An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association in Vehicular Ad Hoc Networks
Abstract
:1. Introduction
2. Related Works
3. An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association
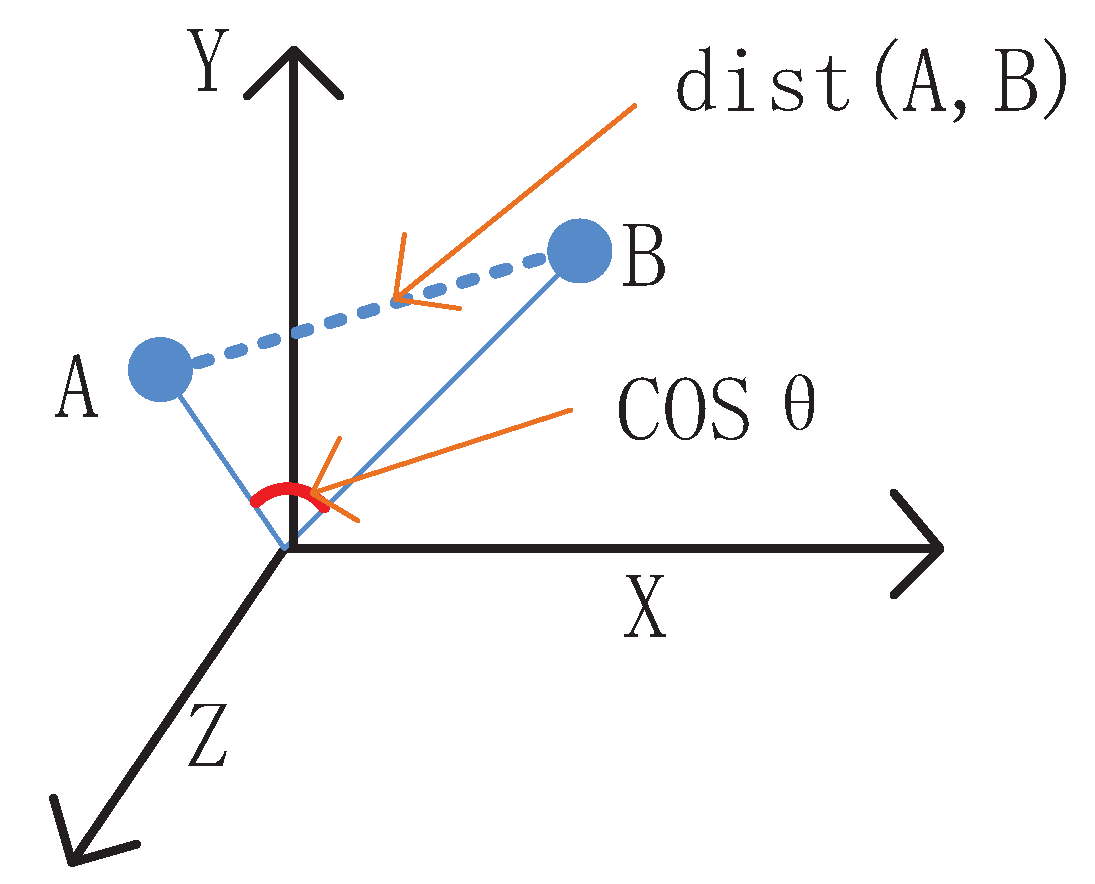
3.1. Definition and Analysis
- Information efficient region phase.
- Information efficient region boundary phase.
- EM (Ev, Es, Ec, Er, , Ert) represents exchange information, which means that the replica information is carried and can spread in a certain range.
- HM (Request) refers to the response information, which contains the response information and can spread in a certain range.
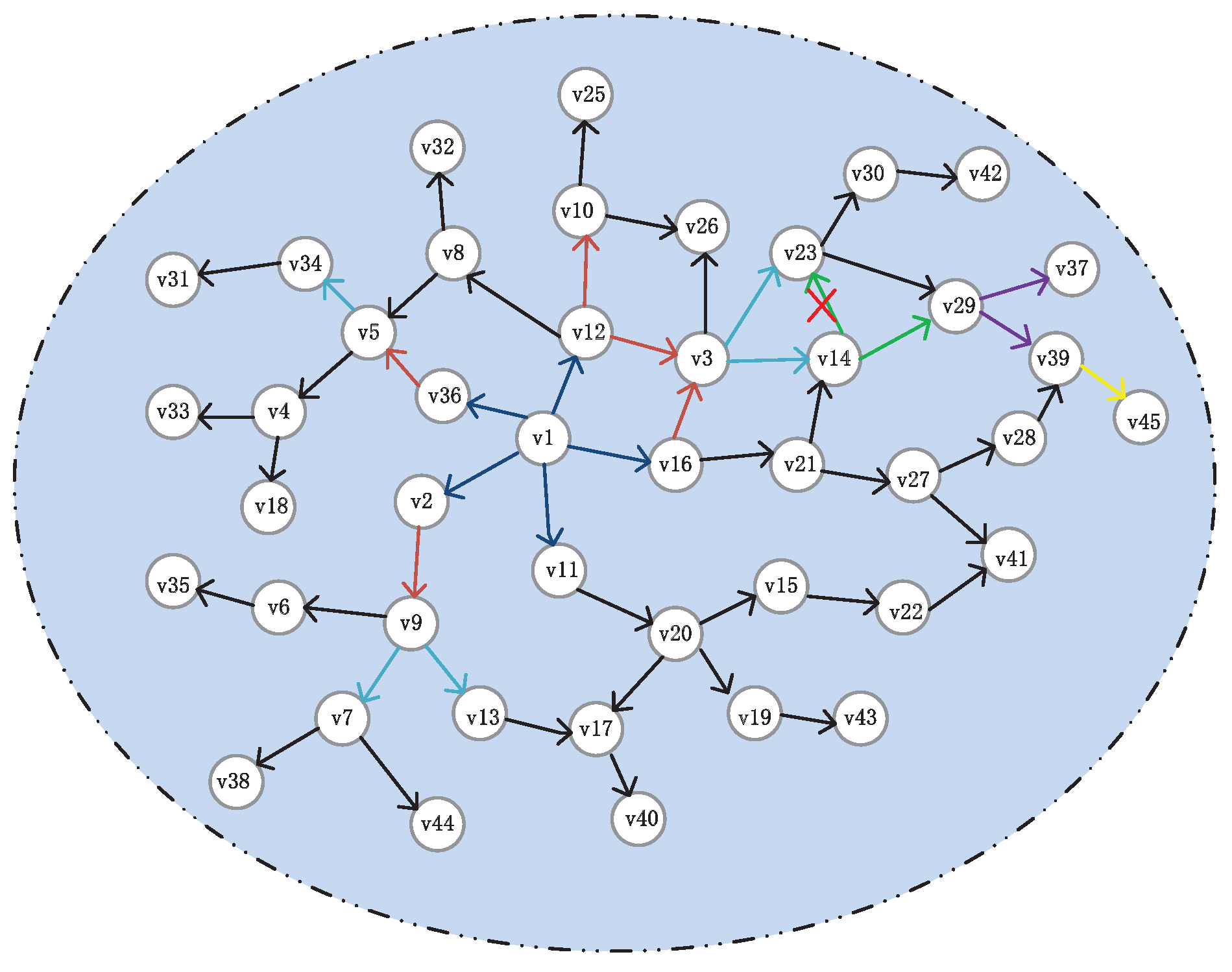
3.2. Node Traversal Process
3.3. The Algorithm Design of OVMA
- A graph G(V, E), a source node i, initial state: = = Q;
- Accessing adjacent nodes of i and calculating the data transfer probability, > ;
- If a node s cannot be found, > , reduce the value of > ( > );
- Add in , (j,s) ∈ ;
- Accessing adjacent nodes of j and s and calculating the data transfer probability;
- If > , the algorithm is unable to execute, because ;
- Add the data delivery path in Er to calculate adjacent node affinity, = , update Ec table.
