Data Analytic Approaches for Mining Process Improvement—Machinery Utilization Use Case
Abstract
1. Introduction
2. Materials and Methods
2.1. Business Process Management
- process model discovery,
- process analysis,
- process redesign,
- process implementation, and
- process monitoring and controlling.
2.2. Data Mining—Data-Oriented Approach in Process Analytics
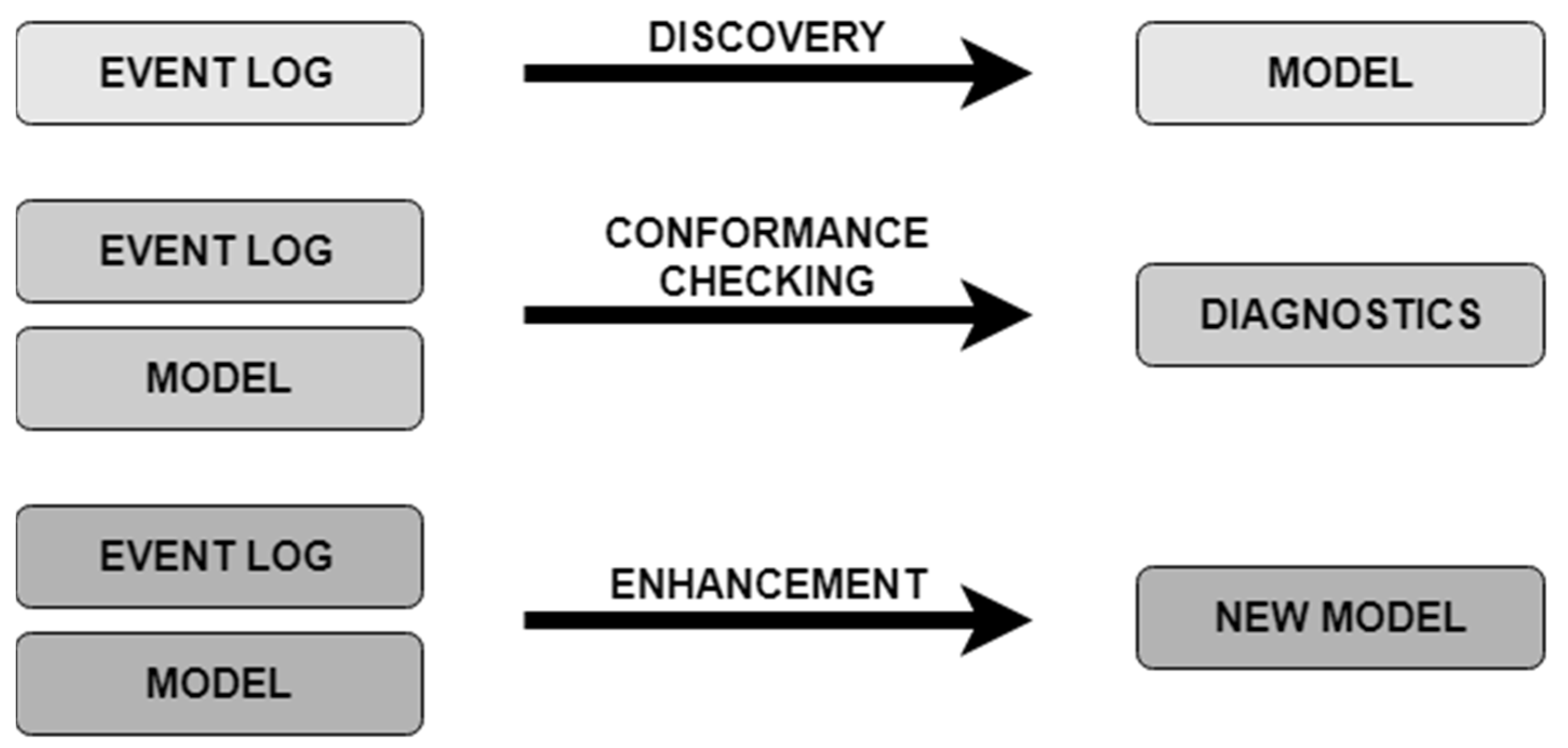
2.3. Process Mining—Process-Oriented Approach and Software in Process Analytics
- Conformance checking—based on comparing the existing model with actual event log records. This task allows for checking whether