MSAM: Modular Statistical Analytical Model for MAC and Queuing Latency of VLC Networks under ICS Conditions
Abstract
1. Introduction
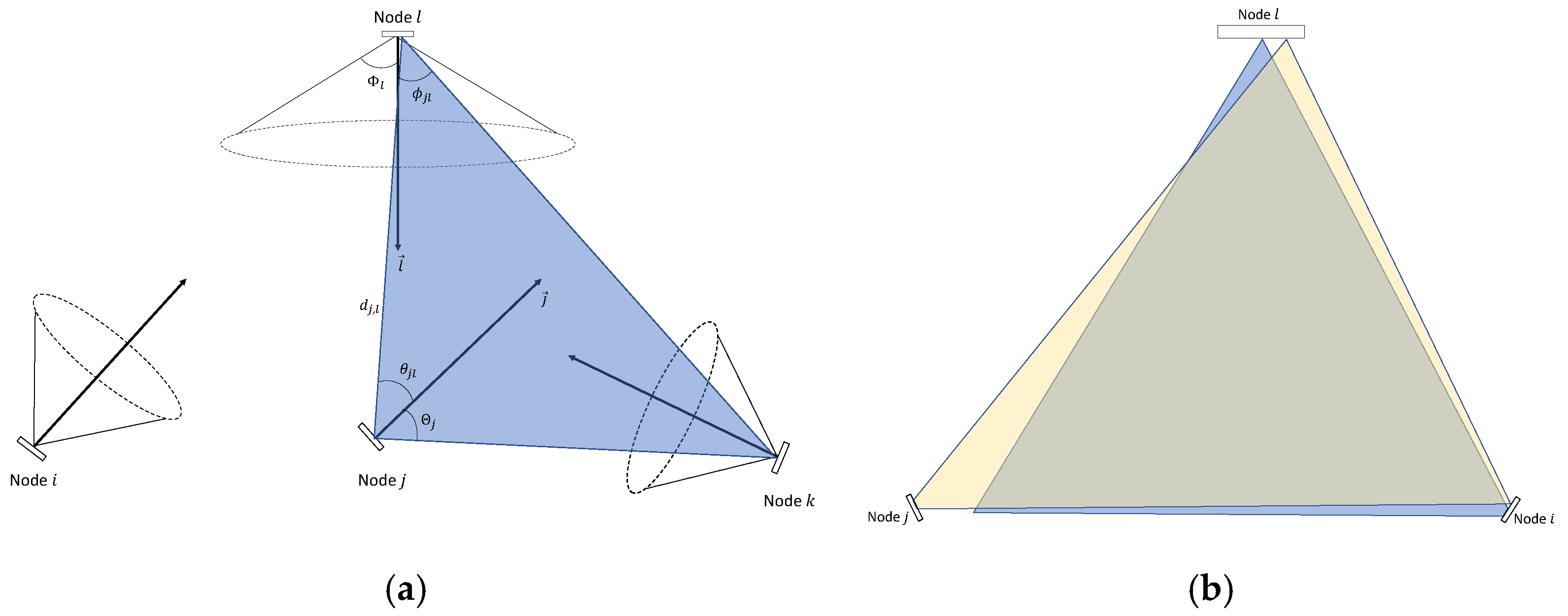
- Develop a novel approach to model a VLC network operating the IEEE 802.15.7 CSM-CA protocol as a network of mutually dependent queues whose inter-arrival and service time distributions are of the general form, i.e., a network of G/G/1 queues. Subsequently, apply the principles of the tagged user analysis [23,24,25,26] to define the key assumptions under which dependency is decoupled, considering the distinct contention behaviour used by each node to access the shared channel. Moreover, this study employs the radiometry and photometry characteristics of the VLC [2] and set theory [27] to develop mathematical expressions describing the hidden and exposed node from a perspective of an arbitrary node within the network.
- Derive the service time distribution that quantifies the CSMA-CA operations based on near-real assumptions. Subsequently, utilise some of the statistical and queuing theorems in conjunction with the modularity approach of MSAM to generate several distributions signifying the network’s operations from different aspects, i.e., the probability distributions of the time required to service successful packets, packet’s inter-departure distribution and the distribution of queueing delay. Besides the derivation of these distributions, MSAM also offers several metrics to measure the performance of MAC protocol, including the probability of exposed and hidden node collisions, probability of dropping packet due to exceeding the maximum number of busy channel assessments, network throughput, packets’ average delay and jitter.
- Provide extensive assessment for the integrity of MSAM by comparing its results with the simulation outcomes, considering several scenarios, e.g., heterogeneous traffic patterns, various network densities and the different number of hidden and exposed nodes. The results of these assessments demonstrate the ability of MSAM to predict the performance of the IEEE 802.15.7 CSMA-CA protocol precisely.