- If node i and node j are located in information efficient region boundary, broadcast the EM information and calculate the angle between A and B: ;
- Feedback HM information to determine whether or not the EM information is exchanged.
- Update EM info: tabun = null, Er = null, Ec: = = Q
| Algorithm 1 Information efficient region phase |
| Input: A graph G(V, E), a source node S, a destination node D; Output: optimal path and nodes association degree;
|
| Algorithm 2 Information efficient region boundary phase |
|
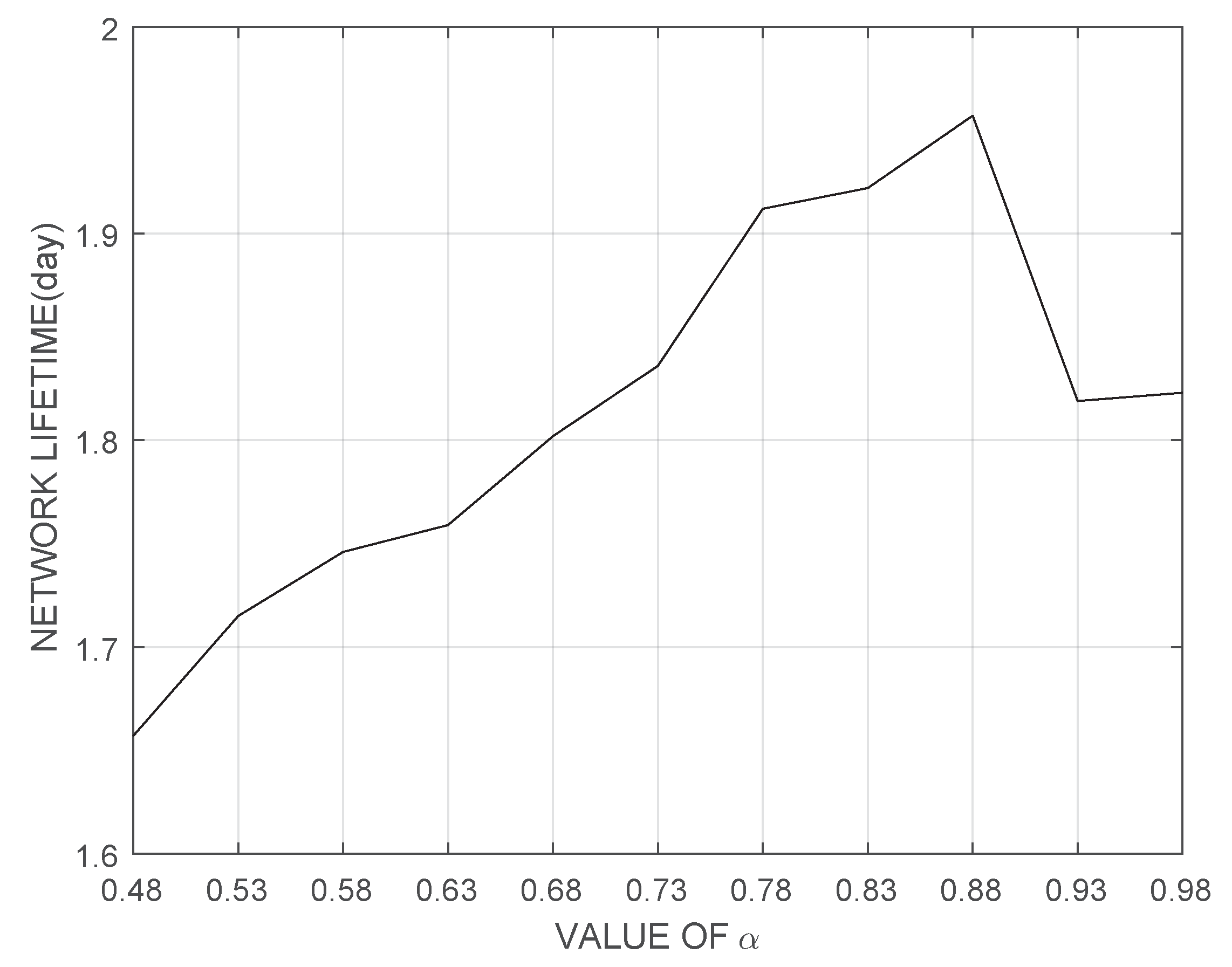
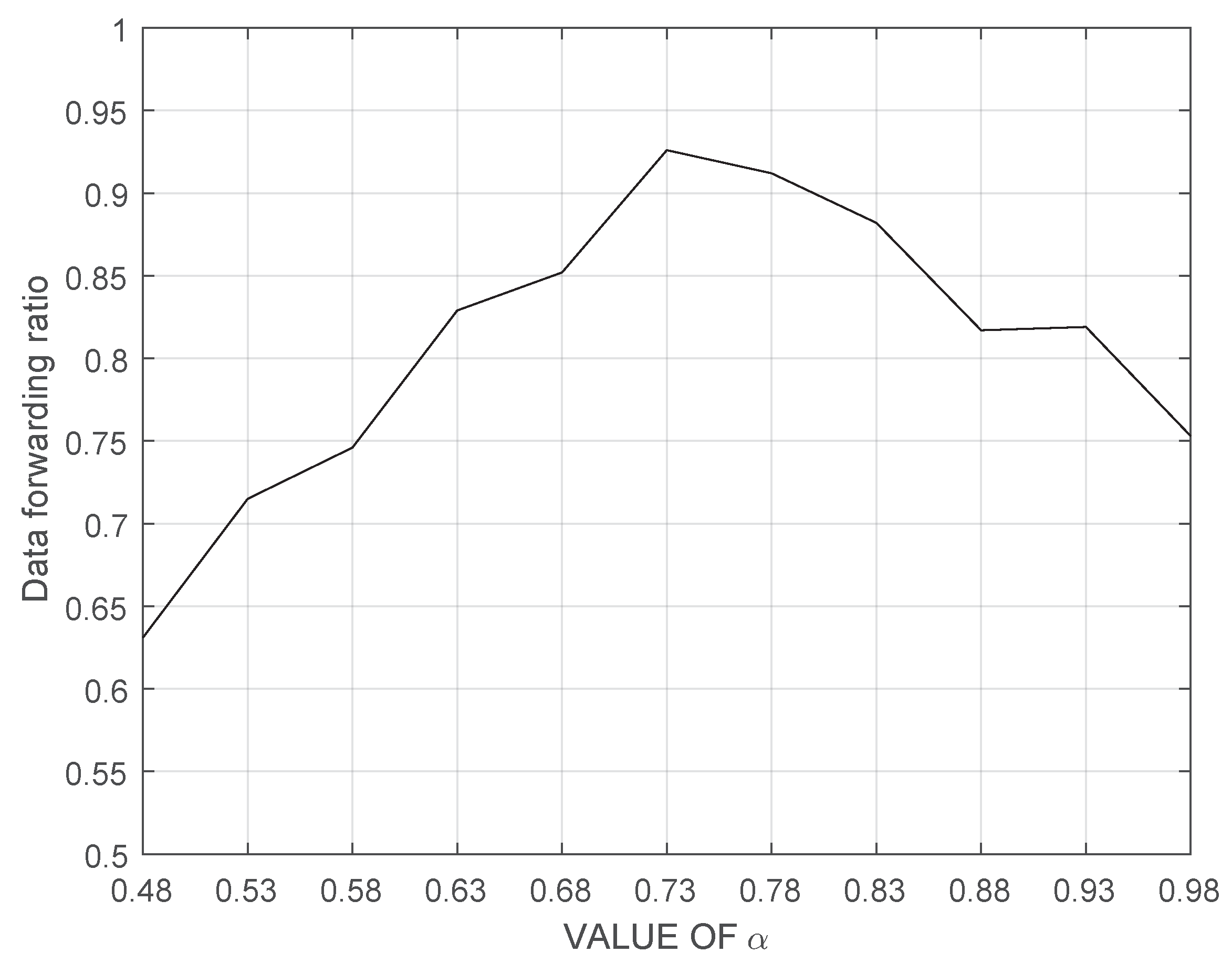
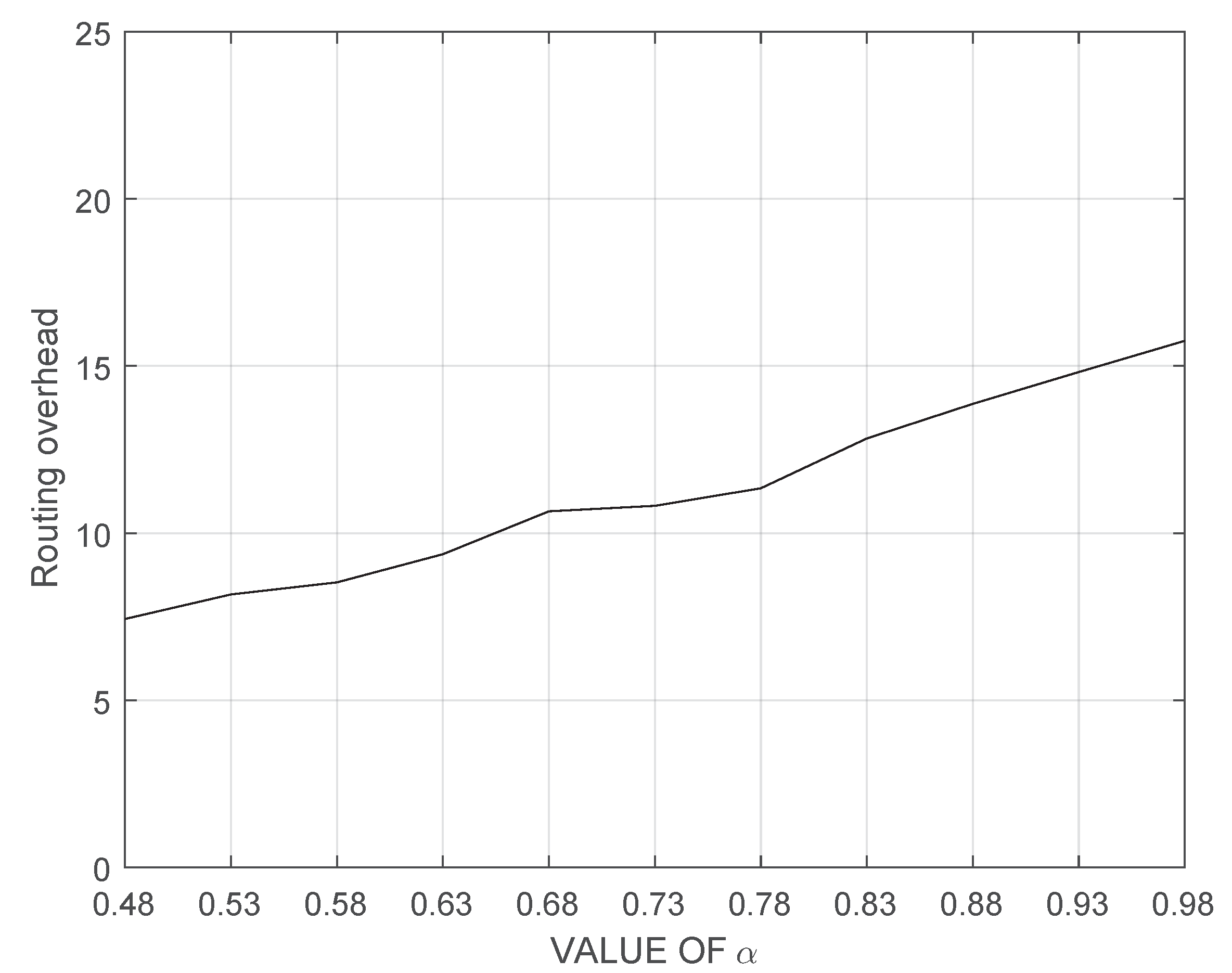
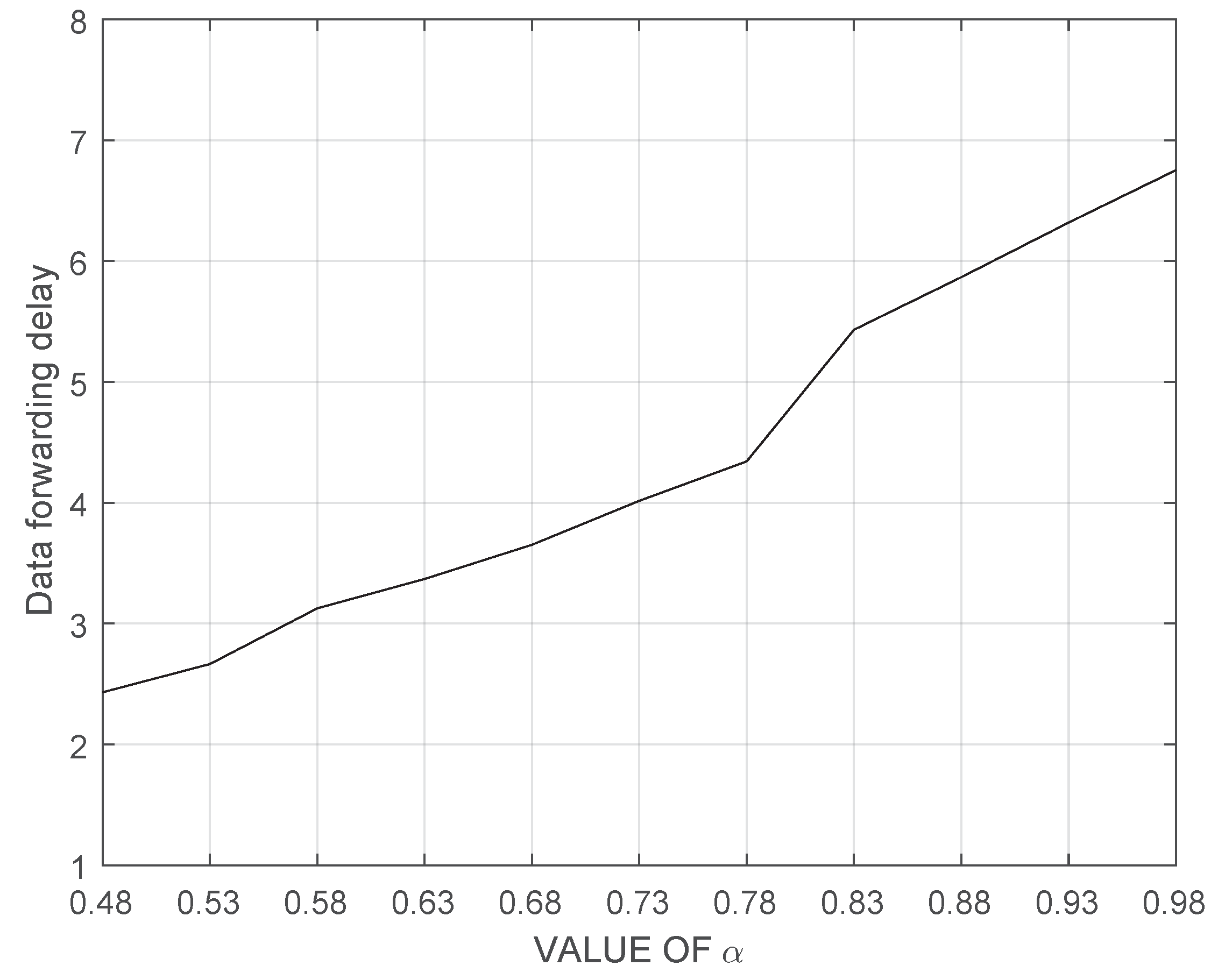
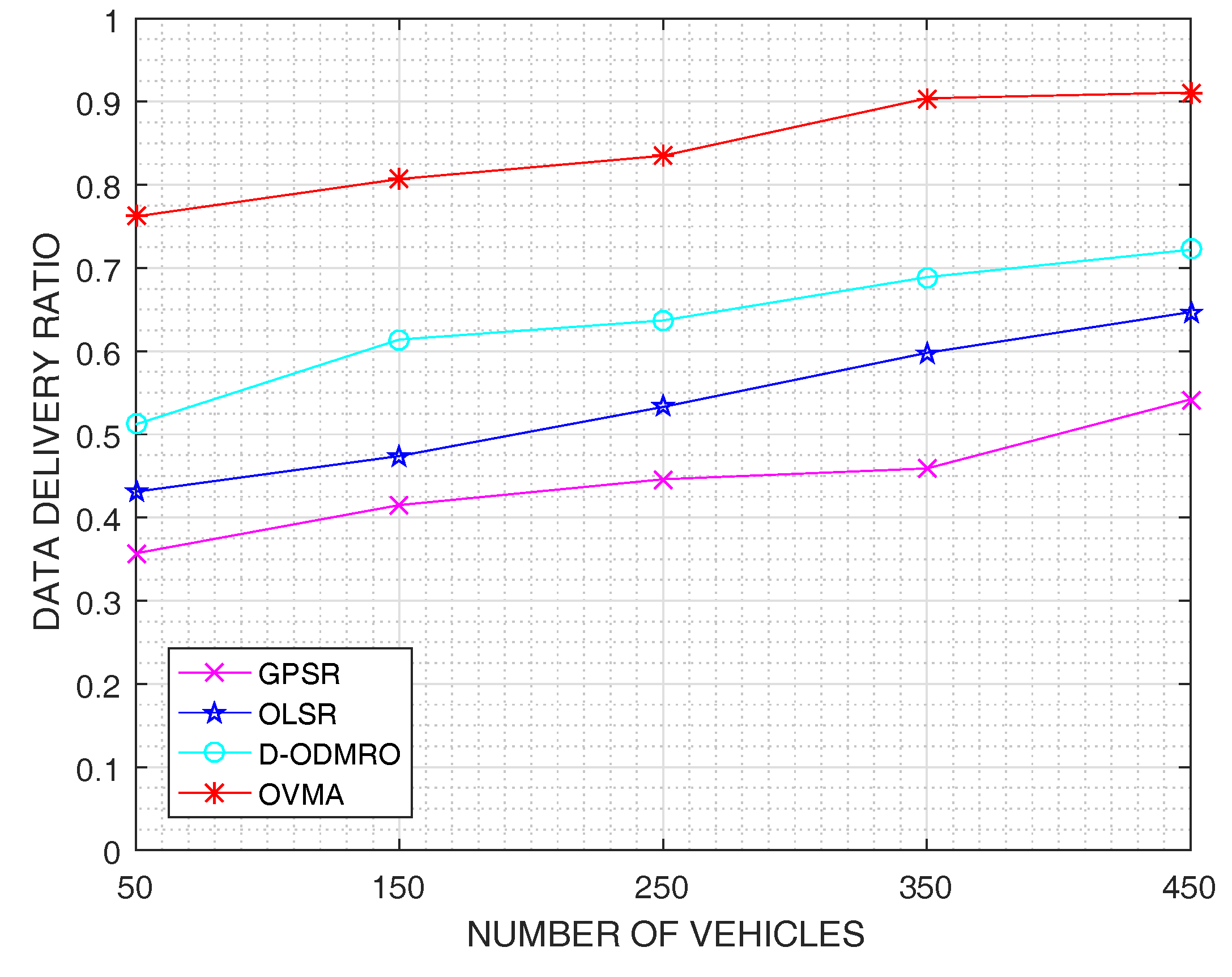
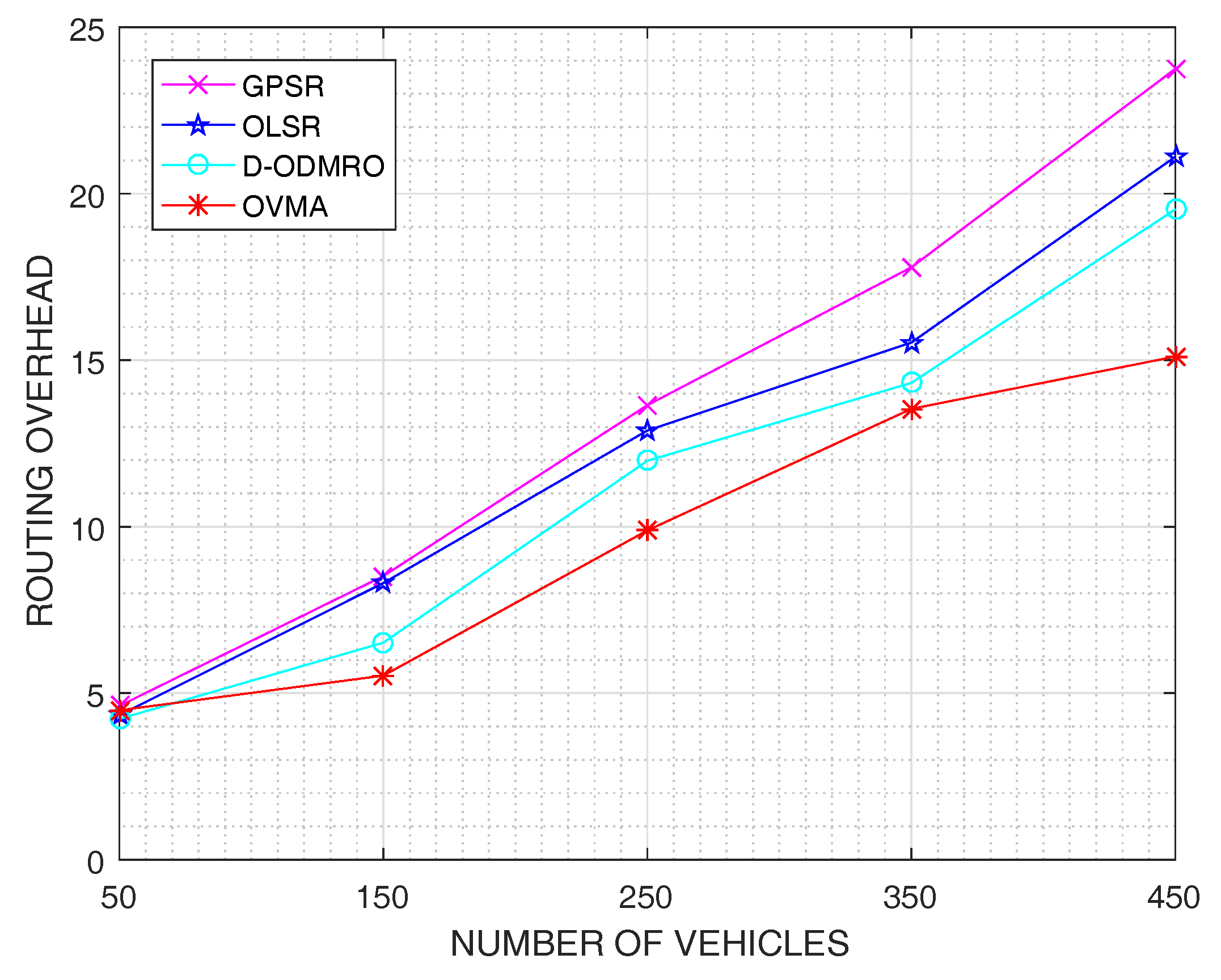
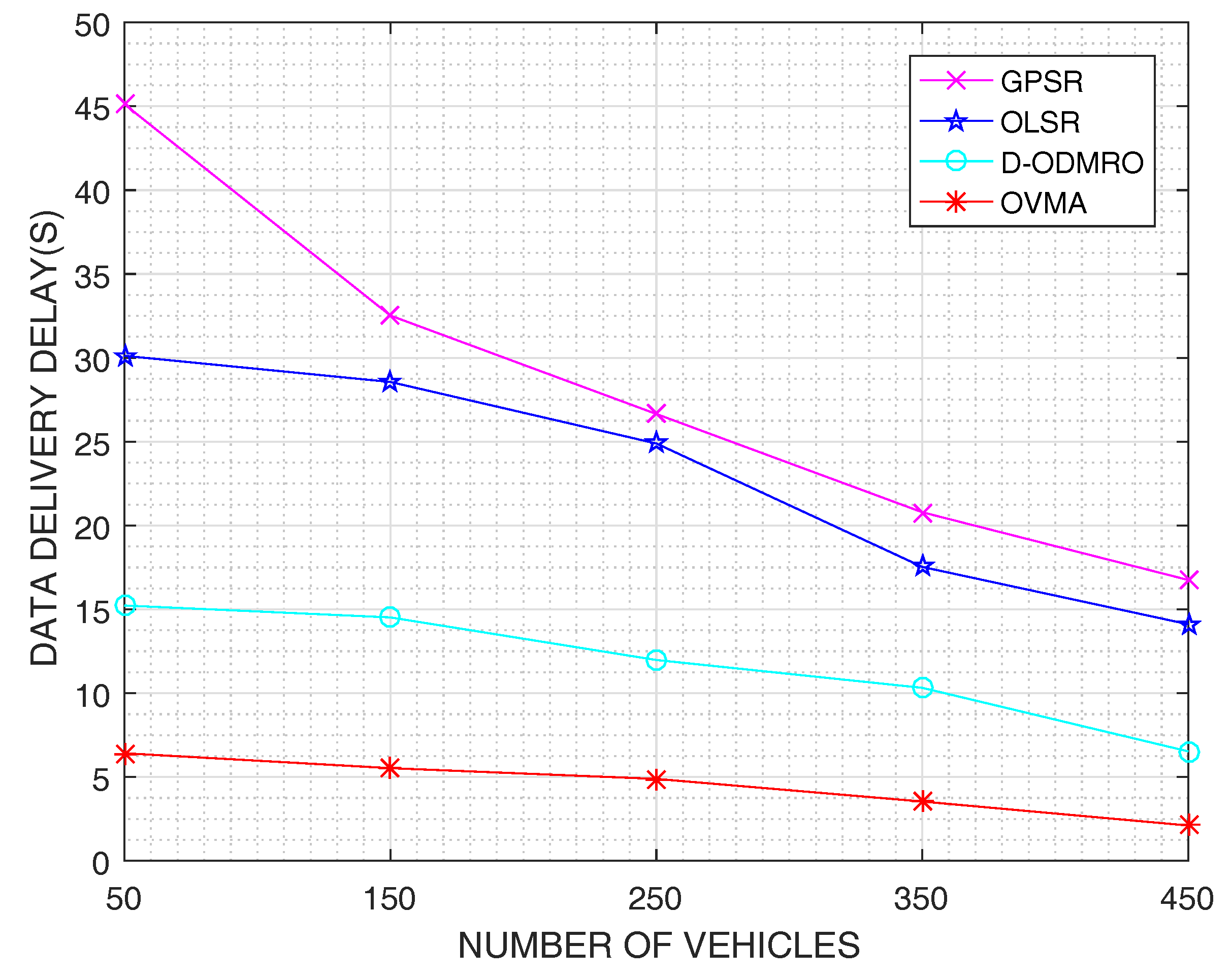
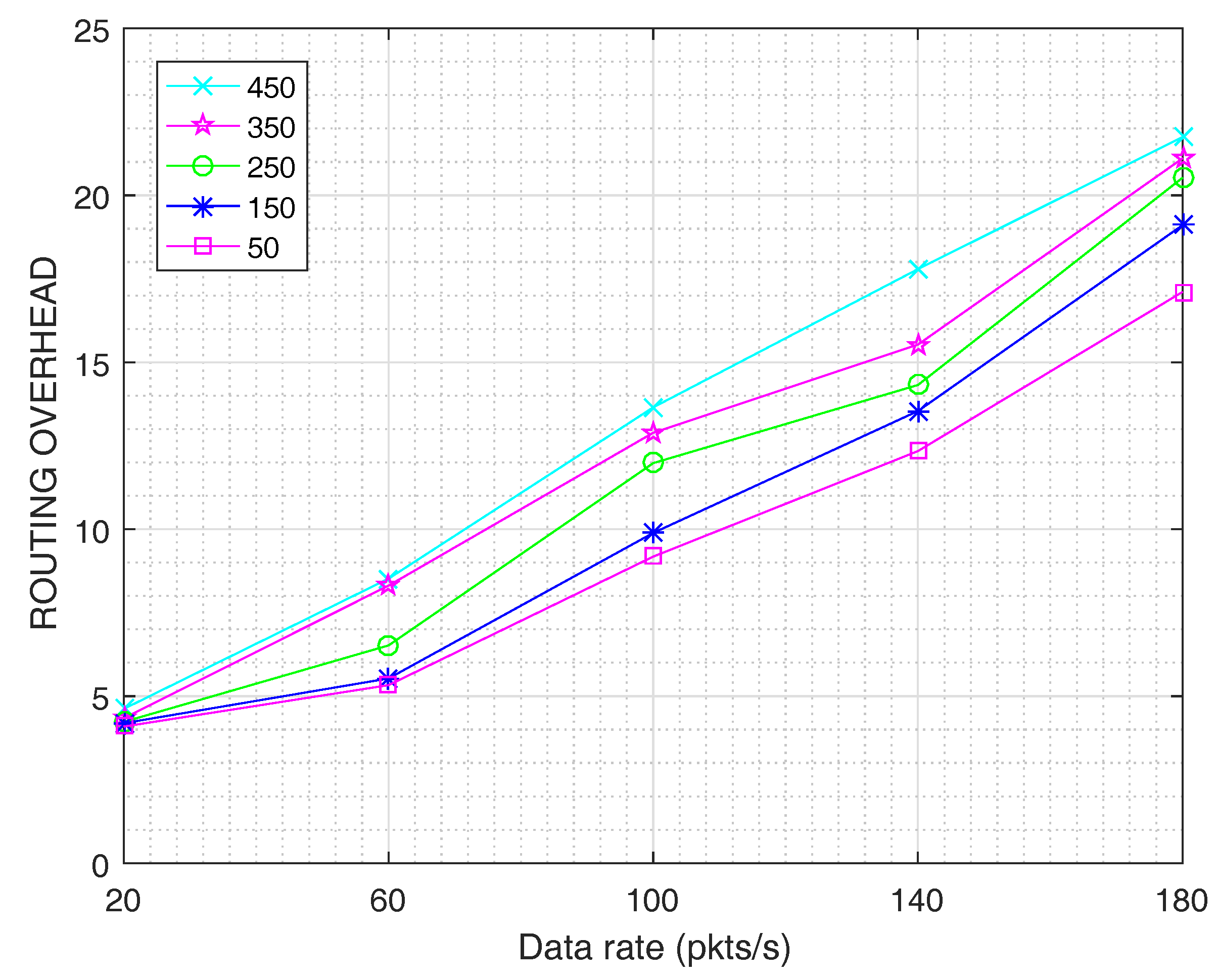
4. Performance Evaluation
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| DSRC | Dedicated short range communication |
| WAVE | Wireless access in a vehicular environment |
| GPRS | General Packet Radio Service |
| EDGE | Enhanced Data Rate for GSM Evolution |
| LTE | Long Term Evolution |
| NEMO | Network mobility |
| VADD | Vehicle-Assisted Data Delivery |
| MDDV | Mobility-centric data dissemination algorithm for vehicular networks |
| DSDV | Destination-Sequenced Distance-Vector Routing |
| AODV | Ad hoc On-demand Distance Vector Routing |
| OLSR | Optimized Link State Routing |
| DSR | Dynamic Source Routing |
| MAODV | Muticast ad hoc ondemand vetor |
