Abstract
This work formulates and solves the actual problem of studying the logistics of unmanned aerial vehicle (UAV) operations in facility security planning. The study is related to security tasks, including perimeter control, infrastructure condition monitoring, prevention of unauthorized access, and analysis of potential threats. Thus, the topic of the proposed publication is relevant as it examines the sequence of logistical actions in the large-scale application of a swarm of drones for facility protection. The purpose of the research is to create a set of mathematical and simulation models that can be used to analyze the capabilities of a drone swarm when organizing security measures. The article analyzes modern problems of using a drone swarm: formation of the swarm, assessment of its potential capabilities, organization of patrols, development of monitoring scenarios, planning of drone routes and assessment of the effectiveness of the security system. Special attention is paid to the possibilities of wave patrols to provide continuous surveillance of the object. In order to form a drone swarm and possibly divide it into groups sent to different surveillance zones, the necessary UAV capacity to effectively perform security tasks is assessed. Possible security scenarios using drone waves are developed as follows: single patrolling with limited resources; two-wave patrolling; and multi-stage patrolling for complete coverage of the protected area with the required number of UAVs. To select priority monitoring areas, the functional potential of drones and current risks are taken into account. An optimization model of rational distribution of drones into groups to ensure effective control of the protected area is created. Possible variants of drone group formation are analyzed as follows: allocation of one priority surveillance zone, formation of a set of key zones, or even distribution of swarm resources along the entire perimeter. Possible scenarios for dividing the drone swarm in flight are developed as follows: dividing the swarm into groups at the launch stage, dividing the swarm at a given navigation point on the route, and repeatedly dividing the swarm at different patrol points. An original algorithm for the formation of drone flight routes for object surveillance based on the simulation modeling of the movement of virtual objects simulating drones has been developed. An agent-based model on the AnyLogic platform was created to study the logistics of security operations. The scientific novelty of the study is related to the actual task of forming possible strategies for using a swarm of drones to provide integrated security of objects, which contributes to improving the efficiency of security and monitoring systems. The results of the study can be used by specialists in security, logistics, infrastructure monitoring and other areas related to the use of drone swarms for effective control and protection of facilities.
1. Introduction
The use of unmanned aerial vehicles (UAVs) for facility protection has become particularly relevant in recent years due to the growing need for continuous surveillance, improved response time, and risk reduction under limited resources. UAV-based automated security systems offer flexibility and scalability in monitoring large areas, enabling real-time adaptation to changing conditions. This is especially important for complex or strategically significant sites that require persistent observation and rapid threat detection. Swarm-based UAV systems demonstrate considerable potential for enhancing perimeter control, threat prevention, and infrastructure monitoring. The implementation of drone swarms enables distributed sensing, cooperative behavior, and synchronized patrol missions. Of particular importance is the development of strategies for wave-based patrolling, where groups of drones alternate in carrying out surveillance tasks to maintain uninterrupted coverage of critical zones. Recent research has focused on key technical components necessary for the deployment of drone swarms, including RF-based UAV detection [1,2], group formation and patrol coordination [3], and ensuring mission reliability in swarm configurations [4]. These studies emphasize the potential of swarm-based surveillance systems and the growing need to design robust and adaptive operational strategies. Work in the field also highlights the importance of drone classification based on protocol-layer signatures [5,6], as well as biologically inspired routing approaches that support flexible trajectory planning [7]. Furthermore, the efficiency of any swarm patrol mission is largely dependent on the correct configuration of the swarm, taking into account the characteristics of individual drones and the surveillance demands of the area [8].
Nevertheless, a number of unresolved challenges remain. Among them are the following: limited flight endurance of UAVs; the need for dynamic redistribution of surveillance tasks under changing threat conditions; and the necessity of ensuring continuous monitoring over wide or segmented areas. These issues are particularly acute in wave patrolling scenarios, where different drone groups must coordinate to maintain persistent coverage and adapt routes based on threat levels, terrain, or resource availability. The objective of this study is to formalize the sequence of logistical actions required for organizing wave-based patrolling of protected facilities using UAV swarms. To achieve this, a system of mathematical and simulation models is developed. These models help evaluate the swarm’s surveillance potential, predict performance degradation, construct patrol routes, and optimize the allocation of drones across multiple zones of interest. An additional contribution to this research is the development of an agent-based simulation model using the AnyLogic platform. This model enables the testing of patrol strategies under realistic and dynamic threat scenarios. By simulating the behavior of individual drones as autonomous agents, the system supports real-time decision-making, coordination, and adaptation—factors that are critical for mission success in real-world deployments. The proposed approach aims to bridge the gap between theoretical models and practical applications of UAV swarms in facility security. It contributes to the advancement of integrated security systems by offering scalable, adaptive, and efficient methods for surveillance mission planning and execution.
1.1. Motivation
The organization of wave patrolling by drone swarms requires careful planning of logistical operations to ensure the effectiveness of drone use [9,10]. It is necessary to analyze the situation in the area of the protected object and identify actual high-risk areas requiring enhanced surveillance, taking into account the necessary monitoring capacity (surveillance capability and security terminology). Further formation of the swarm and its division into groups in flight depend on the limited capabilities of the drones to maintain the required level of observation capability (OP). In order to fully cover the territory and ensure reliable security, it is possible to use wave patrolling for the following:
where PM = PM1 + … + PMk + … + PMN, where every k-a wave of surveillance drones has observation potential PMk, and where . The success rate of wave patrolling depends on the PM value. After detailed monitoring of risk areas by wave surveillance drones, the final observation potential of the territory emerges P′Q (P′Q < PQ). This has to be taken into account in order to conduct a new patrolling phase of the protected object. In this case, different strategies related to the formation of surveillance drone waves are possible to effectively utilize the swarm [11,12].