the process steps performed in the event log are consistent with the model and vice versa, while taking various types of models into account, including, for example, procedural, organizational, declarative, or business rules.
- Enhancement—based on an in-depth performance analysis of the implemented process by using contextual information recorded in the event log. This task is used to expand and improve the existing process model (e.g., by indicating process bottlenecks, capacity of individual resources, frequency of activities, loops analysis).
2.4. Implementation of Process Mining into Mining Domain—Approach and Challenges
3. Results
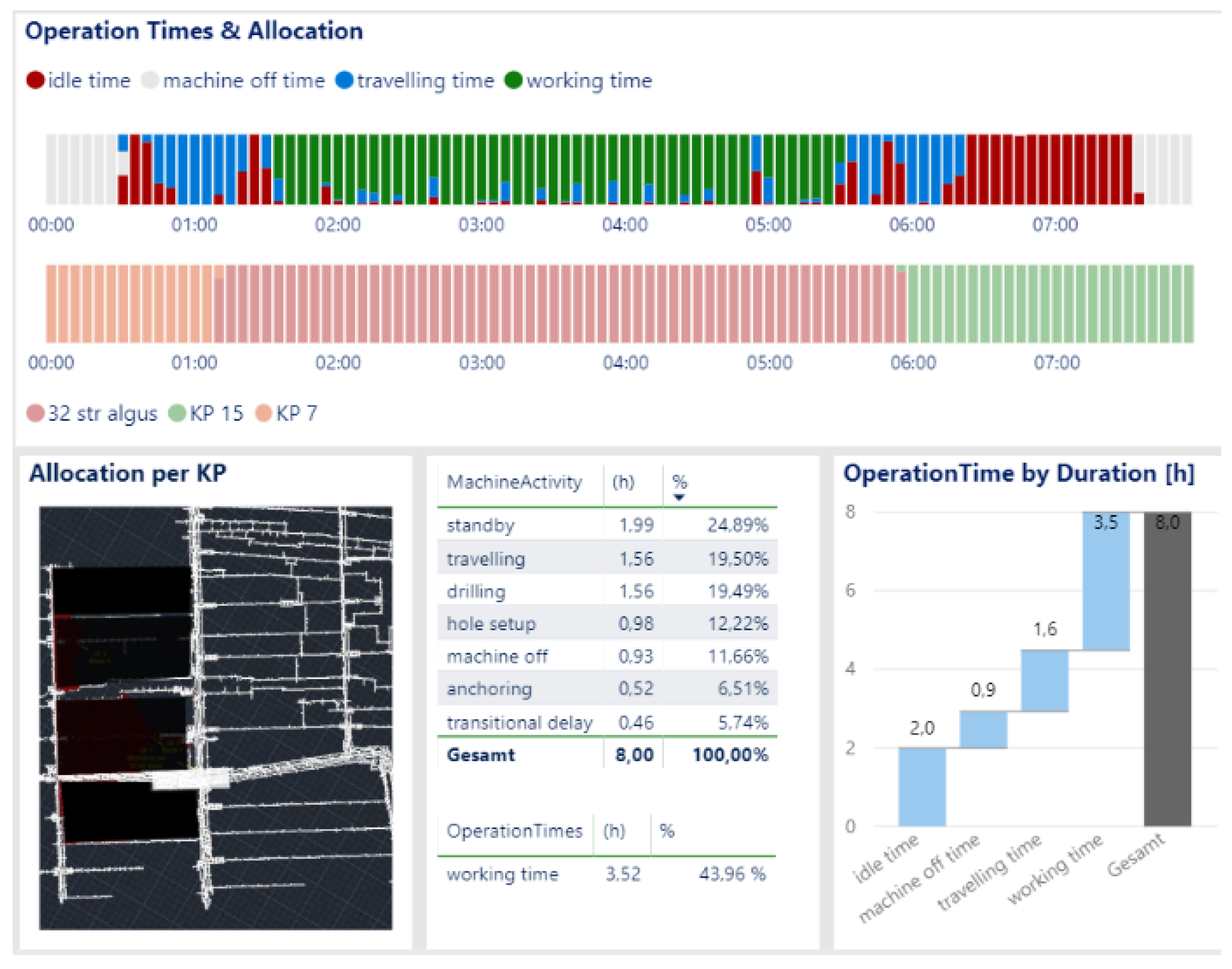
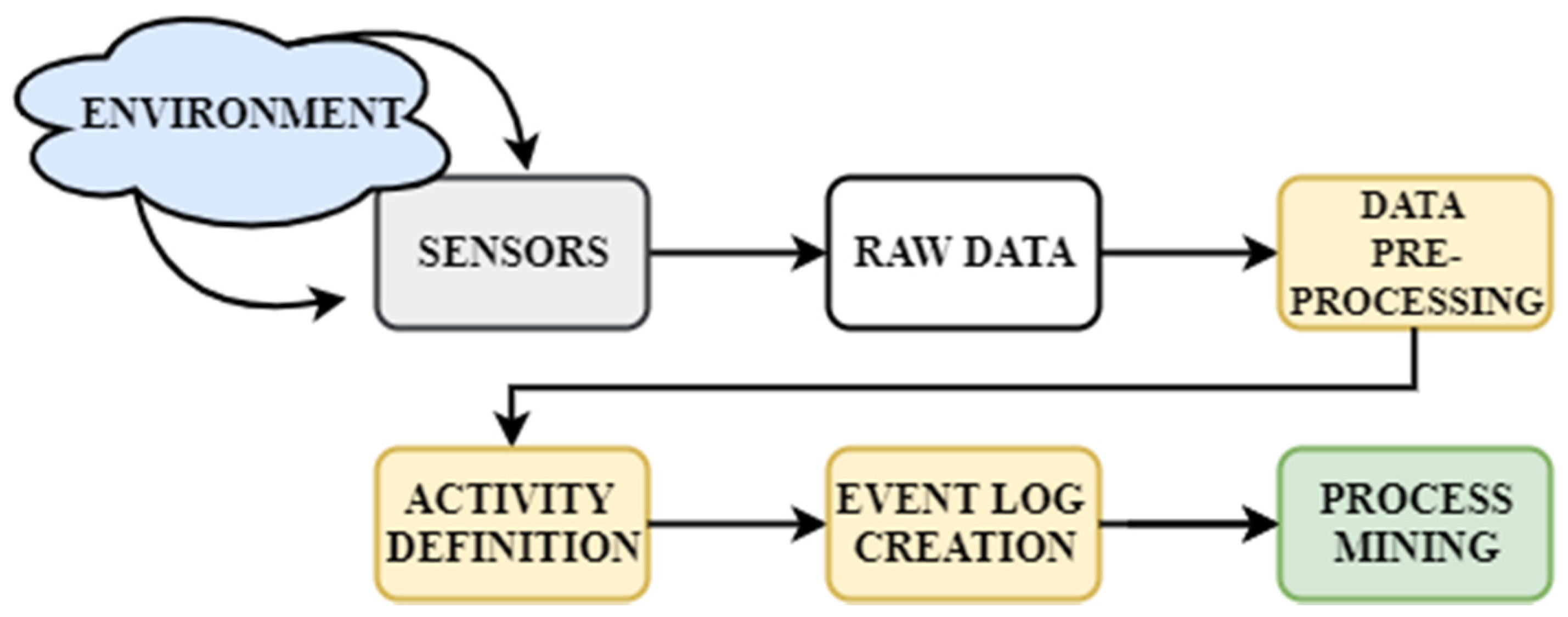
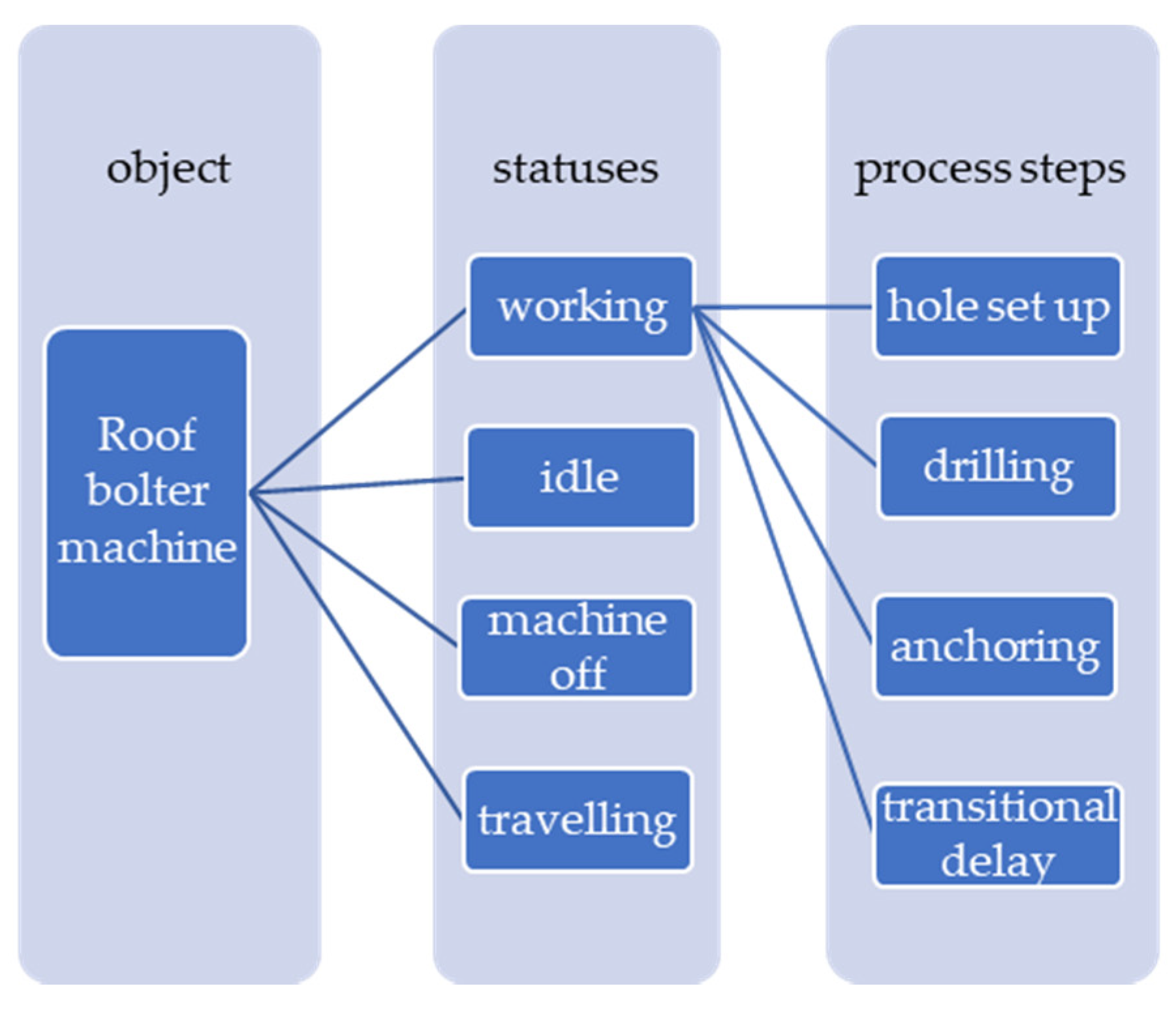
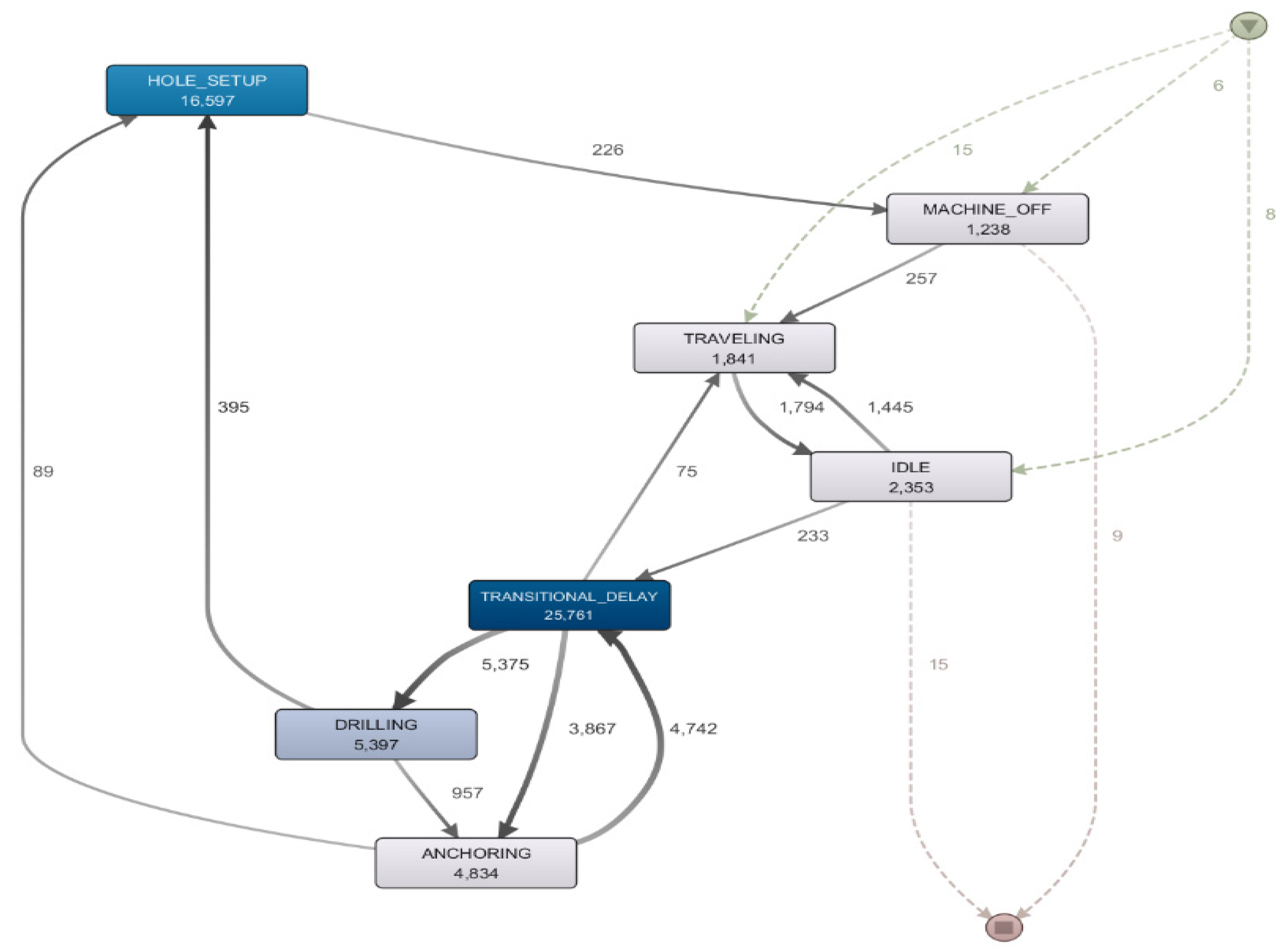
3.1. Process Description and Event Log Creation
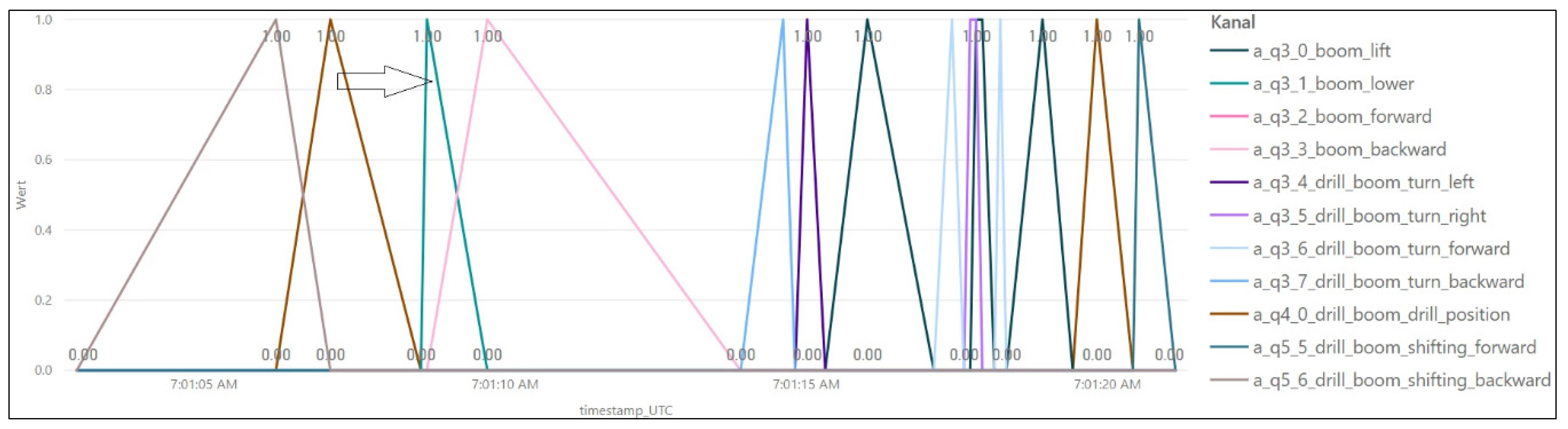
- Hole setup—before the hole can be drilled and directly after a bolt is installed, the boom needs to be positioned under the initial/next planned drill hole. This process is called the hole setup and it is defined by a number of hydraulic signals, which are indicating boom movement in different directions, as can be seen in Figure 7.
