Security Awareness of the Digital Natives
Abstract
:1. Introduction
2. Related Work
3. Methodology
3.1. Data Collection and Instruments
3.2. Sample and Analysis
- The data set collected by Ariu et.al., which was targeted at the Italian digital natives, is included in this study and corresponds to our general security competence group (GSCG). The sample consists of 1012 respondents from various university departments (Including law, engineering, computer science, humanitarian, marketing, and multiple other faculties not directed to IT education), which are mapped for the purposes of this study to the general population of digital natives.
- Secondly, we collected data for the medium security competence group (MSCG) by targeting digital natives from Greece with education exclusively in computer science. This group is expected to a have wider knowledge over the use of mobile technologies and increased awareness over security related aspects due to their educational background. The sample consists of 303 responders in total at the undergraduate (234), postgraduate (54), and doctoral (15) levels.
- Finally, the target population for the high security competence group (HSCG) was undergraduate, postgraduate and doctoral students of information security from Norway. These were expected to have a higher security awareness regarding the four main areas than the medium and generic groups, due to their specialized education. For this group, we had 35 respondents in total, of which 21 are undergraduate students, 10 postgraduate, and four doctoral students.
4. Analysis of Results and Discussion
4.1. Use of Mobile Devices
4.2. Connectivity and Network Access
4.3. Management of Credentials
4.4. Knowledge and Fear of Risks
5. Summary of Results
- Users tend to have increased confidence in the daily use of their mobile devices, leading them to negligent behavior towards actions with potential security related impact. However, the digital natives seem to adopt a more constrained stance when security threats become directly visible. It would be interesting to investigate the variations in user behavior prior and after a major security incident, along with analyzing the duration and extent of this phenomenon.
- Specific areas of user behavior (such as the storage of plaintext passwords in mobile devices) are not significantly affected by their security awareness or background, with a consistent percentage of digital natives remaining willing to accept the risk. Aiming to facilitate further security improvements in such areas would require not only informing the users about the potential threats, but also channeling those who persist in the practicality of such actions into more secure alternatives (e.g., password managers).
- The digital natives still remain unaware of some countermeasures that are available at their disposal and could improve their user experience while maintaining higher security standards.
- Variations in user behavior have been identified to originate not only from their level of security awareness, but also from regional, financial and cultural agents. Thus, regional studies and campaigns aiming to raise security awareness, must be scoped and adapted accordingly.
- Users tend to prioritize access to services and the usability of their mobile devices over the enforcement of security measures, without major differentiations based on their background. However, the results of this study have shown that users who are aware of the security risks are willing to opt for security when usable solutions become available.
- Digital natives are willing to accept risks despite of their concerns about security (e.g., jailbreaking/rooting, unofficial application sources) in order to obtain access to additional services. This decision is not significantly affected by their overall knowledge about security, while users with backgrounds in engineering, computer science or information security are less reluctant due to their increased confidence.
