Software-Driven Definition of Virtual Testbeds to Validate Emergent Network Technologies †
Abstract
:1. Introduction
2. Related Work
2.1. Background
2.2. Enabling Technologies
2.3. Synthetic Network Load Generation
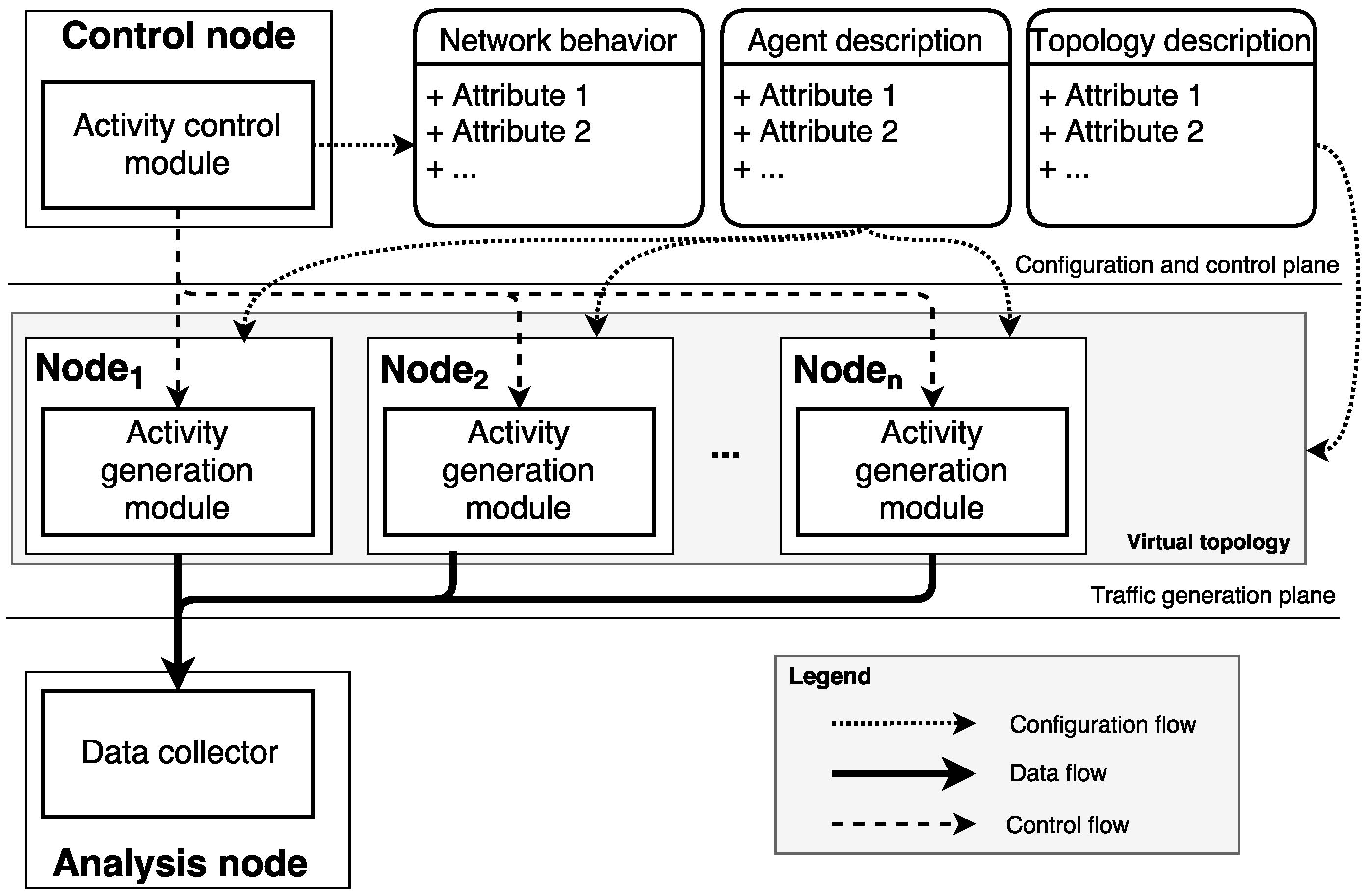
3. Formulation of the Method for the Generation of Network Activity
3.1. General Traffic-Generation Model
- A baseline for the temporal evolution of the number of active connections exists.
- A characteristic process for the creation of new connections per time unit exists and can be adjusted using its expected value.
- The distribution of the connections’ duration does not change over time.