| MAV-AODV | Multicast with ant colony optimization for VANETs based on MAODV protocol |
| M-AODV+ | An extension of AODV+ routing protocol for supporting vehicle-to-vehicle communication |
| MAODV | Multicast ad hoc on-demand distance vector protocol |
| MAR-DYMO | Mobility-aware Ant Colony Optimization Routing DYMO |
| DCMP | Distributed Cycle Minimization Protocol |
| GPSR | Greedy perimeter stateless routing |
| D-ODMRO | destination driven on demand multicast routing protocol |
| CBR | Constant bitrate |
| GPS | Global Positioning System |
| EM | Exchange information |
| HM | Response information |
References
- Wu, J.; Chen, Z. Human Activity Optimal Cooperation Objects Selection Routing Scheme in Opportunistic Networks Communication. Wirel. Person. Commun. 2017, 95, 3357–3375. [Google Scholar] [CrossRef]
- Barros, J. How to Build Vehicular Networks in the Real World. In Proceedings of the ACM International Symposium on Mobile Ad Hoc Networking and Computing, Philadelphia, PA, USA, 11–14 August 2014; pp. 123–124. [Google Scholar]
- Sharef, B.T.; Alsaqour, R.A.; Ismail, M. Vehicular communication ad hoc routing protocols: A survey. J. Netw. Comput. Appl. 2014, 40, 363–396. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Bawa, S. A systematic review on routing protocols for Vehicular Ad Hoc Networks. Veh. Commun. 2014, 1, 33–52. [Google Scholar] [CrossRef]
- Kim, T.; Kim, I.H.; Sun, Y.; Jin, Z. Physical Layer and Medium Access Control Design in Energy Efficient Sensor Networks: An Overview. IEEE Trans. Ind. Inf. 2015, 11, 2–15. [Google Scholar]
