1. Introduction
In the past years, wireless sensor networks (WSNs) have been extensively utilized as key networks on the Internet of Things, body area networks, smart cities, smart grids [
1,
2,
3], agriculture, healthcare, the military domain, environment [
4,
5] etc., due to their ease of installation, scalability, low cost, and operating flexibility of nodes. Sensors can be distributed over a wide area and can perform the simultaneous data acquisition of desired ambient conditions (humidity, temperature, fire detection, vibrations, presence, gas pollution, noise, water level, etc.). For the practical use-case deployment of the WSN, security and reliability in communication among legitimate users are crucial [
6,
7].
Due to the open access nature of propagation channels, wireless communication suffers considerably from interception of confidential data transmissions. Consequently, great efforts have been devoted to finding effective methods in suppressing the deleterious actions of eavesdroppers. Physical layer security (PLS) is an emerging concept related to secrecy transmission by exploiting the natural phenomena of channels, such as fading, shadowing, path loss, and noise [
7,
8,
9,
10]. Relative to cryptography, which is complex and requires large energy consumption, PLS shows simplicity without the processing resources requirements. Unauthorized entities can be highly computational capable and, hence, can easily break the encryption undertaken at upper layers, thus, enhancing the security at the physical layer.
The seminal works of Shannon [
11] and Wyner [
12] showed that, if there are better channel conditions in the main propagation channel in comparison to the wiretap channel, secure transmission can be enabled. There are numerous published papers on the PLS performance analysis in the concept of information-theoretic security, over various fading channels. The average secrecy capacity and the probability of strictly positive secrecy capacity over Fisher–Snedecor
fading channels have been addressed in [
13].
The
distribution was experimentally proved for describing both fading and shadowing phenomena over wireless channels and showed a high level of generality [
14]. As an alternative to composite generalized
, the
model better fits the experimental data and accurately characterizes the legitimate channels for device-to-device communication (D2D). The authors in [
15] utilized this model in the analysis of different secrecy metrics for the essential wiretap channel consisting of the source, the destination, and an eavesdropper.
Additionally, achievable PLS over mixed fading channels, including the
, such as Nakagami-
m/
channels, was determined in [
16]. In [
17], the intercept probability of a randomly distributed eavesdroppers in the
N cascaded
wiretap channels, was introduced. The asymptotic behavior of intercept probability in the case of the nearest and the best eavesdropper’s overhearing was also investigated.
The WSN security enhancement is highly challenging and requires the utilization of novel approaches. The artificial noise method [
18] was pointed out as effective in certain wireless networks, but the need for an additional power resource to generate noise at the legitimate users was marked as unwanted in energy-constrained networks. The relay selection is another approach that assists the source–destination communication against eavesdropping [
19]. However, complex synchronization among relays and additional nodes in the network result in an undesirable system complexity.
The sensor scheduling approach has been adopted in [
20] as energy-aware solution in networks with limited-life power resources. In [
20], the authors proposed optimal scheduling (OS) based on selecting the sensor with the highest signal-to-noise ratio (SNR) for confidential transmission in industrial WSN, over Nakagami-
m fading channels. The results showed a significant intercept probability decreasing in comparison to the conventional round-robin scheduling (RS).
However, the OS has a fairness problem in selecting the node. To overcame this issue, scheduling based on the channel cumulative distribution function (CDF) assumption, which was suggested earlier in [
21,
22] for multiuser downlink wiretap transmission, can be exploited. Hence, scheduling schemes have been utilized in [
23] to improve the security of WSN i.e., to decrease the intercept probability of an attacker over generalized
fading links.
The authors in [
23] did not consider the network security–reliability tradeoff (SRT), which is another important issue from the WSN design perspective [
24,
25]. A detailed review on the challenges and solutions of improving the security and reliability for industrial WSN is given in [
6]. The analysis has shown that even the path loss can be involved in simultaneous upgrading of the security and throughput.
In this work, we deal with the WSN security on the physical layer employing sensor scheduling. The main, as well as the wiretap channels, are modeled as fading channels. The path loss originating from stationary and randomly located nodes is also taken into consideration. We determine the exact and the asymptotic expressions for the intercept probability employing CDF-based scheduling (CS), OS, as well as RS scheduling scheme as a benchmark. The secrecy diversity order of each scheme is also defined.
We also obtain the intercept probability as the function of the outage probability in order to quantify the tradeoff between security and reliability of the WSN. The impacts of numerous system parameters, such as the number of active WSN nodes, fading depth, and/or shadowing sharpness over main/wiretap links, the distances among nodes, and the pre-defined SRT-constrained outage threshold on the intercept probability, are identified. Novel analytical expressions are verified by Monte Carlo simulated results.
In overall, the main contributions can be stated as:
Novel, highly general exact intercept probability expressions for WSN security in the presence of an unauthorized node, under RS, OP, and CS scheduling methods, are derived.
Asymptotic expressions in simpler form, showing good accuracy in the region of medium-to-high SNR values at the sink, are also determined with the aim to enable the evaluation of the security metrics required for optimal system design.
Novel SRT analysis is identified, and the intercept probability is additionally quantified by the outage threshold.
Numerical and simulation results verify the presented analysis and illustrate the influence of channel and system parameters against eavesdropping in WSN.
The paper is structured as follows. In
Section 2, the system and channel model are introduced. Our intercept probability analyses, the exact and the asymptotic, are presented in
Section 3.
Section 4 addresses the SRT analysis. The numerical and simulated results are discussed in
Section 5. The main concluding remarks are given in
Section 6.
Appendix A and
Appendix B, contain the derivation procedures of particular expressions for the intercept probabilities.