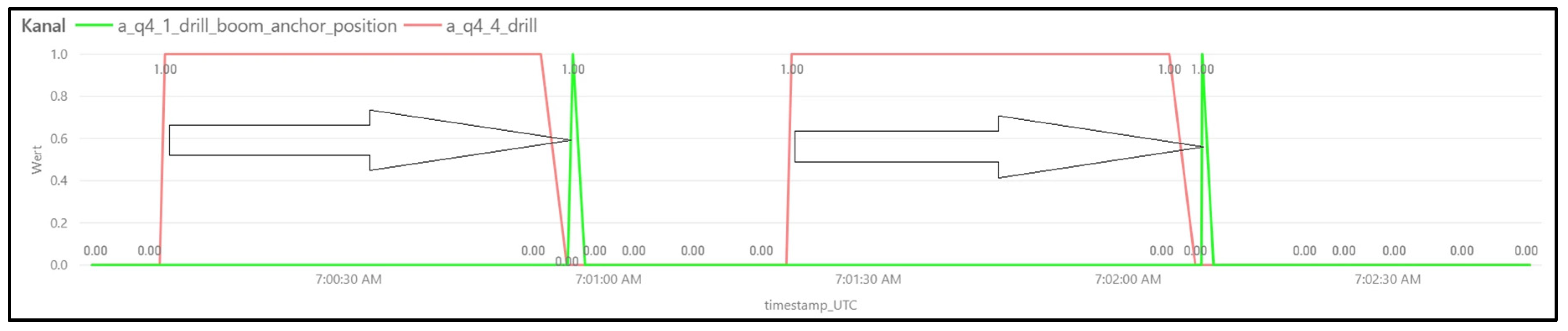
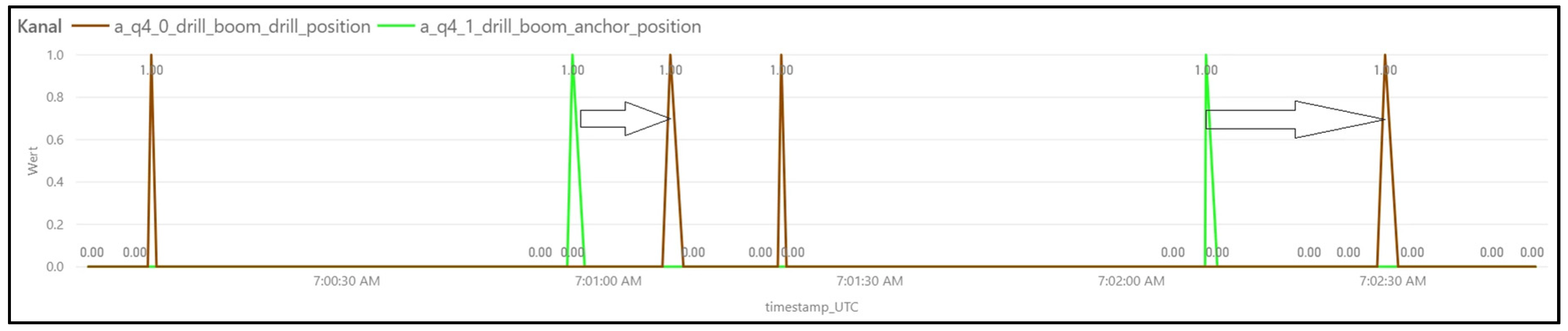
- Drilling—once the boom is positioned correctly, the drilling process is the next production process. Thus, the rotating drill rod drills a hole into the roof and it is extracted by the machine after completion. Here, another set of hydraulic signals and mechanical sensors are taken into account, such as rpm of the drill itself and the position of the drill boom in respect to the anchor boom (Figure 8).
- Anchoring—after the drill hole is completed, an anchor is inserted automatically or at the operator’s request into the hole, and torque is applied to secure the rock bolt. Again, different hydraulic sensors and the boom position are providing a signature like sequence to identify the activity (Figure 9).
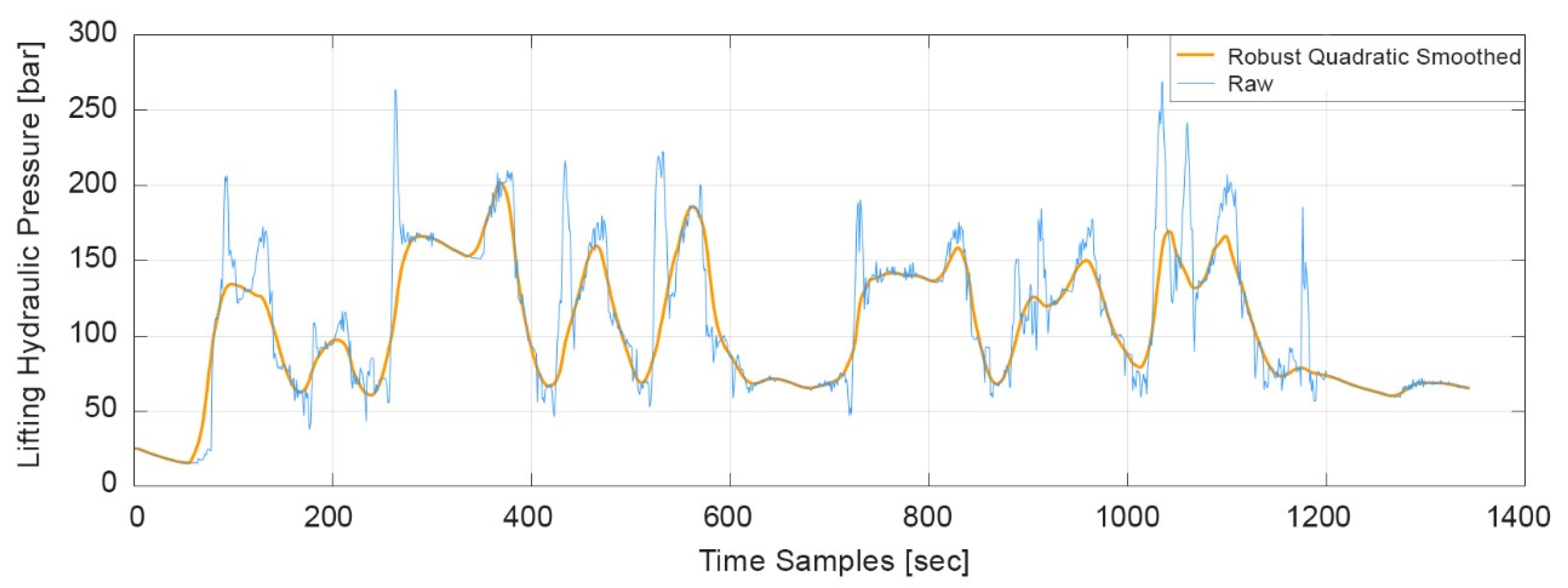
- Transitional delay is the state when the machine’s hydraulic system is switched on; however, no work is being performed (a.k.a. hydraulic standby). It can happen when manual work is required by the operator to continue production, e.g., changing the drilling rod/head or loading new bolts into the bolt magazine. Therefore, this process step is still considered to be a part of the machine status working.