2. Materials
2.1. Overview of the IEEE 802.1.7 CSMA-CA Protocol
2.2. Imperfect Channel Sensing (ICS)
2.3. Related Works
3. Methods
3.1. Model Assumptions Underlying MSAM
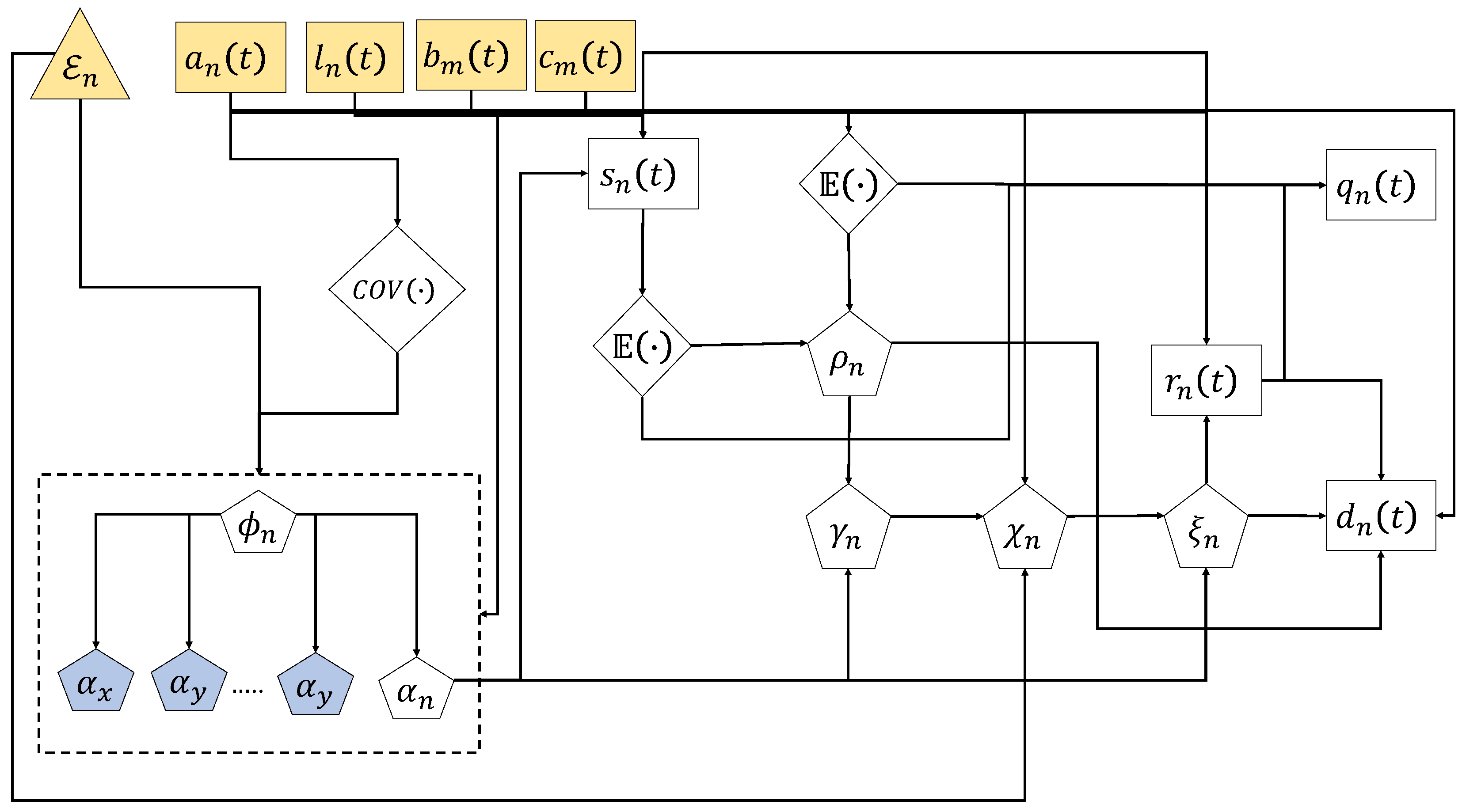
3.2. Derivation of the MSAM
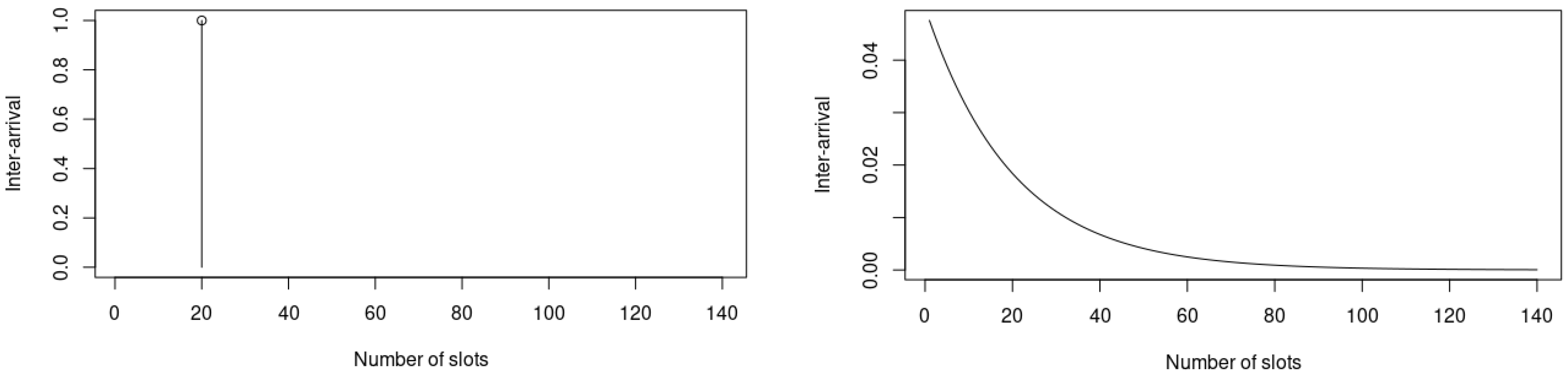
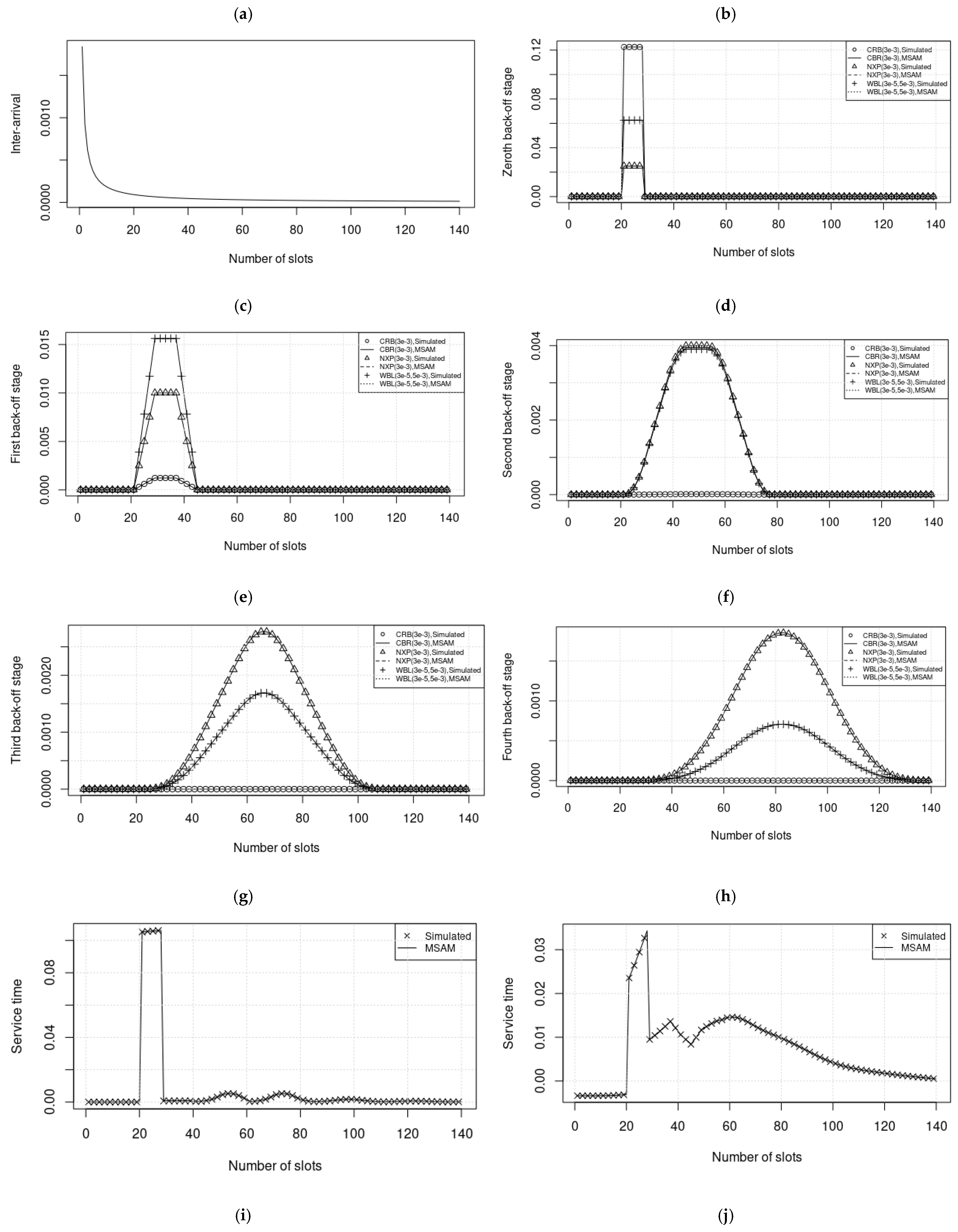
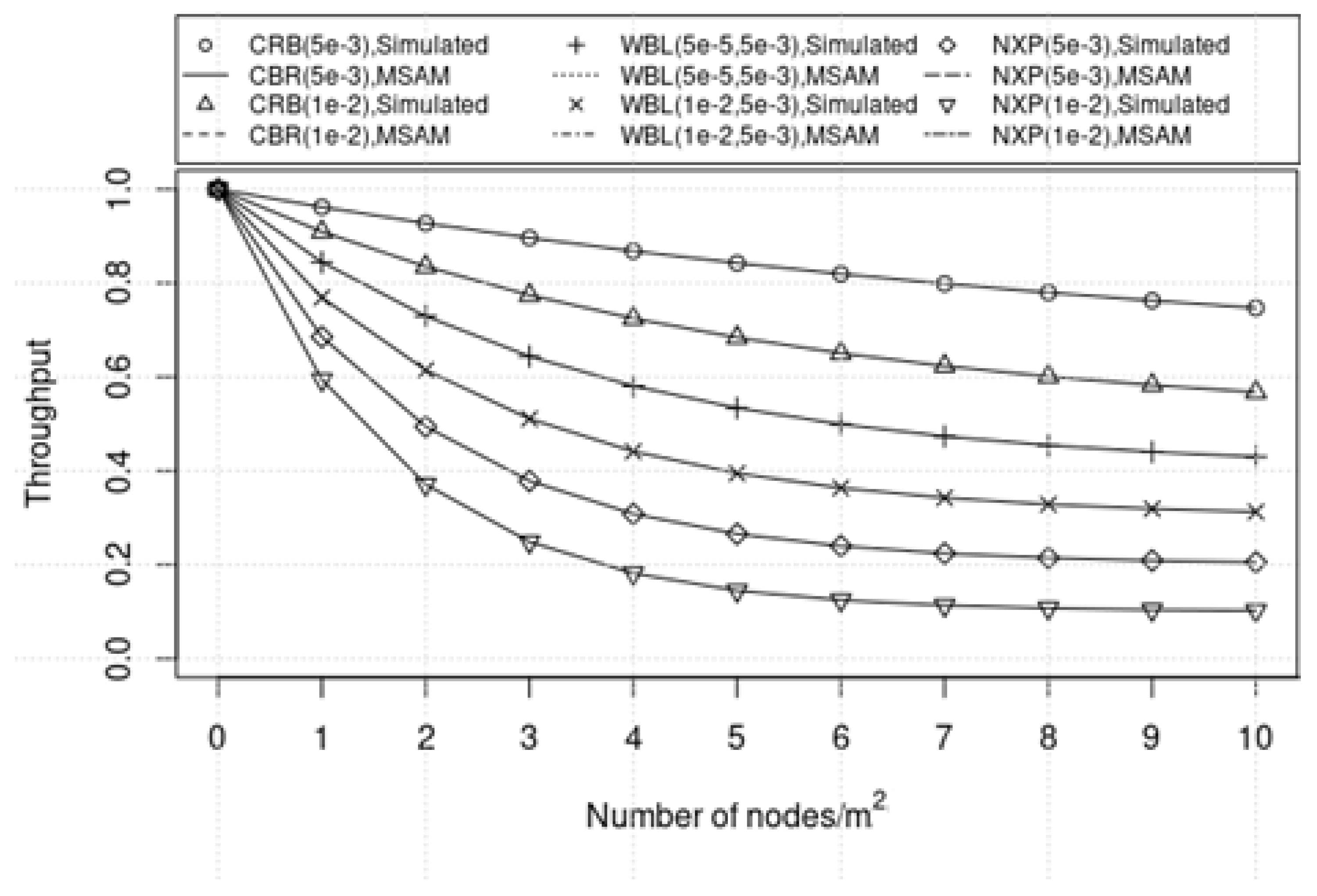
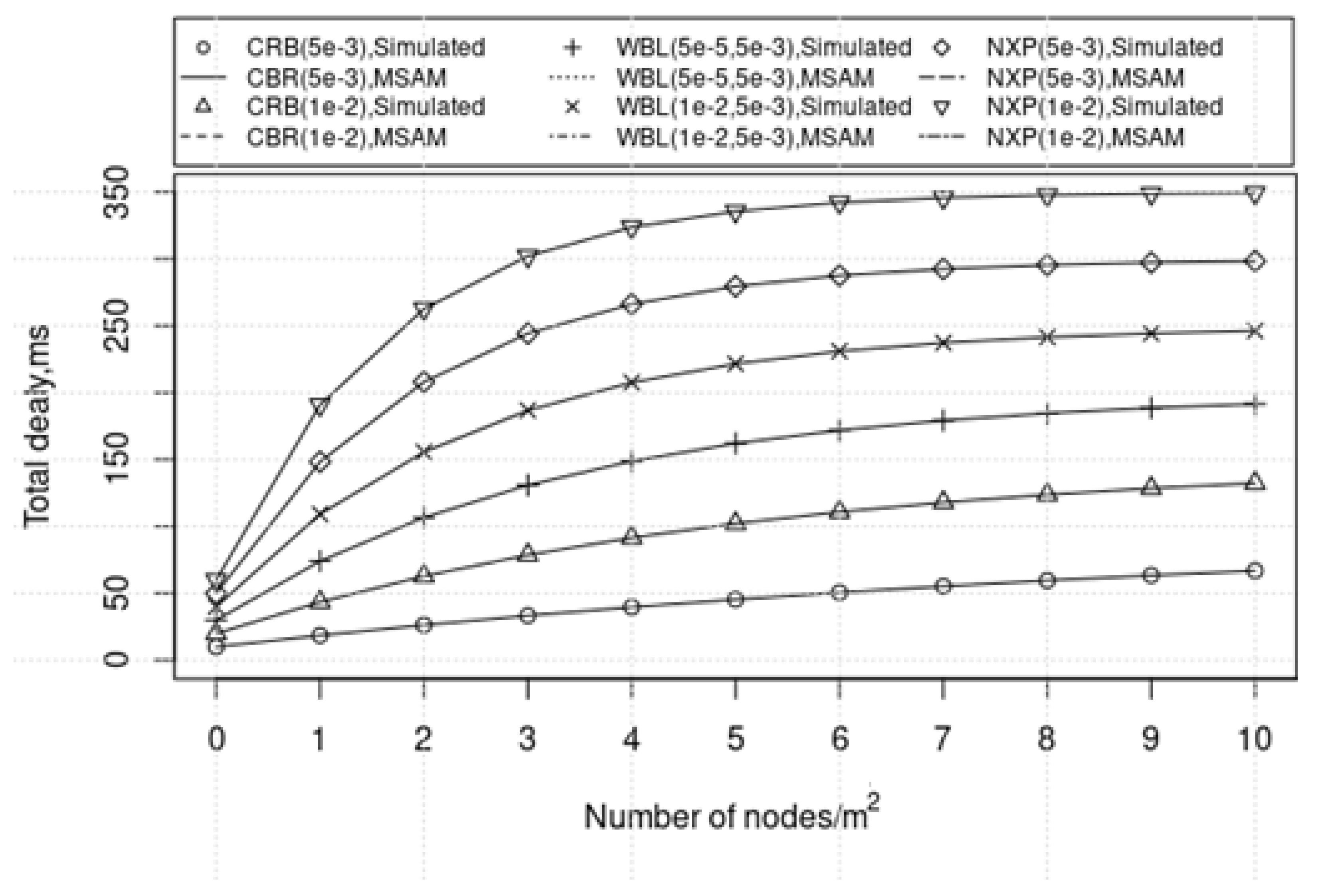
4. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Chi, N. LED-Based Visible Light Communications; Tsinghua University Press: Beijing, China, 2018; ISBN 9783662566602. [Google Scholar]
- Pathak, P.H.; Feng, X.; Hu, P.; Mohapatra, P. Visible Light Communication, Networking, and Sensing: A Survey, Potential and Challenges. IEEE Commun. Surv. Tutor. 2015, 17, 2047–2077. [Google Scholar] [CrossRef]
