autoCoin: Secure Content Sharing Based on Blockchain for Vehicular Cloud
Abstract
1. Introduction
- Throughput and scalability: large amounts of data generated over geographical regions need to be recorded or queried simultaneously;
- Latency: a wide range of time limits; safety or traffic data should be exchanged almost in real-time, while the normal road view is not as urgent;
- Reliability: records should be immutable, and actual data should be retrievable;
- Auditability: data to be written in a new block need to be audited by other nodes, not only in terms of inspecting hashes for block serialization but regarding the credibility of the data itself.
- Content publisher: every vehicle can be a publisher, creating data and publishing them through a blockchain;
- Content consumer: not only can vehicles but anyone who needs vehicular data act as the consumer. For example, the NHTSA (National Highway Traffic Safety Administration) or DoT (Department of Transportation) may have interest in traffic information and videos of the road view. A consumer would search for contents in a blockchain and pay for them;
- Miner: not only can vehicles and RSUs of the vehicular cloud but dedicated blockchain nodes in the Internet act as a “miner”, sustaining a public ledger for vehicular data with a specific consensus algorithm. Fixed and wired nodes such as RSUs are more reliable to manage a blockchain rather than vehicles.
2. Background
2.1. Vehicular Cloud
2.2. Blockchain Overview
2.3. Blockchain Consensus Algorithms
2.4. Blockchain Scalability
3. autoCoin: Blockchain for Vehicular Cloud
3.1. Vehicular Data Management Using Blockchain
- Regional cloud: the video data are stored within a vehicular cloud, where vehicles can access the data using a Geographic Hash Table (GHT) [55]. However, it is complicated to manage the videos transferred over the regional cloud as vehicles enter and exist the cloud frequently; for instance, vehicles have to copy videos to all incoming vehicles by broadcasting;
- Central cloud: the video data are stored at a central cloud. Accordingly, each vehicle should upload its own data regardless of demands from other vehicles, which demands large amounts of storage in the Internet and expensive cellular connections, even though all parties can easily look up the data;
- Local cache with location registration: VICN allows each vehicle to hold its own data in its local storage, while it registers the data location in the same manner as a Uniform Resource Identifier (URI) (e.g., /blockchain-account/mike/v/1.mp4 (accessed on 18 June 2021)) on a central server as meta-data information for data query. Content data can be queried and delivered by content routing [14,22].
3.2. Hierarchical Vehicular Blockchain
- Macro vehicular blockchain: a blockchain deals with vehicular data generated in a certain country, state or big city. Many vehicles and roads can generate tremendous numbers of transactions and also increase the forking probability. However, a single chain is tamper-resilient due to the difficulty of forming a majority for attack and allows vehicles to exchange contents with a single coin;
- Micro vehicular blockchain: a blockchain can be set for a small city or district. The small size of a group allows nodes to reach agreement quickly and significantly reduces the effort to perform synchronization globally, although it could be vulnerable to a majority attack; a small number of nodes for attacks on the chain can be easily gathered. In addition, there could be more than several hundred chains for a country. Therefore, additional management and consensus algorithms for security and multiple regional chains are necessary.
