Enhancing Smart IoT Malware Detection: A GhostNet-based Hybrid Approach
Abstract
:1. Introduction
- We investigate eight big datasets encompassing malware and benign instances, essential insights to train our model effectively: Gagfyt, Hide and Seek, Kenjiro, Linux Hajime, Mirai, Muhstik, Okiru, and Tori.
- By adeptly utilizing feature engineering techniques like precise feature scaling, extensive one-hot encoding, and insightful feature importance analysis employing MDI and XGBoost, we empower our model to outperform in identifying intricate malware behaviors.
- We proposed a pioneering deep learning ensemble named GNGRUE, designed to effectively process and classify large datasets, thereby enhancing the efficiency of our approach.
- The proposed approach, GNGRUE, enhances classification performance accuracy by 15%, accompanied by a 10% reduction in time complexity compared to existing approaches.
- By tuning the parameters of GNGRUE through JA, our model can easily handle large amounts of data with the same accuracy and execution time.
- Real-world Applicability: By successfully identifying and countering eight distinct malware strains, our research provides a valuable contribution to securing IoT systems. This impact resonates particularly in sectors like smart cities and advanced manufacturing.
2. Literature Review
3. Motivation and Problem Statement
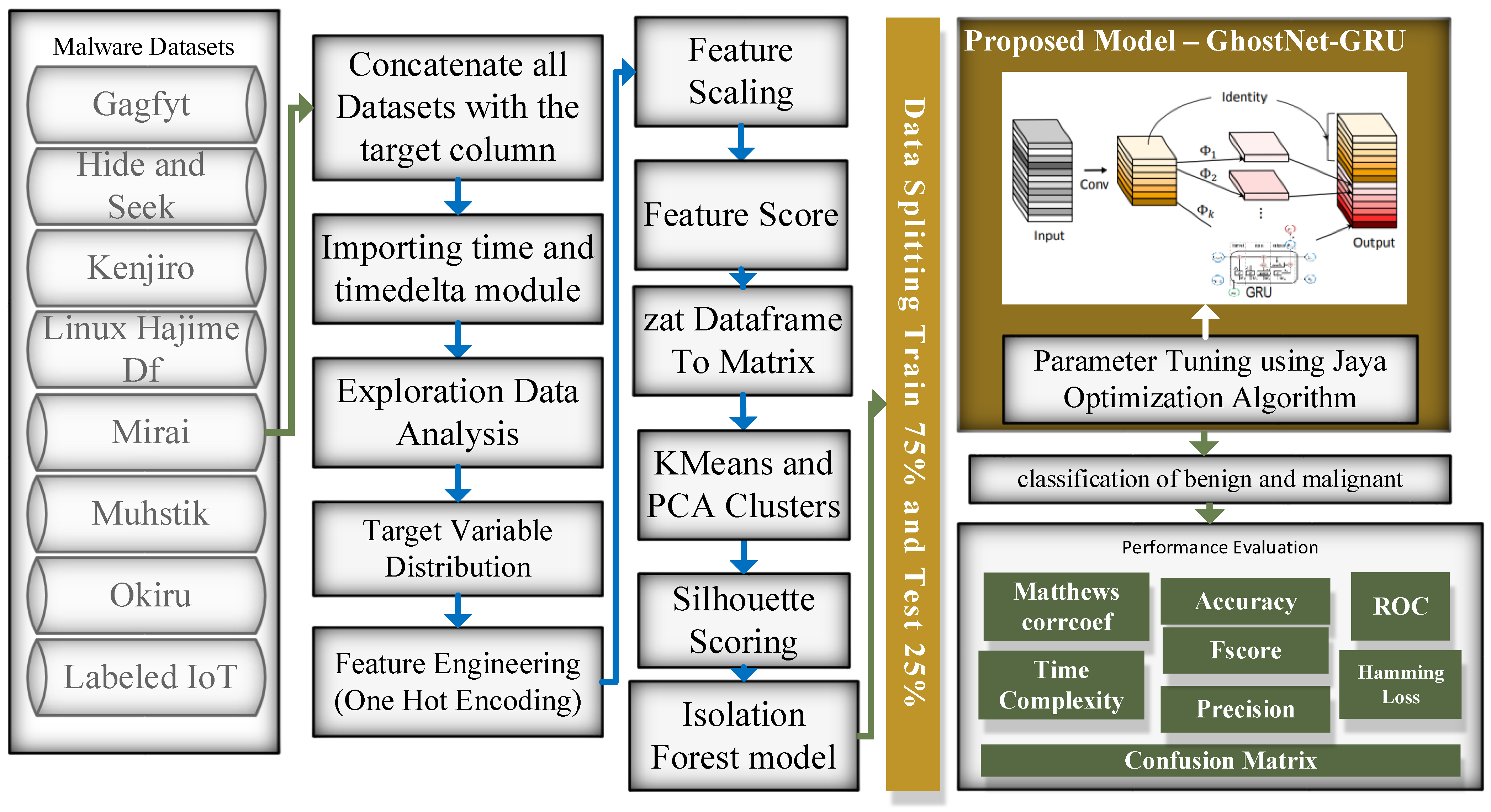
4. Proposed System Model
4.1. Dataset
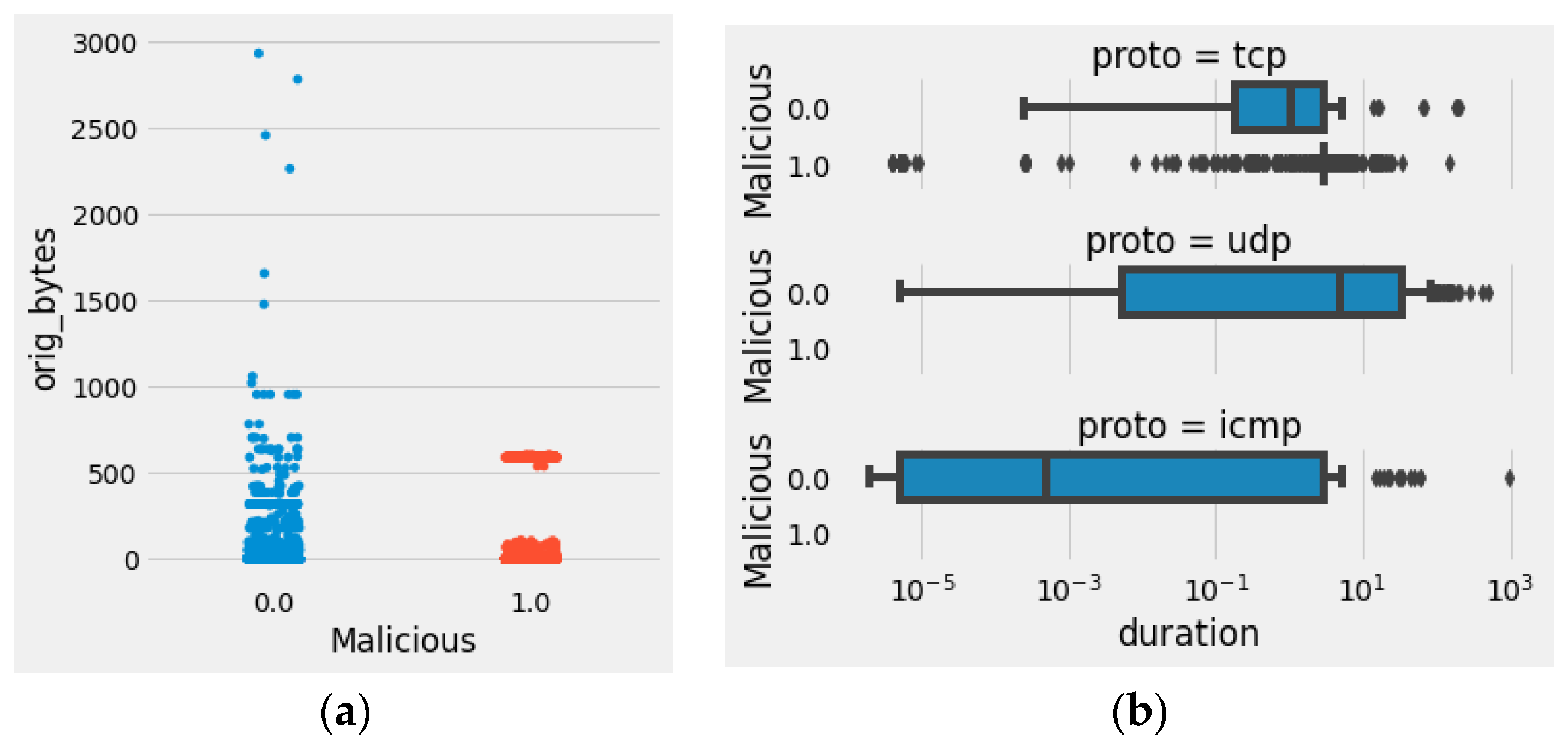
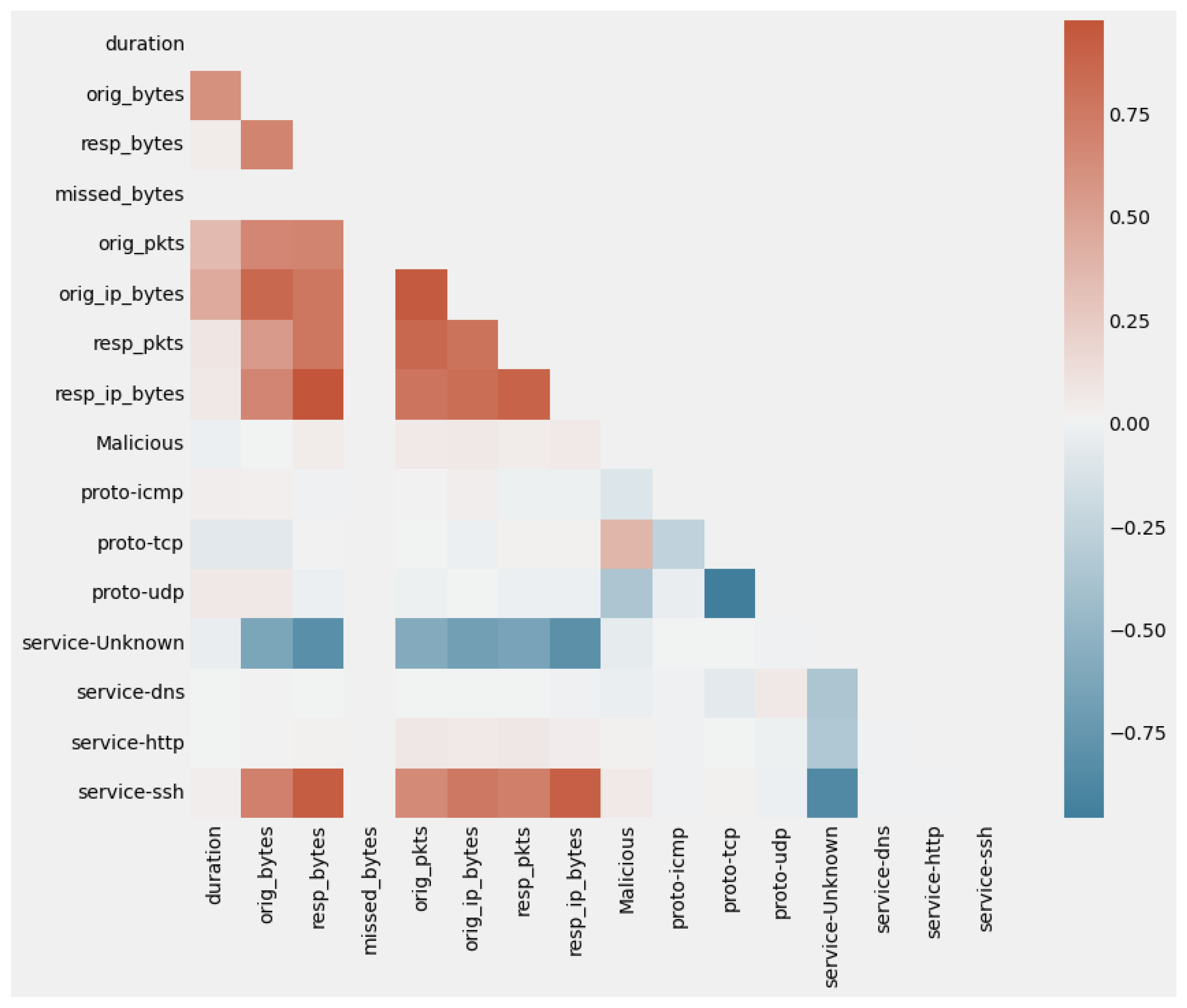
4.2. PreProcessing
- Train an XGBoost model using the training data.
- Access the feature_importance attribute of the trained model to obtain an array of feature importance scores.
- Rank the feature significance ratings in descending order to identify the most critical characteristics.
4.3. Ensemble Classification Model
4.3.1. GNGRUE
4.3.2. Jaya Algorithm
5. Experimental Results
6. Discussion on Adaptability to New Types of Malware
