Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective
Abstract
:1. Introduction
1.1. Purpose, Rationale and Structure of the Review
1.2. Notation
2. Modelling of CPSs Subject to Attacks
2.1. Modelling of the CPS Subject to Attacks by Using Deterministic Linear Descriptor Systems
Attack Detection and Identification
- only if there is actually an attack. Equivalently, , that is, false positives are excluded;
- if and only if (an internal coherency property of the detector);
- only if there is no other attack set , , such that there exists an initial state and an attack signal such that , (i.e., no other attack set with equal or smaller cardinality can “explain” the attack). If this cannot be assured, then it is .
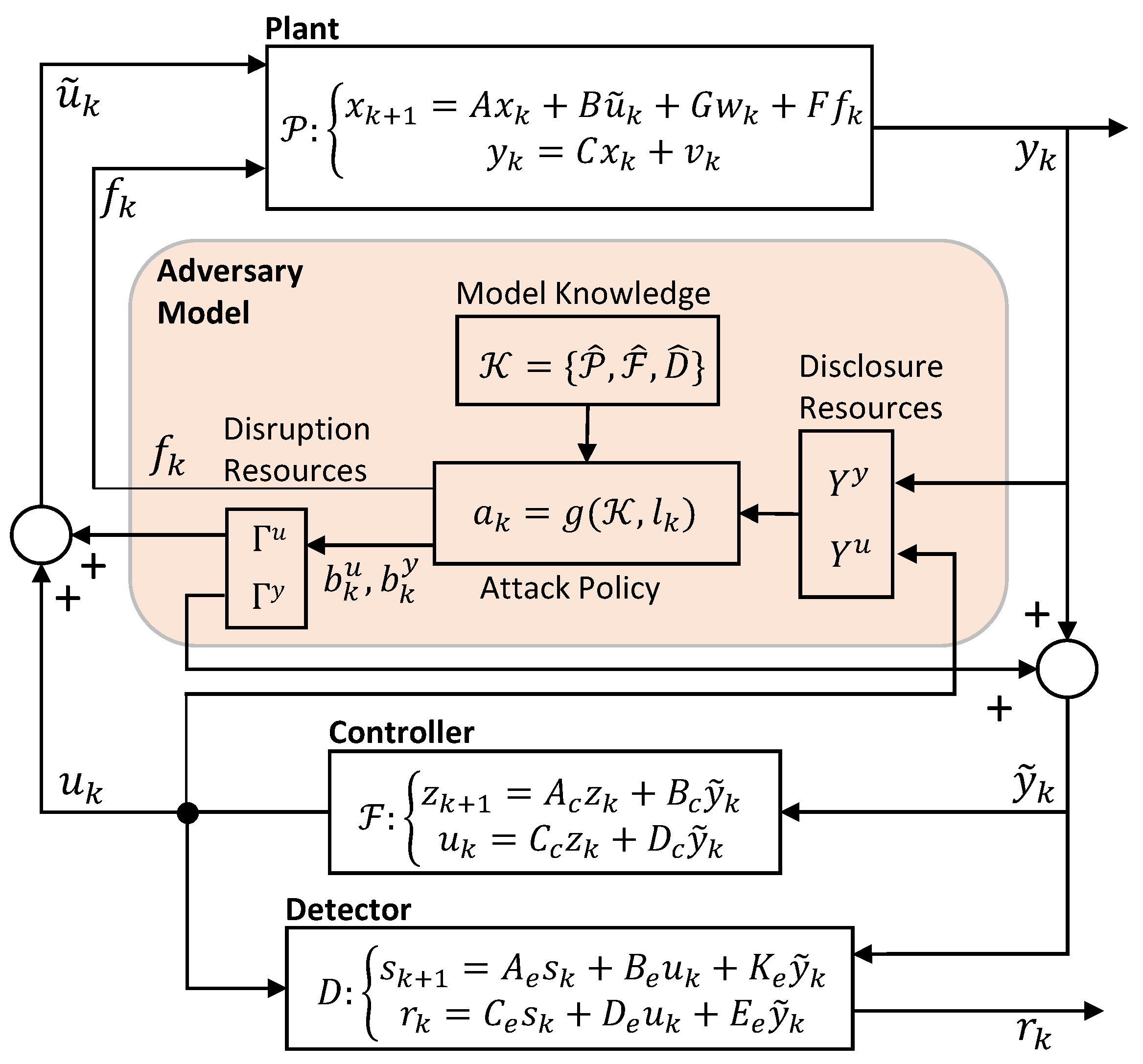
2.2. Modelling of Networked CPSs under Attack
2.2.1. Attack Space and Adversary Model
- The model knowledge, i.e., the adversary’s a priori knowledge about the CPS;
- The disclosure resources, i.e., the information that the attacker is able to retrieve about the system during the attack (violation of confidentiality);
- The disruption resources, i.e., integrity/availability violations through which the attacker compromises the system (e.g., through manipulation of the system’s control inputs, measurements, etc.).
2.2.2. Stealthy and Successful Attacks
2.3. Modelling of Basic Attacks
- Eavesdropping attacks, in which the adversary acquires some data transmitted in the CPS (3). The attacker posses only disclosure resources. These attacks are functional to collect the model knowledge needed to later carry out a disruptive attack;
- FDIAs (or data deception attacks), aimed at compromising the integrity of control and/or measurement packets, or some other information in the system. They can be modelled as in (4a) and (4b). In bias injection attacks, the attacker injects at steady state a constant bias in the communication channels, with the aim to cause disruption, while remaining undetected. Simple bias injection attacks only require disruption resources, and model knowledge, to optimize the bias value to be injected. More complex FDIAs include for example covert attacks [29], in which the attacker can alter the output of the system without being detected. Referring to Figure 2, this means in practice that the attacker can arbitrarily control system output , while keeping unaffected. Finally, in zero-dynamics attacks, the attack is designed so as to be decoupled from (i.e., have no impact on) the residual (see Section 3.12);
- DoS attacks [30] are meant to interrupt some or all of the communication channels in the system, making impossible for the sensor and/or the control data to reach the destination. As shown in [28], they can be modelled as FDIAs by properly selecting and in (4). No model knowledge and disclosure resources are needed to implement simple DoS attacks. The disruption resources are the data channel that the adversary is able to impact;
- In replay attacks [31], the attacker hijacks certain sensors, records readings from them for a certain amount of time, and then repeats (i.e., replays) the readings on the monitoring channels, while possibly injecting an exogenous signal into the system. Recording can be modelled as in (3), replay as in (4). Replay can have the purpose of covering simultaneous cyber-physical attacks, delay/impede detection, and so forth. Disclosure resources are the channels from which the attacker can record. The disruption resources are in general a subset of the disclosure resources, plus the physical attack resources modelled by F. No model knowledge is needed for the basic versions;
- In time delay attacks, the attacker injects delays in the sensing and actuating channels, with the aim of disrupting operations. In particular, delays can have a detrimental impact on the stability of the system. In time synchronization attacks, the attacker breaks synchronization of data and signals, which can be crucial for the correct functioning of the CPS (Section 3.14);
- In Structural Attacks/Tampering, the attacker physically alters the system, with the aim to cause disruption. The effect of the attack can be modelled as a change in the dynamics of the system, as represented in Figure 2, through the action of the attack signal .