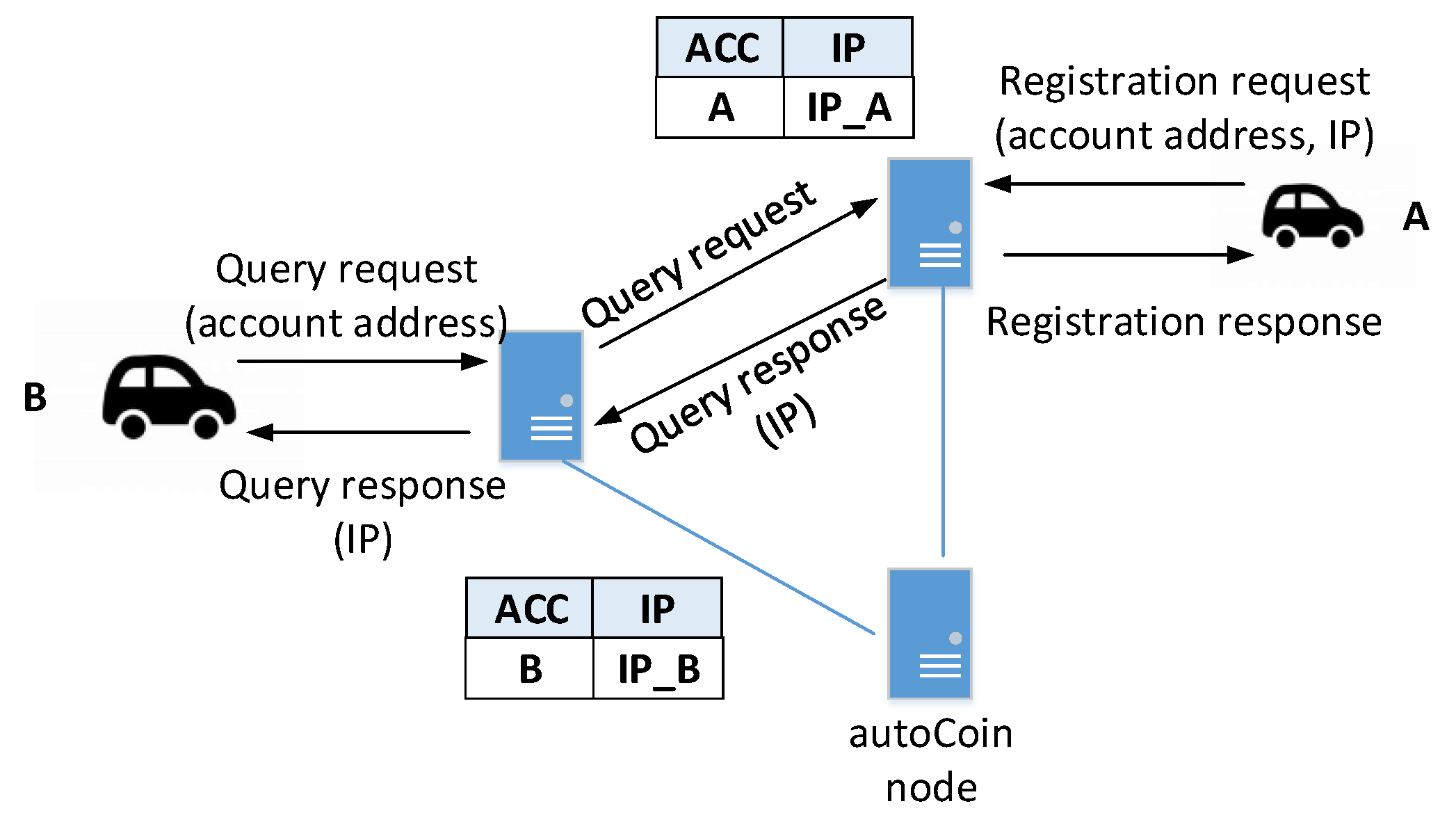
3.3. Bootstrap for Joining a Regional Chain
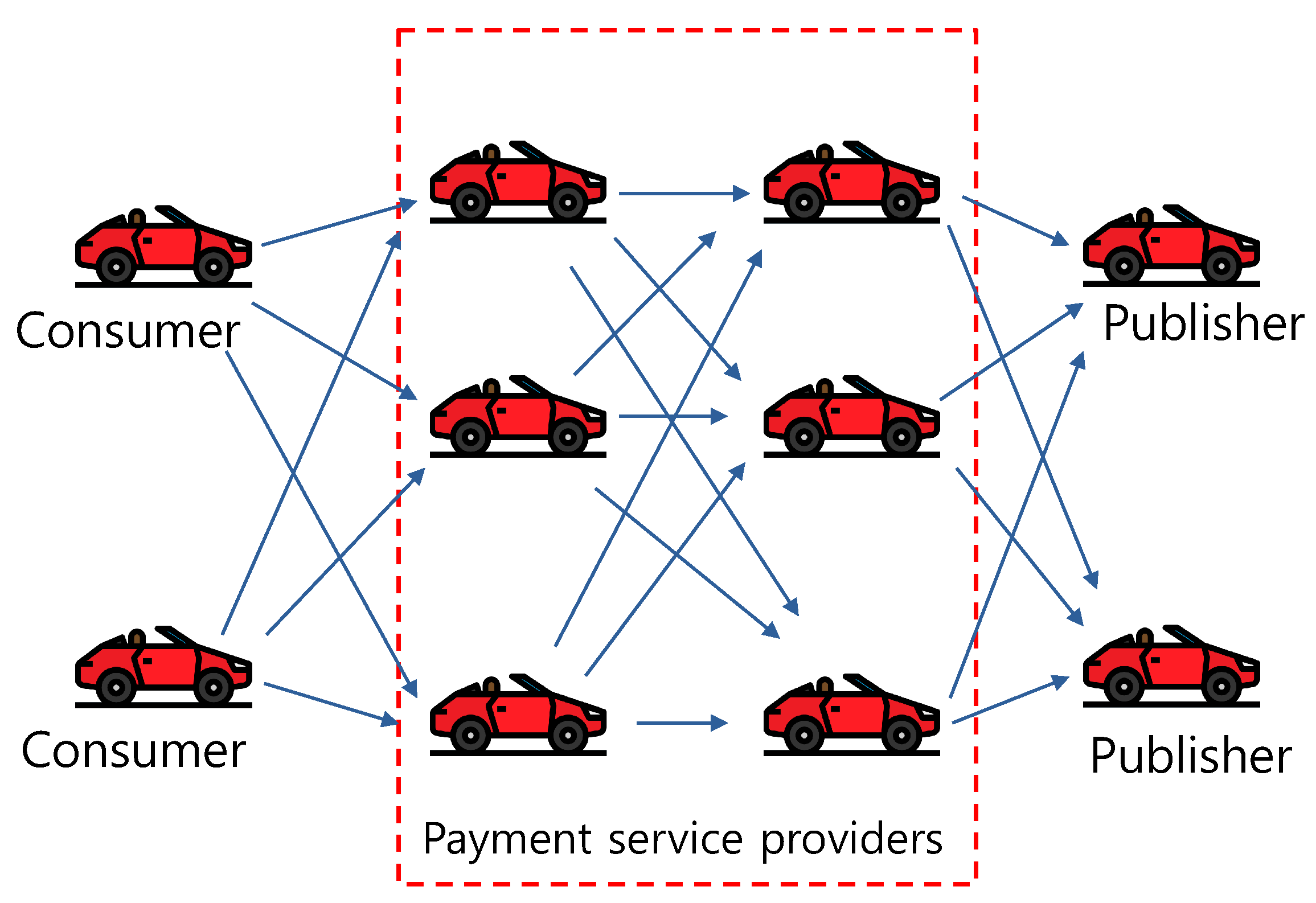
3.4. Content Market Place for Vehicles
- Data integrity: a consumer purchases content based on the meta-data information in the blockchain. Thus, there must be a proof that the received content from a publisher is the same as that noted in the blockchain;
- Data trustworthiness: a publisher can publish content without any verified evidence. For example, a publisher can deploy a video captured at A location with meta-data of location B;
- Trading concurrency: trading without a third party always incurs a risk. Both a publisher and consumer can cheat each other at any step of trading. For instance, a consumer could refuse to pay even though it received data.
3.4.1. Data Integrity
3.4.2. Data Trustworthiness
3.4.3. Trading Concurrency and Completeness
- Reject to pay: a consumer does not pay although it receives data;
- Reject to provide content: a publisher does not send content though it obtains payment first;
- Purchasing capability: a consumer who does not have enough money requests contents;
- Contract destruction: one party leaves in the middle of data transfer (some video data can be more than 1 GB in size).