2. System and Channel Model
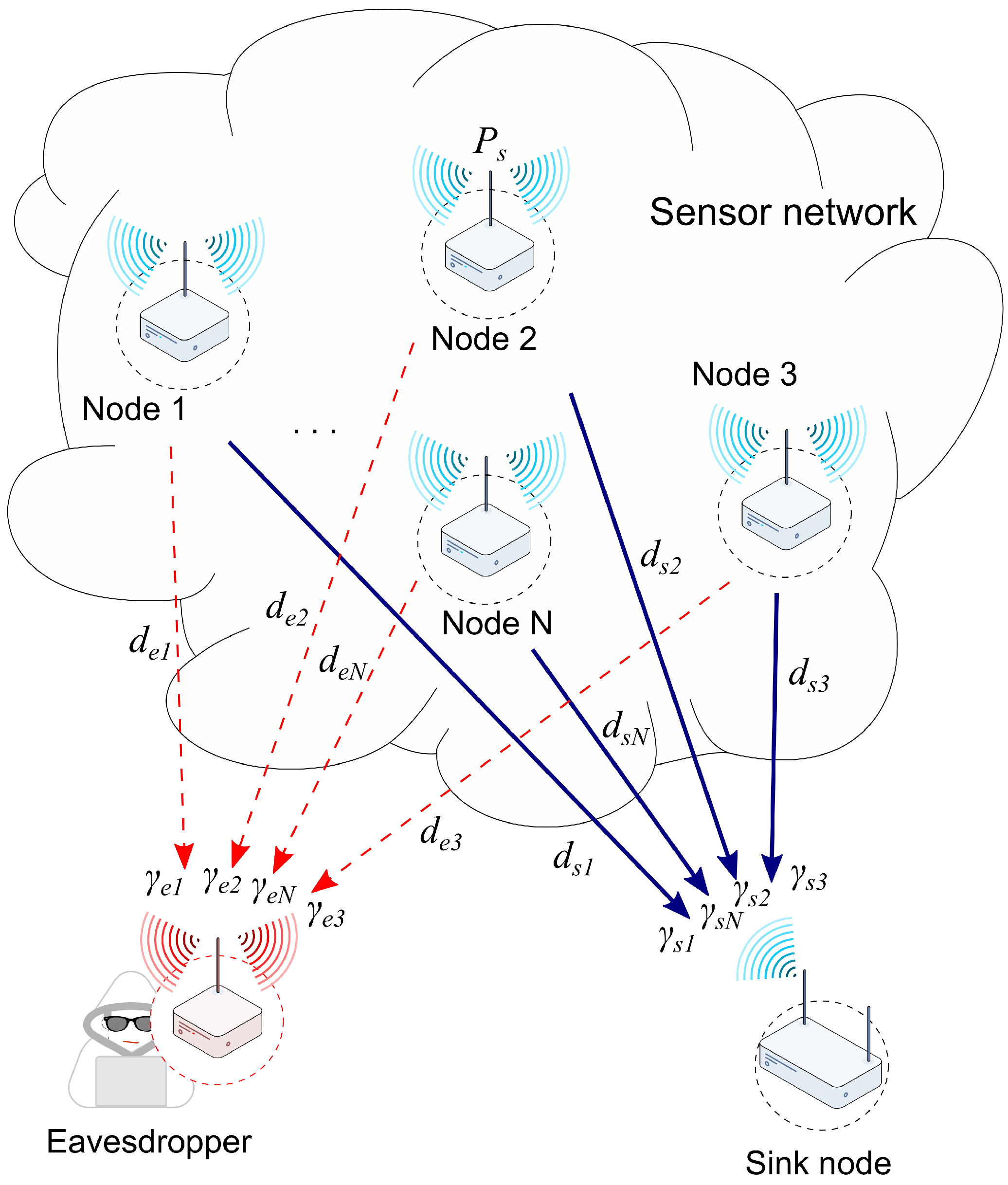
We assume the system model given in
Figure 1. The wireless network consists of an arbitrary number
N of stationary, randomly located sensors. Sensors sense specific data for the intended purpose of the WSN. Legitimate communication is obtained via sensor-sink links utilizing orthogonal multiple access, e.g., time division or orthogonal frequency division multiple access. Legitimate channels are marked as solid-blue lines in
Figure 1.
A selected sensor performs transmission over a main channel, e.g., referring to a time slot in time division multiple access, while an unauthorized node attempts to intercept secret information. The wiretap channels are marked with dashed lines. In an orthogonal channel, typically, the sensor with the highest data throughput has priority to communicate with the sink, which, in turn, maximizes the channel capacity without considering possible overhearing.
Contrary to that, in the analysis that follows, we consider sensor scheduling as an auxiliary tool to upgrade the PLS. The scheduling framework requires knowledge of the channel state information (CSI) of the main as well as the wiretap channels. This is a commonly exploited assumption in PLS analysis and frequently justified in numerous papers [
13,
15,
16,
17,
20,
23].
The sensed information propagates from the scheduled sensor to the sink. During the propagation, the signal is attenuated due to path loss, multipath fading, and shadowing. The composite fading is described by
distribution as suitable one for describing D2D communication channels [
14]. Owing to its generality, other fading distributions, such as Nakagami-
m, one-sided Gaussian, and Rayleigh, can be obtained as special cases. In addition, it is statistically more tractable in comparison to the composite generalized-
K fading model, which can be approximated by
. Thus, the analysis of PLS that follows has a high level of generality.
The received instantaneous SNR at the sink, from the
i-th sensor, can be expressed as
where
is the channel fading amplitude at the
i-th link,
denotes the signal power from the sensor,
is the distance between the
i-th sensor and the sink,
is the path loss parameter, and
is the variance of a zero-mean additive white Gaussian noise (AWGN).