PM ≥ PQ,
Therefore, the topic of the proposed research is relevant, as the modeling of possible planning strategies for wave patrolling of a swarm of drones to maximize the security level of the protected object is conducted.
1.2. State of the Art and Problem Statement
- Therefore, the technologically innovative element of modern security system in the form of wave patrolling of surveillance drones allows for a change in the approach to the protection. The use of unmanned aerial systems in wave patrol mode has demonstrated high potential for ensuring the security of facilities. However, analysis of the literature indicates a number of serious problems that require systematic scientific study. In particular, difficulties have been identified related to navigation in the absence of GPS [13], as well as the need to counter modern drone suppression and interception systems [14].
- One of the key tasks remains the development of wave patrol strategies in the area of the protected facility. Existing studies mainly describe the autonomous behavior of drones and the basics of swarm construction, but rarely take into account the variability of threats and the need to adapt routes in real time [15,16].
- The task of forming waves of drones within a swarm remains relevant. Existing methods often assume the homogeneity of the swarm, ignoring differences in the functional characteristics of UAVs, as well as possible limitations in terms of radio interference, energy shortages, and external interference [17,18].
- Considerable attention is paid, in the literature, to planning patrol routes, but most proposals are based on fixed trajectories and do not take into account adaptive responses to identified threats or possible countermeasures by intruders [19,20].
- A separate problem is the assessment of the potential of drones to provide complete zonal visualization of the protected territory. A number of studies use a simplified coverage assessment that does not take into account efficiency losses when encountering electronic countermeasures or adverse weather conditions [21,22].
- Questions regarding the justification of wave patrol scenarios have not yet been fully resolved. In many cases, there is no link between the choice of scenario, the current operational situation, and the parameters of the swarm. It is necessary to take into account the level of risk, priority areas, and available resources when forming a scenario series [23,24].
- Organizing a group of drones within a swarm requires more flexible approaches. It is necessary to take into account not only the number of available drones, but also the need for dynamic resource reallocation, considering security tasks and the configuration of the object [25,26].
- It is important to plan wave routes taking into account risks and obstacles. Although some studies consider methods of potential fields and formation of structures, they are often not adapted to the real situation and do not provide resistance to external influences [27,28].
- Finally, the assessment of threats identified by the first waves and the formation of repeat patrol routes remain poorly researched. Approaches in which the results of the first pass are used to adjust the composition and trajectory of subsequent waves are practically not implemented in existing models [29,30].
Thus, despite the achievements made, the current state of research in the field of wave patrolling drones remains fragmented. It is necessary to develop an integrated concept that includes swarm formation strategies, scenario planning, risk assessment, routing, and adaptive organization of repeat observation waves in real-world threat conditions.
1.3. Objectives and Methodology
There is a contradiction between the possibilities of effective use of surveillance drone waves for object security and the imperfection of existing research methods and models, as well as the lack of system analysis of strategies for conducting complex monitoring with the help of drone waves. This contradiction is the object of research in the proposed publication, which presents models for the creation of applied information technology for planning wave patrol strategies that maximize the level of security of the protected object.
The purpose of the research is to create a set of mathematical and simulation models that can be used to analyze the capabilities of a swarm of surveillance drones in conducting wave patrolling of the territory.
In accordance with the purpose of the study, the following tasks need to be accomplished:
- Conduct a system analysis of wave patrolling by a swarm of surveillance drones.
- Formulate a set of scenarios for conducting territory monitoring by drone swarm waves.
- Divide the drone swarm into groups to effectively cover the territory and monitor different areas.
- Plan the flight paths of surveillance drones in wave patrolling.
- Create an agent model to implement automated wave patrolling by surveillance drones.
Mathematical methods and models used to study wave patrolling using a swarm of surveillance drones: system analysis, optimization models, simulation model, and agent model.
This study uses modern methods—system analysis, optimization models, simulation, and agent-based modeling—which were compared with traditional approaches previously used to solve facility security problems. Unlike static or simplified models, system analysis allows for the consideration of complex interrelationships and the dynamics of threats that arise during surveillance and patrols. Optimization approaches provide a more efficient allocation of resources compared to heuristic methods, which do not always take into account changing security conditions. Simulation modeling, in particular using the AnyLogic platform, allows you to create realistic patrol scenarios that take into account external influences, while agent models reflect the behavior and interaction of individual drones within a complex system. This is especially important in the context of multi-level management and real-time threat response. Thus, ref. [22] emphasizes the importance of using UAVs in logistics, taking into account routes and restrictions similar to security tasks. Ref. [23] analyzes the limitations of traditional drone security systems and emphasizes the need for adaptive solutions. Ref. [24] examines threats in hybrid conflicts, where the use of standard methods proves insufficient. All this confirms the relevance of applying the approaches used in this study.
2. System Analysis of Wave Patrolling with a Swarm of Surveillance Drones
The experience of applying unmanned technologies in the field of facility security has shown the effectiveness of using a swarm of drones. However, to ensure complete security and control over the territory, it is necessary to apply waves of patrol drones due to the following reasons:
- Limited capacity (PM) of the formed swarm of patrol drones, which does not allow for full control of the protected area at one time (PQ), (PM < PQ).
