Traffic Classification for Network Slicing in Mobile Networks
Abstract
:1. Introduction
- On the one hand, a mechanism based on a traffic classifier is used to identify the class of individual data flows. This allows for subsequent slicing to be dynamic, adaptive and transparent to end users by being able to transmit all types of traffic.
- On the other hand, the proposed approaches assign, in real time, the data flow to one of the available slices associated with a 5G QoS identifier (5QI) value from [10], according to specific policies. Here, the data flow classes considered are the main ones present in the industrial and automotive sectors, including control messaging, video streaming, IoT data, and generic web data.
2. Background and Related Work
2.1. Network Slicing
2.2. Traffic Types
- Video traffic is the streaming of video data between endpoints. This type of traffic is loss-tolerant but sensitive to delays in real-time streaming.
- Audio/voice traffic is the transmission of audio data between endpoints. Similar to video traffic, this type of traffic is loss-tolerant but sensitive to delays in real-time streaming.
- IoT traffic is the streaming of cyber-physical data and information about the environment collected by hundreds or thousands of devices and transmitted periodically. This kind of traffic is not very loss-tolerant. However, ensuring a high number of connections while guaranteeing bandwidth and latency is very important.
- WebData traffic is the amount of data sent and received by visitors to a website. The typical size of the data is variable, as it mainly depends on the type of website from which the data originates. By contrast, the main focus for this traffic is on bandwidth.
- Data transfer traffic refers to the transmission of files of varying sizes between endpoints. For this type of traffic, the most important requirement is the reliability of the content upon reception, with longer delays being more tolerable than for other types of traffic.
- Control data traffic contains network control messages. These messages are usually produced in low volumes with very low packet sizes but have strong delivery requirements, for example, a very long delay or the network control frames experiencing a loss can lead to loss of network functions.
- Best-effort traffic comprises traffic that has no specific requirements to be fulfilled.
2.3. Traffic Classification
- Statistics-based classification: this uses statistical information related to the traffic without analyzing the packet payload. Algorithms belonging to this group have a high computational overhead as an analysis of heuristics for individual packets is required.
- Correlation-based classification: this uses the correlation of flows combined with the statistical information of the traffic. As in the case of the statistics-based classification group, these also have a high computational overhead.
- Behavior-based classification: this uses host interaction and connection data to classify traffic. Despite the good results in terms of accuracy and the lightweight processing demand, the traffic classification result does not provide much detail.
- Payload-based classification: this uses the content of the payload or some specific fields of the payload to perform traffic classification. Therefore, the accuracy obtained by these algorithms is the highest among the groups mentioned in this paper. This group can be further divided into deep packet inspection (DPI) algorithms and stochastic packet inspection (SPI) algorithms. The difference between them is the way in which they inspect the content of the packet. While DPI algorithms are generally not able to classify encrypted packets, SPI algorithms can deal with encrypted traffic. Both have high computational overheads.
- Port-based classification: this uses only the port to classify the traffic. This method is the least accurate among all of the above groups since many traffic sources use dynamic ports or two traffic sources may use the same port to transmit data with different protocols. Therefore, in these cases, the results of the classification may not be correct.
3. Network Slicing Solutions
- 1.
- The context is required to find out which slices are in the 5GC database for that specific UE. These slices, as shown in Figure 2, are identified with their corresponding SST and SD using the NG Application Protocol (NGAP) Initial Context Setup Request message.
- 2.
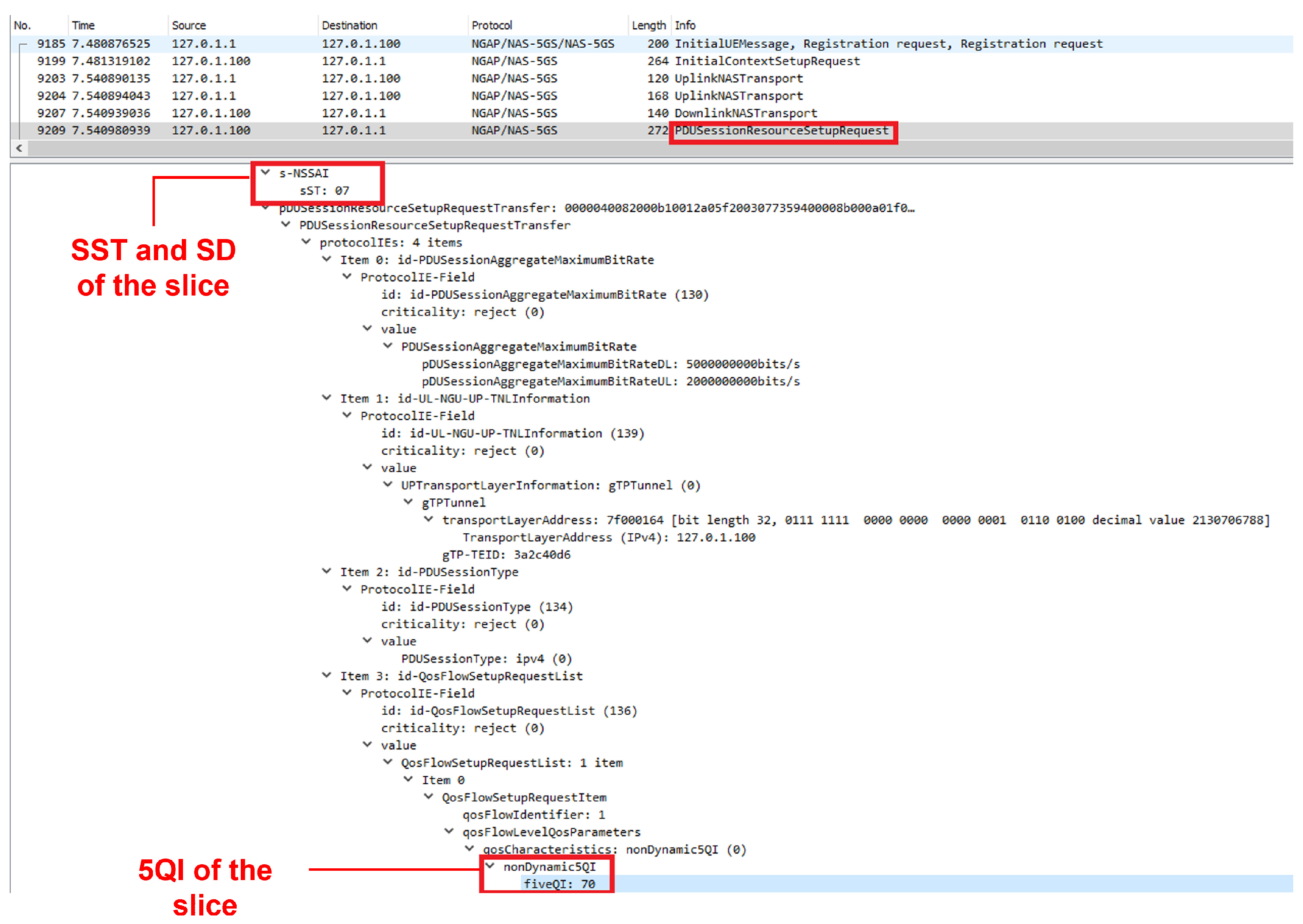
- The connection to a slice is established, as in Figure 3—in this example, a slice with an SST 7 and an associated 5QI of 70—using a message PDU Session Resource Setup Request, where the UE receives the 5QI parameter of that slice. Therefore, to compile all of the 5QI parameters of the available slices, it would be necessary to previously connect to each of them.