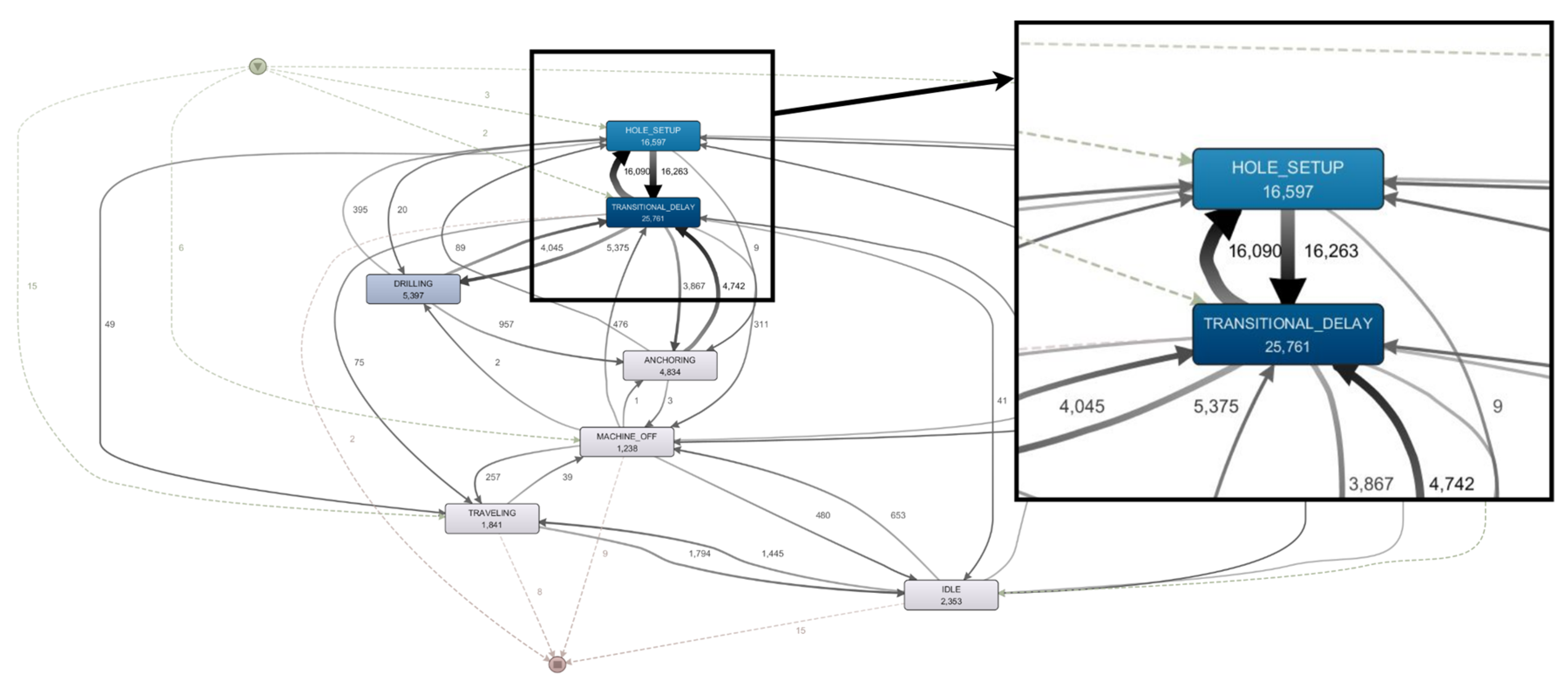
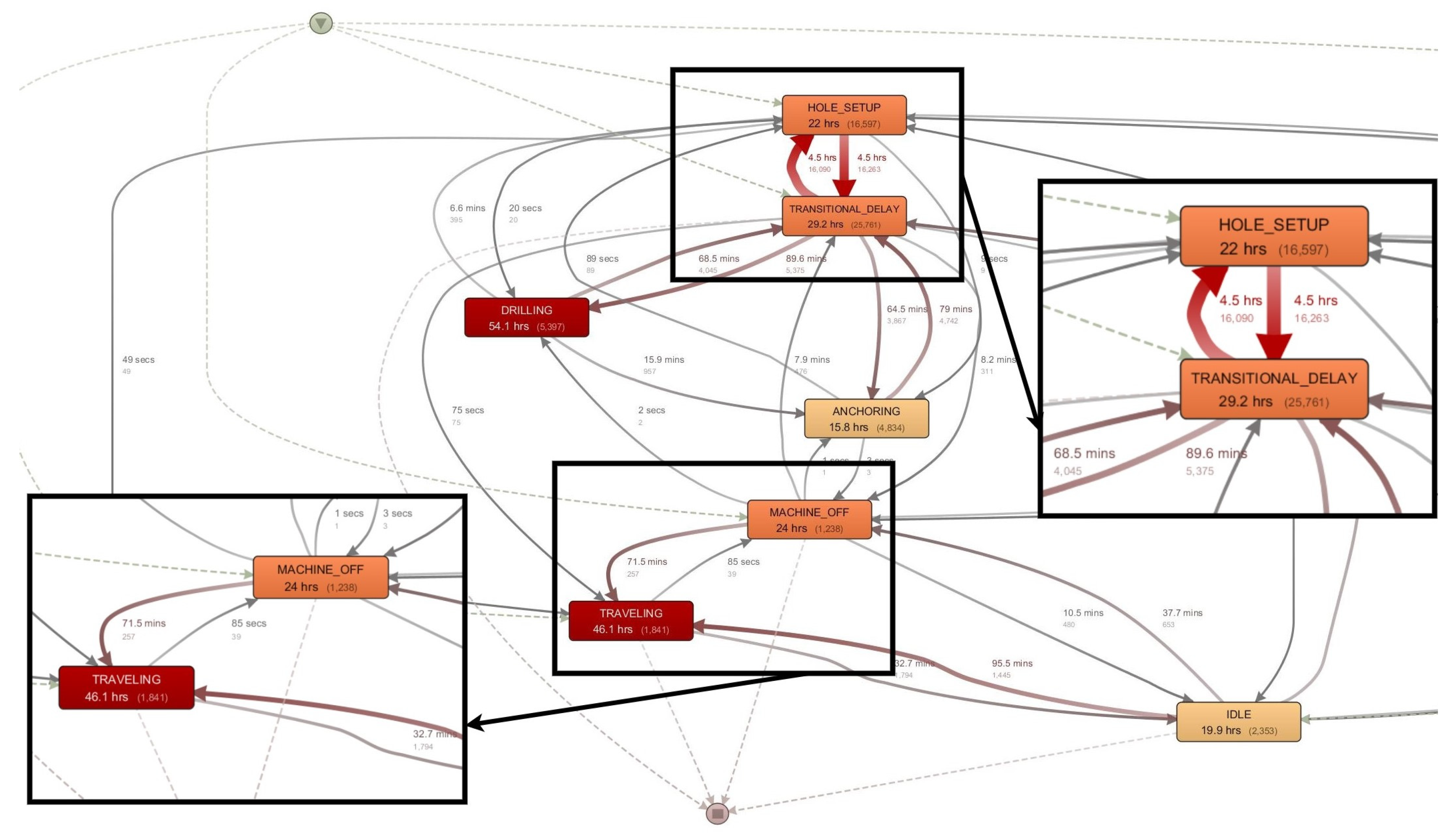
3.2. Process Modeling and Analysis with Process Mining
4. Discussion and Conclusions
- identification of possible non-compliant behavior during process execution (i.e., shifts started with unusual activities);
- identification of high impacts area in process execution (repetitions and loops between activities—i.e., "transitional delay"—"hole setup"); and,
- identification of time lost in the process (based on activity duration statistics, duration of time between activities, especially in working operation time).