- Cao, Y.F.; Cheung, S.W.; Yuk, T.I. A Multiband Slot Antenna for GPS/WiMAX/WLAN Systems. IEEE Trans. Antennas Propag. 2015, 63, 952–958. [Google Scholar] [CrossRef]
- Zhang, Z.; Boukerche, A.; Pazzi, R. A Novel Multi-Hop Clustering Scheme for Vehicular Ad-Hoc Networks. In Proceedings of the Mobiwac’11 ACM International Workshop on Mobility Management and Wireless Access, Miami, FL, USA, 31 October–4 November 2011; pp. 19–26. [Google Scholar]
- Zhao, J.; Cao, G. VADD: Vehicle-Assisted Data Delivery in Vehicular Ad Hoc, Networks. IEEE Trans. Veh. Technol. 2006, 57, 1910–1922. [Google Scholar] [CrossRef]
- Yang, X.; Sun, Z.; Miao, Y.; Wang, N.; Kang, S.; Wang, Y.; Yang, Y. Performance Optimisation for DSDV in VANETs. In Proceedings of the Uksim-Amss International Conference on Modelling and Simulation, Cambridge, UK, 25–27 March 2016. [Google Scholar]
- Abbas, N.I.; Ilkan, M.; Ozen, E. Fuzzy approach to improving route stability of the AODV routing protocol. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 1–11. [Google Scholar] [CrossRef]
- Toutouh, J.; Garcia-Nieto, J.; Alba, E. Intelligent OLSR Routing Protocol Optimization for VANETs. IEEE Trans. Veh. Technol. 2012, 61, 1884–1894. [Google Scholar] [CrossRef]
- Johnson, D.B. The Dynamic Source Routing Protocol for Mobile Ad Hoc Networking (DSR). Internet-Draft, draft-ietf-manet-dsr-09.txt. 2003. [Google Scholar]
