Time- and Amplitude-Controlled Power Noise Generator against SPA Attacks for FPGA-Based IoT Devices
Abstract
:1. Introduction
- Simple Power Analysis (SPA) consists of information being extracted directly from power traces [14]. This type of attack does not require specialized instrumentation and allows extracting information from a low number of power traces; thus, it is critical to implement some kind of countermeasure to prevent these attacks. These countermeasures are usually based on masking operations executed in the system [15] by randomizing the order in which instructions are executed [16], or masking the data involved in some operations by means of arithmetic or boolean operations with random values [17]. Other very effective countermeasures consist of generating “power noise” to prevent useful information from being extracted from the power traces [18,19].
- Differential Power Analysis (DPA) is based on analysis of the statistical correlation of acquired power traces [20]. Attacks based on DPA are more difficult to avoid than those based on SPA, especially if they are combined with other techniques such as Artificial Intelligence (AI) [21], because the effects of masking or noise introduction can be overridden. On the other hand, this type of attack requires the acquisition of a high number of power traces, and frequent changes of the secret key can be an effective countermeasure in the particular case of cryptographic circuits. In this case, a Public-Key Cryptosystem (PKC) is usually required, which may be provided by hybrid cryptoprocessors such as in [22] or [4] in order to enable the completion of these frequent changes securely. Other countermeasures in the literature include advanced masking [23] or sophisticated power noise generation [24].
- Correlation Power Analysis (CPA) is based on the same principles as DPA, and the only difference is that CPA makes use of the correlation factor instead of plain correlation [25] to guess the secret key or any other relevant information. It provides similar results and also require a high number or power traces [26,27].
2. Previous Work
2.1. Side Channel Attacks on Computing and Cryptographic Circuits
2.2. Countermeasures for SPA Attacks