- Active use of drone countermeasures by intruders reduces the effectiveness of patrol drones as they approach the security object (P′M < PM), where P′M is the final potential of the drone swarm after the impact of suppression means.
- Using a single patrol route in each drone wave allows intruders to adapt and find ways to bypass the security system. Therefore, a new route should be formed in each new wave, which increases the unexpectedness of patrolling and the efficiency of violation detection.
- Dividing the drone swarm into groups focused on different control areas makes it difficult to predict their movements, which increases the effectiveness of site security.
Thus, a systematic analysis of the above factors led to the following logical sequence of actions for organizing patrol waves using drone swarms:
- Forming a set of protected areas (F) as subsets (), where each subset fi represents a separate protected area associated with a particular i-th security zone (SZ);
- Assessment of the required level of control and surveillance (PQi), in each i-th SZ to form the appropriate drone patrol team capability (PMi ≥ PQi);
- Analyzing possible drone countermeasures in each i-th SZ and predicting the potential loss of drone effectiveness while performing patrols (P′Mi < PMi);
- Predicting the number of patrolling waves required to provide full control in each i-th SZ such that P′Mi1 + … + P′Mik + … + P′Miv ≥ PQi, where P′Mik is the patrolling potential realized by the k-th wave after analyzing the security level of the facility, and v is the possible set of active zones of the SZ;
- Formation of travel routes for each i-th group of drone swarm in the k-th wave, taking into account the final set of zones located in each i-th SZ.
In order to plan the proposed logistical actions in the field of site security, it is necessary to develop strategies for possible patrol waves. Due to the complexity of the problem to be solved and the risks associated with predicting potential violations, it is necessary to form not one, but a whole set of possible strategies. Choice of the necessary strategy will depend on the current circumstances in the protected area, as well as on the operational and tactical tasks facing the security service at the moment.
3. Generating a Set of Scenarios for Conducting Waves of Drone Swarm Patrols
The formation and selection of a rational scenario for conducting patrol waves with drone swarms depend on the capabilities of patrol drone swarm formation (number of drones and their functional potential PM), a set of actual surveillance areas requiring the necessary level of control (PQ), operational and tactical tasks of the security service at the moment, as well as other factors related to the situation at the protected object. Therefore, the following set of strategies for organizing drone swarm patrol waves was analyzed and presented, which is not definitive but takes into account the existing practice of unmanned systems application in facility security.
- A strategy related to the limited ability to create a swarm of patrol drones to provide full control over a facility. In this case PM < PQ. Therefore, it is necessary to define a set of prioritized surveillance areas to be controlled by a swarm of patrol drones. Due to capacity constraints, patrolling will be conducted by a single wave of drones. When the swarm flies, it is necessary to form groups of drones that will be directed to the corresponding set of security zones such that PMi ≈ PQi for each selected zone i. Due to the possible use of drone countermeasures by intruders, the final potential P′Mi arises when approaching the target zones, which may be less than PQi (P′Mi < PQi). Therefore, after a single drone patrol of the protected object, the control over certain zones may remain incomplete due to the limited capabilities of the swarm.
- A strategy where it is possible to create a swarm of patrol drones to conduct not one but two waves of patrols in order to ensure full control over the protected object. In this case, after the first wave of patrolling, the total surveillance potential required for complete control of the area is analyzed (P′Q1), and the possibility of forming a swarm of patrol drones for the second wave of patrolling is evaluated. The following options are possible:
- PM2 > P′Q1. In this case, it is possible to ensure full control over the protected area after patrolling by drone swarms.
- PM2 ≈ P′Q1. Patrol results may not result in full control of the protected area if trespassers actively use drone countermeasures.
- PM2 < P′Q1. In this case, the security management decides whether it is possible to conduct a second wave of drone patrols under the conditions of incomplete control of the protected area, taking into account the resulting surveillance potential that needs to be considered to ensure full control of P′Q2. Therefore, if necessary, a third wave of drone patrol swarms should be formed to fully cover and monitor the protected site.
- A strategy aimed at complete control over the protected territory in all surveillance zones by forming the required number of patrol drone swarm waves. In this case, the results of each drone patrol for the k-th wave determine the final surveillance potential required for complete control of the territory (P′Qk) and a swarm of patrol drones with surveillance potential PMk ≥ P′Qk is formed. To ensure complete control of all i-th security zones, the following is necessary:where N is the number of waves providing full control over all security zones in the protected area.
4. Split the Drone Swarm into Groups for Effective Control and Surveillance of Protected Areas
The mathematical models presented are aimed at the effective distribution of unmanned aerial vehicles (UAVs) between zones of the protected area, taking into account their functional potential. The potential of each drone (pMj) reflects its surveillance and control capabilities. The total potential of the group sent to zone i is denoted as PMi and must satisfy the requirement PMi ≥ PQi, where PQi is the required level of surveillance in a given zone.
For a better understanding, let us look at a simplified example. Let there be three drones:
pM1 = 5, pM2 = 6, and pM3 = 7.
There are two surveillance zones:
Q1 = 10 and Q2 = 6.
The possible distribution is as follows:
drones 2 and 3 are sent to zone 1, PM1 = 13;
drone 1 is sent to zone 2, PM2 = 5 (the zone is partially covered).
Thus, the priority zone is provided with the required level of control, and the available resources are used as efficiently as possible.