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mishra, N.; Pandya, S. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Gaurav, A.; Gupta, B.B.; Panigrahi, P.K. A Comprehensive Survey on Machine Learning Approaches for Malware Detection in IoT-Based Enterprise Information System. Enterp. Inf. Syst. 2023, 17, 2023764. [Google Scholar] [CrossRef]
- Macas, M.; Wu, C.; Fuertes, W. A Survey on Deep Learning for Cybersecurity: Progress, Challenges, and Opportunities. Comput. Netw. 2022, 212, 109032. [Google Scholar] [CrossRef]
- Zhou, J.X.; Shen, G.Q.; Yoon, S.H.; Jin, X. Customization of On-Site Assembly Services by Integrating the Internet of Things and BIM Technologies in Modular Integrated Construction. Autom. Constr. 2021, 126, 103663. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V. A Novel Deep Learning-Based Approach for Malware Detection. Eng. Appl. Artif. Intell. 2023, 122, 106030. [Google Scholar] [CrossRef]
- Palša, J.; Ádám, N.; Hurtuk, J.; Chovancová, E.; Madoš, B.; Chovanec, M.; Kocan, S. MLMD—A Malware-Detecting Antivirus Tool Based on the XGBoost Machine Learning Algorithm. Appl. Sci. 2022, 12, 6672. [Google Scholar] [CrossRef]
- Maniriho, P.; Mahmood, A.N.; Chowdhury, M.J.M. A Study on Malicious Software Behaviour Analysis and Detection Techniques: Taxonomy, Current Trends and Challenges. Future Gener. Comput. Syst. 2022, 130, 1–18. [Google Scholar] [CrossRef]
- Udousoro, I.C. Machine Learning: A Review. Semicond. Sci. Inf. Devices 2020, 2, 5–14. [Google Scholar]
- Shaukat, K.; Luo, S.; Varadharajan, V. A Novel Method for Improving the Robustness of Deep Learning-Based Malware Detectors against Adversarial Attacks. Eng. Appl. Artif. Intell. 2022, 116, 105461. [Google Scholar] [CrossRef]
- Aslan, Ö.A.; Samet, R. A Comprehensive Review on Malware Detection Approaches. IEEE Access 2020, 8, 6249–6271. [Google Scholar] [CrossRef]
- Mishra, A.; Almomani, A. Malware Detection Techniques: A Comprehensive Study. Insights Int. Interdiscip. J. 2023, 1, 1–5. [Google Scholar]
- Kwon, H.Y.; Kim, T.; Lee, M.K. Advanced Intrusion Detection Combining Signature-Based and Behavior-Based Detection Methods. Electronics 2022, 11, 867. [Google Scholar] [CrossRef]