- Use of voltage regulators. In [52], it is shown that Low-Dropout Regulators (LDO) help to de-correlate the input current from the current drawn by the circuit. A more advanced proposal is carried out in [53], where a converter-gating technique including a multi-phase switched-capacitor converter is used for de-correlating currents. These solutions are intended for ASIC implementations of the circuit under protection, where the voltage regulator is included in the same chip.
- Masking arithmetic or boolean operations. As has been previously commented, a method to hide the results of cryptographic operations is to mask the operands or the results with boolean or arithmetic operations with random values. In [55], the addition of a randomly generated mask is proposed for protecting AES against SPA and DPA, while [56] proposes the use of multiplication as the masking arithmetic operation. As an example of the use of boolean masking, [57] proposes the use of the operation. These techniques are not suitable for microcrontollers used in IoT because they require additional area and increment the processing time of software programs.
- In the case of processing systems, the combination of the techniques above with the specific design of some modules of the microprocessor can lead to the implementation of designs resistant to power attacks. An example can be found in [58], in which a RISC-V processor is modified in order to be resistant to power side channel attacks, but at the cost of severe area overhead.
2.3. Power Watermarking
3. Power Noise Generation
- The amplitude of the peaks should be similar to that generated by the operations of interest.
- The times when the peaks are generated should be random.
3.1. Power Consumption Generators in FPGAs
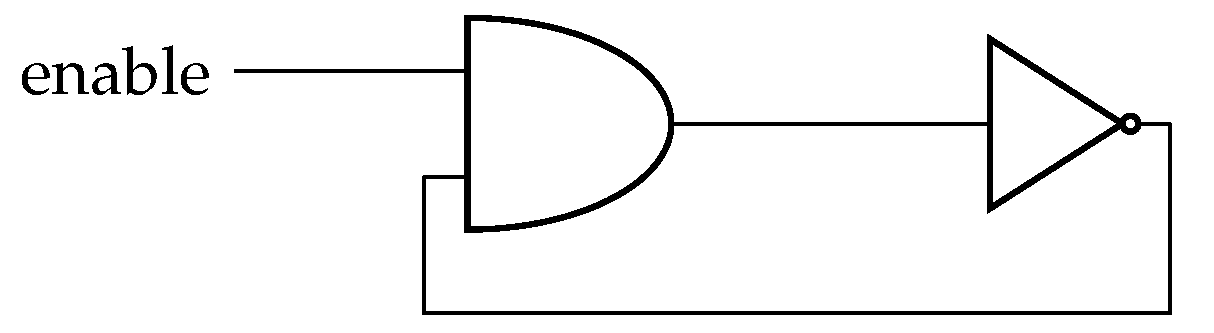
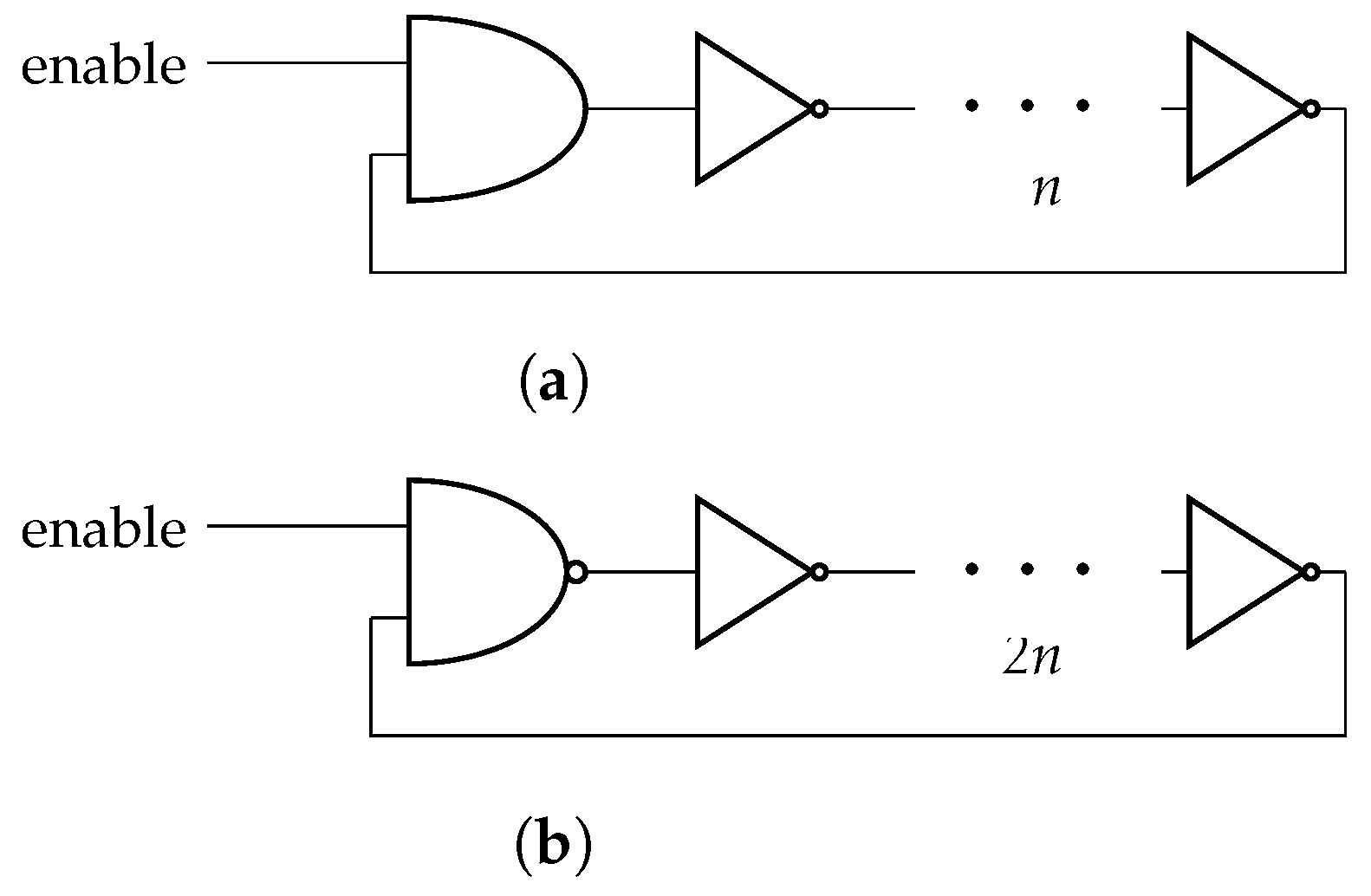
3.2. Xored High Consuming Modules (XHCMs)
4. Controlled XHCMs
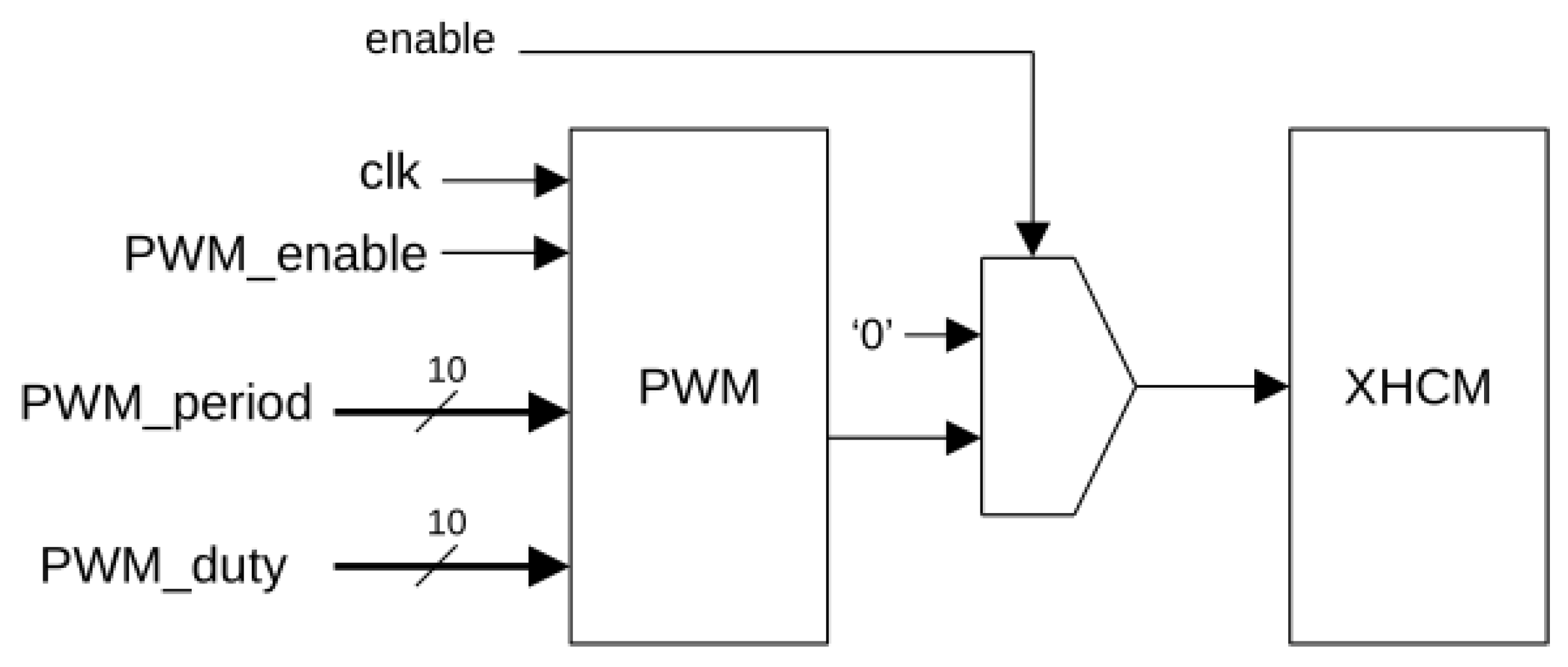
4.1. PWM-XHCM
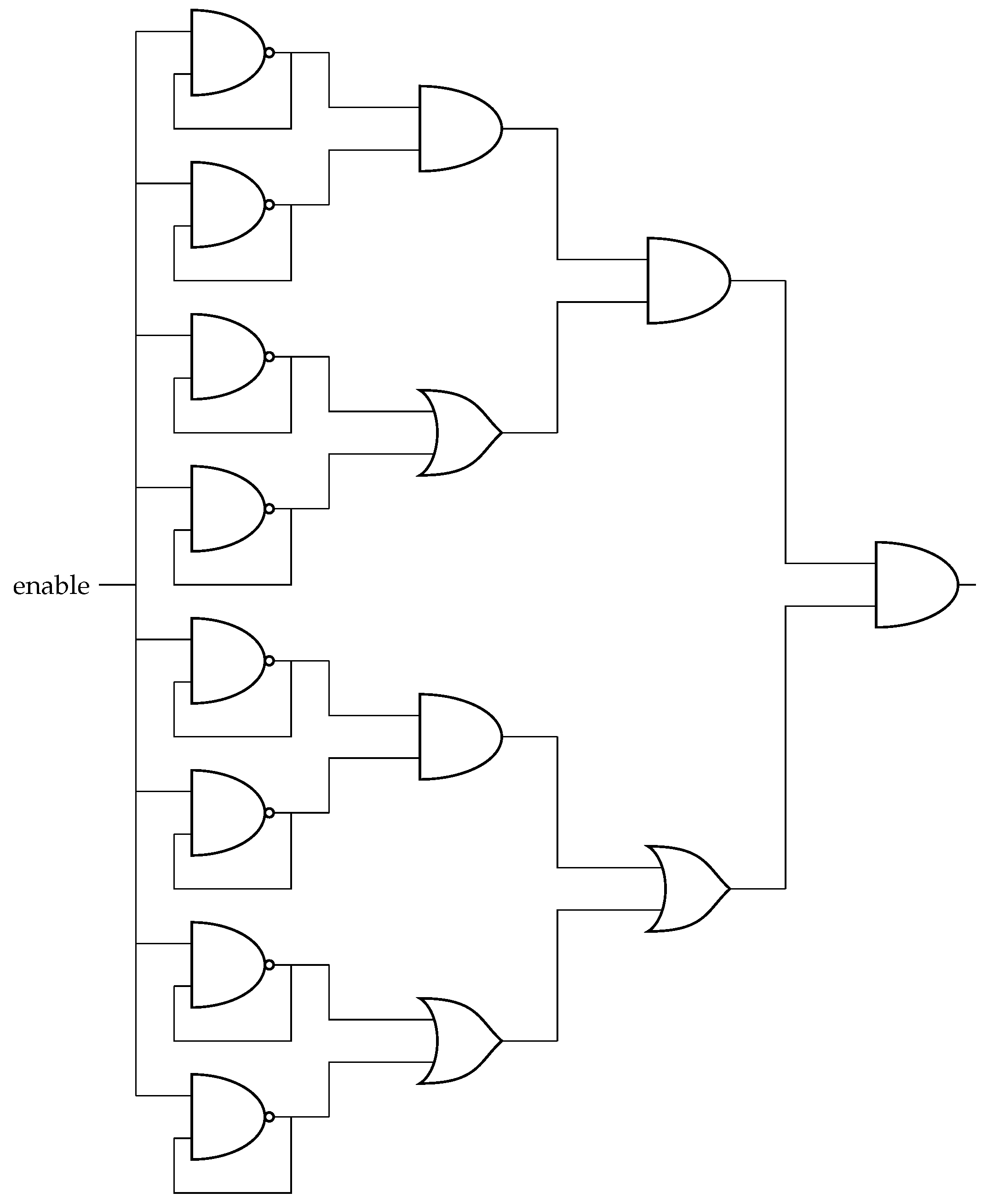
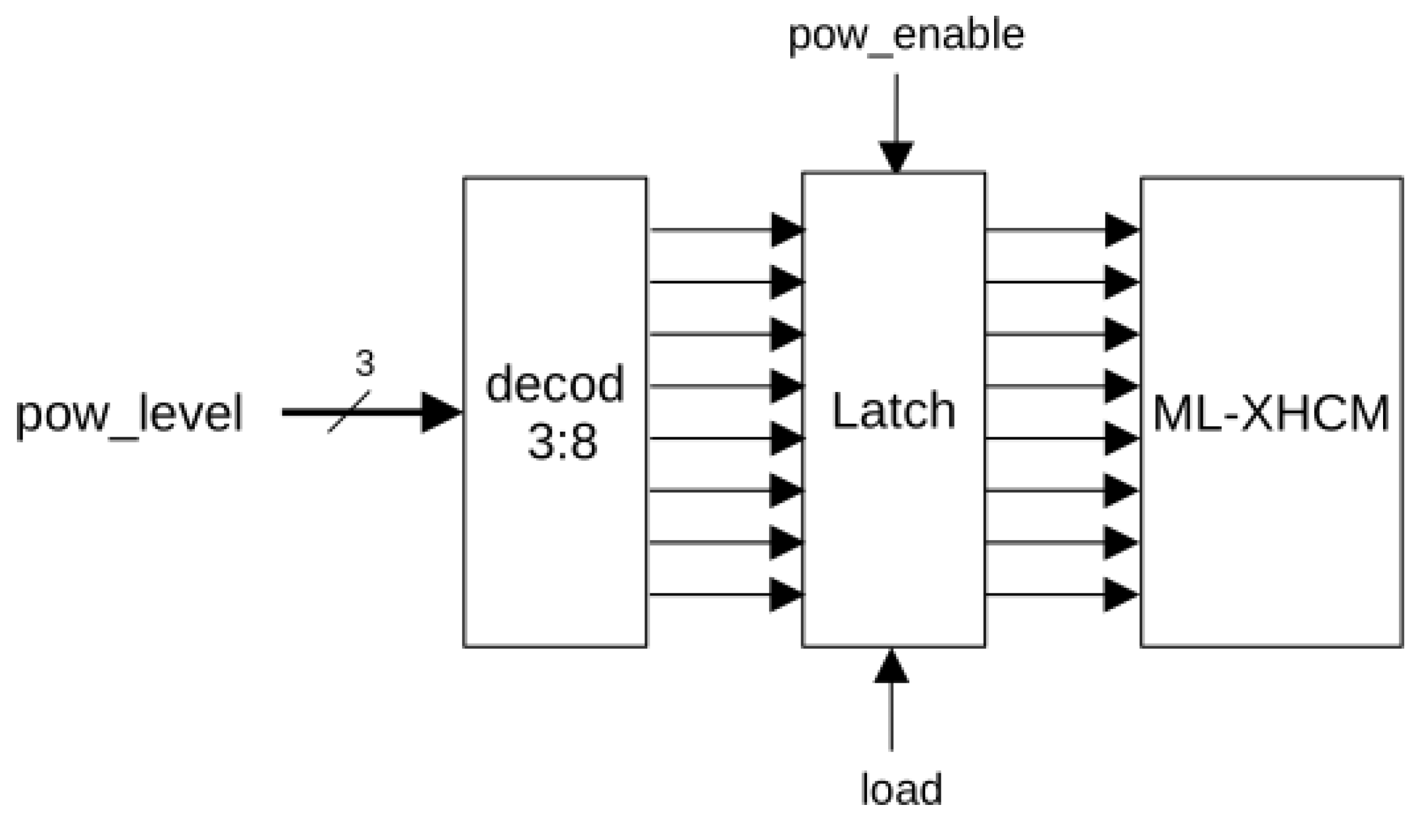
4.2. Multi-Level XHCMs
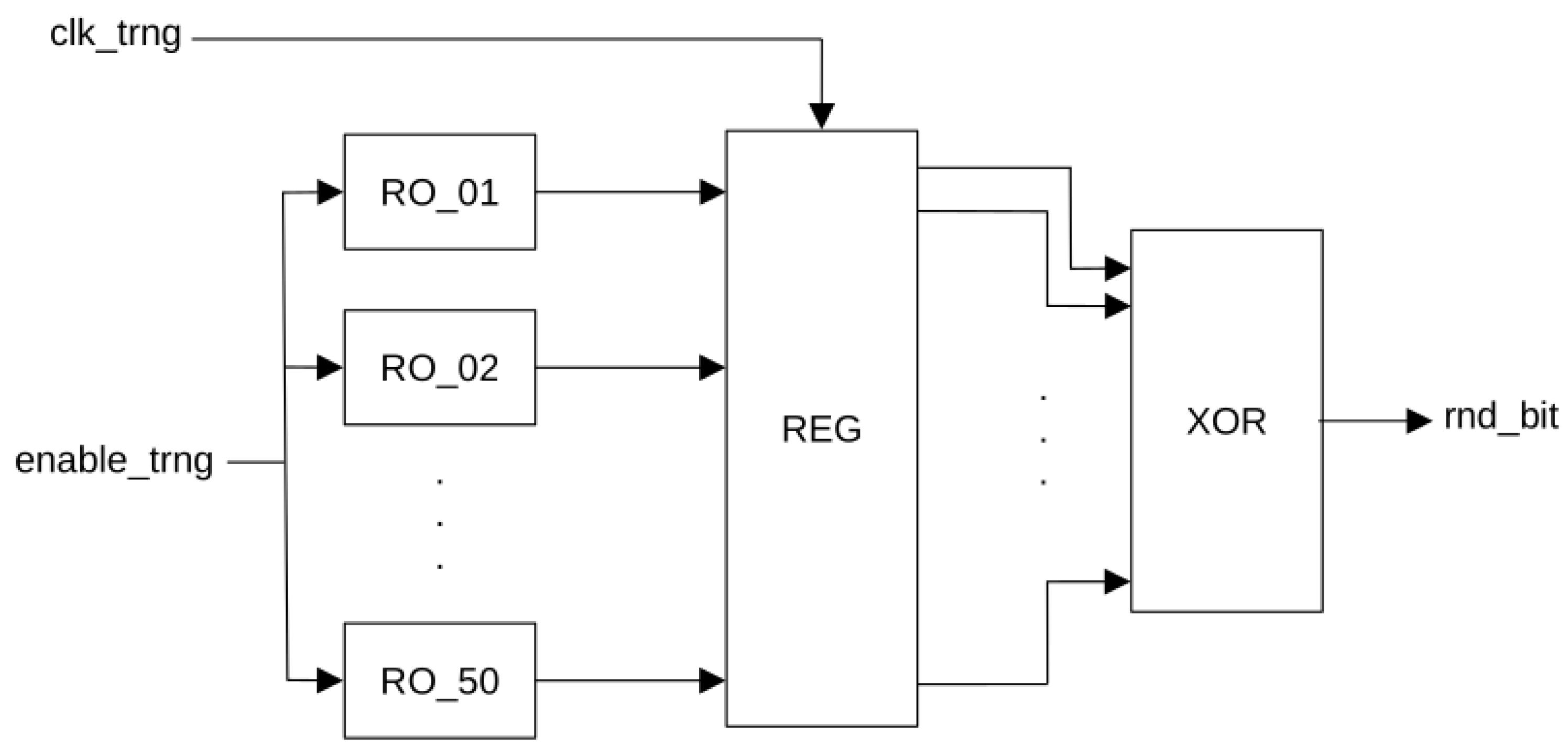
4.3. Random Number Generation
4.4. Randomized ML-XHCM
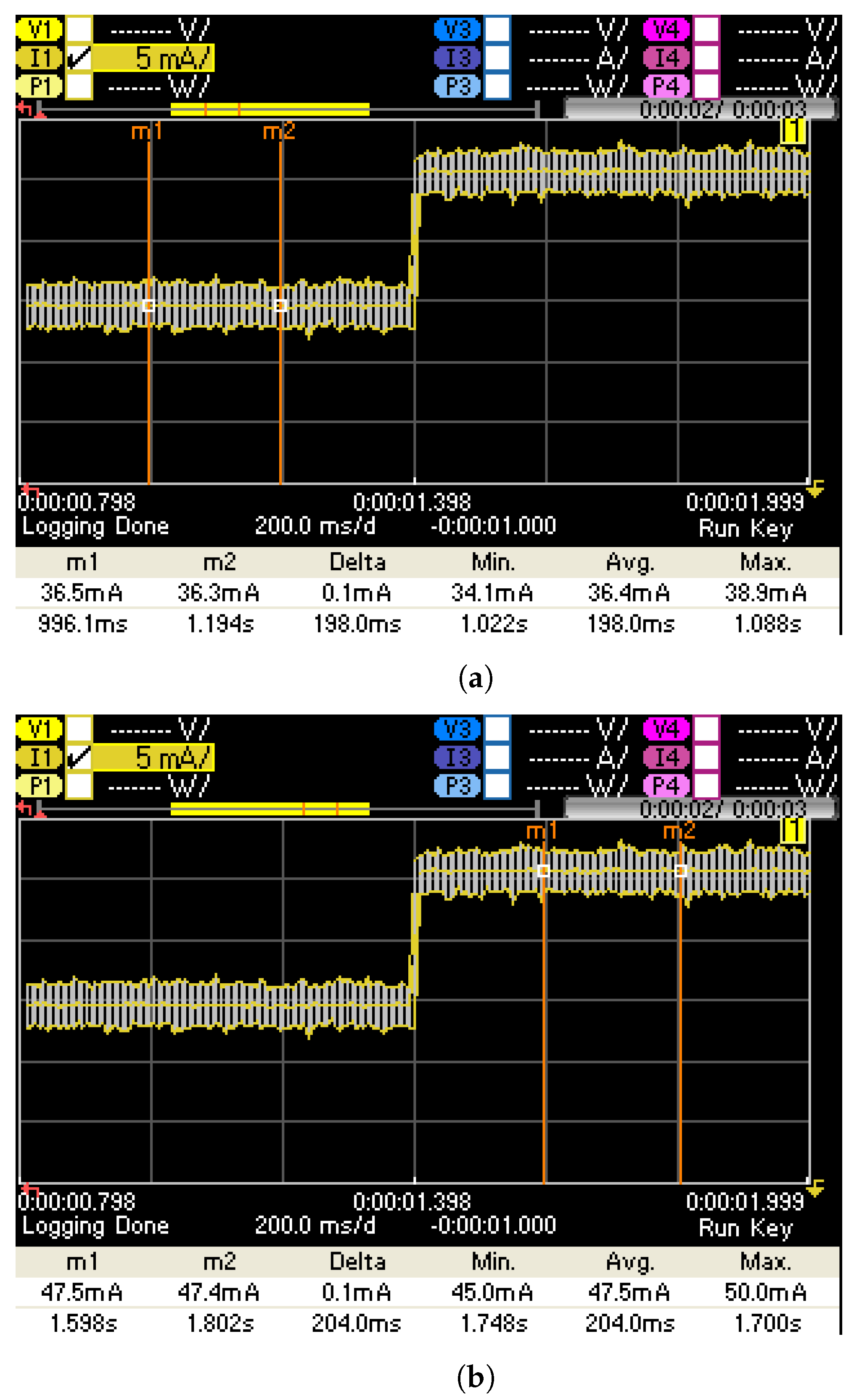
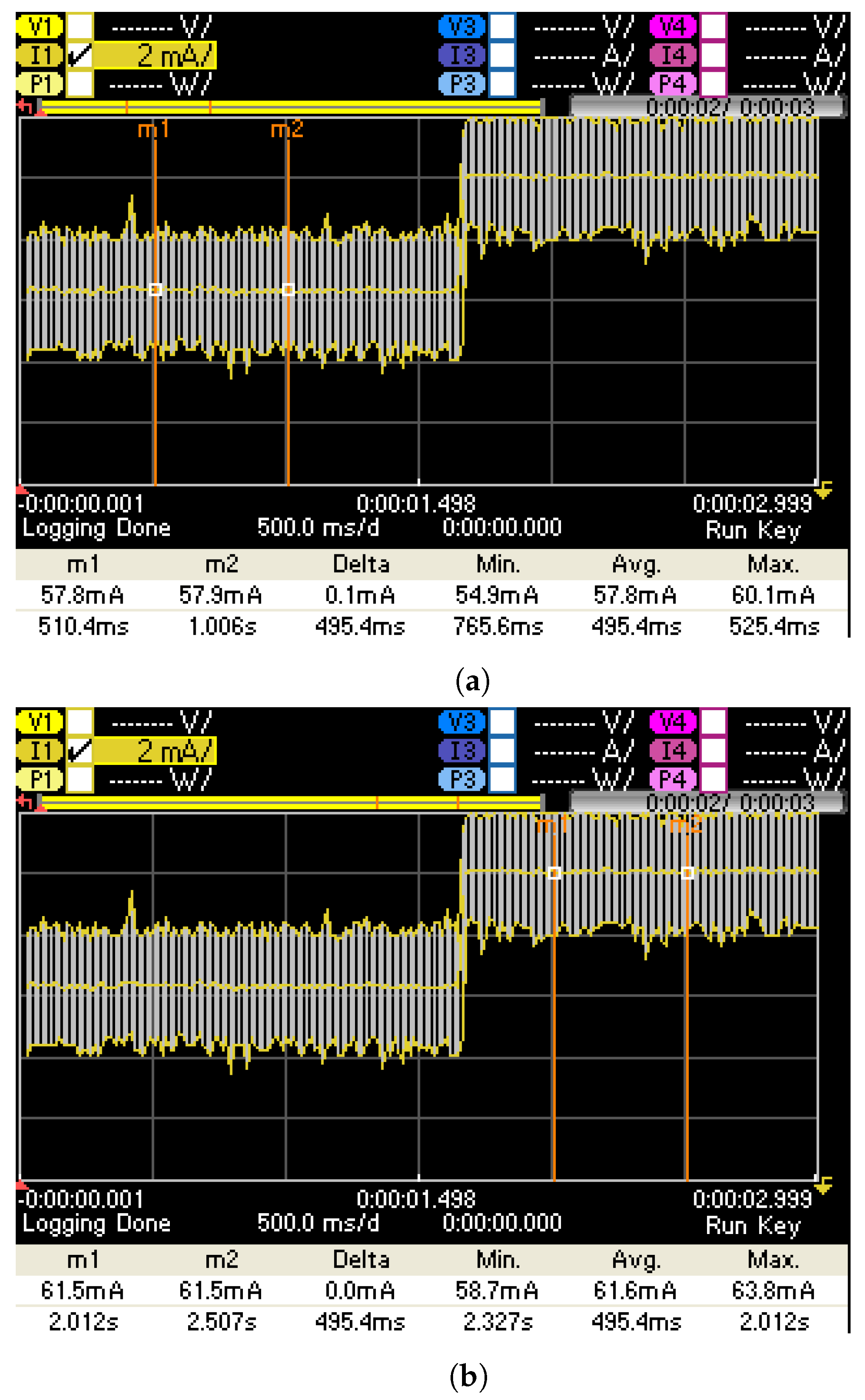
