A Public Platform for Virtual IoT-Based Monitoring and Tracking of COVID-19
Abstract
1. Introduction
- Legalization of location tracking: South Korea’s large-scale diagnosis of COVID-19 suspects and the unveiling of a full moving line of COVID-19 confirmed cases surprised world health experts [7,8]. In 2015, after the Mers (Middle east respiratory syndrome) crisis, South Korea institutionalized tracking the path of the infected [9]. Since then, it is now possible for health authorities to use location information without their consent, if necessary, for preventing infection. It is essential to establish a location tracking system based on the safety plates to track the suspected legally. This paper is based on the following legal aspects: the Center for Disease Control and Prevention (CDC) manages a list of people who needs to be monitored related to the COVID-19 and forcibly installs virtual Internet of Things (vIoT) nodes in the form of applications on their smartphones.
- Public platforms used by the world: In the unpredictable circumstances of COVID-19’s cause and development, organizations operating under secret central control, which hides some information, have exposed instability and failed to help overcome the COVID-19 crisis. Secrecy and authoritarianism may be useful in preventing the explosive distribution of false information, but they cannot contribute to the spread of viruses effectively. Therefore, transparent and open CDCs should manage infected suspects. However, they still make their tracking information public locally and individually. Consequently, it is necessary to build a global public platform that can capture them.
- Real-time authentication and reliability of information: Even though Singapore and Hong Kong announced fewer than 100 COVID-19 confirmed cases, there was civil unrest. However, there have been no such situations in South Korea despite a surge in confirmed numbers. South Korea had maintained stable social functions even when the number of infected people reached their peak. The reason for this is that South Korea’s Director of Disease Control and Health Authorities have given them a detailed and transparent briefing on the information, giving them confidence that they are in control of the situation. However, they gave intelligence briefings once every 24 h as frequently as they can. The background of releasing information every 24 h is the product of the era of offline newspapers. Information should be collected immediately on an online basis. When ordinary users request the information they need, they should receive the disclosure service of that information as fast as possible. For these services to be successful, the information collection and this authentication should occur at the same time. In addition, the reliability of the newly collected information must be able to be proven in real-time.
- Blind naming of infected persons: The real-time tracking of confirmed cases and suspected infections is possible now because everyone has a smartphone connected to the Internet. However, their personal information should be protected thoroughly. A different approach to naming is necessary [10,11]. The authority responsible for tracking them can give each of them a different conceptual identifier that is the same as a number assigned to the Internet of Things device. This blind id enables one to prevent hackers from inferring the identity information corresponding to this number, even if they secretly obtain this identifier number.
- Confidentiality: The privacy information of the confirmed cases, person suspected of infection, or person in need of management should be encrypted and stored using a secret key that is granted separately for each individual. With a large number of CDCs distributed around the world and enough people to manage per CDC, the platform should provide a security management service that allows individuals to use different secret keys for each individual [1,12,13,14].
- Scalability: The platform should provide real-time disclosure services for the COVID-19-related tracking information to any CDC and anyone in the world in the same way as a DNS (Domain Name System) provides name-address conversion services in HTTP communications in real-time. It is a prerequisite that the platform should be able to accommodate enough people to manage per CDC as well as a large number of CDCs distributed around the world. So, the data structure that the platform handles must be concise and straightforward so that the scalability of the system can be satisfied [15].
- Latency: Currently, the person gets to figure global COVID-19 cases out based on data provided by the World Health Organization (WHO). In addition, they usually get to know Global COVID-19 case trends based on WHO data. However, it takes time for the WHO to gather reliable, comprehensive data. It should also go beyond the official statistical data presentation method. It is necessary to send a query on an individual basis and receive a reply to the information service in real-time. The time it takes to complete the Query/Reply process in a global public service must be faster to satisfy the Quality of Service to the users [16].
2. Related Works
- Rapid diagnostic tests for all symptomatic cases or those with reasonable suspicion of COVID-19 exposure.
- The ability to trace all contacts of reported cases.
- Appropriate privacy tradeoffs can be obtained so that people can be willing to endure for the sake of public health.
- With sufficient computational resources and the use of cryptographic protocols, app-based contact tracing can be accomplished without completely sacrificing privacy.
- We design a global platform focusing on monitoring and tracking to prevent COVID-19.
- A virtual Internet of Things (vIoT) node can be a confirmed case or a suspected infection.
- CDC forcibly installs virtual vIoT nodes in the form of applications on their smartphones.
- CDC controls the vIoT nodes for a list of people who need monitoring and tracking in its control range.
- SDNC is a centralized center that collects location-related information sent from vIoT nodes under all the distributed CDCs’ control.
- Each vIoT node is responsible for updating location-related information into SDNC.
- An individual vIoT’s secret key is created and provided by its CDC.
- Each vIoT node uses the secret key to update location-related information to SDNC.
- SDNC generates and uses the secret key in real-time when it receives the update message.
- CDC can monitor the location-related information about the vIoT nodes under its control.
