Security and Resilience of a Data Space Based Manufacturing Supply Chain
Abstract
1. Introduction
2. Background and Literature Review
2.1. System Security Engineering in Supply Chain Management
2.2. Resilience in Systems Engineering
2.3. Data Space
2.4. Literature Review of Interoperable System in Supply Chain
3. Research Methodologies
3.1. Enterprise Architecture (EA) Modeling: Theoretical Background
3.2. Overview of Methodology
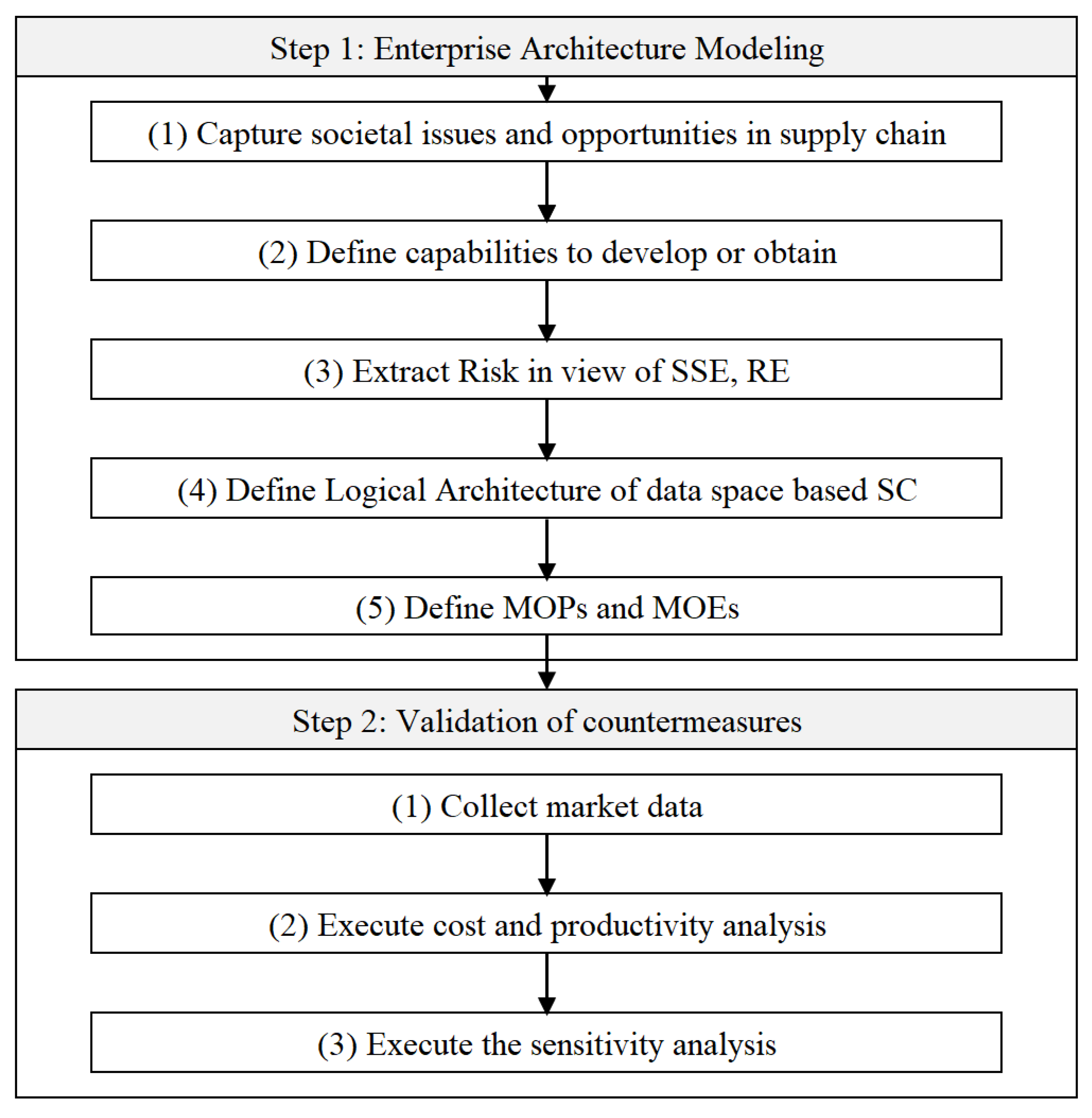
3.2.1. (Step 1) Enterprise Architecture Modeling of System of Systems
- (1)
- Capture issues and opportunities in the supply chain (Section 4.1.1 and Section 4.1.2):
- (2)
- Define capabilities to develop or obtain a resilient manufacturing supply chain (Section 4.1.3):
- (3)
- Extract risks in view of SSE and RE (Section 4.2.1):
- (4)
- Define logical architecture of data space-based supply chain (Section 4.2.2):
- (5)
- Define MOP (Measure of Performance) and MOE (Measure of Effectiveness) (Section 4.2.3):
3.2.2. (Step 2) Validation: Parts Supply Disruption and Alternative Manufacturing
- (1)
- Collect data from service provider (Section 4.3.1)
- (2)
- Execute cost and productivity analysis (Section 4.3.2)
- (3)
- Execute sensitivity analysis (Section 4.3.3)
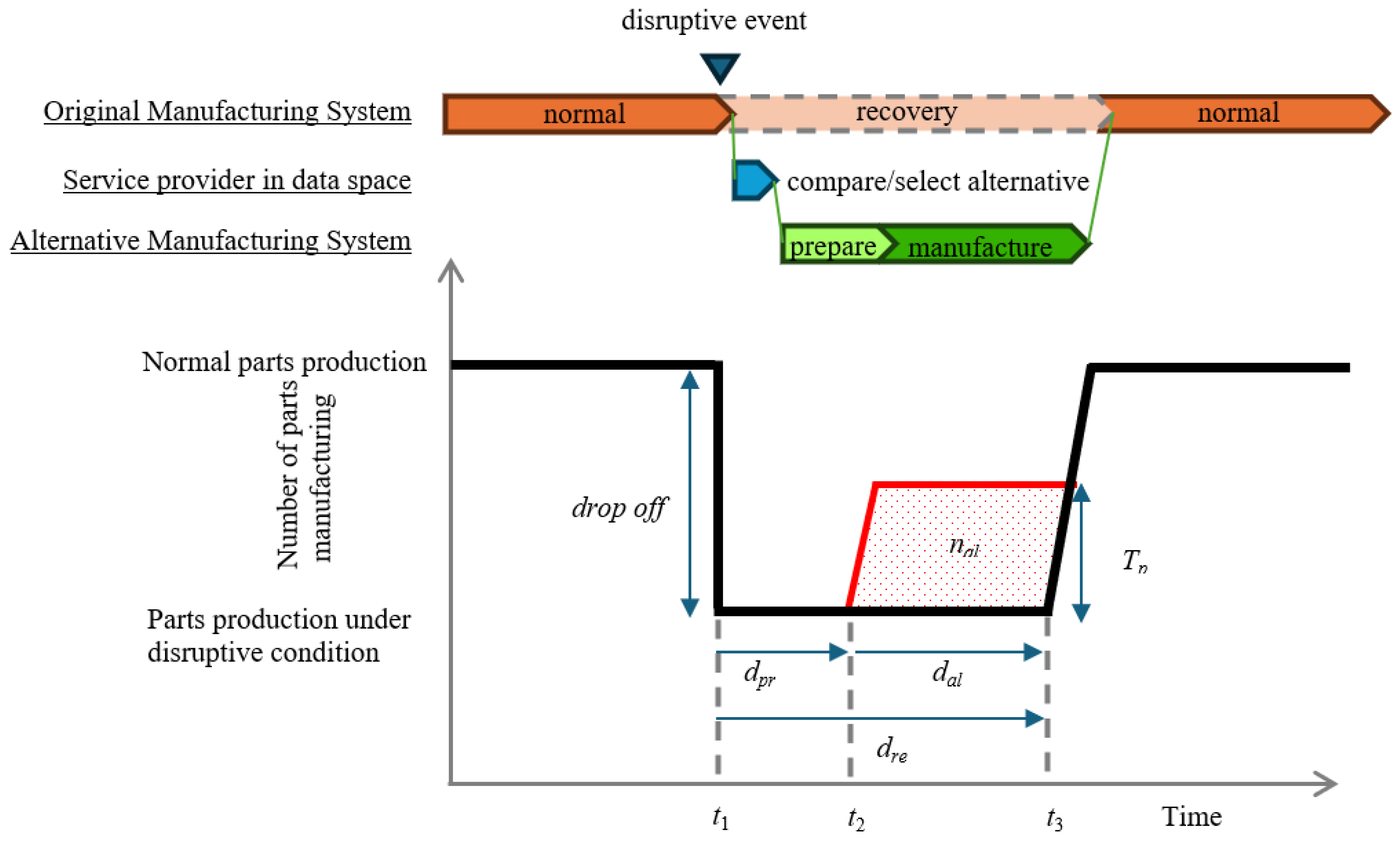
3.3. Disruption and Alternative Manufacturing Scenario
3.4. Evaluation of Alternative Manufacturing Performance
- nal: total manufacturing volume during alternative manufacturing [parts].
- Tp: daily performance of alternative manufacturing [parts/day].
- Cu: unit cost of parts during alternative manufacturing [USD/parts].
- Cin: initial additional cost of alternative manufacturing [USD].
- : BTF ratio, which is the ratio of total material weight and used material weight in parts [-].
- CM: cost of used material [USD/kg].
- Cop: operational cost for single parts [USD/parts].
3.5. Sensitivity Analysis
4. Results
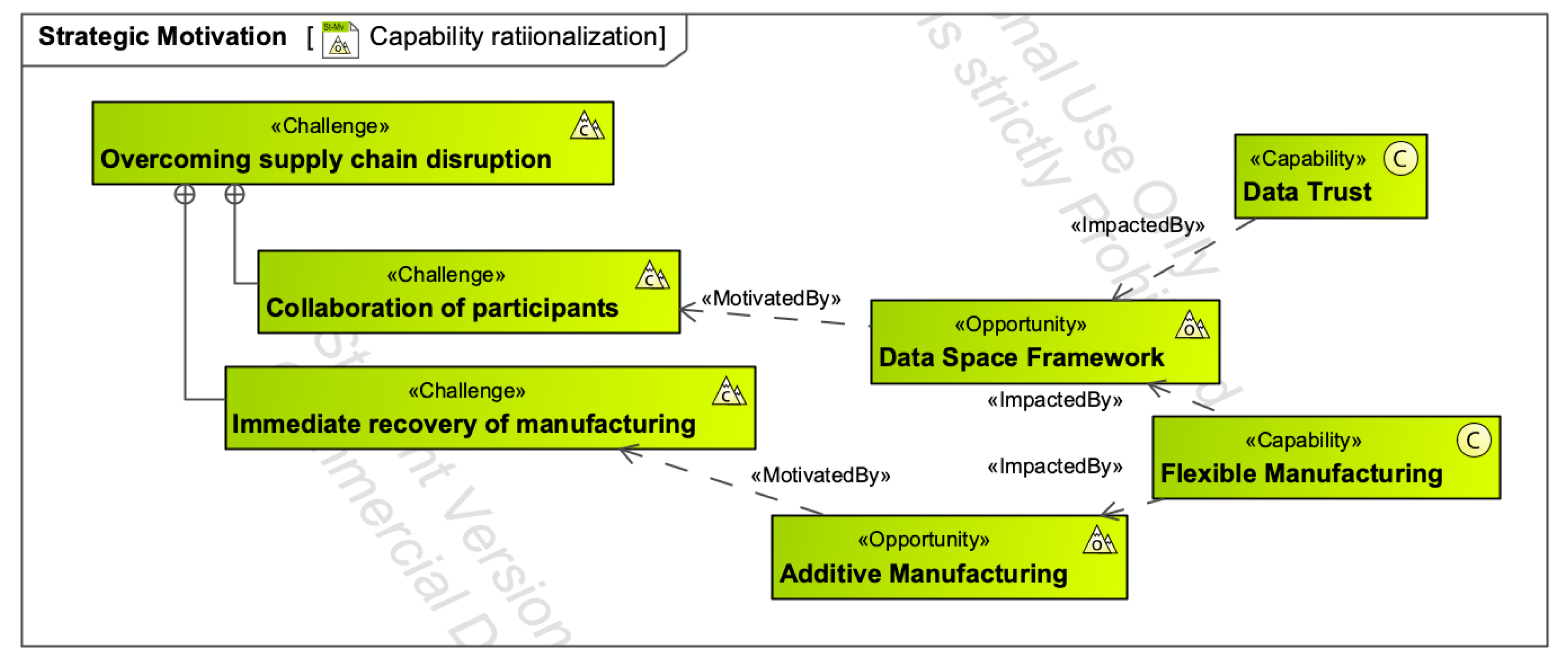
4.1. Conceptualization of Security and Resilience Strategy
4.1.1. Enterprise Goals
- A. Resilience
- B. Sustainability
- C. Human-Centric Nature
- D. Maximize Efficiency
4.1.2. Opportunities
4.1.3. Capability Identification of a Secure and Robust Manufacturing Supply Chain