In order to divide the patrol drone swarm into groups to provide control over the security zones, the functional potential of the drone swarm (PM), as well as the surveillance potential required for complete control over the area (PQ) must be considered. To ensure complete control in each i-th SZ, the difference between PMi-PQi is considered, where PMi ≥ PQi. Here PQi will refer to those SZs that have been selected for priority patrolling by the patrol drone swarm (). The following strategies for dividing the drone swarm into groups are possible:
1. A strategy based on selecting one of the most important SZ to maximize territory control. The selected SZ will be under increased surveillance by patrol drones under limited drone swarm formation capabilities. In this case, in order to maximize the effectiveness of territory control in the selected SZ (suppose it has the number “1”), it is necessary to provide max (PM1-PQ1), where PM1 ≥ PQ1. For the remaining i-th safety zones, constraints are introduced in the form of allowable values of P′Mi such that PMi ≥ P′Mi, . To find max (PM1-PQ1), where PM1 ≥ PQ1, we introduce a Boolean variable xij, where “i” denotes the i-th safety zone and “j” denotes the j-th functional potential of the j-th drone in the swarm:
Then the functional potential of the i-th drone group, which will be directed to the i-th SZ, is defined as follows:
where pMj is the functional potential of the j-th drone (e.g., its technical capabilities for surveillance and data collection),
M is the number of patrol drones in the swarm.
You need to find max (PM1-PQ1), PM1 ≥ PQ1, where
taking into account the restrictions on the permissible values of P′Mi for the remaining i-th safety zones:
2. A strategy based on the formation of a priority series for a set of SZ in which key surveillance objects are located. For this purpose, we introduce the importance (weight) for each zone, where . Then we will use an optimization criterion in the form of additive convolution when creating groups of patrol drones from a swarm:
It is necessary to maximize D, that is the following:
subject to restrictions on permissible values P′Mi, PMi ≥ P′Mi, :
3. A strategy based on evenly distributing the functional potential of patrol drones into groups that will be sent to security zones for surveillance and control. In this case, the following criteria are used to form patrol drone groups from the swarm .
We need to find the following:
where is an additional variable used to transform the minmax search problem into a min search problem [30].
To solve the optimization problem, it is necessary to take into account the constraints on the formation of the functional potential of drones P′Mi, which are determined by the security service to ensure surveillance and control in each security zone:
The division of a patrol drone swarm during flight into groups that will be sent to selected SZ for surveillance and control has many solutions. The choice of a rational solution depends on the operational situation in the protected area, possible means of drone countermeasures, capabilities of the drone swarm control system, goals of the security operation, and other factors. Let us consider typical schemes of distribution of patrol drones in flight, which are used in practice:
- The division of the patrol drone swarm into groups to be sent to the respective SZ for surveillance and control is performed at the very initial stage when the drone swarm is launched. Each i-th group of drones is sent to the i-th security zone to ensure effective monitoring and control over the territory.
- A swarm of patrol drones is divided into groups at a pre-selected navigation point to which it is directed after launch. Once separated, each i-th group of drones will be sent to the i-th SZ to provide control and monitoring of the area.
- The patrol drone swarm is divided into groups as many times as the number of actual data points used to conduct monitoring and control in the selected security zones (), where N is the number of actual SZ to be monitored. For this purpose, it is necessary to generate N navigation points for the patrol drones flight, where the swarm will be divided into groups.
- The distribution of the patrol drone swarm is performed N′ times, where N′ < N. That is, the number of navigation points for drone swarm separation is less than the number of actual SZ selected for surveillance and control.
To solve the problem of optimal distribution of the swarm into groups, we used linear programming with constraints on observation potential. Standard simplex optimization methods were applied using built-in AnyLogic 8.9.5 functions and the Python 3.11.10 PuLP module. Each objective function (e.g., maximum D for the zone prioritization strategy) was calculated taking into account constraints on the number of drones, their functional load, and zone coverage. In the uniform distribution problem, a minmax model was used, converted into a minimization problem using auxiliary variables.
5. Planning Drone Patrol Routes to Protect the Facility from Threats
An original algorithm based on simulation modeling (AnyLogic platform) was developed to plan drone patrol routes for facility security. It allows you to form the movement of drones (swarms, groups) in the face of active threats, such as unauthorized intrusion or countermeasures against unmanned vehicles. With the help of the developed algorithm, you can effectively organize patrol routes, optimizing the coverage of the territory and the speed of response to potential dangers:
- The fastest patrol route that allows drones to respond quickly to suspicious objects and potential violations, minimizing the time to detect incidents;
- The safest route that minimizes risks to drones in the event of adverse conditions, communication failures, or environmental interference;
- A compromise solution that combines speed and safety, allowing for effective control of the territory, reducing the likelihood of losing coverage of important areas.
Let us take a look at the main steps of the developed algorithm using the example of finding the shortest drone flight route (swarm, group) for patrolling and protecting an object:
Step 1. Formation of a map with a set of navigation points along the drone’s route. These points are used for possible flight adjustments and division of drones into groups for more efficient coverage of the territory.
Step 2. Determining the parameters of the initial navigation point of the drone flight—“A” (navigation coordinates), as well as the parameters of the final flight point—“B” (controlled area or point of interest for protection).
Step 3. Start the simulation of the drone (or group of drones) movement from the starting point “A”. If there are several possible routes to different navigation points, the algorithm divides the route into alternative directions, allowing parallel analysis of different trajectories.