- Souza, A.B.; Celestino, J.; Xavier, F.A.; Oliveira, F.D.; Patel, A.; Latifi, M. Stable Multicast Trees Based on Ant Colony Optimization for Vehicular Ad Hoc Networks. In Proceedings of the 2013 International Conference on Information Networking (ICOIN), Bangkok, Thailand, 28–30 January 2013; pp. 101–106. [Google Scholar]
- Royer, E.M.; Perkins, C.E. Multicast Operation of the ad-hoc on-Demand Distance Vector Routing Protocol. In Proceedings of the 5th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Seattle, Washington, DC, USA, 15–19 August 2001; pp. 207–218. [Google Scholar]
- Wantoro, J.; Mustika, I.W. M-AODV+: An Extension of AODV+ Routing Protocol for Supporting Vehicle-to-Vehicle Communication in Vehicular ad hoc Networks. In Proceedings of the IEEE International Conference on Communication, Networks and Satellite, Jakarta, Indonesia, 4–5 November 2014; pp. 39–44. [Google Scholar]
- Correia, S.L.O.B.; Celestino, J.; Cherkaoui, O. Mobility-Aware Ant Colony Optimization Routing for Vehicular ad hoc Networks. In Proceedings of the Wireless Communications and Networking Conference, Cancun, Quintana Roo, Mexico, 28–31 March 2011; pp. 1125–1130. [Google Scholar]
- Billington, J.; Yuan, C. On Modelling and Analysing the Dynamic MANET On-Demand (DYMO) Routing Protocol. In Transactions on Petri Nets and Other Models of Concurrency III; Springer: Berlin, Germany, 2009. [Google Scholar]
- Chen, X.; Zhong, Q.; Liu, D. An Improved MAODV Protocol Based on Mobility Prediction and Self-Pruning Flooding. In Proceedings of the WRI International Conference on Communications and Mobile Computing, Yunnan, China, 6–8 January 2009; pp. 127–131. [Google Scholar]