4. Proposed Approaches for Network Slicing
4.1. Target Scenario
4.2. Radio Slicing Mechanism
- 1.
- The UE receives all types of traffic and forwards them to the Internet through the main interface.
- 2.
- The classifier runs on the main interface and classifies the different traffic flows.
- 3.
- The slicing policy selects the best slice based on the previous classification. Accordingly, the UE sends the traffic through the chosen slice.
4.2.1. Approach 1: Dynamic Slice Selection
| Algorithm 1: Algorithm for dynamic slice selection. |
|
4.2.2. Approach 2: Dynamic Traffic Redirection
| Algorithm 2: Algorithm for dynamic traffic redirection. |
|
5. Performance Evaluation
5.1. Experimental Setup and Evaluation Metrics
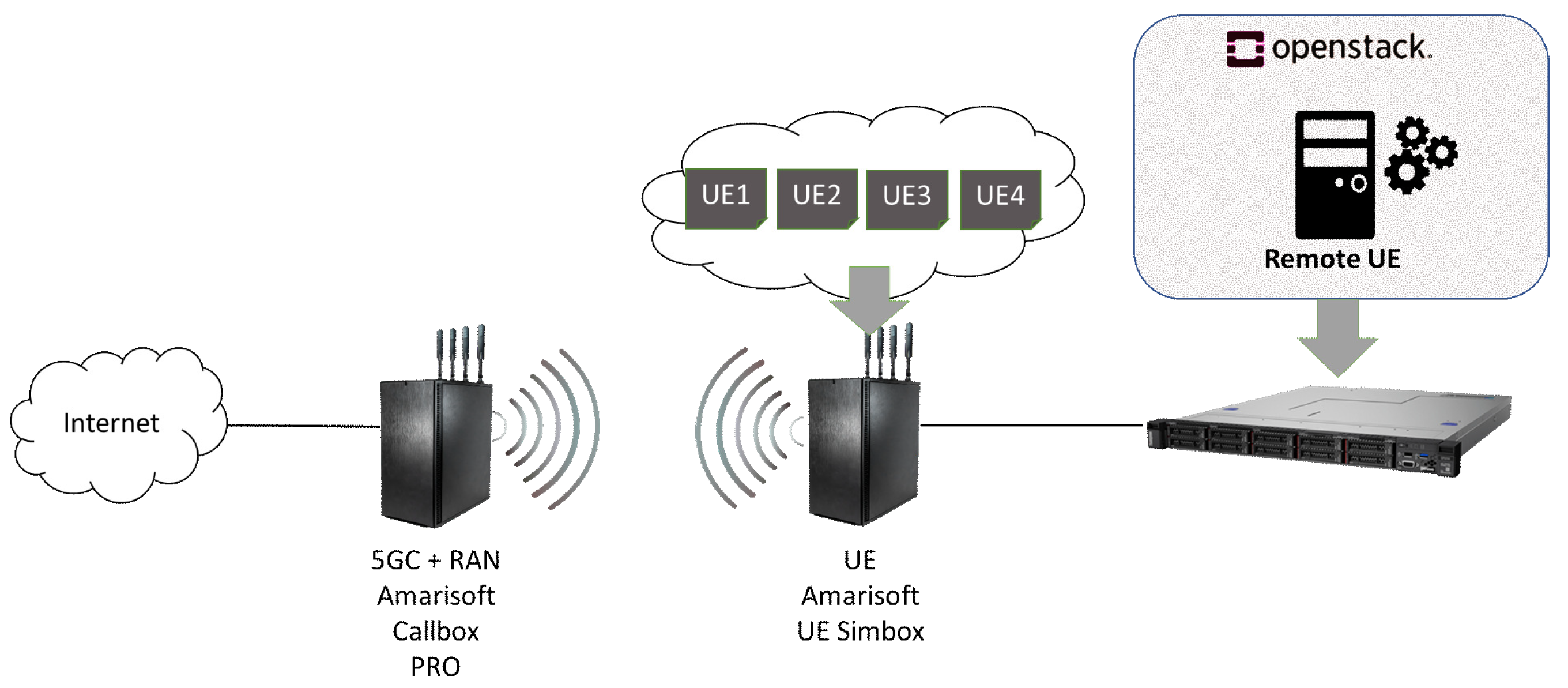
- An Amarisoft Callbox Pro device in order to deploy the Core and RAN segments of the 5G SA network;
- An Amarisoft UE Simbox unit, which allows for the deployment of multiple simultaneous 5G UEs in the same hardware;
- A virtual instance, which remotely manages the UEs offered by Amarisoft acting as a traffic injector in the 5G network and the various algorithms that perform the selection of the slice or the dynamic traffic redirection through the corresponding slice. In our setup, the virtual instance was hosted on an OpenStack server.
