An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks
Abstract
1. Introduction
1.1. Problem Definition
1.2. Related Works
1.3. Contributions
- A secure anonymous authentication protocol is proposed to establish the trust relationship between RSU and vehicle, which realizes the legality verification of communication entity before data sharing.
- We use blockchain technology and cloud storage to realize the data sharing among vehicles in VSNs, so as to ensure that the data users can obtain the data information they are interested in in time.
- The proposed scheme supports sensitive hidden information to ensure that data users can not find the sensitive information of the data owners through the obtained data.
- Security analysis and performance analysis show that our scheme is secure and effective.
1.4. Paper Organization
2. Preliminaries
2.1. Vehicular Scoial Networks (VSNs)
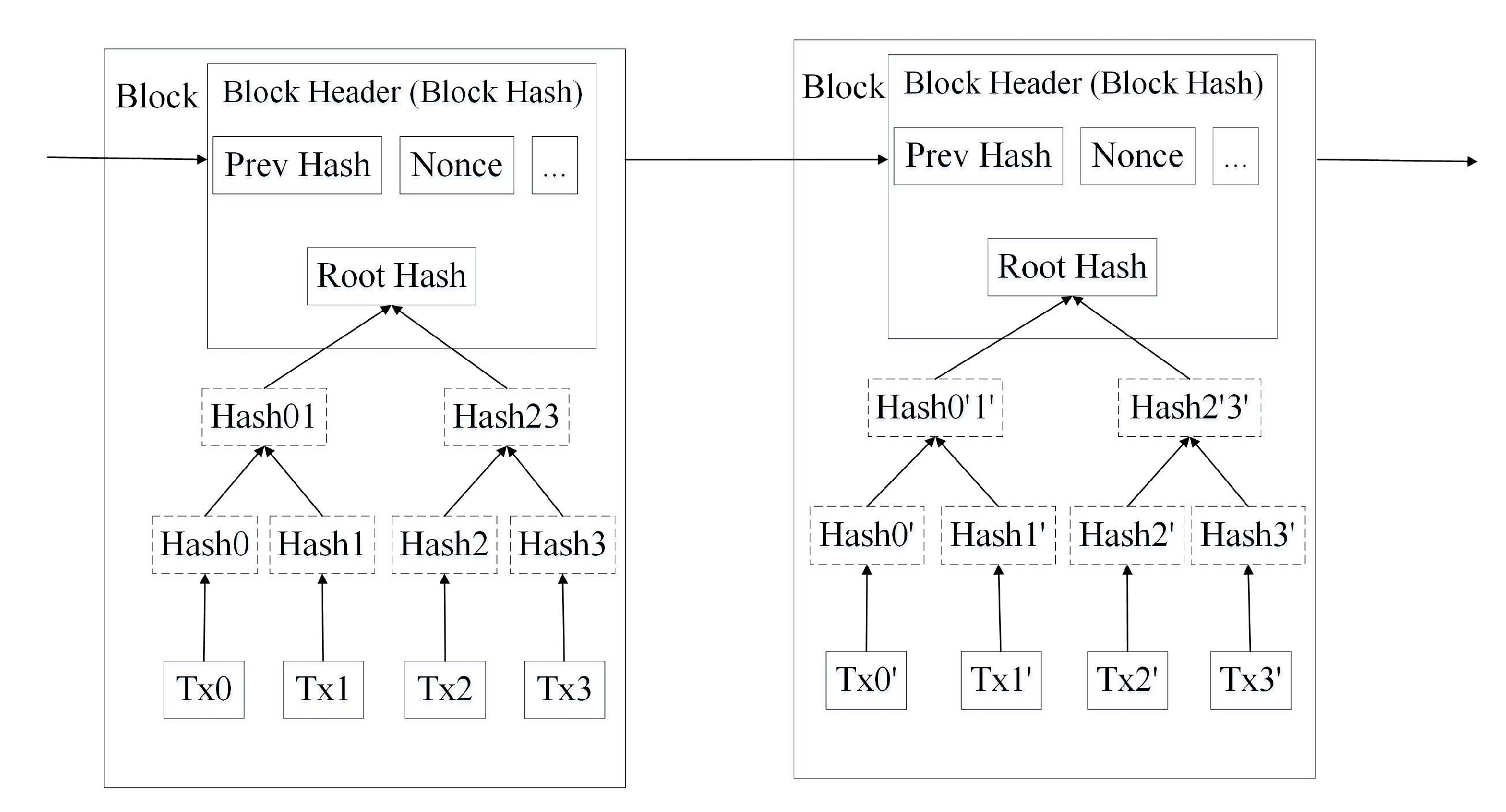
2.2. Blockchain
- Decentralization. Decentralization means there is no need for a third party to centrally manage the system. Due to distributed account and storage, the rights and obligations of any node in system are equal. The data blocks in the system are jointly maintained by the nodes in the whole system.
- No tampering. In blockchain, individual tampering cannot be recognized by the whole network, which makes data tampering impossible.
- Openness. Blockchain data opens to all nodes except the protected private information. Anyone can query the data stored in blockchain and develop applications.
- Auditability. The operation information of nodes is required to store in blockchain and all nodes in the system hold the copy of all data saved. Thus, all logs of users’ operations on the blockchain can be queried.
- Fault tolerance: Any faults can be corrected by decentralized consensus. If a node fails, blockchain support other nodes to recover all data stored by the fails node.
2.3. Bilinear Mapping
- Bilinearty: For any P, Q ∈ and a, b ∈ , .
- Non-degeneracy: Existing P, Q ∈ satisfies .
- Computability: For all P, Q ∈ , can be calculated efficiently.
