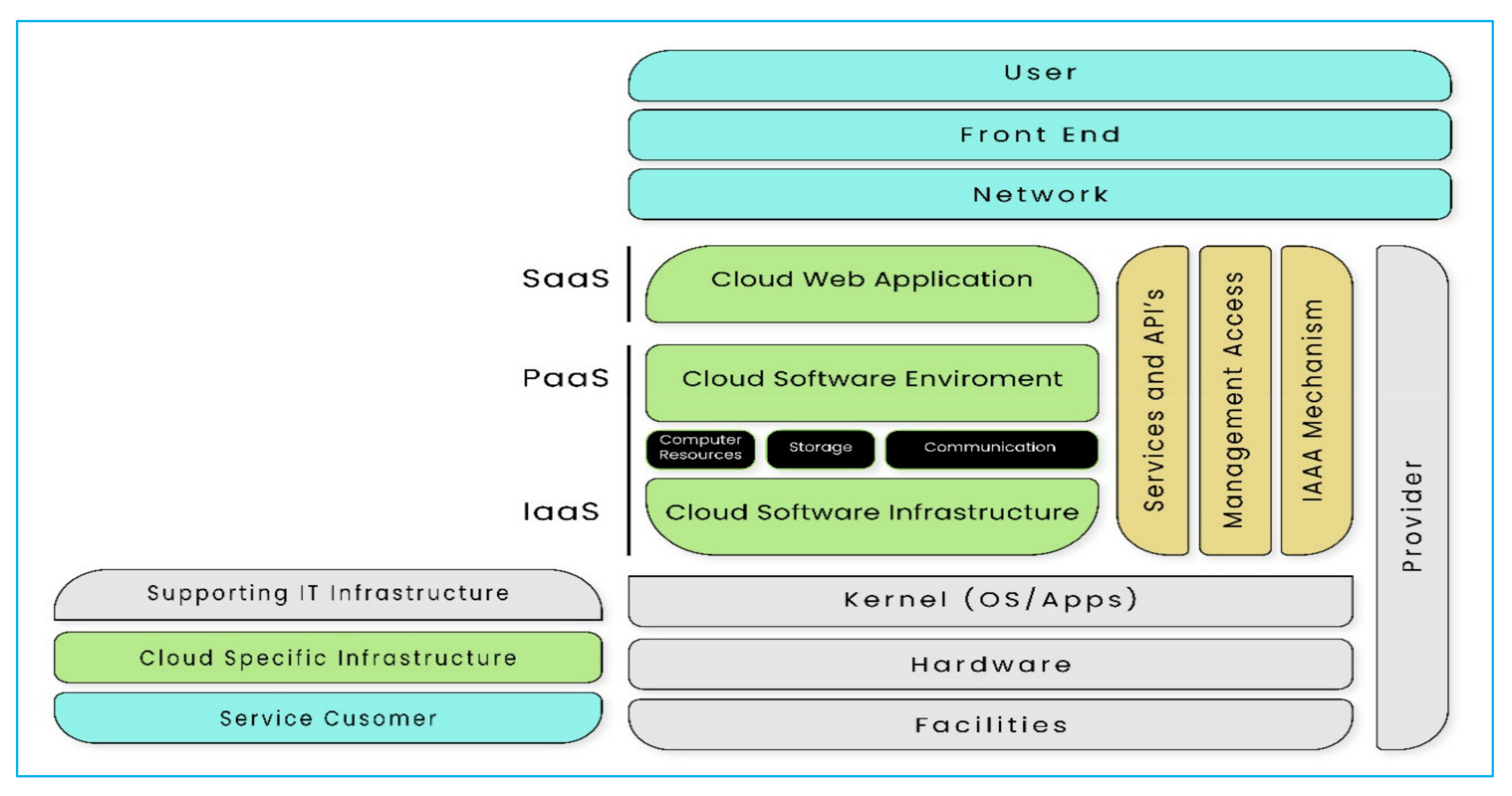
2. Problem Background
2.1. Cloud Data Centre Security Concerns and Threats
- Multitenancy (more for CSP compared to Client)
- Velocity of attack (more for CSP compared to Client)
- Information assurance (Client)
- Data privacy and ownership (Client)
2.1.1. Multitenancy
2.1.2. The “Velocity-of-Attack”
2.1.3. Information Assurance
2.1.4. Data Privacy and Ownership
- Single user Identification on Cloud
- Clients’ details as per request
- Ownership of client data