3. Review of Cyber-Physical Attacks to the Smart Grid
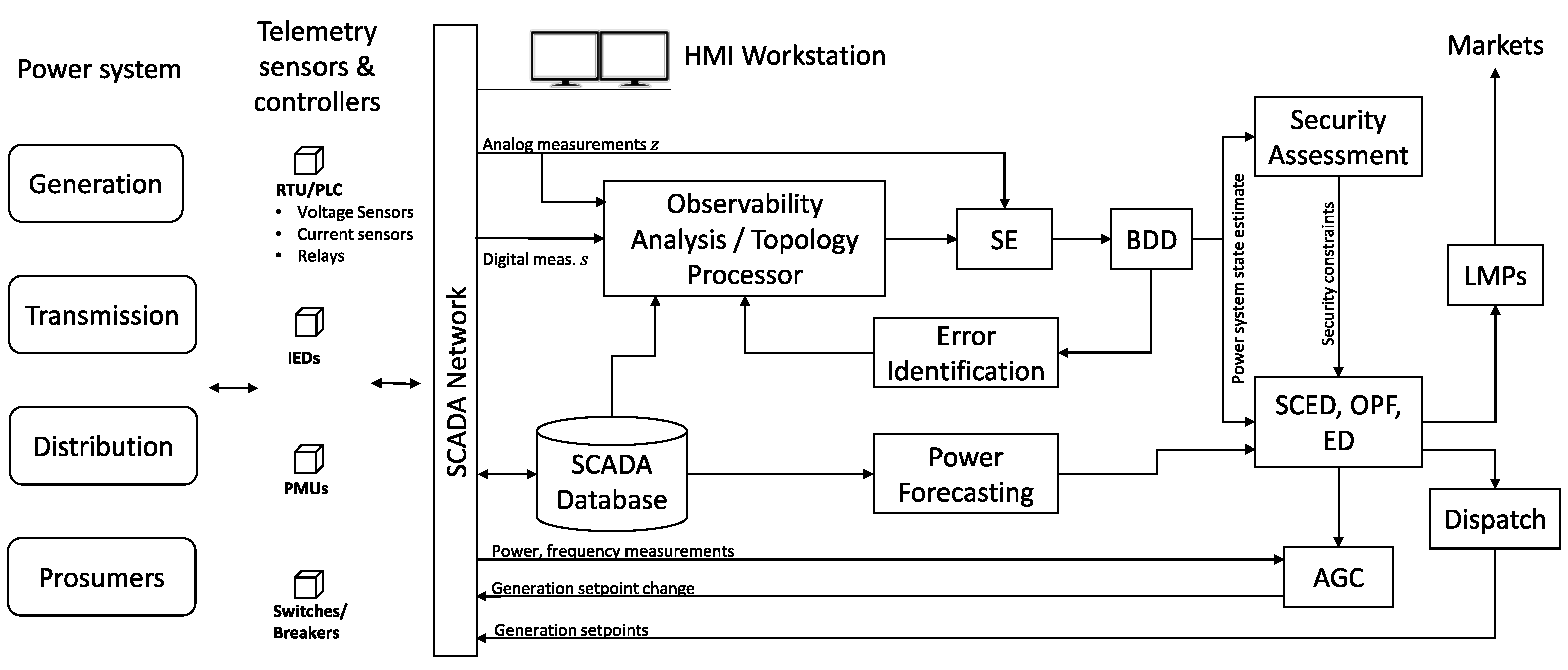
3.1. Reference Smart Grid Architecture for the Review
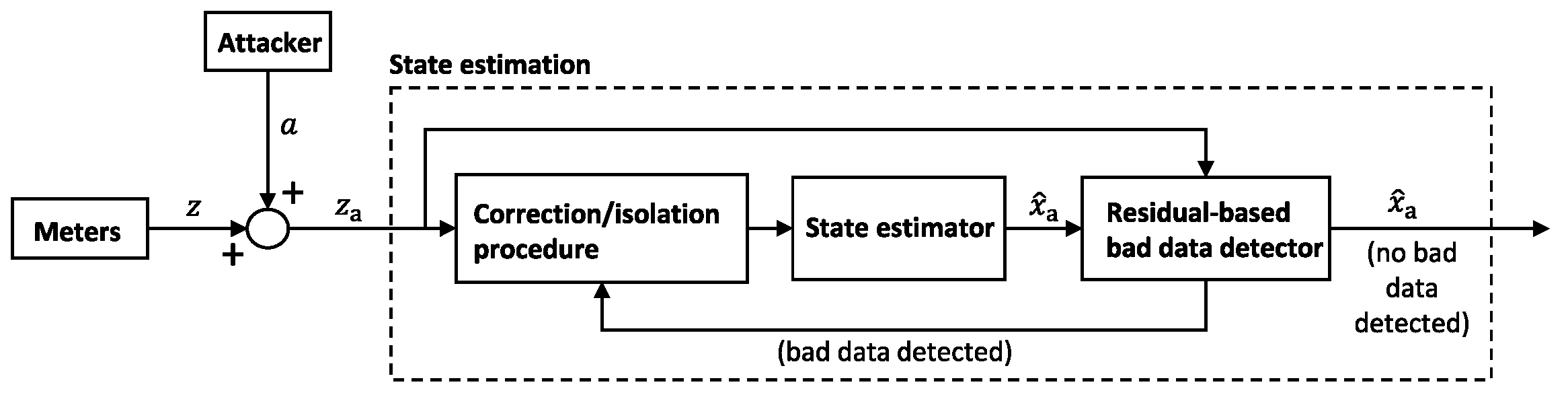
3.2. False Data Injection Attacks against State Estimation
3.2.1. Grid State Estimation
3.2.2. FDIA against DC State Estimation
3.2.3. Security Indices and Attacker-Defender Problem Design
- Protect a set of strategic measurements, so that they cannot be corrupted;
- Independently check a set of state variables, by directly measuring them with PMUs;
- Design more advanced detection methods.