Author Contributions
Funding
 .
.Acknowledgments
Conflicts of Interest
References
- Lööw, J.; Abrahamsson, L.; Johansson, J. Mining 4.0—The Impact of New Technology from a Work Place Perspective. Mining Metall. Explor. 2019, 36, 701–707. [Google Scholar] [CrossRef]
- Ghattas, J.; Soffer, P.; Peleg, M. Improving business process decision making based on past experience. Decision Support Syst. 2014, 59, 93–107. [Google Scholar] [CrossRef]
- Lööw, J.; Nygren, M. Initiatives for increased safety in the Swedish mining industry: Studying 30 years of improved accident rates. Saf. Sci. 2019, 117, 437–446. [Google Scholar] [CrossRef]
- Wojaczek, A.; Wojaczek, A.K. Monitoring the environment and machines in underground mine. Zesz. Nauk. Inst. Gosp. Sur. Miner. Energ. PAN. 2017, 99, 57–70. [Google Scholar]
- Wojaczek, A.; Wojaczek, A.K. Systemy monitoringu w kopalni podziemnej. Syst. Support. Prod. Eng. 2016, 1, 526–536. [Google Scholar]
- Jonek-Kowalska, I.; Turek, M. Dependence of total production costs on production and infrastructure parameters in the polish hard coal mining industry. Energies 2017, 10, 1480. [Google Scholar] [CrossRef]
- Qiao, W.; Liu, Q.; Li, X.; Luo, X.; Wan, Y.L. Using data mining techniques to analyze the influencing factor of unsafe behaviors in Chinese underground coal mines. Resour. Policy 2018, 59, 210–216. [Google Scholar] [CrossRef]
- Kopacz, M. The impact assessment of quality parameters of coal and waste rock on the value of mining investment projects - hard coal deposits. Miner. Resour. Manag. 2015, 31, 161–188. [Google Scholar] [CrossRef][Green Version]
- Bongers, D.R.; Gurgenci, H. Fault Detection and Identification for Longwall Machinery Using SCADA Data. In Complex System Maintenance Handbook. Springer Series in Reliability Engineering; Springer: London, UK, 2008; Volume 8, pp. 611–641. [Google Scholar]
- Elsayed, E.A. Reliability Prediction and Accelerated Testing; In Complex System Maintenance Handbook. Springer Series in Reliability Engineering; Springer: London, UK, 2008; Volume 8. [Google Scholar]
- Al-Chalabi, H.; Ahmadzadeh, F.; Lundberg, J.; Ghodrati, B. Economic lifetime prediction of a mining drilling machine using an artificial neural network. Int. J. Mining Reclam. Environ. 2014, 28, 311–322. [Google Scholar] [CrossRef]
- Bodlak, M.; Kudełko, J.; Zibrow, A. Machine Learning in predicting the extent of gas and rock outburst. E3S Web Conf. 2018, 71. [Google Scholar] [CrossRef]
- Moczulski, W. A new decision support tool for fault diagnosis, hazard prediction and analysis in mining industry—a case study. In Proceedings of the 24th World Mining Congress, Rio de Janeiro, Brazil, 18–21 October 2016; pp. 38–48. [Google Scholar]
- Mahdevari, S.; Shahriar, K.; Sharifzadeh, M.; Tannant, D.D. Stability prediction of gate roadways in longwall mining using artificial neural networks. Neural Comput. Appl. 2017, 28, 3537–3555. [Google Scholar] [CrossRef]
- Boullé, M. Predicting dangerous seismic events in coal mines under distribution drift. In Proceedings of the 2016 Federated Conference on Computer Science and Information Systems (FedCSIS), Gdansk, Poland, 11–14 September 2016; pp. 221–224. [Google Scholar]
- Deb, D.; Kumar, A.; Rosha, R.P.S. Forecasting shield pressures at a longwall face using artificial neural networks. Geotech. Geol. Eng. 2006, 24, 1021–1037. [Google Scholar] [CrossRef]
- Verma, A.K.; Kishore, K.; Chatterjee, S. Prediction Model of Longwall Powered Support Capacity Using Field Monitored Data of a Longwall Panel and Uncertainty-Based Neural Network. Geotech. Geol. Eng. 2016, 34, 2033–2052. [Google Scholar] [CrossRef]
- Gernand, J. Machine Learning Classification Models for More Effective Mine Safety Inspections. In Proceedings of the ASME 2014 International Mechanical Engineering Congress and Exposition, Montreal, QC, Canada, 14–20 November 2014; Volume 14. [Google Scholar]
- Hargrave, C.O.; James, C.A.; Ralston, J.C. Infrastructure-based localisation of automated coal mining equipment. Int. J. Coal Sci. Technol. 2017, 4, 252–261. [Google Scholar] [CrossRef]
- Jamróz, D.; Niedoba, T. Application of multidimensional data visualization by means of self-organizing Kohonen maps to evaluate classification possibilities of various coal types. Arch. Min. Sci. 2015, 60, 39–50. [Google Scholar]
- Jedliński, Ł.; Gajewski, J. Optimal selection of signal features in the diagnostics of mining head tools condition. Tunn. Undergr. Sp. Technol. 2019, 84, 451–460. [Google Scholar] [CrossRef]
- Zhou, J.; Li, X.; Mitri, H.S.; Wang, S.; Wei, W. Identification of large-scale goaf instability in underground mine using particle swarm optimization and support vector machine. Int. J. Min. Sci. Technol. 2013, 23, 701–707. [Google Scholar] [CrossRef]
- van der Aalst, W. Process Mining: Overview and Opportunities. ACM Trans. Manag. Inf. Syst. 2012, 3, 7:1–7:17. [Google Scholar] [CrossRef]
- van der Aalst, W.M.P. Process mining in the large: A tutorial. Lect. Notes Bus. Inf. Process. 2014, 172, 33–76. [Google Scholar]
- He, Z.; Wu, Q.; Wen, L.; Fu, G. A process mining approach to improve emergency rescue processes of fatal gas explosion accidents in Chinese coal mines. Saf. Sci. 2019, 111, 154–166. [Google Scholar] [CrossRef]
- Brzychczy, E.; Trzcionkowska, A. Creation of an event log from a low-level machinery monitoring system for process mining purposes. In Intelligent Data Engineering and Automated Learning—IDEAL 2018; Yin, H., Camacho, D., Novais, P., Tallón-Ballesteros, A.J., Eds.; Springer Nature: Cham, Switzerland, 2018; pp. 54–63. [Google Scholar]
- Brzychczy, E.; Trzcionkowska, A. Process-Oriented Approach for Analysis of Sensor Data from Longwall Monitoring System. In Intelligent Systems in Production Engineering and Maintenance; Burduk, A., Chlebus, E., Nowakowski, T., Tubis, A., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 611–621. [Google Scholar]
- David McHutchon, Industry 4.0 in Mining—Challenges and Opportunities. Available online: https://www.minexforum.com/en/industry-4-0-in-mining-challenges-and-opportunities/ (accessed on 25 September 2019).