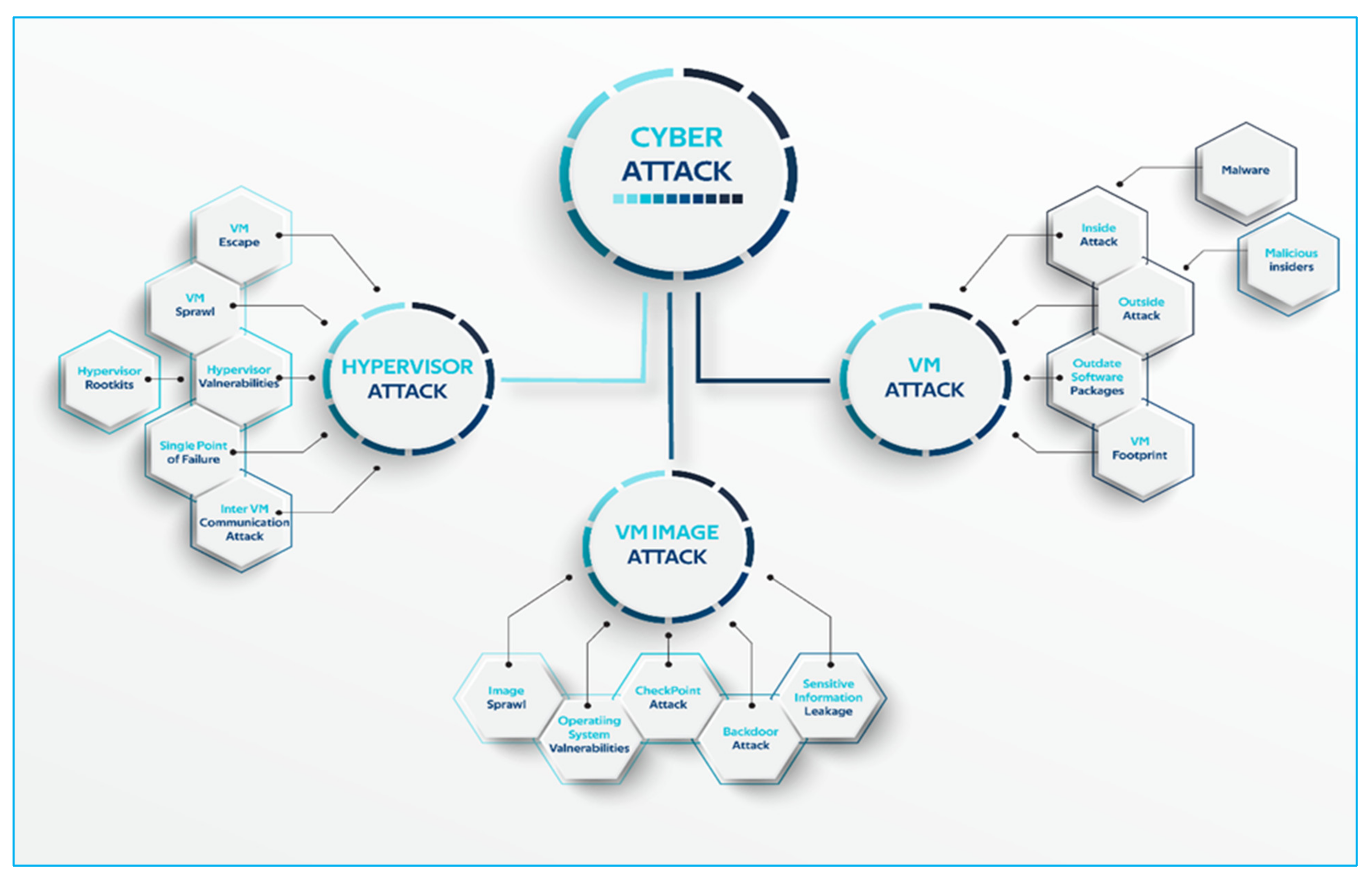
2.2. Virtualization-Specific Vulnerabilities, Security Concerns, and Threats
2.2.1. VM Theft or VM Stealing
2.2.2. VM Escape
2.2.3. VM Sprawl and VM Image Sprawl
2.2.4. VM Inside and Outside Attacks
2.2.5. VM Cross Side-Channel Attack
2.2.6. Outdated Software Packages in VMS
2.2.7. Hyperjacking
2.2.8. Data Leakage
2.2.9. Denial of Service (DoS)
3. Blockchain-Enabled Cloud Security Related Work
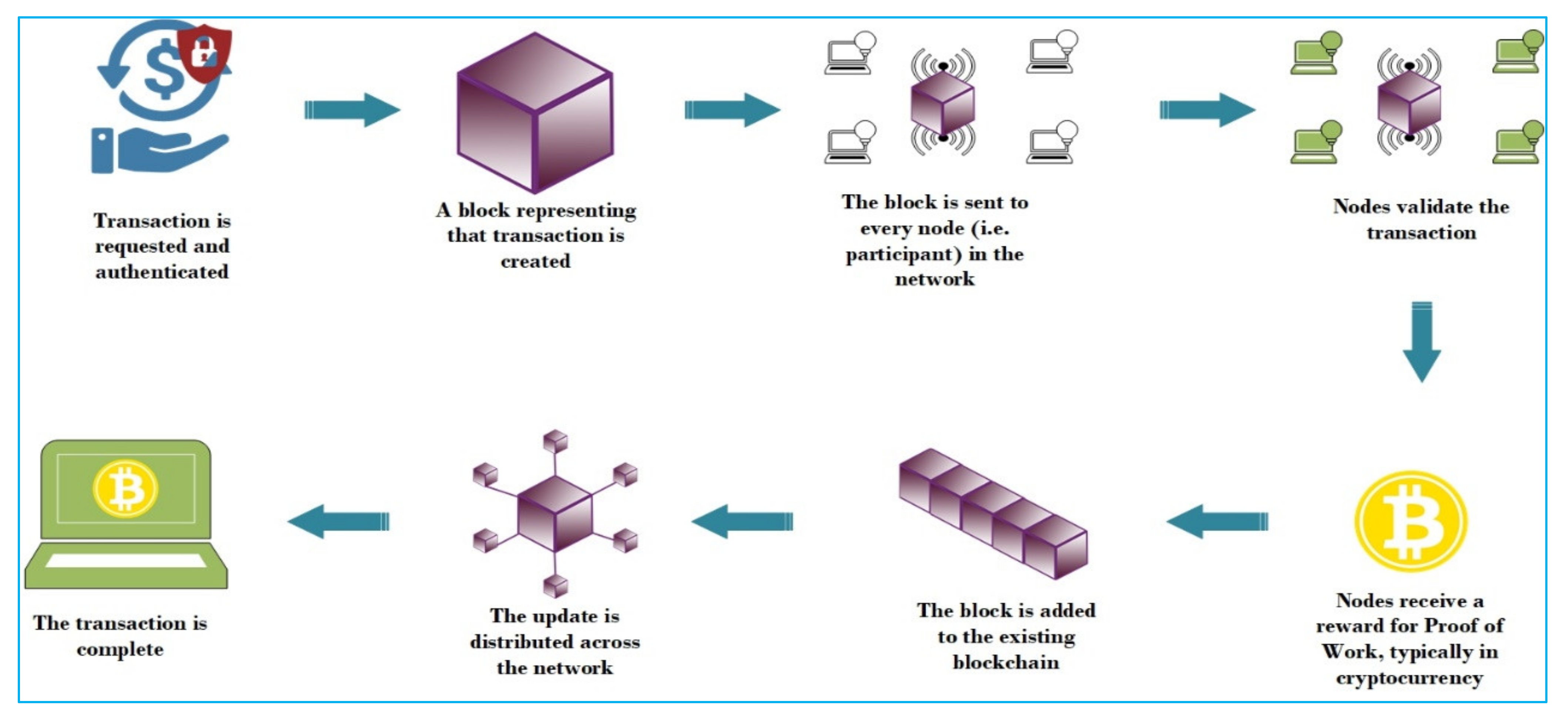
4. Blockchain as Technology Solution
- Public or Permissionless Blockchains: An open network system where the nodes and devices can freely access without permission. The ledger is shared and transparent for anyone to join in.
- Private or Permissioned Blockchains: A user or participating node has to be permitted by the blockchain network authority before he/she could get access to the network. It is restricted to a particular group of participants (better access control), making it more secure and transparent, increasing popularity.