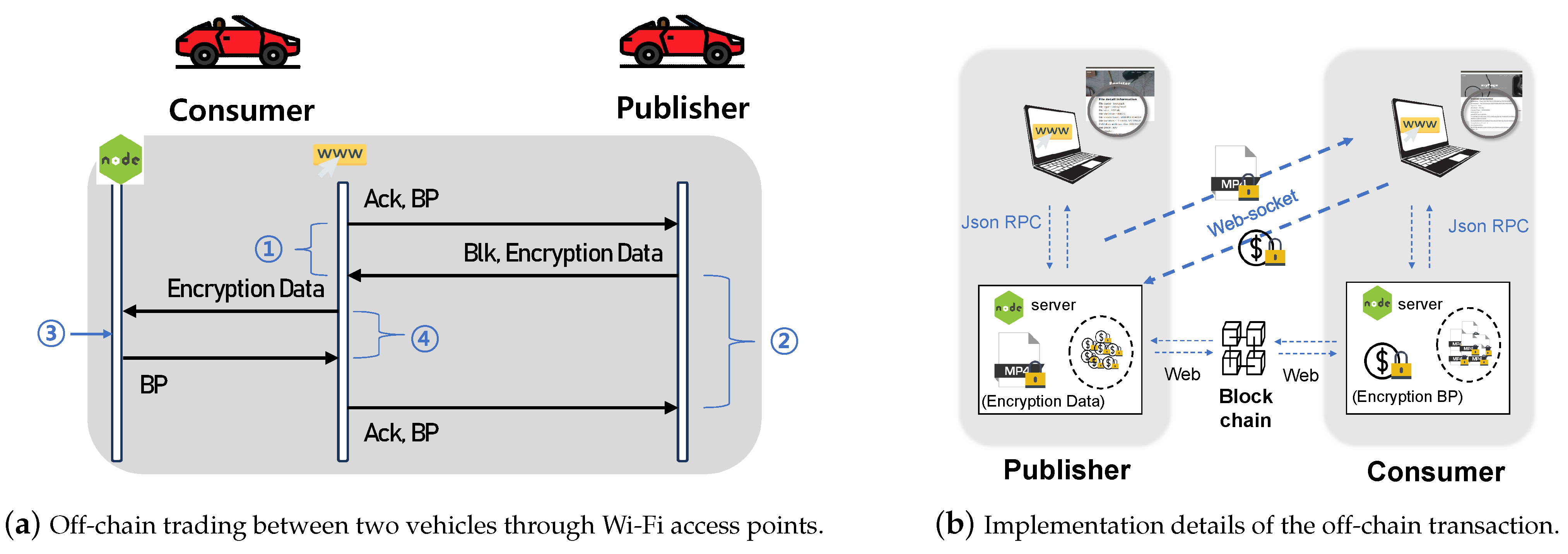
3.5. Off-Chain Content Trading Using Smart Contract
3.6. autoCoin Consensus Algorithm
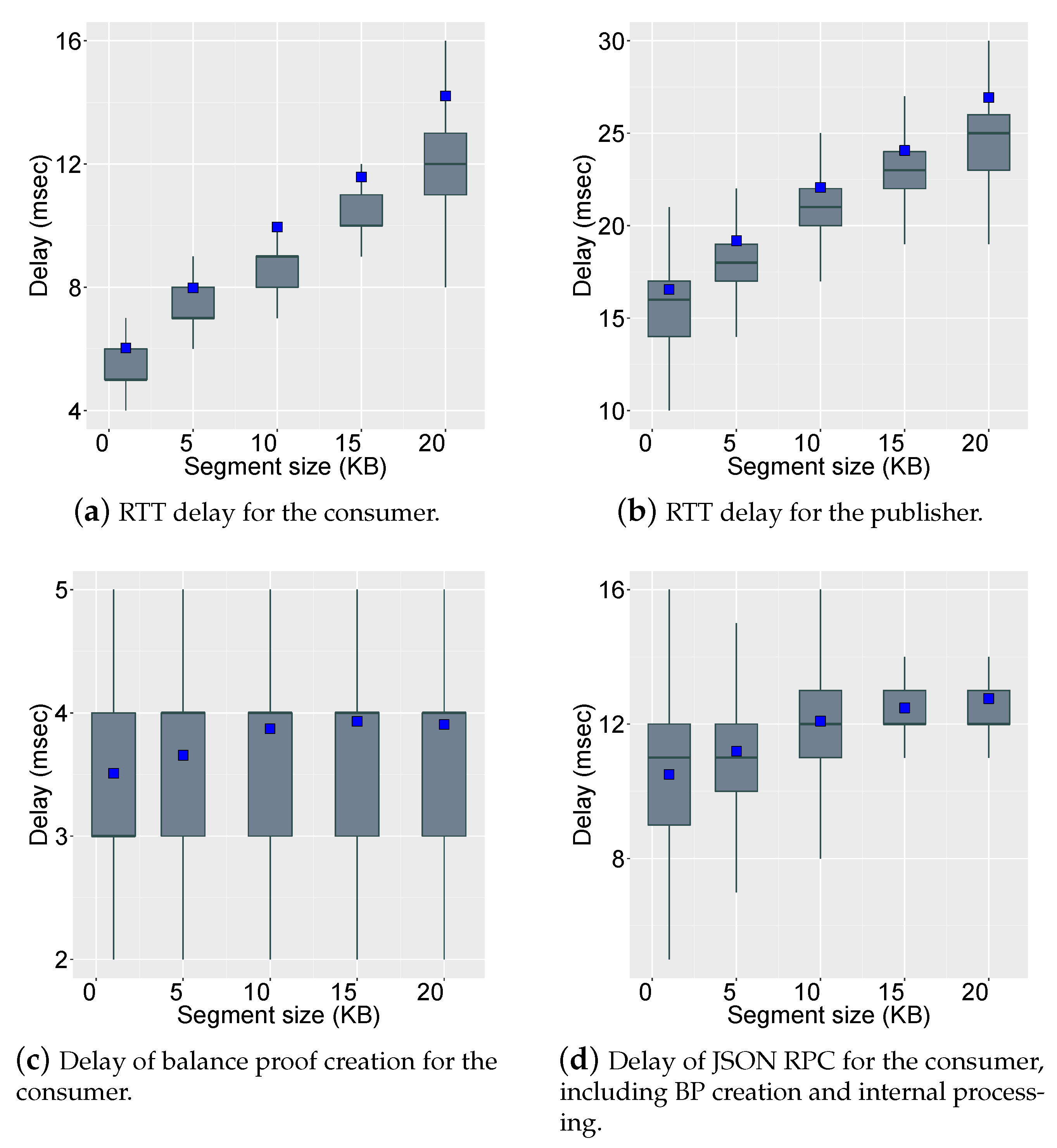
4. autoCoin Implementation and Experiment
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Smart Contract Codes for autoCoin
| //Content MetaData struct struct ItemMetaData { address publisher; uint256 itemPrice; string itemLocation; string itemSize; string itemType; uint256 itemDuration; uint256 itemCreateTime; bytes32 itemHash; bytes32[] cosigners; bool isRegistered; } //Channel struct struct Channel { address publisher; address consumer; uint256 deposit; uint256 duration; uint256 creatTime; uint256 itemSerial; string proofOfEncryption; bytes32 deliveredItemHash; string encryptionKey; uint256 state; bool isRegistered; } |
| //Channel deposit function deposit(address consumer, uint256 value) internal { _balances[consumer] = _balances[consumer].sub(value); ] //Channel complete function complete(address publisher, uint256 value) internal { _balances[publisher] = _balances[publisher].add(value); } |
| //Channel create function createChannel(uint256 _deposit, uint256 _itemSerial) public returns(uint256) { uint256 _channelSerial = channelSerial++; require(registeredItemMetaData[_itemSerial].isRegistered == true); require(registeredItemMetaData[_itemSerial].itemPrice == _deposit); //deposit deposit(msg.sender, _deposit); registeredChannel[_channelSerial].publisher = registeredItemMetaData[_itemSerial].publisher; registeredChannel[_channelSerial].consumer = msg.sender; registeredChannel[_channelSerial].deposit = _deposit; registeredChannel[_channelSerial].duration = duration; registeredChannel[_channelSerial].createTime = now; registeredChannel[_channelSerial].itemSerial = _itemSerial; registeredChannel[_channelSerial].state = 0; registeredChannel[_channelSerial].isRegistered = true; return _channelSerial; } |
| //Channel completion function completeChannel(uint256 _channelSerial, string memory _encryptionKey, bytes32 _balanceProof, uint8 v, bytes32 r, bytes32 s, uint256 _balance) public ongoingChannel(_channelSerial) publisher(_c) { require(comparisonContent(getItemSerial(_channelSerial), registeredChannel[_channelSerial].deliverredItemHash)); //check balance proof require(checkBalanceProof(registeredChannel[_channelSerial].consumer, _balanceProof, v, r, s)); //check balance require(registeredChannel[_channelSerial].deposit == _balance); //deposit token refund complete(msg.sender, registeredChannel[_channelSerial].deposit); registeredChannel[_channelSerial].encryptionKey = _encryptionKey; registeredChannel[_channelSerial].state = 2; } |