Step 4. The reached navigation point is marked as passed. If other drones (or their digital equivalents in the simulation) approach the same point, they receive updated data on the already laid route, which avoids duplication of trajectories and optimizes the patrolling process.
K-step. At each subsequent step of the algorithm, steps 3 and 4 are repeated for the navigation points that have been marked and from which requests have been sent to neighboring points.
When the drone or its digital equivalent (in the simulation) reaches the endpoint “B” (controlled area or important security point), the movement of other options (clones) stops.
Next, the drone’s patrol route (swarm, group) is formed using navigation points that have labels. This route is the shortest in terms of travel time.
To find the safest patrol route in the developed algorithm using simulation modeling, the main parameter is not the flight time (T), but the level of risk (R). Risks that form the overall risk level R on the drone’s flight route are determined after analyzing the environment, possible obstacles, meteorological conditions, and other factors that may affect the drone’s operation.
A compromise solution (in terms of time and risk level) for finding a rational drone patrol route (swarm, group) is formed using a generalized assessment of time and risk, which allows for an optimal balance of the object’s security efficiency:
where —the importance of drone (swarm, group) flight time between navigation points;
—the significance of the risk level of drone flight (swarm, group) between navigation points;
, meaning , are determined by the operator or security system depending on the environment;
is the relative value of the flight time between the e-th and k-th navigation points (dimensionless value);
is the relative value of the flight risk between the e-th and k-th waypoints (dimensionless value).
The developed algorithm is indeed based on the principles of A* and Dijkstra, but differs in its adaptation to the specifics of swarm tasks: it includes a route risk assessment mechanism and a module for distributing navigation points between groups of drones in real time. This hybrid approach allows for the probability of attacks, communication interruptions, and obstacle avoidance to be taken into account. This is critical for patrol tasks, which require coordinated behavior and multiple branching of the swarm, which goes beyond the scope of classical routing algorithms.
6. Agent-Based Modeling of Drone Swarm Coordination for Facility Security
The developed set of models is the basis for creating an agent-based technology for studying drone coordination in the process of object protection using wave patrolling of a swarm of drones. The AnyLogic platform was used to develop the agent-based simulation model [30]. Due to the complexity of the tasks to be solved, the agent structure of the model has a two-level representation. At the first level, the following set of agents is formed:
- Agent for selecting the wave patrol scenario. It consists of the following second-level agents:
- Single-wave patrol agent—provides inspection of the object in one pass of a swarm of drones, which is used for quick monitoring of the territory.
- Dual-wavelength patrol agent—allows for repeated passes of drones to increase the accuracy of detecting potential threats or to check the object after the first scan.
- Multi-wave patrol agent—organizes continuous monitoring of the object, which ensures the maximum level of protection and control of all changes in the patrol area.
- The agent for forming patrol drone groups (based on their functional capabilities) consists of the following second-level agents:
- An agent for selecting the most important security zone for surveillance.
- An agent that uses zone prioritization to allocate drones.
- An agent for evenly distributing the potential of a swarm (groups) of patrol drones to monitor the protected area.
- An agent for dividing a swarm of patrol drones in flight into groups consists of the following second-level agents:
- An agent for dividing a swarm into groups when launching patrol drones.
- An agent for distributing the swarm at a given navigation point of the patrol drones flight.
- An agent for repeatedly dividing the swarm of patrol drones in flight at specified navigation points.
- The agent for patrol drone flight routing consists of the following second-level agents:
- An agent for generating the shortest (in time) flight route of patrol drones to surveillance areas.
- An agent for generating the least risky flight route of patrol drones to surveillance areas.
- An agent for generating a compromise flight route (in terms of time and risk) of patrol drones to surveillance areas.
- An agent for interactive simulation of wave patrolling by a swarm of patrol drones to control a protected area.
- Agent for analyzing simulation results.
Figure 1 shows a block diagram of the agent model.
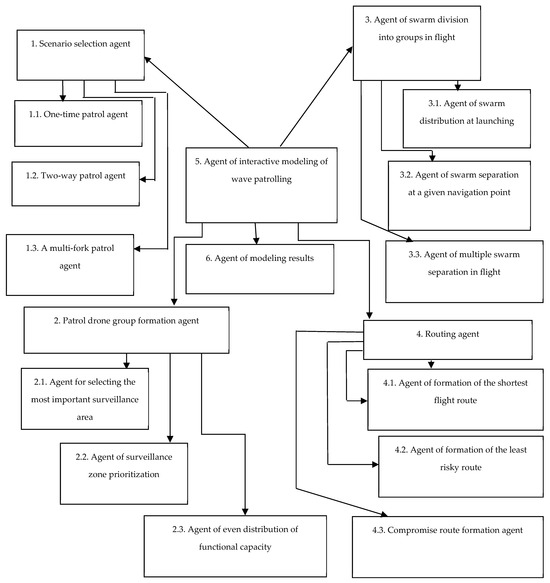
Figure 1.
Block diagram of the agent model.
To ensure coordination of the drone swarm, mechanisms are provided to avoid collisions and maintain formation. The model implements Boids rules (separation, alignment, cohesion), supplemented by dynamic restrictions on speed and maneuver angle. This allows the behavior of drones in a dense group to be simulated while maintaining mutual distance and synchronizing movement. In addition, a priority response mechanism is used when trajectories intersect, which prevents local conflicts and maintains the stability of the formation.