3. The Proposed Scheme
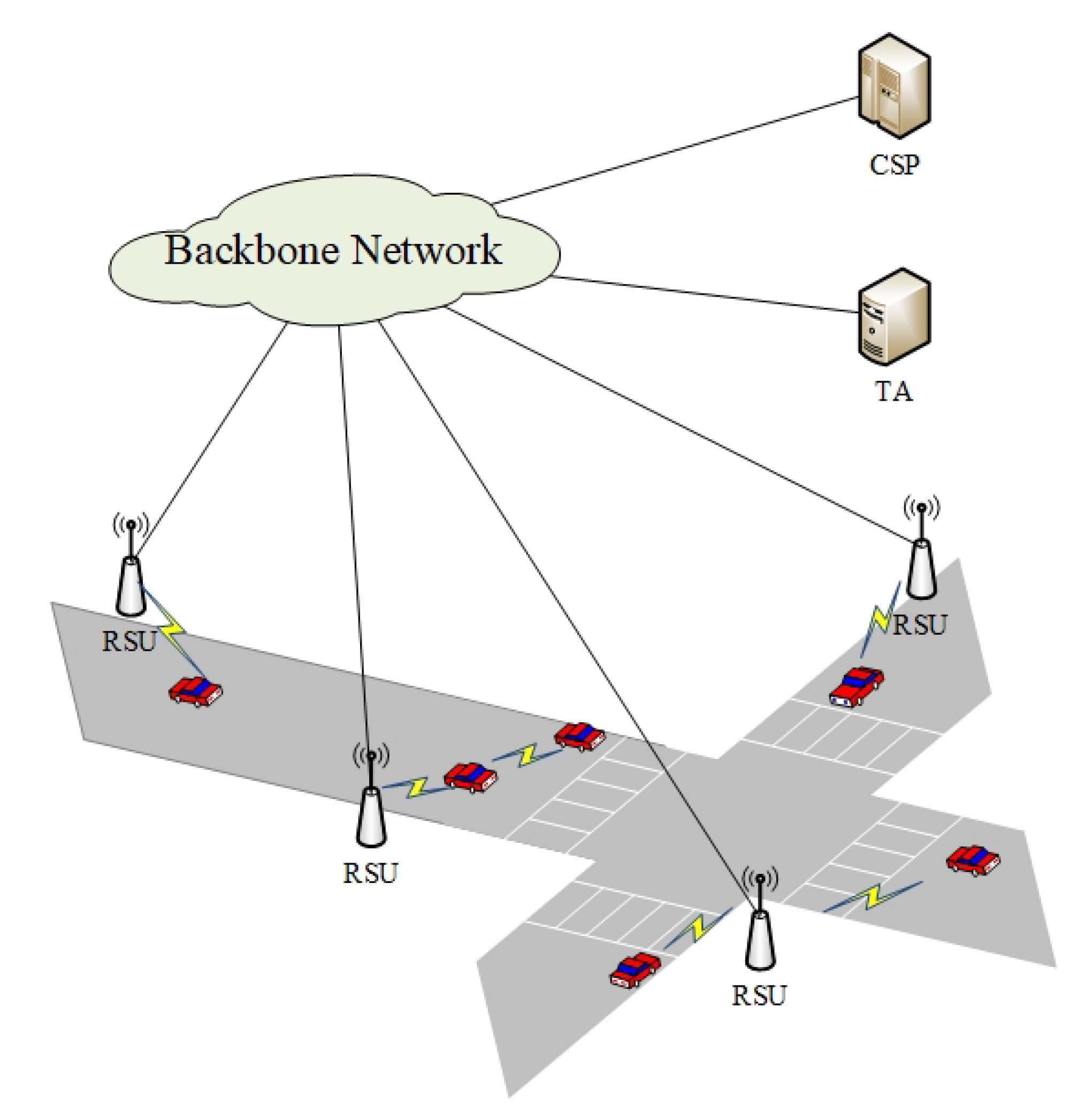
3.1. System Model
- TA is a third-party trusted authority. All entities in VSNs trust TA. In system initialization, TA is responsible for generating public system parameters, providing registration services for other nodes in VSNs, and supports for establishing trust relationship between vehicles and RSUs.
- CSP is the entity managing the cloud resources and provides a variety of application services based on cloud resources for vehicles in VSNs. In the proposed scheme, CSP provides data sharing services for vehicles to support vehicles to obtain interested data in time.
- RSUs deployed on both roadside have the ability to obtain the surrounding road information by communicating with vehicles, so as to support the vehicles to obtain the necessary information in time. At the same time, RSUs assist vehicles to communicate with CSP to upload or use data. Moreover, all RSUs in VSNs build blockchain network, which stores data owner pseudonym, the key words of shared data, and the address of storing data in CSP. Each RSU shares the data with other RSUs through the consensus mechanism. The vehicle authenticated by RSUs can obtain the address of the required data stored in CSP through communication with RSUs, and then obtain the data.
- Vehicles follow the WAVE/DSRC standard to communicate with surrounding vehicles and RSUs. In VSNs, vehicles can apply to upload data to cloud through RSU and CSP, and legitimate vehicles can also obtain interested data information from cloud.
3.2. Security Assumption
3.3. Security Goal
- (1)
- User Privacy. The true identities of vehicles are hidden from CSP, RSUs, and other vehicles, which means RSU cannot get the true identities of vehicles in authentication and providing services. Meanwhile, data users can not determine the real identity of the data sharer according to the data obtained.
- (2)
- Data Confidentiality. Entities that do not meet the access policy cannot obtain any information related to plaintext through ciphertext.
- (3)
- Accountability and Credential Revocation. All operations on data sharing should be recorded. Once illegal behaviors are found, illegal entities should be revoked in time.
- (4)
- CSP Attacks Resistance. On the basis of guaranteeing data confidentiality, CSP cannot forge or tamper with data.
- (5)
- Minimum Disclosure and Unlinkability. The data users cannot associate with the true identity of the data owner through the acquired data.
- (6)
- Distributed Resolution Authority. Any single authority can not track a vehicle’s trajectory or all its behaviors.
3.4. System Initialization
- Let be an additive group where for prime p, be an multiplicative group with the same prime p. P is the generator of . Meanwhile, An bilinear pairing is selected
- Two hash functions , are defined. TA chooses master key .