3.2.4. Attack Design under Reduced Assumptions, PMU Measurements, and AC Models
3.3. Load Redistribution Attacks
3.4. Topology Attacks
3.4.1. Topology Attacks on SCED and Coordinated Cyber-Physical Topology Attacks
3.5. FDIA against Security Assessment, Contingency Analysis, SCED and Remedial Action Schemes
3.6. FDIA against Model Parameters
3.7. Attacks to Markets
3.7.1. Attack on the PJM Virtual Bidding Mechanism
- (easy to obtain based on historical data);
- is such that ;
- is such that .
3.7.2. Market Attacks with Limited Model Knowledge and Other Bi-Level Formulations
3.8. Attacks to Automatic Generation Control
3.9. Interdiction Attacks and Sequential Attacks
3.10. Switching Attacks
3.11. Load Altering Attacks
3.12. Zero Dynamics and Covert Attacks
3.13. Attacks against Automatic Voltage Control
3.14. Other Cyber-Physical Attacks
4. Discussion and Ongoing Research Directions
- A deeper understanding and analysis of known vulnerabilities and attack types, to evaluate to which extent attacks already documented in the literature can be formulated by relaxing assumptions on the attack model. It is normally the case in fact that, for the discovery and the first analysis of new vulnerabilities, researchers assume very broad and strong model knowledge and disclosure/disruption resources for attacker. For example, some works in literature have been discussed which use machine learning approaches, or tools from adaptive and robust control, to design attacks requiring reduced model knowledge and/or attack resources;
- Integration of more accurate models of the system under attack. It is often the case in fact that the early attack analysis are performed on simplified models, for example, typically on linearized models (e.g., DC models), while it is known that most of the smart grid systems are complex, nonlinear systems. The analysis with nonlinear (or, more in general, more detailed system models) is more complex, but could bring additional insights as well (as discussed for example for the case of FDIAs against SE and switching attacks).
- Combining attack models to generate complex, coordinated multi point-attacks. Concepts and tools used in the design of a given attack often find applications in the design of new attacks. As the analysis of known attacks reveals, in real, complex scenarios, different attack types can be combined with the aim of, for example, amplifying disruption, delaying the attack detection/identification, delaying response, mitigation and service restoration, and so forth.
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| AC | Alternating current |
| ACE | Area control error |
| AGC | Automatic generation control |
| AVC | Automatic voltage control |
| BDD | Bad data detection |
| CPS | Cyber-physical system |
| DC | Direct current |
| DoS | Denial of service |
| DLAA | Dynamic load altering attack |
| EMS | Energy management system |
| ESS | Energy storage system |
| FACTS | Flexible alternating current transmission system |
| FDIA | False data injection attack |
| GPS | Global positioning system |
| KKT | Karush–Kuhn–Tucker |
| LAA | Load altering attack |
| LFC | Load frequency control |
| LMP | Locational marginal price |
| LR | Load redistribution |
| MILP | Mixed integer linear programming |
| PV | Photovoltaic |
| PMU | Phasor measurement unit |
| PJM | Pennsylvania-New Jersey-Maryland |
| RAS | Remedial action scheme |
| RL | Reinforcement learning |
| SCADA | Supervisory control and data acquisition |
| SCED | Security-constrained economic dispatch |
| SE | State estimation |
| STATCOM | Static synchronous compensator |
| TA | Topology attack |
References
- Lee, E.A. Cyber physical systems: Design challenges. In Proceedings of the 2008 11th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), Orlando, FL, USA, 5–7 May 2008; pp. 363–369. [Google Scholar]
- Mrabet, Z.E.; Kaabouch, N.; Ghazi, H.E.; Ghazi, H.E. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef] [Green Version]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: A survey. IET-Cyber-Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef] [Green Version]
- Sun, C.C.; Liu, C.C.; Xie, J. Cyber-physical system security of a power grid: State-of-the-art. Electronics 2016, 5, 40. [Google Scholar] [CrossRef] [Green Version]
- Pandey, R.K.; Misra, M. Cyber security threats—Smart grid infrastructure. In Proceedings of the 2016 National Power Systems Conference (NPSC), Bhubaneswar, India, 19–21 December 2016; pp. 1–6. [Google Scholar]
- Ashok, A.; Govindarasu, M.; Wang, J. Cyber-physical attack-resilient wide-area monitoring, protection, and control for the power grid. Proc. IEEE 2017, 105, 1389–1407. [Google Scholar] [CrossRef]
- Sun, C.C.; Hahn, A.; Liu, C.C. Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- Otuoze, A.O.; Mustafa, M.W.; Larik, R.M. Smart grids security challenges: Classification by sources of threats. J. Electr. Syst. Inf. Technol. 2018, 5, 468–483. [Google Scholar] [CrossRef]
- Wadhawan, Y.; AlMajali, A.; Neuman, C. A comprehensive analysis of smart grid systems against cyber-physical attacks. Electronics 2018, 7, 249. [Google Scholar] [CrossRef] [Green Version]
- Weerakkody, S.; Sinopoli, B. Challenges and opportunities: Cyber-physical security in the smart grid. In Smart Grid Control; Springer: Berlin/Heidelberg, Germany, 2019; pp. 257–273. [Google Scholar]
- Gusrialdi, A.; Qu, Z. Smart grid security: Attacks and defenses. In Smart Grid Control; Springer: Berlin/Heidelberg, Germany, 2019; pp. 199–223. [Google Scholar]
- Lun, Y.Z.; D’Innocenzo, A.; Smarra, F.; Malavolta, I.; Di Benedetto, M.D. State of the art of cyber-physical systems security: An automatic control perspective. J. Syst. Softw. 2019, 149, 174–216. [Google Scholar]
- Ding, D.; Han, Q.L.; Xiang, Y.; Ge, X.; Zhang, X.M. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing 2018, 275, 1674–1683. [Google Scholar] [CrossRef]
- Aoufi, S.; Derhab, A.; Guerroumi, M. Survey of false data injection in smart power grid: Attacks, countermeasures and challenges. J. Inf. Secur. Appl. 2020, 54, 102518. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, B.; Wu, H. Smart Grid Cyber-Physical Attack and Defense: A Review. IEEE Access 2021, 9, 29641–29659. [Google Scholar] [CrossRef]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-physical energy systems security: Threat modeling, risk assessment, resources, metrics, and case studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- Giani, A.; Sastry, S.; Johansson, K.H.; Sandberg, H. The VIKING project: An initiative on resilient control of power networks. In Proceedings of the 2009 2nd International Symposium on Resilient Control Systems, Idaho Falls, ID, USA, 11–13 August 2009; pp. 31–35. [Google Scholar]
- SPEAR Website. Available online: https://cordis.europa.eu/project/id/787011 (accessed on 21 August 2020).