- Singh, J.; Singh, J. A Survey on Machine Learning-Based Malware Detection in Executable Files. J. Syst. Archit. 2021, 112, 101861. [Google Scholar] [CrossRef]
- Tayyab, U.E.H.; Khan, F.B.; Durad, M.H.; Khan, A.; Lee, Y.S. A Survey of the Recent Trends in Deep Learning Based Malware Detection. J. Cybersecur. Priv. 2022, 2, 800–829. [Google Scholar] [CrossRef]
- Aboaoja, F.A.; Zainal, A.; Ghaleb, F.A.; Al-rimy, B.A.S.; Eisa, T.A.E.; Elnour, A.A.H. Malware Detection Issues, Challenges, and Future Directions: A Survey. Appl. Sci. 2022, 12, 8482. [Google Scholar] [CrossRef]
- Alomari, E.S.; Nuiaa, R.R.; Alyasseri, Z.A.A.; Mohammed, H.J.; Sani, N.S.; Esa, M.I.; Musawi, B.A. Malware Detection Using Deep Learning and Correlation-Based Feature Selection. Symmetry 2023, 15, 123. [Google Scholar] [CrossRef]
- Hemalatha, J.; Roseline, S.A.; Geetha, S.; Kadry, S.; Damaševičius, R. An Efficient DenseNet-Based Deep Learning Model for Malware Detection. Entropy 2021, 23, 344. [Google Scholar] [CrossRef]
- Ngo, Q.D.; Nguyen, H.T.; Le, V.H.; Nguyen, D.H. A Survey of IoT Malware and Detection Methods Based on Static Features. ICT Express 2020, 6, 280–286. [Google Scholar] [CrossRef]
- Khalid, A.; Badshah, G.; Ayub, N.; Shiraz, M.; Ghouse, M. Software Defect Prediction Analysis Using Machine Learning Techniques. Sustainability 2023, 15, 5517. [Google Scholar] [CrossRef]
- Ravi, V.; Alazab, M.; Selvaganapathy, S.; Chaganti, R. A Multi-View Attention-Based Deep Learning Framework for Malware Detection in Smart Healthcare Systems. Comput. Commun. 2022, 195, 73–81. [Google Scholar] [CrossRef]
- Bhat, P.; Behal, S.; Dutta, K. A System Call-Based Android Malware Detection Approach with Homogeneous & Heterogeneous Ensemble Machine Learning. Comput. Secur. 2023, 130, 103277. [Google Scholar]
- Dewanje, A.; Kumar, K.A. A New Malware Detection Model Using Emerging Machine Learning Algorithms. Int. J. Electron. Inf. Eng. 2021, 13, 24–32. [Google Scholar]