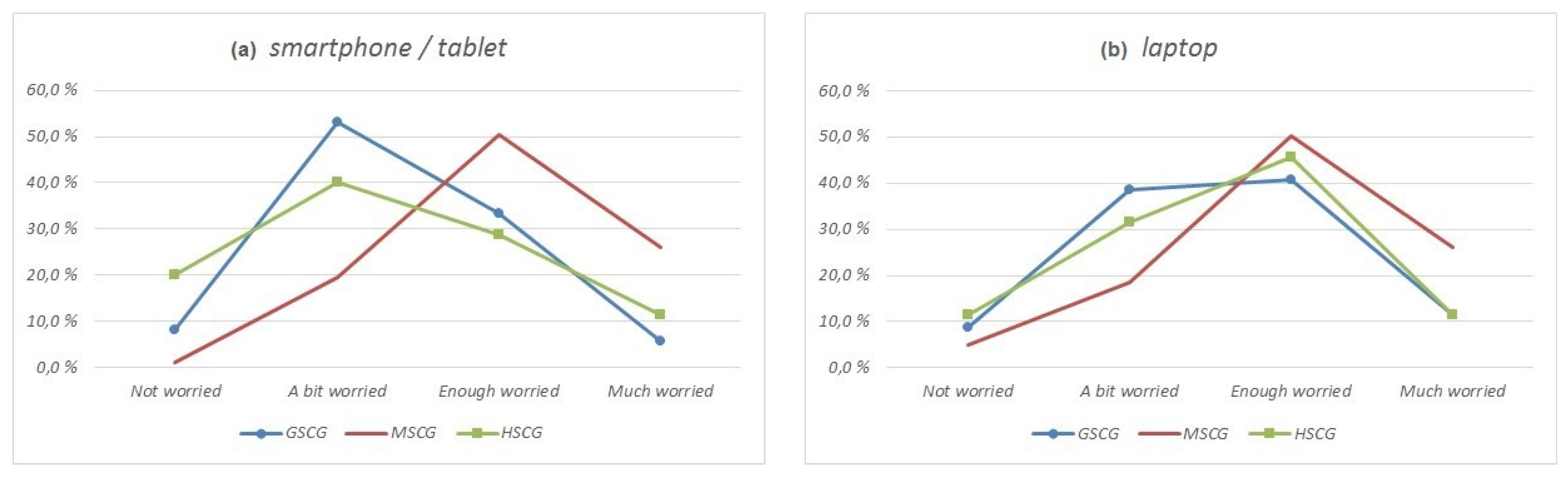
- The users of mobile devices seem to feel more confident and less constrained in terms of security when using their laptops in comparison to smartphones and tablets. This is attributed to the maturity of the technologies, but also the lack of recognition of the increased computational capacity and criticality of tasks allocated to smartphones and tablets.
- In some aspects, such as the selection of secure passwords, the digital natives seem to be informed of the appropriate practices. However, the results highlight that, despite the noticeable improvement, a precise framework still needs to be consolidated across the users’ mindsets.
6. Limitations
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Lella, A.; Lipsman, A. The US Mobile App Report. 2014. Available online: http://www.comscore.com/Insights/Presentationsand-Whitepapers/2014/The-US-Mobile-App-Report (accessed on 8 April 2015).
- Prensky, M. Digital natives, digital immigrants part 1. On the Horizon 2001, 9, 1–6. [Google Scholar] [CrossRef]
- Bennett, S.; Maton, K.; Kervin, L. The ‘digital natives’ debate: A critical review of the evidence. Br. J. Educ. Technol. 2008, 39, 775–786. [Google Scholar] [CrossRef]
- Chin, E.; Felt, A.P.; Sekar, V.; Wagner, D. Measuring user confidence in smartphone security and privacy. In Proceedings of the Eighth Symposium on Usable Privacy and Security, Washington, DC, USA, 11–13 July 2012. [Google Scholar]
- Felt, A.P.; Ha, E.; Egelman, S.; Haney, A.; Chin, E.; Wagner, D. Android permissions: User attention, comprehension, and behavior. In Proceedings of the Eighth Symposium on Usable Privacy and Security, Washington, DC, USA, 11–13 July 2012. [Google Scholar]
- Kelley, P.G.; Consolvo, S.; Cranor, L.F.; Jung, J.; Sadeh, N.; Wetherall, D. A conundrum of permissions: Installing applications on an android smartphone. In Proceedings of the International Conference on Financial Cryptography and Data Security, Kralendijk, Bonaire, 27 February–2 March 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 68–79. [Google Scholar]
- Mylonas, A.; Gritzalis, D.; Tsoumas, B.; Apostolopoulos, T. A qualitative metrics vector for the awareness of smartphone security users. In Proceedings of the International Conference on Trust, Privacy and Security in Digital Business, Prague, Czech Republic, 28–29 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 173–184. [Google Scholar]
- Mylonas, A.; Kastania, A.; Gritzalis, D. Delegate the smartphone user? Security awareness in smartphone platforms. Comput. Secur. 2013, 34, 47–66. [Google Scholar] [CrossRef]
- Ophoff, J.; Robinson, M. Exploring end-user smartphone security awareness within a South African context. In Proceedings of the 2014 Information Security for South Africa, Johannesburg, South Africa, 13–14 August 2014. [Google Scholar]
- Parker, F.; Ophoff, J.; Van Belle, J.P.; Karia, R. Security awareness and adoption of security controls by smartphone users. In Proceedings of the 2015 Second International Conference on Information Security and Cyber Forensics (InfoSec), Cape Town, South Africa, 15–17 November 2015. [Google Scholar]
- Markelj, B.; Bernik, I. Safe use of mobile devices arises from knowing the threats. J. Inf. Secur. Appl. 2015, 20, 84–89. [Google Scholar] [CrossRef]
- Markelj, B.; Zgaga, S. Comprehension of cyber threats and their consequences in Slovenia. Comput. Law Secur. Rev. 2016, 32, 513–525. [Google Scholar] [CrossRef]
- Sheila, M.; Faizal, M.; Shahrin, S. Dimension of mobile security model: Mobile user security threats and awareness. Int. J. Mob. Learn. Organ. 2015, 9, 66–85. [Google Scholar] [CrossRef]
- Ariu, D.; Bosco, F.; Ferraris, V.; Perri, P.; Spolti, G.; Stirparo, P.; Vaciago, G.; Zanero, S. Security of the Digital Natives. 2014. Available online: https://ssrn.com/abstract=2442037 (accessed on 13 October 2016).
