Lightweight Failover Authentication Mechanism for IoT-Based Fog Computing Environment
Abstract
1. Introduction
1.1. Motivation
1.2. Research Contributions
- We present the architecture and threat model for the envisioned failover authentication model.
- We define the proposed failover authentication model in detail with all its phases.
- We present a detailed security analysis with both formal and informal security analysis, and also a formal security verification using the AVISPA software validation tool to prove the robustness of the proposed scheme against various known attacks.
- A testbed experiment for measuring computational time for different cryptographic primitives using the MIRACL library has been provided.
- Finally, through a detailed comparative study, we showcase the unique advantages of the proposed scheme.
1.3. Paper Outline
2. Related Work
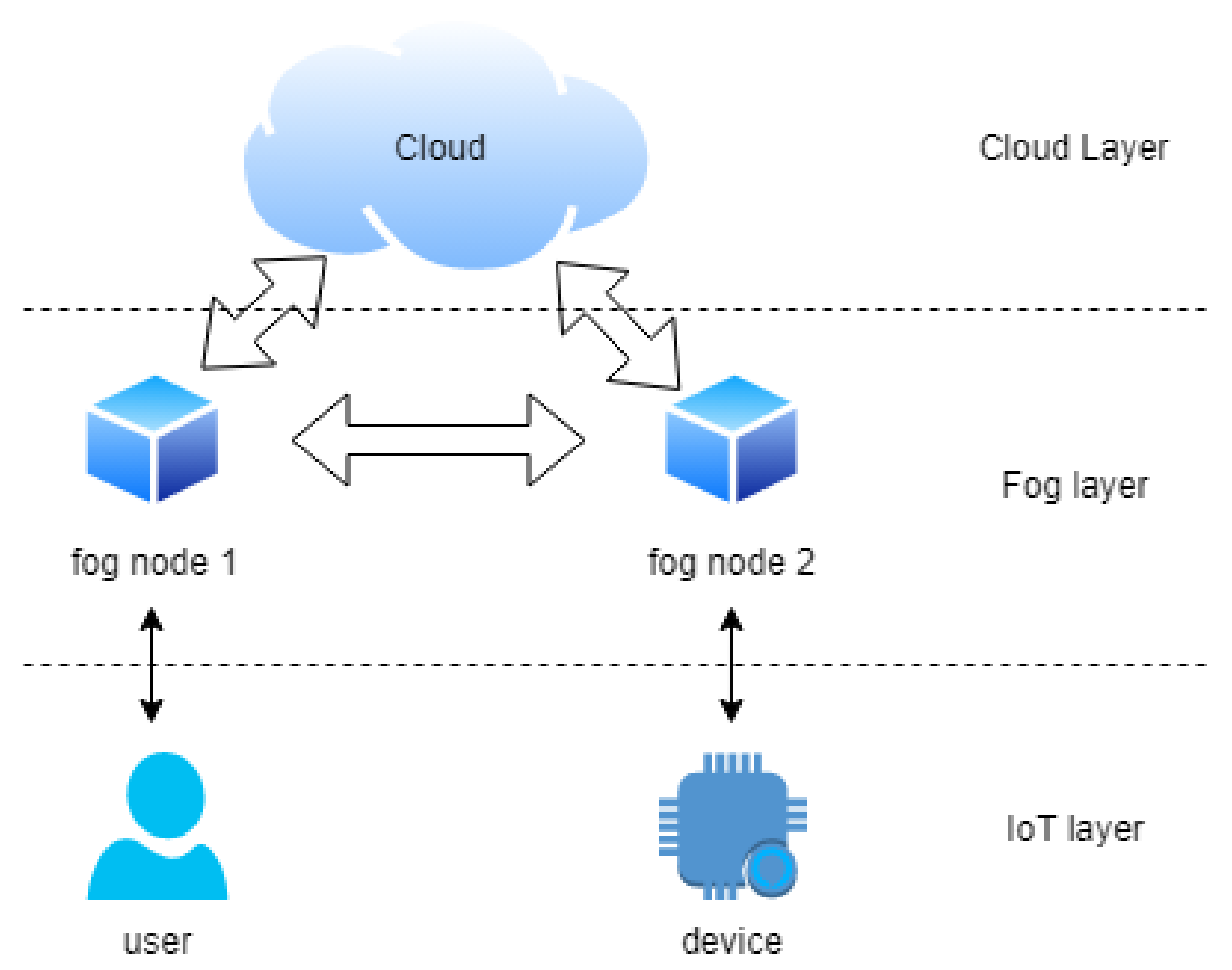
3. System Models
3.1. Network Model
3.2. Threat Model
4. Proposed Failover Authentication Scheme
4.1. Setup Phase
4.2. Fog Node Enrollment Phase
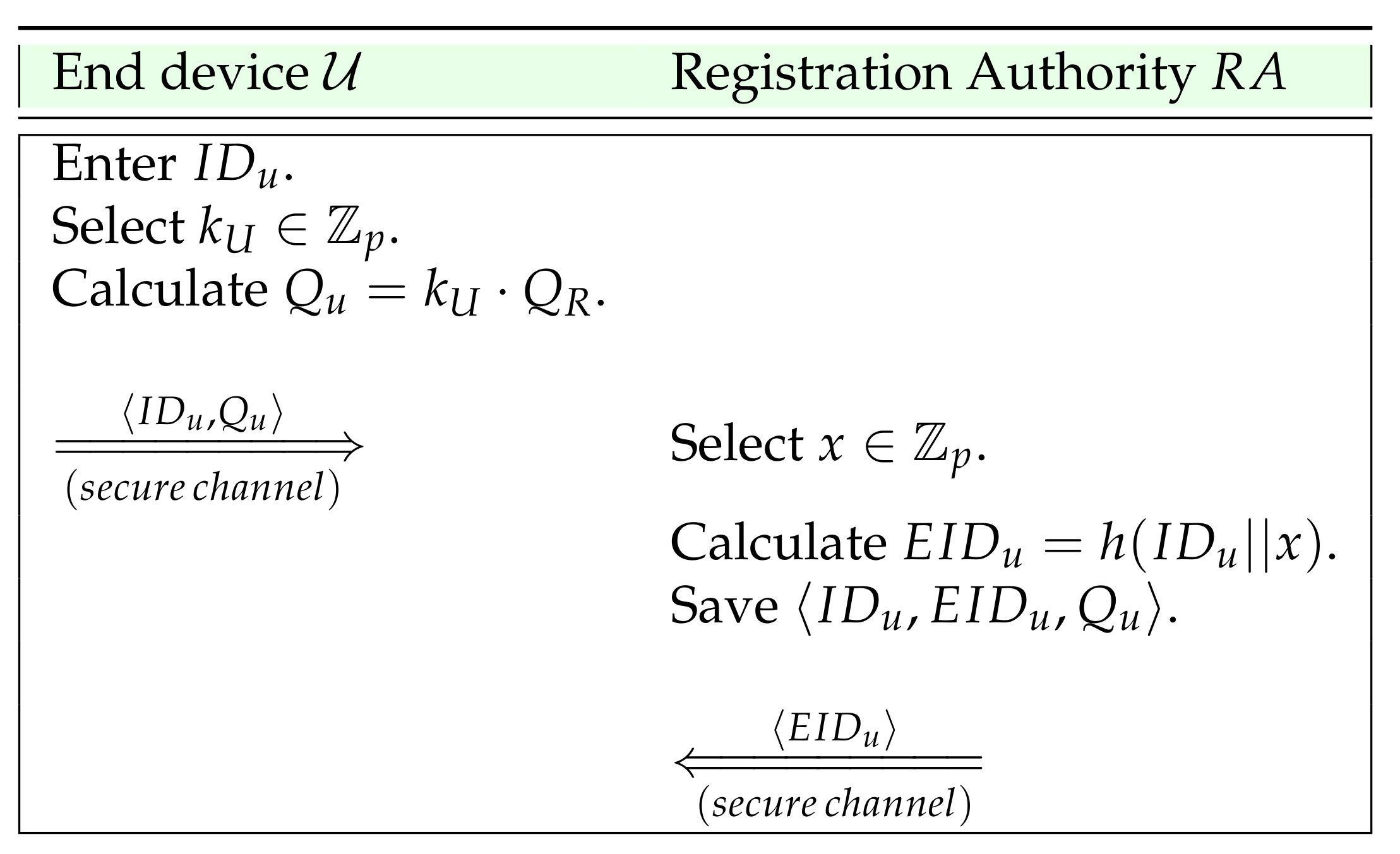
4.3. End Device Registration
- The end device provides its identity (user’s identity or otherwise), and selects as its private key. Then it computes its public key and securely transmits to the .
- On receiving the registration request, selects a and computes the obscured end-device identity . securely transmits to the end device saves .
- The credentials in the end device can be secured with multi-factor authentication, which is beyond the scope of the scheme.