- TA compute its public key .
- For k attributes , attributes values are defined, where each attribute includes 3 values: : a vehicle has ; : a vehicle does not a proper the attribute , and : does not care.
- TA chooses and computes , where . Then TA selects and gets .
- TA broadcasts the parameters , , p, e, P, , , ..., , ..., , , , , to all entities in VSNs.
3.5. Vehicle Registration Protocol
- Vehicle chooses , random number and uses to compute and . Finally, and are sent to TA.
- If receiving the registration message from vehicle, TA first decrypts to get , . Then, TA generates n pseudonyms () and computes corresponding public key , private key: , where , is the expiration of . After that, For the vehicle attribute list , TA picks k random numbers , and computes . Then, TA generates vehicle attribute based private key , where , . Finally, TA calculates and adopts AES mechanism to encrypt , , , , : , , , , . TA sends to vehicle.
- When obtain the cipthertext from TA, vehicle first computes session key: , and uses to decrypt and gets , , , , . vehicle verifies the correctness of , if is correct, then vehicle stores , , , .
3.6. RSU Registration Protocol
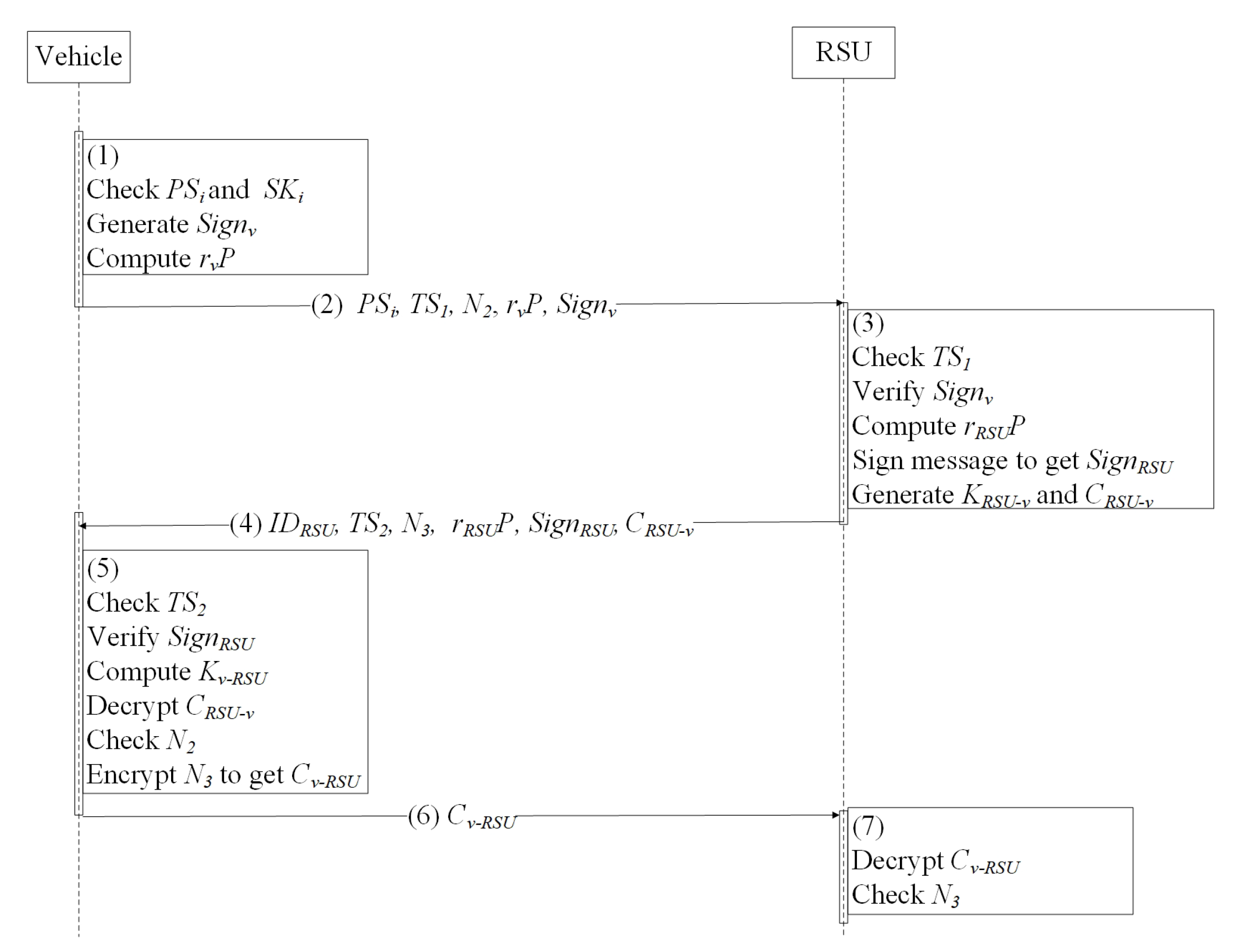
3.7. V2I Authentication Protocol
- Vehicle chooses , , , , and to generate signature , , , , , where , , is current timestamp, is challenge value and is the key agreement parameter.
- Vehicle sends , , , , , and to RSU.
- When receiving the request message from vehicle, RSU first checks the freshness of and the validity of . If is fresh and is valid, then, RSU computes , and check , if the equation holds, vehicle is considered as a legal vehicle. Finally, RSU signs , , , to get and generates session key . Then RSU adopts AES mechanism to encrypt and gets , where .
- RSU sends , , , , , and to vehicle.
- Vehicle checks the freshness of and verifies the legitimacy of . If is fresh, and is legal, RSU is thought to be a legal entity. Then, vehicle generates session key to decrypt and gets , if is legal, vehicle believe that a secure channel is established between the vehicle and the RSU. Finally, vehicle adopts AES mechanism to encrypt : .
- Vehicle sends to RSU.
- RSU decrypts to get . If is legal, RSU believes a secure channel is established.