5. Experimental Results
6. Conclusions and Future Work
- An improved high-consuming power generator, XHCM, and a PWM-controlled variant, PWM-XHCM, have been developed, thus providing an efficient solution to extract digital signatures through the power side channel.
- A modification of XCHM enabling the control of both amplitude and time domains, named ML-XHCM, has been proposed, providing a powerful tool for the protection of processing units against SPA attacks in IoT devices implemented on FPGAs. Moreover, a time-randomized version, called RML-XHCM, has also been developed as a proof-of-concept.
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Park, C.S.; Nam, H.M. Security architecture and protocols for secure MQTT-SN. IEEE Access 2020, 8, 226422–226436. [Google Scholar] [CrossRef]
- Kim, Y.; Seo, S.C. Efficient Implementation of AES and CTR_DRBG on 8-bit AVR-based Sensor Nodes. IEEE Access 2021, 9, 30496–30510. [Google Scholar] [CrossRef]
- Parrilla, L.; Castillo, E.; López-Ramos, J.A.; Álvarez-Bermejo, J.A.; García, A.; Morales, D.P. Unified compact ECC-AES co-processor with group-key support for IoT devices in wireless sensor networks. Sensors 2018, 18, 251. [Google Scholar] [CrossRef]
- Devi, M.; Majumder, A. Side-channel attack in Internet of Things: A survey. In Applications of Internet of Things; Springer: Berlin/Heidelberg, Germany, 2021; pp. 213–222. [Google Scholar]
- Park, J.; Tyagi, A. Using Power Clues to Hack IoT Devices: The power side channel provides for instruction-level disassembly. IEEE Consum. Electron. Mag. 2017, 6, 92–102. [Google Scholar] [CrossRef]
- Wei, L.; Luo, B.; Li, Y.; Liu, Y.; Xu, Q. I know what you see: Power side-channel attack on convolutional neural network accelerators. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 393–406. [Google Scholar]
- Naghibijouybari, H.; Neupane, A.; Qian, Z.; Abu-Ghazaleh, N. Rendered insecure: Gpu side channel attacks are practical. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 2139–2153. [Google Scholar]
- Maji, S.; Banerjee, U.; Chandrakasan, A.P. Leaky nets: Recovering embedded neural network models and inputs through simple power and timing side-channels—Attacks and defenses. IEEE Internet Things J. 2021, 8, 12079–12092. [Google Scholar] [CrossRef]