- Norman, G. Likert scales, levels of measurement and the “laws” of statistics. Adv. Health Sci. Educ. 2010, 15, 625–632. [Google Scholar] [CrossRef] [PubMed]
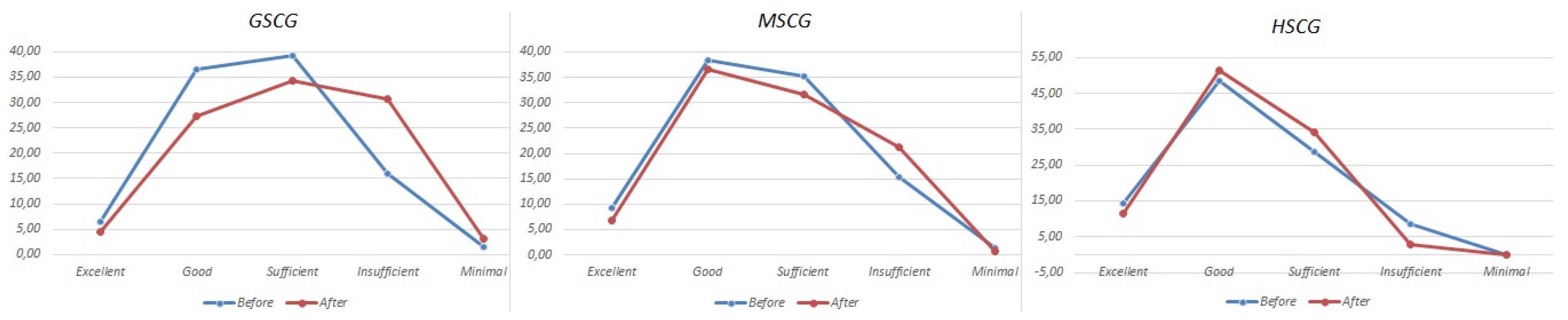


| Excellent | Good | Sufficient | Insufficient | Minimal | ||
|---|---|---|---|---|---|---|
| Before | GSCG | 6.5% | 36.6% | 39.3% | 16.0% | 1.6% |
| MSCG | 9.3% | 38.5% | 35.3% | 15.4% | 1.3% | |
| HSCG | 14.3% | 48.6% | 28.6% | 8.6% | 0.0% | |
| After | GSCG | 4.4% | 27.4% | 34.4% | 30.7% | 3.1% |
| MSCG | 6.7% | 36.5% | 31.7% | 21.2% | 0.6% | |
| HSCG | 11.4% | 51.4% | 34.3% | 2.9% | 0.0% |
| Yes | No | |
|---|---|---|
| GSCG | 27.7% | 72.3% |
| MSCG | 31.1% | 68.9% |
| HSCG | 28.6% | 71.4% |
| Yes | No | |
|---|---|---|
| GSCG | 68.5% | 31.5% |
| MSCG | 33.5% | 66.5% |
| HSCG | 28.6% | 71.4% |
| Apps and OS | Apps | OS | Anything | ||
|---|---|---|---|---|---|
| Cellphone/tablet | GSCG | 81.3% | 8.8% | 6.8% | 3.1% |
| MSCG | 79.5% | 8.3% | 5.1% | 4.2% | |
| HSCG | 88.6% | 8.6% | 0.0% | 2.9% | |
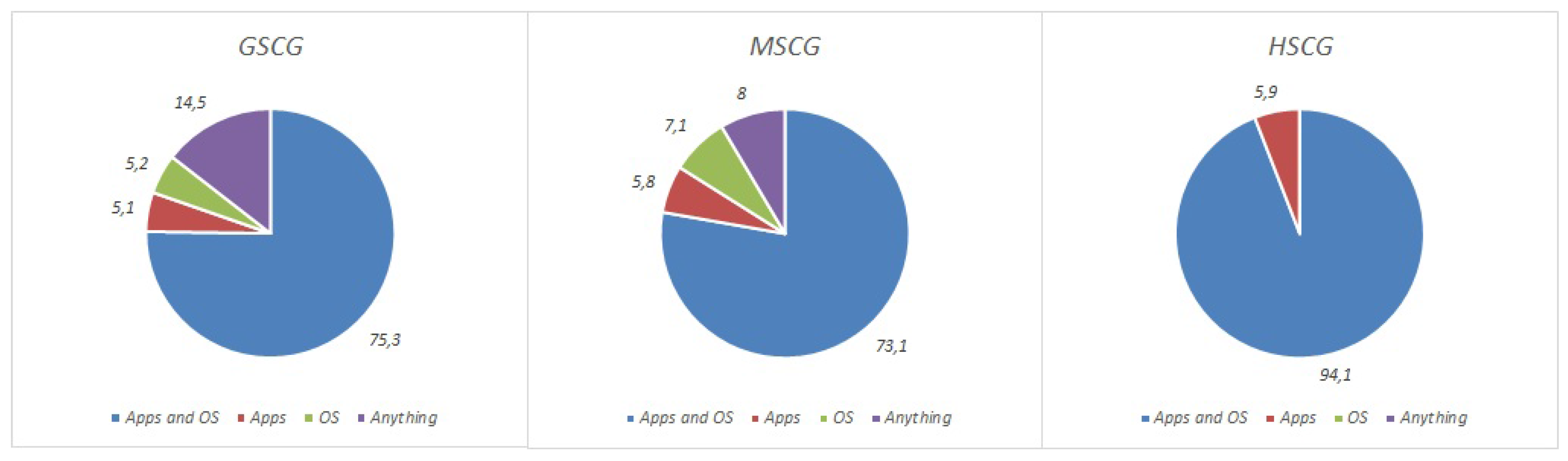
| Laptop | GSCG | 75.3% | 5.1% | 5.2% | 14.5% |
| MSCG | 73.1% | 5.8% | 7.1% | 8.0% | |
| HSCG | 94.1% | 5.9% | 0.0% | 0.0% |
| Official Store | Other Sources | |
|---|---|---|
| GSCG | 83.1% | 16.9% |
| MSCG | 85.9% | 11.5% |