- ENERGY SHIELD Website. Available online: https://cordis.europa.eu/project/id/832907 (accessed on 21 August 2020).
- PHOENIX Website. Available online: https://cordis.europa.eu/project/id/832989 (accessed on 21 August 2020).
- DEFENDER Website. Available online: https://cordis.europa.eu/project/id/740898 (accessed on 21 August 2020).
- SDNmicroSENSE Website. Available online: https://cordis.europa.eu/project/id/833955 (accessed on 21 August 2020).
- SUCCESS Website. Available online: https://cordis.europa.eu/project/id/700416 (accessed on 21 August 2020).
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Cyber-physical attacks in power networks: Models, fundamental limitations and monitor design. In Proceedings of the 2011 50th IEEE Conference on Decision and Control and European Control Conference, Orlando, FL, USA, 12–15 December 2011; pp. 2195–2201. [Google Scholar] [CrossRef] [Green Version]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack Detection and Identification in Cyber-Physical Systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef] [Green Version]
- Pasqualetti, F.; Dorfler, F.; Bullo, F. Control-Theoretic Methods for Cyberphysical Security: Geometric Principles for Optimal Cross-Layer Resilient Control Systems. IEEE Control. Syst. Mag. 2015, 35, 110–127. [Google Scholar] [CrossRef]
- Chong, M.S.; Sandberg, H.; Teixeira, A.M.H. A Tutorial Introduction to Security and Privacy for Cyber-Physical Systems. In Proceedings of the 2019 18th European Control Conference (ECC), Naples, Italy, 25–28 June 2019; pp. 968–978. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef] [Green Version]
- Smith, R.S. A Decoupled Feedback Structure for Covertly Appropriating Networked Control Systems. IFAC Proc. Vol. 2011, 44, 90–95. [Google Scholar] [CrossRef] [Green Version]
- Amin, S.; Cárdenas, A.A.; Sastry, S.S. Safe and secure networked control systems under denial-of-service attacks. In International Workshop on Hybrid Systems: Computation and Control; Springer: Berlin/Heidelberg, Germany, 2009; pp. 31–45. [Google Scholar]
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the 2009 47th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Allerton House, IL, USA, 30 September–2 October 2009; pp. 911–918. [Google Scholar] [CrossRef] [Green Version]
- Kundur, P.; Balu, N.J.; Lauby, M.G. Power System Stability and Control; McGraw-Hill: New York, NY, USA, 1994; Volume 7. [Google Scholar]
- Abur, A.; Exposito, A.G. Power System State Estimation: Theory and Implementation; CRC Press: Boca Raton, FL, USA, 2004. [Google Scholar]
- Liu, Y.; Ning, P.; Reiter, M. False data injection attacks against state estimation in electric power grids. In Proceedings of the CCS’09 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 21–32. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False Data Injection Attacks Against State Estimation in Electric Power Grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 13:1–13:33. [Google Scholar] [CrossRef]
- Rahman, M.A.; Mohsenian-Rad, H. False data injection attacks against nonlinear state estimation in smart power grids. In Proceedings of the 2013 IEEE Power Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Kosut, O.; Jia, L.; Thomas, R.J.; Tong, L. Malicious Data Attacks on the Smart Grid. IEEE Trans. Smart Grid 2011, 2, 645–658. [Google Scholar] [CrossRef] [Green Version]
- Deng, R.; Xiao, G.; Lu, R.; Liang, H.; Vasilakos, A.V. False data injection on state estimation in power systems—Attacks, impacts, and defense: A survey. IEEE Trans. Ind. Inform. 2016, 13, 411–423. [Google Scholar] [CrossRef]
- Liu, T.; Sun, Y.; Liu, Y.; Gui, Y.; Zhao, Y.; Wang, D.; Shen, C. Abnormal traffic-indexed state estimation: A cyber–physical fusion approach for smart grid attack detection. Future Gener. Comput. Syst. 2015, 49, 94–103. [Google Scholar] [CrossRef]
- Haider, A.; Khan, M.A.; Rehman, A.; Rahman, M.U.; Kim, H.S. A Real-Time Sequential Deep Extreme Learning Machine Cybersecurity Intrusion Detection System. CMC-Comput. Mater. Contin. 2021, 66, 1785–1798. [Google Scholar] [CrossRef]
- Kim, J.; Tong, L. On Topology Attack of a Smart Grid: Undetectable Attacks and Countermeasures. IEEE J. Sel. Areas Commun. 2013, 31, 1294–1305. [Google Scholar] [CrossRef]
- Giani, A.; Bitar, E.; Garcia, M.; McQueen, M.; Khargonekar, P.; Poolla, K. Smart Grid Data Integrity Attacks. IEEE Trans. Smart Grid 2013, 4, 1244–1253. [Google Scholar] [CrossRef]
- Zhang, J.; Chu, Z.; Sankar, L.; Kosut, O. False data injection attacks on phasor measurements that bypass low-rank decomposition. In Proceedings of the 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm), Dresden, Germany, 23–26 October 2017; pp. 96–101. [Google Scholar] [CrossRef] [Green Version]
- Yang, Q.; Chang, L.; Yu, W. On false data injection attacks against Kalman filtering in power system dynamic state estimation. Secur. Commun. Netw. 2016, 9, 833–849. [Google Scholar] [CrossRef]
- Karimipour, H.; Dinavahi, V. On false data injection attack against dynamic state estimation on smart power grids. In Proceedings of the 2017 IEEE International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 14–17 August 2017; pp. 388–393. [Google Scholar]