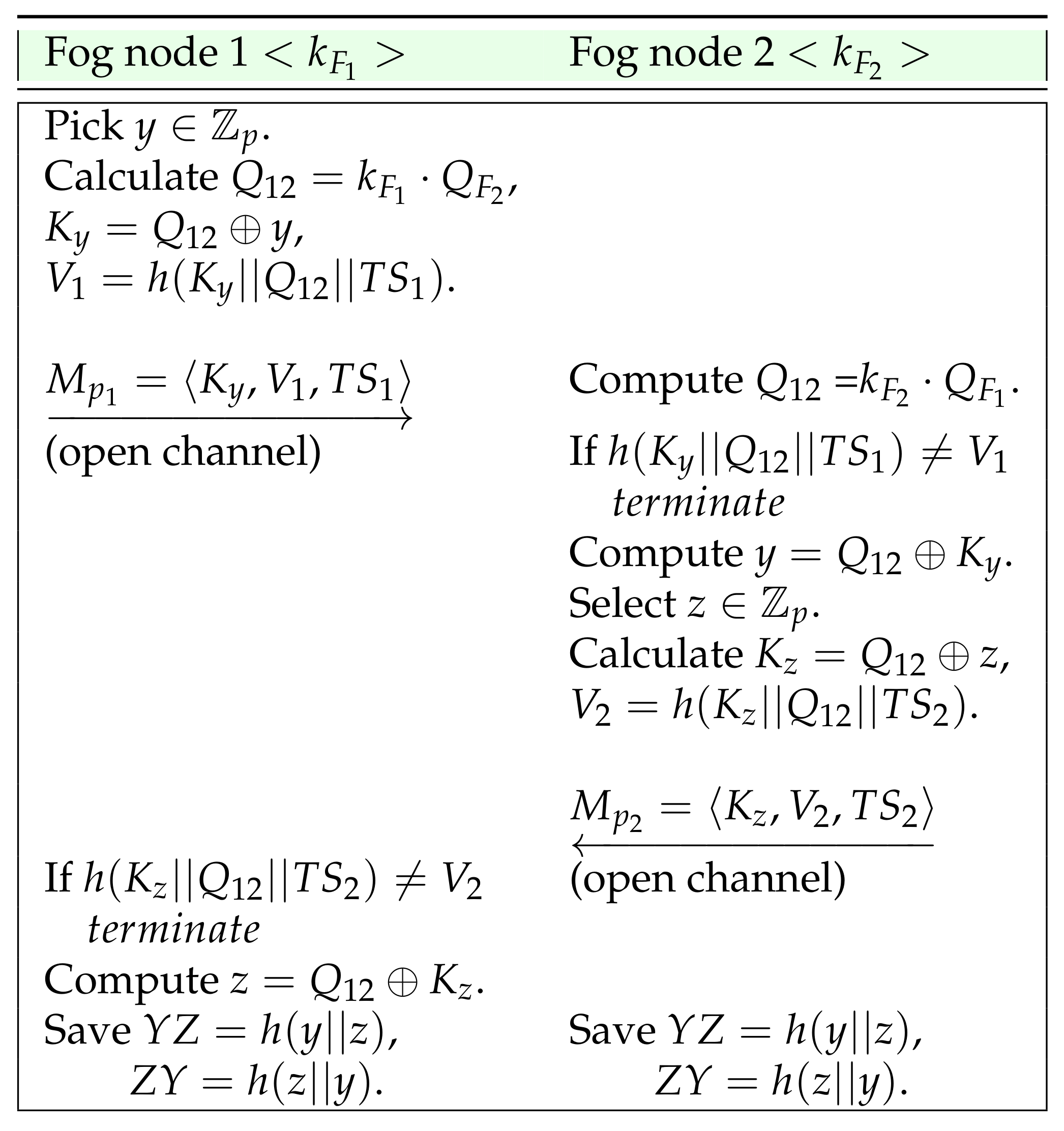
4.4. Inter-Fog Node Pre-Agreement
- Fog node 1 selects a random secret and computes . Additionally, it calculates , sets as the current timestamp and then computes in order to transmit a message to Fog node 2 via open channel.
- On receiving the message , Fog node 2 computes and verifies if is equal to . Only if the verification holds, it proceeds ahead. It then recovers , selects a random secret and computes . It also sets as the current timestamp, computes and transmits the message to Fog node 1 via an open channel. Moreover, it computes the security tokens and .
- On receiving the message , Fog node 1 verifies if is equal to . If it is valid, it recovers , and computes the security tokens and .