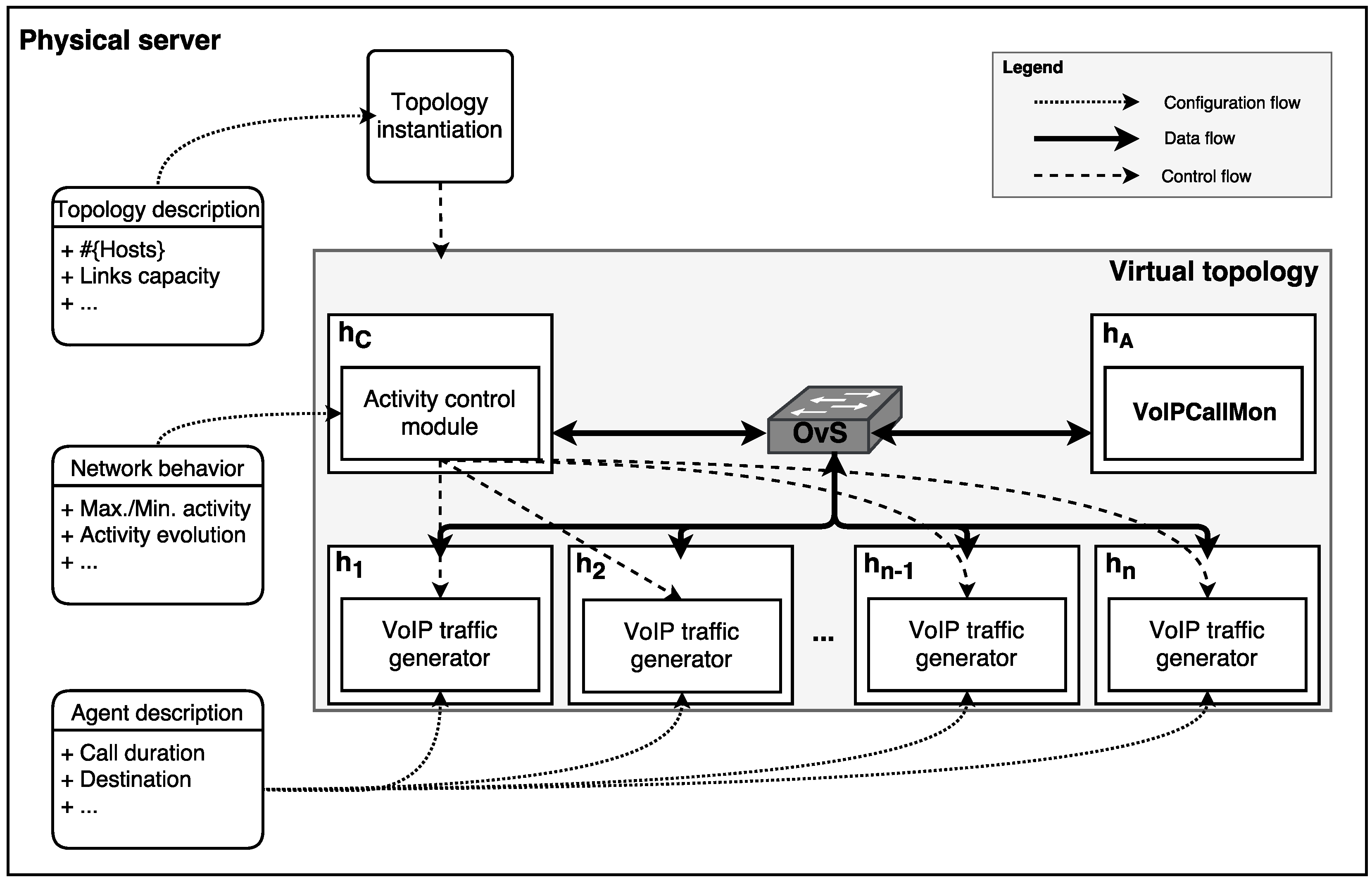
3.2. Specific Traffic-Generation Model for VoIP Devices
4. Experimental Evaluation
4.1. Methodology
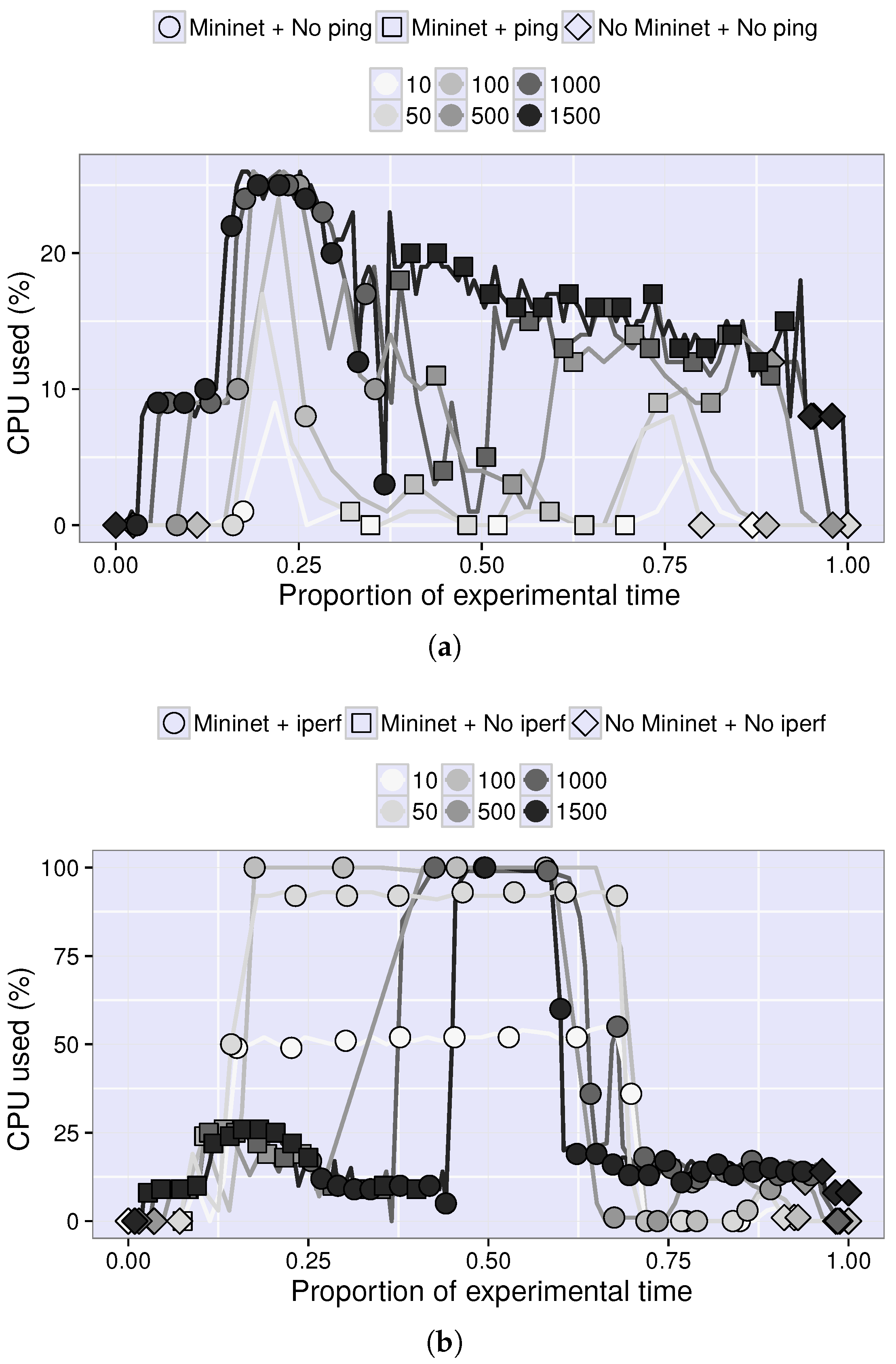
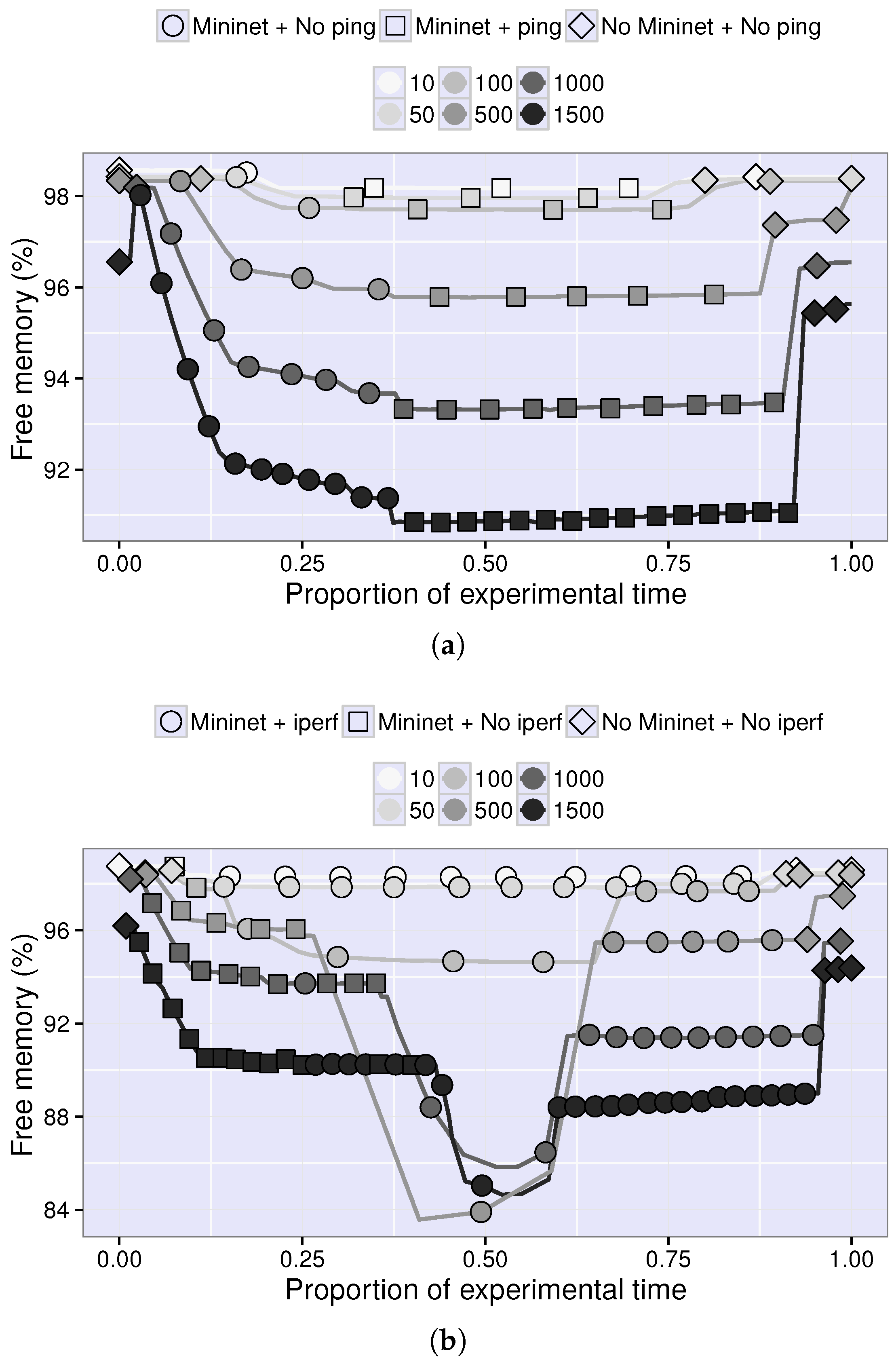
4.2. Resource Consumption
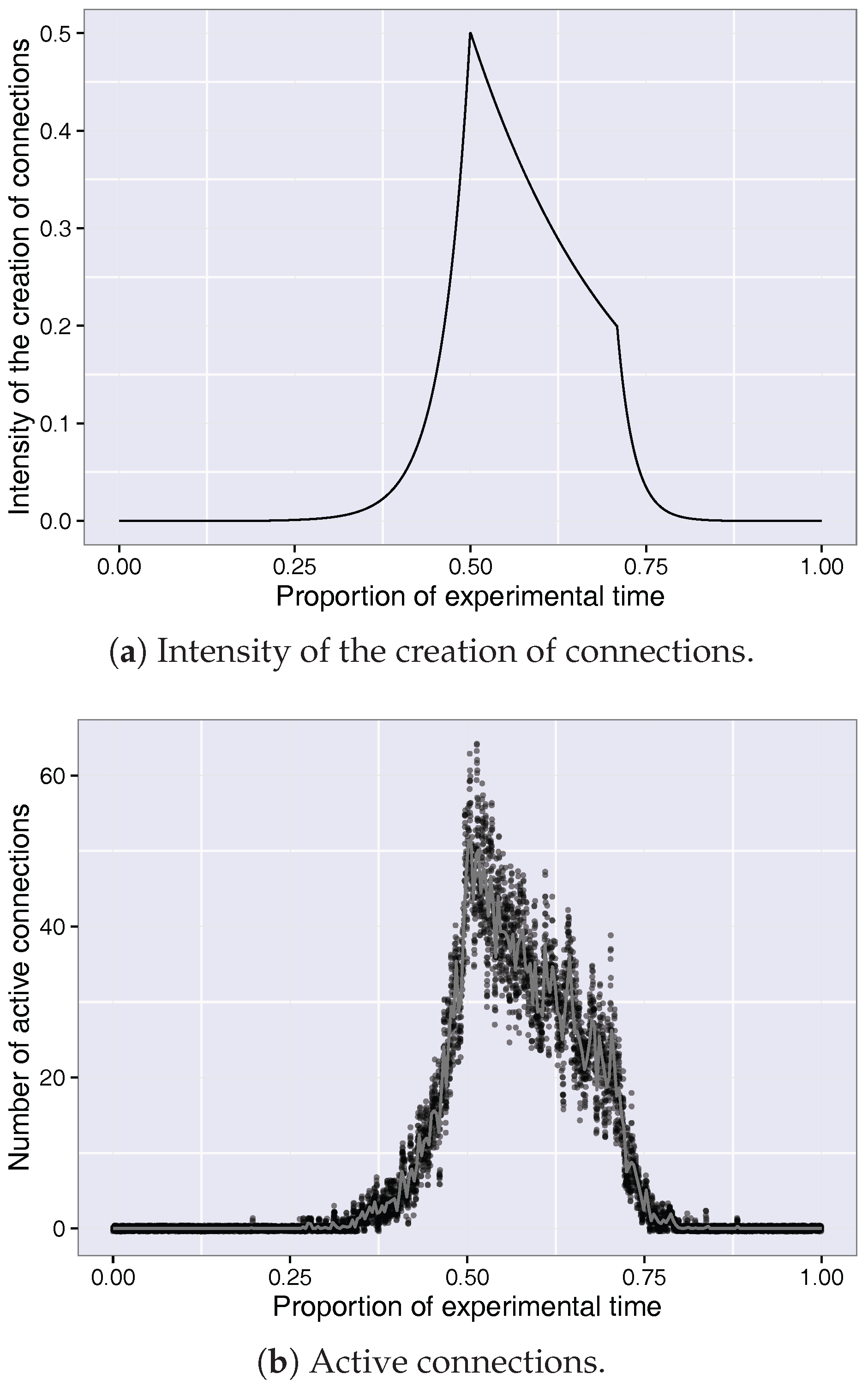
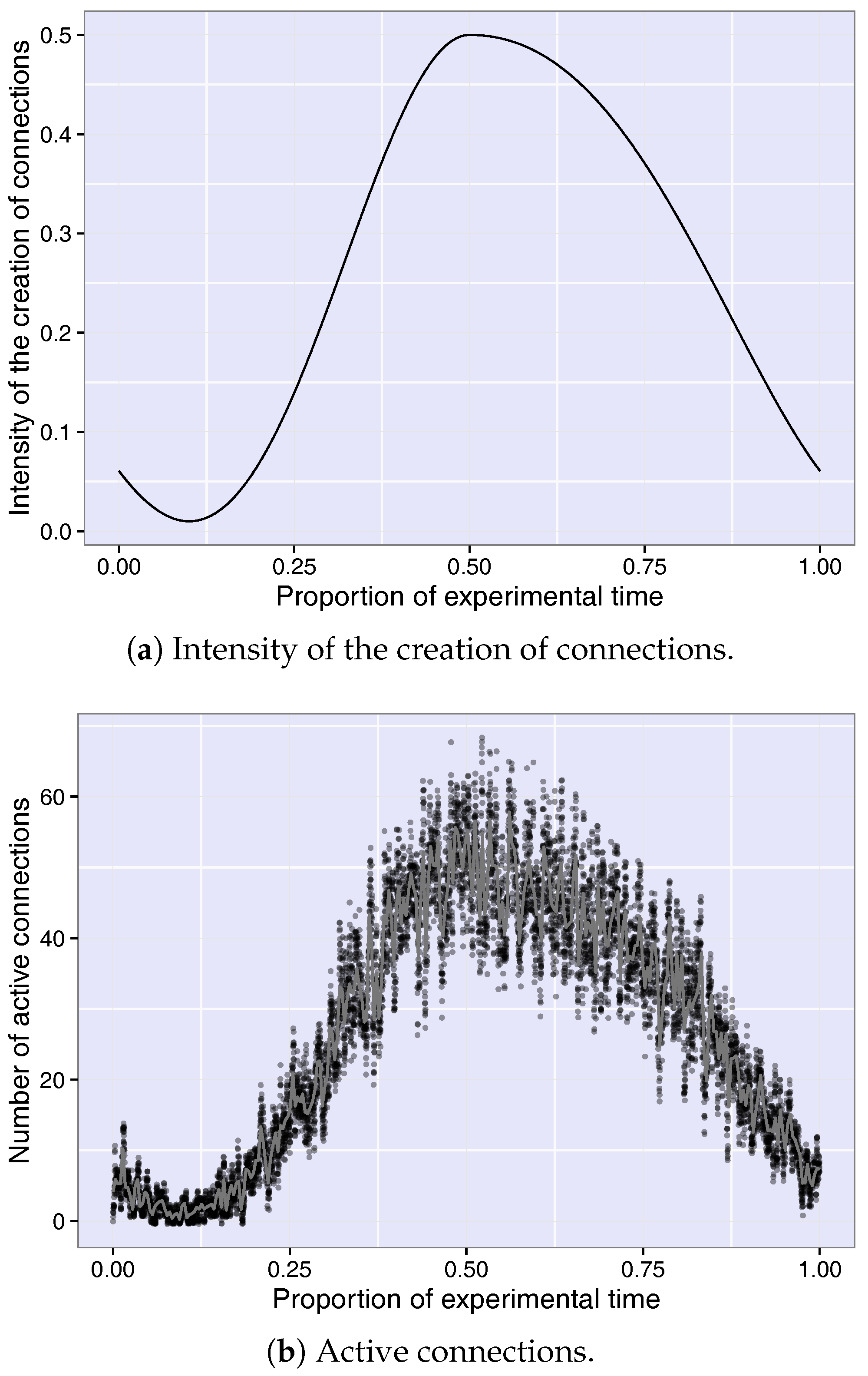
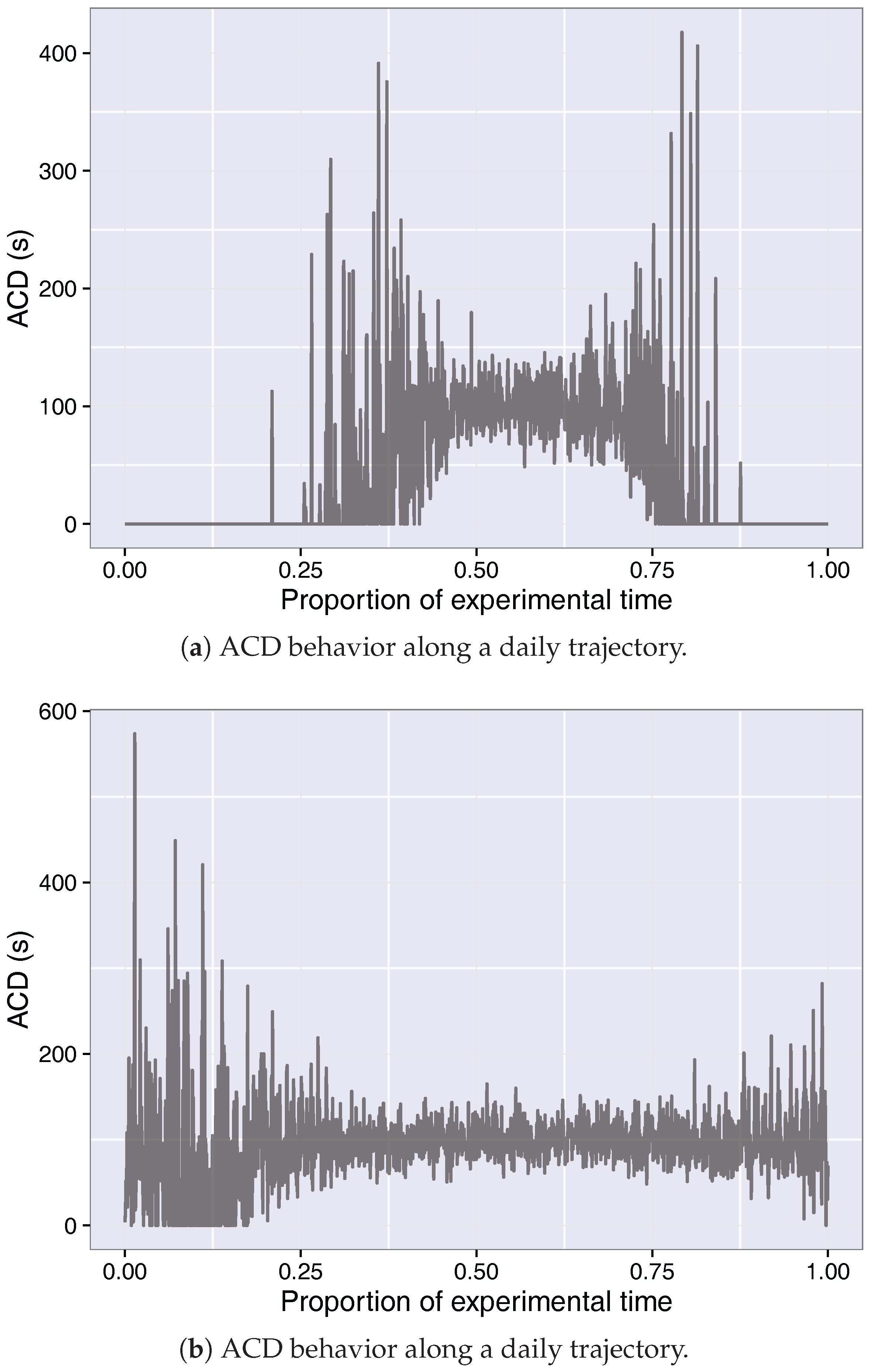