- Arfaoui, M.A.; Soltani, M.; Tavakkolnia, I.; Ghrayeb, A.; Safari, M.; Assi, C.; Haas, H. Physical Layer Security for Visible Light Communication Systems: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 1887–1908. [Google Scholar] [CrossRef]
- Al-Khori, J.; Nauryzbayev, G.; Abdallah, M.; Hamdi, M. Secrecy Performance of Decode-and-Forward Based Hybrid RF/VLC Relaying Systems. IEEE Access 2019, 7, 10844–10856. [Google Scholar] [CrossRef]
- IEEE 802.15.7 Task Group. IEEE Standard for Local and metropolitan area networks—Part 15.7: Short-Range Optical Wireless Communications. IEEE Std 802.15.7 2011, 1–407. [Google Scholar] [CrossRef]
- Dimitrov, S.; Hass, H. Principles of LED Light Communications towards Networked Li-Fi; Cambridge University Press: Cambridge, UK, 2015; ISBN 9781107049420. [Google Scholar]
- Jung, H.; Kim, S.-M. A Full-Duplex LED-to-LED Visible Light Communication System. Electronics 2020, 9, 1713. [Google Scholar] [CrossRef]
- Kim, B.W.; Yoo, J.-H.; Jung, S.-Y. Design of Streaming Data Transmission Using Rolling Shutter Camera-Based Optical Camera Communications. Electronics 2020, 9, 1561. [Google Scholar] [CrossRef]
- Corbellini, G.; Aksit, K.; Schmid, S.; Mangold, S.; Gross, T.R. Connecting networks of toys and smartphones with visible light communication. IEEE Commun. Mag. 2014, 52, 72–78. [Google Scholar] [CrossRef]
- 5G Infrastructure Public Private Partnership (5G PPP). Available online: https://5g-ppp.eu/ (accessed on 15 April 2021).
- Căilean, A.; Dimian, M. Current Challenges for Visible Light Communications Usage in Vehicle Applications: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2681–2703. [Google Scholar] [CrossRef]
- Internet of Radio-Light (IoRL) Project. Available online: https://iorl.5g-ppp.eu/ (accessed on 15 April 2021).