4.2. Structural Overview of Supply Chain with Data Space
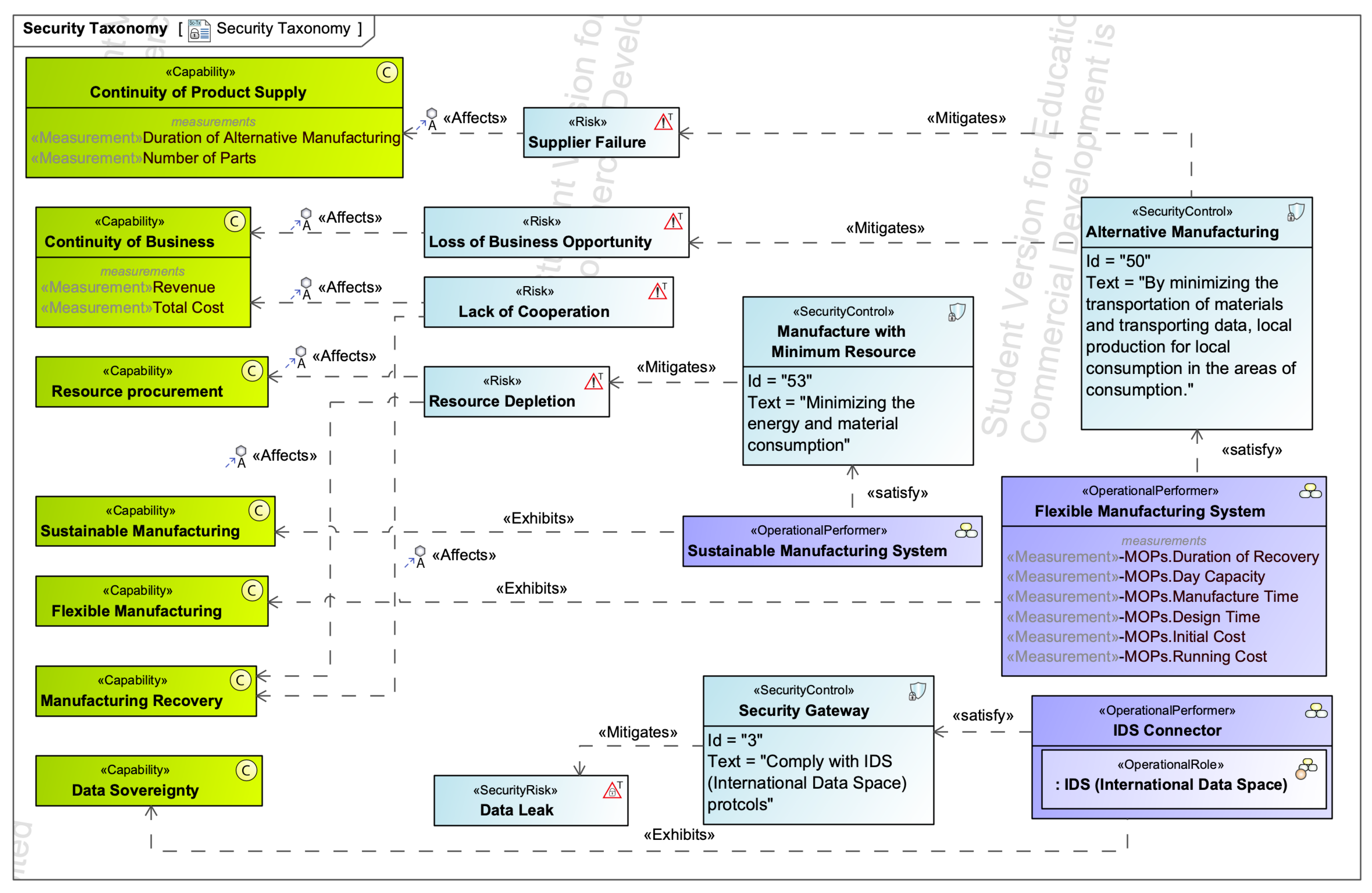
4.2.1. Investigation of Security in Manufacturing Supply Chain
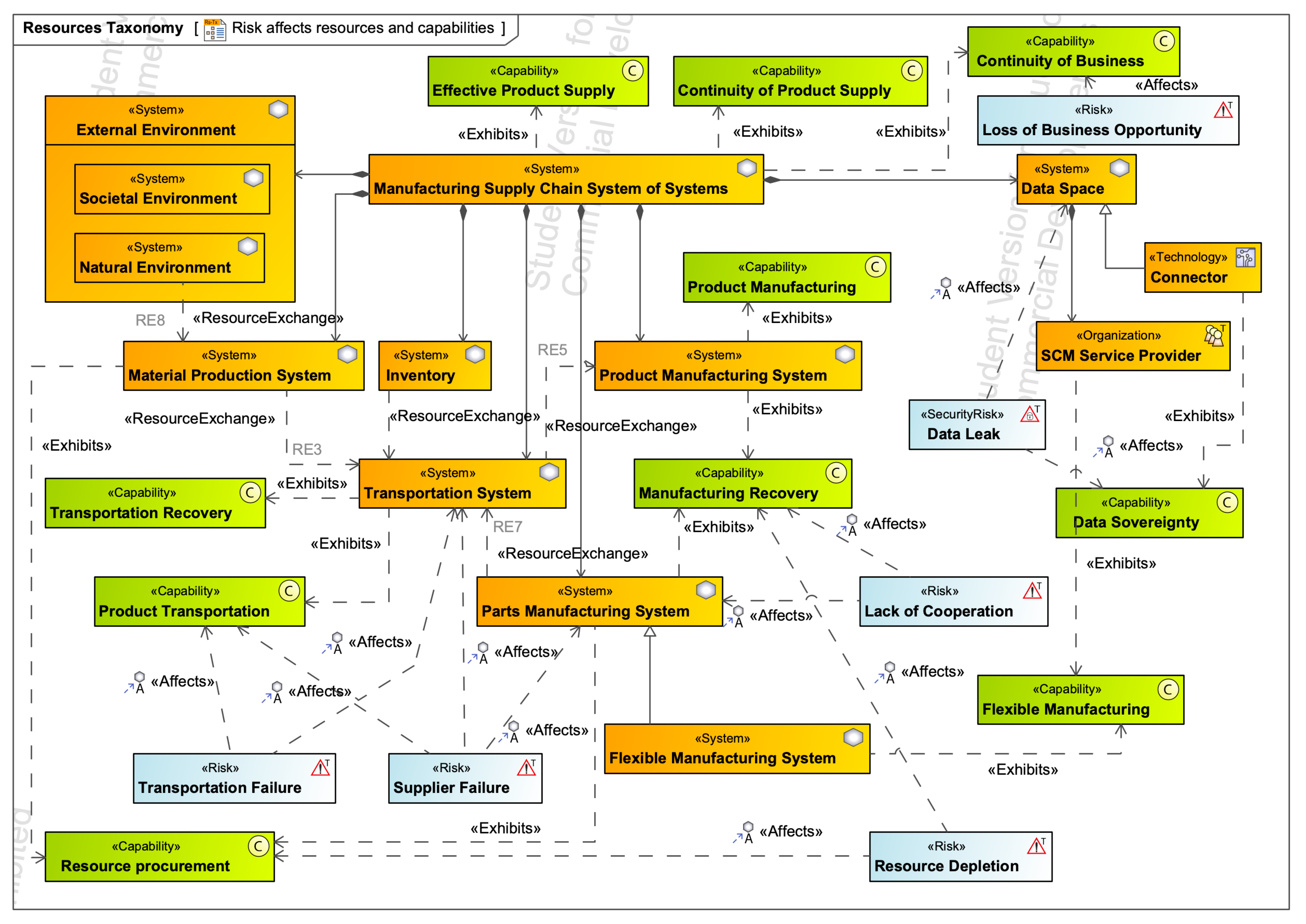
4.2.2. System of Systems of Supply Chain with Data Space and Risk Mapping
4.2.3. Measure of Effectiveness and Performance of Risk Mitigation
4.3. Parts Supply Disruption and Alternative Manufacturing
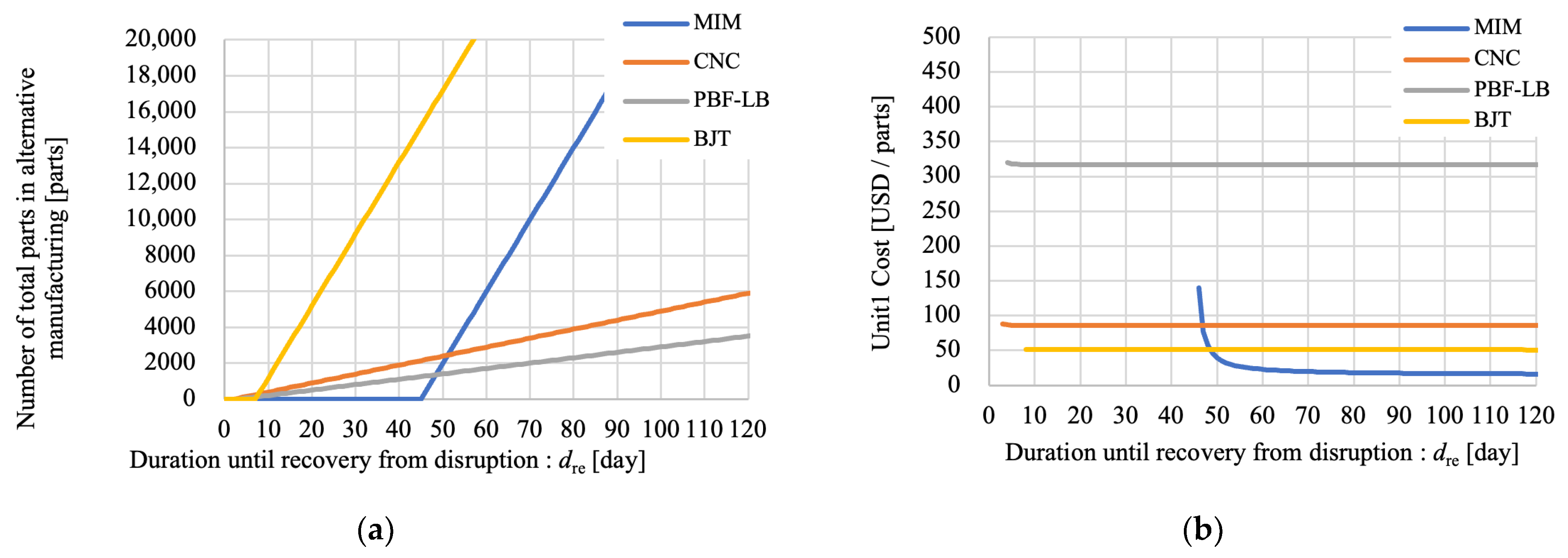
4.3.1. Evaluation Result of Alternative Manufacturing Performance
4.3.2. Cost and Productivity Analysis
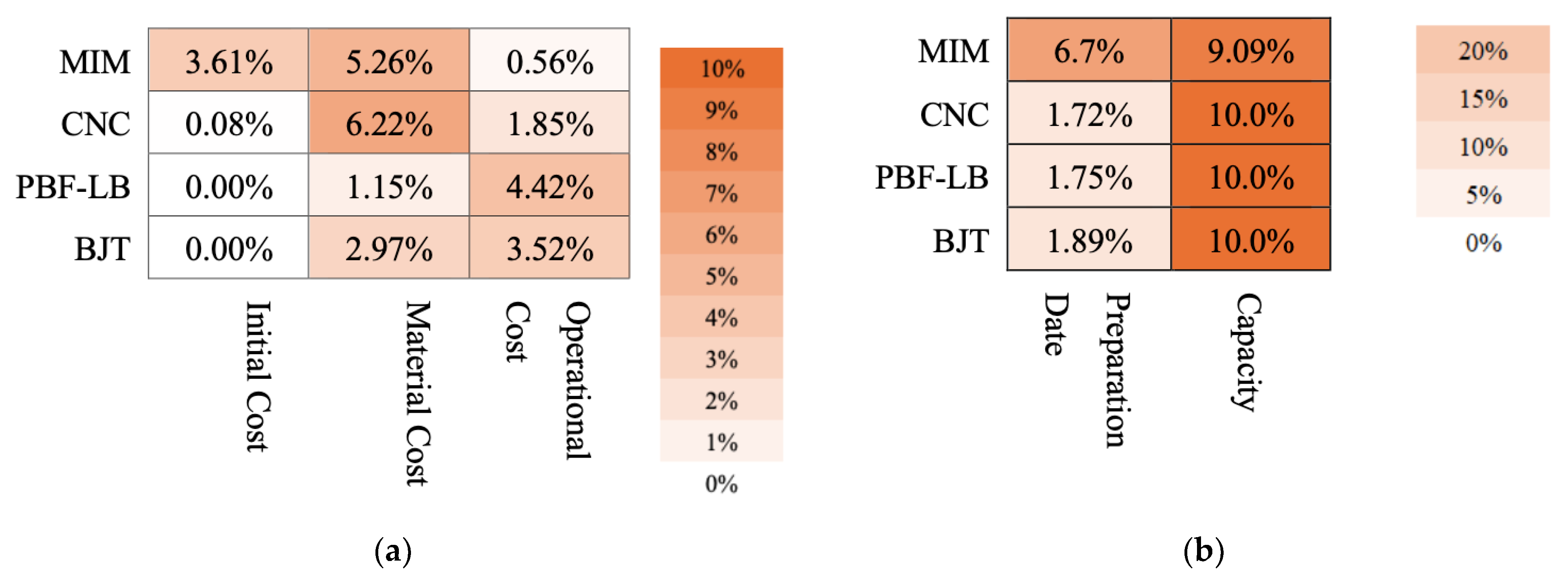
4.3.3. Sensitivity Analysis Results
5. Discussion
5.1. Architecture Definition and Elaboration
5.2. Evaluation of Alternative Manufacturing
5.3. Limitations
5.4. Next Steps and Recommendations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
DURC Statement
Conflicts of Interest
Appendix A. Predefined Words in UAF Models
| Diagram | Figure | Description |
|---|---|---|
| Strategic Motivation Diagram (St-Mv) | Figure 3 and Figure 4 | Assemble Strategic Drivers—for enterprise transformation that deal with national, department, community, joint, coalition, business, technology, or other kinds of considerations [37] (p. 24). Capture Enterprise Challenges and Opportunities—Identify challenges, opportunities, and concerns that pertain to enterprise transformation efforts. [37] (p. 24). |
| Security Taxonomy Diagram (Sc-Tx) | Figure 5 and Figure 7 | Establish security taxonomy to define the hierarchy of kinds of security and protection assets and asset owners that mitigate threats. [37] (p. 90). |
| Resource Taxonomy Diagram (Rs-Tx) | Figure 6 | A set of resource performers are described, including any that have been preliminarily identified. [37] (p. 65). |
| Terminology | Extension | Figure | Description |
|---|---|---|---|
| ActualEnterprisePhase | Instance specification | Figure 3 | An individual that describes the phase of an actual enterprise endeavor. [39] (p. 50). |
| EnterpriseVision | Class | Figure 3 | Describes the future state of the enterprise without regard to how it is to be achieved. [39] (p. 42). |