- Patil, S.; Varadarajan, V.; Walimbe, D.; Gulechha, S.; Shenoy, S.; Raina, A.; Kotecha, K. Improving the Robustness of AI-Based Malware Detection Using Adversarial Machine Learning. Algorithms 2021, 14, 297. [Google Scholar] [CrossRef]
- Taheri, R.; Ghahramani, M.; Javidan, R.; Shojafar, M.; Pooranian, Z.; Conti, M. Similarity-Based Android Malware Detection Using Hamming Distance of Static Binary Features. Future Gener. Comput. Syst. 2020, 105, 230–247. [Google Scholar] [CrossRef]
- Sayadi, H.; Patel, N.; Sasan, A.; Rafatirad, S.; Homayoun, H. Ensemble Learning for Effective Run-Time Hardware-Based Malware Detection: A Comprehensive Analysis and Classification. In Proceedings of the 55th Annual Design Automation Conference, San Francisco, CA, USA, 24–29 June 2018; pp. 1–6. [Google Scholar]
- Sihwail, R.; Omar, K.; Zainol Ariffin, K.A.; Al Afghani, S. Malware Detection Approach Based on Artifacts in Memory Image and Dynamic Analysis. Appl. Sci. 2019, 9, 3680. [Google Scholar] [CrossRef]
- Huang, X.; Ma, L.; Yang, W.; Zhong, Y. A Method for Windows Malware Detection Based on Deep Learning. J. Signal Process. Syst. 2021, 93, 265–273. [Google Scholar] [CrossRef]
- Atitallah, S.B.; Driss, M.; Almomani, I. A Novel Detection and Multi-Classification Approach for IoT-Malware Using Random Forest Voting of Fine-Tuning Convolutional Neural Networks. Sensors 2022, 22, 4302. [Google Scholar] [CrossRef]
- Malvacio, E.M.; Duarte, J.C. An assessment of the effectiveness of pretrained neural networks for malware detection. IEEE Latin America Transactions 2023, 21, 47–53. [Google Scholar] [CrossRef]
- Roseline, S.A.; Geetha, S.; Kadry, S.; Nam, Y. Intelligent Vision-Based Malware Detection and Classification Using Deep Random Forest Paradigm. IEEE Access 2020, 8, 206303–206324. [Google Scholar] [CrossRef]
- Andreopoulos, W.B. Malware Detection with Sequence-Based Machine Learning and Deep Learning. In Malware Analysis Using Artificial Intelligence and Deep Learning; Springer: Cham, Switzerland, 2021; pp. 53–70. [Google Scholar]