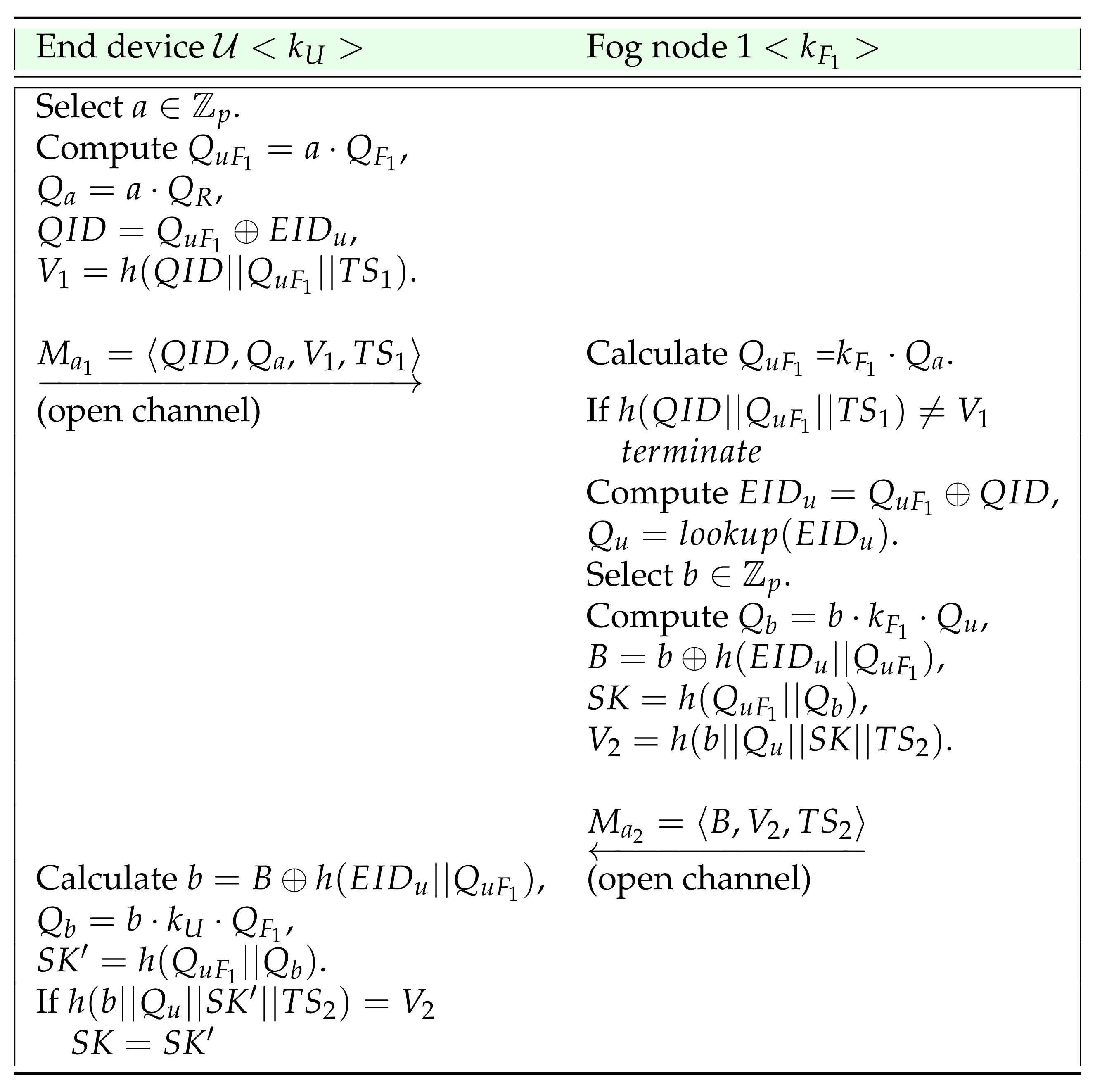
4.5. Initial Authentication
- The end device selects a random secret and computes , and . Additionally, it sets as the current timestamp, computes and transmits a message to Fog node 1 over an insecure channel.
- On receiving the message , the Fog node 1 computes and verifies if is equal to . Only if the check holds, it proceeds ahead. It then recovers , looks up from , selects another random secret , and also computes , and . Moreover, it sets as the current timestamp, computes and transmits the message back to via an open channel.
- On receiving the message , computes , and . If is equal to , sets
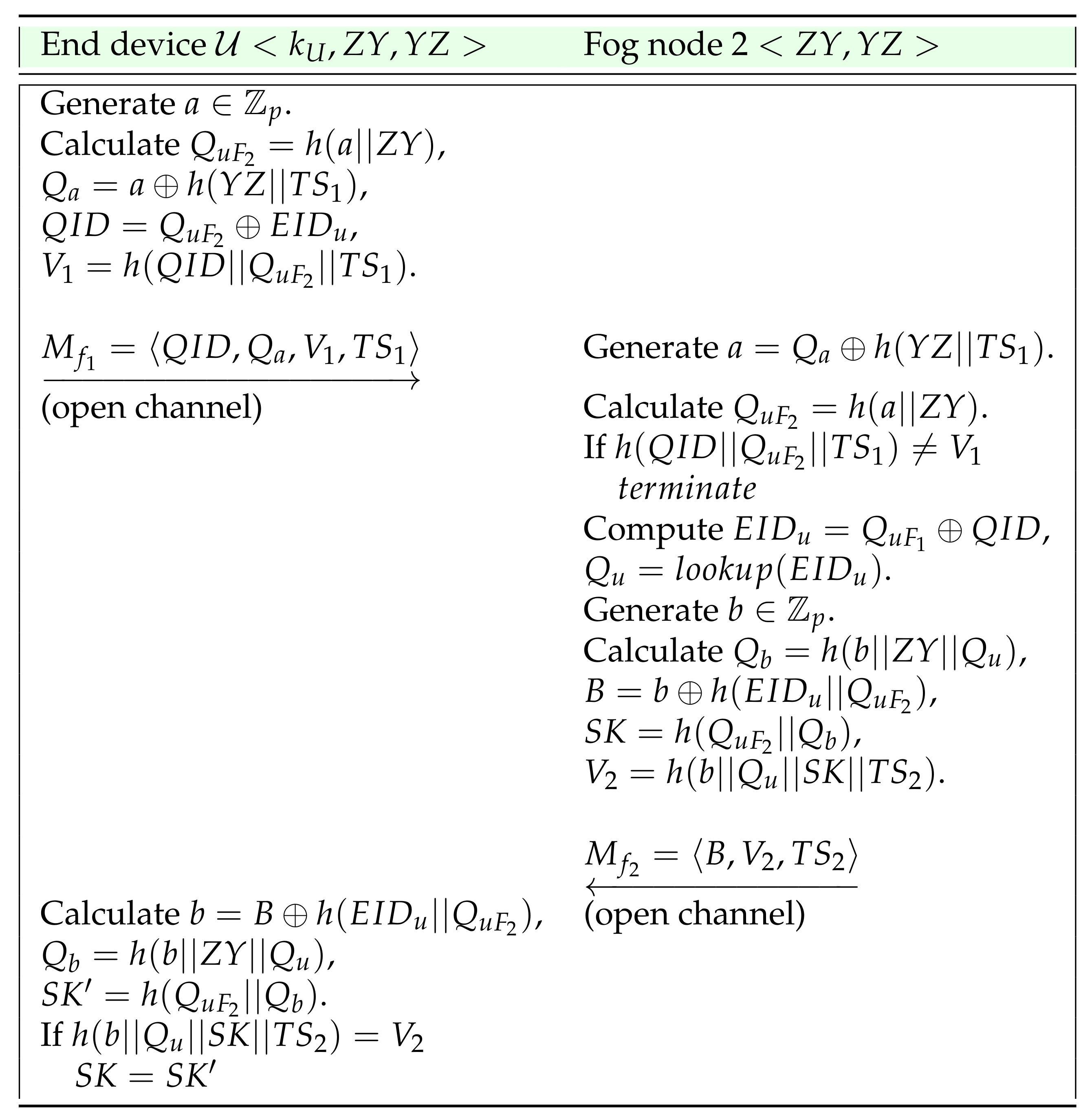
4.6. Fast Authentication
- The end device selects a random secret and computes , , and , where is the current timestamp. It then computes and transmits a message to Fog node 1 via a public channel.
- On receiving the message , the Fog node 2 computes , recovers and verifies if is equal to . Only if the check holds, it proceeds ahead. It recovers , looks up from , selects a random secret and computes , and , where is the current timestamp. Moreover, it computes and transmits the message back to via a public channel.
- On receiving the message , recovers , and computes and . If is equal to , sets the session key shared with the Fog node 2 ass .
5. Security Analysis
5.1. Formal Security Analysis Using ROR Model
- : By this query, which models an eavesdropping attack, can intercept all the transmitted messages among , and .
- : This query models an as an active attack and enables to send a message, say to its participating instance , and also to receive a response in reply.
- : This query utilizes the indistinguishability in the ROR model [40] to determine the semantic security of the session key established between and . TO begin with, performs an unbiased coin toss c. Its outcome decides the result of the query. If is fresh, or produces upon the satisfaction of the condition or a random number for the fulfillment of the condition . Otherwise, it returns a null value.
- : Through this query, can learn the session key between and or between and .
- Game: This game models an actual (real) attack on the proposed scheme, by . Thus, the bit c is guessed at the beginning of . Therefore, the semantic security of the proposed scheme defined in Definition 1, it follows that