- Bandwidth, which allows for the level of saturation suffered by each slice to be known;
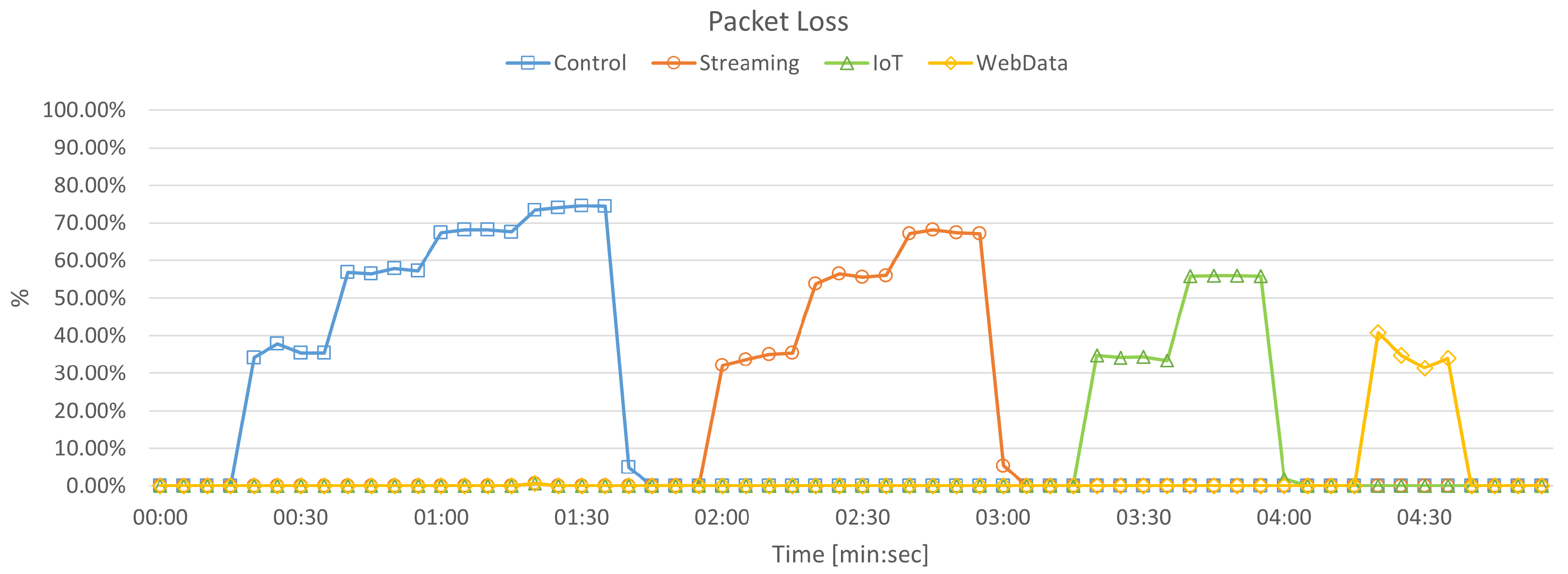
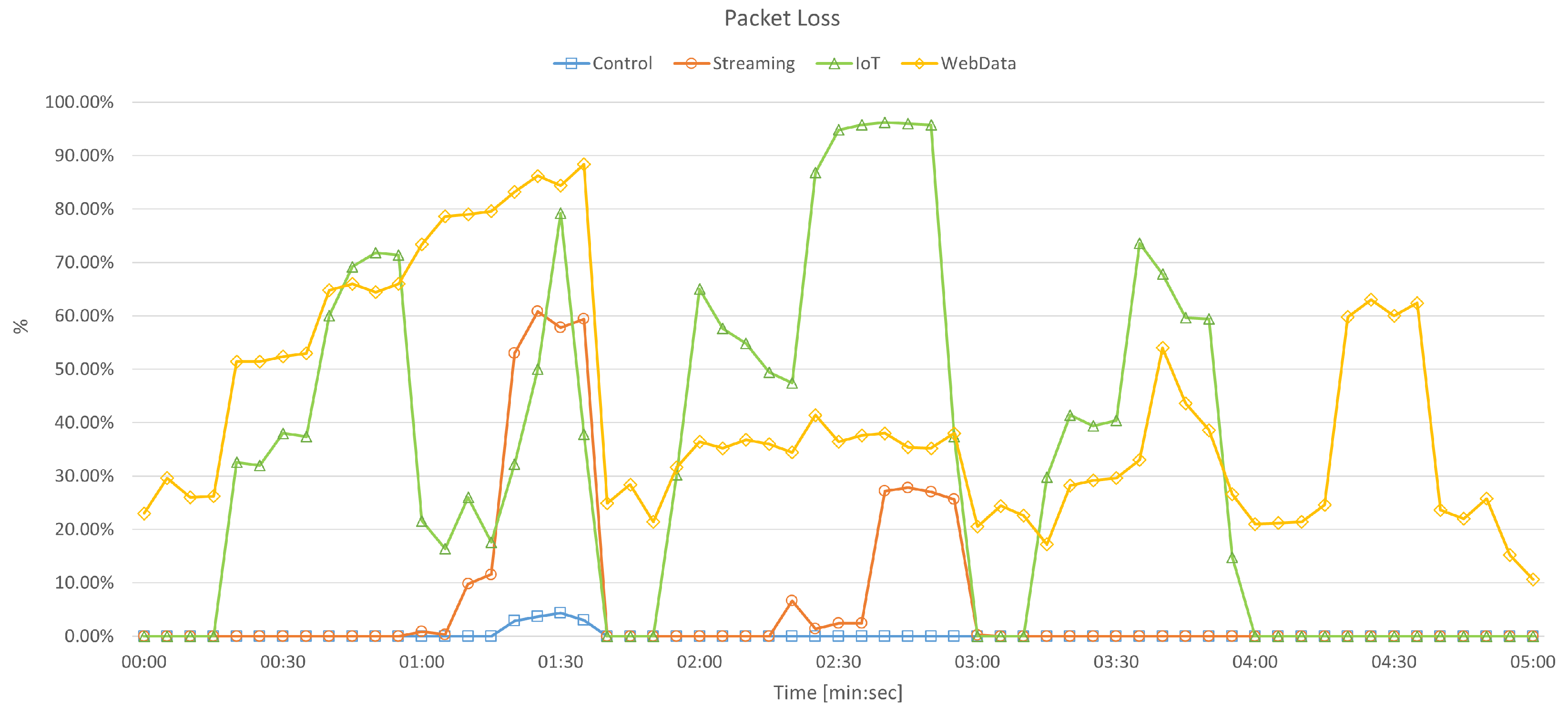
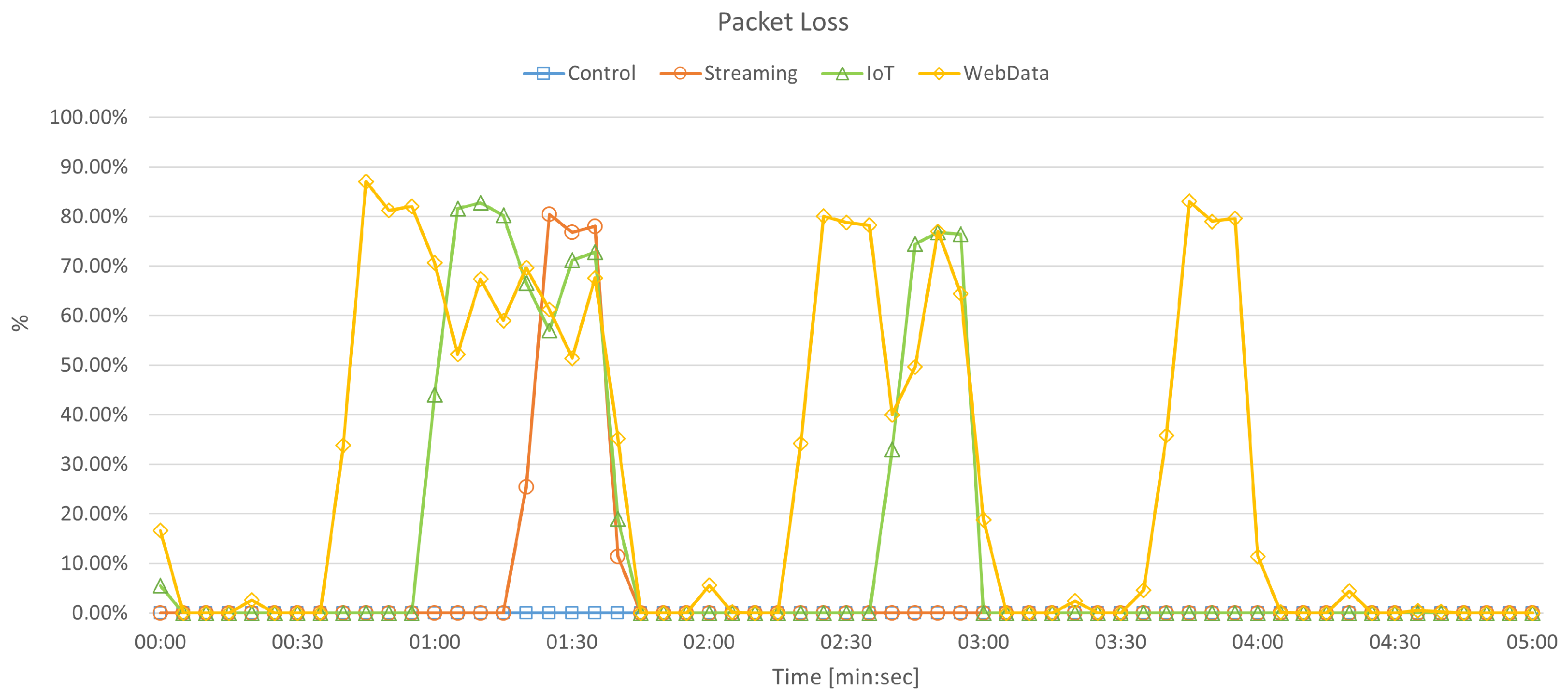
- Percentage of packets lost, which provides a measure of the reliability, complementing the bandwidth metric;
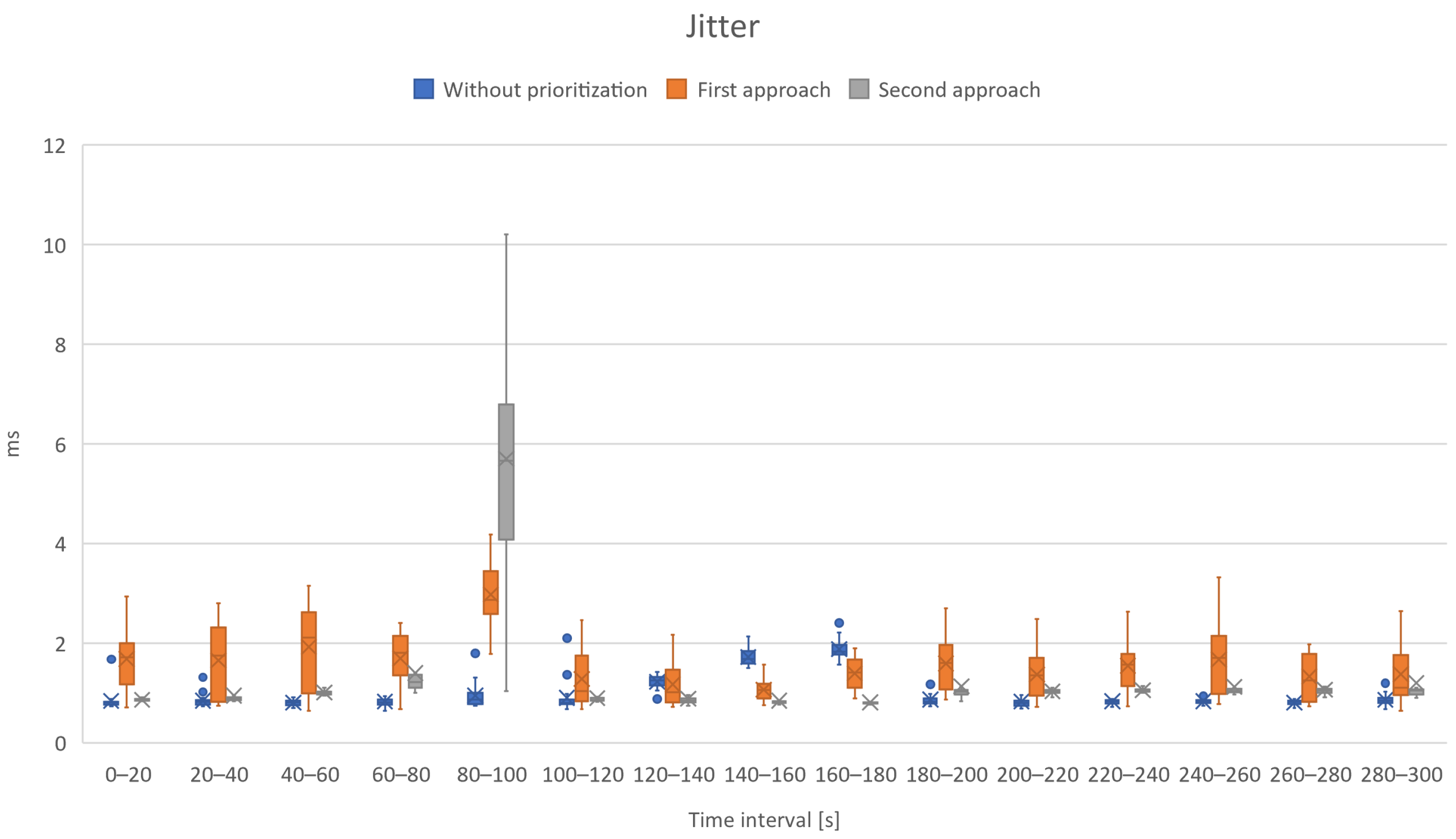
- Jitter, which allows the level of stability of the different scenarios to be known and for which the higher its value, the greater the time variations in packet reception.
- A scenario in which there is no network slicing, as an initial reference scenario that outlines a baseline performance and behavior;
- A scenario where each UE is associated with a single slice, representing the scenario of the first approach;
- A scenario where each UE is connected to all available slices, representing the scenario of the second approach.
