A Distributed Ledger for Supply Chain Physical Distribution Visibility †
Abstract
1. Introduction
2. Related Work
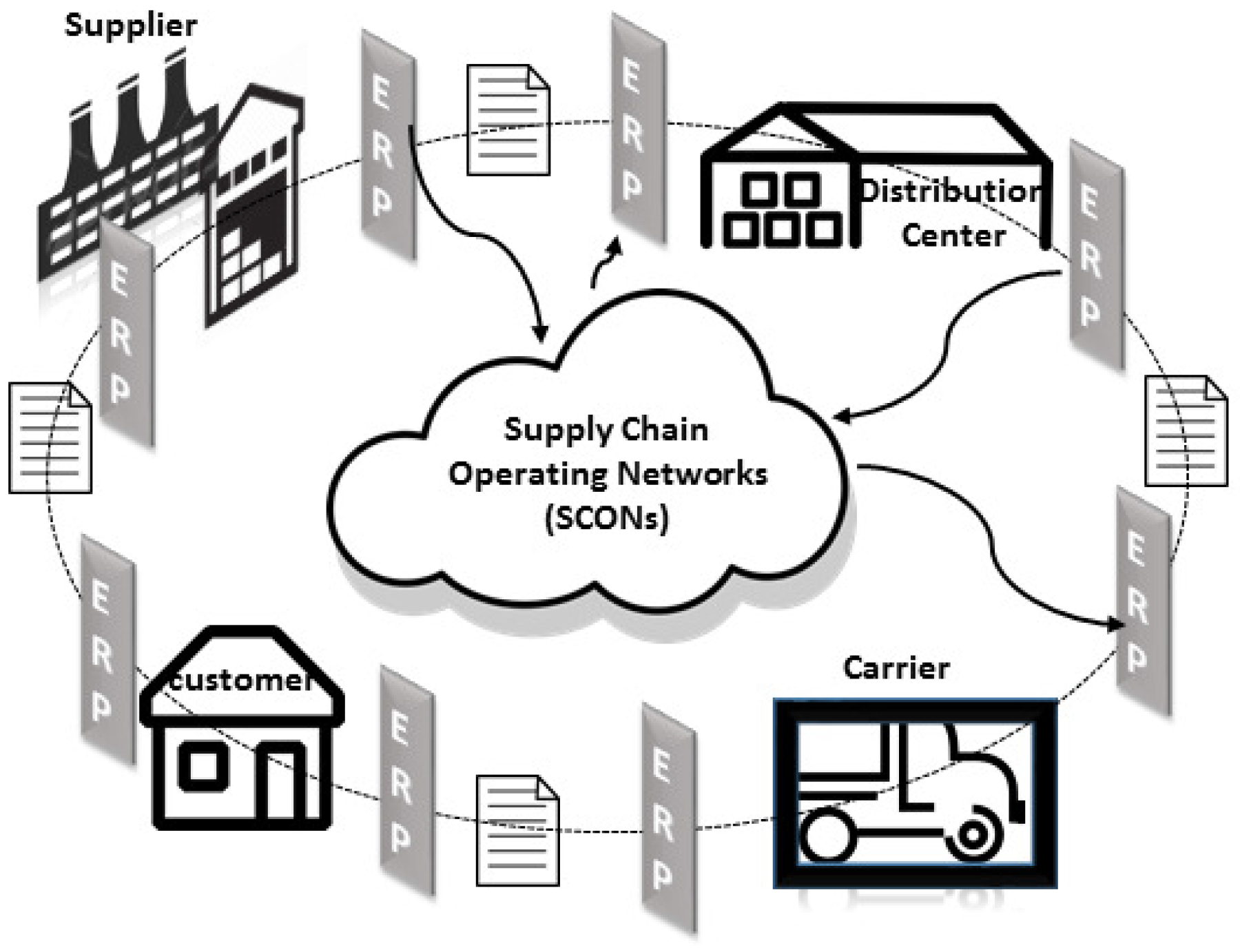
3. Framework Design
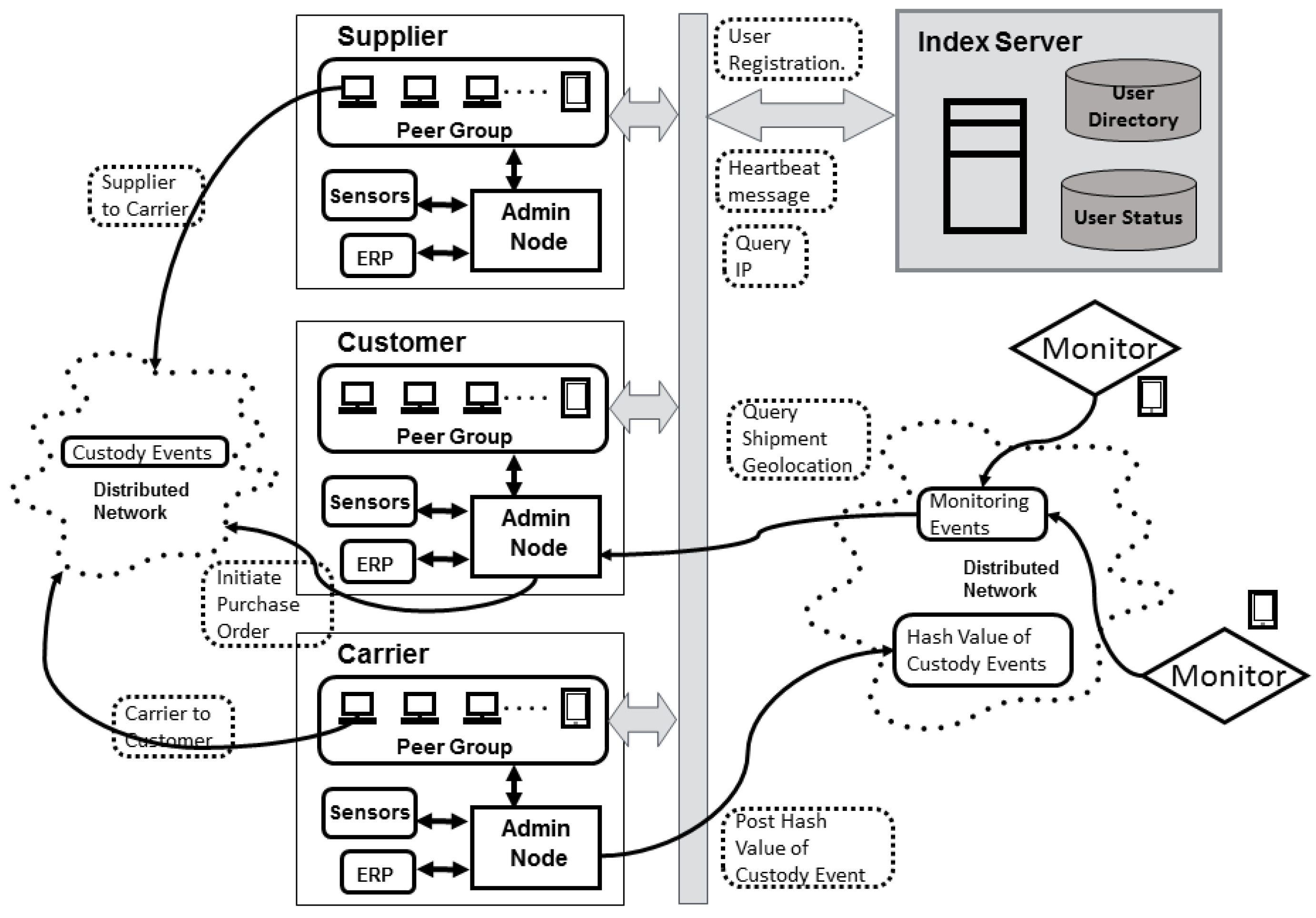
3.1. Architecture Overview
- The index server is a central directory that maintains the address of all the nodes in the network. It also assigns a unique ID to each participant.