| HSCG | 91.4% | 8.6% |
| Save Credentials to Stay Logged in | Log out | Forget to Log out | Do Not Log out Because It Is Not Important | Do Not Log out Because I Do Not Know How | |
|---|---|---|---|---|---|
| GSCG | 40.3% | 24.1% | 19.6% | 10.3% | 5.6% |
| MSCG | 30.8% | 26.6% | 16.7% | 20.5% | 1.9% |
| HSCG | 48.6% | 22.9% | 14.3% | 14.3% | 0.0% |
| Never | Rarely | Often | Always | |
|---|---|---|---|---|
| GSCG | 15.6% | 38.2% | 25.5% | 20.7% |
| MSCG | 8.0% | 26.3% | 27.6% | 34.9% |
| HSCG | 5.7% | 14.3% | 40.0% | 40.0% |
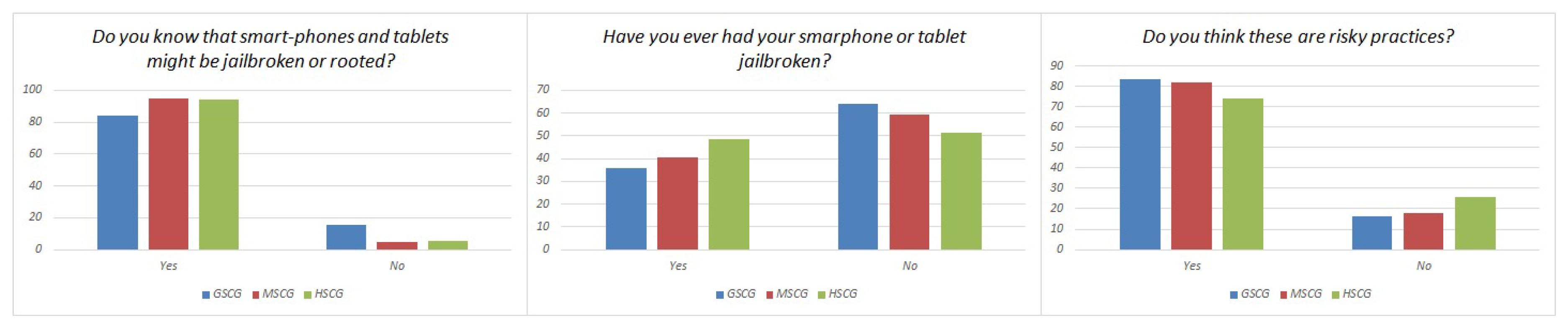
| Do you know that smartphones and tablets might be jailbroken or rooted? | ||
| Yes | No | |
| GSCG | 84.2% | 15.8% |
| MSCG | 94.9% | 5.1% |
| HSCG | 94.3% | 5.7% |
| Have you ever had your smarphone or tablet jailbroken? | ||
| GSCG | 35.7% | 64.3% |
| MSCG | 40.4% | 59.6% |
| HSCG | 48.6% | 51.4% |
| Do you think these are risky practices? | ||
| GSCG | 83.5% | 16.5% |
| MSCG | 82.1% | 17.9% |
| HSCG | 74.3% | 25.7% |
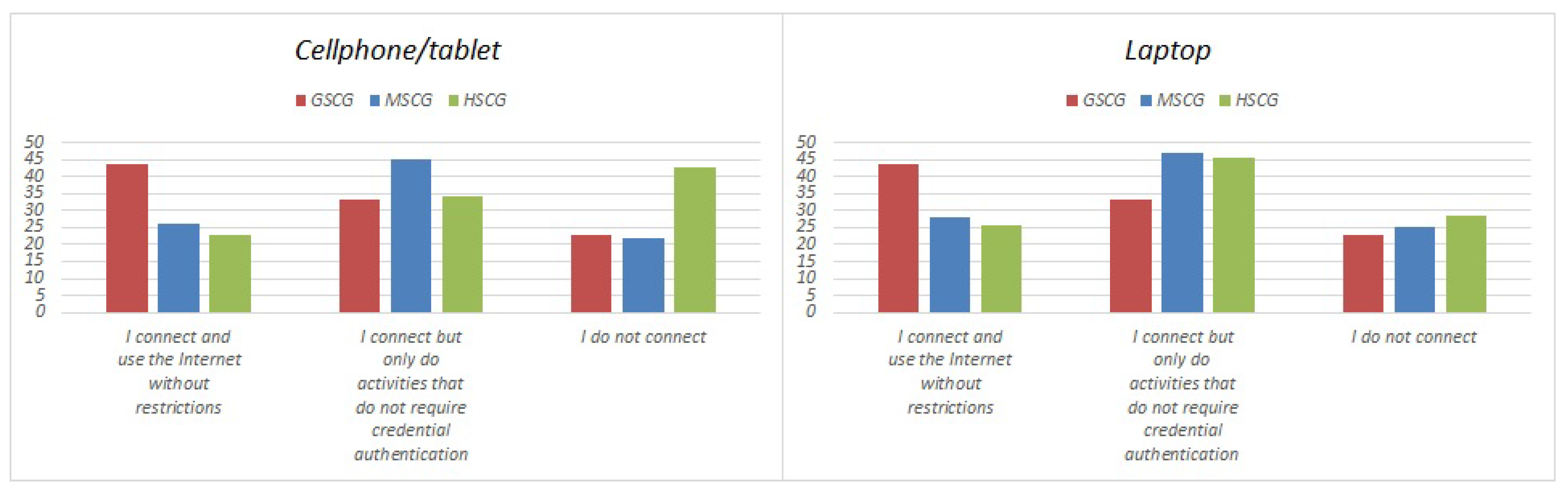
| I Connect and Use the Internet without Restrictions | I Connect but Only Do Activities that Do Not Require Credential Authentication | I Do Not Connect | ||
|---|---|---|---|---|
| Cellphone/tablet | GSCG | 43.6% | 33.4% | 23.0% |