Following the Shannon capacity formula [
11], we can evaluate the instantaneous channel capacity of the
i-th main link as
with
B denoting the transmission bandwidth.
Following the physical layer security literature [
16,
17,
20,
23], the eavesdropper is assumed to have perfect knowledge of legitimate transmissions from and to the sink, including the coding and modulation scheme, encryption algorithm, and secret key, except that the source signal is confidential. This is a common assumption in numerous papers since the eavesdropper could be a legitimate WSN user with restricted access to secrecy data. Thus, the instantaneous SNR tapped by the eavesdropper on the
i-th path can be defined as
with
being a fading coefficient of the wiretap channel between the
i-th sensor and eavesdropper and
denoting the distances between the sensor and eavesdropper. The
i-th instantaneous wiretap channel capacity can be calculated as
The probability density function (PDF) of the instantaneous SNR over the
i-th main or wiretap
channel, relying on [
14], can be expressed as
where * denotes subscript
s or
e, referring to the instantaneous SNR at sink or the eavesdropper, respectively. The fading severity parameter at the
i-th link is denoted as
, the shadowing factor as
,
is the average SNR at the sink or the eavesdropper, and
denotes Gamma function [
26] (Equation (8.310.1)). The
is notation of Meijer’s
G function [
26] (Equation (9.301)).
Based on the definition integral of the CDF and solving it by utilizing [
27] (Equation (
26)), the CDF of the instantaneous SNR over the main/wiretap links has the following form
3. Intercept Probability Based on Sensor Scheduling
Let us assume that the
i-th sensor is scheduled to transmit a confidential signal. An eavesdropper attempts to intercept the signal over the
i-th wiretap channel, whose capacity is
. The secrecy capacity that characterizes transmission from the
i-th specified sensor to the sink is the difference between the channel capacity of that
i-th main link and the
i-th wiretap link, as in [
20,
23]
The probability of intercept is the probability that the secrecy capacity of the
i-th link becomes non-positive and can be defined as [
20,
28]
By substituting (
2) and (
4) in (
8), it yields
Both integrals in (
9) are solved, first utilizing [
27] (Equation (
26)) and subsequently [
29] (Equation (07.34.21.0011.01)), so that the intercept probability of the
i-th transmitting link can be evaluated as
with
being the
i-th average main-to-eavesdropper’s signal ratio (MER) and with
denoting the ratio between the
i-th sensor-sink and the sensor-eavesdropper’s link distances.
In the rest of this section, we will obtain the exact and asymptotic intercept probability analyses, employing a scheduling framework.
3.1. Exact Analysis
Conventional RS scheduling is incapable of bringing multinode diversity gain in intercept probability decreasing. This method is the simplest one and is only a baseline in the analysis that follows. All sensors can access a given transmission channel, randomly, with an equal probability to send confidential data. Based on that, the RS intercept probability can be defined as the mean value of all
N intercept probabilities, in the form [
20]
On the other hand, the OS criterion should minimize the intercept probability but, subsequently, may cause a fairness problem among the sensors since the sink tends to select sensor closer to it i.e., to select links for transmission with higher SNR. The sensor is scheduled based on the following criteria
[
20], where
S denotes the set of sensors in the network under consideration. It follows that the secrecy capacity when the OS scheme is applied can be defined as
. Thus, assuming that
and
are independent, and with the help of (
8), the OS intercept probability can be found as [
20]
Although, the OS scheme enables significant multinode diversity gain, the sensors randomly located at different locations far from the sink rarely participate or do not participate at all in communication with the sink. This is a problem in the network with limited life-time users.
The CS scheduling policy enables fair selection among users while exploiting multinode diversity. This is an efficient algorithm that schedules the sensor for transmission based on the CDF of the sensor rates, in such a way that the sensor whose rate is high enough, but least probable to become higher, is selected first. Analytically, the sensor is selected as
, where
is defined by (
6).
The sink performs the previously defined selection after collecting the instantaneous SNRs,
, from all sensor nodes at each time slot,
t. The random variable
is uniformly distributed within the range
[
21]. Although, different main channels may have different channel distributions, i.e.,
, the values
have the same distribution. The CDF that characterizes the SNR of a selected transmission,
, can be defined as [
22]
Herewith, we will adopt the assumption that all main links as well as associate wiretap links are identically distributed, i.e.,
,
;
,
. According to the fact that the distances among the network’s nodes are not large enough to make the channel conditions differ severely, analysis for the independent but identically distributed (i.i.d) fading channels is not a rigid constraint. Thus, according to (
9), the CS scheduling intercept probability can be evaluated as
Invoking the procedure presented in
Appendix A,
is derived in the form of (
15).
where
.
3.2. Asymptotic Analysis
To gain more insights for the medium-to-high MER regime, we analyzed the asymptotic behavior of (
10) and (
15) and present them in an easy-tractable form with good accuracy. Thed erivation procedure of asymptotic expressions is given in
Appendix B.
We derive the asymptotic expression for evaluating
of each
i-th link, in the following way
when
. Therewith, relying on (
16), it is easy to evaluate the asymptotic intercept probability when RS or OS policies are applied, by substituting (
16) in (
11) or (
12), respectively.
An easily tractable asymptotic solution of (
15) has the following form
Moreover, derived asymptotic forms can be used to determine the secrecy diversity performance of multinode wireless transmissions with the aim of intuitively obtaining the impact of the number of active sensors in a network or other system parameters on the secrecy. The generalized definition form of the secrecy diversity order,
, is related to the asymptotic ratio of the logarithmic intercept probability to the logarithmic MER, when MER tends to Infinity, as in [
22]
According to (
11), the secrecy diversity order of the RS scheme yields
Thus, relying on (
16), it can be concluded that RS secrecy diversity order can be determined as
The diversity gain of RS scheduling with N sensors is determined according to the previous equation, as the minimum of the channel fading depth and shadowing sharpness parameters among all main and wiretap links. This also means that upon increasing the number of sensors, the wireless security of the conventional RS scheduling scheme would not improve, and even degrades.