- van der Aalst, W.; Zhao, J.L.; Wang, H. Editorial: Business Process Intelligence: Connecting Data and Processes. ACM Trans. Manag. Inf. Syst. 2015, 5. [Google Scholar] [CrossRef]
- Maita, A.R.C.; Martins, L.C.; López Paz, C.R.; Rafferty, L.; Hung, P.C.K.; Peres, S.M.; Fantinato, M. A systematic mapping study of process mining. Enterp. Inf. Syst. 2018, 12, 505–549. [Google Scholar] [CrossRef]
- Dumas, M.; La Rosa, M.; Mendling, J.; Reijers, H.A. Fundamentals of Business Process Management; Springer: Berlin/Heidelberg, Germany, 2013; ISBN 9783642331428. [Google Scholar]
- Pujari, A.K. Data Mining Techniques; Universities Press: Hyderguda, India, 2001; ISBN 8173713804. [Google Scholar]
- Azevedo, A. Data Mining and Knowledge Discovery in Databases. In Advanced Methodologies and Technologies in Network Architecture, Mobile Computing, and Data Analytics; M. Khosrow-Pour, D.B.A., Ed.; IGI Global: Hershey, PA, USA, 2019; pp. 502–514. [Google Scholar]
- Larose, D.T.; Larose, C.D. Discovering Knowledge In Data: An Introduction to Data Mining, 2nd ed.; Wiley: Hoboken, NJ, USA, 2014; ISBN 9780470908747. [Google Scholar]
- zur Muehlen, M.; Shapiro, R. Business Process Analytics. In Handbook on Business Process Management 2: Strategic Alignment, Governance, People and Culture; vom Brocke, J., Rosemann, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 243–263. [Google Scholar]
- Internal Documentation of Talpasolutions GmbH. Talpasolutions GmbH; Essen, Germany, Unpublished work; 2018.
- Krot, P.; Sliwinski, P.; Zimroz, R.; Gomolla, N. The identification of operational cycles in the monitoring systems of underground vehicles. Measurement 2020, 151, 107–111. [Google Scholar] [CrossRef]
- van der Aalst, W. Process Mining: Data Science in Action; Springer-Verlag: Berlin/Heidelberg, Germany, 2016; ISBN 9783662498514. [Google Scholar]
- van der Aalst, W.; Adriansyah, A.; de Medeiros, A.K.A.; Arcieri, F.; Baier, T.; Blickle, T.; Bose, J.C.; van den Brand, P.; Brandtjen, R.; Buijs, J.; et al. Process Mining Manifesto. Business Process Management Workshops; Daniel, F., Barkaoui, K., Dustdar, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 169–194. [Google Scholar]
- van der Aalst, W.M.P. Process-Aware Information Systems: Lessons to Be Learned from Process Mining. In Transactions on Petri Nets and Other Models of Concurrency II: Special Issue on Concurrency in Process-Aware Information Systems; Jensen, K., van der Aalst, W.M.P., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–26. [Google Scholar]
- Leemans, S.J.J.; Poppe, E.; Wynn, M.T. Directly Follows-Based Process Mining: Exploration & a Case Study. In Proceedings of the 2019 International Conference on Process Mining (ICPM), Aachen, Germany, 24–26 June 2019; pp. 25–32. [Google Scholar]
- van der Aalst, W.M.P. Decomposing Petri Nets for Process Mining: A Generic Approach. Distrib. Parallel Databases 2013, 31, 471–507. [Google Scholar] [CrossRef]
- van Der Aalst, W.M.P.; Van Hee, K.M.; Ter Hofstede, A.H.M.; Sidorova, N.; Verbeek, H.M.W.; Voorhoeve, M.; Wynn, M.T. Soundness of workflow nets: Classification, decidability, and analysis. Form. Asp. Comput. 2011, 23, 333–363. [Google Scholar] [CrossRef]
- Bauer, M.; Senderovich, A.; Gal, A.; Grunske, L.; Weidlich, M. How Much Event Data Is Enough? A Statistical Framework for Process Discovery. In Advanced Information Systems Engineering. CAiSE 2018; Krogstie, J., Reijers, H., Eds.; Springer: Cham, Switzerland, 2018; pp. 239–256. [Google Scholar]
- Kerremans, M. Market Guide for Process Mining. Gartner 2019, 1–33. [Google Scholar]
- Bru, F.; Claes, J. The perceived quality of process discovery tools. arXiv 2018, arXiv:1808.06475. Available online: https://arxiv.org/ftp/arxiv/papers/1808/1808.06475.pdf (accessed on 1 February 2020).
- Claes, J.; Poels, G. Process Mining and the ProM Framework: An Exploratory Survey. In Proceedings of the Business Process Management Workshops; La Rosa, M., Soffer, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 187–198. [Google Scholar]
- La Rosa, M.; Reijers, H.A.; Van Der Aalst, W.M.P.; Dijkman, R.M.; Mendling, J.; Dumas, M.; García-Bañuelos, L. APROMORE: An advanced process model repository. Expert Syst. Appl. 2011, 38, 7029–7040. [Google Scholar] [CrossRef]
- Nguyen, H.; Dumas, M.; ter Hofstede, A.H.M.; La Rosa, M.; Maggi, F.M. Business Process Performance Mining with Staged Process Flows. In Advanced Information Systems Engineering; Nurcan, S., Soffer, P., Bajec, M., Eder, J., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 167–185. [Google Scholar]
- Dees, M.; de Leoni, M.; Mannhardt, F. Enhancing Process Models to Improve Business Performance: A Methodology and Case Studies. In On the Move to Meaningful Internet Systems. OTM 2017 Conferences; Panetto, H., Debruyne, C., Gaaloul, W., Papazoglou, M., Paschke, A., Ardagna, C.A., Meersman, R., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 232–251. [Google Scholar]
- dos Santos Garcia, C.; Meincheim, A.; Faria Junior, E.R.; Dallagassa, M.R.; Sato, D.M.V.; Carvalho, D.R.; Santos, E.A.P.; Scalabrin, E.E. Process mining techniques and applications—A systematic mapping study. Expert Syst. Appl. 2019, 133, 260–295. [Google Scholar] [CrossRef]
- Rozinat, A.; de Jong, I.S.M.; Günther, C.W.; van der Aalst, W.M.P. Process mining applied to the test process of wafer scanners in ASML. IEEE Trans. Syst. Man Cybern. Part C Appl. Rev. 2009, 39, 474–479. [Google Scholar] [CrossRef]
- Liu, T.; Yi, H.; Ni, Z.; Liu, X. A closed-loop workflow management technique based on process mining. In Proceedings of the 15th International Conference on Mechatronics and Machine Vision in Practice, Auckland, New Zealand, 2–4 December 2008; pp. 435–440. [Google Scholar]
- Ho, G.T.S.; Lau, H.C.W. Development of an olap–fuzzy based process mining system for quality improvement. IFIP Int. Fed. Inf. Process. 2006, 228, 243–258. [Google Scholar]
- Lee, S.K.; Kim, B.; Huh, M.; Cho, S.; Park, S.; Lee, D. Mining transportation logs for understanding the after-assembly block manufacturing process in the shipbuilding industry. Expert Syst. Appl. 2013, 40, 83–95. [Google Scholar] [CrossRef]
- Myers, D.; Suriadi, S.; Radke, K.; Foo, E. Anomaly detection for industrial control systems using process mining. Comput. Secur. 2018, 78, 103–125. [Google Scholar] [CrossRef]
- Cleveland, W.S. Robust Locally Weighted Regression and Smoothing Scatterplots. J. Am. Stat. Assoc. 1979, 74, 829–836. [Google Scholar] [CrossRef]
- Diba, K.; Batoulis, K.; Weidlich, M.; Weske, M. Extraction, correlation, and abstraction of event data for process mining. WIREs Data Mining Knowl Discov. 2019, e1346. [Google Scholar] [CrossRef]
- Riboni, D.; Murtas, M. Sensor-based activity recognition: One picture is worth a thousand words. Future Gen. Computer Syst. 2019, 101, 709–722. [Google Scholar] [CrossRef]
- Günther, C.W.; Rozinat, A. Disco: Discover your processes. In Proceedings of the Demonstration Track of the 10th International Conference on Business Process Management, BPM Demos 2012, Tallinn, Estonia, 4 September 2012; pp. 40–44. [Google Scholar]
- Disco User Guide. Available online: https://fluxicon.com/book/read/reference/ (accessed on 15 October 2019).