| EnterpriseGoal | Class | Figure 3 | A statement about a state or condition of the enterprise to be brought about or sustained through appropriate means. An Enterprise Goal amplifies an Enterprise Vision, i.e., it indicates what must be satisfied on a continuing basis to effectively attain the Enterprise Vision. [39] (p. 41). |
| EnterpriseObjective | Class | Figure 3 | A statement of an attainable, time-targeted, and measurable target that the enterprise seeks to meet in order to achieve its goals. [39] (pp. 41–42). |
| MotivatedBy | Dependency | Figure 3 and Figure 4 | A tuple denoting the reason or reasons one has for acting or behaving in a particular way. [39] (pp. 36–37). |
| ImpactedBy | Abstraction | Figure 4 | A dependency relationship denoting that a Capability is affected by an Opportunity. [39] (p. 35). |
| Enables | Dependency | Figure 3 | A dependency relationship denoting that an Opportunity provides the means for achieving an Enterprise Goal or objective. [39] (p. 35). |
| Challenge | Class | Figure 3 and Figure 4 | An existing or potential difficulty, circumstance, or obstacle that will require effort and determination from an enterprise to be overcome so they can achieving their goals. [39] (p. 33). |
| Opportunity | Class | Figure 3 and Figure 4 | An existing or potential favorable circumstance or combination of circumstances which can be advantageous for addressing enterprise Challenges. [39] (p. 38). |
| Driver | Class | Figure 3 | A factor which will have a significant impact on the activities and goals of an enterprise. [39] (p. 34). |
| Risk | Class | Figure 5 and Figure 6 | A type that represents a situation involving exposure to the danger of Affectable Elements (e.g., Assets, Processes, Capabilities, Opportunities, or Enterprise Goals) where the effects of such exposure can be characterized in terms of the likelihood of occurrence of a given threat and the potential adverse consequences of that threat’s occurrence. [39] (p. 186). |
| SecurityRisk | Class | Figure 5 and Figure 6 | The level of impact on enterprise operations, assets, or individuals resulting from the operation of an information system given the potential impact of a threat and the likelihood of that threat occurring. [NIST SP 800-65]. [39] (p. 141). |