By substituting (
16) into (
12), and relying on (
18), we obtain the OS secrecy diversity order in the following form
which is determined according to the exponential decrease of the OS intercept probability as
, when
. Thus, by increasing the number of sensors in the network, the secrecy diversity order of the OS scheme is increased.
Finally, by substituting (
17) into (
18), the secrecy diversity order of the CS scheduling scheme is defined as
We notice that the secrecy diversity order is highly dependent on the number of network nodes, especially when the channel conditions of the main links are favorable. This coincides with the diversity order achieved with the optimal multiuser scheduling policy and indicates the full diversity achieved by the CS scheduling policy. To be more specific, although the secrecy performance will be degraded, e.g., if the distance between the sensor and eavesdropper becomes shorter, this will not affect the speed at which the intercept probability decreases when
tends to infinity. [
21].
4. Security–Reliability Tradeoff
When a sensor’s transmission power is increased, the reliability of the link is improved due to the fact that the sink receives more power and the corresponding outage probability decreases. On the other hand, this increase of output power also increases the probability of intercept events as an eavesdropper can receive more power and potentially detect the received information bits correctly. Therefore, there is a tradeoff between outage and intercept probabilities.
We adopt a definition of the intercept probability that also takes into account the pre-defined outage threshold. The outage threshold corresponds to the SNR threshold
below which detection is very unlikely for the given data rate, and the intercept occurs when eavesdropper detects the signal with an SNR over this threshold. The intercept probability is then
keeping in mind that
and
are statistically independent.
Increasing the data rate works in the opposite direction to the output power increase, as higher data rates generally require higher SNR values. Therefore, this balance between the output power and data rate reflects the balance between the outage probability and secrecy capacity, and, in turn, the intercept probability. Although increasing the data rate or decreasing the transmitting power of sensors may reduce the intercept probability and improve the level of security, it comes with the cost of transmission reliability degradation, since the outage probability of the main link also increases. Therefore, our motivation is to find a tradeoff between reliability and security in this context. However, this balance of reliability versus security can be further enhanced by means of sensor scheduling.
Equation (
23) can be rewritten as
Apart from the previous definitions, the outage probability of each
i-th sensor-sink link, is defined as
According to the derived solutions in the previous section and recalling the asymptotic form of the
CDF, (
A6), we derive the
as the function of
in the following form
where
is given in (
10).
By recalling, (
11) and (
12), the RS and OS intercept probabilities can be evaluated, respectively, as
Following the previous case, the CS intercept probability constrained by the
, can be defined as
In addition, the outage probability in the scheduled sensor-sink channel, is given by
Thus, combining the latter two expressions, after some mathematical manipulations, we derive the CS intercept probability from the SRT perspective, as
Overall, one limitation of the proposed approach is that it refers to the scenario when the channel state information (CSI) of all main as well as wiretap channels are available at the sink. This can be justified when the eavesdropper is an authorized part of WSN allowed in communication among nodes but unwanted in the transmission of secure data. In some practical networks, the eavesdroppers are passive and malicious and it is difficult to obtain instantaneous CSI of a wiretap channel.
Another limitation is that the data streams are assumed with the same priority in accessing the wireless channel for transmission although the sensors may generate different types of data having different quality of service (QoS) requirements. For instance, some sensors may have strict real-time data requirements, which should be assigned with a higher priority in accessing the communication channel.
5. Numerical Results and Simulation
In this section, numerical results are presented utilizing ®, according to the fact that the exact expressions are in the form of special Meijer’s G functions, which are built-in functions in this software package. Along with the analytical results, independent Monte Carlo simulations are also shown. One value is estimated on the basis of generated samples, in ®. For the sake of simplicity, we assume i.i.d. main or/and wiretap links, in the analysis that follows.