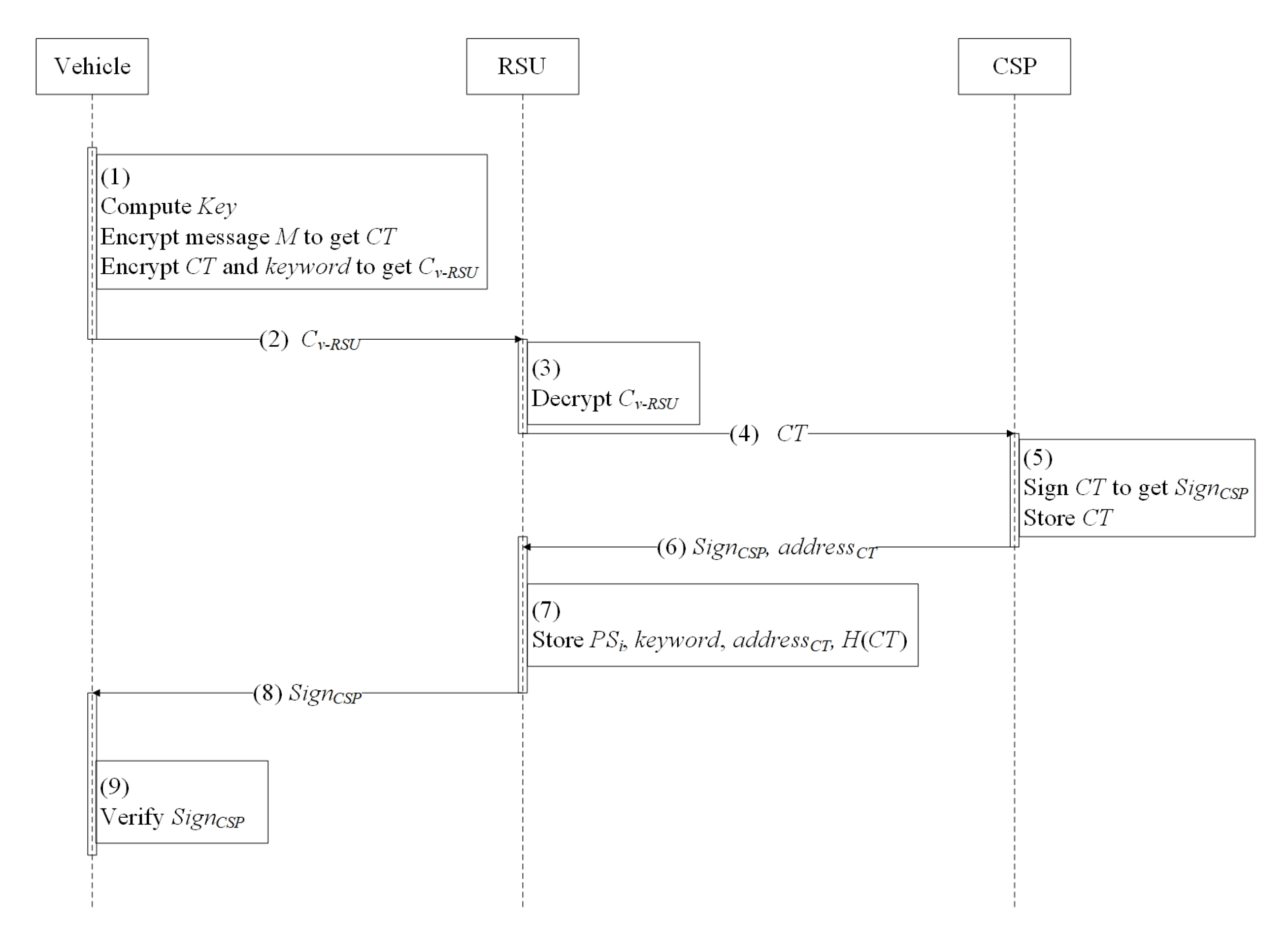
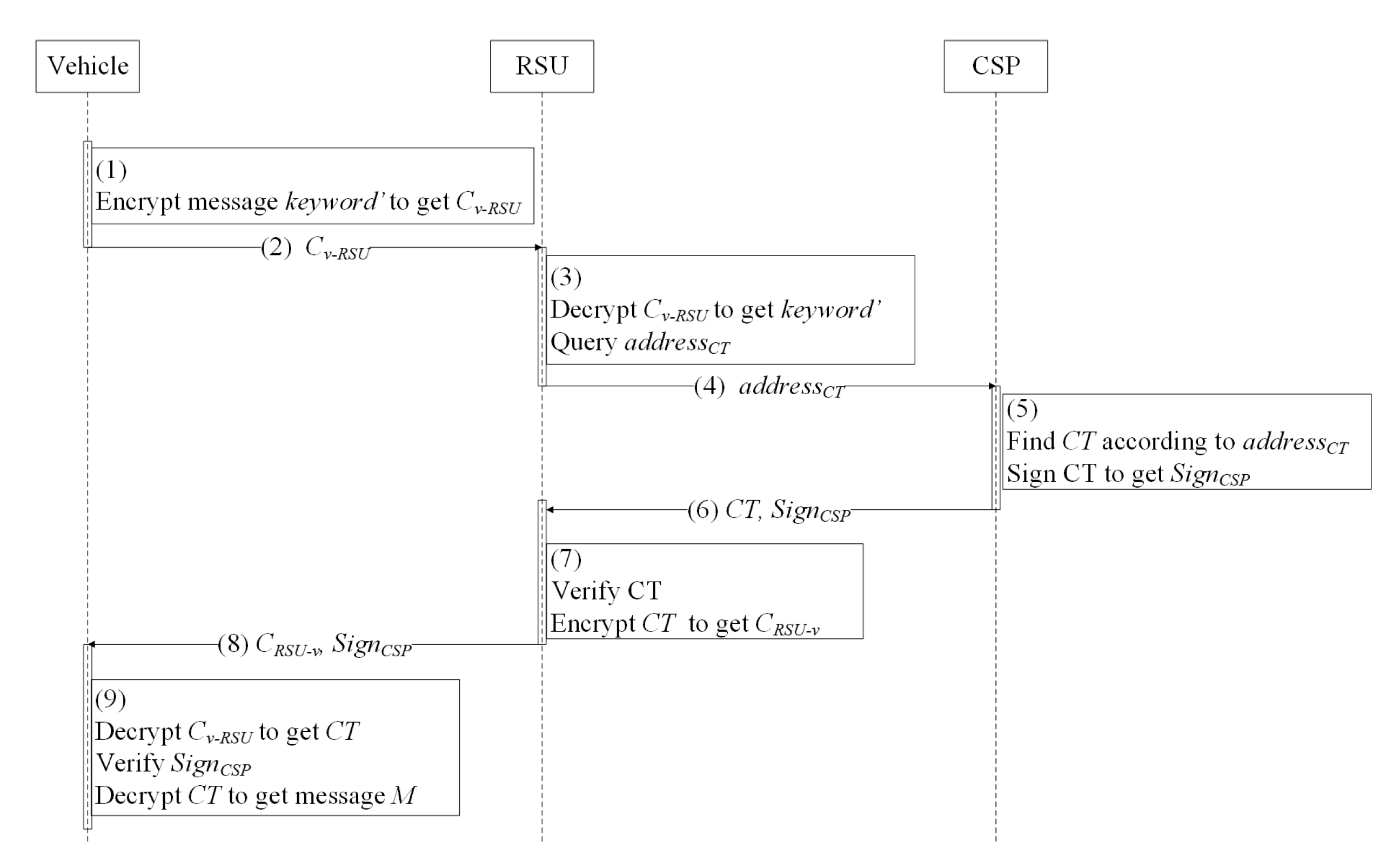
3.8. Data Sharing Protocol
- For message M and the policy W with k attributes, vehicle chooses and computes data encryption key .
- Vehicle adopts AES mechanism to encrypt M to get . Meanwhile, vehicle sets , . Finally vehicle outputs . The encryptext of M is .
- Vehicle encrypts , the keyword of message M to get , , where AES mechanism is used as encryption mechanism.
- Vehicle sends to RSU.
- When RSU receives the ciphertext from vehicle, RSU decrypts to get , , and sends to CSP.
- CSP stores and signs and to gets , where is the address of data stored in cloud. Then CSP sends to RSU.
- RSU verifies and stores , , , and hash value of in blockchain. Then RSU sends to vehicle.
- Vehicle verifies , if is legal, vehicle believes that has been stored in cloud.
- Vehicle adopts AES mechanism to encrypt it interested in to get .
- Vehicle sends to RSU.
- RSU decrypts and gets . Then RSU finds of the data according to .
- RSU sends to CSP via secure tunnel.
- CSP queries by address and signs to get .
- CSP sends and back to RSU.
- RSU verifies and checks whether the hash value of stored in blockchain equals , if the equation holds, RSU encrypts to get and stores the data downloading log into blockchain.
- RSU sends and to vehicle.
- Vehicle decrypts to get . Then, vehicle verifies signature , if the signature is legal, vehicle constructs local guess of access policy , after that, , vehicle computes , . Afterwards, vehicle computes . When computing all k terms, vehicle are able to get =·. Finally, vehicle decrypts to get the message it interested in.
4. Security Analysis
- (1)
- User Privacy. For vehicle identity privacy protection, in mutual authentication, a vehicle uses its pseudonym and signature to prove the legality of its identity in VSNs, which means that no entity other than the TA can determine the true identity of other vehicles. In the process of data downloading, a data user only needs to prove that he/she has the right to obtain the required data, and meanwhile, since data does not contain any identity information, the data user cannot associate the real identity of the data owner according to the data.
- (2)
- Data Confidentiality. The data is encrypted and stored in the CSP. Any user who does not meet access policies cannot obtain the plaintext. In addition, since the blockchain maintained by RSUs only stores the mapping relationship between keyword and address, RSUs cannot obtain useful data information.
- (3)