5.2. Experimental Results
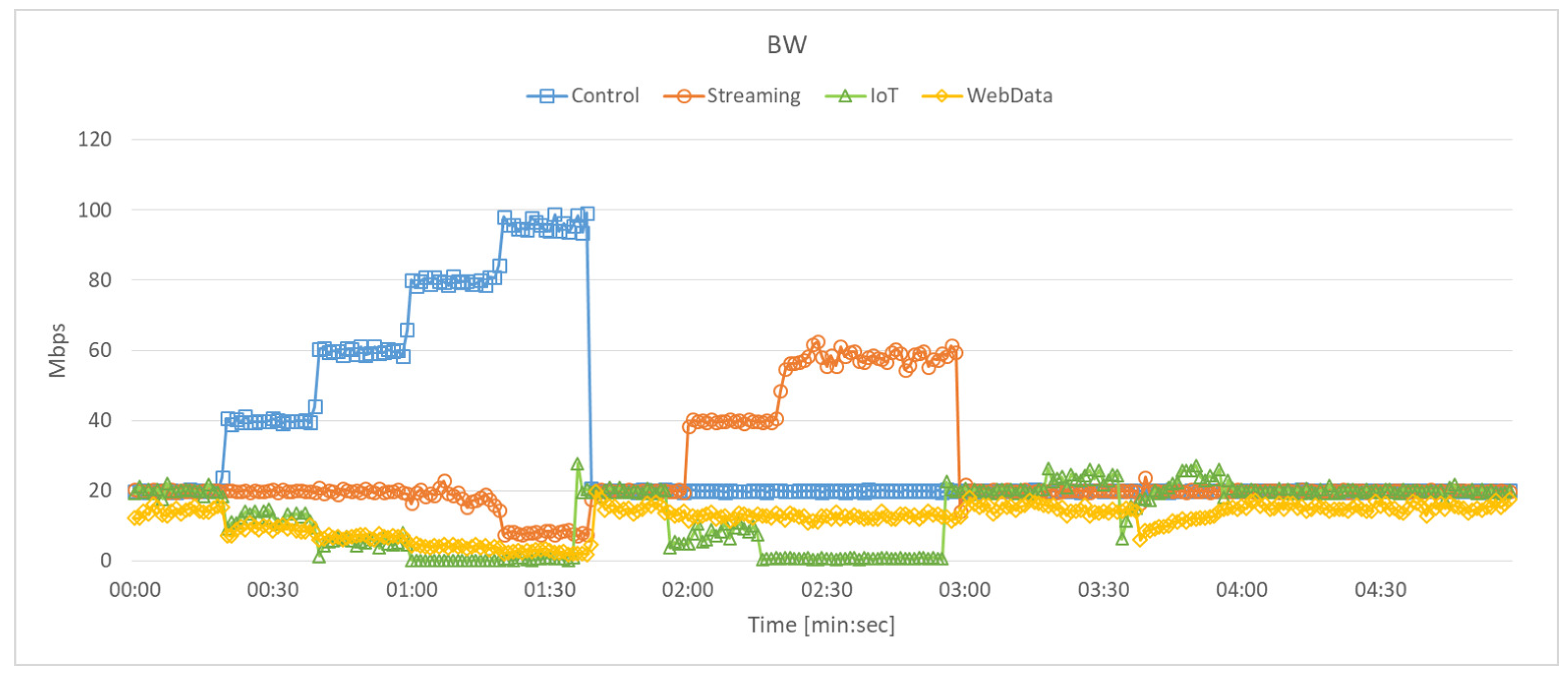
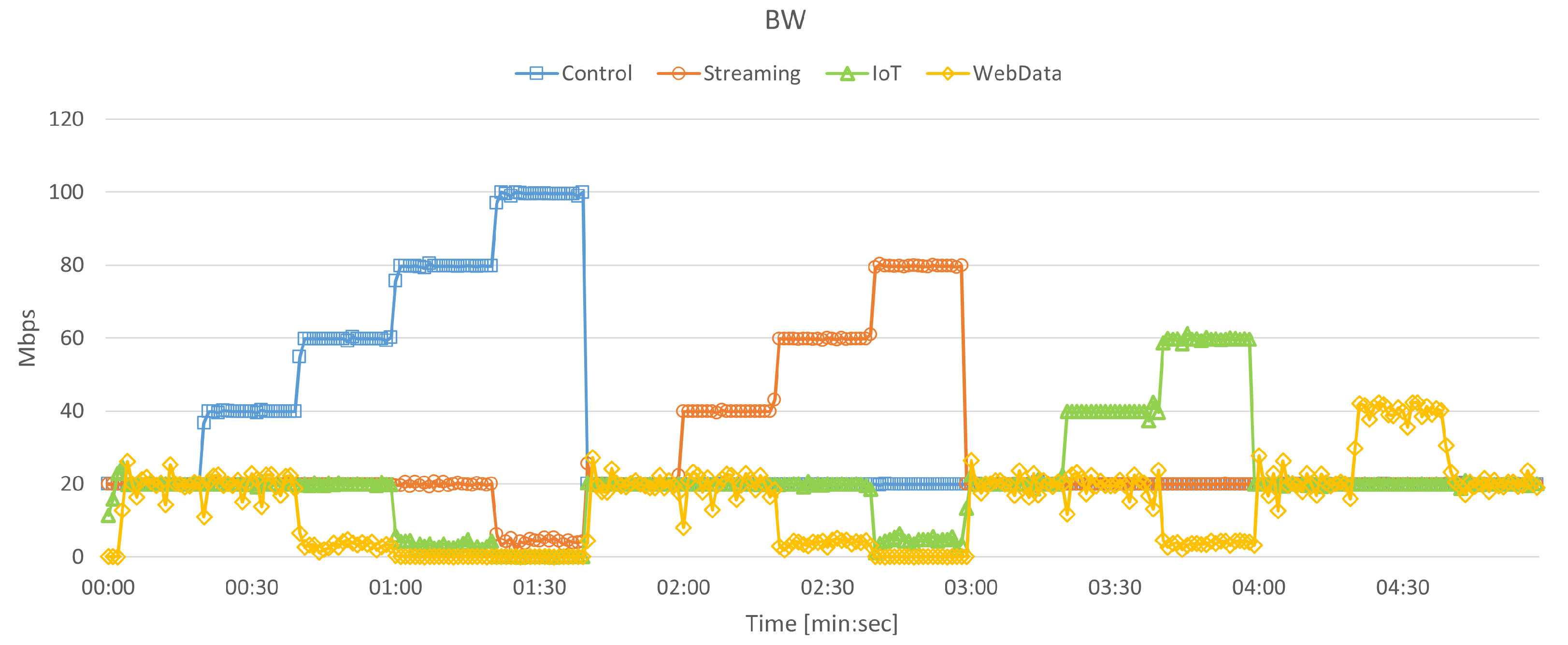
5.2.1. Bandwidth
5.2.2. Packet Loss
5.2.3. Jitter
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| 5GC | 5G Core |
| 5GPPP | 5G Infrastructure Public Private Partnership |
| 5QI | 5G QoS identifier |
| DL | Downlink |
| DPI | Deep packet inspection |
| eMBB | Enhanced mobile broadband |
| gNB | gNodeB |
| HMTC | High-performance machine-type communications |
| HTTP | Hypertext Transfer Protocol |
| ICMP | Internet Control Message Protocol |
| IoT | Internet of Things |
| IIoT | Industrial Internet of Things |
| KPI | Key performance indicators |
| MAC | Media access control |
| MEC | Multi-access edge computing |
| MIoT | Massive IoT |
| mMTC | Massive machine-type communications |
| MQTT | Message Queue Telemetry Transport |
| NGAP | NG Application Protocol |
| NGMN | Next Generation Mobile Network |
| NFV | Network function virtualization |
| OAI | OpenAirInterface |
| OSI | Open systems interconnection |
| PDU | Protocol data unit |
| PRB | Physical resource block |
| QoS | Quality of service |
| RAN | Radio access network |
| RTP | Real Time Protocol |
| SA | Standalone |
| SD | Slice differentiator |
| SDN | Software-defined network |
| SPI | Stochastic packet inspection |
| SSL | Secure sockets layer |
| SST | Slice/service type |
| S-NSSAI | Single Network Slice Selection Assistance Information |
| TCU | Telematic control unit |
| UDP | User Datagram Protocol |
| UE | User equipment |
| UL | Uplink |
| URLLC | Ultra-reliable low-latency communications |
| V2X | Vehicle to everything |
| VNF | Virtualized network functions |
References
- Shu, Z.; Taleb, T. A novel QoS framework for network slicing in 5G and beyond networks based on SDN and NFV. IEEE Netw. 2020, 34, 256–263. [Google Scholar] [CrossRef]
- Sohaib, R.M.; Onireti, O.; Sambo, Y.; Imran, M.A. Network Slicing for Beyond 5G Systems: An Overview of the Smart Port Use Case. Electronics 2021, 10, 1090. [Google Scholar] [CrossRef]
- Cisco, U. Cisco Annual Internet Report (2018–2023) White Paper. 2020. Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 15 January 2022).