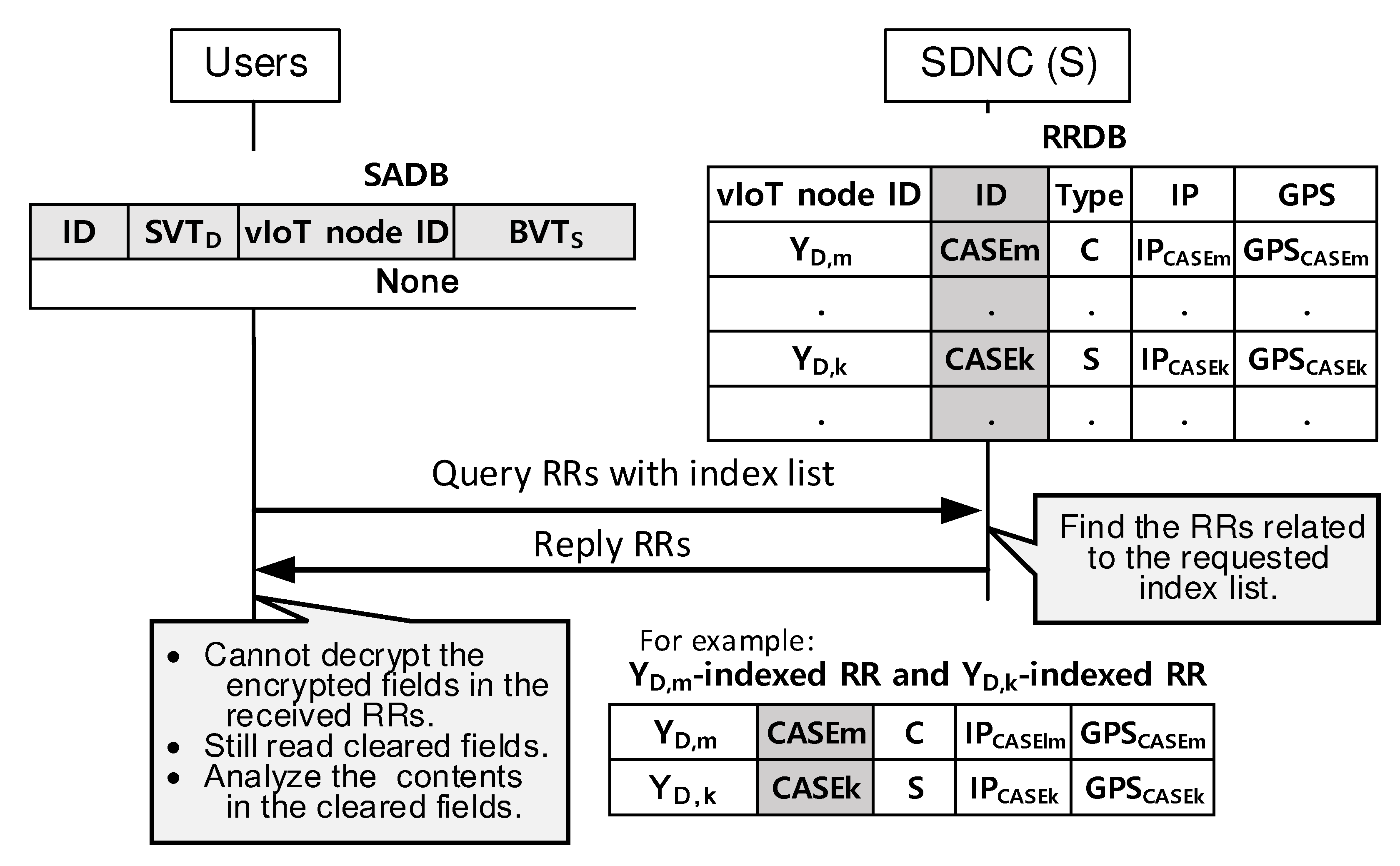
- Unlike vIoT nodes, the ordinary user can obtain limited information from the SNDC without a secret key.
- An ordinary user can reach SDNC and obtain necessary information except for privacy-related data even though the user does not maintain any security associations
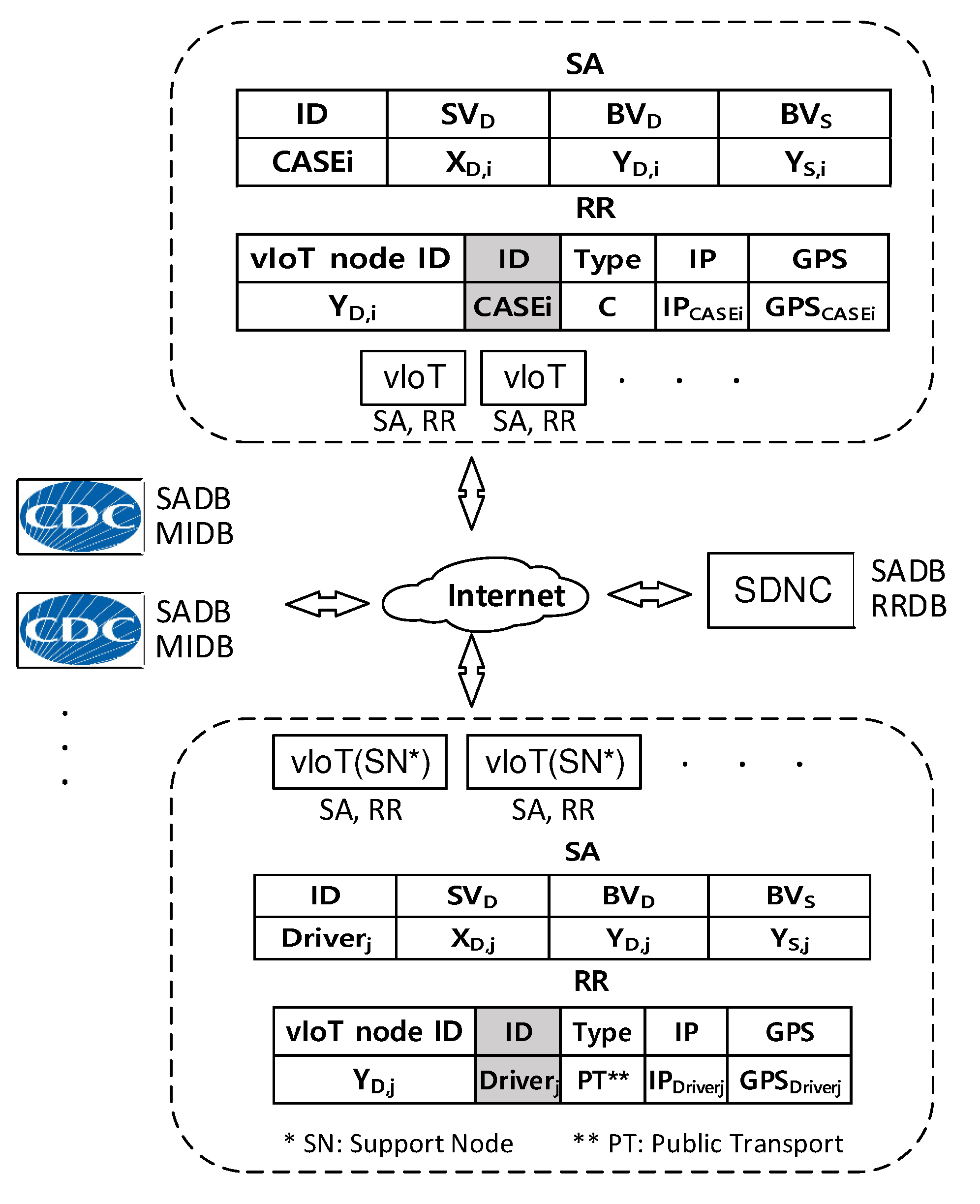
3. Platform Architecture with vIoTs, CDCs and SDNC
3.1. Basics of the Proposed Security Management
3.2. Platform Structure Based on Software-Defined Networking Controller
- Get an SA from its CDC and install it. The CDC is responsible for its revocation.