- Menouar, H.; Lenardi, M.; Filali, F. Movement Prediction-Based Routing (MOPR) Concept for Position-Based Routing in Vehicular Networks. In Proceedings of the Vtc-2007 Fall Vehicular Technology Conference, Baltimore, MD, USA, 30 September–3 October 2007; pp. 2101–2105. [Google Scholar]
- Karp, B.; Kung, H.T. GPSR: Greedy Perimeter Stateless Routing for Wireless Networks. In Proceedings of the International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 243–254. [Google Scholar]
- Gomez, A.E.; Glaser, S.; Alayli, Y.; Neto, A.D.M.; Wolf, D.F. Cooperative Collision Warning for Driving Assistance. In Proceedings of the IEEE International Conference on Intelligent Transportation Systems, Rio de Janeiro, Brazil, 1–4 November 2016; pp. 990–997. [Google Scholar]
- Saleh, A.I.; Gamel, S.A.; Abo-Al-Ez, K.M. A Reliable Routing Protocol for Vehicular Ad hoc Networks. Comput. Electr. Eng. 2016. [Google Scholar] [CrossRef]
- He, Y.; Xu, W.; Lin, X. A Stable Routing Protocol for Highway Mobility over Vehicular Ad-Hoc Networks. In Proceedings of the IEEE Vehicular Technology Conference, Glasgow, UK, 11–14 May 2015; pp. 1–5. [Google Scholar]
- Wu, H.; Fujimoto, R.; Guensler, R.; Hunter, M. MDDV: A Mobility-Centric Data Dissemination Algorithm for Vehicular Networks. In Proceedings of the ACM International Workshop on Vehicular Ad Hoc Networks, Philadelphia, PA, USA, 1 October 2004; pp. 47–56. [Google Scholar]