- Game: This game models an eavesdropping attack, where can query oracle to intercept the messages , , , and during the initial and fast authentication processes. Afterwards, can also query oracle and determine if the result is the actual session key or just simply a random number. Note that in the proposed scheme, is the session key established between an end device and fog node during the initial authentication, and also is the established session key between a user and a fog node during the fast authentication. In both cases, to compute , must know the short term secrets (a and b) as well as long term secrets (, and ) simultaneously. Thus, only the intended user and fog nodes and can compute . Therefore, ’s probability of wining the game is not increased form through an eavesdropping attack. Consequently, both the games and are indistinguishable, and we have the following result:
- Game: Under this game, the and hash queries are simulated. This game is modeled as an active attack, where can attempt to fool a legitimate participant into accepting a modified message. is permitted to make repeated queries to the random oracles to examine the presence of hash collisions. However, since all the messages , , and contain unique single use values, hash coalition does not occur (see Definition 2) when queries the oracle with the help of . Moreover, to derive the session key is the session key established between an end device and fog node during the initial authentication, the adversary needs to solve the computational ECDDHP defined in Definition 2. It is worth noticing that both the games and are “indistinguishable” except the and hash queries are simulated in along with solving ECDDHP. Thus, by using the birthday paradox results and the advantage of in solving ECDDHP, we have,Finally, to win the game , needs to guess bit after querying the oracle. Thus, it is clear thatFrom Equations (1)–(4), we haveBy solving Equation (5), we obtain the required result:□
5.2. Informal Security Analysis
5.2.1. Mutual Authentication
5.2.2. Anonymity and Untraceability
5.2.3. Forward and Backward Secrecy
5.2.4. Ephemeral Secret Leakage (ESL) Attack
5.2.5. Impersonation Attacks
5.2.6. Clogging Attacks
6. Formal Security Verification through AVISPA Simulation
6.1. Specifying the Roles
6.2. Simulation Results and Discussion
7. Testbed Experiments Using MIRACL
- Platform 1: This platform corresponds to a server setting under the environment: “Ubuntu 18.04.4 LTS, with 7.7 GiB memory, Intel Core i7 processor- 8565U, CPU @ 1.80GHz × 8, 64-bit OS type and disk size 966.1 GB”. The experimental results for different primitives are then measured using MIRACL library and then provided in Table 2. Note that under this platform, milliseconds by considering average time. In addition, it is assumed that [53].