- Nath, S.; Akingeneye, I.; Wu, J.; Han, Z. Quickest detection of false data injection attacks in smart grid with dynamic models. IEEE J. Emerg. Sel. Top. Power Electron. 2019. [Google Scholar] [CrossRef]
- Song, Y.; Liu, X.; Li, Z.; Shahidehpour, M.; Li, Z. Intelligent data attacks against power systems using incomplete network information: A review. J. Mod. Power Syst. Clean Energy 2018, 6, 630–641. [Google Scholar] [CrossRef] [Green Version]
- Cao, Y.; Li, Y.; Liu, X.; Rehtanz, C. Local False Data Injection Attacks with Incomplete Network Information. In Cyber-Physical Energy and Power Systems; Springer: Berlin/Heidelberg, Germany, 2020; pp. 177–199. [Google Scholar]
- Zhang, J.; Chu, Z.; Sankar, L.; Kosut, O. Can Attackers with Limited Information Exploit Historical Data to Mount Successful False Data Injection Attacks on Power Systems? IEEE Trans. Power Syst. 2018, 33, 4775–4786. [Google Scholar] [CrossRef] [Green Version]
- Li, Q.; Cui, D.; Liu, M. Data-Driven False Data Injection Attacks on State Estimation in Smart Grid. In Proceedings of the 2018 37th Chinese Control Conference (CCC), Wuhan, China, 25–27 July 2018; pp. 6190–6195. [Google Scholar]
- Tian, J.; Wang, B.; Li, X. Data-driven and low-sparsity false data injection attacks in smart grid. Secur. Commun. Netw. 2018, 2018, 8045909. [Google Scholar] [CrossRef]
- Hug, G.; Giampapa, J.A. Vulnerability assessment of AC state estimation with respect to false data injection cyber-attacks. IEEE Trans. Smart Grid 2012, 3, 1362–1370. [Google Scholar] [CrossRef] [Green Version]
- Jin, M.; Lavaei, J.; Johansson, K.H. Power grid AC-based state estimation: Vulnerability analysis against cyber attacks. IEEE Trans. Autom. Control 2018, 64, 1784–1799. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z. False Data Attacks Against AC State Estimation with Incomplete Network Information. IEEE Trans. Smart Grid 2017, 8, 2239–2248. [Google Scholar] [CrossRef]
- Nayak, J.; Al-Anbagi, I. Modelling False Data Injection Attacks Against Non-linear State Estimation in AC Power Systems. In Proceedings of the 2020 8th International Conference on Smart Grid (icSmartGrid), Paris, France, 17–19 June 2020; pp. 37–42. [Google Scholar]
- Yang, Q.; Jiang, L.; Hao, W.; Zhou, B.; Yang, P.; Lv, Z. PMU placement in electric transmission networks for reliable state estimation against false data injection attacks. IEEE Internet Things J. 2017, 4, 1978–1986. [Google Scholar] [CrossRef] [Green Version]
- Alexopoulos, T.A.; Korres, G.N.; Manousakis, N.M. Complementarity reformulations for false data injection attacks on PMU-only state estimation. Electr. Power Syst. Res. 2020, 189, 106796. [Google Scholar] [CrossRef]
- Ayad, A.; Farag, H.; Youssef, A.; El-Saadany, E. Cyber–physical attacks on power distribution systems. IET Cyber-Phys. Syst. Theory Appl. 2020, 5, 218–225. [Google Scholar] [CrossRef]
- Bhattar, P.L.; Pindoriya, N.M.; Sharma, A. A combined survey on distribution system state estimation and false data injection in cyber-physical power distribution networks. IET-Cyber-Phys. Syst. Theory Appl. 2021. [Google Scholar] [CrossRef]
- Primadianto, A.; Lu, C.N. A review on distribution system state estimation. IEEE Trans. Power Syst. 2016, 32, 3875–3883. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Quantitative Analysis of Load Redistribution Attacks in Power Systems. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1731–1738. [Google Scholar] [CrossRef]
- Yang, L.; Zhang, X.; Li, Z.; Li, Z.; He, Y. Detecting Bi-level False Data Injection Attack Based on Time Series Analysis Method in Smart Grid. Comput. Secur. 2020, 96, 101899. [Google Scholar] [CrossRef]
- He, H.; Huang, S.; Liu, Y.; Zhang, T. A tri-level optimization model for power grid defense with the consideration of post-allocated DGs against coordinated cyber-physical attacks. Int. J. Electr. Power Energy Syst. 2021, 130, 106903. [Google Scholar] [CrossRef]
- Pan, K.; Teixeira, A.; Cvetkovic, M.; Palensky, P. Cyber risk analysis of combined data attacks against power system state estimation. IEEE Trans. Smart Grid 2018, 10, 3044–3056. [Google Scholar] [CrossRef] [Green Version]
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. A Framework for Cyber-topology Attacks: Line-switching and New Attack Scenarios. IEEE Trans. Smart Grid 2017, 10, 1704–1712. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z.; Liu, X.; Li, Z. Masking Transmission Line Outages via False Data Injection Attacks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1592–1602. [Google Scholar] [CrossRef]
- Chung, H.; Li, W.; Yuen, C.; Chung, W.; Zhang, Y.; Wen, C. Local Cyber-Physical Attack for Masking Line Outage and Topology Attack in Smart Grid. IEEE Trans. Smart Grid 2018, 10, 4577–4588. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; He, H.; Wan, Z.; Sun, Y.L. Coordinated Topology Attacks in Smart Grid Using Deep Reinforcement Learning. IEEE Trans. Ind. Inform. 2020, 17, 1407–1415. [Google Scholar] [CrossRef]