| System | Class | Figure 6 | An integrated set of elements, subsystems, or assemblies that accomplish a defined objective. These elements include products (hardware, software, firmware), processes, people, information, techniques, facilities, services, and other support elements (INCOSE SE Handbook V4, 2015). [39] (p. 110). |
| Technology | Class | Figure 6 | A subtype of ResourceArtifact that indicates a technology domain, i.e., nuclear, mechanical, electronic, mobile telephony, etc. [39] (p. 127). |
| Capability | Class | Figure 4, Figure 6 and Figure 7 | An enterprise’s ability to achieve a desired effect realized through a combination of ways and means (e.g., Capability Configurations) along with specified measures. [39] (p. 40). |
| OperationalPerformer | Class | Figure 7 | A logical entity that is capable of performing operational activities which produce, consume, and process resources. [39] (p. 68). |
| SecurityControl | Class | Figure 7 | The management, operations, and technical control (i.e., safeguard or countermeasure) required to protect the confidentiality, integrity, and availability of the system and its information [NIST SP 800-53]. [39] (p. 133). |
| OperationalRole | Property | Figure 7 | The usage of an Operational Performer or Operational Architecture in the context of another Operational Performer or Operational Architecture. Creates a whole-part relationship. [39] (p. 69). |
| Affects | Dependency | Figure 7 | A dependency that asserts that a risk is applicable to an asset. [39] (p. 173). |
| Mitigates | Dependency | Figure 7 | A tuple relating security control to a risk. Mitigation is established to manage the risk and could be represented as an overall strategy or through techniques (mitigation configurations) and procedures (security processes). [39] (p. 183). |
| Exhibits | Abstraction | Figure 7 | A tuple that exists between a Capable Element and a Capability that it meets under specific environmental conditions. [39] (p. 61). |
| Satisfy | - | Figure 7 | A stereotype of the SysML relationship in the requirement diagram [60]. |
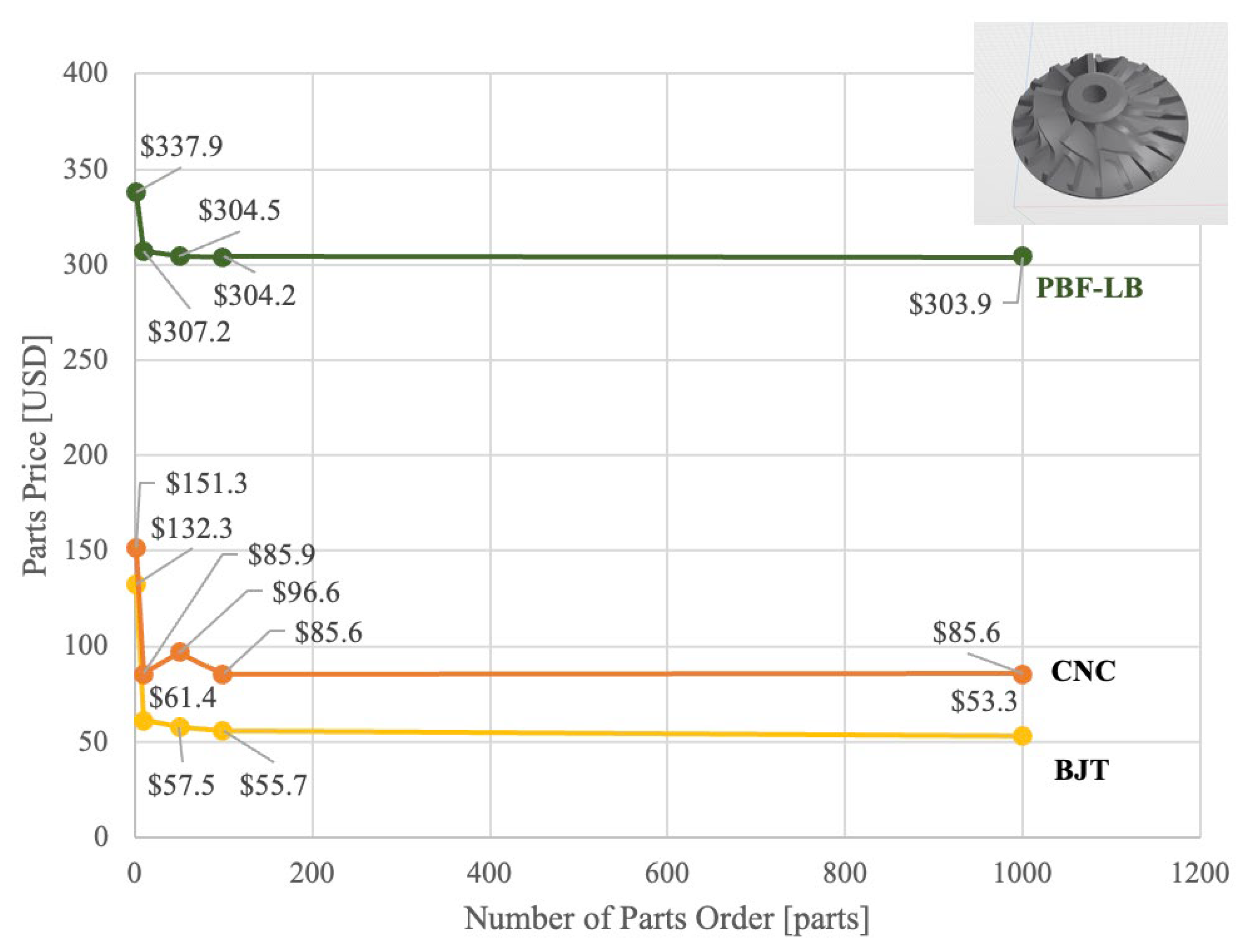
Appendix B. Estimation Result of Online Parts Manufacturing
References
- Rahman, T.; Paul, S.K.; Shukla, N.; Agarwal, R.; Taghikhah, F. Supply chain resilience initiatives and strategies: A systematic review. Comput. Ind. Eng. 2022, 170, 108317. [Google Scholar] [CrossRef]