| MSCG | 26.0% | 44.9% | 21.8% | |
| HSCG | 22.9% | 34.3% | 42.9% | |
| Laptop | GSCG | 43.6% | 33.4% | 23.0% |
| MSCG | 28.0% | 46.9% | 25.1% | |
| HSCG | 25.7% | 45.7% | 28.6% |
| I Know Them but Never Thought About Using Them | I Know Them but I Am Not Interested in Using Them | I Know Them but They Make the Use of My Device Uncomfortable | I Do Not Know Them | |
|---|---|---|---|---|
| GSCG | 13.6% | 27.7% | 52.5% | 6.3% |
| MSCG | 3.0% | 41.5% | 51.0% | 5.0% |
| HSCG | 16.7% | 33.3% | 50.0% | 0.0% |
| I Always Use the Same Password for All the Applications | I Use Small Variations of the Same Password for Different Applications | I Always Use Different Passwords | I Do Not Use Applications that Require Passwords | |
|---|---|---|---|---|
| GSCG | 20.6% | 41.3% | 31.7% | 6.3% |
| MSCG | 8.7% | 41.7% | 39.1% | 6.7% |
| HSCG | 5.7% | 51.4% | 40.0% | 2.9% |
| The passwords that I use are at least 8 characters long | ||
| Yes | No | |
| GSCG | 87.0% | 13.0% |
| MSCG | 83.7% | 11.5% |
| HSCG | 100.0% | 0.0% |
| I use passwords that contain personal information | ||
| GSCG | 36.5% | 63.5% |
| MSCG | 36.8% | 63.2% |
| HSCG | 17.1% | 82.9% |
| I use passwords that contain simple strings of characters (1234, qwerty, etc.) | ||
| GSCG | 8.7% | 91.3% |
| MSCG | 29.5% | 80.5% |