References
- Kim, W. Evolutionary Game for Content Cache in a mm-Wave-Based Vehicular Fog. Electronics 2020, 9, 1794. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 18 June 2021).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Sharma, P.K.; Moon, S.Y.; Park, J.H. Block-VN: A distributed blockchain based vehicular network architecture in smart City. J. Inf. Process. Syst. 2017. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C. Blockchain-based decentralized trust management in vehicular networks. IEEE Internet Things J. 2018, 6, 1495–1505. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Zhang, N. LVBS: Lightweight vehicular blockchain for secure data sharing in disaster rescue. IEEE Trans. Dependable Secur. Comput. 2020. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. Data security sharing and storage based on a consortium blockchain in a vehicular ad-hoc network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Li, M.; Zhu, L.; Lin, X. Efficient and privacy-preserving carpooling using blockchain-assisted vehicular fog computing. IEEE Internet Things J. 2018, 6, 4573–4584. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Liang, K. BPAS: Blockchain-assisted privacy-preserving authentication system for vehicular ad hoc networks. IEEE Trans. Ind. Inform. 2019, 16, 4146–4155. [Google Scholar] [CrossRef]
- Li, C.; Fu, Y.; Yu, F.R.; Luan, T.H.; Zhang, Y. Vehicle position correction: A vehicular blockchain networks-based GPS error sharing framework. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Fu, Y.; Yu, F.R.; Li, C.; Luan, T.H.; Zhang, Y. Vehicular blockchain-based collective learning for connected and autonomous vehicles. IEEE Wirel. Commun. 2020, 27, 197–203. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Zhang, K.; Maharjan, S.; Zhang, Y. Deep reinforcement learning and permissioned blockchain for content caching in vehicular edge computing and networks. IEEE Trans. Veh. Technol. 2020, 69, 4312–4324. [Google Scholar] [CrossRef]
- Gerla, M.; Lee, E.K.; Pau, G.; Lee, U. Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 241–246. [Google Scholar]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient adaptive resource management for real-time vehicular cloud services. IEEE Trans. Cloud Comput. 2016, 7, 196–209. [Google Scholar] [CrossRef]