- Li, J.; Song, N.; Yang, G.; Li, M.; Cai, Q. Improving positioning accuracy of vehicular navigation system during GPS outages utilizing ensemble learning algorithm. Inf. Fusion 2017, 35, 1–10. [Google Scholar] [CrossRef]
- Ramadhani, P.E.; Setiawan, M.D.; Yutama, M.A.; Perdana, D.; Sari, R.F. Performance Evaluation of Hybrid Wireless Mesh Protocol (HWMP) on VANET Using VanetMobiSim. In Proceedings of the International Conference on Computational Intelligence and Cybernetics, Makassar, Indonesia, 22–24 November 2017; pp. 41–46. [Google Scholar]
- Mirjazaee, N.; Moghim, N. An opportunistic routing based on symmetrical traffic distribution in vehicular networks. Comput. Electr. Eng. 2015, 47, 1–12. [Google Scholar] [CrossRef]
- Hirose, T.; Makino, T.; Taniguchi, M.; Kubota, H. Activation Timing in a Vehicle-to-Vehicle Communication System for Traffic Collision. In Proceedings of the SAE 2016 World Congress and Exhibition, Detroit, MI, USA, 12–14 April 2016. [Google Scholar]
- Wu, J.; Chen, Z. Data Decision and Transmission Based on Mobile Data Health Records on Sensor Devices in Opportunistic Networks. Wirel. Person. Commun. 2016, 90, 2073–2087. [Google Scholar] [CrossRef]
- Qing-song, C.A.I.; Chang, N.J.W.L. Adaptive Data Dissemination Algorithm for Vehicular Opportunistic Networks. Comput. Sci. 2011, 38, 58–63. [Google Scholar]
- Zhou, B.; Xu, K.; Gerla, M. Group and Swarm Mobility Models for Ad Hoc Network Scenarios Using Virtual Tracks. In Proceedings of the Military Communications Conference, Monterey, CA, USA, 31 October–3 November 2004; Volume 1, pp. 289–294. [Google Scholar]