- Zhang, N.; Xue, J.; Ma, Y.; Zhang, R.; Liang, T.; Tan, Y.A. Hybrid Sequence-Based Android Malware Detection Using Natural Language Processing. Int. J. Intell. Syst. 2021, 36, 5770–5784. [Google Scholar] [CrossRef]
- Gržinić, T.; González, E.B. Methods for Automatic Malware Analysis and Classification: A Survey. Int. J. Inf. Comput. Secur. 2022, 17, 179–203. [Google Scholar] [CrossRef]
- Roh, Y.; Heo, G.; Whang, S.E. A Survey on Data Collection for Machine Learning: A Big Data-AI Integration Perspective. IEEE Trans. Knowl. Data Eng. 2019, 33, 1328–1347. [Google Scholar] [CrossRef]
- Demirezen, M.U. Image Based Malware Classification with Multimodal Deep Learning. Int. J. Inf. Secur. Sci. 2021, 10, 42–59. [Google Scholar]
- Manzil, H.H.R.; Naik, S.M. Detection approaches for android malware: Taxonomy and review analysis. Expert Syst. Appl. 2023, 2023, 122255. [Google Scholar]
- Manzano, C.; Meneses, C.; Leger, P.; Fukuda, H. An empirical evaluation of supervised learning methods for network malware identification based on feature selection. Complexity 2022, 2022, 6760920. [Google Scholar] [CrossRef]
- Kimmel, J.C.; Mcdole, A.D.; Abdelsalam, M.; Gupta, M.; Sandhu, R. Recurrent neural networks-based online behavioral malware detection techniques for cloud infrastructure. IEEE Access 2021, 9, 68066–68080. [Google Scholar] [CrossRef]
- Ghurab, M.; Gaphari, G.; Alshami, F.; Alshamy, R.; Othman, S. A detailed analysis of benchmark datasets for a network intrusion detection system. Asian J. Res. Comput. Sci. 2021, 7, 14–33. [Google Scholar] [CrossRef]
- Alavizadeh, H.; Jang-Jaccard, J.; Enoch, S.Y.; Al-Sahaf, H.; Welch, I.; Camtepe, S.A.; Kim, D.S. A Survey on Threat Situation Awareness Systems: Framework, Techniques, and Insights. arXiv 2021, arXiv:2110.15747. [Google Scholar]
- Saeed, M.M. A real-time adaptive network intrusion detection for streaming data: A hybrid approach. Neural Comput. Appl. 2022, 34, 6227–6240. [Google Scholar] [CrossRef]
- Malware Dataset, IoT23. Available online: https://www.stratosphereips.org/datasets-iot23 (accessed on 12 September 2023).