- El Baz, J.; Ruel, S. Can supply chain risk management practices mitigate the disruption impacts on supply chains’ resilience and robustness? Evidence from an empirical survey in a COVID-19 outbreak era. Int. J. Prod. Econ. 2021, 233, 107972. [Google Scholar] [CrossRef]
- Camarinha-Matos, L.M.; Rocha, A.D.; Graça, P. Collaborative approaches in sustainable and resilient manufacturing. J. Intell. Manuf. 2024, 35, 499–519. [Google Scholar] [CrossRef]
- Salkin, C.; Oner, M.; Ustundag, A.; Cevikcan, E. A Conceptual Framework for Industrie 4.0. In Managing the Digital Transformation; Springer Series in Advanced Manufacturing; Springer International Publishing: Cham, Switzerland, 2018; pp. 3–23. [Google Scholar]
- Federal Ministry for Economic Affairs and Energy, 2030 Vision for Industrie 4.0. 2019. Available online: https://www.plattform-i40.de/IP/Redaktion/EN/Downloads/Publikation/Vision-2030-for-Industrie-4.0.html (accessed on 14 February 2025).
- Otto, B. GAIA-X and IDS, Ver. 1; International Data Spaces Association: Berlin, Germany, 2021. [CrossRef]
- Directorate General for Research and Innovation. Industry 5.0: A Transformative Vision for Europe: Governing Systemic Transformations Towards a Sustainable Industry; European Commission, Eurostat: Luxembourg, 2021. [Google Scholar]
- Directorate General for Research and Innovation. Industry 5.0: Towards a Sustainable, Human Centric and Resilient European Industry; European Commission, Eurostat: Luxembourg, 2021. [Google Scholar]
- Wofuru-Nyenke, O.K.; Briggs, T.A.; Aikhuele, D.O. Advancements in sustainable manufacturing supply chain modelling: A review. Process Integr. Optim. Sustain. 2023, 7, 3–27. [Google Scholar] [CrossRef]
- Özbayrak, M.; Papadopoulou, T.C.; Akgun, M. Systems dynamics modeling of a manufacturing supply chain system. Simul. Model. Pract. Theory 2007, 15, 1338–1355. [Google Scholar] [CrossRef]
- Gaia-X Association. Gaia-X—Architecture Document 22.04 Release. 2022. Available online: https://gaia-x.eu/wp-content/uploads/2022/06/Gaia-x-Architecture-Document-22.04-Release.pdf (accessed on 14 February 2025).