- Platform 2: In this platform, we measured the execution time for cryptographic primitives by MIRACL for the smart device side under the Raspberry PI 3 setting. The system configuration is considered as follows: “Raspberry PI 3 B+ Rev 1.3, Ubuntu 20.04 LTS, 64- bit OS, 1.4 GHz Quad-core processor, cores 4, 1 GB RAM” [54]. In Table 3, we have tabulated the experimental results of different cryptographic primitives. Note that under this platform, milliseconds by considering average time.
8. Comparative Study
- Case 1: It denotes the “fog node pre-agreement” phase
- Case 2: It corresponds to the “initial authentication” phase
- Case 3: It represents the “fast authentication” phase
- LAAP1: It is for the “initial authentication protocol for device-to-device (D2D)-aided fog computing”
- LAAP2: It denotes the “subsequent authentication protocol with the co-operation of EDs in D2D-aided fog computing”
- LAAP3: It corresponds to the “subsequent authentication protocol with the co-operation of NADs in D2D-aided fog computing”
8.1. Computation Costs Comparison
8.2. Communication Costs Comparison
8.3. Security and Functionality Features Comparison
9. Concluding Remarks and Future Works
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Das, A.K.; Zeadally, S.; He, D. Taxonomy and analysis of security protocols for Internet of Things. Future Gener. Comput. Syst. 2018, 89, 110–125. [Google Scholar] [CrossRef]
- Zeadally, S.; Das, A.K.; Sklavos, N. Cryptographic technologies and protocol standards for Internet of Things. Internet Things 2019, 14, 100075. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Dizdarević, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A Survey of Communication Protocols for Internet of Things and Related Challenges of Fog and Cloud Computing Integration. ACM Comput. Surv. 2019, 51, 1–29. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.; Ghosh, S.; Buyya, R. Chapter 4—Fog Computing: Principles, architectures, and applications. In Internet of Things; Buyya, R., Vahid Dastjerdi, A., Eds.; Morgan Kaufmann: San Francisco, CA, USA, 2016; pp. 61–75. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Bhat, K.V.; Vasilakos, A.V. LAM-CIoT: Lightweight authentication mechanism in cloud-based IoT environment. J. Netw. Comput. Appl. 2020, 150, 102496. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. On the Design of Provably Secure Lightweight Remote User Authentication Scheme for Mobile Cloud Computing Services. IEEE Access 2017, 5, 25808–25825. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. SEAP: Secure and efficient authentication protocol for NFC applications using pseudonyms. IEEE Trans. Consum. Electron. 2016, 62, 30–38. [Google Scholar] [CrossRef]
- Chatterjee, S.; Das, A.; Sing, J. An Enhanced Access Control Scheme in Wireless Sensor Networks. Ad-Hoc Sens. Wirel. Netw. 2014, 21, 121–149. [Google Scholar]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure and efficient ECC-based user anonymity-preserving session initiation authentication protocol using smart card. Peer- Netw. Appl. 2016, 9, 171–192. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Gope, P.; Kumar, N.; Wu, F.; Vasilakos, A.V. Design and analysis of authenticated key agreement scheme in cloud-assisted cyber–physical systems. Future Gener. Comput. Syst. 2020, 108, 1267–1286. [Google Scholar] [CrossRef]
- Das, A.K.; Sutrala, A.K.; Kumari, S.; Odelu, V.; Wazid, M.; Li, X. An efficient multi-gateway-based three-factor user authentication and key agreement scheme in hierarchical wireless sensor networks. Secur. Commun. Netw. 2016, 9, 2070–2092. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Choo, K.R.; Vinel, A.; Huang, X. Security and Privacy for the Internet of Drones: Challenges and Solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Khan, M.K.; Al-Ghaiheb, A.A.; Kumar, N.; Vasilakos, A.V. Secure Authentication Scheme for Medicine Anti-Counterfeiting System in IoT Environment. IEEE Internet Things J. 2017, 4, 1634–1646. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated Key Management Protocol in Fog Computing-Based Internet of Vehicles Deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous Lightweight Chaotic Map-Based Authenticated Key Agreement Protocol for Industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2020, 17, 1133–1146. [Google Scholar] [CrossRef]
- Bera, B.; Das, A.K.; Sutrala, A.K. Private blockchain-based access control mechanism for unauthorized UAV detection and mitigation in Internet of Drones environment. Comput. Commun. 2021, 166, 91–109. [Google Scholar] [CrossRef]