- Mangard, S. A simple power-analysis (SPA) attack on implementations of the AES key expansion. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2002; pp. 343–358. [Google Scholar]
- Kadir, S.A.; Sasongko, A.; Zulkifli, M. Simple power analysis attack against elliptic curve cryptography processor on FPGA implementation. In Proceedings of the 2011 International Conference on Electrical Engineering and Informatics, Bandung, Indonesia, 17–19 July 2011; pp. 1–4. [Google Scholar]
- Ghandali, S.; Ghandali, S.; Tehranipoor, S. Deep K-TSVM: A Novel Profiled Power Side-Channel Attack on AES-128. IEEE Access 2021, 9, 136448–136458. [Google Scholar] [CrossRef]
- Lyu, Y.; Mishra, P. A survey of side-channel attacks on caches and countermeasures. J. Hardw. Syst. Secur. 2018, 2, 33–50. [Google Scholar] [CrossRef]
- Oswald, E. Enhancing simple power-analysis attacks on elliptic curve cryptosystems. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 82–97. [Google Scholar]
- Akkar, M.L.; Giraud, C. An implementation of DES and AES, secure against some attacks. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Paris, France, 14–16 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 309–318. [Google Scholar]
- Bayrak, A.G.; Velickovic, N.; Ienne, P.; Burleson, W. An architecture-independent instruction shuffler to protect against side-channel attacks. ACM Trans. Archit. Code Optim. (TACO) 2012, 8, 1–19. [Google Scholar] [CrossRef]
- Herbst, C.; Oswald, E.; Mangard, S. An AES smart card implementation resistant to power analysis attacks. In Proceedings of the International Conference on Applied Cryptography and Network Security, Singapore, 6–9 June 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 239–252. [Google Scholar]
- Duan, S.; Wang, W.; Luo, Y.; Xu, X. A survey of recent attacks and mitigation on FPGA systems. In Proceedings of the 2021 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Tampa, FL, USA, 7–9 July 2021; pp. 284–289. [Google Scholar]