4.1. Blockchain Key Characteristics
4.1.1. Immutability
4.1.2. Decentralization
4.1.3. Transparency
4.1.4. Security and Privacy
4.2. Blockchain Services
4.2.1. Distributed Shared Ledger
4.2.2. Consensus
4.2.3. Smart Contract (Chain Codes)
4.2.4. Cryptography
4.2.5. Blockchain Platform
Bitcoin
Ethereum Blockchain
Hyperledger Fabric Blockchain
5. Blockchain-Enabled Virtualized Cloud Security Solutions
5.1. Blockchain-Enabled Virtualized Task Scheduling
5.2. Blockchain-Enabled Anonymity of Data Algorithms
5.3. Blockchain-Enabled Data Integrity and Privacy
5.4. Blockchain-Enabled Authentication and Authorization
5.5. Blockchain-Enabled System Resilience and Fault Tolerance
6. Discussion and Open Challenges
6.1. Cloud Stakeholder Agreement
6.2. Attacks and Vulnerabilities
6.3. Lack of Data Standardization and Scope
6.4. Interoperability Challenge
6.5. Regulatory Consideration and Compliance
6.6. Costs of Operating Blockchain Technology
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Nzanywayingoma, F.; Yang, Y. Efficient resource management techniques in cloud computing environment: A review and discussion. Int. J. Comput. Appl. 2018, 41, 165–182. [Google Scholar] [CrossRef]
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. Integration of Cloud computing and Internet of Things: A survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Moura, J.; Hutchison, D. Review and analysis of networking challenges in cloud computing. J. Netw. Comput. Appl. 2016, 60, 113–129. [Google Scholar] [CrossRef] [Green Version]
- Alves, M.P.; Delicato, F.C.; Santos, I.L.; Pires, P.F. LW-CoEdge: A lightweight virtualization model and collaboration process for edge computing. World Wide Web 2020, 23, 1127–1175. [Google Scholar] [CrossRef]
- Suleiman, H.; Basir, O. Service Level Driven Job Scheduling in Multi-Tier Cloud Computing: A Biologically Inspired Approach. Comput. Sci. 2019, 9, 99–118. [Google Scholar] [CrossRef]
- Al-Mashhadi, S.; Anbar, M.; Jalal, R.A.; Al-Ani, A. Design of Cloud Computing Load Balance System Based on SDN Technology. Lect. Notes Electr. Eng. 2020, 603, 123–133. [Google Scholar] [CrossRef]
- Raju, C.J.; Babu, M.R.; Narayanamoorthy, M. Cost Effective Model for Using Different Cloud Services. In Emerging Research in Data Engineering Systems and Computer Communications; Springer: Singapore, 2020; pp. 313–319. [Google Scholar]
- Loubière, P.; Tomassetti, L. Towards Cloud Computing. In TORUS 1—Toward an Open Resource Using Services: Cloud Computing for Environmental Data; John Wiley & Sons: Hoboken, NJ, USA, 2020; pp. 179–189. [Google Scholar] [CrossRef]
- Tripathi, A.K.; Agrawal, S.; Gupta, R.D. Cloud enabled SDI architecture: A review. Earth Sci. Inform. 2020, 13, 211–231. [Google Scholar] [CrossRef]
- Ehwerhemuepha, L.; Gasperino, G.; Bischoff, N.; Taraman, S.; Chang, A.; Feaster, W. HealtheDataLab—A cloud computing solution for data science and advanced analytics in healthcare with application to predicting multi-centre pediatric readmissions. BMC Med. Inform. Decis. Mak. 2020, 20, 115. [Google Scholar] [CrossRef]
- Wagh, N.; Pawar, V.; Kharat, K. Educational Cloud Framework—A Literature Review on Finding Better Private Cloud Framework for Educational Hub. In Microservices in Big Data Analytics; Springer: Singapore, 2020; pp. 13–27. [Google Scholar] [CrossRef]
- Vähäkainu, P.; Lehto, M.; Kariluoto, A.; Ojalainen, A. Artificial Intelligence in Protecting Smart Building’s Cloud Service Infrastructure from Cyberattacks. In Cyber Defence in the Age of AI, Smart Societies and Augmented Humanity; Springer: Cham, Switzerland, 2020; pp. 289–315. [Google Scholar] [CrossRef]
- Chitturi, A.K.; Swarnalatha, P. Exploration of Various Cloud Security Challenges and Threats. In Soft Computing for Problem Solving; Springer: Singapore, 2020; pp. 891–899. [Google Scholar] [CrossRef]
- Mthunzi, S.N.; Benkhelifaa, E.; Bosakowskia, T.; Guegan, C.G.; Barhamgic, M. Cloud computing security taxonomy: From an atomistic to a holistic view. Future Gener. Comput. Syst. 2020, 107, 620–644. [Google Scholar] [CrossRef]