- 5GPPP: The 5G Infrastructure Public Private Partnership. Available online: https://5g-ppp.eu/ (accessed on 7 January 2022).
- 5G-ACIA: 5G Alliance for Connected Industries and Automation. Available online: https://5g-acia.org/ (accessed on 7 January 2022).
- 5G-AA: 5G Automotive Association. Available online: https://5gaa.org/ (accessed on 7 January 2022).
- Siddiqi, M.A.; Yu, H.; Joung, J. 5G ultra-reliable low-latency communication implementation challenges and operational issues with IoT devices. Electronics 2019, 8, 981. [Google Scholar] [CrossRef] [Green Version]
- Rinaldi, F.; Raschella, A.; Pizzi, S. 5G NR system design: A concise survey of key features and capabilities. Wirel. Netw. 2021, 27, 5173–5188. [Google Scholar] [CrossRef]
- Teng, Y.; Yan, M.; Liu, D.; Han, Z.; Song, M. Distributed learning solution for uplink traffic control in energy harvesting massive machine-type communications. IEEE Wirel. Commun. Lett. 2019, 9, 485–489. [Google Scholar] [CrossRef]
- 3GPP. System Architecture for the 5G System (5GS). TS 23.501 V17.2.0. September 2021. Available online: https://www.3gpp.org/ftp/Specs/archive/23_series/23.501/23501-h20.zip (accessed on 22 December 2021).
- NGMN Alliance. 5G White Paper. In Next Generation Mobile Networks, White Paper; NGMN Alliance: Frankfurt am Main, Germany, 2015; Volume 1, Available online: https://ngmn.org/wp-content/uploads/NGMN_5G_White_Paper_V1_0.pdf (accessed on 20 January 2022).
- Afolabi, I.; Taleb, T.; Samdanis, K.; Ksentini, A.; Flinck, H. Network slicing and softwarization: A survey on principles, enabling technologies, and solutions. IEEE Commun. Surv. Tutor. 2018, 20, 2429–2453. [Google Scholar] [CrossRef]
- Barakabitze, A.A.; Ahmad, A.; Mijumbi, R.; Hines, A. 5G network slicing using SDN and NFV: A survey of taxonomy, architectures and future challenges. Comput. Netw. 2020, 167, 106984. [Google Scholar] [CrossRef]
- Afolabi, I.; Taleb, T.; Frangoudis, P.A.; Bagaa, M.; Ksentini, A. Network slicing-based customization of 5G mobile services. IEEE Netw. 2019, 33, 134–141. [Google Scholar] [CrossRef] [Green Version]
- Granelli, F. Chapter 3-Network slicing. In Computing in Communication Networks; Fitzek, F.H., Granelli, F., Seeling, P., Eds.; Academic Press: Cambridge, MA, USA, 2020; pp. 63–76. [Google Scholar] [CrossRef]
- Elayoubi, S.E.; Jemaa, S.B.; Altman, Z.; Galindo-Serrano, A. 5G RAN slicing for verticals: Enablers and challenges. IEEE Commun. Mag. 2019, 57, 28–34. [Google Scholar] [CrossRef] [Green Version]
- 5G-NORMA—5G Novel Radio Multiservice Adaptive Network Architecture. Available online: https://www.it.uc3m.es/wnl/5gnorma/ (accessed on 7 January 2022).
- SLICENET: End-to-End Cognitive Network Slicing and Slice Management Framework in Virtualised Multi-Domain, Multi-Tenant 5G Networks. Available online: https://slicenet.eu/ (accessed on 7 January 2022).
- 5Gtango: 5G Development and Validation Platform for Global Industry—Specific Network Services and Apps. Available online: https://www.5gtango.eu/ (accessed on 7 January 2022).