- Krautter, J.; Gnad, D.R.; Schellenberg, F.; Moradi, A.; Tahoori, M.B. Active fences against voltage-based side channels in multi-tenant FPGAs. In Proceedings of the 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019; pp. 1–8. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Wang, H.; Dubrova, E. Tandem deep learning side-channel attack against FPGA implementation of AES. In Proceedings of the 2020 IEEE International Symposium on Smart Electronic Systems (iSES) (Formerly iNiS), Chennai, India, 14–16 December 2020; pp. 147–150. [Google Scholar]
- De La Piedra, A.; Braeken, A.; Touhafi, A. Sensor systems based on FPGAs and their applications: A survey. Sensors 2012, 12, 12235–12264. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Han, D.G. Security analysis on dummy based side-channel countermeasures—Case study: AES with dummy and shuffling. Appl. Soft Comput. 2020, 93, 106352. [Google Scholar] [CrossRef]
- Kamoun, N.; Bossuet, L.; Ghazel, A. Correlated power noise generator as a low cost DPA countermeasures to secure hardware AES cipher. In Proceedings of the 2009 3rd International Conference on Signals, Circuits and Systems (SCS), Medenine, Tunisia, 6–8 November 2009; pp. 1–6. [Google Scholar]
- Brier, E.; Clavier, C.; Olivier, F. Correlation power analysis with a leakage model. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Cambridge, MA, USA, 11–13 August 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 16–29. [Google Scholar]
- Alioto, M.; Poli, M.; Rocchi, S. Power analysis attacks to cryptographic circuits: A comparative analysis of DPA and CPA. In Proceedings of the 2008 International Conference on Microelectronics, Medenine, Tunisia, 6–8 November 2008; pp. 333–336. [Google Scholar]
- Fei, Y.; Ding, A.A.; Lao, J.; Zhang, L. A statistics-based success rate model for DPA and CPA. J. Cryptogr. Eng. 2015, 5, 227–243. [Google Scholar] [CrossRef]
- van Geest, J.; Buhan, I. A Side-Channel Based Disassembler for the ARM-Cortex M0. Cryptology ePrint Archive. 2022. Available online: https://eprint.iacr.org/2022/523 (accessed on 23 May 2022).
- Banciu, V.; Oswald, E. Pragmatism vs. elegance: Comparing two approaches to simple power attacks on AES. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design, Leuven, Belgium, 11–12 April 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 29–40. [Google Scholar]