- Peers are nodes that can take on different roles in different shipments (e.g., customer, supplier and carrier).
- The administrative node is a special peer node. Each trading partner has one administrative node, which is responsible for communicating with the ERP internal to the organization. This node participates in all sub-networks involving the associated partner and maintains a permanent record of all information exchanges related to the partner’s shipments.
- Third party external monitors are responsible for the validation of the geolocation of the shipments and the posting of this information to the public ledger.
3.2. Events
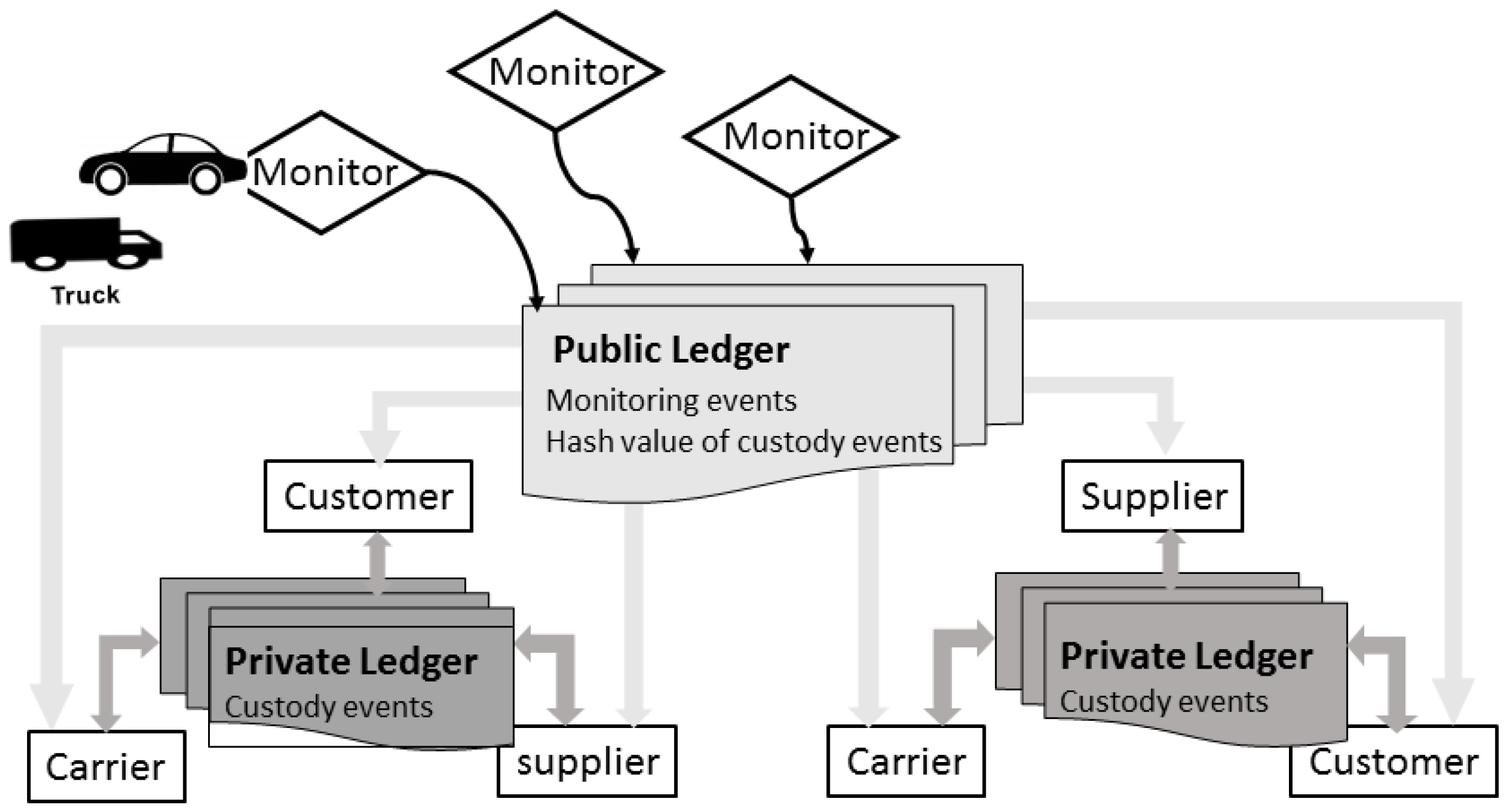
- The genesis event indicates the start of a shipment (i.e., the issue of a purchase order). This event is similar to the genesis event in Bitcoin [15]. It is initiated by the administrative node of the customer and broadcasted to all trading partners. Each partner that is participating in the shipment stores this information into its local database in the form of a document. The details of the genesis event are only accessible to the trading partners. However, a hash value calculated from the genesis event is also posted to the public ledger by the event generator, in this case, the customer.
- The custody event is a record of the custody status of the shipment. The custody can remain with the current holder of the shipment or show a transfer from one participant to another (e.g., shipment transferred from supplier to carrier, shipment delivered to customer by carrier). In addition to the genesis event, the custody events form the shipment-centric private ledger that is shared among the supplier, carrier and customer for a given shipment. Similar to the genesis event, the hash value of each custody event is also calculated and posted to the public ledger by the event generator.