Model Verification and Error Analysis
In order to increase the reliability of the results obtained and confirm the adequacy of the developed agent model for patrolling a protected area using a swarm of unmanned aerial vehicles (UAVs), a verification and sensitivity analysis procedure was carried out. The model was implemented in the AnyLogic software environment, where each unit of the swarm is considered as an autonomous agent with its own characteristics and behavior.
Model verification. The following activities were carried out during the verification stage. The simulation results—in particular, the coverage area of the protected territory and the average response time to a potential threat—corresponded to the expected values calculated analytically for the given system parameters (number of UAVs, size of surveillance areas, autonomous operation time of drones). During multiple runs with the same input data (10 series of 100 iterations each), stable values of key metrics were observed. The average standard deviation for the territory coverage indicator did not exceed 2.5%, which indicates the reproducibility of the results. Under extreme parameters (for example, when using the minimum number of UAVs or when the threat density is high), the model demonstrated the expected decrease in patrol efficiency, correctly reflecting the insufficiency of system resources.
7. Modeling of a Special Case of Using a Swarm of Drones to Perform a Task
In the case of modeling swarm task execution by drones, each drone is treated as a separate agent with its own goals, behavior, and constraints, while interacting with other agents to achieve a common goal.
Each drone is described as an agent with a set of characteristics such as the following:
- -
- Position pi(t)—coordinates in space ;
- -
- Speed ;
- -
- Orientation ;
- -
- Max speed ;
- -
- Limitations on speed and maneuverability.
The following tasks were chosen as the goal: movement towards a given target (modeled in Unity environment) and object protection (AnyLogic).
The general goal is formed through the function of the target state for the whole swarm:
where —final position of each agent.
In doing so, each agent had localized goals:
- -
- Following the leader;
- -
- Keeping an optimal distance from neighbors;
- -
- Avoiding obstacles;
- -
- Avoiding collisions.
The rules of cooperation between drones are chosen to follow the Boids models:
- -
- Collision avoidance rule: Each agent avoids collision with neighboring drones:where —set of neighbor’s agents that are less than a given distance from the threshold.
- -
- Alignment rule: An agent corrects its speed based on the average direction of its neighbor’s speed:
- -
- Cohesion rule: The agent tends to keep a certain distance from the center of mass of its neighbors:where .
The cost minimization function is chosen as the optimization function (considering deviation from the goal for each agent, energy costs (e.g., through the ), sanctions for collisions, and getting too close to other agents):
where —weights that prioritize the objectives.
Each agent is controlled based on local information and data received from neighbors’ drones. The control is based on the feedback principle:
where —control action, and —control function that takes into account the local state of the drone and its environment.
The dynamics of each drone are described by a system of differential equations:
where —control, depending on the planning algorithm and interaction with neighbors.
So, when modeling the protection of the territory, the area of the territory to be considered for the selected period of time was chosen as a parameter of monitoring efficiency. For this purpose, the simulation model realized the function of “coloring” the territory located in the ellipsoid of the local neighborhood for the observed UAVs (Figure 2). After the end of the monitoring time (set by the user before the experiment), the area of the “colored” territory is calculated.
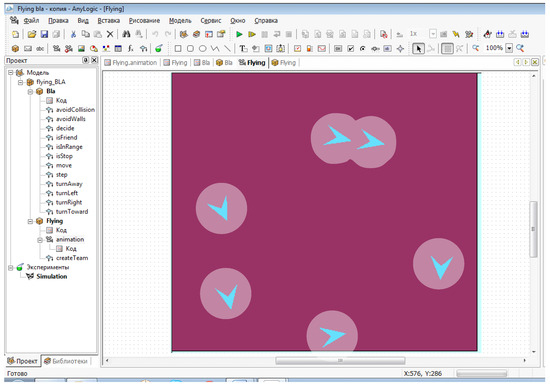
Figure 2.
Simulation model.
For modeling the movement towards a given object, it was found that the greatest effect is expected when using UAVs in the form of self-organizing groups (flocks, swarms, clusters, orders, etc.) with a variable degree of autonomy—in time and by control functions—from remote control to fully automated behavior.
For modeling the movement of a UAV swarm, several drone models were placed on the stage, and their original positions were adjusted. After adding the Ros interaction script and the control program modeling subscripts, the UAV team behavior simulation was launched (Figure 3).
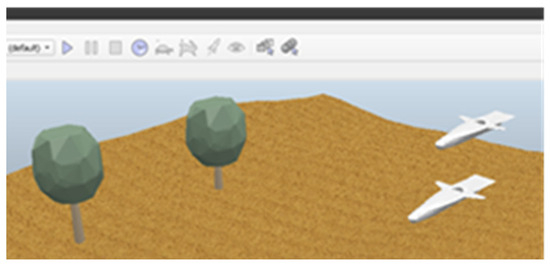
Figure 3.
Model of visualization of the flight of unmanned aerial vehicles according to the “master-slave” model.
8. Discussion
A system representation of logistic actions for organizing mass patrolling of a protected area by waves of drone swarms is carried out. A set of scenarios is analyzed to plan security actions using a swarm of patrol drones. To create patrol drone swarm groups that will move to key SZ, possible formation options are presented in the form of allocating an important security zone with priority control, forming a priority row of security zones for patrolling, and evenly distributing the potential of patrol drone swarms sent to surveillance zones.