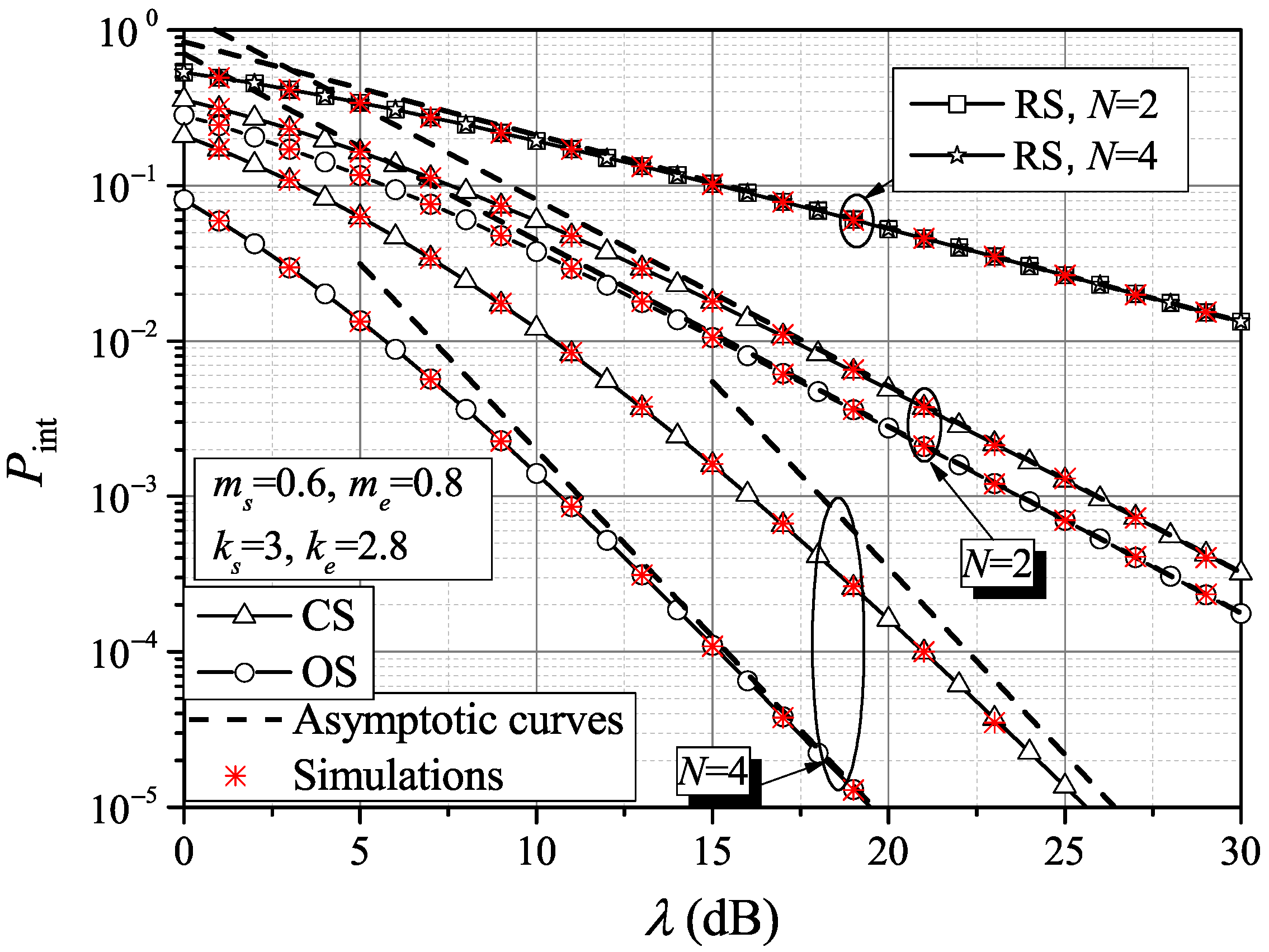
Figure 2 shows the intercept probability (exact and asymptotic) versus the average MER under different scheduling schemes. It is noticeable that, if the network dimension increases, the probability of intercept decreases, especially when an OS scheduling policy is applied. Asymptotic results fit better when
for all scheduling schemes and are also quite accurate in the range of higher MER values in the case of OS when the number of sensors increases from
to
.
Under a scenario with i.i.d. links, tracking the asymptotic curves, we can notice the same secrecy diversity order of the OS and CS scheduling policies. This concluding remark can also be obtained analytically by comparing (
21) and (
22). Finally, the RS intercept probability is independent of the network dimension modification.
The intercept probability as a function of the fading depth parameter for the main links, is illustrated in
Figure 3. When the fading depth decreases, i.e., parameter
increases, the probability of the intercept is improved. In other words, favorable channel conditions are expected to enhance secure WSN communication.
Modification in the network dimension shows less impact on the CS intercept probability in comparison to the OS intercept probability for the given set of parameters. For the increase in the number of sensor nodes, N, from 2 to 4, remains constant in the case of RS scheme, it decreases for less than one order of magnitude in the case of the CS scheduling framework and for more than two orders of magnitude in the case of the OS policy, when . In addition, the Monte Carlo simulated results show good agreement with the analytical ones.