| HSCG | 0.0% | 100.0% |
| I use passwords that contain meaningful words | ||
| GSCG | 45.0% | 55.0% |
| MSCG | 27.8% | 72.2% |
| HSCG | 34.3% | 65.7% |
| I use passwords that contain numbers and special characters | ||
| GSCG | 74.6% | 25.4% |
| MSCG | 9.1% | 90.9% |
| HSCG | 97.1% | 2.9% |
| If the system allows it, I do not use a password | ||
| GSCG | 6.2% | 93.8% |
| MSCG | 9.4% | 90.6% |
| HSCG | 14.3% | 85.7% |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gkioulos, V.; Wangen, G.; Katsikas, S.K.; Kavallieratos, G.; Kotzanikolaou, P. Security Awareness of the Digital Natives. Information 2017, 8, 42. https://doi.org/10.3390/info8020042
Gkioulos V, Wangen G, Katsikas SK, Kavallieratos G, Kotzanikolaou P. Security Awareness of the Digital Natives. Information. 2017; 8(2):42. https://doi.org/10.3390/info8020042
Chicago/Turabian StyleGkioulos, Vasileios, Gaute Wangen, Sokratis K. Katsikas, George Kavallieratos, and Panayiotis Kotzanikolaou. 2017. "Security Awareness of the Digital Natives" Information 8, no. 2: 42. https://doi.org/10.3390/info8020042
APA StyleGkioulos, V., Wangen, G., Katsikas, S. K., Kavallieratos, G., & Kotzanikolaou, P. (2017). Security Awareness of the Digital Natives. Information, 8(2), 42. https://doi.org/10.3390/info8020042