- Chadwick, D.W.; Fan, W.; Costantino, G.; De Lemos, R.; Di Cerbo, F.; Herwono, I.; Manea, M.; Mori, P.; Sajjad, A.; Wang, X.-S. A cloud-edge based data security architecture for sharing and analysing cyber threat information. Future Gener. Comput. Syst. 2020, 102, 710–722. [Google Scholar] [CrossRef]
- Uddin, M.; Memon, M.S.; Memon, I.; Ali, I.; Memon, J.; Abdelhaq, M.; Alsaqour, R. Hyperledger Fabric Blockchain: Secure and Efficient Solution for Electronic Health Records. CMC Comput. Mater. Continua. 2021, 68, 2377–2397. [Google Scholar] [CrossRef]
- Juma, M.; Monem, A.A.; Shaalan, K. Hybrid End-to-End VPN Security Approach for Smart IoT Objects. J. Netw. Comput. Appl. 2020, 158, 102598. [Google Scholar] [CrossRef]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G Support for Industrial Iot Applications—Challenges, Solutions, and Research Gaps. Sensors 2020, 20, 828. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Zahmatkesh, H.; Al-Turjman, F. Fog computing for sustainable smart cities in the IoT era: Caching techniques and enabling technologies—An overview. Sustain. Cities Soc. 2020, 59, 102139. [Google Scholar] [CrossRef]
- Shahid, F.; Khan, A.; Jeon, G. Post-quantum distributed ledger for internet of things. Comput. Electr. Eng. 2020, 83, 106581. [Google Scholar] [CrossRef]
- Hassan, H.E.-R.; Tahoun, M.; ElTaweel, G. A robust computational DRM framework for protecting multimedia contents using AES and ECC. Alex. Eng. J. 2020, 59, 1275–1286. [Google Scholar] [CrossRef]
- Chen, N.; Li, F.; White, G.; Clarke, S.; Yang, Y. A Decentralized Adaptation System for QoS Optimization. Fog Fogonomics 2020, 213–247. [Google Scholar] [CrossRef]
- Baker, T.; Asim, M.; MacDermott, Á.; Iqbal, F.; Kamoun, F.; Shah, B.; Alfandi, O.; Hammoudeh, M. A secure fog-based platform for SCADA-based IoT critical infrastructure. Softw. Pract. Exp. 2020, 50, 503–518. [Google Scholar] [CrossRef]
- Ahmed, M.; Jaidka, S.; Sarkar, N.I. Security in decentralised computing, IoT and industrial IoT. In Industrial IoT; Springer: Cham, Switzerland, 2020; pp. 191–211. [Google Scholar] [CrossRef]
- Firouzi, F.; Farahani, B. Architecting IoT Cloud. In Intelligent Internet of Things; Springer: Cham, Switzerland, 2020; pp. 173–241. [Google Scholar] [CrossRef]
- Chandel, S.; Ni, T.-Y.; Yang, G. Enterprise cloud: Its growth & security challenges in China. In Proceedings of the 2018 5th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2018 4th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Shanghai, China, 22–24 June 2018; pp. 144–152. [Google Scholar] [CrossRef]
- Kimani, K.; Oduol, V.; Langat, K. Cyber security challenges for IoT-based smart grid networks. Int. J. Crit. Infrastruct. Prot. 2019, 25, 36–49. [Google Scholar] [CrossRef]
- Singh, N.; Singh, A.K. Data privacy protection mechanisms in cloud. Data Sci. Eng. 2018, 3, 24–39. [Google Scholar] [CrossRef] [Green Version]
- Bartolini, C.; Santos, C.; Ullrich, C. Property and the cloud. Comput. Law Secur. Rev. 2018, 34, 358–390. [Google Scholar] [CrossRef]
- Baumann, A.; Peinado, M.; Hunt, G.C. Shielding applications from an untrusted cloud with Haven. In Proceedings of the 11th USENIX Symposium on Operating Systems Design and Implementation, OSDI 2014, Broomfield, CO, USA, 6–8 October 2014; pp. 267–283. [Google Scholar]
- Aljahdali, H.; Albatli, A.; Garraghan, P.; Townend, P.; Lau, L.; Xu, J. Multi-tenancy in cloud computing. In Proceedings of the 2014 IEEE 8th International Symposium on Service Oriented System Engineering, Oxford, UK, 7–11 April 2014; pp. 344–351. [Google Scholar] [CrossRef] [Green Version]
- Jayanetti, A.; Buyya, R. J-OPT: A Joint Host and Network Optimization Algorithm for Energy-Efficient Workflow Scheduling in Cloud Data Centres. In Proceedings of the 12th IEEE/ACM International Conference on Utility and Cloud Computing, Auckland, New Zealand, 2–5 December 2019; pp. 199–208. [Google Scholar] [CrossRef]
- Morabito, R.; Petrolo, R.; Loscrì, V.; Mitton, N. Reprint of: LEGIoT: A Lightweight Edge Gateway for the Internet of Things. Future Gener. Comput. Syst. 2019, 92, 1157–1171. [Google Scholar] [CrossRef] [Green Version]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Kadam, S.; Motwani, D. Blockchain based E-healthcare record system. In International Conference on Image Processing and Capsule Networks; Springer: Cham, Switzerland, 2020; pp. 366–380. [Google Scholar] [CrossRef]