A set of scenarios was analyzed and formed to divide a swarm of drones in flight into groups for patrolling a protected area: swarm distribution at drone launch; swarm distribution at a given navigation point of flight; and multiple distribution of drones at navigation points of flight.
The routes of movement of drone swarm groups to the security zones were formed taking into account time and risk indicators in the form of the route with the shortest movement time, the least risky route, and the compromise route.
The use of a set of logically related models allows for the planning of patrol drone actions using wave patrolling.
The formal representation of the methodology of security action research using wave patrolling of a drone swarm includes the following steps:
- Selecting a security scenario for the facility.
- Formation of swarm groups taking into account the surveillance and defense potential of security drones.
- Distribution of the swarm in flight to cover different areas of the protected territory using groups of security drones.
- Planning flight routes for security drones to monitor and respond to potential threats in the face of enemy UAVs.
- Interactive agent-based simulation modeling of logistics operations to ensure the protection of a certain territory using waves of swarms of security drones.
The set of developed models was implemented on the AnyLogic agent platform using interactive simulation modeling. The results of the study will allow security forces in the face of modern hybrid threats to plan protective actions to protect critical infrastructure using security drones in the form of coordinated waves of drone swarms. This helps to ensure continuous monitoring, rapid detection of threats, and increase the level of security of the facility.
To increase the practical value of the research, it is advisable to present possible scenarios for the practical application of the proposed models. The developed patrol system using a swarm of UAVs can be adapted to protect various types of facilities, from logistics centers to industrial enterprises and critical infrastructure nodes. The use of wave patrolling allows for continuous monitoring of the territory, rapid response to threats, and efficient use of limited drone resources. The use of agent-based modeling on the AnyLogic platform allows the model parameters to be adapted to the specific conditions of the facility—perimeter length, terrain characteristics, presence of obstacles, and intrusion scenarios. Thus, the developed strategies can be integrated into existing security systems, enhancing their autonomy, flexibility, and scalability.
9. Conclusions
This study presents a comprehensive approach to organizing wave-based patrolling using UAV swarms for facility security. A system of mathematical and simulation models has been developed to support surveillance planning, drone group formation, optimal route selection, and dynamic redistribution of UAV resources based on threat levels and zone priorities.
The research introduces patrol strategies adapted to varying operational scenarios, including single, dual, and multi-stage wave deployment. The use of agent-based modeling in the AnyLogic environment allowed for evaluating coordination mechanisms, swarm division schemes, and route behavior under dynamic conditions.
Despite the effectiveness of the proposed models, certain limitations remain. The simulation does not yet account for environmental factors such as weather, terrain complexity, or energy consumption variability. Additionally, physical validation of the proposed approach has not been performed.
Future research will aim to incorporate real-time environmental data, model UAV endurance more accurately, and conduct field testing to enhance realism and reliability.
Overall, the developed system provides a scalable and adaptable framework for UAV-based facility protection, enabling continuous monitoring and improved responsiveness to emerging threats.
The proposed approach allows analyzing the possibilities of effective patrolling with the help of a swarm of security drones to ensure the security of objects, which contributes to the efficiency of operational and tactical actions of security forces in the protection zone.
Author Contributions
Systematic representation of logistics actions for the formation of a swarm of drones for mass patrolling of a protected object and the creation of security scenarios—O.F. Distribution of tasks in the group for modeling patrolling, modeling monitoring of protected objects, interactive swarm division into groups taking into account the observation potential of security drones, and modeling of swarm interaction in software environments—M.L. Division of the swarm into groups taking into account the observation potential of security drones, modeling the interaction of swarms in software environments, and description of the mathematical model of swarm interaction—D.K. Interactive modeling of the flight of groups of swarms of drones and agent-based modeling of logistics actions of security forces for organizing patrolling of a protected object—O.P. All authors have read and agreed to the published version of the manuscript.
Funding
This research has not received external funding.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Lv, H.; Liu, F.; Yuan, N. Drone Presence Detection by the Drone’s RF Communication. J. Phys. Conf. Ser. 2021, 1738, 012044. [Google Scholar] [CrossRef]