- Chicco, D.; Jurman, G. The Advantages of the Matthews Correlation Coefficient (MCC) over F1 Score and Accuracy in Binary Classification Evaluation. BMC Genom. 2020, 21, 6. [Google Scholar] [CrossRef]
- Geetha, K.; Brahmananda, S.H. Network Traffic Analysis Through Deep Learning for Detection of an Army of Bots in Health IoT Network. Int. J. Pervasive Comput. Commun. 2022. ahead-of-print. [Google Scholar]
- Manju, N.; Harish, B.S.; Prajwal, V. Ensemble Feature Selection and Classification of Internet Traffic Using XGBoost Classifier. Int. J. Comput. Netw. Inf. Secur. 2019, 11, 37. [Google Scholar] [CrossRef]
- AbdulRaheem, M.; Oladipo, I.D.; Imoize, A.L.; Awotunde, J.B.; Lee, C.C.; Balogun, G.B.; Adeoti, J.O. Machine Learning Assisted Snort and Zeek in Detecting DDoS Attacks in Software-Defined Networking. Int. J. Inf. Technol. 2023, 1–17. [Google Scholar] [CrossRef]
- Anaraki, S.A.M.; Haeri, A.; Moslehi, F. A Hybrid Reciprocal Model of PCA and K-means with an Innovative Approach of Considering Sub-datasets for the Improvement of K-means Initialization and Step-by-Step Labeling to Create Clusters with High Interpretability. Pattern Anal. Appl. 2021, 24, 1387–1402. [Google Scholar] [CrossRef]
- Shutaywi, M.; Kachouie, N.N. Silhouette analysis for performance evaluation in machine learning with applications to clustering. Entropy 2021, 23, 759. [Google Scholar] [CrossRef] [PubMed]
- Lovmar, L.; Ahlford, A.; Jonsson, M.; Syvänen, A.C. Silhouette Scores for Assessment of SNP Genotype Clusters. BMC Genom. 2005, 6, 35. [Google Scholar] [CrossRef]
- Hariri, S.; Kind, M.C.; Brunner, R.J. Extended Isolation Forest. IEEE Trans. Knowl. Data Eng. 2019, 33, 1479–1489. [Google Scholar] [CrossRef]
- Han, K.; Wang, Y.; Tian, Q.; Guo, J.; Xu, C.; Xu, C. GhostNet: More Features from Cheap Operations. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition; IEEE/CVF, Seattle, WA, USA, 13–19 June 2020; pp. 1580–1589. [Google Scholar]











| Ref | Method | Key Characteristics | Differences | Limitations | Dataset |
|---|---|---|---|---|---|
| [14,15] | Malware Analysis and Detection | Static, Dynamic, Machine Learning Based Strategies | Varied approaches for malware categorization explored | Only specific malware is considered | muhstik, kenjiro |
| [16,17,18,19] | Static Assessment Techniques | Extracts byte, text, opcode sequences, function length distribution, functional call graph, PE file features | Focuses on static attributes for malware classification | Limited assessment of dynamic behaviors | MIRAI, okiru |
| [20,21] | Machine Learning Approaches | Utilizes static attributes for malware classification; Introduces oblique random forest technique | May face challenges in accurately detecting complex malware variants | Dependent on analysts’ interpretation of behaviors | Binary file datasets |
| [22] | Dynamic Assessment Methods | Extracts behavioral elements (system calls, network interactions, instruction sequences) | Captures malware behavior in dynamic environments | Limited applicability to heavily obfuscated malware | Behavioral traces, system call datasets |
| [23] | Similarity-Based Classification | Uses Hidden Markov Models (HMMs) to retrieve API call sequences | This entails computational overhead, particularly with reduced data | Efficacy may decrease with highly polymorphic malware | API call sequence datasets |
| [24] | Hybrid Methodologies | Combines static and dynamic attributes with machine learning | Offers an integrated approach combining diverse analysis techniques | Resource-intensive due to combined methodologies | Various malware datasets |
| [25,26] | Support Vector Machine (SVM) Approach | Extracts dynamic API call attributes for identification; Utilizes hybrid approach for improved results | The hybrid approach may outperform standalone techniques | Requires substantial labeled data for training | Dynamic behavior traces, labeled datasets |