- Tank, D.; Aggarwal, A.; Chaubey, N. Virtualization vulnerabilities, security issues, and solutions: A critical study and comparison. Int. J. Inf. Technol. 2019, 1–16. [Google Scholar] [CrossRef]
- Pandi, G.S.; Shah, S.; Wandra, K. Exploration of Vulnerabilities, Threats and Forensic Issues and its impact on the Distributed Environment of Cloud and its mitigation. Procedia Comput. Sci. 2020, 167, 163–173. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion detection systems in the Internet of things: A comprehensive investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Srinivasan, K.; Mubarakali, A.; Alqahtani, A.S.; Kumar, A.D. A survey on the impact of DDoS attacks in cloud computing: Prevention, detection and mitigation techniques. In Intelligent Communication Technologies and Virtual Mobile Networks; Springer: Cham, Switzerland, 2019; pp. 252–270. [Google Scholar] [CrossRef]
- Monge, M.A.S.; González, A.H.; Fernández, B.L.; Vidal, D.M.; García, G.R.; Vidal, J.M. Traffic-flow analysis for source-side DDoS recognition on 5G environments. J. Netw. Comput. Appl. 2019, 136, 114–131. [Google Scholar] [CrossRef]
- Van Der Werff, L.; Fox, G.; Masevic, I.; Emeakaroha, V.C.; Morrison, J.P.; Lynn, T. Building consumer trust in the cloud: An experimental analysis of the cloud trust label approach. J. Cloud Comput. 2019, 8, 6. [Google Scholar] [CrossRef]
- Castro, P.; Ishakian, V.; Muthusamy, V.; Slominski, A. The rise of serverless computing. Commun. ACM 2019, 62, 44–54. [Google Scholar] [CrossRef]
- Sierra-Arriaga, F.; Branco, R.; Lee, B. Security Issues and Challenges for Virtualization Technologies. ACM Comput. Surv. 2020, 53, 1–37. [Google Scholar] [CrossRef]
- Mavridis, I.; Karatza, H. Combining containers and virtual machines to enhance isolation and extend functionality on cloud computing. Future Gener. Comput. Syst. 2019, 94, 674–696. [Google Scholar] [CrossRef]
- Alwakeel, A.M.; Alnaim, A.K.; Fernandez, E.B. A survey of network function virtualization security. In Proceedings of the in SoutheastCon 2018, St. Petersburg, FL, USA, 19–22 April 2018; pp. 1–8. [Google Scholar]
- Tiburski, R.T.; Moratelli, C.R.; Johann, S.F.; Neves, M.V.; De Matos, E.; Amaral, L.A.; Hessel, F. Lightweight security architecture based on embedded virtualization and trust mechanisms for IoT edge devices. IEEE Commun. Mag. 2019, 57, 67–73. [Google Scholar] [CrossRef]
- Zhang, X.; Zheng, X.; Wang, Z.; Li, Q.; Fu, J.; Zhang, Y.; Shen, Y. Fast and Scalable VMM Live Upgrade in Large Cloud Infrastructure. In Proceedings of the Twenty-Fourth International Conference on Architectural Support for Programming Languages and Operating Systems, Providence, RI, USA, 13–17 April 2019; pp. 93–105. [Google Scholar] [CrossRef]
- Alhenaki, L.; Alwatban, A.; Alamri, B.; Alarifi, N. A Survey on the Security of Cloud Computing. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 19–21 March 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Win, S.S.; Thwin, M.M.S. Handling the Hypervisor Hijacking Attacks on Virtual Cloud Environment. In Advances in Biometrics; Springer: Cham, Switzerland, 2019; pp. 25–50. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Moon, D.; Park, J.H. A comprehensive study on APT attacks and countermeasures for future networks and communications: Challenges and solutions. J. Supercomput. 2019, 75, 4543–4574. [Google Scholar] [CrossRef]
- Abbasi, H.; Ezzati-Jivan, N.; Bellaiche, M.; Talhi, C.; Dagenais, M.R. Machine Learning-Based EDoS Attack Detection Technique Using Execution Trace Analysis. J. Hardw. Syst. Secur. 2019, 3, 164–176. [Google Scholar] [CrossRef]
- Singh, S.; Sanwar Hosen, A.S.M.; Yoon, B. Blockchain security attacks, challenges, and solutions for the future distributed iot network. IEEE Access 2021, 9, 13938–13959. [Google Scholar]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain Technology for Cloud Storage: A Systematic Literature Review. ACM Comput. Surv. 2020, 53, 1–32. [Google Scholar] [CrossRef]