- Accountability and Credential Revocation. In a secure network environment, the system can track the data information sent by vehicles in time, and exclude illegal vehicles from the network. The proposed scheme supports illegal vehicles revocation. If a vehicle is comprised, RSU are able to upload its pseudonym , signature , and operation logs to TA and applies to reveal the true identity of the comprised vehicle. due to the signature and unforgeable logs, the vehicle cannot deny its illegal behaviour. Consequently, when the information of the illegal vehicle is broadcast in VSNs, the illegal vehicle can not communicate with other entities in VSNs.
- (4)
- CSP Attacks Resistance. According to security assumption, CSP has access to grant the data stored, which means CSP may analyze the stored data and try to obtain the privacy of the data owner. In the proposed scheme, the message is encrypted by attribute-based encryption mechanism, CSP can not decrypt the ciphertext depending on its own attributes. Besides, for the issue that CSP may tamper with data, in data uploading protocol, CSP is required to generate to prove that the message was stored in the cloud without being tampered with. In data downloading protocol, RSU is able to check whether stored in blockchain is equal , where is the data from CSP. If the verification fails, the data is considered to be tempered.
- (5)
- Minimum Disclosure and Unlinkability. In data sharing scheme, data users can not reveal information other than what the data owner wants to share. In the proposed scheme, the content of data in CSP is completely determined by the data owner. Therefore, any entity cannot obtain the information that the data owner does not want to expose through the data. In the aspect of data association, the association between data and real vehicle information depends on the security of pseudonym changing mechanism.
- (6)
- Distributed Resolution Authority. In a security network environment, any single entity cannot rely on the information collected by itself to track vehicles. For the proposed scheme, in terms of vehicle identity privacy protection, the mapping between the pseudonym and the real vehicle identity is maintained by TA. However, as the vehicle changes its pseudonym frequently during the communication with the surrounding RSUs and other vehicles, TA can not know the vehicle’s trajectory alone. Similarly, RSUs only know the pseudonym information and location information of the current communication vehicle. RSUs can not obtain the real identity and long-term trajectory of the vehicle. In terms of data sharing, CSP only provides data uploading and data downloading services for vehicles and cannot accurately know the identity of the data owner. Similarly, RSUs only maintain the list of keyword address and cannot obtain the real content of the data.