- Crippa, M.R.; Arnold, P.; Friderikos, V.; Gajic, B.; Guerrero, C.; Holland, O.; Pavon, I.L.; Sciancalepore, V.; Von Hugo, D.; Wong, S.; et al. Resource Sharing for a 5G Multi-tenant and Multi-service Architecture. In Proceedings of the 23th European Wireless Conference 2017, Dresden, Germany, 17–19 May 2017; pp. 1–6. [Google Scholar]
- Gavras, A.; Weiss, M.B.; Wang, Q.; Calero, J.M.A. SliceNet: E2E cognitive network slicing and slice management in 5G networks. In Proceedings of the European Conference on Networks and Communications 2018, Ljubljana, Slovenia, 18–21 June 2018. [Google Scholar]
- Martínez, R.; Vilalta, R.; Casellas, R.; Muñoz, R.; Fei, L.; Tang, P.; López, V. Network slicing resource allocation and monitoring over multiple clouds and networks. In Optical Fiber Communication Conference; Optical Society of America: San Diego, CA, USA, 2018; p. Tu3D-11. [Google Scholar]
- Banchs, A.; de Veciana, G.; Sciancalepore, V.; Costa-Perez, X. Resource Allocation for Network Slicing in Mobile Networks. IEEE Access 2020, 8, 214696–214706. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Tran, N.H.; Han, Z.; Hong, C.S. Network slicing: Recent advances, taxonomy, requirements, and open research challenges. IEEE Access 2020, 8, 36009–36028. [Google Scholar] [CrossRef]
- Wijethilaka, S.; Liyanage, M. Survey on network slicing for Internet of Things realization in 5G networks. IEEE Commun. Surv. Tutor. 2021, 23, 957–994. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Khorov, E.; Kiryanov, A.; Kovkov, D.; Krasilov, A.; Liubogoshchev, M.; Shmelkin, D.; Tang, S. XStream: A new platform enabling communication between applications and the 5G network. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Van Giang, N.; Kim, Y.H. Slicing the next mobile packet core network. In Proceedings of the 2014 11th International Symposium on Wireless Communications Systems (ISWCS), Barcelona, Spain, 26–29 August 2014; pp. 901–904. [Google Scholar]
- Subedi, P.; Alsadoon, A.; Prasad, P.; Rehman, S.; Giweli, N.; Imran, M.; Arif, S. Network slicing: A next generation 5G perspective. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 102. [Google Scholar] [CrossRef]
- Sallent, O.; Perez-Romero, J.; Ferrus, R.; Agusti, R. On radio access network slicing from a radio resource management perspective. IEEE Wirel. Commun. 2017, 24, 166–174. [Google Scholar] [CrossRef]
- Chang, C.Y.; Nikaein, N. RAN runtime slicing system for flexible and dynamic service execution environment. IEEE Access 2018, 6, 34018–34042. [Google Scholar] [CrossRef]
- Ferrus, R.; Sallent, O.; Perez-Romero, J.; Agusti, R. On 5G radio access network slicing: Radio interface protocol features and configuration. IEEE Commun. Mag. 2018, 56, 184–192. [Google Scholar] [CrossRef]
- Liu, Y.J.; Feng, G.; Sun, Y.; Qin, S.; Liang, Y.C. Device association for RAN slicing based on hybrid federated deep reinforcement learning. IEEE Trans. Veh. Technol. 2020, 69, 15731–15745. [Google Scholar] [CrossRef]
- Mazied, E.A.; Liu, L.; Midkiff, S.F. Towards Intelligent RAN Slicing for B5G: Opportunities and Challenges. arXiv 2021, arXiv:2103.00227. [Google Scholar]
- Consortium, I.I. Time Sensitive Networks for Flexible Manufacturing Testbed Characterization and Mapping of Converged Traffic Types; Industrial Internet Consortium: Boston, MA, USA, 2019. [Google Scholar]
- Zhao, J.; Jing, X.; Yan, Z.; Pedrycz, W. Network traffic classification for data fusion: A survey. Inf. Fusion 2021, 72, 22–47. [Google Scholar] [CrossRef]
- Application Layer Packet Classifier for Linux. Available online: http://l7-filter.sourceforge.net/ (accessed on 30 November 2021).
- OpenDPI. Available online: https://github.com/thomasbhatia/OpenDPI (accessed on 30 November 2021).
- Libprotoident. Available online: https://github.com/wanduow/libprotoident (accessed on 30 November 2021).
- nDPI. Available online: https://github.com/ntop/nDPI (accessed on 30 November 2021).
- NFStream. Available online: https://github.com/nfstream/nfstream (accessed on 30 November 2021).
- Bujlow, T.; Carela-Español, V.; Barlet-Ros, P. Independent comparison of popular DPI tools for traffic classification. Comput. Netw. 2015, 76, 75–89. [Google Scholar] [CrossRef] [Green Version]
- Open5GCore. Available online: https://www.open5gcore.org (accessed on 2 December 2021).
- Fokus. Available online: https://www.fokus.fraunhofer.de/en (accessed on 2 December 2021).
- Open5GS. Available online: https://open5gs.org (accessed on 2 December 2021).
- Amarisoft. Available online: https://www.amarisoft.com (accessed on 2 December 2021).
- OpenAirInterface Software Alliance, OpenAirInterface (OAI). Available online: https://openairinterface.org (accessed on 2 December 2021).
- free5GC. Available online: https://free5gc.org (accessed on 2 December 2021).
- 3GPP. Non-Access-Stratum (NAS) Protocol for 5G System (5GS). TS 24.501 V17.4.1. September 2021. Available online: https://www.3gpp.org/ftp/Specs/archive/24_series/24.501/24501-h41.zip (accessed on 14 January 2022).
- Alcock, S.; Nelson, R. Measuring the accuracy of open-source payload-based traffic classifiers using popular internet applications. In Proceedings of the 38th Annual IEEE Conference on Local Computer Networks-Workshops, Sydney, NSW, Australia, 21–24 October 2013; pp. 956–963. [Google Scholar]
- Deri, L.; Martinelli, M.; Bujlow, T.; Cardigliano, A. ndpi: Open-source high-speed deep packet inspection. In Proceedings of the 2014 International Wireless Communications and Mobile Computing Conference (IWCMC), Nicosia, Cyprus, 4–8 August 2014; pp. 617–622. [Google Scholar]
- iPerf. Available online: https://iperf.fr/ (accessed on 25 January 2022).