- Żyrek, L.; Zasadni, W.; Lubryka, J.; Szołtysik, R. ENDIS 4.0 as replay on requirements of Industry 4.0 in field of power supply and automation for mining. Min. – Informatics, Autom. Electr. Eng. 2018, 533, 95–100. [Google Scholar] [CrossRef]
- Vaidya, S.; Ambad, P.; Bhosle, S. Industry 4.0—A Glimpse. Procedia Manuf. 2018, 20, 233–238. [Google Scholar] [CrossRef]
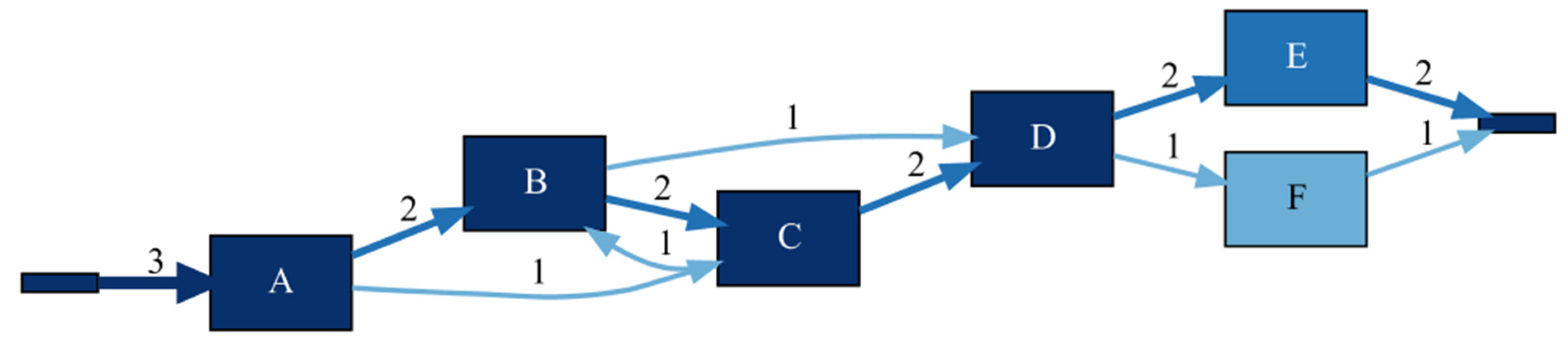

| Case Id | Activity | Timestamp |
|---|---|---|
| 1 | A | 01.04.2017 00:56:15 |
| 1 | B | 01.04.2017 01:24:25 |
| 1 | C | 01.04.2017 01:52:14 |
| 1 | D | 01.04.2017 01:52:35 |
| 1 | E | 01.04.2017 01:59:21 |
| 2 | A | 01.04.2017 02:13:35 |
| 2 | C | 01.04.2017 02:15:17 |
| 2 | B | 01.04.2017 02:22:06 |
| 2 | D | 01.04.2017 02:23:08 |
| 2 | F | 01.04.2017 02:24:31 |
| 3 | A | 01.04.2017 02:35:17 |
| 3 | B | 01.04.2017 02:41:44 |
| 3 | C | 01.04.2017 02:46:09 |
| 3 | D | 01.04.2017 02:49:09 |
| 3 | E | 01.04.2017 02:55:37 |
| Shift Id | Activity | Timestamp Activity Start | Timestamp Activity End |
|---|---|---|---|
| … | … | … | … |
| 1 | DRILLING | 2019-07-31 22:24:15 | 2019-07-31 22:24:55 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:24:56 | 2019-07-31 22:24:56 |
| 1 | ANCHORING | 2019-07-31 22:24:57 | 2019-07-31 22:25:04 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:25:05 | 2019-07-31 22:25:09 |
| 1 | HOLE_SETUP | 2019-07-31 22:25:10 | 2019-07-31 22:25:10 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:25:11 | 2019-07-31 22:25:11 |
| 1 | HOLE_SETUP | 2019-07-31 22:25:12 | 2019-07-31 22:25:16 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:25:17 | 2019-07-31 22:25:19 |
| 1 | DRILLING | 2019-07-31 22:25:20 | 2019-07-31 22:25:58 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:25:59 | 2019-07-31 22:25:59 |
| 1 | ANCHORING | 2019-07-31 22:26:00 | 2019-07-31 22:26:08 |
| 1 | TRANSITIONAL_DELAY | 2019-07-31 22:26:09 | 2019-07-31 22:26:11 |
| 1 | HOLE_SETUP | 2019-07-31 22:26:12 | 2019-07-31 22:26:13 |
| … | … | … | … |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Brzychczy, E.; Gackowiec, P.; Liebetrau, M. Data Analytic Approaches for Mining Process Improvement—Machinery Utilization Use Case. Resources 2020, 9, 17. https://doi.org/10.3390/resources9020017
Brzychczy E, Gackowiec P, Liebetrau M. Data Analytic Approaches for Mining Process Improvement—Machinery Utilization Use Case. Resources. 2020; 9(2):17. https://doi.org/10.3390/resources9020017
Chicago/Turabian StyleBrzychczy, Edyta, Paulina Gackowiec, and Mirko Liebetrau. 2020. "Data Analytic Approaches for Mining Process Improvement—Machinery Utilization Use Case" Resources 9, no. 2: 17. https://doi.org/10.3390/resources9020017
APA StyleBrzychczy, E., Gackowiec, P., & Liebetrau, M. (2020). Data Analytic Approaches for Mining Process Improvement—Machinery Utilization Use Case. Resources, 9(2), 17. https://doi.org/10.3390/resources9020017