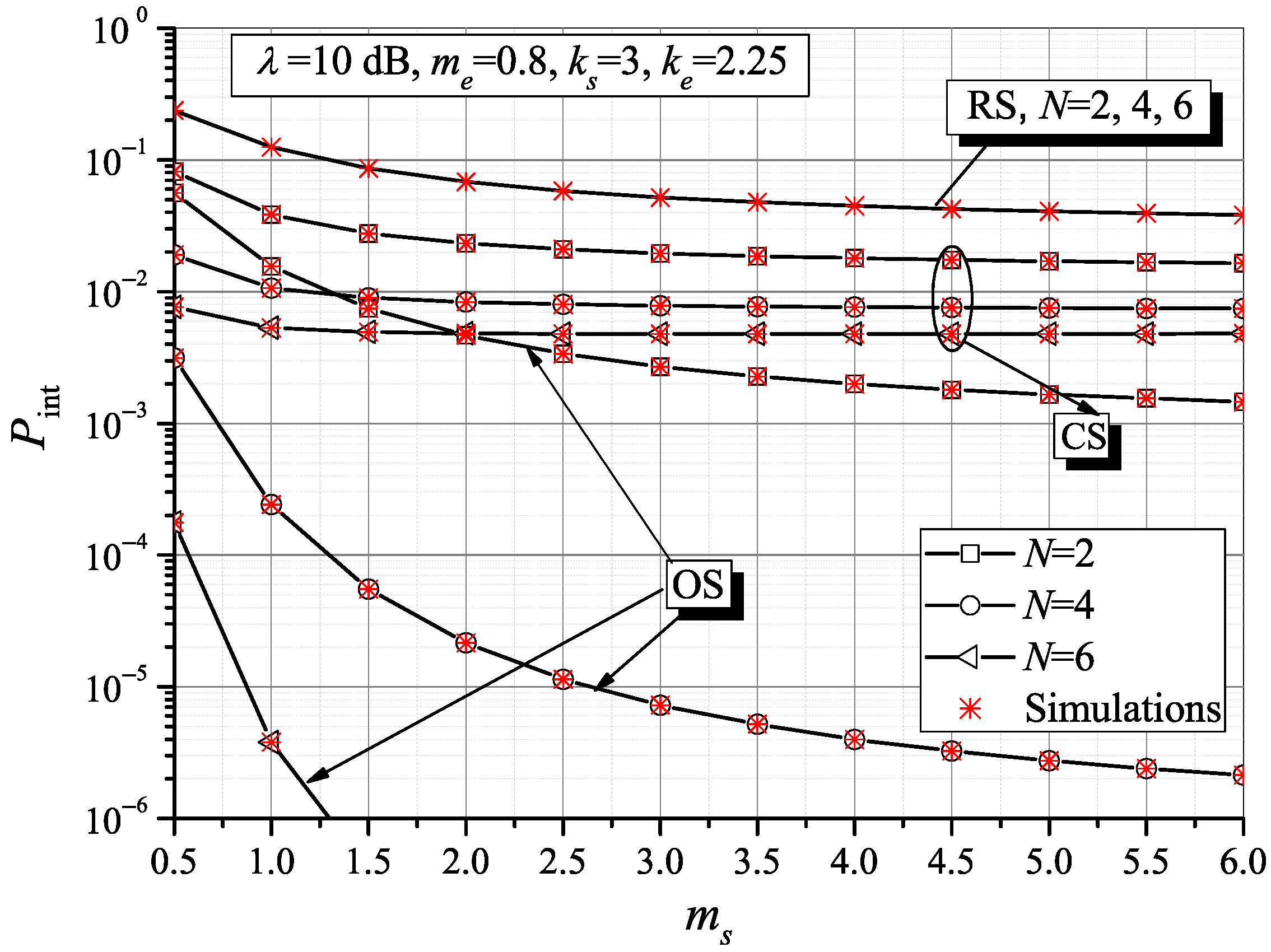
The intercept probability versus the number of active sensors for two specific average MER values (
,
), is shown in
Figure 4. Again, the results demonstrate the RS intercept probability independence on the network dimension, regardless of the average MER value. For
, i.e., when the average SNR over the wiretap channel equals the average SNR over the main channel, the acceptable
can be obtained only under the OS scheduling scheme. For larger
values, the CS policy is also acceptable to schedule energy-aware nodes for secure transmission.
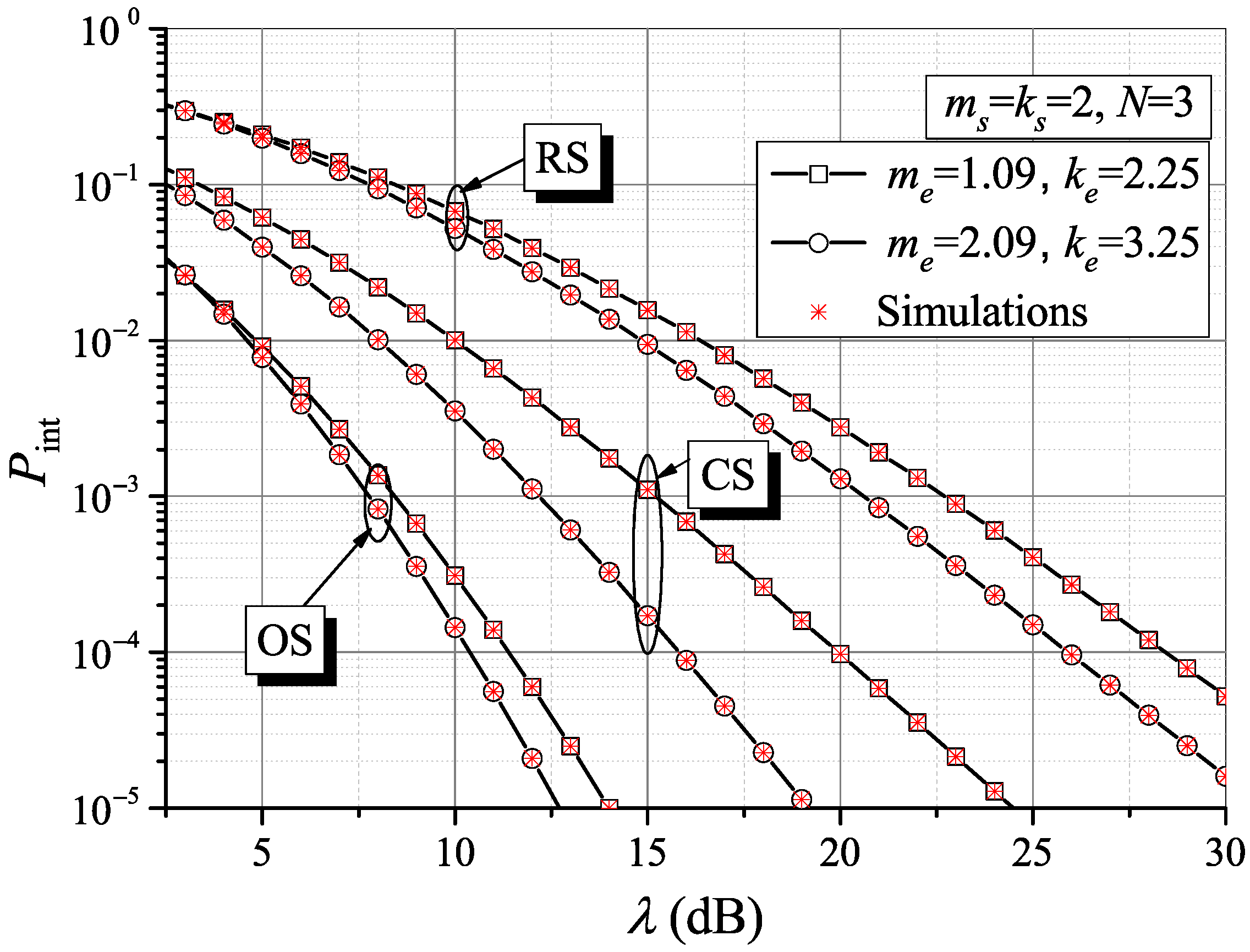
The impact of various fading/shadowing channel conditions over wiretap channels during the intercept events is shown in
Figure 5. When the wiretap channel fading and shadowing parameters are modified, more pronounced effects are noticed when the CS scheme is applied. The required average MER gain to obtain
is 2 in the case of OS policy and even 5 in the case of CS policy, when the channel condition parameters increase from
to
. This confirms that favorable wiretap channel conditions, as well as the favorable main channel conditions, also degrade the intercept probability. Even RS has shown visible dependence on the wiretap channel condition change.