- Tian, J.; Wang, B.; Li, T.; Shang, F.; Cao, K. Coordinated cyber-physical attacks considering DoS attacks in power systems. Int. J. Robust Nonlinear Control 2020, 30, 4345–4358. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z. Local Topology Attacks in Smart Grids. IEEE Trans. Smart Grid 2017, 8, 2617–2626. [Google Scholar] [CrossRef]
- Jiongcong, C.; Liang, G.; Zexiang, C.; Chunchao, H.; Yan, X.; Fengji, L.; Junhua, Z. Impact analysis of false data injection attacks on power system static security assessment. J. Mod. Power Syst. Clean Energy 2016, 4, 496–505. [Google Scholar]
- Kang, J.; Joo, I.; Choi, D. False Data Injection Attacks on Contingency Analysis: Attack Strategies and Impact Assessment. IEEE Access 2018, 6, 8841–8851. [Google Scholar] [CrossRef]
- Khanna, K.; Panigrahi, B.K.; Joshi, A. Bi-level modelling of false data injection attacks on security constrained optimal power flow. IET Gener. Transm. Distrib. 2017, 11, 3586–3593. [Google Scholar] [CrossRef] [Green Version]
- Basumallik, S.; Eftekharnejad, S.; Johnson, B.K. The impact of false data injection attacks against remedial action schemes. Int. J. Electr. Power Energy Syst. 2020, 123, 106225. [Google Scholar] [CrossRef]
- Jahromi, A.A.; Kemmeugne, A.; Kundur, D.; Haddadi, A. Cyber-Physical Attacks Targeting Communication-Assisted Protection Schemes. IEEE Trans. Power Syst. 2020, 35, 440–450. [Google Scholar] [CrossRef]
- Zou, T.; Bretas, A.S.; Ruben, C.; Dhulipala, S.C.; Bretas, N. Smart grids cyber-physical security: Parameter correction model against unbalanced false data injection attacks. Electr. Power Syst. Res. 2020, 187, 106490. [Google Scholar] [CrossRef]
- Bretas, A.S.; Bretas, N.G.; Carvalho, B.E. Further contributions to smart grids cyber-physical security as a malicious data attack: Proof and properties of the parameter error spreading out to the measurements and a relaxed correction model. Int. J. Electr. Power Energy Syst. 2019, 104, 43–51. [Google Scholar] [CrossRef]
- Liu, C.; Liang, H.; Chen, T. Network Parameter Coordinated False Data Injection Attacks against Power System AC State Estimation. IEEE Trans. Smart Grid 2020. [Google Scholar] [CrossRef]
- Xie, L.; Mo, Y.; Sinopoli, B. Integrity Data Attacks in Power Market Operations. IEEE Trans. Smart Grid 2011, 2, 659–666. [Google Scholar] [CrossRef]
- Mengis, M.R.; Tajer, A. Data injection attacks on electricity markets by limited adversaries: Worst-case robustness. IEEE Trans. Smart Grid 2017, 9, 5710–5720. [Google Scholar] [CrossRef]
- Ahmadian, S.; Tang, X.; Malki, H.A.; Han, Z. Modelling cyber attacks on electricity market using mathematical programming with equilibrium constraints. IEEE Access 2019, 7, 27376–27388. [Google Scholar] [CrossRef]
- Xu, H.; Lin, Y.; Zhang, X.; Wang, F. Power system parameter attack for financial profits in electricity markets. IEEE Trans. Smart Grid 2020, 11, 3438–3446. [Google Scholar] [CrossRef]
- Mohajerin Esfahani, P.; Vrakopoulou, M.; Margellos, K.; Lygeros, J.; Andersson, G. Cyber attack in a two-area power system: Impact identification using reachability. In Proceedings of the 2010 American Control Conference, Baltimore, MD, USA, 30 June–2 July 2010; pp. 962–967. [Google Scholar]
- Sargolzaei, A.; Yen, K.; Abdelghani, M. Delayed inputs attack on load frequency control in smart grid. In Proceedings of the ISGT 2014, Washington, DC, USA, 19–22 February 2014; pp. 1–5. [Google Scholar] [CrossRef]
- De Pace, G.; Wang, Z.; Benin, J.; He, H.; Sun, Y.L. Evaluation of Communication Delay Based Attack Against the Smart Grid. In Proceedings of the 2020 IEEE Kansas Power and Energy Conference (KPEC), Manhattan, KS, USA, 14 April 2020; pp. 1–6. [Google Scholar]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-service (DoS) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 16–18 February 2013; pp. 1–6. [Google Scholar]
- Sridhar, S.; Govindarasu, M. Model-Based Attack Detection and Mitigation for Automatic Generation Control. IEEE Trans. Smart Grid 2014, 5, 580–591. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.S.; Yau, D.K.Y.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Modeling and Mitigating Impact of False Data Injection Attacks on Automatic Generation Control. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1609–1624. [Google Scholar] [CrossRef]
- Wu, Y.; Wei, Z.; Weng, J.; Li, X.; Deng, R.H. Resonance Attacks on Load Frequency Control of Smart Grids. IEEE Trans. Smart Grid 2018, 9, 4490–4502. [Google Scholar] [CrossRef]
- Mohan, A.M.; Meskin, N.; Mehrjerdi, H. A Comprehensive Review of the Cyber-Attacks and Cyber-Security on Load Frequency Control of Power Systems. Energies 2020, 13, 3860. [Google Scholar] [CrossRef]
- Salmeron, J.; Wood, K.; Baldick, R. Analysis of electric grid security under terrorist threat. IEEE Trans. Power Syst. 2004, 19, 905–912. [Google Scholar] [CrossRef] [Green Version]
- Motto, A.L.; Arroyo, J.M.; Galiana, F.D. A mixed-integer LP procedure for the analysis of electric grid security under disruptive threat. IEEE Trans. Power Syst. 2005, 20, 1357–1365. [Google Scholar] [CrossRef]
- Arroyo, J.M.; Galiana, F.D. On the solution of the bilevel programming formulation of the terrorist threat problem. IEEE Trans. Power Syst. 2005, 20, 789–797. [Google Scholar] [CrossRef]