- Bertoni, G.; Zaccaria, V.; Breveglieri, L.; Monchiero, M.; Palermo, G. AES power attack based on induced cache miss and countermeasure. In Proceedings of the International Conference on Information Technology: Coding and Computing (ITCC’05)-Volume II, Las Vegas, NV, 4–6 April 2005; Volume 1, pp. 586–591. [Google Scholar]
- Regazzoni, F.; Wang, Y.; Standaert, F.X. FPGA implementations of the AES masked against power analysis attacks. Proc. COSADE 2011, 2011, 56–66. [Google Scholar]
- Wang, X.; Yueh, W.; Roy, D.B.; Narasimhan, S.; Zheng, Y.; Mukhopadhyay, S.; Mukhopadhyay, D.; Bhunia, S. Role of power grid in side channel attack and power-grid-aware secure design. In Proceedings of the 50th Annual Design Automation Conference, Austin, TX, USA, 29 May–7 June 2013; pp. 1–9. [Google Scholar]
- Liu, P.C.; Chang, H.C.; Lee, C.Y. A low overhead DPA countermeasure circuit based on ring oscillators. IEEE Trans. Circuits Syst. II Express Briefs 2010, 57, 546–550. [Google Scholar]
- Fu, H.P.; Hsiao, J.H.; Liu, P.C.; Chang, H.C.; Lee, C.Y. A low cost DPA-resistant 8-bit AES core based on ring oscillators. In Proceedings of the Technical Program of 2012 VLSI Design, Automation and Test, Hsinchu, Taiwan, 23–25 April 2012; pp. 1–4. [Google Scholar]
- Liu, P.C.; Chang, H.C.; Lee, C.Y. A true random-based differential power analysis countermeasure circuit for an AES engine. IEEE Trans. Circuits Syst. II Express Briefs 2012, 59, 103–107. [Google Scholar] [CrossRef]
- Chung, S.C.; Yu, C.Y.; Lee, S.S.; Chang, H.C.; Lee, C.Y. An improved DPA countermeasure based on uniform distribution random power generator for IoT applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 64, 2522–2531. [Google Scholar] [CrossRef]
- Parrilla, L.; Castillo, E.; Todorovich, E.; García, A.; Morales, D.P.; Botella, G. Improvements for the applicability of power-watermarking to embedded IP cores protection: E-coreIPP. Digit. Signal Process. 2015, 44, 110–122. [Google Scholar] [CrossRef]
- Ziener, D.; Teich, J. Power signature watermarking of IP cores for FPGAs. J. Signal Process. Syst. 2008, 51, 123–136. [Google Scholar] [CrossRef]
- Pub, F. Data Encryption Standard (des). FIPS PUB. 1999, pp. 46–53. Available online: https://www.techtarget.com/searchsecurity/definition/Data-Encryption-Standard (accessed on 24 May 2022).