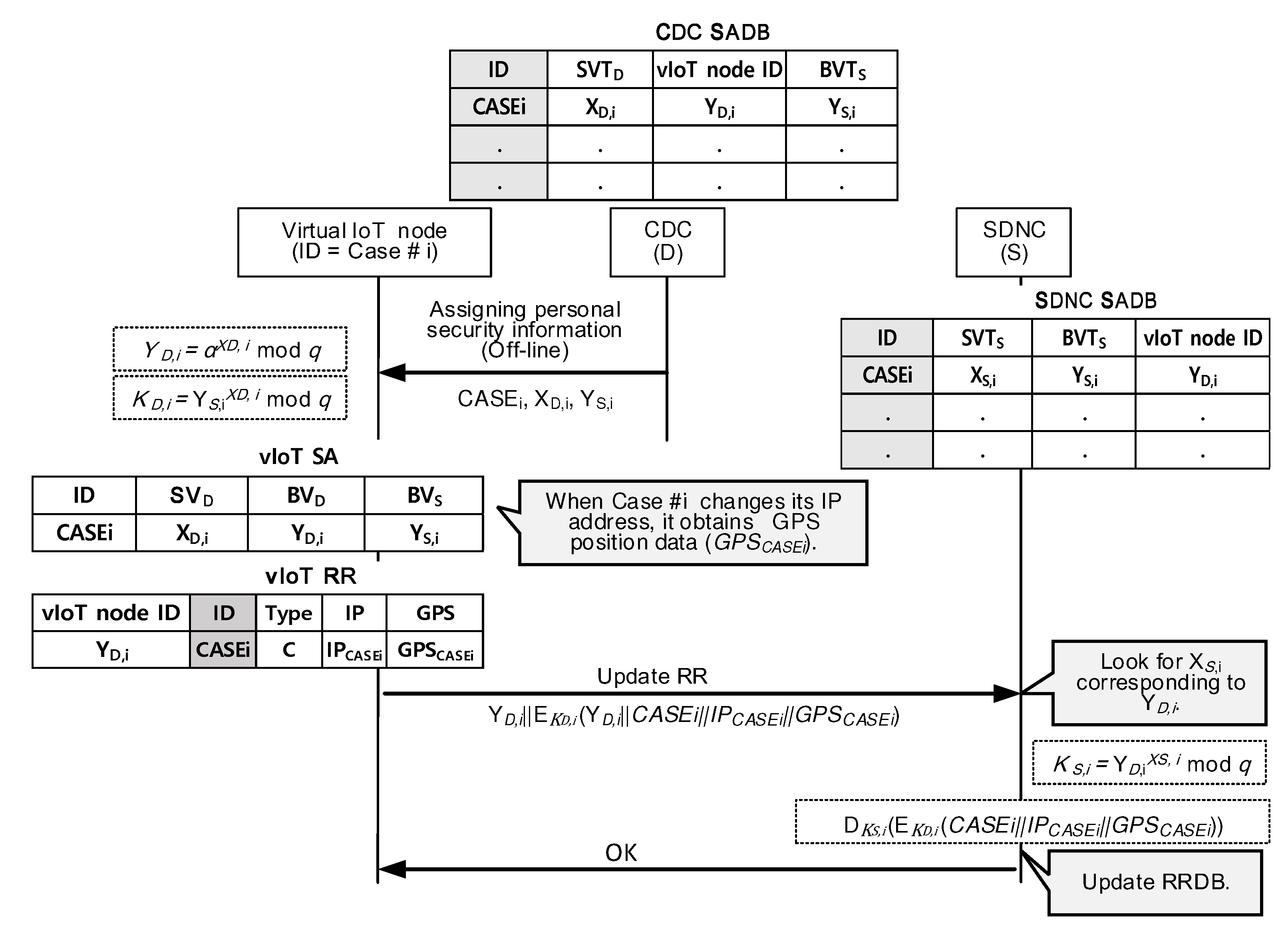
- Track its location-related status such as current IP address and GPS data when it moves.
- Renew its RR based on the changed location-related status.
- Register the renewed RR to the SDNC immediately in any change of the current RR.
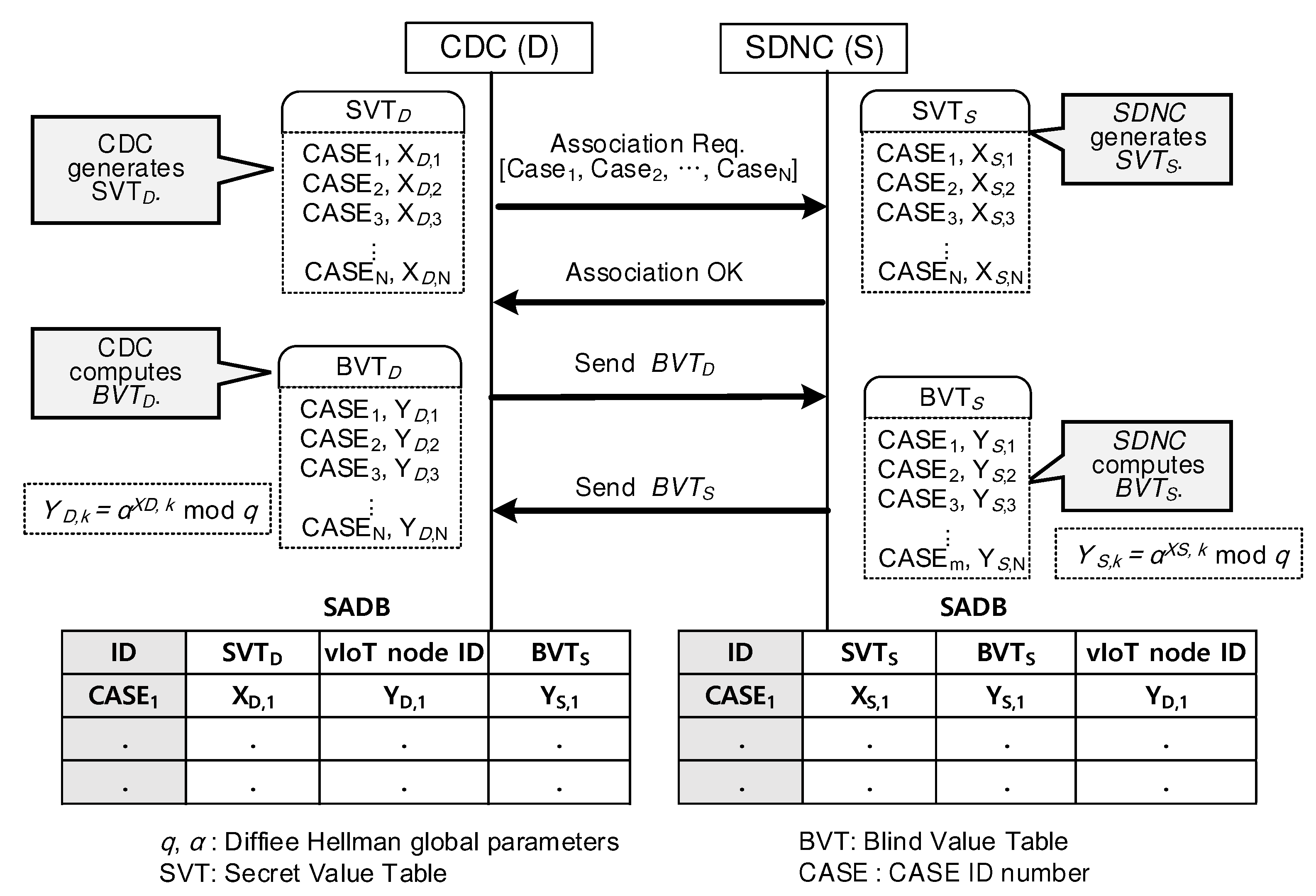
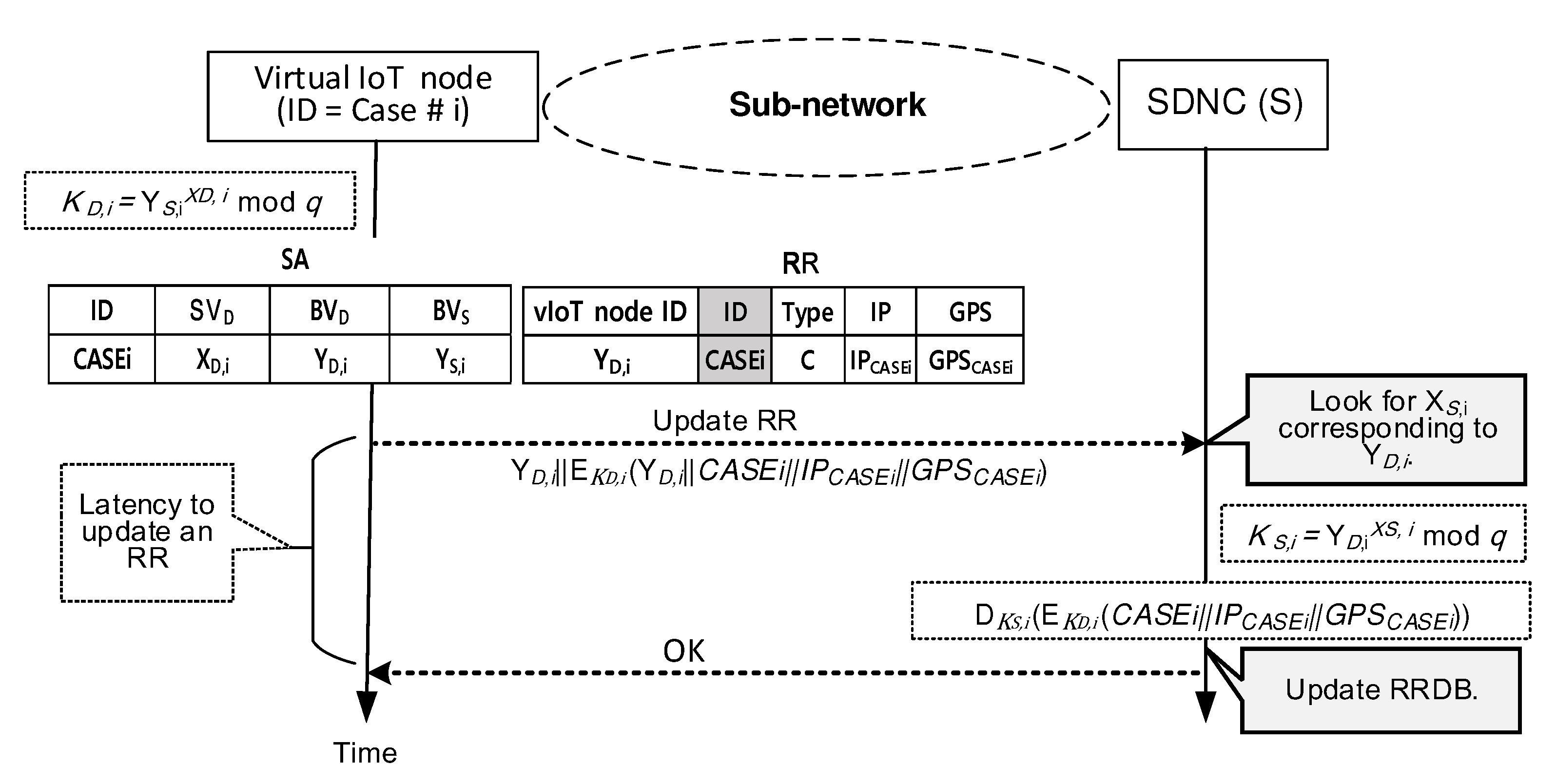
- Request to generate all SADB entries at a time to the SDNC. An SA contains Diffie–Hellman (DH) parameters necessary to determine the resultant DH key. The key is applied to encrypt sensitive information in RRs. The field value of “vIoT node ID” identifies each SA.
- Maintain SADB entries that tell which SA to use to apply to decipher an encrypted part of a given RR. An SA specifies the same DH key applied between the CDC and SDNC as well as vIoT and SDNC. The field value of “vIoT node ID” indicates a specific SA among SADB entries.
- Maintain MIDB entries. The field value of “vIoT node ID” identifies the medical status information related to a specific person in need of care. The CDC gives him (or her) a unique management number (“ID”) and classes it according to its severity. Each can belong to one of a confirmed case group (C), self-isolation group (S), those who need observation (O). The field of “Type” classifies a specific group. This field also includes PT (Public Transportation) to specify the vIoT support node. People with COVID-19 can experience mild to severe respiratory illness. The field of “Medical information ” (*** in Figure 2) can explain COVID-19-related symptoms or combinations of symptoms.