- Yao, Y.; Edmunds, T.; Papageorgiou, D.; Alvarez, R. Trilevel Optimization in Power Network Defense. IEEE Trans. Syst. Man Cybern. Part Appl. Rev. 2007, 37, 712–718. [Google Scholar] [CrossRef]
- Salmeron, J.; Wood, K.; Baldick, R. Worst-Case Interdiction Analysis of Large-Scale Electric Power Grids. IEEE Trans. Power Syst. 2009, 24, 96–104. [Google Scholar] [CrossRef] [Green Version]
- Yan, J.; Tang, Y.; Zhu, Y.; He, H.; Sun, Y. Smart Grid Vulnerability under Cascade-Based Sequential Line-Switching Attacks. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar]
- Zhu, Y.; Yan, J.; Tang, Y.; Sun, Y.L.; He, H. Resilience Analysis of Power Grids Under the Sequential Attack. IEEE Trans. Inf. Forensics Secur. 2014, 9, 2340–2354. [Google Scholar] [CrossRef]
- Yan, J.; He, H.; Zhong, X.; Tang, Y. Q-Learning-Based Vulnerability Analysis of Smart Grid Against Sequential Topology Attacks. IEEE Trans. Inf. Forensics Secur. 2017, 12, 200–210. [Google Scholar] [CrossRef]
- Liu, S.; Feng, X.; Kundur, D.; Zourntos, T.; Butler-Purry, K.L. Switched system models for coordinated cyber-physical attack construction and simulation. In Proceedings of the 2011 IEEE First International Workshop on Smart Grid Modeling and Simulation (SGMS), Brussels, Belgium, 17 October 2011; pp. 49–54. [Google Scholar] [CrossRef]
- Liu, S.; Feng, X.; Kundur, D.; Zourntos, T.; Butler-Purry, K. A Class of Cyber-physical Switching Attacks for Power System Disruption. In Proceedings of the CSIIRW’11, Seventh Annual Workshop on Cyber Security and Information Intelligence Research, Oak Ridge, TN, USA, 12–14 October 2011; ACM: New York, NY, USA, 2011; p. 16. [Google Scholar] [CrossRef]
- Liu, S.; Mashayekh, S.; Kundur, D.; Zourntos, T.; Butler-Purry, K.L. A smart grid vulnerability analysis framework for coordinated variable structure switching attacks. In Proceedings of the 2012 IEEE Power and Energy Society General Meeting, San Diego, CA, USA, 22–26 July 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, S.; Mashayekh, S.; Kundur, D.; Zourntos, T.; Butler-Purry, K. A Framework for Modeling Cyber-Physical Switching Attacks in Smart Grid. IEEE Trans. Emerg. Top. Comput. 2013, 1, 273–285. [Google Scholar] [CrossRef]
- Liu, S.; Chen, B.; Zourntos, T.; Kundur, D.; Butler-Purry, K. A Coordinated Multi-Switch Attack for Cascading Failures in Smart Grid. IEEE Trans. Smart Grid 2014, 5, 1183–1195. [Google Scholar] [CrossRef]
- Farraj, A.K.; Kundur, D. On using energy storage systems in switching attacks that destabilize smart grid systems. In Proceedings of the 2015 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 16–18 February 2015; pp. 1–5. [Google Scholar]
- Patel, A.; Purwar, S. Switching attacks on smart grid using non-linear sliding surface. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 382–392. [Google Scholar] [CrossRef]
- Yamashita, K.; Ten, C.W.; Rho, Y.; Wang, L.; Wei, W.; Ginter, A.F. Measuring systemic risk of switching attacks based on cybersecurity technologies in substations. IEEE Trans. Power Syst. 2020, 35, 4206–4219. [Google Scholar] [CrossRef]
- Arani, M.F.; Jahromi, A.A.; Kundur, D.; Kassouf, M. Modeling and simulation of the aurora attack on microgrid point of common coupling. In Proceedings of the 2019 7th Workshop on Modeling and Simulation of Cyber-Physical Energy Systems (MSCPES), Montreal, QC, Canada, 15 April 2019; pp. 1–6. [Google Scholar]
- Mohsenian-Rad, A.; Leon-Garcia, A. Distributed Internet-Based Load Altering Attacks Against Smart Power Grids. IEEE Trans. Smart Grid 2011, 2, 667–674. [Google Scholar] [CrossRef]
- Amini, S.; Pasqualetti, F.; Mohsenian-Rad, H. Dynamic Load Altering Attacks Against Power System Stability: Attack Models and Protection Schemes. IEEE Trans. Smart Grid 2018, 9, 2862–2872. [Google Scholar] [CrossRef]
- Xun, P.; Zhu, P.D.; Maharjan, S.; Cui, P.S. Successive direct load altering attack in smart grid. Comput. Secur. 2018, 77, 79–93. [Google Scholar] [CrossRef]
- Yankson, S.; Ghamkhari, M. Transactive energy to thwart load altering attacks on power distribution systems. Future Internet 2020, 12, 4. [Google Scholar] [CrossRef] [Green Version]
- Germanà, R.; Giuseppi, A.; Di Giorgio, A. Ensuring the Stability of Power Systems Against Dynamic Load Altering Attacks: A Robust Control Scheme Using Energy Storage Systems. In Proceedings of the 2020 European Control Conference (ECC), St. Petersburg, Russia, 29 June–2 July 2020; pp. 1330–1335. [Google Scholar]
- Wu, G.; Wang, G.; Sun, J.; Chen, J. Optimal partial feedback attacks in cyber-physical power systems. IEEE Trans. Autom. Control 2020, 65, 3919–3926. [Google Scholar] [CrossRef]
- Arnaboldi, L.; Czekster, R.M.; Morisset, C.; Metere, R. Modelling Load-Changing Attacks in Cyber-Physical Systems. Electron. Notes Theor. Comput. Sci. 2020, 353, 39–60. [Google Scholar] [CrossRef]
- Byrnes, C.I.; Isidori, A. A frequency domain philosophy for nonlinear systems, with applications to stabilization and to adaptive control. In Proceedings of the 23rd IEEE Conference on Decision and Control, Las Vegas, NV, USA, 12–14 December 1984; pp. 1569–1573. [Google Scholar]