- Catena-X Automotive Network e.V. Catena-X Operating Model Version 2.1 White Paper; Catena-X Automotive Network e.V.: Berlin, Germany 2023. Available online: https://cdn.prod.website-files.com/5f19a993f080600777bbd184/65f86cfa9b30f326f4d51446_CX_Operating_Modelv2.1_final.pdf (accessed on 14 February 2025).
- INCOSE. Systems Engineering Handbook: A Guide for System Life Cycle Process and Activities, 5th ed.; Wiley: Hoboken, NJ, USA, 2023. [Google Scholar]
- Ross, R.; Winstead, M.; McEvilley, M. Engineering Trustworthy Secure Systems; (No. NIST SP 800-160v1r1); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2022. [Google Scholar]
- Ross, R.; Pillitteri, V.; Graubart, R.; Bodeau, D.; McQuaid, R. Developing Cyber-Resilient Systems: A Systems Security Engineering Approach; (No. NIST SP 800-160v2r1); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021. [Google Scholar]
- ISO/IEC/IEEE 15288; Systems and Software Engineering—System Life Cycle Processes. ISO: Geneva, Switzerland, 2023.
- Boyens, J.M. Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations; (No. NIST SP 800-161r1-upd1); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024.
- Nemeth, C.P.; Hollnagel, E. Resilience Engineering in Practice Volume 2: Becoming Resilient; Ashgate CRC Press: Boca Raton, FL, USA, 2014. [Google Scholar]
- Seidel, A.; Wenzel, K.; Hänel, A.; Teicher, U.; Weiß, A.; Schäfer, U.; Ihlenfeldt, S.; Eisenmann, H.; Ernst, H. Towards A seamless data cycle for space components: Considerations from the growing European future digital ecosystem Gaia-X. CEAS Space J. 2023, 16, 351–365. [Google Scholar] [CrossRef]
- Forte, S.; Gast, F.; Dickopf, T.; Sturmer, C.; Weber, M. Gaia-X based Data Ecosystem Offerings in the Context of Data Management Systems. In Proceedings of the IEEE 29th International Conference on Emerging Technologies and Factory Automation (ETFA), Padova, Italy, 10–13 September 2024; pp. 1–6. [Google Scholar]
- Li, Z.; Faheem, F.; Husung, S. Collaborative model-based systems engineering using data spaces and SysML v2. Systems 2024, 12, 18. [Google Scholar] [CrossRef]
- Bonfiglio, F. Vision & Strategy Gaia-X. 2021. Available online: https://gaia-x.eu/wp-content/uploads/2021/12/Vision-Strategy.pdf (accessed on 16 February 2025).