- Kocher, P.C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 1996; Springer: Berlin/Heidelberg, Germany, 1996; pp. 104–113. [Google Scholar]
- Bertoni, G.; Breveglieri, L.; Fragneto, P.; Macchetti, M.; Marchesin, S. Efficient software implementation of AES on 32-bit platforms. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 159–171. [Google Scholar]
- Ors, S.B.; Gurkaynak, F.; Oswald, E.; Preneel, B. Power-analysis attack on an ASIC AES implementation. In Proceedings of the International Conference on Information Technology: Coding and Computing, 2004. Proceedings. ITCC 2004, Las Vegas, NV, USA, 5–7 April 2004; Volume 2, pp. 546–552. [Google Scholar]
- Renauld, M.; Standaert, F.X.; Veyrat-Charvillon, N. Algebraic side-channel attacks on the AES: Why time also matters in DPA. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Lausanne, Switzerland, 6–9 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 97–111. [Google Scholar]
- Mohamed, M.S.E.; Bulygin, S.; Zohner, M.; Heuser, A.; Walter, M.; Buchmann, J. Improved algebraic side-channel attack on AES. J. Cryptogr. Eng. 2013, 3, 139–156. [Google Scholar] [CrossRef]
- Roche, T.; Lomné, V.; Khalfallah, K. Combined fault and side-channel attack on protected implementations of AES. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Leuven, Belgium, 14–16 September 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 65–83. [Google Scholar]
- Niu, Y.; Zhang, J.; Wang, A.; Chen, C. An efficient collision power attack on AES encryption in edge computing. IEEE Access 2019, 7, 18734–18748. [Google Scholar] [CrossRef]
- Wang, R.; Wang, H.; Dubrova, E.; Brisfors, M. Advanced Far Field EM Side-Channel Attack on AES. In Proceedings of the 7th ACM on Cyber-Physical System Security Workshop, Hong Kong, China, 7 June 2021; pp. 29–39. [Google Scholar]
- Cristiani, V.; Lecomte, M.; Hiscock, T. A bit-level approach to side channel based disassembling. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Prague, Czech Republic, 11–13 November 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 143–158. [Google Scholar]
- Méndez Real, M.; Salvador, R. Physical side-channel attacks on embedded neural networks: A survey. Appl. Sci. 2021, 11, 6790. [Google Scholar] [CrossRef]
- Tillich, S.; Herbst, C.; Mangard, S. Protecting AES software implementations on 32-bit processors against power analysis. In Proceedings of the International Conference on Applied Cryptography and Network Security, Zhuhai, China, 5–8 June 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 141–157. [Google Scholar]
- Krieg, A.; Grinschgl, J.; Steger, C.; Weiss, R.; Haid, J. A side channel attack countermeasure using system-on-chip power profile scrambling. In Proceedings of the 2011 IEEE 17th International On-Line Testing Symposium, Athens, Greece, 13–15 July 2011; pp. 222–227. [Google Scholar]
- Singh, A.; Kar, M.; Ko, J.H.; Mukhopadhyay, S. Exploring power attack protection of resource constrained encryption engines using integrated low-drop-out regulators. In Proceedings of the 2015 IEEE/ACM International Symposium on Low Power Electronics and Design (ISLPED), Rome, Italy, 22–24 July 2015; pp. 134–139. [Google Scholar]
- Yu, W.; Köse, S. A voltage regulator-assisted lightweight AES implementation against DPA attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2016, 63, 1152–1163. [Google Scholar] [CrossRef]
- Kamoun, N.; Bossuet, L.; Ghazel, A. A masked correlated power noise generator use as a second order DPA countermeasure to secure hardware AES cipher. In Proceedings of the ICM 2011 Proceeding, Hammamet, Tunisia, 19–22 December 2011; pp. 1–5. [Google Scholar]
- Messerges, T.S. Securing the AES finalists against power analysis attacks. In Proceedings of the International Workshop on Fast Software Encryption, New York, NY, USA, 10–12 April 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 150–164. [Google Scholar]
- Golić, J.D.; Tymen, C. Multiplicative masking and power analysis of AES. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Hammamet, Tunisia, 19–22 December 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 198–212. [Google Scholar]
- Trichina, E. Combinational Logic Design for AES Subbyte Transformation on Masked Data. Cryptology EPrint Archive. 2003. Available online: https://eprint.iacr.org/2003/236 (accessed on 23 May 2022).
- KF, M.A.; Ganesan, V.; Bodduna, R.; Rebeiro, C. PARAM: A microprocessor hardened for power side-channel attack resistance. In Proceedings of the 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 7–11 December 2020; pp. 23–34. [Google Scholar]
- Castillo, E.; Meyer-Baese, U.; García, A.; Parrilla, L.; Lloris, A. IPP@ HDL: Efficient intellectual property protection scheme for IP cores. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2007, 15, 578–591. [Google Scholar] [CrossRef]
- Degalahal, V.; Tuan, T. Methodology for high level estimation of FPGA power consumption. In Proceedings of the 2005 Asia and South Pacific Design Automation Conference, Shanghai, China, 18–21 January 2005; pp. 657–660. [Google Scholar]
- La, T.M.; Matas, K.; Grunchevski, N.; Pham, K.D.; Koch, D. Fpgadefender: Malicious self-oscillator scanning for xilinx ultrascale+ fpgas. ACM Trans. Reconfigurable Technol. Syst. (TRETS) 2020, 13, 1–31. [Google Scholar] [CrossRef]