- Park, G.; Shim, H.; Lee, C.; Eun, Y.; Johansson, K.H. When adversary encounters uncertain cyber-physical systems: Robust zero-dynamics attack with disclosure resources. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016; pp. 5085–5090. [Google Scholar]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. Revealing stealthy attacks in control systems. In Proceedings of the 2012 50th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 1–5 October 2012; pp. 1806–1813. [Google Scholar] [CrossRef] [Green Version]
- Di Giorgio, A.; Pietrabissa, A.; DelliPriscoli, F.; Isidori, A. Robust protection scheme against cyber-physical attacks in power systems. IET Control. Theory Appl. 2018, 12, 1792–1801. [Google Scholar] [CrossRef] [Green Version]
- Shim, H.; Park, G.; Joo, Y.; Back, J.; Jo, N.H. Yet another tutorial of disturbance observer: Robust stabilization and recovery of nominal performance. Control. Theory Technol. 2016, 14, 237–249. [Google Scholar] [CrossRef] [Green Version]
- Ao, W.; Song, Y.; Wen, C. Adaptive cyber-physical system attack detection and reconstruction with application to power systems. IET Control. Theory Appl. 2016, 10, 1458–1468. [Google Scholar] [CrossRef]
- Keller, J.Y.; Sauter, D. Monitoring of stealthy attack in networked control systems. In Proceedings of the Control and Fault-Tolerant Systems (SysTol), Nice, France, 9–11 October 2013; pp. 462–467. [Google Scholar]
- Hoehn, A.; Zhang, P. Detection of covert attacks and zero dynamics attacks in cyber-physical systems. In Proceedings of the American Control Conference (ACC), Boston, MA, USA, 6–8 July 2016; pp. 302–307. [Google Scholar]
- Freidovich, L.B.; Khalil, H.K. Performance Recovery of Feedback-Linearization-Based Designs. IEEE Trans. Autom. Control. 2008, 53, 2324–2334. [Google Scholar] [CrossRef]
- Wang, L.; Isidori, A.; Su, H. Output feedback stabilization of nonlinear MIMO systems having uncertain high-frequency gain matrix. Syst. Control. Lett. 2015, 83, 1–8. [Google Scholar] [CrossRef]
- Sridhar, S.; Manimaran, G. Data integrity attack and its impacts on voltage control loop in power grid. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–6. [Google Scholar]
- Chen, B.; Mashayekh, S.; Butler-Purry, K.L.; Kundur, D. Impact of cyber attacks on transient stability of smart grids with voltage support devices. In Proceedings of the 2013 IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Teixeira, A.; Dán, G.; Sandberg, H.; Berthier, R.; Bobba, R.B.; Valdes, A. Security of smart distribution grids: Data integrity attacks on integrated volt/VAR control and countermeasures. In Proceedings of the 2014 American Control Conference, Portland, OR, USA, 4–6 June 2014; pp. 4372–4378. [Google Scholar]
- Chen, Y.; Huang, S.; Liu, F.; Wang, Z.; Sun, X. Evaluation of reinforcement learning-based false data injection attack to automatic voltage control. IEEE Trans. Smart Grid 2018, 10, 2158–2169. [Google Scholar] [CrossRef]
- Isozaki, Y.; Yoshizawa, S.; Fujimoto, Y.; Ishii, H.; Ono, I.; Onoda, T.; Hayashi, Y. Detection of cyber attacks against voltage control in distribution power grids with PVs. IEEE Trans. Smart Grid 2015, 7, 1824–1835. [Google Scholar] [CrossRef]
- Cameron, C.; Patsios, C.; Taylor, P.C.; Pourmirza, Z. Using Self-Organizing Architectures to Mitigate the Impacts of Denial-of-Service Attacks on Voltage Control Schemes. IEEE Trans. Smart Grid 2019, 10, 3010–3019. [Google Scholar] [CrossRef] [Green Version]
- Teixeira, A.; Paridari, K.; Sandberg, H.; Johansson, K.H. Voltage control for interconnected microgrids under adversarial actions. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Ghafouri, M.; Au, M.; Kassouf, M.; Debbabi, M.; Assi, C.; Yan, J. Detection and mitigation of cyber attacks on voltage stability monitoring of smart grids. IEEE Trans. Smart Grid 2020, 11, 5227–5238. [Google Scholar] [CrossRef]
- Zhang, Z.; Gong, S.; Dimitrovski, A.D.; Li, H. Time synchronization attack in smart grid: Impact and analysis. IEEE Trans. Smart Grid 2013, 4, 87–98. [Google Scholar] [CrossRef]
- Liu, Y.; Hu, S.; Ho, T.Y. Leveraging strategic detection techniques for smart home pricing cyberattacks. IEEE Trans. Dependable Secur. Comput. 2015, 13, 220–235. [Google Scholar] [CrossRef]
- Brown, H.E.; DeMarco, C.L. A Cautionary Tale: On the Effectiveness of Inertia-Emulating Load as a Cyber-Physical Attack Path. In Energy Markets and Responsive Grids; Springer: New York, NY, USA, 2018. [Google Scholar]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liberati, F.; Garone, E.; Di Giorgio, A. Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective. Electronics 2021, 10, 1153. https://doi.org/10.3390/electronics10101153
Liberati F, Garone E, Di Giorgio A. Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective. Electronics. 2021; 10(10):1153. https://doi.org/10.3390/electronics10101153
Chicago/Turabian StyleLiberati, Francesco, Emanuele Garone, and Alessandro Di Giorgio. 2021. "Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective" Electronics 10, no. 10: 1153. https://doi.org/10.3390/electronics10101153
APA StyleLiberati, F., Garone, E., & Di Giorgio, A. (2021). Review of Cyber-Physical Attacks in Smart Grids: A System-Theoretic Perspective. Electronics, 10(10), 1153. https://doi.org/10.3390/electronics10101153