| [27,28,29,30,31] | Visual-Based Techniques | Represents opcodes and system calls as visual images | Utilizes visual representations for malware analysis | Limited capability for handling dynamic behaviors | Image datasets, malware binaries |
| [32] | Treemaps, Thread Graphs | Visualizes malware behaviors from behavior records; Condenses significant behavior record reports | Offers visual summarization of behavior data | Complexity may increase with a large volume of behavior records | Behavior report datasets |
| [33,34] | Variant Malicious Code Detection | Utilizes image processing for rapid detection; Applies grayscale image conversion CNN features extraction | Rapid detection approach with high accuracy | May struggle with highly encrypted or packed malware | Image datasets, malware binaries |
| SNo | Name | Packets | Duration (h) | Zeek Flows | Pcap Size | Name of Dataset |
|---|---|---|---|---|---|---|
| 1 | Gagfyt | 217,000 | 12 | 35810 | 2. 8 MB | CTU-IOT 60-1 |
| 2 | Hide and Seek | 1,786,000 | 112 | 1008749 | 173 MB | CTU-IOT 1-1 |
| 3 | Kenjiro | 50,000 | 24 | 54659 | 433 MB | CTU-IOT 17-1 |
| 4 | Linux Hajime | 637,000 | 24 | 6378294 | 8.33 MB | CTU-IOT 9-1 |
| 5 | Mirai | 130,000 | 24 | 3394346 | 1.34 MB | CTU-IOT 48-1 |
| 6 | Muhstik | 496,000 | 36 | 156104 | 50 MB | CTU-IOT 3-1 |
| 7 | Okiru | 1,300,000 | 24 | 1364513 | 20 MB | CTU-IOT 3-1 |
| 8 | Tori | 50,000 | 24 | 3288 | 3.9 MB | CTU-IOT 3-2 |
| # | Column | Non-Null Count | Dtype |
|---|---|---|---|
| 0 | ts | 8008 non-null | object |
| 1 | uid | 8008 non-null | object |
| 2 | id.orig_h | 8008 non-null | object |
| 3 | id.orig_p | 8008 non-null | int64 |
| 4 | id.resp_h | 8008 non-null | object |
| 5 | id.resp_p | 8008 non-null | int64 |
| 6 | proto | 8008 non-null | object |
| 7 | service | 196 non-null | object |
| 8 | duration | 3213 non-null | object |
| 9 | orig_bytes | 3213 non-null | float64 |
| 10 | resp_bytes | 3213 non-null | float64 |
| 11 | conn_state | 8008 non-null | object |
| 12 | local_orig | 0 non-null | float64 |
| 13 | local_resp | 0 non-null | float64 |
| 14 | missed_bytes | 8008 non-null | int64 |
| 15 | history | 7481 non-null | object |
| 16 | orig_pkts | 8008 non-null | int64 |
| 17 | orig_ip_bytes | 8008 non-null | int64 |
| 18 | resp_pkts | 8008 non-null | int64 |
| 19 | resp_ip_bytes | 8008 non-null | int64 |
| 20 | TrafficLabeled | 8008 non-null | object |
| # | Column | Non-Null Count | Dtype |
|---|---|---|---|
| 0 | ts | 8008 non-null | object |
| 1 | id.orig_h | 8008 non-null | object |
| 2 | id.orig_p | 8008 non-null | object |
| 3 | id. resp_h | 8008 non-null | object |
| 4 | id.resp_p | 8008 non-null | object |
| 5 | proto | 8008 non-null | object |
| 6 | service | 8008 non-null | object |
| 7 | duration | 8008 non-null | float 64 |
| 8 | orig_bytes | 8008 non-null | float64 |
| 9 | resp_bytes | 8008 non-null | float64 |
| 10 | conn_state | 8008 non-null | object |
| 11 | missed bytes | 8008 non-null | int64 |
| 12 | history | 8008 non-null | object |
| 13 | orig_pkts | 8008 non-null | int64 |
| 14 | orig_ip_bytes | 8008 non-null | int64 |
| 15 | resp_pkts | 8008 non-null | int64 |
| 16 | resp_ip_bytes | 8008 non-null | int64 |
| 17 | Traffic_Labeled | 8008 non-null | object |
| 18 | Malicioūs | 8008 non-null | loat6 |
| ts | 1d.orig p | 1d.resp_p | duration | orig_bytes | resp_bytes | orig_ip_bytes | resp_ip_bytes | proto-icnp | proto-tcp | proto-udp | … | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Cluster 0 | 00:29.6 | 123 | 123 | 0.102094 | 48 | 48 | 76 | 76 | e | theta | 1 | … |
| 01:15.4 | 123 | 123 | 0.051969 | 48.6 | 48 | 76 | 76 | 8 | 8 | 1 | … | |
| 01:43.0 | 123 | 123 | 0.008233 | 96.6 | 96 | 152 | 152 | 0 | theta | 1 | … | |
| 02:22.8 | 123 | 123 | 0.008248 | 96 | 96 | 152 | 152 | e | e | 1 | … | |
| 03:48.0 | 29930 | 47659 | 0.044972 | 103 | 289 | 131 | 317 | e | 0 | 1 | … | |