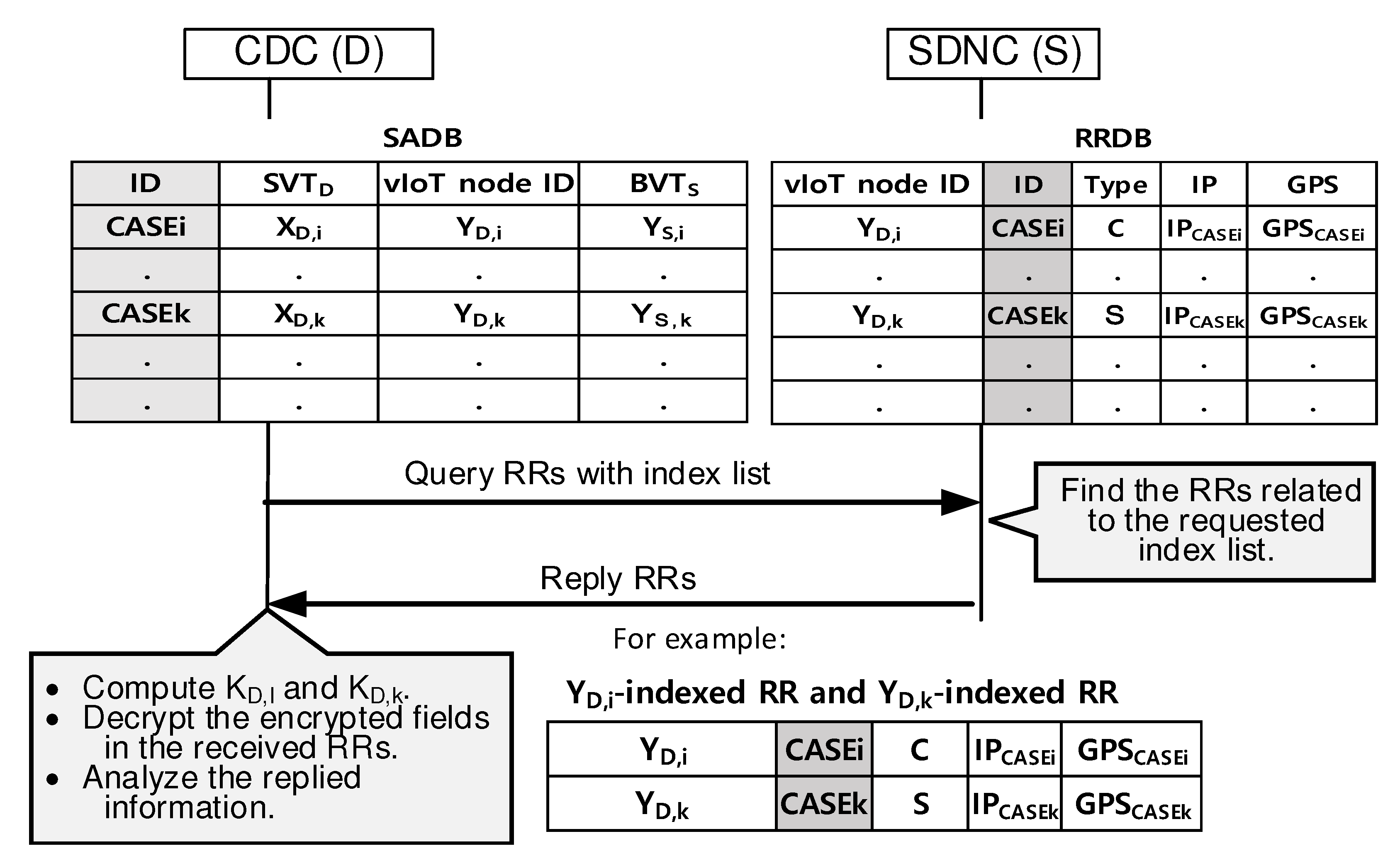
- Query the RRDB in the SDNC and analyze the dynamical behaviors of the people under monitoring.
- Maintain SADB entries generated as results of BVT exchange procedures initiated by the CDC.
- Calculate the DH key using the SA, which the field value of “vIoT node ID” points out, to encrypt sensitive information in RRs.
- Maintain RRDB entries and updates them when the “Update RR” messages arrive from vIoT nodes.
- Send the corresponding RRs matched after receiving queries from the CDC and normal users, in response.
4. SDNC-Centric Tracking and Real-Time Information Services
4.1. Associating SADBs between CDC and SDNC
4.2. Updating an RR in RRDB at SDNC
4.3. Querying RRs Matched with the Index List
4.4. Accessing RRDB from Normal Users Having No Security Associations
5. Discussions
5.1. Benefits of the Proposed Platform
5.1.1. Authentication
5.1.2. Confidentiality
5.1.3. Scalability
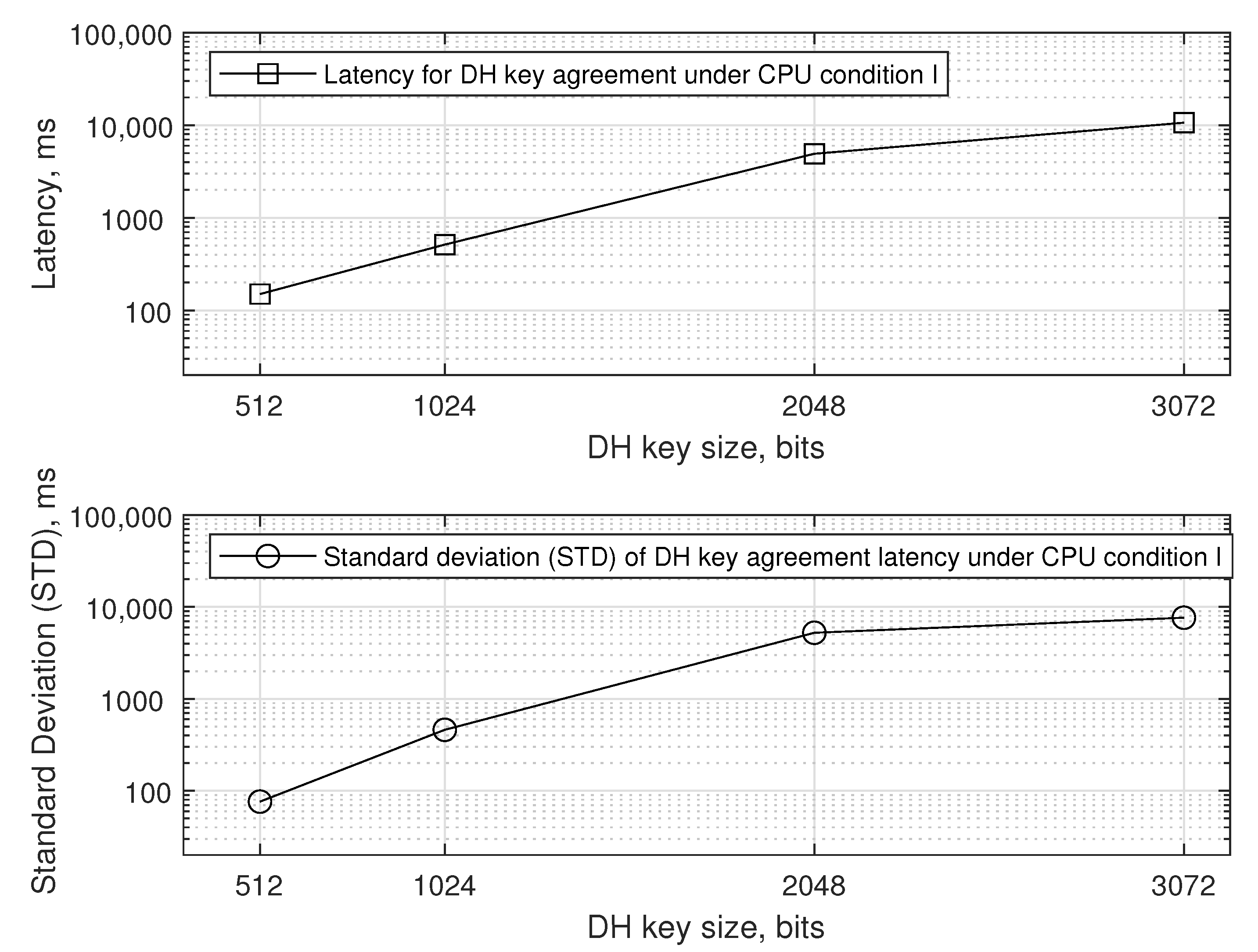