- DuHadway, S.; Carnovale; Hazen, B. Understanding risk management for intentional supply chain disruptions: Risk detection, risk mitigation, and risk recovery. Ann. Oper. Res. 2019, 283, 179–198. [Google Scholar] [CrossRef]
- Trappey, A.J.C.; Hareesh Govindarajan, U.; Chuang, A.C.; Sun, J.J. A review of essential standards and patent landscapes for the Internet of Things: A key enabler for Industry 4.0. Adv. Eng. Inform. 2017, 33, 208–229. [Google Scholar] [CrossRef]
- Menanno, M.; Savino, M.M.; Accorsi, R. Digitalization of Fresh Chestnut Fruit Supply Chain through RFID: Evidence, Benefits and Managerial Implications. Appl. Sci. 2023, 13, 5086. [Google Scholar] [CrossRef]
- Pohlmeyer, F.; Möbitz, C.; Gries, T. A Sovereign and Interoperable Data Ecosystem for an Eco-Efficient Nonwovens Industry. Sustainability 2024, 16, 10735. [Google Scholar] [CrossRef]
- Mitra, A.; Seetharaman, A.; Maddulety, K. A Structural Equation Model Study for Adoption of Internet of Things for the Growth of Manufacturing Industries in Australia. J. Compr. Bus. Adm. Res. 2024, 1, 93–104. [Google Scholar] [CrossRef]
- Hause, M.; Brooks, M.; Kennedy, R. Securing your eggs in multiple baskets—Assuring a resilient and secure supply chain. INCOSE Int. Symp. 2024, 34, 1748–1770. [Google Scholar] [CrossRef]
- Hosseini, S.; Ivanov, D.; Blackhurst, J. Conceptualization and Measurement of Supply Chain Resilience in an Open-System Context. IEEE Trans. Eng. Manag. 2022, 69, 3111–3126. [Google Scholar]
- Alexopoulos, K.; Anagiannis, I.; Nikolakis, N.; Chryssolouris, G. A quantitative approach to resilience in manufacturing systems. Int. J. Prod. Res. 2022, 60, 7178–7193. [Google Scholar] [CrossRef]
- Bakopoulos, E.; Sipsas, K.; Nikolakis, N.; Alexopoulos, K. A Digital Twin and Data Spaces framework towards Resilient Manufacturing Value Chains. IFAC-Pap. 2024, 58, 163–168. [Google Scholar] [CrossRef]
- ISO/IEC/IEEE 42020; Software, Systems and Enterprise–Architecture Processes. ISO: Geneva, Switzerland, 2019.
- ISO/IEC/IEEE 21839; Systems and Software Engineering—System of Systems (SoS) Considerations in Life Cycle Stages of a System. ISO: Geneva, Switzerland, 2019.
- Wand, Y.; Monarchi, D.; Parsons, J.; Woo, C. Theoretical foundations for conceptual modelling in information systems development. Decis. Support Syst. 1995, 15, 285–304. [Google Scholar] [CrossRef]
- Thalheim, B. The Theory of Conceptual Models, the Theory of Conceptual Modelling and Foundations of Conceptual Modelling. In Handbook of Conceptual Modeling; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Hause, M.; Kihlstrom, L. Tilting at windmills: Drivers, risk, opportunity, resilience and the 2021 Texas electricity grid failure. In Proceedings of the 32nd INCOSE International Symposium, Detroit, MI, USA, 25–30 June 2022; INCOSE: San Diego, CA, USA, 2022; Volume 32, pp. 545–564. [Google Scholar] [CrossRef]
- Enterprise Architecture Guide for UAF-Object Management Group Unified Architecture Framework—Appendix C Version 1.2; The Objective Management Group: Milford, MA, USA, 2022.
- Martin, J.J.; Brookshier, D. Linking UAF and SysML Models: Achieving Alignment between Enterprise and System Architectures. In Proceedings of the 33rd Annual INCOSE International Symposium, Honolulu, HI, USA, 15–20 July 2023; INCOSE: San Diego, CA, USA, 2023; 33, pp. 1132–1155. [Google Scholar] [CrossRef]
- Unified Architecture Framework Modeling Language (UAFML) Version 1.2; Object Management Group Unified Architecture Framework (OMG UAF): Milford, MA, USA, 2022.
- APICS Operations Management Body of Knowledge Framework, 3rd ed.; APICS The Association for Operations Management: Parramatta, NSW, Australia, 2011.
- Alghamdi, A.; Torkjazi, M.; Davila-Andino, A.J.; Zaidi, A.K. Employing UAF Inter-Domain Traceability for Performance and Effectiveness Evaluation. In Proceedings of the 2023 IEEE International Systems Conference, Vancouver, BC, Canada, 9–11 February 2023; IEEE: Los Alamitos, CA, USA, 2023; pp. 1–8. [Google Scholar]
- Rupp, M.; Buck, M.; Klink, R.; Merke, M.; Harrison, D.K. Additive manufacturing of steel for digital spare parts—A perspective on carbon emissions for decentral production. Clean. Environ. Syst. 2022, 4, 100069. [Google Scholar] [CrossRef]
- E-Metals (SUS316L Powder). Available online: https://www.e-metals.net/product/800174/ (accessed on 21 June 2025).
- E-Metals (SLS316L Rod). Available online: https://www.e-metals.net/product/200828/ (accessed on 21 June 2025).
- Net3d. Available online: https://met3dp.com/ja/316l-stainless-steel-powder-20240108/ (accessed on 21 June 2025).
- Commission. Regulation (EU) No 2016/679 of the European Parliament and of the Council-of 27 April 2016-on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of such Data, and Repealing Directive 95/46/EC (General Data Protection Regulation); Official Journal of the European Union, Eurostat: Luxembourg, 2016. [Google Scholar]
- Eyers, D.R.; Potter, A.T.; Gosling, J.; Naim, M.M. The flexibility of industrial additive manufacturing systems. Int. J. Oper. Prod. Manag. 2018, 38, 2313–2343. [Google Scholar] [CrossRef]
- Jimo, A.; Braziotis, C.; Rogers, H.; Pawar, K. Traditional vs additive manufacturing supply chain configurations: A comparative case study. Procedia Manuf. 2019, 39, 765–774. [Google Scholar] [CrossRef]
- Groover, M.P. Fundamentals of Modern Manufacturing, 6th ed.; Wiley: Hoboken, NJ, USA, 2019. [Google Scholar]
- Nabertherm. Metal Injection Molding (MIM) Furnaces for Debinding and Sintering. Available online: https://nabertherm.com/sites/default/files/2023-12/K4_4_Englisch.pdf (accessed on 21 June 2025).
- Asami, K.; Herzog, D.; Deutschmann, T.; Röver, T.; Kelbassa, I.; Emmelmann, C. Methodology for Cost Estimation Using Characteristic Factors in Additive Manufacturing. J. Jpn. Soc. Powder Powder Metall. 2025, 72, S75–S82. [Google Scholar] [CrossRef]
- Impeller Parts Design by Bijibijmak is Licensed Under the Creative Commons-Attribution-Non-Commercial License. Available online: https://thinverse.com (accessed on 21 June 2025).