- Li, C.; Lee, C.; Weng, C. Security and Efficiency Enhancement of Robust ID Based Mutual Authentication and Key Agreement Scheme Preserving User Anonymity in Mobile Networks. J. Inf. Sci. Eng. 2018, 34, 155–170. [Google Scholar]
- Bera, B.; Saha, S.; Das, A.K.; Kumar, N.; Lorenz, P.; Alazab, M. Blockchain-Envisioned Secure Data Delivery and Collection Scheme for 5G-Based IoT-Enabled Internet of Drones Environment. IEEE Trans. Veh. Technol. 2020. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal Credential-Based Anonymous Lightweight Authentication Scheme for Internet of Drones Environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified Biometric Privacy Preserving Three-Factor Authentication and Key Agreement for Cloud-Assisted Autonomous Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Lee, J.H. Authentication protocols for the internet of drones: Taxonomy, analysis and future directions. J. Ambient. Intell. Humaniz. Comput. 2018. [Google Scholar] [CrossRef]
- Li, C.T.; Chen, C.L.; Lee, C.C.; Weng, C.Y.; Chen, C.M. A novel three-party password-based authenticated key exchange protocol with user anonymity based on chaotic maps. Soft Comput. 2018, 22, 2495–2506. [Google Scholar] [CrossRef]
- Wazid, M.; Bera, B.; Mitra, A.; Das, A.K.; Ali, R. Private Blockchain-Envisioned Security Framework for AI-Enabled IoT-Based Drone-Aided Healthcare Services. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and Beyond (DroneCom’20), London, UK, 25 September 2020; pp. 37–42. [Google Scholar]
- Bera, B.; Das, A.K.; Garg, S.; Piran, M.J.; Hossain, M.S. Access Control Protocol for Battlefield Surveillance in Drone-Assisted IoT Environment. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Gope, P. LAAP: Lightweight anonymous authentication protocol for D2D-Aided fog computing paradigm. Comput. Secur. 2019, 86, 223–237. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; pp. 453–474. [Google Scholar]
- Concone, F.; Re, G.L.; Morana, M. SMCP: A Secure Mobile Crowdsensing Protocol for fog-based applications. Hum.-Centric Comput. Inf. Sci. 2020, 10, 1–23. [Google Scholar] [CrossRef]
- Basudan, S.; Lin, X.; Sankaranarayanan, K. A Privacy-Preserving Vehicular Crowdsensing-Based Road Surface Condition Monitoring System Using Fog Computing. IEEE Internet Things J. 2017, 4, 772–782. [Google Scholar] [CrossRef]
- Cui, M.; Han, D.; Wang, J. An efficient and safe road condition monitoring authentication scheme based on fog computing. IEEE Internet Things J. 2019, 6, 9076–9084. [Google Scholar] [CrossRef]
- Guo, Y.; Zhang, Z.; Guo, Y. Fog-Centric Authenticated Key Agreement Scheme Without Trusted Parties. IEEE Syst. J. 2020, 2020, 1–10. [Google Scholar] [CrossRef]
- Ali, Z.; Chaudhry, S.A.; Mahmood, K.; Garg, S.; Lv, Z.; Zikria, Y.B. A clogging resistant secure authentication scheme for fog computing services. Comput. Netw. 2020, 185, 107731. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- May, W.E. Secure Hash Standard. 2015. Available online: http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.180-4.pdf (accessed on 10 February 2021).
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Lecture Notes in Computer Science (LNCS), Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84. [Google Scholar]
- AVISPA. Automated Validation of Internet Security Protocols and Applications. 2021. Available online: http://www.avispa-project.org/ (accessed on 10 January 2021).
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment. IEEE Trans. Dependable Secur. Comput. 2020, 17, 391–406. [Google Scholar] [CrossRef]
- Chang, C.C.; Le, H.D. A provably secure, efficient, and flexible authentication scheme for ad hoc wireless sensor networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Sarkar, P. A Simple and Generic Construction of Authenticated Encryption with Associated Data. ACM Trans. Inf. Syst. Secur. 2010, 13, 33. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.; Park, Y. Physically secure lightweight anonymous user authentication protocol for internet of things using physically unclonable functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]
- Banerjee, S.; Roy, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.; Park, Y. Multi-Authority CP-ABE-Based user access control scheme with constant-size key and ciphertext for IoT deployment. J. Inf. Secur. Appl. 2020, 53, 102503. [Google Scholar] [CrossRef]
- von Oheimb, D. The high-level protocol specification language hlpsl developed in the eu project avispa. In Proceedings of the 3rd APPSEM II (Applied Semantics II) Workshop (APPSEM’05), Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- AVISPA. SPAN, the Security Protocol ANimator for AVISPA. 2021. Available online: http://www.avispa-project.org/ (accessed on 10 January 2021).