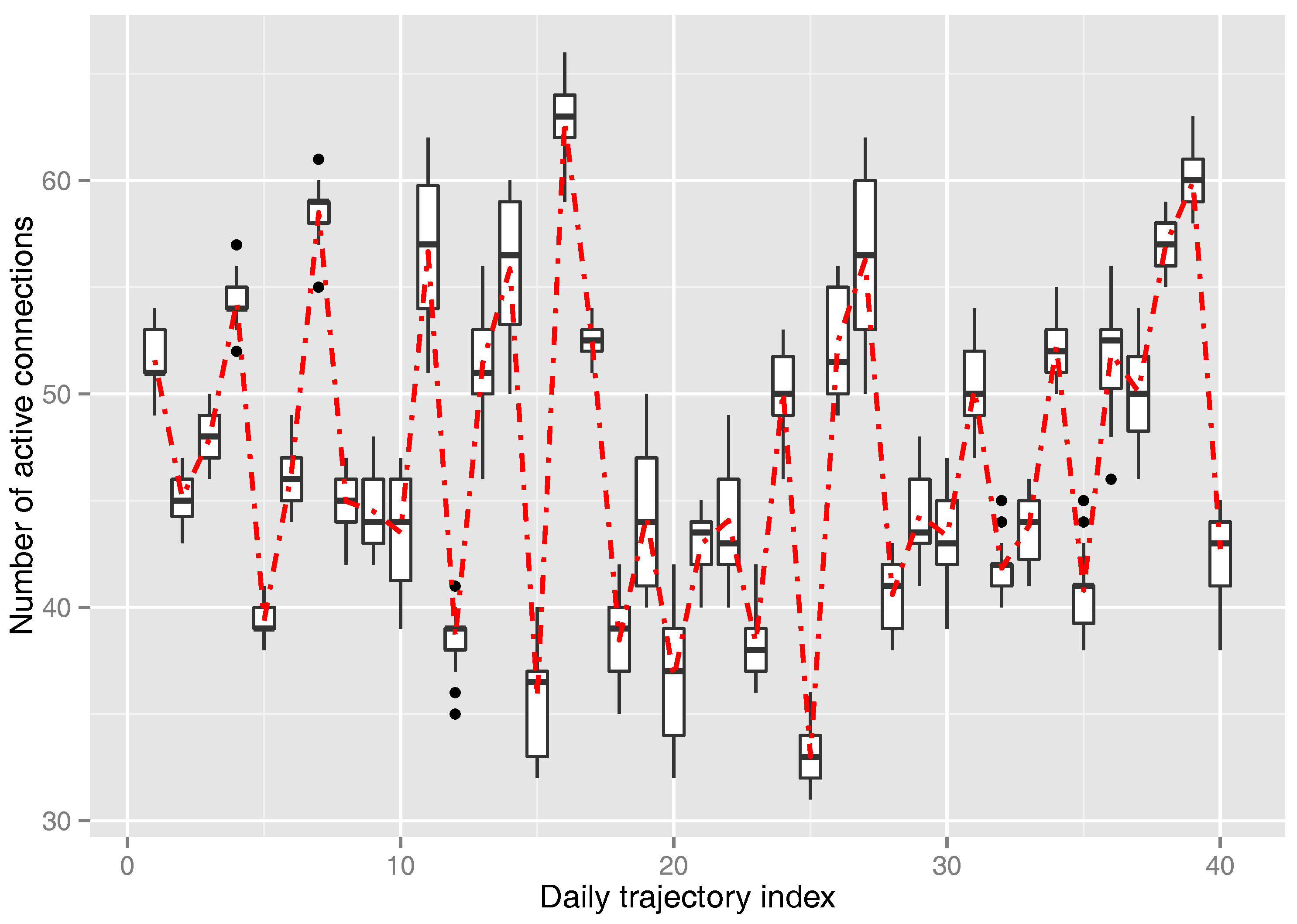
4.3. Measured Network Activity
- Activity starting time: 6 a.m.
- Activity end time: 8 p.m.
- Busy hour (H1): 12 p.m.
- Transition from mid-afternoon to close period (H2): 5 p.m.
- High activity (H1): 12 p.m.
- Low activity (H2): 3 a.m.
4.4. Qualitative Comparison with Other Methods
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Pediaditakis, D.; Rotsos, C.; Moore, A.W. Faithful Reproduction of Network Experiments. In Proceedings of the Tenth ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS ’14), Los Angeles, CA, USA, 20–21 October 2014; pp. 41–52. [Google Scholar]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A Survey on Software-Defined Networking. IEEE Commun. Surv. Tutor. 2015, 17, 27–51. [Google Scholar] [CrossRef]
- Horneber, J.; Hergenröder, A. A Survey on Testbeds and Experimentation Environments for Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2014, 16, 1820–1838. [Google Scholar] [CrossRef]
- Goel, U.; Wittie, M.P.; Claffy, K.C.; Le, A. Survey of End-to-End Mobile Network Measurement Testbeds, Tools, and Services. IEEE Commun. Surv. Tutor. 2016, 18, 105–123. [Google Scholar] [CrossRef]
- Tsai, P.W.; Piccialli, F.; Tsai, C.W.; Luo, M.Y.; Yang, C.S. Control frameworks in network emulation testbeds: A survey. J. Comput. Sci. 2017, 22, 148–161. [Google Scholar] [CrossRef]
- NFX250 Network Services Platform. Available online: https://www.juniper.net/us/en/products-services/sdn/nfx250/ (accessed on 23 February 2018).