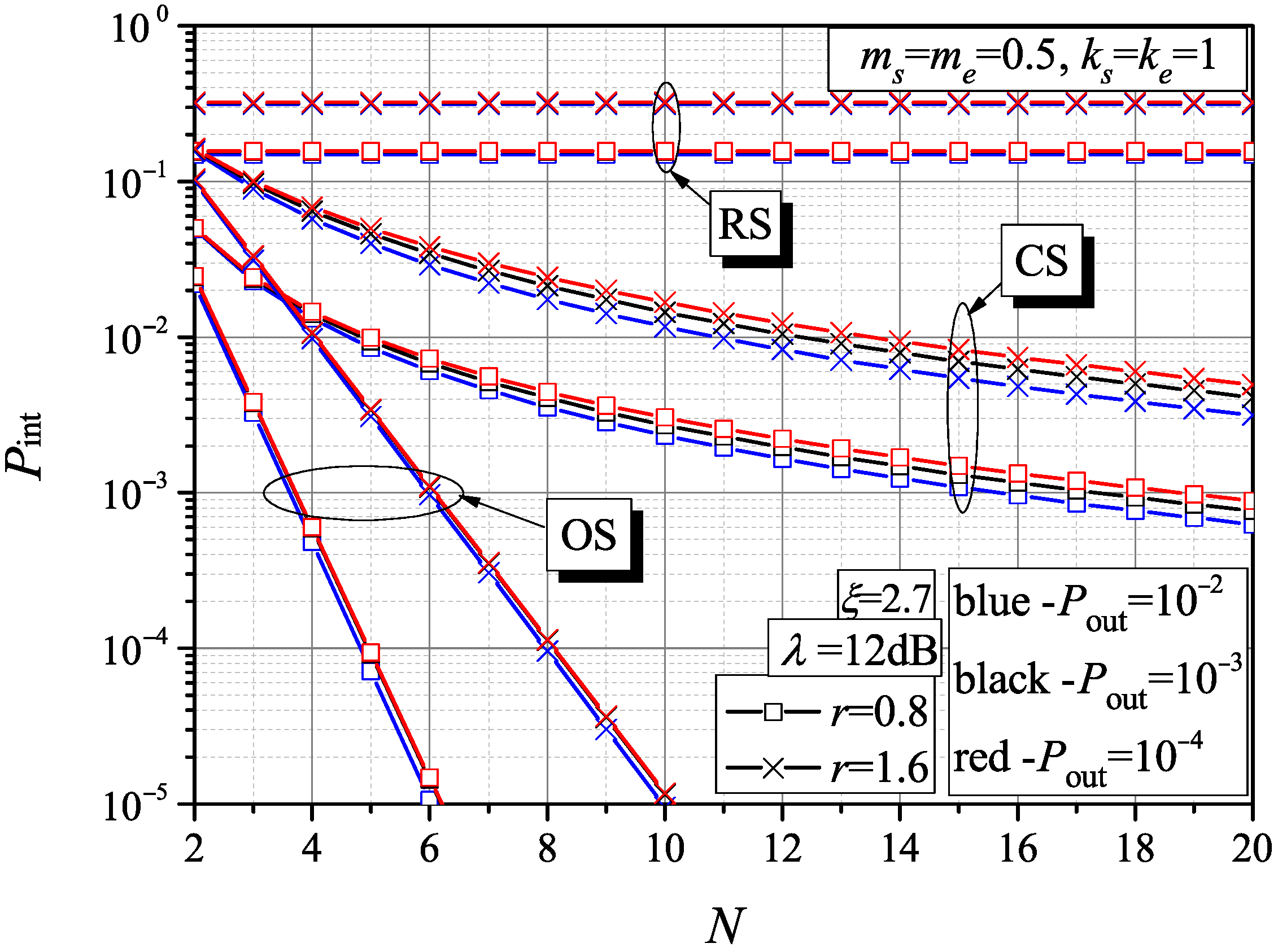
In order to avoid complexity and illegibility of the Figure legends, the path loss impact was not included in the previous Figures. Hence,
Figure 6 shows the required values of the average MER versus the ratio
r to reach the intercept probability of
and
, under CS and OS schemes. Increasing the parameter
r indicates larger distances between the scheduled sensor and the sink in comparison to the distances between the sensor and eavesdropper, which results in higher MER values required to obtain the specified intercept probabilities. The results also show that the CS scheduling is more dependent on the ratio
r, as well as of the variations of channel conditions in comparison to the OS scheme.