- Waheed, N.; He, X.; Ikram, M.; Usman, M.; Hashmi, S.S. Security and privacy in IoT using machine learning and blockchain: Threats and countermeasures. ACM Computing Surveys (CSUR) 2020, 53, 1–37. [Google Scholar] [CrossRef]
- Alcaraz, C.; Rubio, J.E.; Lopez, J. Blockchain-assisted access for federated Smart Grid domains: Coupling and features. J. Parallel Distrib. Comput. 2020, 144, 124–135. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for 5G and beyond networks: A state of the art survey. J. Netw. Comput. Appl. 2020, 166, 102693. [Google Scholar] [CrossRef]
- Tavana, M.; Hajipour, V.; Oveisi, S. IoT-based enterprise resource planning: Challenges, open issues, applications, architecture, and future research directions. Internet Things 2020, 11, 100262. [Google Scholar] [CrossRef]
- Wang, H.; Ma, S.; Dai, H.-N.; Imran, M.; Wang, T. Blockchain-based data privacy management with Nudge theory in open banking. Future Gener. Comput. Syst. 2020, 110, 812–823. [Google Scholar] [CrossRef]
- Ruqia, B.; Javaid, N.; Husain, A.; Hassan, N.M.; Hassan, H.G.; Memon, Y. Influential reasonable robust virtual machine placement for efficient utilization and saving energy. In International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing; Springer: Cham, Switzerland, 2019; pp. 549–561. [Google Scholar]
- Zhang, Y.; Xu, C.; Lin, X.; Shen, X.S. Blockchain-Based Public Integrity Verification for Cloud Storage against Procrastinating Auditors. IEEE Trans. Cloud Comput. 2019, 1. [Google Scholar] [CrossRef] [Green Version]
- Yang, H.; Yuan, J.; Yao, H.; Yao, Q.; Yu, A.; Zhang, J. Blockchain-Based Hierarchical Trust Networking for JointCloud. IEEE Internet Things J. 2019, 7, 1667–1677. [Google Scholar] [CrossRef]
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of blockchain from security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17. [Google Scholar] [CrossRef]
- Aileni, R.M.; Suciu, G. IoMT: A blockchain perspective. In Decentralised Internet of Things; Springer: Cham, Switzerland, 2020; pp. 199–215. [Google Scholar]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and AI amalgamation for energy cloud management: Challenges, solutions, and future directions. J. Parallel Distrib. Comput. 2020, 143, 148–166. [Google Scholar] [CrossRef]
- Hu, J.-W.; Yeh, L.-Y.; Liao, S.-W.; Yang, C.-S. Autonomous and malware-proof blockchain-based firmware update platform with efficient batch verification for Internet of Things devices. Comput. Secur. 2019, 86, 238–252. [Google Scholar] [CrossRef]
- Delgado-Mohatar, O.; Felis-Rota, M.; Fernández-Herraiz, C. The Bitcoin mining breakdown: Is mining still profitable? Econ. Lett. 2019, 184, 108492. [Google Scholar] [CrossRef]
- Cao, B.; Zhang, Z.; Feng, D.; Zhang, S.; Zhang, L.; Peng, M.; Li, Y. Performance analysis and comparison of PoW, PoS and DAG based blockchains. Digit. Commun. Netw. 2020, 6, 480–485. [Google Scholar] [CrossRef]
- Wang, S. Performance Evaluation of Hyperledger Fabric with Malicious Behavior. In International Conference on Blockchain; Springer: Cham, Switzerland, 2019; pp. 211–219. [Google Scholar] [CrossRef]
- Bekhouche, L.; Saou, R.; Guerroudj, C.; Kouzou, A.; Zaim, M.E.-H. Electromagnetic torque ripple minimization of slotted doubly-salient-permanent-magnet generator for wind turbine applications. Prog. Electromagn. Res. M 2019, 83, 181–190. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.Y. A decentralized token economy: How blockchain and cryptocurrency can revolutionize business. Bus. Horiz. 2019, 62, 773–784. [Google Scholar] [CrossRef]
- Khan, S.; Amin, A.; Hossain, H.; Noor, N.; Sadik, W. A pragmatical study on blockchain empowered decentralized application development platform. In Proceedings of the International Conference on Computing Advancements, New York, NY, USA, 10–12 January 2020. [Google Scholar] [CrossRef]
- Falazi, G.; Khinchi, V.; Breitenbücher, U.; Leymann, F. Transactional properties of permissioned blockchains. SICS Softw. Intensive Cyber-Phys. Syst. 2019, 35, 49–61. [Google Scholar] [CrossRef] [Green Version]
- Ismail, L.; Hameed, H.; Alshamsi, M.; Alhammadi, M.; Aldhanhani, N. Towards a blockchain deployment at UAE University: Performance evaluation and blockchain taxonomy. In Proceedings of the 2019 International Conference on Blockchain Technology, Honolulu, HI, USA, 15–18 March 2019; pp. 30–38. [Google Scholar] [CrossRef]