- Arista 7500E Series. Available online: https://www.arista.com/en/products/7500-series (accessed on 23 February 2018).
- Lantz, B.; Heller, B.; McKeown, N. A network in a laptop: Rapid prototyping for Software-Defined Networks. In Proceedings of the 9th ACM SIGCOMM Workshop on Hot Topics in Networks, Monterey, CA, USA, 20–21 October 2010; ACM: New York, NY, USA, 2010; pp. 1–6. [Google Scholar]
- Yan, J.; Jin, D. VT-Mininet: Virtual-time-enabled Mininet for Scalable and Accurate Software-Define Network Emulation. In Proceedings of the 1st ACM SIGCOMM Symposium on Software Defined Networking Research (SOSR ’15), Santa Clara, CA, USA, 17–18 June 2015; pp. 1–7. [Google Scholar]
- Handigol, N.; Heller, B.; Jeyakumar, V.; Lantz, B.; McKeown, N. Reproducible Network Experiments Using Container-based Emulation. In Proceedings of the 8th International Conference on Emerging Networking Experiments and Technologies (CoNEXT ’12), Nice, France, 10–13 December 2012; pp. 253–264. [Google Scholar]
- Lantz, B.; O’Connor, B. A Mininet-based Virtual Testbed for Distributed SDN Development. SIGCOMM Comput. Commun. Rev. 2015, 45, 365–366. [Google Scholar] [CrossRef]
- Baldesi, L.; Maccari, L. NePA TesT: Network protocol and application testing toolchain for community networks. In Proceedings of the 12th Annual Conference on Wireless On-demand Network Systems and Services (WONS), Cortina d’Ampezzo, Italy, 20–22 January 2016; pp. 1–8. [Google Scholar]
- Moreno, V.; del Río, P.M.S.; Ramos, J.; Garnica, J.J.; García-Dorado, J.L. Batch to the Future: Analyzing Timestamp Accuracy of High-Performance Packet I/O Engines. IEEE Commun. Lett. 2012, 16, 1888–1891. [Google Scholar] [CrossRef]
- Myers, M.D.; Venable, J.R. A set of ethical principles for design science research in information systems. Inf. Manag. 2014, 51, 801–809. [Google Scholar] [CrossRef]
- Meeran, M.T.; Annus, P.; Alam, M.M.; Moullec, Y.L. Evaluation of VoIP QoS Performance in Wireless Mesh Networks. Information 2017, 8, 88. [Google Scholar] [CrossRef]
- Bachmeir, C.; Tabery, P.; Uzumcu, S.; Steinbach, E. A scalable virtual programmable real-time testbed for rapid multimedia service creation and evaluation. In Proceedings of the 2003 International Conference on Multimedia and Expo (ICME ’03), Baltimore, MD, USA, 6–9 July 2003; Volume 3, pp. 257–260. [Google Scholar]
- Fuertes, W.; López de Vergara, J.E. An emulation of VoD services using virtual network environments. Electron. Commun. EASST 2009, 17. [Google Scholar] [CrossRef]
- Han, B.; Gopalakrishnan, V.; Ji, L.; Lee, S. Network function virtualization: Challenges and opportunities for innovations. IEEE Commun. Mag. 2015, 53, 90–97. [Google Scholar] [CrossRef]
- Mijumbi, R.; Serrat, J.; Gorricho, J.L.; Bouten, N.; Turck, F.D.; Boutaba, R. Network Function Virtualization: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 236–262. [Google Scholar] [CrossRef]
- Peach, S.; Irwin, B.; van Heerden, R. An overview of linux container based network emulation. In Proceedings of the European Conference on Information Warfare and Security (ECCWS), Munich, Germany, 7–8 July 2016; pp. 253–259. [Google Scholar]
- Raza, M.; Chowdhury, S.; Robertson, W. SDN based emulation of an academic networking testbed. In Proceedings of the 2016 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Vancouver, BC, Canada, 15–18 May 2016; pp. 1–6. [Google Scholar]
- Rong, R.; Liu, J. Distributed mininet with symbiosis. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Fontes, R.D.R.; Mahfoudi, M.; Dabbous, W.; Turletti, T.; Rothenberg, C. How Far Can We Go? Towards Realistic Software-Defined Wireless Networking Experiments. Comput. J. 2017, 60, 1458–1471. [Google Scholar] [CrossRef]
- Lentisco, C.M.; Aguayo, M.; Bellido, L.; Pastor, E.; De-Antonio-Monte, D.; Bolívar, A.G. A virtualized platform for analyzing LTE broadcast services. In Proceedings of the 2015 European Conference on Networks and Communications (EuCNC), Paris, France, 29 June–2 July 2015; pp. 512–516. [Google Scholar]
- Moyano, R.F.; Cambronero, D.F.; Triana, L.B. A user-centric SDN management architecture for NFV-based residential networks. Comput. Stand. Interfaces 2017, 54, 279–292. [Google Scholar] [CrossRef]
- Jimenez, J.M.; Martínez, J.O.R.; Rego, A.; Dilendra, A.; Lloret, J. Study of multimedia delivery over software defined networks. Netw. Protoc. Algorithms 2015, 7, 37–62. [Google Scholar] [CrossRef]
- Weigle, M.C.; Adurthi, P.; Hernández-Campos, F.; Jeffay, K.; Smith, F.D. Tmix: A Tool for Generating Realistic TCP Application Workloads in Ns-2. SIGCOMM Comput. Commun. Rev. 2006, 36, 65–76. [Google Scholar] [CrossRef]
- Botta, A.; Dainotti, A.; Pescapé, A. A tool for the generation of realistic network workload for emerging networking scenarios. Comput. Netw. 2012, 56, 3531–3547. [Google Scholar] [CrossRef]