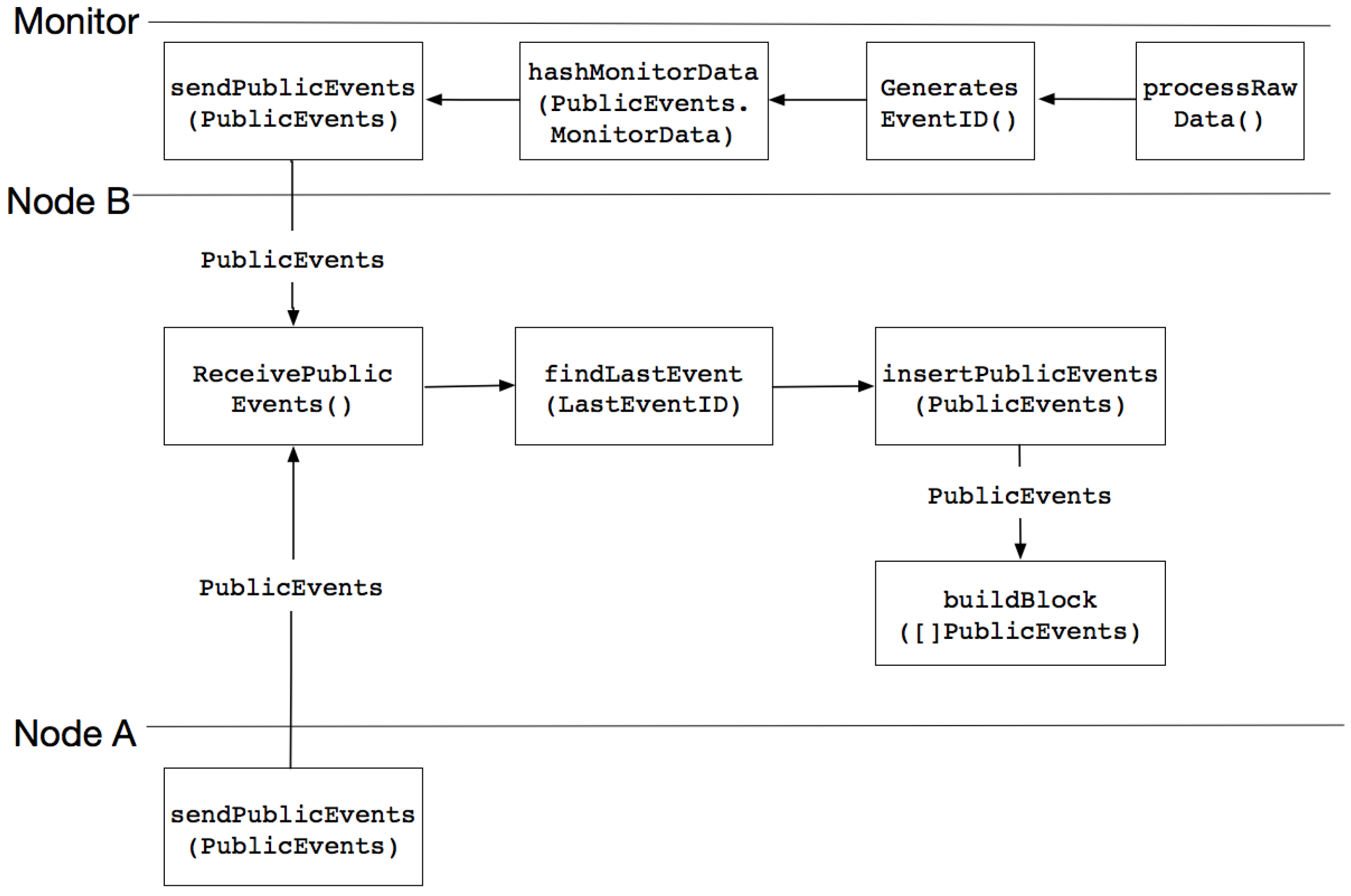
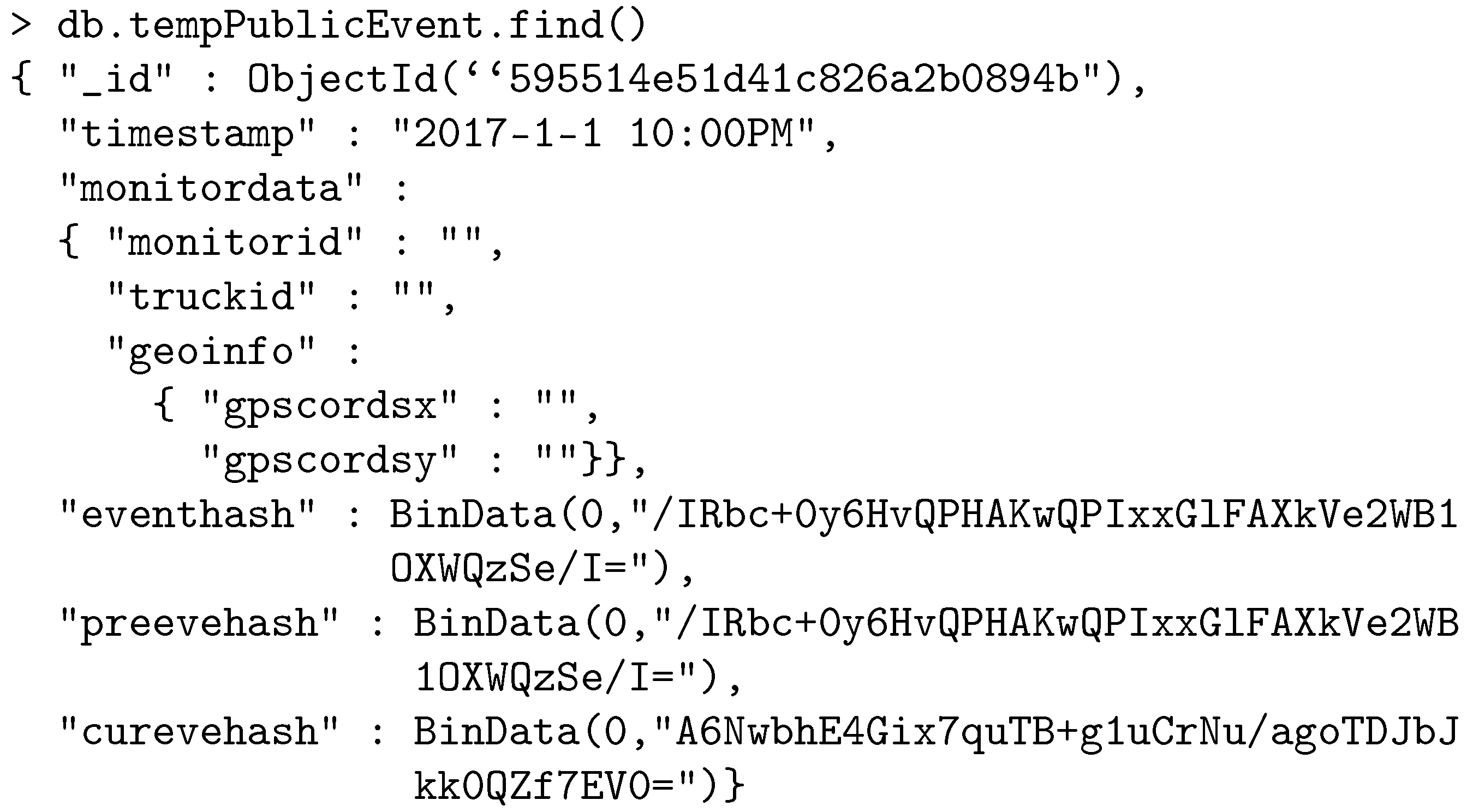
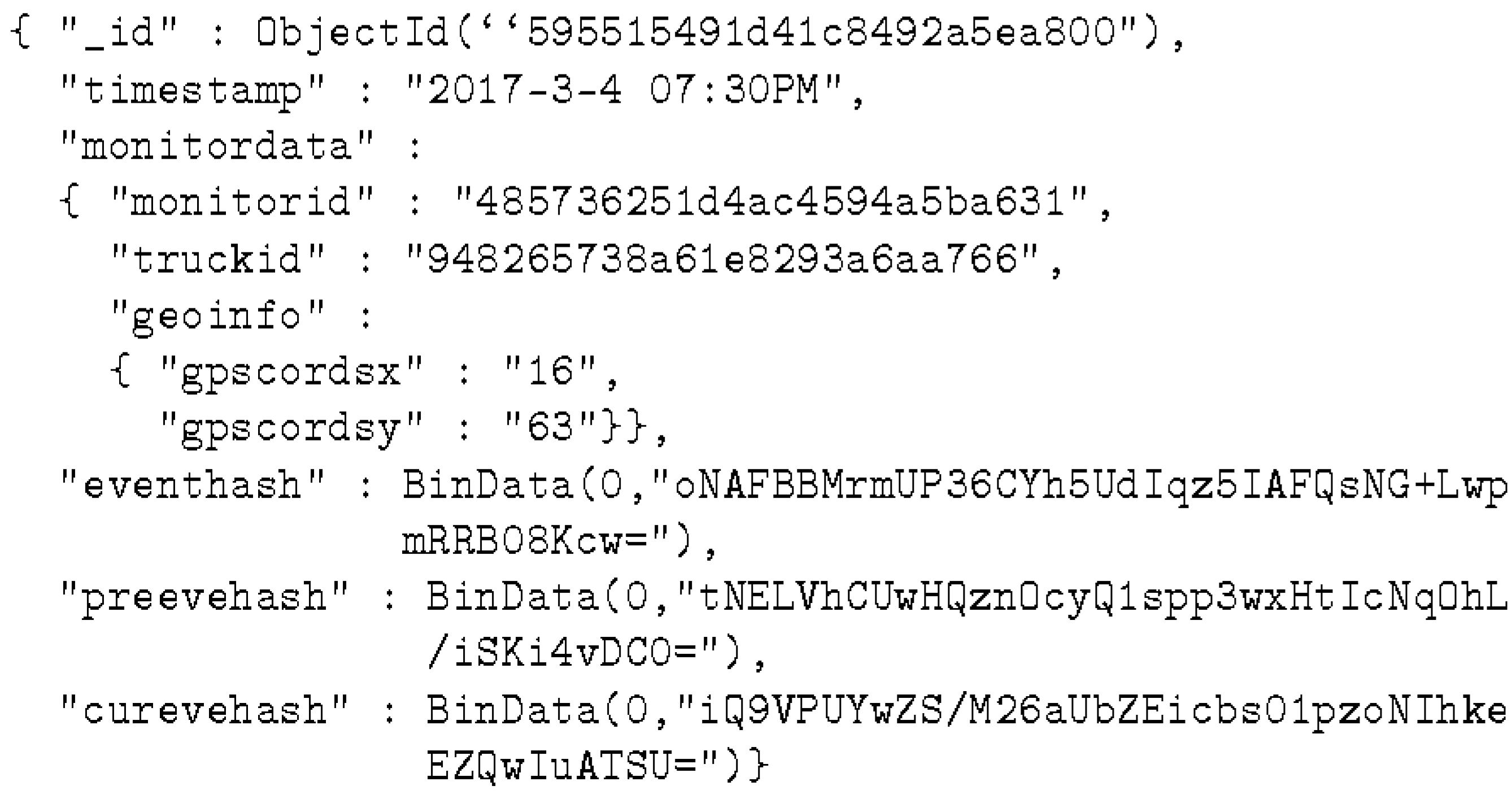
- The monitoring event indicates the geographical location of a shipment. This information is generated by external