- Huynh-The, T.; Pham, Q.-V.; Nguyen, T.-V.; Da Costa, D.B.; Kim, D.-S. RF-UAVNet: High-Performance Convolutional Network for RF-based Drone Surveillance Systems. IEEE Access 2022, 10, 49696–49707. [Google Scholar] [CrossRef]
- Soto, M.; Nava, P.; Alvarado, L. Drone Formation Control System Real-Time Path Planning. In Collection of Technical Papers—Proceedings of the 2007 AIAA InfoTech at Aerospace Conference, Rohnert Park, CA, USA, 7–10 May 2007; American Institute of Aeronautics and Astronautics: Reston, VA, USA, 2017; Volume 1. [Google Scholar] [CrossRef]
- Guo, J.; Wang, L.; Wang, X. A Group Maintenance Method of Drone Swarm Considering System Mission Reliability. Drones 2022, 6, 269. [Google Scholar] [CrossRef]
- Jordan, J. The future of unmanned combat aerial vehicles: An analysis using the Three Horizons framework. Futures 2021, 134, 102848. [Google Scholar] [CrossRef]
- Morge-Rollet, L.; Le Jeune, D.; Le Roy, F.; Canaff, C.; Gautier, R. Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint. Sensors 2022, 22, 6701. [Google Scholar] [CrossRef]
- Chao, Y.; Augenstein, P.; Roennau, A.; Dillmann, R.; Xiong, Z. Brain inspired path planning algorithms for drones. Front. Neurorobot. 2023, 17, 1111861. [Google Scholar] [CrossRef]
- Yu, R.; Liu, Y.; Meng, Y.; Guo, Y.; Xiong, Z.; Jiang, P. Optimal Configuration of Heterogeneous Swarm for Cooperative Detection with Minimum DOP Based on Nested Cones. Drones 2024, 8, 11. [Google Scholar] [CrossRef]
- Yang, Y.; Xiong, X.; Yan, Y. UAV Formation Trajectory Planning Algorithms: A Review. Drones 2023, 7, 62. [Google Scholar] [CrossRef]
- National Academies of Sciences, Engineering, and Medicine. Counter-Unmanned Aircraft System (CUAS) Capability for Battalion-and-Below Operations: Abbreviated Version of a Restricted Report; The National Academies Press: Washington, DC, USA, 2018. [Google Scholar] [CrossRef]
- Oh, B.-S.; Lin, Z. Extraction of Global and Local m-DS features from FMCW Radar Returns for UAV Detection. IEEE Trans. Aerosp. Electron. Syst. 2020, 57, 1351–1360. [Google Scholar] [CrossRef]
- Siemiatkowska, B.; Stecz, W. A Framework for Planning and Execution of Drone Swarm Missions in a Hostile Environment. Sensors 2021, 21, 4150. [Google Scholar] [CrossRef]
- Balamurugan, G.; Valarmathi, J.; Naidu, V.P.S. Survey on UAV navigation in GPS denied environments. In Proceedings of the 2016 International Conference on Signal Processing, Communication, Power and Embedded System (SCOPES), Paralakhemundi, India, 3–5 October 2016; pp. 198–204. [Google Scholar] [CrossRef]
- Castrillo, V.U.; Manco, A.; Pascarella, D.; Gigante, G. A Review of Counter-UAS Technologies for Cooperative Defensive Teams of Drones. Drones 2022, 6, 65. [Google Scholar] [CrossRef]
- Grimal, F.; Sundaram, J. Combat Drones: Hives, Swarms, and Autonomous Action? J. Confl. Secur. Law 2018, 23, 105–135. [Google Scholar] [CrossRef]
- Zuo, M.; Xie, S.; Zhang, X.; Yang, M. Recognition of UAV Video Signal Using RF Fingerprints in the Presence of WiFi Interference. IEEE Access 2021, 9, 88844–88851. [Google Scholar] [CrossRef]
- Lee, H.; Han, S.; Byeon, J.-I.; Han, S.; Myung, R.; Joung, J.; Choi, J. CNN-Based UAV Detection and Classification Using Sensor Fusion. IEEE Access 2023, 11, 68791–68808. [Google Scholar] [CrossRef]
- Konert, A.; Balcerzak, T. Military autonomous drones (UAVs)-from fantasy to reality. Legal and Ethical implications. Transp. Res. Procedia 2021, 59, 292–299. [Google Scholar] [CrossRef]
- Merkert, R.; Bushell, J. Managing the drone revolution: A systematic literature review into the current use of airborne drones and future strategic directions for their effective control. J. Air Transp. Manag. 2020, 89, 101929. [Google Scholar] [CrossRef] [PubMed]
- Csengeri, J. Counter-drone activity as a system. Secur. Future 2019, 3, 31–34. [Google Scholar]
- Coluccia, A.; Parisi, G.; Fascista, A. Detection and Classification of Multirotor Drones in Radar Sensor Networks: A Review. Sensors 2020, 20, 4172. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Simske, S.J.; Treiblmaier, H. Drones for supply chain management and logistics: A review and research agenda. Int. J. Logist. Res. Appl. 2023, 26, 708–731. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Martins, B.O.; Michel, A.H.; Silkoset, A. Countering the Drone Threat Implications of C-UAS Technology for Norway in an EU and NATO Context; PRIO: Oslo, Norway, 2020. [Google Scholar]
- Kunertova, D. Drones have boots: Learning from Russia’s war in Ukraine. Contemp. Secur. Policy 2023, 44, 576–591. [Google Scholar] [CrossRef]
- Petrovski, A.; Radovanović, M.; Behlić, A. Application of drones with artificial intelligence for military purposes. In Proceedings of the 10th International Scientific Conference on Defensive Technologies (OTEH), Belgrade, Serbia, 13–14 October 2022. [Google Scholar]
- Lee, D.; Kim, S.; Suk, J. Formation flight of unmanned aerial vehicles using track guidance. Aerosp. Sci. Technol. 2018, 76, 412–420. [Google Scholar] [CrossRef]
- Sun, H.; Qi, J.; Wu, C.; Wang, M. Path Planning for Dense Drone Formation Based on Modified Artificial Potential Fields. In Proceedings of the 2020 39th Chinese Control Conference (CCC), Shenyang, China, 27–29 July 2020; pp. 4658–4664. [Google Scholar] [CrossRef]
- Chen, Y.; Deng, T. Leader-Follower UAV formation flight control based on feature modelling. Syst. Sci. Control Eng. 2023, 11, 2268153. [Google Scholar] [CrossRef]
- Solaiman, S.; Alsuwat, E.; Alharthi, R. Simultaneous Tracking and Recognizing Drone Targets with Millimeter-Wave Radar and Convolutional Neural Network. Appl. Syst. Innov. 2023, 6, 68. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).