- Sarfraz, U.; Alam, M.; Zeadally, S.; Khan, A. Privacy aware IOTA ledger: Decentralized mixing and unlinkable IOTA transactions. Comput. Netw. 2019, 148, 361–372. [Google Scholar] [CrossRef]
- Oswald, E.; Fischlin, M. (Eds.) Advances in Cryptology–EUROCRYPT 2015. In Proceedings of the 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Volume 9057. [Google Scholar]
- Lone, A.H.; Mir, R.N. Forensic-chain: Blockchain based digital forensics chain of custody with PoC in Hyperledger Composer. Digit. Investig. 2019, 28, 44–55. [Google Scholar] [CrossRef]
- Khan, M.Y.; Zuhairi, M.F.; Ali, T.; Alghamdi, T.; Marmolejo-Saucedo, J. An extended access control model for permissioned blockchain frameworks. Wirel. Netw. 2019, 26, 4943–4954. [Google Scholar] [CrossRef]
- Berdik, D.; Otoum, S.; Schmidt, N.; Porter, D.; Jararweh, Y. A survey on blockchain for information systems management and security. Inf. Process. Manag. 2021, 58, 102397. [Google Scholar] [CrossRef]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Moin, S.; Karim, A.; Safdar, Z.; Safdar, K.; Ahmed, E.; Imran, M. Securing IoTs in distributed blockchain: Analysis, requirements and open issues. Future Gener. Comput. Syst. 2019, 100, 325–343. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R. P4-to-blockchain: A secure blockchain-enabled packet parser for software defined networking. Comput. Secur. 2020, 88, 101629. [Google Scholar] [CrossRef]
- Dai, H.-N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Bertin, E.; Hussein, D.; Sengul, C.; Frey, V. Access control in the Internet of Things: A survey of existing approaches and open research questions. Ann. Telecommun. 2019, 74, 375–388. [Google Scholar] [CrossRef] [Green Version]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Blockchain Threat Report-Mcafee.com. Available online: www.mcafee.com/enterprise/enus/assets/reports/rp-blockchain-security-risks.pdf (accessed on 15 April 2021).
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G.; Rosenbloom, S.T. FHIRChain: Applying Blockchain to Securely and Scalably Share Clinical Data. Comput. Struct. Biotechnol. J. 2018, 16, 267–278. [Google Scholar] [CrossRef]
- Uddin, M. Blockchain Medledger: Hyperledger fabric enabled drug traceability system for counterfeit drugs in pharmaceutical industry. Int. J. Pharm. 2021, 597, 120235. [Google Scholar] [CrossRef]

| Platform | Consensus Algorithms | Operation Mode | Programming Languages | Source |
|---|---|---|---|---|
| Bitcoin | PoW | Public | Ivy, RSK, BitML | [66] |
| Ethereum | PoW, PoS | Public and permissioned | Solidity, Flint, SCILLA | [67] |
| Hyperledger | PBFT | Permissioned | Go, Node.js, Java | [68] |
| Ripple | PoW | Permissioned | C++ | [69] |
| R3 Corda | PoW, PoS | Permissioned | Kotlin, Java | [70] |
| Openchain | Partionned | Consensus | Java | [71] |
| BigChainDB | BFT | Public and permissioned | C++, Java | [72] |
| Chain core | Federated consensus | Permissioned | Java | [73] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Uddin, M.; Khalique, A.; Jumani, A.K.; Ullah, S.S.; Hussain, S. Next-Generation Blockchain-Enabled Virtualized Cloud Security Solutions: Review and Open Challenges. Electronics 2021, 10, 2493. https://doi.org/10.3390/electronics10202493
Uddin M, Khalique A, Jumani AK, Ullah SS, Hussain S. Next-Generation Blockchain-Enabled Virtualized Cloud Security Solutions: Review and Open Challenges. Electronics. 2021; 10(20):2493. https://doi.org/10.3390/electronics10202493
Chicago/Turabian StyleUddin, Mueen, Anjum Khalique, Awais Khan Jumani, Syed Sajid Ullah, and Saddam Hussain. 2021. "Next-Generation Blockchain-Enabled Virtualized Cloud Security Solutions: Review and Open Challenges" Electronics 10, no. 20: 2493. https://doi.org/10.3390/electronics10202493
APA StyleUddin, M., Khalique, A., Jumani, A. K., Ullah, S. S., & Hussain, S. (2021). Next-Generation Blockchain-Enabled Virtualized Cloud Security Solutions: Review and Open Challenges. Electronics, 10(20), 2493. https://doi.org/10.3390/electronics10202493