monitors when trucks are physically near the monitors and an information exchange is executed between the monitors and the trucks in order to document this physical proximity. The monitoring events are posted to the public ledger by the external monitors.
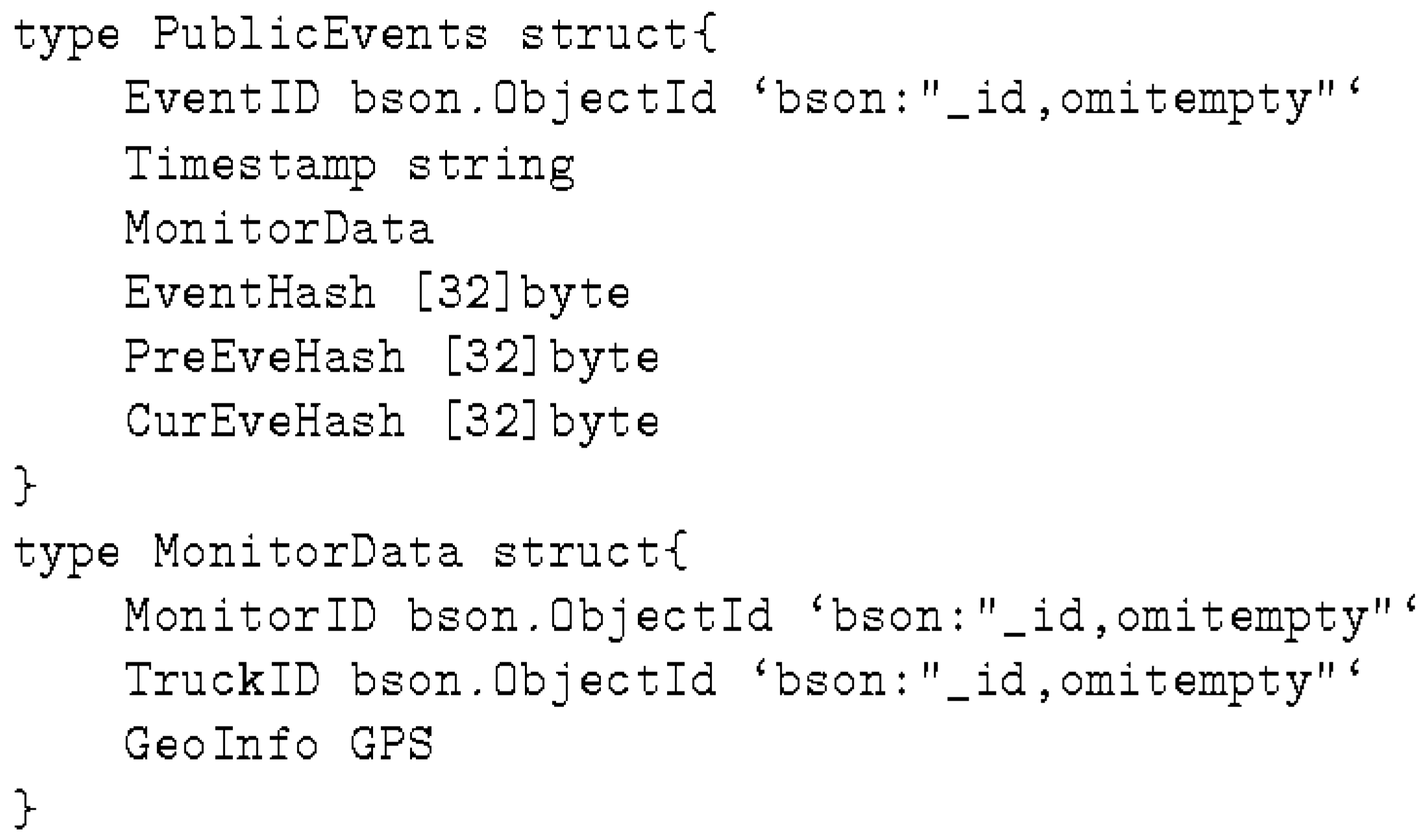
3.3. Data Structures
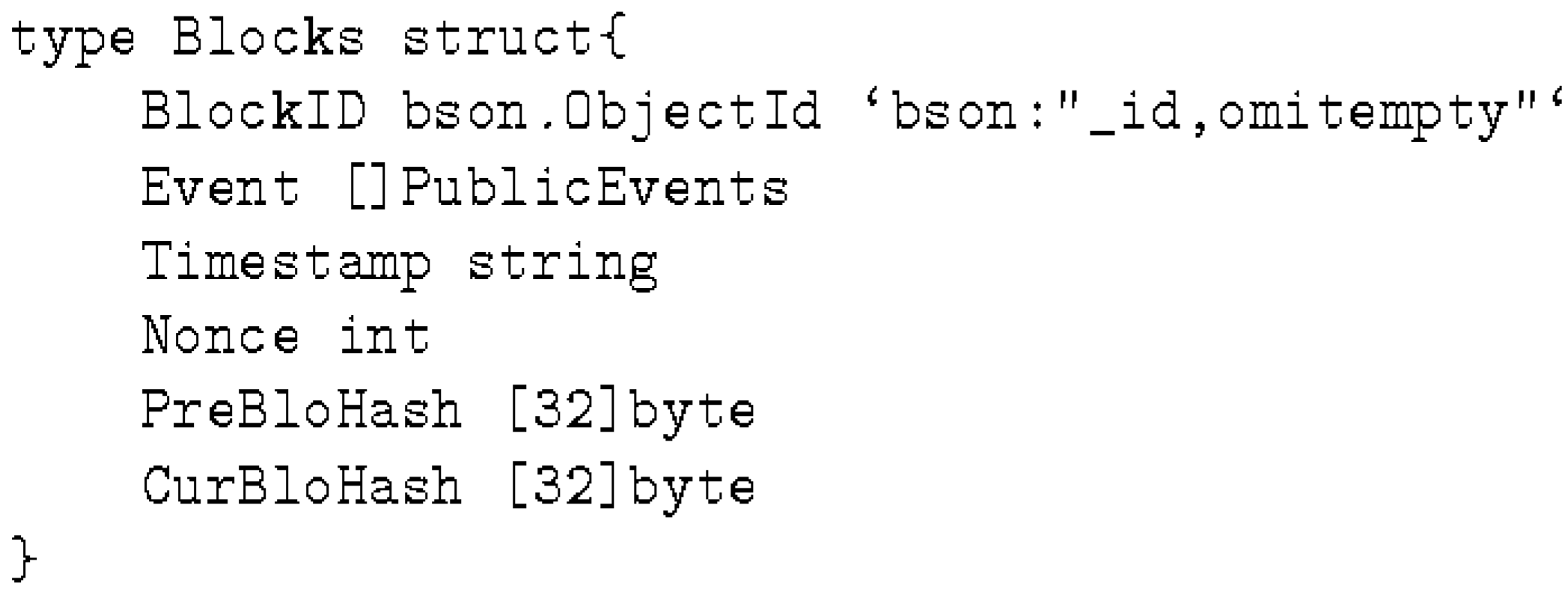
3.4. Blockchain
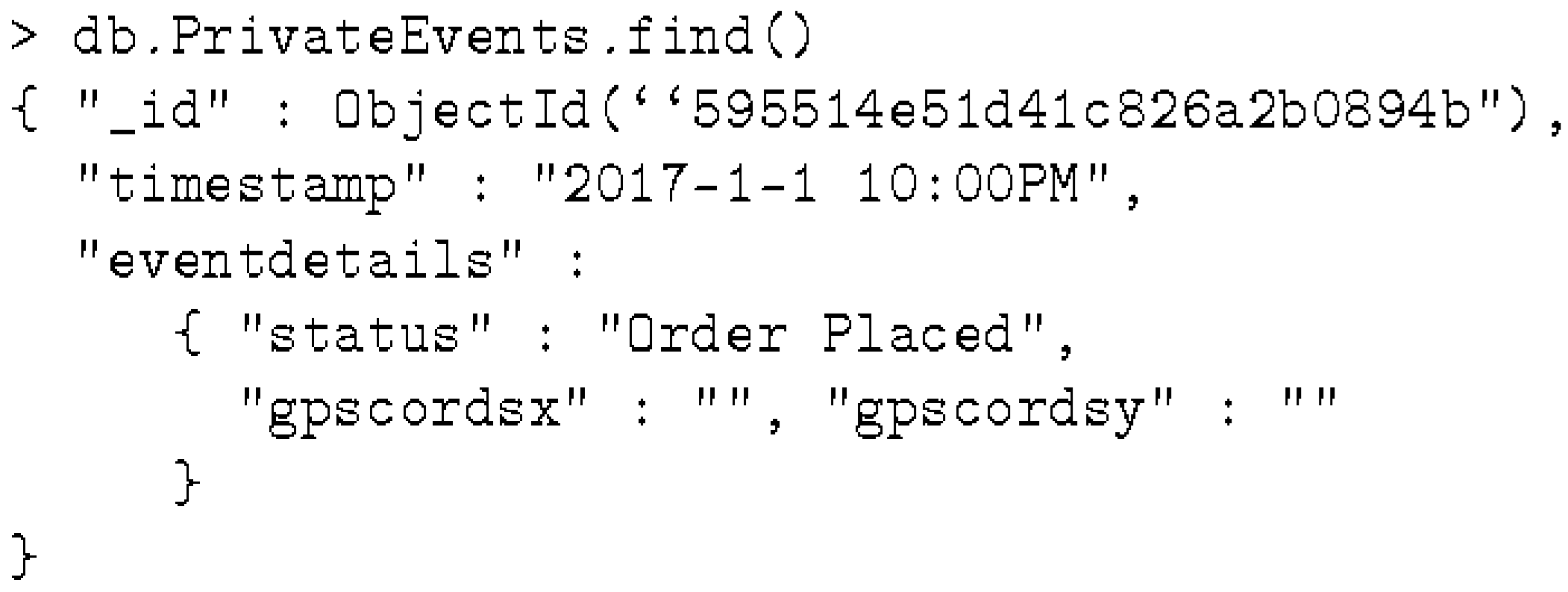
- PrivateEvents captures the details of genesis and custody events.