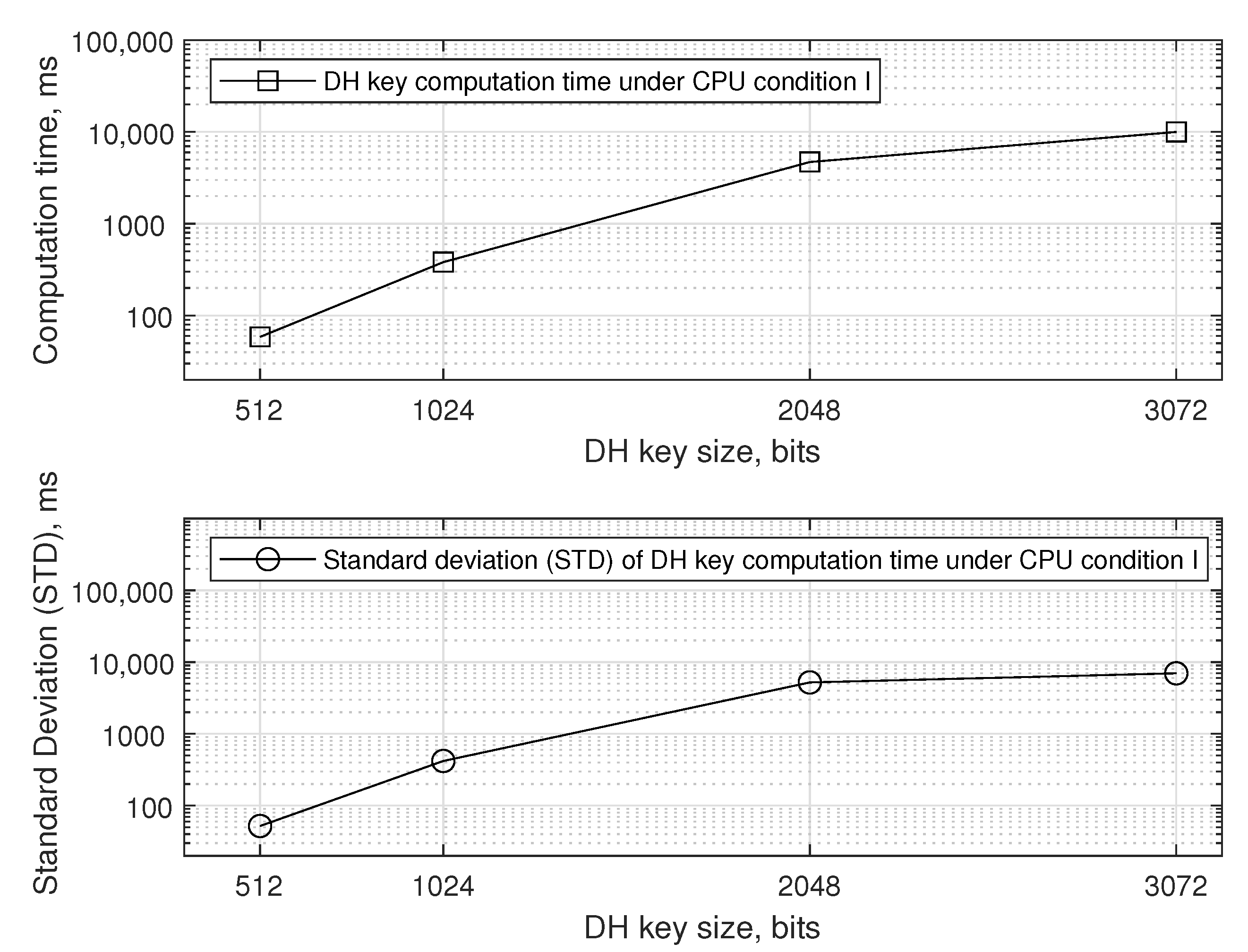
5.1.4. Quality of Service on Latency
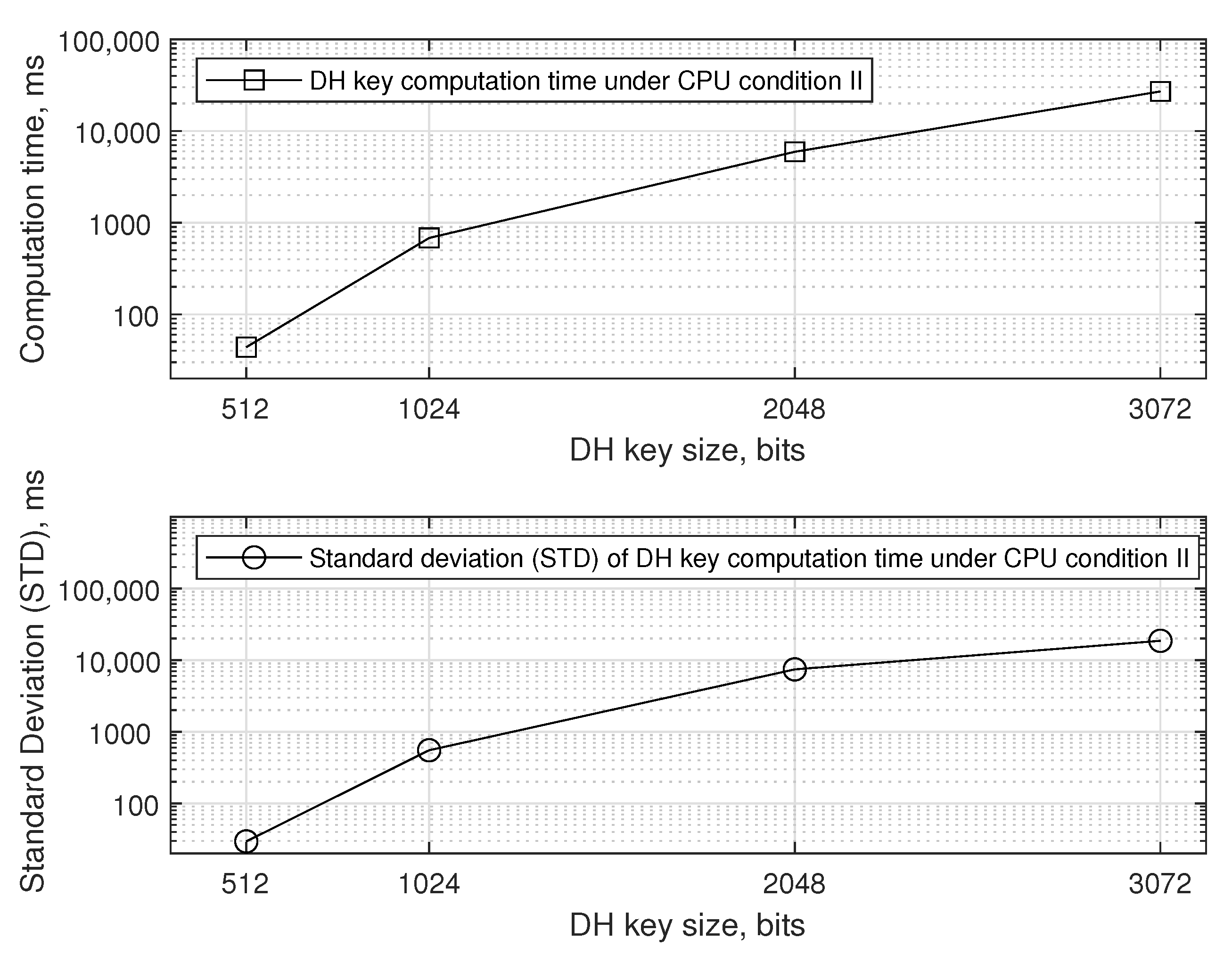
- CPU condition I assumes that the smartphone’s CPU power is almost free when the Update RR request arrives.
- CPU condition II assumes that the smartphone’s CPU power is already occupied by other Update RR requests by 35% when the Update RR request arrives.
5.2. Further Study Area
5.2.1. Expansion of Information Providers
5.2.2. Intelligent Searching Algorithm
5.2.3. CDC Rating Algorithm
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Sultan, A.; Mushtaq, M.A.; Abubakar, M. IOT Security Issues Via Blockchain: A Review Paper. In Proceedings of the 2019 International Conference on Blockchain Technology, Honolulu, HI, USA, 15 March 2019; pp. 60–65. [Google Scholar]
- Bai, Z.; Gong, Y.; Tian, X.; Cao, Y.; Liu, W.; Li, J. The Rapid Assessment and Early Warning Models for COVID-19; Springer: Berlin, Germany, 2020; p. 1. [Google Scholar]
- Ndiaye, M.; Oyewobi, S.S.; Abu-Mahfouz, A.M.; Hancke, G.P.; Kurien, A.M.; Djouani, K. IoT in the Wake of COVID-19: A Survey on Contributions, Challenges and Evolution. IEEE Access 2020, 8, 186821–186839. [Google Scholar] [CrossRef]
- Ksentini, A.; Brik, B. An Edge-Based Social Distancing Detection Service to Mitigate COVID-19 Propagation. IEEE Internet Things Mag. 2020, 3, 35–39. [Google Scholar] [CrossRef]
- Exposure Notification Bluetooth Specification Preliminary—Subject to Modification and Extension. 2020, Volume 1.2. Available online: https://covid19-static.cdn-apple.com/applications/covid19/current/static/contact-tracing/pdf/ExposureNotification-BluetoothSpecificationv1.2.pdf (accessed on 23 June 2020).
- Cooper, D.; Quathem, K.; Meneses, A. COVID-19 Apps and Websites–The “Pan-European Privacy Preserving Proximity Tracing Initiative” and Guidance by Supervisory Authorities. Available online: https://www.insideprivacy.com/covid-19/covid-19-apps-and-websites/ (accessed on 23 June 2020).