- Zhao, L.; Chi, X.; Yang, S. Optimal ALOHA-Like Random Access with Heterogeneous QoS Guarantees for Multi-Packet Reception Aided Visible Light Communications. IEEE Trans. Wirel. Commun. 2017, 15, 7872–7884. [Google Scholar] [CrossRef]
- Schenk, T. RF Imperfections in High-Rate Wireless Systems; Springer: Dordrecht, The Netherlands, 2008; ISBN 9781402069031. [Google Scholar]
- Samano-Robles, R.; Ghogho, M.; McLernon, D.C. Wireless Networks With Retransmission Diversity and Carrier-Sense Multiple Access. IEEE Trans. Signal Process. 2009, 57, 3722–3726. [Google Scholar] [CrossRef]
- Ley-Bosch, C.; Alonso-González, I.; Sánchez-Rodríguez, D.; Ramírez-Casañas, C. Evaluation of the Effects of Hidden Node Problems in IEEE 802.15.7 Uplink Performance. Sensors 2016, 16, 216. [Google Scholar] [CrossRef]
- Nan, Z.; Chi, X. Research on an uplink carrier sense multiple access algorithm of large indoor visible light communication networks based on an optical hard core point process. Appl. Opt. 2016, 55, 10392–10399. [Google Scholar] [CrossRef]
- Hwang, J.; Do, T.; Yoo, M. Performance analysis on MAC protocol based on beacon-enabled visible personal area networks. In Proceedings of the 5th Fifth International Conference on Ubiquitous and Future Networks (ICUFN), Da Nang, Vietnam, 2–5 July 2013; pp. 384–388. [Google Scholar]
- Musa, A.; Dani Baba, M.; Mansor, H.M.A.H. Performance analysis of the IEEE 802.15.7 CSMA/CA algorithm based on Discrete Time Markov Chain (DTMC). In Proceedings of the IEEE 11th Malaysia International Conference on Communications (MICC), Kuala Lumpur, Malaysia, 26–28 November 2013; pp. 385–389. [Google Scholar]
- Nobar, S.K.; Mehr, K.A.; Niya, J.M. Comprehensive performance analysis of IEEE 802.15.7 CSMA/CA mechanism for saturated traffic. IEEE OSA J. Opt. Commun. Netw. 2015, 7, 62–73. [Google Scholar] [CrossRef]
- Mehr, K.A.; Nobar, S.K.; Niya, J.M. IEEE 802.15.7 MAC under unsaturated traffic: Performance analysis and queue modeling. IEEE OSA J. Opt. Commun. Netw. 2015, 7, 875–884. [Google Scholar] [CrossRef]
- Dang, N.T.; Mai, V.V. A PHY/MAC Cross-Layer Analysis for IEEE 802.15.7 Uplink Visible Local Area Network. IEEE Photonics J. 2019, 11, 1–17. [Google Scholar] [CrossRef]
- Baz, M.; Mitchell, P.D.; Pearce, D.A.J. Analysis of Queuing Delay and Medium Access Distribution over Wireless Multihop PANs. IEEE Trans. Veh. Technol. 2014, 64, 2972–2990. [Google Scholar] [CrossRef]
- Sheikh, A.; Wan, T.; Alakhdhar, Z. A Unified Approach to Analyse Multiple Access Protocols for Buffered Finite Users. J. Netw. Comput. Appl. 2004, 27, 49–76. [Google Scholar] [CrossRef]
- Wan, T.; Sheikh, A.U. Performance and stability analysis of buffered slotted ALOHA protocols using tagged user approach. IEEE Trans. Veh. Technol. 2000, 49, 582–593. [Google Scholar] [CrossRef]
- Rasool, S.; Sheikh, A.U. An Approximate Analysis of Buffered S-ALOHA in Fading Channels Using Tagged User Analysis. IEEE Trans. Wirel. Commun. 2007, 6, 1320–1326. [Google Scholar] [CrossRef]
- Dasgupta, A. Set Theory with an Introduction to Real Point Sets; Springer: New York, NY, USA, 2013; ISBN 9781461488545. [Google Scholar]
- Komine, T.; Nakagawa, M. Fundamental analysis for visible-light communication system using LED lights. IEEE Trans. Consum. Electron. 2004, 50, 100–107. [Google Scholar] [CrossRef]
- Lee, K.; Park, H.; Barry, J.R. Indoor Channel Characteristics for Visible Light Communications. IEEE Commun. Lett. 2011, 15, 217–219. [Google Scholar] [CrossRef]
- Moreno, I.; Sun, C.-C. Modeling the radiation pattern of LEDs. Opt. Express 2008, 16, 1808–1819. [Google Scholar] [CrossRef]
- Baccelli, F.; Błaszczyszyn, B. Stochastic Geometry and Wireless Networks Volume 1; Now Publishers: Delft, The Netherlands, 2009; ISBN 9781601982643. [Google Scholar]
- Andrews, J.G.; Ganti, R.K.; Haenggi, M.; Jindal, N.; Weber, S. A primer on spatial modeling and analysis in wireless networks. IEEE Comm. Mag. 2010, 48, 156–163. [Google Scholar] [CrossRef]
- Levitin, G. The Universal Generating Function in Reliability Analysis and Optimization; Springer Science & Business Media: Berlin, Germany, 2006; ISBN 978-1-84628-245-4. [Google Scholar]
- Reiman, M. Asymptotically exact decomposition approximations for open queueing networks. Oper. Res. Lett. 1990, 9, 363–370. [Google Scholar] [CrossRef]
- Czachórsi, T. A Diffusion Approximation Model for Wireless Networks Based on IEEE 802.11 Standard. Comput. Commun. 2010, 33, S86–S92. [Google Scholar] [CrossRef]
- Fischer, H. History of the Central Limit Theorem from Classical to Modern Probability Theory; Springer: New York, NY, USA, 2010; ISBN 9780387878577. [Google Scholar]
- Spitzer, F. Principles of Random Walk; Springer: New York, NY, USA, 2013; ISBN 9781475742299. [Google Scholar]
- Yao, D.; Buzacott, J. The exponentialization approach to flexible manufacturing system models with general processing times. Eur. J. Oper. Res. 1986, 24, 410–416. [Google Scholar] [CrossRef]
- Kleinrock, L. Queuing System: Theory; John Wiley & Sons: Hoboken, NJ, USA, 1976. [Google Scholar]
- Takagi, H. Queuing Analysis as a Foundation for Performance Evaluation; Elsevier Science Publishers B.V.: Amsterdam, The Netherlands, 1993. [Google Scholar]
- Ns-3 Simulator. Available online: https://www.nsnam.org/ (accessed on 15 April 2021).