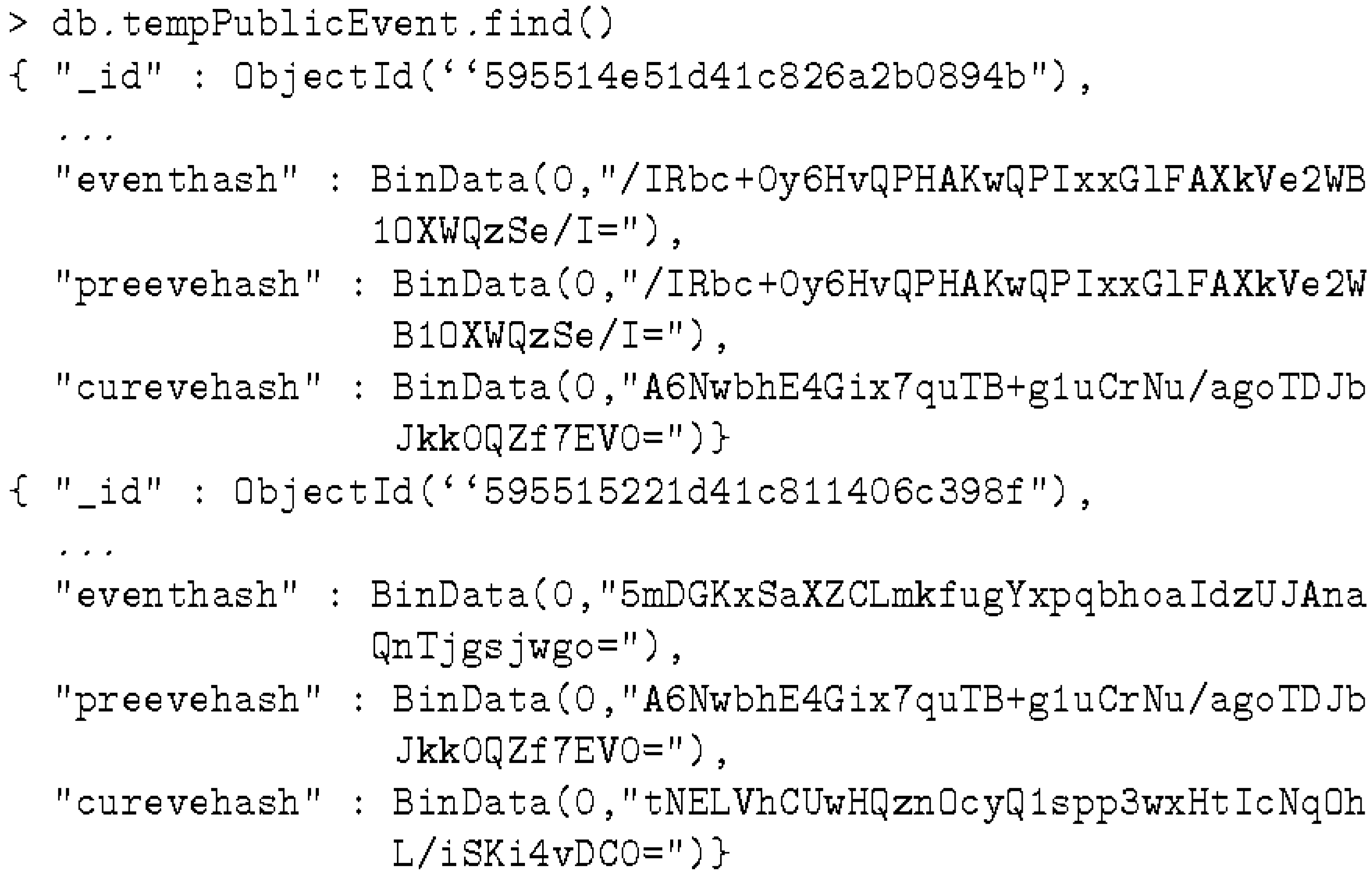
- tempPublicEvent is used for temporary storage of public events that are not yet part of a block in the public ledger.
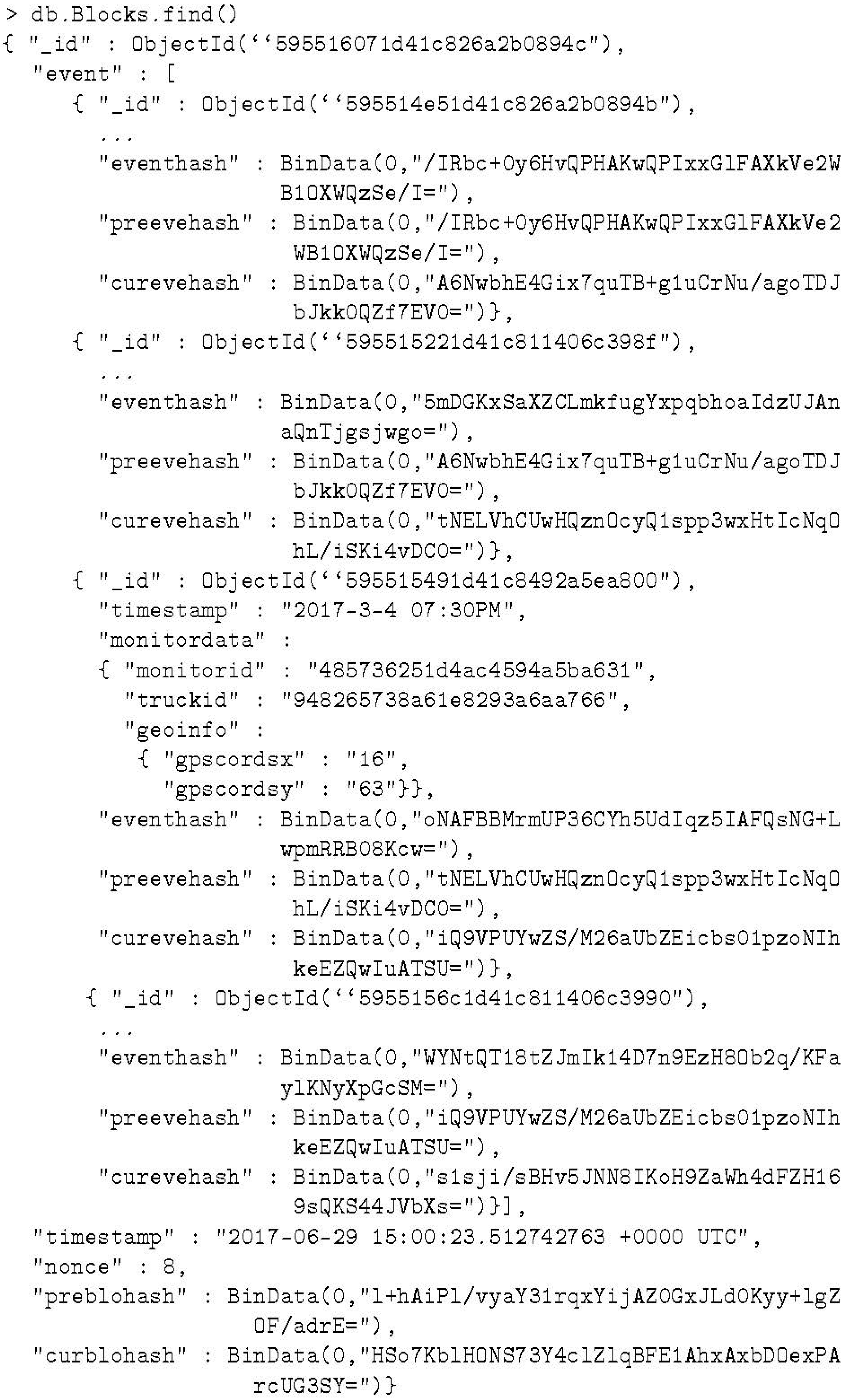
- Blocks is used for chained blocks. The longest chain is accepted by every node in the network as the public ledger of record.