| … | … | … | … | … | … | … | … | … | … | … | … | |
| 55:55.4 | 123 | 123 | 0.037777 | 48.6 | 48 | 76 | 76 | e | B | 1 | … | |
| 56:10.4 | 123 | 123 | 72.025952 | 384.8 | 384 | 698 | 698 | 8 | theta | 1 | … | |
| 56:48.0 | 49094 | 53 | 0.010745 | 39.6 | 55 | 67 | 83 | 8 | 8 | 1 | … | |
| 57:08.0 | 123 | 123 | 0.017637 | 48.6 | 48 | 76 | 76 | 0 | theta | 1 | … | |
| 57:08.0 | 123 | 123 | 0.017637 | 48.6 | 48 | 76 | 76 | 8 | B | 1 | … | |
| Cluster 1 | ts | 1d.orig p | 1d.resp_p | duration | orig_bytes | resp_bytes | orig_ip_bytes | resp_1p_bytes | proto-icnp | proto-tcp | proto-udp | … |
| 00:10.4 | 123 | 123 | 0.00809 | 0 | 0 | 76 | 0 | 8 | theta | 1 | … | |
| 00:10.4 | 123 | 123 | 0.00009 | 0 | B. 0 | 76 | theta | theta | B | 1 | … | |
| 08:32.2 | 29930 | 6889 | 0 | 0 | 0 | 95 | theta | 0 | e | 1 | … | |
| 08:36.0 | 29930 | 1844 | 31.982511 | 318 | 0 | 492 | theta | a | e | 1 | … | |
| 09:40.4 | 123 | 123 | 0.809090 | 0 | 0 | 76 | theta | e | 0 | 1 | … | |
| … | … | … | … | … | … | … | … | … | … | … | … | |
| 59:30.6 | 43763 | 39392 | 0.00009 | 0 | 0 | 40 | theta | 8 | B | 1 | … | |
| 59:39.8 | 43763 | 20473 | 0 | 0 | 0 | 40 | theta | theta | theta | 1 | … | |
| 59:39.0 | 43763 | 20473 | 0 | 0 | 0 | 40 | theta | 8 | B | 1 | … | |
| 59:44.8 | 43763 | 9376 | 0 | 0 | 0 | 40 | theta | 0 | theta | 1 | … | |
| 59:59.6 | 43763 | 50352 | 0.00809 | 0 | 0 | 40 | a | e | 1 | … | ||
| Cluster 2 | ts | id.orig_p | 1d.resp_p | duration | or1g_bytes | resp_bytes | orig_ip_bytes | resp_1p_bytes | proto-icnp | proto-tcp | proto-udp | … |
| 00:38.5 | 24159 | 8981 | 0.000254 | 0 | 0 | 168 | theta | 0 | 1 | 0 | … | |
| 09:46.6 | 35874 | 2323 | 2.998558 | 0 | 0 | 189 | 0 | theta | 1 | theta | … | |
| 00:46.0 | 35874 | 2323 | 2.998558 | 0 | 0 | 180 | theta | 8 | 1 | theta | … | |
| 69:51,0 | 49894 | 23 | 2.998788 | 0 | 189 | theta | theta | 1 | 8 | … | ||
| 01:00,6 | 52469 | 22 | 2.996594 | 0 | 0 | 189 | 6 | a | 1 | 8 | … | |
| … | … | … | … | … | … | … | … | … | … | … | … | |
| 58:29.6 | 49989 | 23 | 2.998792 | 0 | e.0 | 189 | 6 | a | 1 | theta | … | |
| 58:29.6 | 49989 | 23 | 2.998792 | 0 | e.e | 189 | theta | 0 | 1 | 0 | … | |
| 59:34.6 | 24159 | 8881 | 0.000255 | 0 | e.e | 160 | theta | theta | 1 | theta | … | |
| 59:39.0 | 60379 | 8880 | 2.998789 | 0 | 0 | 189 | 0 | 8 | 1 | 0 | … | |
| 59:39.0 | 69379 | 8880 | 2.998789 | 0 | 0 | 189 | e | theta | 1 | a | … | |
| … | … | … | … | … | … | … | … | … | … | … | … | … |
| Techniques | F1-Score | Accuracy | Precision | Recall | ROC-AUC | MCC | Fowlkes–Mallows Index | Cohen’s Kappa |
|---|---|---|---|---|---|---|---|---|
| ADA [20] | 0.78 | 0.89 | 0.81 | 0.76 | 0.88 | 0.67 | 0.79 | 0.65 |
| DTC [21] | 0.72 | 0.83 | 0.75 | 0.69 | 0.84 | 0.59 | 0.73 | 0.57 |
| LDA [22] | 0.68 | 0.82 | 0.72 | 0.65 | 0.8 | 0.55 | 0.7 | 0.52 |
| CNN [27] | 0.85 | 0.9 | 0.88 | 0.82 | 0.92 | 0.71 | 0.86 | 0.69 |
| DenseNet121 [28] | 0.82 | 0.87 | 0.85 | 0.79 | 0.92 | 0.74 | 0.82 | 0.71 |
| LG [29] | 0.73 | 0.85 | 0.76 | 0.7 | 0.87 | 0.63 | 0.75 | 0.61 |
| ResNet [35] | 0.89 | 0.91 | 0.92 | 0.87 | 0.94 | 0.79 | 0.88 | 0.78 |
| GNGRUE | 0.97 | 0.98 | 0.96 | 0.98 | 0.99 | 0.94 | 0.95 | 0.93 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almazroi, A.A.; Ayub, N. Enhancing Smart IoT Malware Detection: A GhostNet-based Hybrid Approach. Systems 2023, 11, 547. https://doi.org/10.3390/systems11110547
Almazroi AA, Ayub N. Enhancing Smart IoT Malware Detection: A GhostNet-based Hybrid Approach. Systems. 2023; 11(11):547. https://doi.org/10.3390/systems11110547
Chicago/Turabian StyleAlmazroi, Abdulwahab Ali, and Nasir Ayub. 2023. "Enhancing Smart IoT Malware Detection: A GhostNet-based Hybrid Approach" Systems 11, no. 11: 547. https://doi.org/10.3390/systems11110547
APA StyleAlmazroi, A. A., & Ayub, N. (2023). Enhancing Smart IoT Malware Detection: A GhostNet-based Hybrid Approach. Systems, 11(11), 547. https://doi.org/10.3390/systems11110547