- MIRACL Cryptographic SDK: Multiprecision Integer and Rational Arithmetic Cryptographic Library. 2020. Available online: https://github.com/miracl/MIRACL (accessed on 10 March 2021).
- Advanced Encryption Standard (AES), 2001. FIPS PUB 197, National Institute of Standards and Technology (NIST), U.S. Department of Commerce, November 2001. Available online: http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf (accessed on 10 February 2021).
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. SIAM J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef]
- Knuth, D.E. The Art of Computer Programming: Seminumerical Algorithms, 3rd ed.; Addison-Wesley Longman Publishing Co., Inc.: Boston, MA, USA, 1997; Volume 2. [Google Scholar]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Raspberry Pi 3 Model B+. 2020. Available online: https://www.raspberrypi.org/products/raspberry-pi-3-model-b-plus/ (accessed on 10 May 2021).






| Symbol | Description |
|---|---|
| A fully-trusted registration authority | |
| An end device | |
| A semi-trusted fog node | |
| p | A sufficiently large prime number (i.e., 160-bit number) |
| A finite (prime) field, | |
| A non-singular elliptic curve over a prime finite field | |
| Public and private key and identity of entity x, respectively | |
| Pre-shared security token for fast authentication | |
| Collision-resistant cryptographic one-way hash function | |
| Concatenation and bitwise XOR operations, respectively | |
| A passive or an active adversary | |
| ⇒ | A secure channel |
| → | A public (insecure) channel |
| Primitive | Max. Time (ms) | Min. Time (ms) | Average Time (ms) |
|---|---|---|---|
| 0.149 | 0.024 | 0.055 | |
| 0.008 | 0.002 | 0.003 | |
| 0.005 | 0.002 | 0.003 | |
| 0.035 | 0.002 | 0.004 | |
| 0.004 | 0.001 | 0.002 | |
| 2.998 | 0.284 | 0.674 | |
| 0.002 | 0.001 | 0.002 |
| Primitive | Max. Time (ms) | Min. Time (ms) | Average Time (ms) |
|---|---|---|---|
| 0.643 | 0.274 | 0.309 | |
| 0.038 | 0.017 | 0.018 | |
| 0.054 | 0.009 | 0.014 | |
| 0.016 | 0.009 | 0.011 | |
| 0.013 | 0.008 | 0.010 | |
| 4.532 | 2.206 | 2.288 | |
| 0.021 | 0.015 | 0.016 |
| Scheme | Cost at ED | Cost at Fog Node (NAD) | Cost at Cloud Server (CCS) |
|---|---|---|---|
| Proposed (Case 1) | − | − | |
| ms | |||
| Proposed (Case 2) | − | ||
| ms | ms | ||
| Proposed (Case 3) | − | ||
| ms | ms | ||
| Gope [30] (LAAP1) | |||
| ms | ms | ms | |
| Gope [30] (LAAP2) | − | ||
| ms | ms | ||
| Gope [30] (LAAP3) | − | ||
| ms | ms | ||
| Guo et al. [35] | − | ||
| ms | ms | ||
| Ali et al. [36] | − | ||
| ms | ms |
| Scheme | No. of Bytes | No. of Messages |
|---|---|---|
| Proposed (Case 1) | 88 | 2 |
| Proposed (Case 2) | 148 | 2 |
| Proposed (Case 3) | 108 | 2 |
| Gope [30] (LAAP1) | 400 | 4 |
| Gope [30] (LAAP2) | 320 | 4 |
| Gope [30] (LAAP3) | 360 | 4 |
| Guo et al. [35] | 272 | 3 |
| Ali et al. [36] | 352 | 3 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Banerjee, S.; Das, A.K.; Chattopadhyay, S.; Jamal, S.S.; Rodrigues, J.J.P.C.; Park, Y. Lightweight Failover Authentication Mechanism for IoT-Based Fog Computing Environment. Electronics 2021, 10, 1417. https://doi.org/10.3390/electronics10121417
Banerjee S, Das AK, Chattopadhyay S, Jamal SS, Rodrigues JJPC, Park Y. Lightweight Failover Authentication Mechanism for IoT-Based Fog Computing Environment. Electronics. 2021; 10(12):1417. https://doi.org/10.3390/electronics10121417
Chicago/Turabian StyleBanerjee, Soumya, Ashok Kumar Das, Samiran Chattopadhyay, Sajjad Shaukat Jamal, Joel J. P. C. Rodrigues, and Youngho Park. 2021. "Lightweight Failover Authentication Mechanism for IoT-Based Fog Computing Environment" Electronics 10, no. 12: 1417. https://doi.org/10.3390/electronics10121417
APA StyleBanerjee, S., Das, A. K., Chattopadhyay, S., Jamal, S. S., Rodrigues, J. J. P. C., & Park, Y. (2021). Lightweight Failover Authentication Mechanism for IoT-Based Fog Computing Environment. Electronics, 10(12), 1417. https://doi.org/10.3390/electronics10121417