- Schulz, P.; Matthe, M.; Klessig, H.; Simsek, M.; Fettweis, G.; Ansari, J.; Ashraf, S.A.; Almeroth, B.; Voigt, J.; Riedel, I.; et al. Latency critical IoT applications in 5G: Perspective on the design of radio interface and network architecture. IEEE Commun. Mag. 2017, 55, 70–78. [Google Scholar] [CrossRef]
- Ma, Z.; Xiao, M.; Xiao, Y.; Pang, Z.; Poor, H.V.; Vucetic, B. High-reliability and low-latency wireless communication for internet of things: Challenges, fundamentals, and enabling technologies. IEEE Internet Things J. 2019, 6, 7946–7970. [Google Scholar] [CrossRef]




| SST | Slice/Service Type |
|---|---|
| 1 | eMBB |
| 2 | URLLC |
| 3 | Massive IoT (MIoT) |
| 4 | Vehicle to everything (V2X) |
| 5 | High-Performance Machine-Type Communications (HMTC) |
| Traffic Characteristics | |||||
|---|---|---|---|---|---|
| Traffic | Tolerance to Loss | Network Requirement Guarantee | Packet Size (Bytes) | Criticality | Periodicity |
| Video | Yes | Latency | High (1000∼1500) | Medium | Periodic |
| Audio/Voice | Yes | Latency | Variable (20∼1500) | Medium | Periodic |
| IoT | No | Nº of connections | Low (50∼500) | Low | Periodic |
| WebData | No | Bandwidth | Variable (30∼1500) | Low | Sporadic |
| Data Transfer | No | Bandwidth | Variable (30∼1500) | Low | Sporadic |
| Control Data | No | Latency | Ultra low (30∼150) | High | Periodic |
| Best-Effort | Yes | None | Variable (30∼1500) | None | Sporadic |
| Name | Released | Updates | Language | Apps/Protocols Identified |
|---|---|---|---|---|
| L7-filter | 2009 | Deprecated | C++ | ∼110 |
| OpenDPI | 2011 | Deprecated | C | ∼100 |
| Libprotoident | 2013 | 2–3 quarter | C++ | ∼250 |
| nDPI | 2014 | Few days | C | ∼170 |
| NFStream | 2019 | Few days | Phyton | ∼180 |
| Name | Description | Pros | Cons |
|---|---|---|---|
| Open5GCore [42] | Commercial software for 5GC [43] | Allows virtualization of the software | The same level of bandwidth, throughput, latency, etc., for each slice. So, no difference between slices. License needed |
| Open5Gs [44] | Open-source software for 5GC with C language | Allows for virtualization of the software. The number of UEs per slice is not limited | Only 5GC deployment without RAN |
| Amarisoft [45] | Commercial products for 5GC, RAN, and UEs | Supports virtualization depending on the license purchased. Allows end-to-end 5G network deployment with network slicing | Radio network slicing is applied in the scheduler of the base station called gNodeB (gNB) through traffic prioritization |
| Slice/ SST ID | 5QI | Traffic Type | Protocol | Periodicity | Priority | IP Address of the PDU Session |
|---|---|---|---|---|---|---|
| 1 | 5 | Control | DNS/ ICMP | Variable | 1 (Ultra high) | 192.168.3.6 |
| 2 | 6 | Video | RTP/ RTCP | 25 frames per second | 5 (High) | 192.168.3.10 |
| 3 | 9 | IoT | MQTT | 0.5 s | 9 (Medium) | 192.168.3.14 |
| 4 | 8 | WebData | HTTP/ HTTPS | Variable | 13 (Low) | 192.168.3.18 |
| 7 | 70 | Best-effort/ default | Non specified | Variable | 16 (Ultra low) | 192.168.3.2 |
| Time (s) | Bandwidth (Mbps) | |||
|---|---|---|---|---|
| Slice 1 | Slice 2 | Slice 3 | Slice 4 | |
| 0–20 | 20 | 20 | 20 | 20 |
| 20–40 | 40 | 20 | 20 | 20 |
| 40–60 | 60 | 20 | 20 | 20 |
| 60–80 | 80 | 20 | 20 | 20 |
| 80–100 | 100 | 20 | 20 | 20 |
| 100–120 | 20 | 20 | 20 | 20 |
| 120–140 | 20 | 40 | 20 | 20 |
| 140–160 | 20 | 60 | 20 | 20 |
| 160–180 | 20 | 80 | 20 | 20 |
| 180–200 | 20 | 20 | 20 | 20 |
| 200–220 | 20 | 20 | 40 | 20 |
| 220–240 | 20 | 20 | 60 | 20 |
| 240–260 | 20 | 20 | 20 | 20 |
| 260–280 | 20 | 20 | 20 | 40 |
| 280–300 | 20 | 20 | 20 | 20 |
| Times (s) | Without Prioritization (ms) | First Approach (ms) | Second Approach (ms) |
|---|---|---|---|
| 0–20 | 0.86865 | 1.69075 | 0.8868 |
| 20–40 | 1.3488 | 1.3746 | 0.8973 |
| 40–60 | 1.75745 | 1.21645 | 0.8373 |
| 60–80 | 2.1286 | 0.9007 | 0.7713 |
| 80–100 | 2.43515 | 0.8378 | 0.79385 |
| 100–120 | 0.85055 | 1.5392 | 0.9122 |
| 120–140 | 0.83605 | 1.6702 | 1.03025 |
| 140–160 | 0.86075 | 1.4451 | 1.1007 |
| 160–180 | 0.9496 | 1.4847 | 1.1278 |
| 180–200 | 0.8391 | 1.70245 | 1.20035 |
| 200–220 | 0.82355 | 1.30005 | 1.1501 |
| 220–240 | 0.85865 | 1.48455 | 1.1113 |
| 240–260 | 0.83575 | 1.50085 | 1.108 |
| 260–280 | 0.83655 | 1.7163 | 1.13495 |
| 280–300 | 0.89005 | 1.64653 | 1.25858 |
| Times (s) | Without Prioritization (ms) | First Approach (ms) | Second Approach (ms) |
|---|---|---|---|
| 0–20 | 0.8396 | 1.681 | 0.8614 |
| 20–40 | 0.8445 | 1.65525 | 0.9488 |
| 40–60 | 0.80605 | 1.92275 | 1.0087 |
| 60–80 | 0.82645 | 1.69285 | 1.3972 |
| 80–100 | 0.94615 | 2.8613 | 5.6984 |
| 100–120 | 0.90295 | 1.3117 | 0.89665 |
| 120–140 | 1.2251 | 1.17465 | 0.88205 |
| 140–160 | 1.7204 | 1.0637 | 0.84345 |
| 160–180 | 1.8813 | 1.39505 | 0.81155 |
| 180–200 | 0.8682 | 1.58875 | 1.13335 |
| 200–220 | 0.82765 | 1.37105 | 1.03115 |
| 220–240 | 0.83425 | 1.5474 | 1.05305 |
| 240–260 | 0.8319 | 1.6727 | 1.12325 |
| 260–280 | 0.80655 | 1.33285 | 1.0661 |
| 280–300 | 0.86074 | 1.37711 | 1.20058 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gabilondo, Á.; Fernández, Z.; Viola, R.; Martín, Á.; Zorrilla, M.; Angueira, P.; Montalbán, J. Traffic Classification for Network Slicing in Mobile Networks. Electronics 2022, 11, 1097. https://doi.org/10.3390/electronics11071097
Gabilondo Á, Fernández Z, Viola R, Martín Á, Zorrilla M, Angueira P, Montalbán J. Traffic Classification for Network Slicing in Mobile Networks. Electronics. 2022; 11(7):1097. https://doi.org/10.3390/electronics11071097
Chicago/Turabian StyleGabilondo, Álvaro, Zaloa Fernández, Roberto Viola, Ángel Martín, Mikel Zorrilla, Pablo Angueira, and Jon Montalbán. 2022. "Traffic Classification for Network Slicing in Mobile Networks" Electronics 11, no. 7: 1097. https://doi.org/10.3390/electronics11071097
APA StyleGabilondo, Á., Fernández, Z., Viola, R., Martín, Á., Zorrilla, M., Angueira, P., & Montalbán, J. (2022). Traffic Classification for Network Slicing in Mobile Networks. Electronics, 11(7), 1097. https://doi.org/10.3390/electronics11071097