- Smith, R. The dynamics of internet traffic: Self-similarity, self-organisation, and complex phenomena. Adv. Complex Syst. 2011, 14, 905–949. [Google Scholar] [CrossRef]

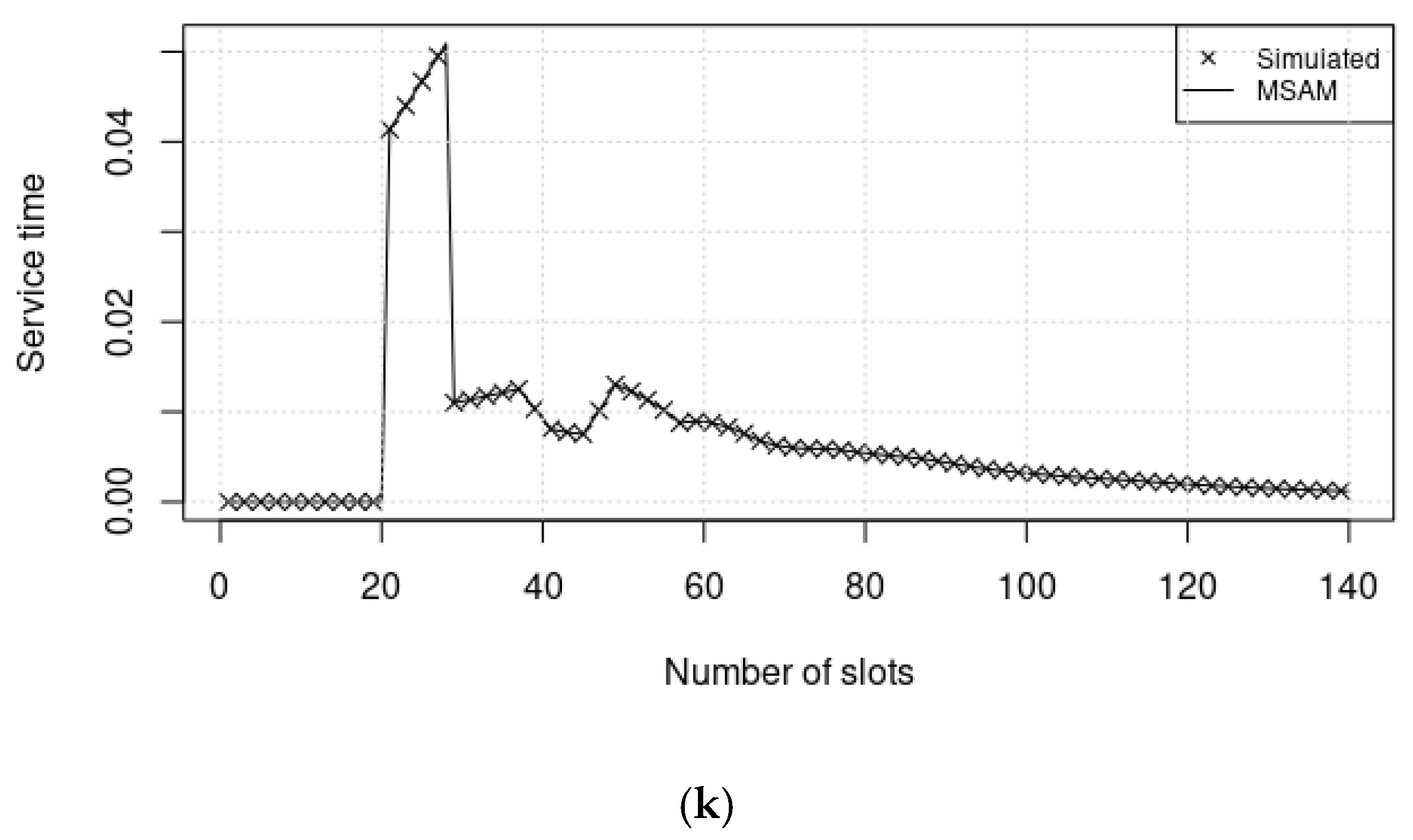
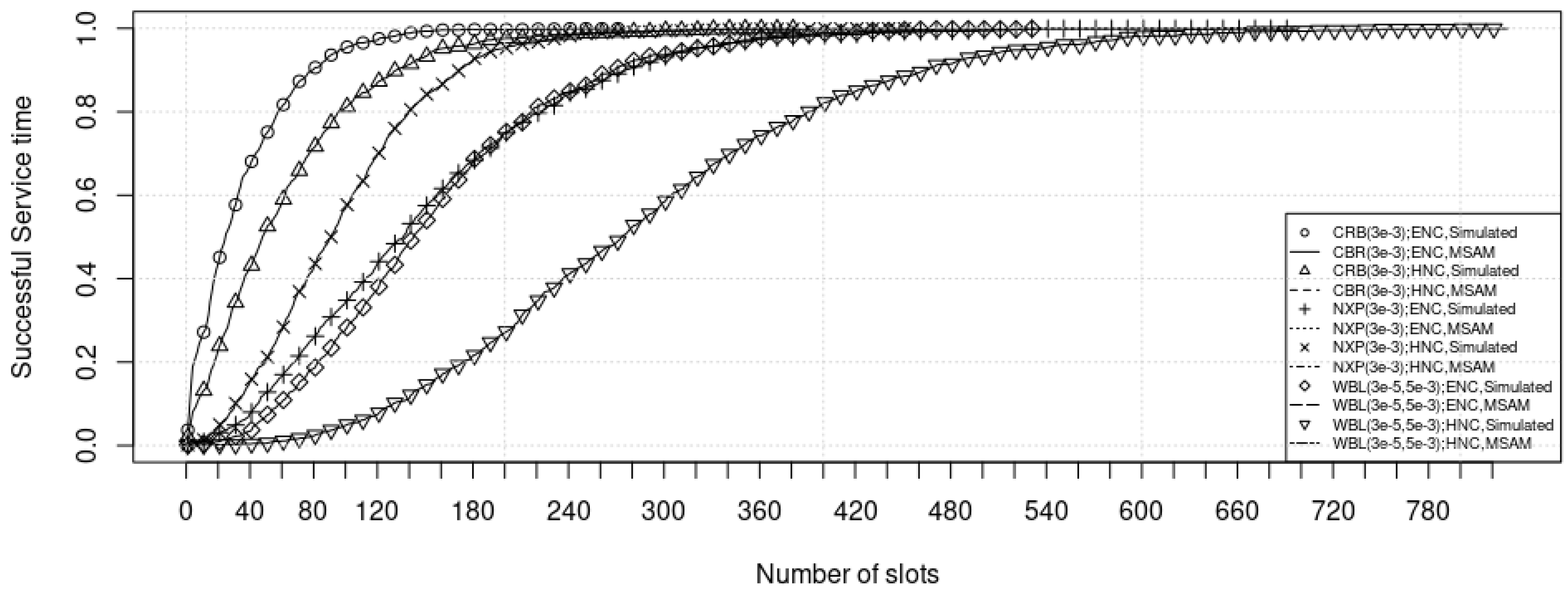
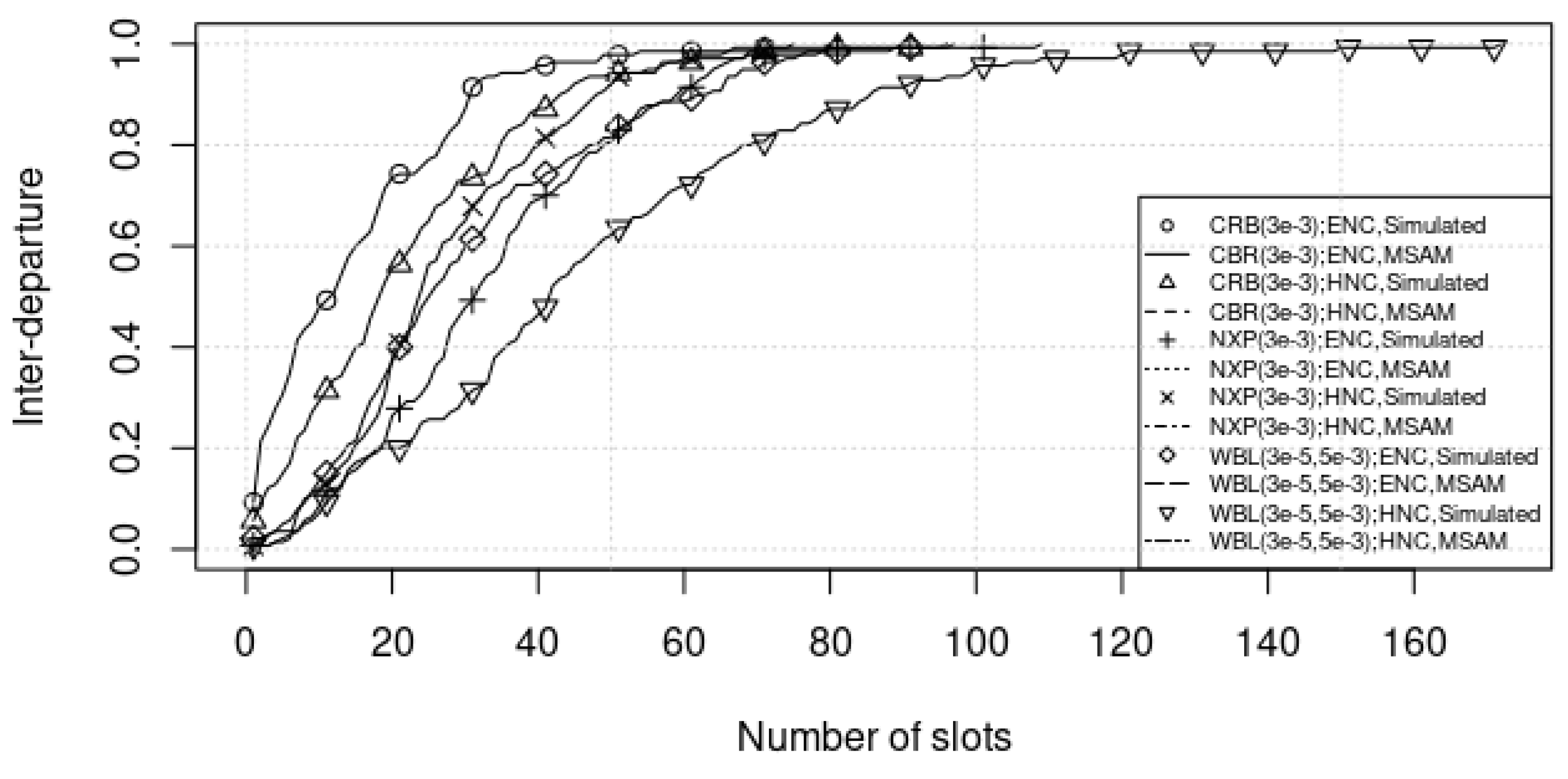
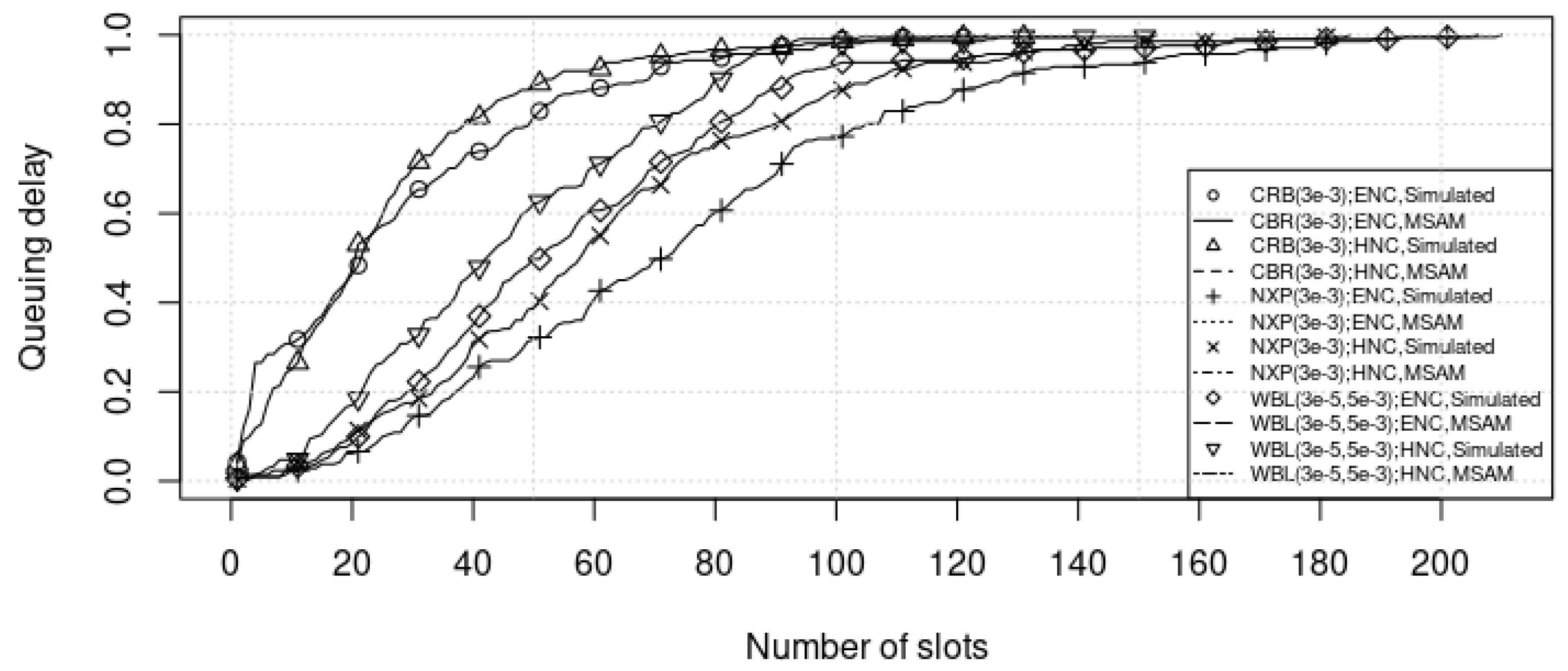
| Ref. | Traffic Pattern | Queuing Model | ICS Conditions | Methods | |
|---|---|---|---|---|---|
| ENC | HNC | ||||
| [16] | Exponential | - | √ | √ | Simulation |
| [17] | Not defined | - | √ | √ | Analytical |
| [18] | Saturated | - | √ | - | Simulation |
| [19] | Exponential | - | √ | - | Simulation |
| [20] | Saturation | - | √ | - | Semi-analytical |
| [21] | Exponential | M/G/1 | √ | - | Semi-analytical |
| [22] | Exponential | M/M/1/B | √ | Analytical | |
| MSAM | Several | G/G/1 | √ | √ | Analytical |
| Symbol | Description |
|---|---|
| Number of back-off stages. | |
| Number of back-off windows. | |
| The minimum number of back-off stages. | |
| The minimum number of back-off windows. | |
| The maximum number of back-off stages. | |
| The maximum number of back-off windows. | |
| The physical areas of the photodiode detector of the receiver. | |
| The distance between and . | |
| The order of Lambertian emission. | |
| The transmitter semi-angle at half power. | |
| The normal of the plan of node . | |
| The angle of the radiance of the light beam emitted from to the measured with respect to . | |