- tempBlocks is used when multiple blocks are received at the same time, or when the PreBloHash of the received block does not match the latest block in the local database of the node.
3.5. Validation
3.6. Processes
- The Private Event Process supports the sharing of private events among trading partners in a shipment.
- The Public Event Process allows the exchange and the posting of public events to the public ledger.
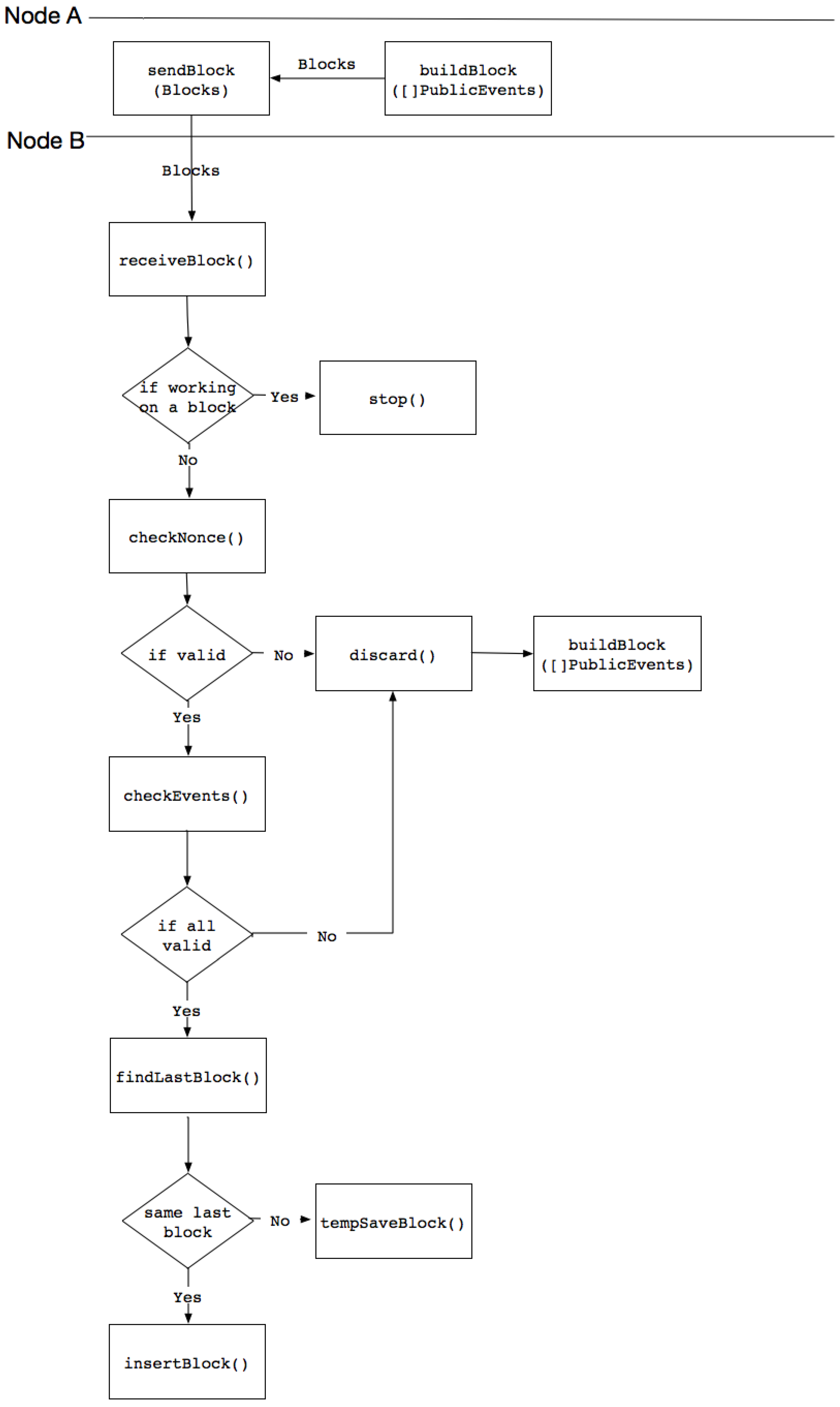
- The Build Block Process combines multiple events into a block and validates each block in the public ledger.
3.6.1. Public Event Process
3.6.2. Build Block Process
4. Implementation and Discussion
- Event 1: A genesis event that is generated by node A. It is an event related to order 1 in which company A and company B are participating.
- Event 2: A custody event that is sent by node B. This is an event related to order 2, which is being shared with company B and company C.
- Event 3: A monitoring event that is generated by an external monitor. It consists of a public event that is sent to all nodes in the network. It represents a geolocation update for order 2.
- Event 4: A custody event that is generated by node B. This is an event related to order 1 in which company A and company B are participating.
- Event 5: A monitoring event that is generated by an external monitor. It consists of a public event that is sent to all nodes in the network and represents a geolocation update for order 1.
5. Conclusions
Author Contributions
Conflicts of Interest
References
- Harrison, A.; van Hoek, R.I. Logistics Management and Strategy; Pearson Education: London, UK, 2008. [Google Scholar]
- Xu, X.; Weber, I.; Staples, M.; Zhu, L.; Bosch, J.; Bass, L.; Pautasso, C.; Rimba, P. A Taxonomy of Blockchain-Based Systems for Architecture Design. In Proceedings of the 2017 IEEE International Conference on Software Architecture (ICSA), Gothenburg, Sweden, 3–7 April 2017; pp. 243–252. [Google Scholar]
- Lundbaek, L.N.; Huth, M. Oligarchic Control of Business-to-Business Blockchains. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 68–71. [Google Scholar]
- Schollmeier, R. A definition of peer-to-peer networking for the classification of peer-to-peer architectures and applications. In Proceedings of the IEEE First International Conference on Peer-To-Peer Computing, Linkoping, Sweden, 27–29 August 2001; pp. 101–102. [Google Scholar]
- Ripeanu, M. Peer-to-peer architecture case study: Gnutella network. In Proceedings of the IEEE First International Conference on Peer-To-Peer Computing, Linkoping, Sweden, 27–29 August 2001; pp. 99–100. [Google Scholar]
- Iacovou, C.L.; Benbasat, I.; Dexter, A.S. Electronic data interchange and small organizations: Adoption and impact of technology. Manag. Inf. Syst. Q. 1995, 19, 465–485. [Google Scholar] [CrossRef]
- Pezoa, F.; Reutter, J.L.; Suarez, F.; Ugarte, M.; Vrgoč, D. Foundations of JSON schema. In Proceedings of the 25th International Conference on World Wide Web, Montréal, QC, Canada, 11–15 April 2016; pp. 263–273. [Google Scholar]
- Beck, R. Supply Chain Segmentation: The Next Step in Supply Chain Excellence. Technical Report. Available online: http://info.e2open.com/rs/e2open/images/WP_SC_Segmentation.pdf (accessed on 1 November 2017).