- Rygielski, P.; Simko, V.; Sittner, F.; Aschenbrenner, D.; Kounev, S.; Schilling, K. Automated Extraction of Network Traffic Models Suitable for Performance Simulation. In Proceedings of the 7th ACM/SPEC on International Conference on Performance Engineering (ICPE ’16), Delft, The Netherlands, 14 March 2016; pp. 27–35. [Google Scholar]
- Smekal, D.; Hajny, J.; Martinasek, Z. Packet generators on field programmable gate array platform. In Proceedings of the 40th International Conference on Telecommunications and Signal Processing (TSP), Barcelona, Spain, 5–7 July 2017; pp. 97–100. [Google Scholar]
- Muelas, D.; López de Vergara, J.E.; Berrendero, J.R.; Ramos, J.; Aracil, J. Facing Network Management Challenges with Functional Data Analysis: Techniques & Opportunities. Mob. Netw. Appl. 2017, 22, 1124–1136. [Google Scholar]
- Muelas, D.; García-Dorado, J.; López de Vergara, J.E.; Aracil, J. Application of functional feature extraction to the compression of network time series. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 592–595. [Google Scholar]
- Mata, F.; García-Dorado, J.L.; Aracil, J. Detection of traffic changes in large-scale backbone networks: The case of the Spanish academic network. Comput. Netw. 2012, 56, 686–702. [Google Scholar] [CrossRef]
- Little, J.D. Little’s Law as Viewed on Its 50th Anniversary. Oper. Res. 2011, 59, 536–549. [Google Scholar] [CrossRef]
- Rosenberg, J.; Schulzrinne, H.; Camarillo, G.; Johnston, A.; Peterson, J.; Sparks, R.; Handley, M.; Schooler, E. RFC 3261: SIP: Session Initiation Protocol. Available online: https://www.rfc-editor.org/rfc/rfc3261.txt (accessed on 23 February 2018).
- Cisco Systems Inc. Cisco Unified Communications Manager System Guide; Chapter Understanding IP Telephony Protocols; Cisco Systems, Inc.: San Jose, CA, USA, 2004. [Google Scholar]
- Jacobson, V.; Frederick, R.; Casner, S.; Schulzrinne, H. RFC 3550: RTP: A Transport Protocol for Real-Time Applications. Available online: https://tools.ietf.org/html/rfc3550 (accessed on 23 February 2018).
- ITU-T. G.711: Pulse Code Modulation (PCM) of Voice Frequencies; International Telecommunication Union: Geneva, Switzerland, 1988. [Google Scholar]
- García-Dorado, J.L.; Santiago del Río, P.M.; Ramos, J.; Muelas, D.; Moreno, V.; López de Vergara, J.E.; Aracil, J. Low-cost and high-performance: VoIP monitoring and full-data retention at multi-Gb/s rates using commodity hardware. Int. J. Netw. Manag. 2014, 24, 181–199. [Google Scholar] [CrossRef]
- Muelas, D.; López de Vergara, J.E.; Ramos, J.; García-Dorado, J.L.; Aracil, J. On the impact of TCP segmentation: Experience in VoIP monitoring. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 708–713. [Google Scholar]
| Ethical Issue | Research Design Aspects |
|---|---|
| Privacy | Boundaries to preserve anonymity of underlying individuals and definition of safeguards and actor(s) in charge of this protection. |
| Accuracy | Guarantees related to the gathered information and definition of who is responsible for these guarantees. |
| Property | Owner(s) of both artifacts and collected information. |
| Access | Definition of authorizations and conditions for actor(s) making use of gathered information and designation of responsibilities related to this use. |
| Virtualization | Key Features | Platforms |
|---|---|---|
| Virtual Machines (VMs) |
|
|
| Containers |
|
|
| Namespaces |
|
|
| Capabilities | Risks | Expenditures | ||||
|---|---|---|---|---|---|---|
| Approach | Realistic Behavior | Fully Customizable | Network Traffic Available | Risk of Critical Failure | Light Ethical Constraints | Cost |
| Operational network | ✓ | ✗ | ✓ | High | ✗ | Low |
| Real traffic traces | ✓ | ✗ | ✓ | Low | ✗ | Low |
| Hardware testbed | ✗ | - | - | None | ✓ | High |
| Network simulation | - | ✓ | ✗ | None | ✓ | Low |
| Our proposal | ✓ | ✓ | ✓ | None | ✓ | Low |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Muelas, D.; Ramos, J.; López de Vergara, J.E. Software-Driven Definition of Virtual Testbeds to Validate Emergent Network Technologies. Information 2018, 9, 45. https://doi.org/10.3390/info9020045
Muelas D, Ramos J, López de Vergara JE. Software-Driven Definition of Virtual Testbeds to Validate Emergent Network Technologies. Information. 2018; 9(2):45. https://doi.org/10.3390/info9020045
Chicago/Turabian StyleMuelas, David, Javier Ramos, and Jorge E. López de Vergara. 2018. "Software-Driven Definition of Virtual Testbeds to Validate Emergent Network Technologies" Information 9, no. 2: 45. https://doi.org/10.3390/info9020045
APA StyleMuelas, D., Ramos, J., & López de Vergara, J. E. (2018). Software-Driven Definition of Virtual Testbeds to Validate Emergent Network Technologies. Information, 9(2), 45. https://doi.org/10.3390/info9020045