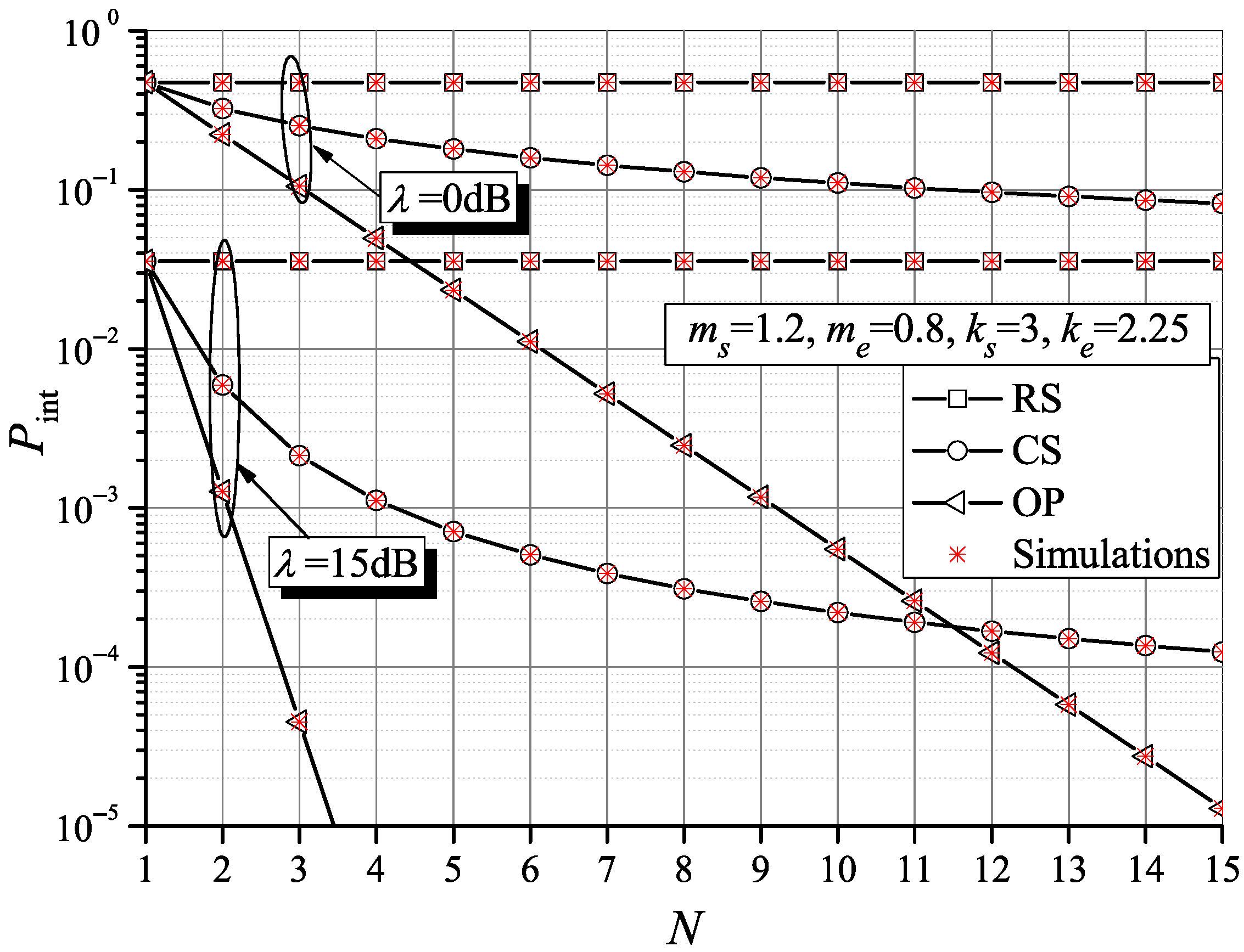
Figure 7 shows the intercept probability versus the number of network nodes for different outage probability constraints and path loss scenarios. When the outage probability increases, the intercept probability is reduced. We can also observe the black and red curves for the OS scheduling overlap, which demonstrate the intercept probability independence on the outage probability over
. By all means, the OS approach leads to the best intercept probability improvement, while the CS scheme is visibly dependent on the outage constraints. However, by increasing the WSN dimension, the intercept probability tends to very low values for both scheme policies.
Overall, we can conclude that the analysis and numerical results are useful in the sense that they can provide a quantitative measure of the physical level security in particular scenarios. If the PLS is found to be low, there are changes that can be implemented in the WSN, such as modifying the output power of some or all nodes and employing directive antennas in critical nodes. In turn, the proposed analysis is then used to check if a criterion in physical level security is met by a particular WSN. If the criterion is not met, than a series of iterations can be implemented, for example: changing the physical placement of the nodes and the node characteristics, until the required PLS is achieved.
6. Conclusions
In this work, the PLS of WSN, in one part versus the reliability, was investigated by employing various scheduling schemes. Analysis was performed for the fading scenario, which indicates a high level of generality of the derived intercept probability expressions, including both the exact and the asymptotic.
The results demonstrated that the asymptotic expressions were closer to the exact ones for a lower number of active nodes in the network but were also quite accurate in the range of higher MER values, for larger WSNs. For the i.i.d. scenario, the same secrecy diversity order of OS and CS scheduling schemes was noted. An increase of the network dimension showed a significant impact on the intercept probability, especially under the OS scheduling policy. The secrecy performance improvement is highly dependent on the main/wiretap channel condition amelioration. In addition, the CS scheduling is more dependent on the fading depth/shadowing sharpness variations and the path loss as well as on the outage probability constraints in comparison to the OS scheme.
Consequently, the performed analyses and highlighted remarks could be useful for security enhancement of energy-aware WSNs on physical layer. The results could be significant in protecting private information for SmartHome purposes, in telemedicine, agriculture, industrial, environment, urban, and in other applications where WSN is a key component. Our future work will be dedicated toward exploring novel scheduling schemes or other PLS based methods in order to upgrade secure WSN transmission or decrease the possibilities of intercept events.