| Parameter | Definition |
|---|---|
| Ev | Velocity vector |
| Ert | EM information lifetime |
| Es | Information source (base station) |
| Tabu List | |
| Ec | The degree of association between vehicles |
| Er | Data delivery path |
| Request | Determine whether to exchange EM information |
| Parameters | Value |
|---|---|
| Mobility model | Manhattan Mobility Model |
| MAC and PHY Layers | IEEE 802.11P |
| Simulation time (s) | 1000 |
| Number of vehicles | 50, 150, 250, 350, 450 |
| Vehicle velocity (km/h) | 40–80 |
| Transmission range (m) | 300 |
| CBR (data per second) | 20–180 |
| EM size (bits) | 320 |
| HM size (bits) | 30 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, L.; Chen, Z.; Wu, J. An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association in Vehicular Ad Hoc Networks. Information 2017, 8, 140. https://doi.org/10.3390/info8040140
Wang L, Chen Z, Wu J. An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association in Vehicular Ad Hoc Networks. Information. 2017; 8(4):140. https://doi.org/10.3390/info8040140
Chicago/Turabian StyleWang, Leilei, Zhigang Chen, and Jia Wu. 2017. "An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association in Vehicular Ad Hoc Networks" Information 8, no. 4: 140. https://doi.org/10.3390/info8040140
APA StyleWang, L., Chen, Z., & Wu, J. (2017). An Opportunistic Routing for Data Forwarding Based on Vehicle Mobility Association in Vehicular Ad Hoc Networks. Information, 8(4), 140. https://doi.org/10.3390/info8040140