5. Performance Analysis
5.1. Computational Cost
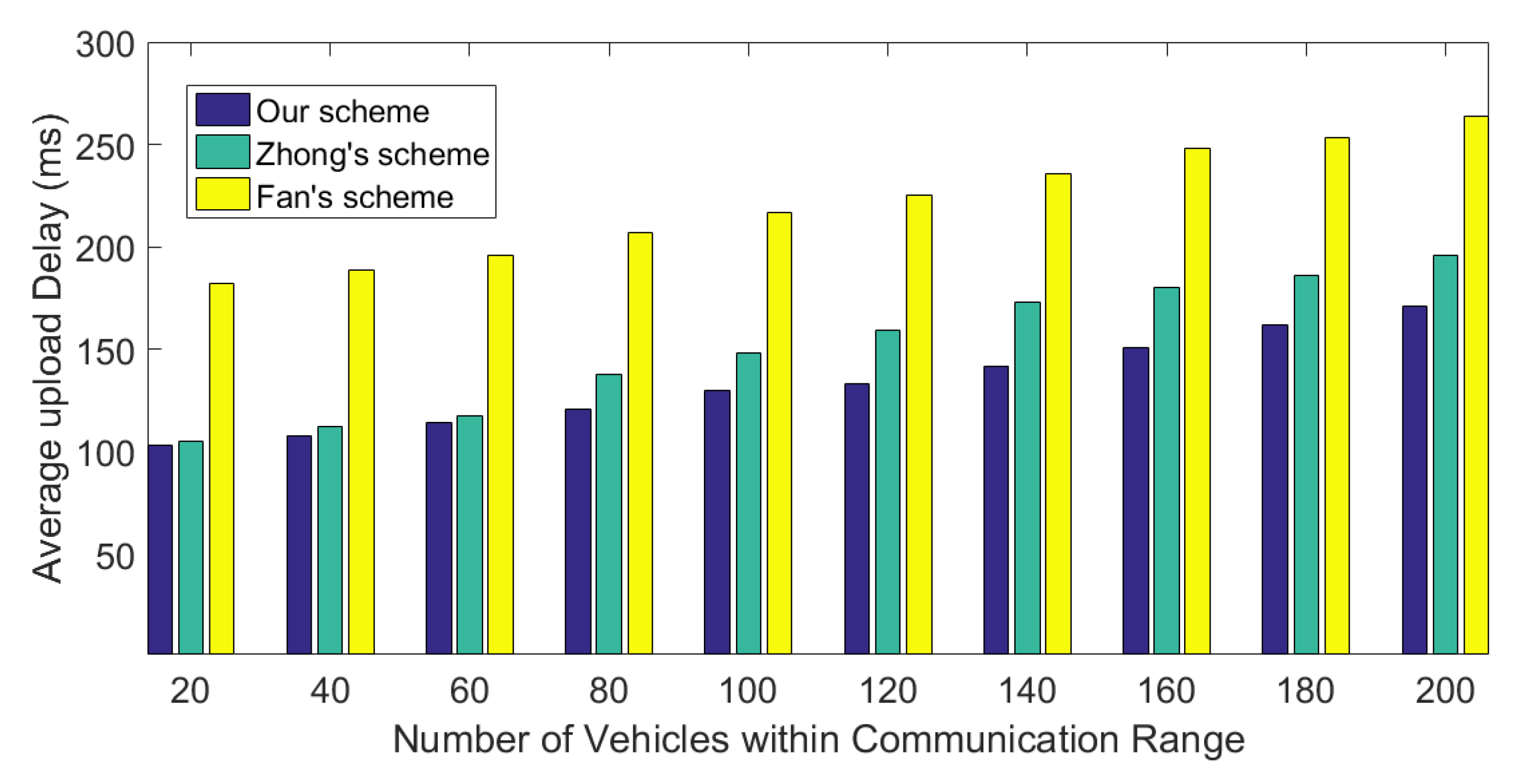
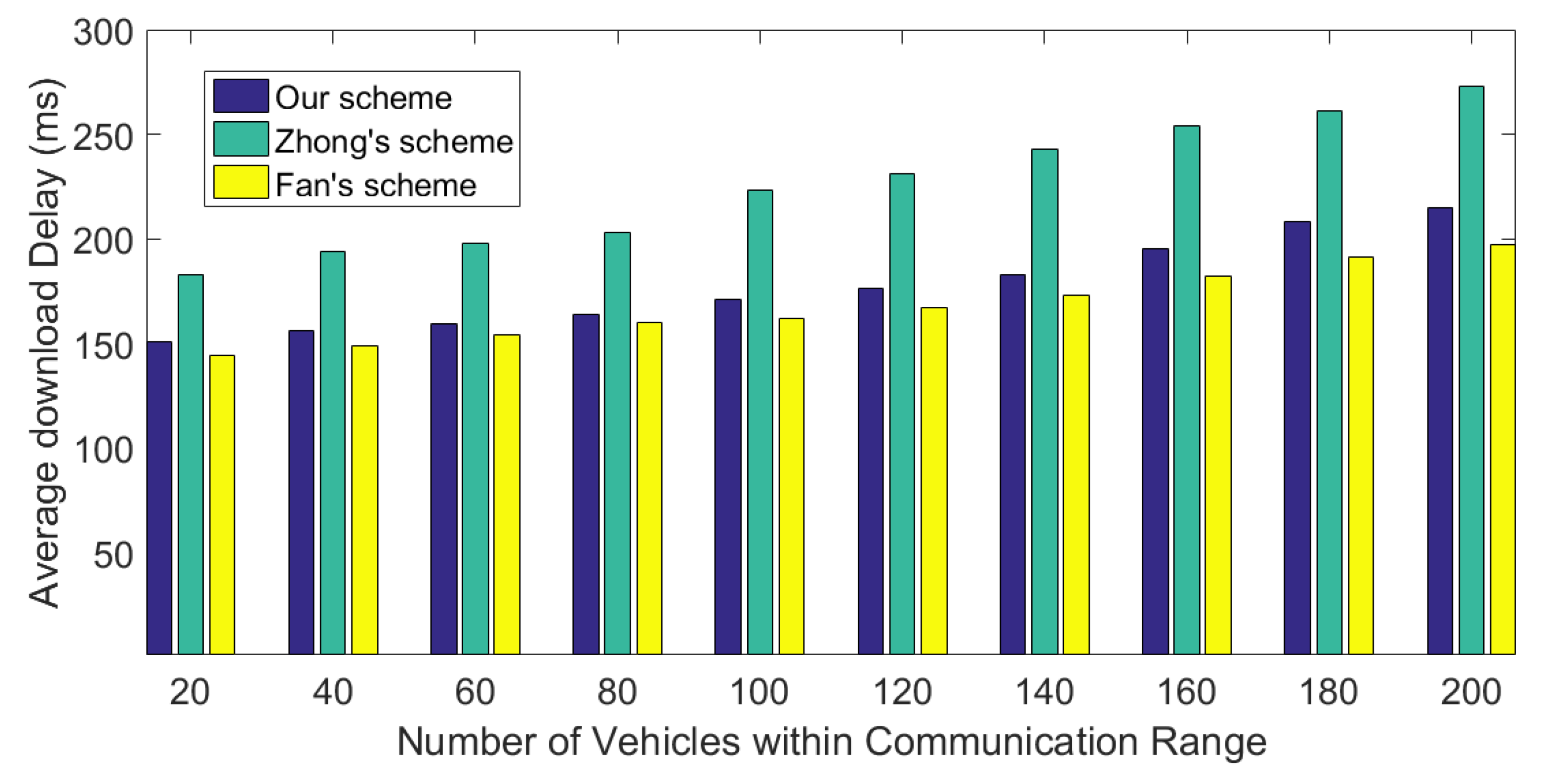
5.2. Communication Cost
5.3. Simulation
6. Discussion
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Qu, F.; Wu, Z.; Wang, F.; Cho, W. A Security and Privacy Review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996. [Google Scholar] [CrossRef]
- Boualouache, A.; Senouci, S.; Moussaoui, S. A Survey on Pseudonym Changing Strategies for Vehicular Ad Hoc Networks. IEEE Commun. Surv. Tutor. 2018, 20, 770–790. [Google Scholar] [CrossRef]
- IEEE Guide for Wireless Access in Vehicular Environments (WAVE) Architecture; IEEE Std; IEEE: Piscatawat, NJ, USA, 2019; pp. 1–219.
- Intelligent Transport Systems (ITS); Communications Architecture. Available online: https://www.etsi.org/deliver/etsi_EN/302600_302699/302665/01.00.00_20/en_302665v010000c.pdf (accessed on 4 November 2020).
- Vegni, A.M.; Loscri, V. A Survey on Vehicular Social Networks. IEEE Commun. Surv. Tutor. 2015, 17, 2397–2419. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Zhou, M.; Hu, X.; Wang, L.; Zhang, Y.; Yu, F.R.; Hu, B. Privacy-Preserving Content Dissemination for Vehicular Social Networks: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2019, 121, 1314–1345. [Google Scholar] [CrossRef]
- Liu, Z.; Xiong, L.; Peng, T.; Peng, D.; Liang, H. A Realistic Distributed Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Access 2018, 6, 26307–26317. [Google Scholar] [CrossRef]
- Ren, H.; Li, H.; Dai, Y.; Yang, K.; Lin, X. Querying in Internet of Things with Privacy Preserving: Challenges, Solutions and Opportunities. IEEE Netw. 2018, 32, 144–151. [Google Scholar] [CrossRef]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2020. under accepted. [Google Scholar] [CrossRef]
- Petit, J.; Schaub, F.; Feiri, M.; Kargl, F. Pseudonym Schemes in Vehicular Networks: A Survey. IEEE Commun. Surv. Tutor. 2015, 17, 228–255. [Google Scholar] [CrossRef]
- Jiang, Y.; Ge, S.; Shen, X. AAAS: An Anonymous Authentication Scheme Based on Group Signature in VANETs. IEEE Access 2020, 8, 98986–98998. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J. The security of vehicular ad hoc networks. In Proceedings of the 3rd ACM Workshop on Security of Ad hoc and Sensor Networks, Alexandria, VA, USA, 7 November 2005. [Google Scholar]
- Wasef, A.; Shen, X. EMAP: Expedite Message Authentication Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2013, 12, 78–89. [Google Scholar] [CrossRef]
- de Fuentes, J.M.; GonzÃąlez-Manzano, L.; Serna-Olvera, J.; Veseli, F. Assessment of attribute-based credentials for privacy-preserving road traffic services in smart cities. Pers. Ubiquitous. Comput. 2017, 21, 869–891. [Google Scholar] [CrossRef][Green Version]
- Lu, R.; Lin, X.; Luan, T.H.; Liang, X.; Shen, X. Pseudonym Changing at Social Spots: An Effective Strategy for Location Privacy in VANETs. IEEE Trans. Veh. Technol. 2012, 61, 86–96. [Google Scholar] [CrossRef]