- Dickersbach, J.T. Supply Chain Management with APO: Structures, Modelling Approaches and Implementation of MySAP SCM 4.1; Springer Science & Business Media: Berlin, Germany, 2005. [Google Scholar]
- Daithankar, J.; Pandit, T. Transportation Management with SAP TM 9: A Hands-On Guide to Configuring, Implementing, and Optimizing SAP TM; Apress: New York, NY, USA, 2014. [Google Scholar]
- Parfett, M. What Is EDI? A Guide to Electronic Data Interchange; Blackwell Publishing: Hoboken, NJ, USA, 1992. [Google Scholar]
- Qureshi, K.N.; Abdullah, A.H. A survey on intelligent transportation systems. Middle-East J. Sci. Res. 2013, 15, 629–642. [Google Scholar]
- Rezaei, J.; Ortt, R.; Trott, P. How SMEs can benefit from supply chain partnerships. Int. J. Prod. Res. 2015, 53, 1527–1543. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar Singh, R. Coordination and responsiveness issues in SME supply chains: A review. Benchmark. Int. J. 2017, 24, 635–650. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-To-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 November 2017).
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology?—A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef] [PubMed]
- Centobelli, P.; Cerchione, R.; Esposito, E. Environmental sustainability in the service industry of transportation and logistics service providers: Systematic literature review and research directions. Trans. Res. Part D Trans. Environ. 2017, 53, 454–470. [Google Scholar] [CrossRef]
- Correia, E.; Carvalho, H.; Azevedo, S.G.; Govindan, K. Maturity Models in Supply Chain Sustainability: A Systematic Literature Review. Sustainability 2017, 9, 64. [Google Scholar] [CrossRef]
- Andrade, N.; Mowbray, M.; Lima, A.; Wagner, G.; Ripeanu, M. Influences on cooperation in bittorrent communities. In Proceedings of the 2005 ACM SIGCOMM Workshop on Economics of Peer-To-Peer Systems, Philadelphia, PA, USA, 22–26 August 2005; pp. 111–115. [Google Scholar]
- Fox, G. Peer-to-peer networks. Comput. Sci. Eng. 2001, 3, 75–77. [Google Scholar] [CrossRef]
- Guha, S.; Daswani, N. An Experimental Study of the Skype Peer-To-Peer Voip System; Technical Report; Cornell University Press: Ithaca, NY, USA, 2005. [Google Scholar]
- IBM Institute for Business Value. Next Generation Supply Chain powered by Cognitive and Blockchain; Technical Report, Digital Supply Chain; International Business Machines Corporation: Armonk, NY, USA, 2017. [Google Scholar]
- Smith, J. Blockfreight: Blockchain Technology for Global Freight. Technical Report. Available online: https://bravenewcoin.com/assets/Whitepapers/BlockfreightWhitepaperFinalDraft.pdf (accessed on 1 November 2017).
- Toyoda, K.; Mathiopoulos, P.T.; Sasase, I.; Ohtsuki, T. A Novel Blockchain-Based Product Ownership Management System (POMS) for Anti-Counterfeits in The Post Supply Chain. IEEE Access 2017. [Google Scholar] [CrossRef]
- Nakasumi, M. Information Sharing for Supply Chain Management Based on Block Chain Technology. In Proceedings of the 2017 IEEE 19th Conference on Business Informatics (CBI), Thessaloniki, Greece, 24–27 July 2017; Volume 1, pp. 140–149. [Google Scholar]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere-a use-case of blockchains in the pharma supply-chain. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 772–777. [Google Scholar]
- Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology. In Proceedings of the 2016 13th International Conference on IEEE Service Systems and Service Management (ICSSSM), Kunming, China, 24–26 June 2016; pp. 1–6. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Wang, H. Blockchain Challenges and Opportunities: A Survey; Work Paper; Inderscience Publishers: Geneva, Switzerland, 2016. [Google Scholar]
- Zhao, J.L.; Fan, S.; Yan, J. Overview of business innovations and research opportunities in blockchain and introduction to the special issue. Financ. Innov. 2016, 2, 28. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops (SPW), San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar]
- Li, Z.; Wu, H.; King, B.; Ben Miled, Z.; Wassick, J.; Tazelaar, J. On the Integration of Event-Based and Transaction-Based Architectures for Supply Chains. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; pp. 376–382. [Google Scholar]
- Pilkington, M. Blockchain technology: Principles and applications. In Research Handbook on Digital Transformations; Edward Elgar Publishing: Northampton, MA, USA, 2015. [Google Scholar]
- Pike, R. The Go Programming Language; Addison-Wesley: Boston, MA, USA, 2015. [Google Scholar]
- Wei-ping, Z.; Ming-Xin, L.; Huan, C. Using MongoDB to implement textbook management system instead of MySQL. In Proceedings of the 2011 IEEE 3rd International Conference on Communication Software and Networks (ICCSN), Xi’an, China, 27–29 May 2011; pp. 303–305. [Google Scholar]


© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, H.; Li, Z.; King, B.; Ben Miled, Z.; Wassick, J.; Tazelaar, J. A Distributed Ledger for Supply Chain Physical Distribution Visibility. Information 2017, 8, 137. https://doi.org/10.3390/info8040137
Wu H, Li Z, King B, Ben Miled Z, Wassick J, Tazelaar J. A Distributed Ledger for Supply Chain Physical Distribution Visibility. Information. 2017; 8(4):137. https://doi.org/10.3390/info8040137
Chicago/Turabian StyleWu, Haoyan, Zhijie Li, Brian King, Zina Ben Miled, John Wassick, and Jeffrey Tazelaar. 2017. "A Distributed Ledger for Supply Chain Physical Distribution Visibility" Information 8, no. 4: 137. https://doi.org/10.3390/info8040137
APA StyleWu, H., Li, Z., King, B., Ben Miled, Z., Wassick, J., & Tazelaar, J. (2017). A Distributed Ledger for Supply Chain Physical Distribution Visibility. Information, 8(4), 137. https://doi.org/10.3390/info8040137