| The angle of incidence of the light beam emitted from to measured with respect to . | |
| The signal transmission coefficient of the optical filter of node due to the transmission to node . | |
| The receiver optical concentrator gain of node due to the transmission to node . | |
| The field of view of node . | |
| The transmission power of node . | |
| The power received to node due to transmission of node . | |
| The DC channel gain of transmission from towards the . | |
| The set of all exposed nodes of | |
| The receiver sensitivity of node . | |
| All Visible Light Nodes (VLNs) within a VLC network. | |
| Rate of spatial Poisson point process, VLNs/m2. | |
| PGF of the inter-arrival times of node . | |
| PGF of the service time distribution node . | |
| The average probability of assessment of the channel as idle by node . | |
| Utilisation factor of node . | |
| Inter-departure distribution of node . | |
| PFG of the queuing delay including queuing and service time of node . | |
| Successful service time distribution of node . | |
| PGF of the time required to drop a packet due to exceeding the number of busy channel assessments by node . | |
| Coefficient of variation of the inter-arrival distribution of node . | |
| Probability of transmission by node in an arbitrary slot. | |
| Probability of collision of node . | |
| Probability of lost a packet of . | |
| Throughput of the network. | |
| Length of a packet in slots. |
| Parameter | Value |
|---|---|
| Optical clock | 0.06 |
| Data rate | 96 Mbps |
| Modulation scheme | On-off keying (OOK) |
| Optical Clock Rate | 120 MHz |
| Physical mode | PHY II |
| Room dimension (length width height) m3 | 100 m3 |
| , NLNs/m2 | [5–30] |
| 0 | |
| 3 | |
| 4 | |
| 5 | |
| −36 dbm | |
| cm2 | |
| ° | |
| 10 | |
| [15–90]° | |
| Watt | |
| Maximum Transmission Unit (MTU) | 65,636 bits |
| VLN ID | Coordination | , watt | , cm2 | H(0) | ||
|---|---|---|---|---|---|---|
| 1 | [1.25,1.25,3] | ° | 15 | 1.5 | ||
| 2 | [1.25,3.75,3] | ° | 13 | 2.0 | ||
| 3 | [3.75,3.75,3] | ° | 12 | 1.5 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Baz, M.; Baz, A. MSAM: Modular Statistical Analytical Model for MAC and Queuing Latency of VLC Networks under ICS Conditions. Electronics 2021, 10, 1371. https://doi.org/10.3390/electronics10121371
Baz M, Baz A. MSAM: Modular Statistical Analytical Model for MAC and Queuing Latency of VLC Networks under ICS Conditions. Electronics. 2021; 10(12):1371. https://doi.org/10.3390/electronics10121371
Chicago/Turabian StyleBaz, Mohammed, and Abdullah Baz. 2021. "MSAM: Modular Statistical Analytical Model for MAC and Queuing Latency of VLC Networks under ICS Conditions" Electronics 10, no. 12: 1371. https://doi.org/10.3390/electronics10121371
APA StyleBaz, M., & Baz, A. (2021). MSAM: Modular Statistical Analytical Model for MAC and Queuing Latency of VLC Networks under ICS Conditions. Electronics, 10(12), 1371. https://doi.org/10.3390/electronics10121371