- Zheng, K.; Meng, H.; Chatzimisios, P.; Lei, L.; Shen, X. An SMDP-based resource allocation in vehicular cloud computing systems. IEEE Trans. Ind. Electron. 2015, 62, 7920–7928. [Google Scholar] [CrossRef]
- Yu, R.; Zhang, Y.; Gjessing, S.; Xia, W.; Yang, K. Toward cloud-based vehicular networks with efficient resource management. IEEE Netw. 2013, 27, 48–55. [Google Scholar] [CrossRef]
- Lee, E.; Lee, E.K.; Gerla, M.; Oh, S.Y. Vehicular cloud networking: Architecture and design principles. IEEE Commun. Mag. 2014, 52, 148–155. [Google Scholar] [CrossRef]
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A survey of information-centric networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A survey of information-centric networking research. IEEE Commun. Surv. Tutor. 2013, 16, 1024–1049. [Google Scholar] [CrossRef]
- Zhang, M.; Luo, H.; Zhang, H. A survey of caching mechanisms in information-centric networking. IEEE Commun. Surv. Tutor. 2015, 17, 1473–1499. [Google Scholar] [CrossRef]
- Kim, W. Beyond LTE-advance for information centric networking. Comput. Stand. Interfaces 2017, 49, 59–66. [Google Scholar] [CrossRef]
- Bouk, S.H.; Ahmed, S.H.; Kim, D. Vehicular content centric network (VCCN) a survey and research challenges. In Proceedings of the 30th Annual ACM Symposium on Applied Computing, Salamanca, Spain, 13–17 April 2015; pp. 695–700. [Google Scholar]
- Jacobson, V.; Mosko, M.; Smetters, D.; Garcia-Luna-Aceves, J. Content-Centric Networking; Whitepaper; Palo Alto Research Center: Palo Alto, CA, USA, 2007; pp. 2–4. [Google Scholar]
- Eyal, I.; Sirer, E.G. Majority is not enough: Bitcoin mining is vulnerable. Commun. ACM 2018, 61, 95–102. [Google Scholar] [CrossRef]
- King, S.; Nadal, S. 2021. Available online: https://https://www.peercoin.net/whitepapers/peercoin-paper.pdf (accessed on 18 June 2021).
- Vasin, P. BlackCoin’s Proof-of-Stake Protocol v2. Available online: https://blackcoin.org/blackcoin-pos-protocol-v2-whitepaper.pdf (accessed on 18 June 2021).
- Nxt Wiki. 2021. Available online: https://https://www.jelurida.com/nxt (accessed on 18 June 2021).
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies without proof of work. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 22–26 February 2016; pp. 142–157. [Google Scholar]
- BitShare. Available online: https://how.bitshares.works/en/master/ (accessed on 18 June 2021).
- P4Titan. Slimcoin: A Peer-to-Peer Crypto-Currency with Proof-of-Burn. Available online: https://slimcoin.info/whitepaperSLM.pdf (accessed on 18 June 2021).