- Craft Cloud. Available online: https://craftcloud3d.com/ (accessed on 21 June 2025).
- Hällgren, S.; Pejryd, L.; Ekengren, J. Additive Manufacturing and High Speed Machining-cost Comparison of short Lead Time Manufacturing Methods. Procedia CIRP 2016, 50, 384–389. [Google Scholar] [CrossRef]
- E-Metals (Aluminum Rod). Available online: https://www.e-metals.net/product/201461/ (accessed on 30 July 2025).
- E-Metals (Aluminum Powder). Available online: https://www.e-metals.net/ (accessed on 30 July 2025).
- ISO/IEC/IEEE 21841; Systems and Software Engineering–Taxonomy of Systems of Systems. ISO: Geneva, Switzerland, 2019.
- Nyamekye, P.; Piili, H.; Leino, M.; Salminen, A. Preliminary investigation on life cycle inventory of powder bed fusion of stainless steel. Phys. Procedia 2017, 89, 108–121. [Google Scholar] [CrossRef]
- Ziaee, M.; Crane, N.B. Binder jetting: A review of process, materials, and methods. Addit. Manuf. 2019, 28, 781–801. [Google Scholar] [CrossRef]
- Freudenthal, S.; Moore, A.; Steiner, R. A Practical Guide to SysML The System Modeling Language, 3rd ed.; Elsevier: North Andover, MA, USA, 2015; p. 314. [Google Scholar]

| Author | Field and Method | Key Findings | Limitations |
|---|---|---|---|
| Menanno (2023) [25] | VCOR and PMS for RFIDs in the SC. | RFIDs in the agri-food industry are influenced by specific organizational procedures. | KPI analysis was limited to a restricted material flow. It did not include economic analysis. |
| Pohlmeyer (2024) [26] | A data ecosystem with a Digital Product Passport for traceability in the SC. | The findings support a sovereign data ecosystem enhancing eco-efficiency and sustainability. | It lacks real-world validation and implementation. Data sharing is hindered by confidentiality concerns and errors. |
| Mitra (2024) [27] | Structural Equation Mode for IoT in the SC. | Quantitative data from over 500 respondents indicate positive impacts and reveal the transformative potential of IoT in enhancing operational efficiency. | Geographical limitations affect the generalizability of the findings. Potential bias in the literature review may influence the results. |
| Hause (2024) [28] | Enterprise architecture modeling of the SC with UAF. | It provides strategic and operational views to define procedures and elements. Robust risk management is investigated. | The focus is on the established supply chain network. Digital technology is limited. |
| Hosseini (2022) [29] | Novel measurement method using Bayesian networks for the SC. | The metric can serve as a KPI for analyzing disruption impacts on the SC. | The metric is applicable only to directed graphs without cycles, limiting its broader application. The measure does not consider recovery processes, which are crucial for resident systems. |
| Alexopoulos (2022) [30] | Resilience qualification of the plastic parts SC by using POC (Penalty of Change). | 3D printing (AM) and injection molding are compared. | The POC metrics can be used in decision-making for the initial investment. |
| Bakopoulos (2024) [31] | A value chain planning approach with POC metrics for a SC using the data space. | A framework for resilient manufacturing value chains is proposed, leveraging data space technology. | Decision-making is often delayed due to reliance on industrial experts. The current architecture is inflexible, hindering structured integration of planning solutions. |
| Manufacturing Method | Description |
|---|---|
| MIM | Metal Injection Molding (MIM) is a manufacturing process that combines the design flexibility of injection molding with the strength and integrity of metal. It is ideal for producing small, complex, high-volume metal parts with tight tolerances. Feedstock made by mixing metal powder with binder is injected into a mold to produce a molded body (green body). The green body undergoes a debinding and sintering process to become a metal part. It is necessary to prepare the mold. |
| CNC | Computational Numerical Control Machining is a manufacturing process in which pre-programmed computer software controls the movement of tools and machinery. It is widely used to produce precise and complex parts from various materials such as metals, plastics, and composites. CNC can be utilized for both prototyping and mass production. |
| PBF-LB | Laser Beam Powder Bed Fusion is an Additive Manufacturing process used to produce metal parts directly from a digital model. PBF-LB is ideal for complex, low-volume parts and rapid prototyping, especially when traditional tooling is impractical. |
| BJT | Binder Jetting Technology (BJT) is an Additive Manufacturing process in which a liquid binding agent is selectively deposited onto a bed of metal powder to form parts layer by layer. After curing, the green body undergoes a debinding and sintering process similar to MIM. |
| MIM | CNC | PBF-LB | BJT | |
|---|---|---|---|---|
| Additional Cost [USD] | 50,000 1 | 100 | 100 | 100 |
| Operational Cost [USD] | 1.3 | 16 | 140 | 18 |
| Material Cost [USD/kg] 3 | 49.5 4 | 22 | 106 | 62 |
| BTF ratio () | 1.0 | 4.47 2 | 1.41 2 | 1.0 |
| Preparation [day] | 45 1 | 2 | 3 | 7 |
| Capacity [parts/day] | 400 | 50 | 30 | 400 |
| Parts Property | Unit Cost [USD/parts] 1 | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Type | Material | Weight [kg] | MIM | CNC | PBF-LB | BJT | MIM | CNC | PBF-LB | BJT | ||
| Impeller | SUS316L | 0.25 | 1 | 4.47 | 1.41 | 1 | 23.1 | 56.1 | 316.7 | 51.2 | ||
| Holder | A7075-T6 | 0.63 | 1 | 5.9 | 1.41 | 1 | 13.4 | 55.6 | 285.0 | 38.0 | ||
| Clamp | A7075-T6 | 0.022 | 1 | 8.6 | 1.41 | 1 | 11.8 | 66.4 | 281.7 | 36.7 | ||
| Guard | A7075-T6 | 0.0025 | 1 | 7.9 | 1.41 | 1 | 11.0 | 63.6 | 280.3 | 36.1 | ||
| Housing | A7075-T6 | 0.063 | 1 | 11.7 | 1.41 | 1 | 13.4 | 78.8 | 285.0 | 38.1 | ||
| Total Number of Parts [parts] | ||||||||||||
| 6000 | 2900 | 1710 | 21,200 | |||||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Norikane, Y.; Nishimura, H. Security and Resilience of a Data Space Based Manufacturing Supply Chain. Systems 2025, 13, 676. https://doi.org/10.3390/systems13080676
Norikane Y, Nishimura H. Security and Resilience of a Data Space Based Manufacturing Supply Chain. Systems. 2025; 13(8):676. https://doi.org/10.3390/systems13080676
Chicago/Turabian StyleNorikane, Yoshihiro, and Hidekazu Nishimura. 2025. "Security and Resilience of a Data Space Based Manufacturing Supply Chain" Systems 13, no. 8: 676. https://doi.org/10.3390/systems13080676
APA StyleNorikane, Y., & Nishimura, H. (2025). Security and Resilience of a Data Space Based Manufacturing Supply Chain. Systems, 13(8), 676. https://doi.org/10.3390/systems13080676