- Zhu, X.; Jiang, S.; Wang, L.; Li, H. Efficient Privacy-Preserving Authentication for Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2014, 63, 907–919. [Google Scholar] [CrossRef]
- Hao, Y.; Cheng, Y.; Zhou, C.; Song, W. A Distributed Key Management Framework with Cooperative Message Authentication in VANETs. IEEE J. Sel. Areas Commun. 2011, 29, 616–629. [Google Scholar] [CrossRef]
- Tzeng, S.; Horng, S.; Li, T.; Wang, X.; Huang, P.; Khan, M.K. Enhancing Security and Privacy for Identity-Based Batch Verification Scheme in VANETs. IEEE Trans. Veh. Technol. 2017, 66, 3235–3248. [Google Scholar] [CrossRef]
- Xie, Y.; Wu, L.; Shen, J.; Alelaiwi, A. EIAS-CP: New efficient identity-based authentication scheme with conditional privacy-preserving for VANETs. Telecommun. Syst. 2017, 65, 229–240. [Google Scholar] [CrossRef]
- Wang, S.; Yao, N. LIAP: A local identity-based anonymous message authentication protocol in VANETs. Comput. Commun. 2017, 112, 154–164. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Z.; Hui, L.; Zhou, Z. A Novel Message Authentication Scheme With Absolute Privacy for the Internet of Things Networks. IEEE Access 2020, 8, 39689–39699. [Google Scholar] [CrossRef]
- Nakamura, N.; Niimi, Y.; Ishihara, S. Live VANET CDN: Adaptive data dissemination scheme for location-dependent data in VANETs. In Proceedings of the 2013 IEEE Vehicular Networking Conference, Boston, MA, USA, 16–18 December 2013. [Google Scholar]
- Zhong, H.; Zhu, W.; Xu, Y.; Cui, J. Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage. Soft Comput. 2016, 22, 1–9. [Google Scholar] [CrossRef]
- Fan, K.; Pan, Q.; Zhang, K.; Bai, Y.; Sun, S.; Li, H.; Yang, Y. A Secure and Verifiable Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. IEEE Trans. Veh. Technol. 2020, 69, 5826–5835. [Google Scholar] [CrossRef]
- Pu, Y.; Xiang, T.; Hu, C.; Alrawais, A.; Yan, H. An Efficient Blockchain-based Privacy Preserving Scheme for Vehicular Social Networks. Inf. Sci. 2020, 540, 308–324. [Google Scholar] [CrossRef]
- Rahim, A.; Kong, X.; Xia, F.; Ning, Z.; Ullah, N.; Wang, J.; Das, S.K. Vehicular Social Networks: A survey. Pervasive Mob. Comput. 2018, 43, 96–113. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. A survey on Intrusion Detection Systems and Honeypot based proactive security mechanisms in VANETs and VANET Cloud. Veh. Commun. 2018, 12, 138–164. [Google Scholar] [CrossRef]
- Abboud, K.; Omar, H.A.; Zhuang, W. Interworking of DSRC and Cellular Network Technologies for V2X Communications: A Survey. IEEE Trans. Veh. Technol. 2016, 12, 9457–9470. [Google Scholar] [CrossRef]
- Ning, Z.; Xia, F.; Ullah, N.; Kong, X.; Hu, X. Vehicular Social Networks: Enabling Smart Mobility. IEEE Commun. Mag. 2017, 55, 16–55. [Google Scholar] [CrossRef]
- Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 21 October 2020).
- Kumar, V. A Bilinear Pairing Based Secure Data Aggregation Scheme for WSNs. In Proceedings of the 2019 15th International Wireless Communications and Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019. [Google Scholar]
- Hess, F. Efficient Identity Based Signature Schemes Based on Pairings. In Selected Areas in Cryptography; Nyberg, K., Heys, H., Eds.; Springer: Berlin, Germany, 2003; pp. 310–324. [Google Scholar]
- Zhou, Z.; Huang, D.; Wang, Z. Efficient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption. IEEE Trans. Comput. 2015, 64, 126–138. [Google Scholar] [CrossRef]
- Institute of Transportation System. Available online: https://www.dlr.de/ts/en/desktopdefault.aspx/tabid-9883/16931_read-41000/ (accessed on 5 November 2020).
| Symbol | Description |
|---|---|
| Entity e’s real identity | |
| The i-th pseudonym of entity e | |
| The i-th challenge value | |
| The signature generated by entity e | |
| The ciphertext encrypted by entity e | |
| The shared key between entity and | |
| The public key of entity e | |
| The private key of entity e | |
| The expiration of pseudonym | |
| Current timestamp | |
| The i-th attribute |
| Symbol | Description | Time (ms) |
|---|---|---|
| Bilinear pairing function | 1.35 | |
| Point multiplication function | 1.77 | |
| Point exponentiation function | 1.74 | |
| Hash-to-point function | 4.06 |
| Scheme | Signature Computational Cost (ms) | Verification Computational Cost (ms) |
|---|---|---|
| KPSD | ||
| LIAP | ||
| IMAEP | ||
| our scheme |
| Scheme | Message-Signature | Communication Cost (Byte) |
|---|---|---|
| KPSD | 416 | |
| LIAP | 640 | |
| IMAEP | 148n+256 | |
| Our scheme | 208 |
| Parameter | Values |
|---|---|
| Operating system | Debian 9.4 |
| Traffic generator | SUMO |
| Network simulator | OMNET++ |
| Simulator | veins |
| Simulation area | 1000 m × 1000 m |
| Simulation time | 500 s |
| Number of cars | 250 |
| Data Transmission Rate | 6 Mbps |
| Transmission Power | 20 mW |
| Noise floor | −89 dBm |
| Blockchain | Ethereum |
| The number of attributes | 10 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Y.; Shen, X.; Zheng, S. An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. Electronics 2021, 10, 114. https://doi.org/10.3390/electronics10020114
Jiang Y, Shen X, Zheng S. An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. Electronics. 2021; 10(2):114. https://doi.org/10.3390/electronics10020114
Chicago/Turabian StyleJiang, Yanji, Xueli Shen, and Sifa Zheng. 2021. "An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks" Electronics 10, no. 2: 114. https://doi.org/10.3390/electronics10020114
APA StyleJiang, Y., Shen, X., & Zheng, S. (2021). An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. Electronics, 10(2), 114. https://doi.org/10.3390/electronics10020114