- Tendermint. 2021. Available online: https://tendermint.com/ (accessed on 18 June 2021).
- Intel. Sawtooth v1.0.1. 2021. Available online: https://www.hyperledger.org/use/sawtooth (accessed on 18 June 2021).
- Park, S.; Pietrzak, K.; Alwen, J.; Fuchsbauer, G.; Gazi, P. Spacemint: A cryptocurrency based on proofs of space. In International Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 480–499. [Google Scholar]
- BurstCoin. 2021. Available online: https://www.burst-coin.org/ (accessed on 18 June 2021).
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the OSDI, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016; Volume 310. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; p. 30. [Google Scholar]
- Symbiont. 2021. Available online: https://www.symbiont.io/ (accessed on 18 June 2021).
- R3 Corda. 2021. Available online: https://www.corda.net/ (accessed on 18 June 2021).
- Schwartz, D.; Youngs, N.; Britto, A. 2021. Available online: https://ripple.com/files/ripple_consensus_whitepaper.pdf (accessed on 18 June 2021).
- Mazieres, D. The Stellar Consensus Protocol: A Federated Model for Internet-Level Consensus; Stellar Development Foundation: San Francisco, CA, USA, 2015. [Google Scholar]
- Ongaro, D.; Ousterhout, J.K. In search of an understandable consensus algorithm. In Proceedings of the USENIX Annual Technical Conference, Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- De Angelis, S.; Aniello, L.; Baldoni, R.; Lombardi, F.; Margheri, A.; Sassone, V. PBFT vs. proof-of-authority: Applying the CAP theorem to permissioned blockchain. In Proceedings of the Italian Conference on Cyber Security, Milan, Italy, 6–9 February 2018. [Google Scholar]
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Van Renesse, R. Bitcoin-NG: A Scalable Blockchain Protocol. In Proceedings of the NSDI, Santa Clara, CA, USA, 16–18 March 2016; pp. 45–59. [Google Scholar]
- Raiden Network. 2021. Available online: https://raiden.network/ (accessed on 18 June 2021).
- Lightning Network. 2021. Available online: https://lightning.network/ (accessed on 18 June 2021).
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. 2021. Available online: https://lightning.network/lightning-network-paper.pdf (accessed on 18 June 2021).
- Plasma. 2021. Available online: https://plasma.io/plasma-deprecated.pdf (accessed on 18 June 2021).
- Herrera-Joancomartí, J.; Pérez-Solà, C. Privacy in bitcoin transactions: New challenges from blockchain scalability solutions. In Proceedings of the Modeling Decisions for Artificial Intelligence, Sant Julià de Lòria, Andorra, 19–21 September 2016; pp. 26–44. [Google Scholar]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A secure sharding protocol for open blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 17–30. [Google Scholar]
- Danezis, G.; Meiklejohn, S. Centrally banked cryptocurrencies. arXiv 2015, arXiv:1505.06895. [Google Scholar]
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. Omniledger: A secure, scale-out, decentralized ledger via sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–23 May 2018; pp. 583–598. [Google Scholar]
- Zamani, M.; Movahedi, M.; Raykova, M. RapidChain: Scaling blockchain via full sharding. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–18 October 2018; pp. 931–948. [Google Scholar]
- Ratnasamy, S.; Karp, B.; Yin, L.; Yu, F.; Estrin, D.; Govindan, R.; Shenker, S. GHT: A geographic hash table for data-centric storage. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, Atlanta, GA, USA, 28 September 2002; pp. 78–87. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 3–16. [Google Scholar]