- Wold, K.; Tan, C.H. Analysis and enhancement of random number generator in FPGA based on oscillator rings. In Proceedings of the 2008 International Conference on Reconfigurable Computing and FPGAs, Cancun, Mexico, 3–5 December 2008; pp. 385–390. [Google Scholar]
- Parrilla, L.; García, A.; Castillo, E.; Álvarez-Bermejo, J.A.; López-Villanueva, J.A.; Meyer-Baese, U. Dracon: An Open-Hardware Based Platform for Single-Chip Low-Cost Reconfigurable IoT Devices. Electronics 2022, 11, 2080. [Google Scholar] [CrossRef]


| n | LUTs | /LUT | ||
|---|---|---|---|---|
| 1 | 2 | 0.4 mA | 2 mW | 1.00 mW |
| 2 | 3 | 0.4 mA | 2 mW | 0.66 mW |
| 5 | 5 | 0.4 mA | 2 mW | 0.40 mW |
| 9 | 9 | 0.4 mA | 2 mW | 0.22 mW |
| 63 | 48 | 0.7 mA | 3.5 mW | 0.07 mW |
| m | LUTs | /LUT | ||
|---|---|---|---|---|
| 1 | 2 | 0.4 mA | 2.0 mW | 1.00 mW |
| 2 | 4 | 0.5 mA | 2.5 mW | 0.63 mW |
| 4 | 8 | 0.7 mA | 3.5 mW | 0.44 mW |
| 8 | 16 | 1.0 mA | 5.0 mW | 0.31 mW |
| Type of Module | m | LUTs | /LUT | ||
|---|---|---|---|---|---|
| HCM | 1 | 8 | 1.2 mA | 6.0 mW | 0.75 mW |
| HCM | 2 | 16 | 2.1 mA | 10.5 mW | 0.66 mW |
| HCM | 4 | 28 | 3.9 mA | 19.0 mW | 0.68 mW |
| HCM | 8 | 68 | 9.3 mA | 46.5 mW | 0.68 mW |
| XHCM | 1 | 8 | 1.3 mA | 6.5 mW | 0.81 mW |
| XHCM | 2 | 16 | 2.3 mA | 11.5 mW | 0.72 mW |
| XHCM | 4 | 28 | 4.2 mA | 21.0 mW | 0.75 mW |
| XHCM | 8 | 64 | 9.3 mA | 46.5 mW | 0.73 mW |
| HCM-gated | 2 | 16 | 2.1 mA | 10.5 mW | 0.66 mW |
| HCM-gated | 4 | 29 | 4.2 mA | 21.0 mW | 0.72 mW |
| HCM-gated | 8 | 66 | 9.3 mA | 46.5 mW | 0.70 mW |
| XHCM-gated | 2 | 16 | 2.4 mA | 12.0 mW | 0.75 mW |
| XHCM-gated | 4 | 37 | 5.8 mA | 29.0 mW | 0.78 mW |
| XHCM-gated | 8 | 67 | 11.1 mA | 55.5 mW | 0.83 mW |
| Duty Cycle | ||
|---|---|---|
| 20% | 1.9 mA | 9.0 mW |
| 40% | 3.8 mA | 19.0 mW |
| 60% | 5.8 mA | 29.0 mW |
| 80% | 8.6 mA | 43.0 mW |
| Type of Module | Amp. Levels | %act.time | LUTs | Application | |||
|---|---|---|---|---|---|---|---|
| XHCM | 8 | 1 | 100 | 8 | 1.3 mA | 0.81 mW/LUT | power watermarking |
| XHCM | 16 | 1 | 100 | 16 | 2.4 mA | 0.75 mW/LUT | power watermarking |
| XHCM | 32 | 1 | 100 | 37 | 5.8 mA | 0.78 mW/LUT | power watermarking |
| XHCM | 64 | 1 | 100 | 67 | 11.1 mA | 0.83 mW/LUT | power watermarking |
| PWM-XHCM | 32 | 1024 | 100 | 59 | 0.004 mA | 0.35 mW/LUT | power watermarking |
| PWM-XHCM | 64 | 1024 | 100 | 80 | 0.009 mA | 0.58 mW/LUT | power watermarking |
| ML-XHCM | 8 | 8 | 100 | 17 | 0.16 mA | 0.38 mW/LUT | power masking |
| ML-XHCM | 16 | 16 | 100 | 27 | 0.13 mA | 0.39 mW/LUT | power masking |
| ML-XHCM | 32 | 32 | 100 | 49 | 0.13 mA | 0.42 mW/LUT | power masking |
| RML-XHCM | 8 | 8 | 50 | 113 | 0.16 mA | 0.057 mW/LUT | power masking |
| RML-XHCM | 8 | 8 | 25 | 118 | 0.16 mA | 0.054 mW/LUT | power masking |
| RML-XHCM | 8 | 8 | 12.5 | 118 | 0.16 mA | 0.054 mW/LUT | power masking |
| RML-XHCM | 16 | 16 | 50 | 127 | 0.13 mA | 0.082 mW/LUT | power masking |
| RML-XHCM | 16 | 16 | 25 | 129 | 0.13 mA | 0.081 mW/LUT | power masking |
| RML-XHCM | 16 | 16 | 12.5 | 129 | 0.13 mA | 0.081 mW/LUT | power masking |
| RML-XHCM | 32 | 32 | 50 | 147 | 0.13 mA | 0.14 mW/LUT | power masking |
| RML-XHCM | 32 | 32 | 25 | 138 | 0.13 mA | 0.15 mW/LUT | power masking |
| RML-XHCM | 32 | 32 | 12 | 138 | 0.13 mA | 0.15 mW/LUT | power masking |
| Module | Amp. Levels | %act.time | LUTs | Amplitude Control | Time Control | ||
|---|---|---|---|---|---|---|---|
| [19] | 620 | 32 | 100 | - | - | Controlled by sensor | Random based on LFSR |
| [24] | - | - | 100 | 104 | - | Fixed by algorithm | Fixed by algorithm |
| [54] | - | - | 100 | 456 | - | Fixed by algorithm | Fixed by algorithm |
| ML-XHCM16 (this work) | 16 | 16 | 100 | 27 | 0.39 mW/LUT | Customizable | Customizable |
| ML-XHCM32 (this work) | 32 | 32 | 100 | 49 | 0.42 mW/LUT | Customizable | Customizable |
| RML-XHCM16 (this work) | 16 | 16 | 12.5 | 129 | 0.081 mW/LUT | TRNG | TRNG |
| RML-XHCM32 (this work) | 32 | 32 | 12.5 | 138 | 0.15 mW/LUT | TRNG | TRNG |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Parrilla, L.; García, A.; Castillo, E.; Rodríguez-Bolívar, S.; López-Villanueva, J.A. Time- and Amplitude-Controlled Power Noise Generator against SPA Attacks for FPGA-Based IoT Devices. J. Low Power Electron. Appl. 2022, 12, 48. https://doi.org/10.3390/jlpea12030048
Parrilla L, García A, Castillo E, Rodríguez-Bolívar S, López-Villanueva JA. Time- and Amplitude-Controlled Power Noise Generator against SPA Attacks for FPGA-Based IoT Devices. Journal of Low Power Electronics and Applications. 2022; 12(3):48. https://doi.org/10.3390/jlpea12030048
Chicago/Turabian StyleParrilla, Luis, Antonio García, Encarnación Castillo, Salvador Rodríguez-Bolívar, and Juan Antonio López-Villanueva. 2022. "Time- and Amplitude-Controlled Power Noise Generator against SPA Attacks for FPGA-Based IoT Devices" Journal of Low Power Electronics and Applications 12, no. 3: 48. https://doi.org/10.3390/jlpea12030048
APA StyleParrilla, L., García, A., Castillo, E., Rodríguez-Bolívar, S., & López-Villanueva, J. A. (2022). Time- and Amplitude-Controlled Power Noise Generator against SPA Attacks for FPGA-Based IoT Devices. Journal of Low Power Electronics and Applications, 12(3), 48. https://doi.org/10.3390/jlpea12030048