- Kim, J.M.; Kim, H.M.; Lee, E.J.; Jo, H.J.; Yoon, Y.; Lee, N.J.; Son, J.; Lee, Y.-J.; Kim, M.S.; Lee, Y.-P.; et al. Detection and Isolation of SARS-CoV-2 in Serum, Urine, and Stool Specimens of COVID-19 Patients from the Republic of Korea. Osong Public Health Res. Perspect. 2020, 11, 112–117. [Google Scholar] [CrossRef] [PubMed]
- Park, O.; Park, Y.J.; Park, S.Y.; Kim, Y.M.; Kim, J.; Lee, J.; Park, E.; Kim, D.; Jeon, B.H.; Ryu, B.; et al. Contact Transmission of COVID-19 in South Korea: Novel Investigation Techniques for Tracing Contacts. Osong Public Health Res. Perspect. 2020, 11, 60–63. [Google Scholar] [CrossRef]
- Team, G.P.T.F. Global Health Security: The Lessons from the West African Ebola Virus Disease Epidemic and MERS Outbreak in the Republic of Korea. Osong Public Health Res. Perspect. 2015, 6, S25–S27. [Google Scholar] [CrossRef]
- Jung, Y.; Peradilla, M.; Saini, A. Software-defined Naming, Discovery and Session Control for IoT Devices and Smart Phones in the Constraint Networks. Procedia Comput. Sci. 2017, 110, 290–296. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Moungla, H.; Liu, Y. A unified hybrid information-centric naming scheme for IoT applications. Comput. Commun. 2020, 150, 103–114. [Google Scholar] [CrossRef]
- Festijo, E.; Jung, Y.; Peradilla, M. Software-defined security controller-based group management and end-to-end security management. J. Ambient Intell. Humaniz. Comput. 2019, 10, 3365–3382. [Google Scholar] [CrossRef]
- Jung, Y.; Agulto, R. Integrated Management of Network Address Translation, Mobility and Security on the Blockchain Control Plane. Sensors 2020, 20, 69. [Google Scholar] [CrossRef] [PubMed]
- Jung, Y.; Peradilla, M.; Agulto, R. Packet Key-Based End-to-End Security Management on a Blockchain Control Plane. Sensors 2019, 19, 2310. [Google Scholar] [CrossRef] [PubMed]
- Choi, Y.J.; Kang, H.J.; Lee, I.G. Scalable and Secure Internet of Things Connectivity. Electronics 2019, 8, 752. [Google Scholar] [CrossRef]
- Kaur, J.; Kaur, K. Internet of Things: A review on technologies, architecture, challenges, applications, future trends. Int. J. Comput. Netw. Inf. Secur. 2017, 9, 57. [Google Scholar] [CrossRef]
- Collado-Borrell, R.; Escudero-Vilaplana, V.; Villanueva-Bueno, C.; Herranz-Alonso, A.; Sanjurjo-Saez, M. Features and functionalities of smartphone apps related to COVID-19: Systematic search in App stores and content analysis. J. Med Internet Res. 2020, 22, e20334. [Google Scholar] [CrossRef] [PubMed]
- Watson, C.; Cicero, A.; Blumenstock, J.S.; Fraser, M.R. A National Plan to Enable Comprehensive COVID-19 Case Finding and Contact Tracing in the US; Johns Hopkins Bloomberg School of Public Health, Center for Health Security: Baltimore, MD, USA, 2020. [Google Scholar]
- Tidy, J. Coronavirus: Israel Enables Emergency Spy Powers. BBC News. 2020. Available online: https://www.bbc.com/news/technology-51930681 (accessed on 17 March 2020).
- Kim, M.; Denyer, S. A ‘Travel Log’ of the Times in South Korea: Mapping the Movements of Coronavirus Carriers. The Washington Post. 2020. Available online: https://www.washingtonpost.com/world/asia_pacific/coronavirus-south-korea-tracking-apps/2020/03/13/2bed568e-5fac-11ea-ac50-18701e14e06d_story.html (accessed on 13 March 2020).
- Wang, C.J.; Ng, C.Y.; Brook, R.H. Response to COVID-19 in Taiwan: Big data analytics, new technology, and proactive testing. JAMA 2020, 323, 1341–1342. [Google Scholar] [CrossRef] [PubMed]
- Lee, Y. Taiwan’s New ‘Electronic Fence’ for Quarantines Leads Wave of Virus Monitoring. Reuters Technology News. 2020. Available online: https://www.reuters.com/article/us-health-coronavirus-taiwan-surveillanc-idUSKBN2170SK (accessed on 20 March 2020).
- Cho, H.; Ippolito, D.; Yu, Y.W. Contact tracing mobile apps for COVID-19: Privacy considerations and related trade-offs. arXiv 2020, arXiv:2003.11511. [Google Scholar]
- Marbouh, D.; Abbasi, T.; Maasmi, F.; Omar, I.A.; Debe, M.S.; Salah, K.; Jayaraman, R.; Ellahham, S. Blockchain for COVID-19: Review, Opportunities, and a Trusted Tracking System. Arab. J. Sci. Eng. 2020, 1–17. [Google Scholar] [CrossRef] [PubMed]
- Bischoff, P. COVID-19 App Tracker: Is Privacy Being Sacrificed in a Bid to Combat the Virus? 2020. Available online: https://www.comparitech.com/blog/vpn-privacy/coronavirus-apps/ (accessed on 23 December 2020).
- Warner, K.; Nowais, S. Coronavirus: Doctors Urge Public to Help Track Covid-19 Cases with Tracing App. The National. 2020. Available online: https://www.thenationalnews.com/uae/health/coronavirus-doctors-urge-public-to-help-track-covid-19-cases-with-tracing-app-1.1012267 (accessed on 28 April 2020).
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed]
- Aileni, R.M.; Suciu, G. IoMT: A Blockchain Perspective; Springer: Cham, Switzerland, 2020; pp. 199–215. [Google Scholar]
- Srivastava, G.; Crichigno, J.; Dhar, S. A Light and Secure Healthcare Blockchain for IoT Medical Devices. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Gupta, D.; Bhatt, S.; Gupta, M.; Tosun, A.S. Future Smart Connected Communities to Fight COVID-19 Outbreak. Internet Things 2020, 100342. [Google Scholar] [CrossRef]
- Gupta, M.; Abdelsalam, M.; Mittal, S. Enabling and enforcing social distancing measures using smart city and ITS infrastructures. arXiv 2020, arXiv:2004.09246. [Google Scholar]

| Operational Conditions | CPU | Background CPU Utilization |
|---|---|---|
| CPU | Intel | 2% |
| condition | i7-10700 | |
| I | 2.90 GHz | |
| CPU | Intel | 35% |
| condition | i7-10700 | |
| II | 2.90 GHz |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jung, Y.; Agulto, R. A Public Platform for Virtual IoT-Based Monitoring and Tracking of COVID-19. Electronics 2021, 10, 12. https://doi.org/10.3390/electronics10010012
Jung Y, Agulto R. A Public Platform for Virtual IoT-Based Monitoring and Tracking of COVID-19. Electronics. 2021; 10(1):12. https://doi.org/10.3390/electronics10010012
Chicago/Turabian StyleJung, Younchan, and Ronnel Agulto. 2021. "A Public Platform for Virtual IoT-Based Monitoring and Tracking of COVID-19" Electronics 10, no. 1: 12. https://doi.org/10.3390/electronics10010012
APA StyleJung, Y., & Agulto, R. (2021). A Public Platform for Virtual IoT-Based Monitoring and Tracking of COVID-19. Electronics, 10(1), 12. https://doi.org/10.3390/electronics10010012