- Sompolinsky, Y.; Zohar, A. Secure high-rate transaction processing in bitcoin. In Proceedings of the International Conference on Financial Cryptography and Data Security, San Juan, Puerto Rico, 26–30 January 2015; pp. 507–527. [Google Scholar]
- Decker, C.; Wattenhofer, R. Information propagation in the bitcoin network. In Proceedings of the IEEE P2P 2013 Proceedings, Trento, Italy, 9–11 September 2013; pp. 1–10. [Google Scholar]
- Cohen, B. Incentives build robustness in BitTorrent. In Proceedings of the Workshop on Economics of Peer-to-Peer systems, Berkeley, CA, USA, 21–22 February 2003; Volume 6, pp. 68–72. [Google Scholar]
- Kaashoek, M.F.; Karger, D.R. Koorde: A simple degree-optimal distributed hash table. In Proceedings of the International Workshop on Peer-to-Peer Systems, Berkeley, CA, USA, 21–22 February 2003; pp. 98–107. [Google Scholar]
- Kim, M.; Lim, J.; Yu, H.; Kim, K.; Kim, Y.; Lee, S.B. ViewMap: Sharing private in-vehicle dashcam videos. In Proceedings of the14th USENIX Symposium on Networked Systems Design and Implementation (NSDI 17), Boston, MA, USA, 27–29 March 2017; pp. 163–176. [Google Scholar]
- Dannen, C. Introducing Ethereum and Solidity; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Koponen, T.; Chawla, M.; Chun, B.G.; Ermolinskiy, A.; Kim, K.H.; Shenker, S.; Stoica, I. A data-oriented (and beyond) network architecture. In Proceedings of the 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Kyoto, Japan, 27–31 August 2007; pp. 181–192. [Google Scholar]







| Symbol | Description | Information |
|---|---|---|
| E | Encryption, ciphering | AES 256 |
| D | Decryption, deciphering | AES 256 |
| H | Hash | SHA 256 |
| Public key | ECDSA | |
| Private key | ECDSA | |
| Message/session key | Temporal ciphering key | |
| Publisher key | Private or public key | |
| Consumer key | Private or public key | |
| M | Message/data | Video |
| X | Ciphered or hashed message/data | Video |
| Split Size | 1 | 5 | 10 | 15 | 20 |
|---|---|---|---|---|---|
| Min | 2 | 4 | 4 | 4 | 6 |
| 1st Q | 5 | 7 | 8 | 10 | 11 |
| Median | 5 | 7 | 9 | 10 | 12 |
| Mean | 6.032 | 7.981 | 9.955 | 11.58 | 14.21 |
| 3rd Q | 6 | 8 | 9 | 11 | 13 |
| Max | 316 | 426 | 432 | 431 | 516 |
| Split Size | 1 | 5 | 10 | 15 | 20 |
|---|---|---|---|---|---|
| Min | 6 | 8 | 9 | 12 | 11 |
| 1st Q | 14 | 17 | 20 | 22 | 23 |
| Median | 16 | 18 | 21 | 23 | 25 |
| Mean | 16.55 | 19.18 | 22.06 | 24.07 | 26.93 |
| 3rd Q | 17 | 19 | 22 | 24 | 26 |
| Max | 314 | 378 | 338 | 415 | 604 |
| Split Size | 1 | 5 | 10 | 15 | 20 |
|---|---|---|---|---|---|
| Min | 1 | 1 | 1 | 1 | 1 |
| 1st Q | 3 | 3 | 3 | 3 | 3 |
| Median | 3 | 4 | 4 | 4 | 4 |
| Mean | 3.51 | 3.656 | 3.872 | 3.931 | 3.906 |
| 3rd Q | 4. | 4 | 4 | 4 | 4 |
| Max | 24 | 23 | 19 | 26 | 19 |
| Split Size | 1 | 5 | 10 | 15 | 20 |
|---|---|---|---|---|---|
| Min | 3 | 2 | 3 | 2 | 3 |
| 1st Q | 9 | 10 | 11 | 12 | 12 |
| Median | 11 | 11 | 12 | 12 | 12 |
| Mean | 10.5 | 11.19 | 12.09 | 12.48 | 12.76 |
| 3rd Q | 12 | 12 | 13 | 13 | 13 |
| Max | 66 | 250 | 70 | 93 | 99 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, W.; Ryu, K. autoCoin: Secure Content Sharing Based on Blockchain for Vehicular Cloud. Electronics 2021, 10, 1477. https://doi.org/10.3390/electronics10121477
Kim W, Ryu K. autoCoin: Secure Content Sharing Based on Blockchain for Vehicular Cloud. Electronics. 2021; 10(12):1477. https://doi.org/10.3390/electronics10121477
Chicago/Turabian StyleKim, Wooseong, and Kyungho Ryu. 2021. "autoCoin: Secure Content Sharing Based on Blockchain for Vehicular Cloud" Electronics 10, no. 12: 1477. https://doi.org/10.3390/electronics10121477
APA StyleKim, W., & Ryu, K. (2021). autoCoin: Secure Content Sharing Based on Blockchain for Vehicular Cloud. Electronics, 10(12), 1477. https://doi.org/10.3390/electronics10121477






