Simulating Advanced Social Botnets: A Framework for Behavior Realism and Coordinated Stealth
Abstract
1. Introduction
- We propose a simulation framework consisting of two core modules: a Human-like Behavior Module that generates plausible user behaviors through distributional mimicry, and a Target-Aware Coordination Module that guides interactive strategies across different user types.
- A likelihood-based reward mechanism is introduced to optimize the Human-like Behavior Module, reducing detectable divergence from real user activity patterns.
- The Target-Aware Coordination Module incorporates social interactions (e.g., following and replies) into a group-state optimization process, enhancing global coordination among bots while maintaining structural stealth.
- Our experimental results serve a dual purpose: they validate the effectiveness of our framework, and more importantly, they act as a diagnostic tool. By demonstrating which detector fails under what conditions, the results explicitly map out the failure modes and blind spots of current detector paradigms.
2. Related Works
2.1. Social Bot Detection
2.2. Social Bot Imitation
3. Methodology
3.1. Threat Model
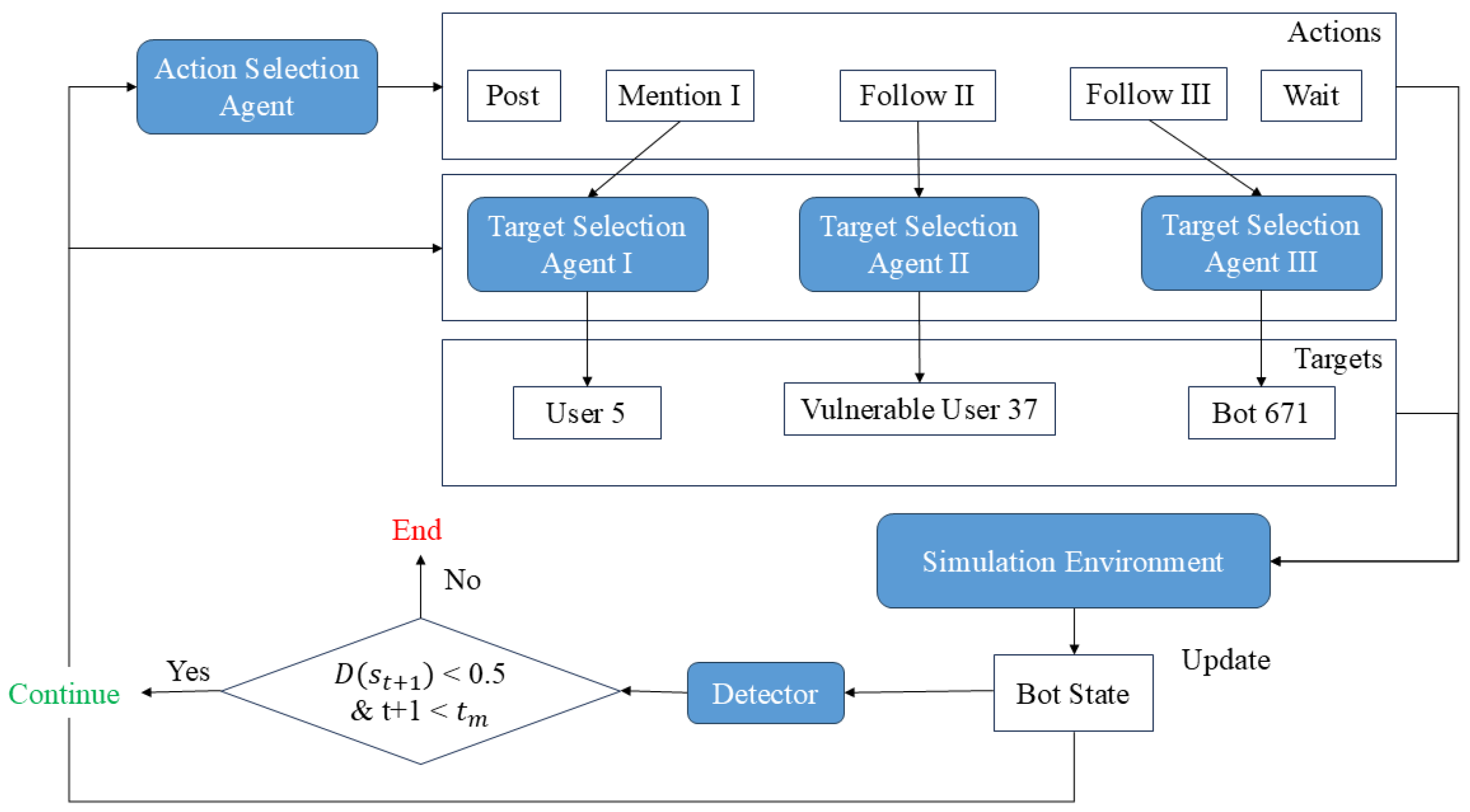
3.2. Framework
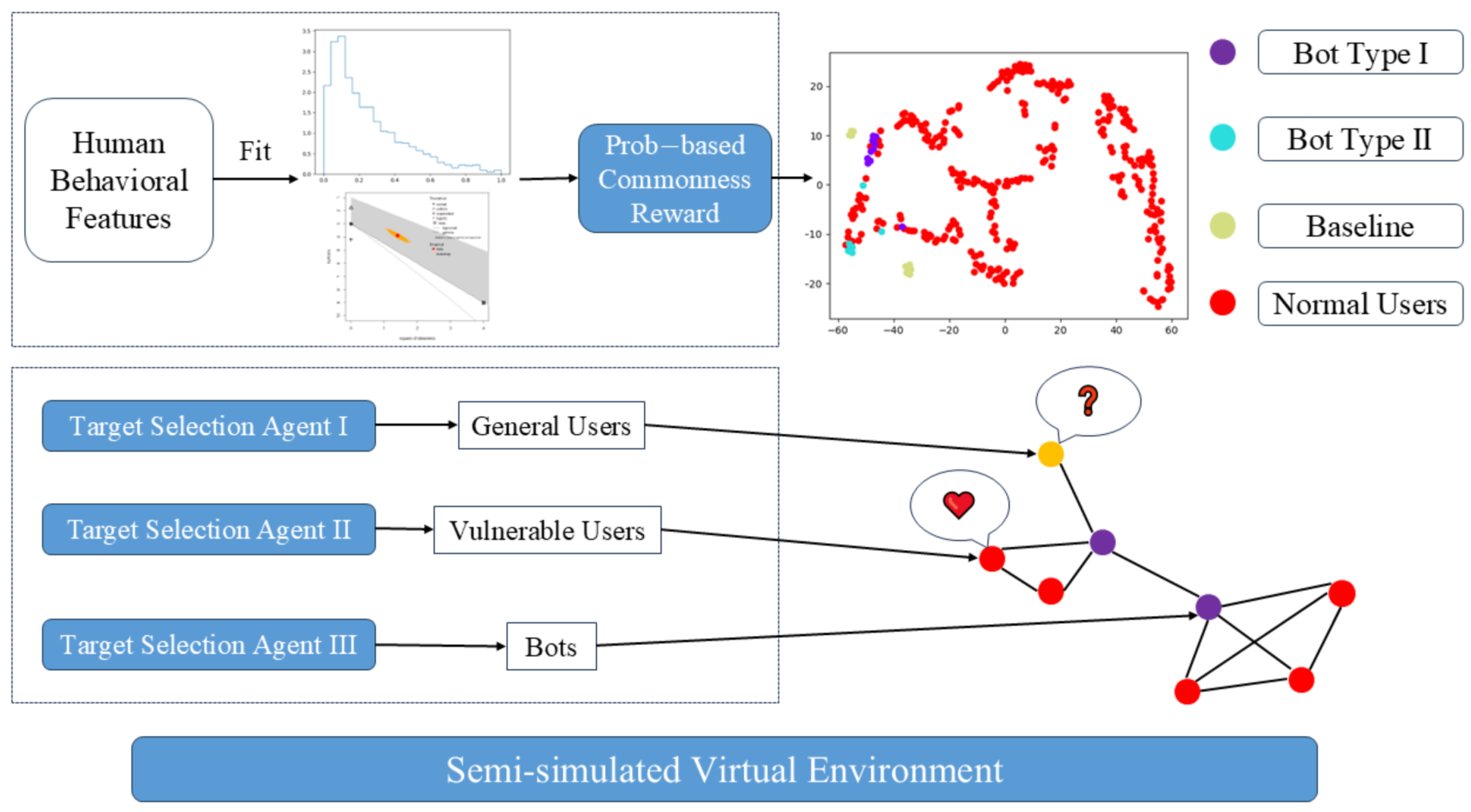
3.3. Human-like Behavior Module
3.3.1. User Clustering
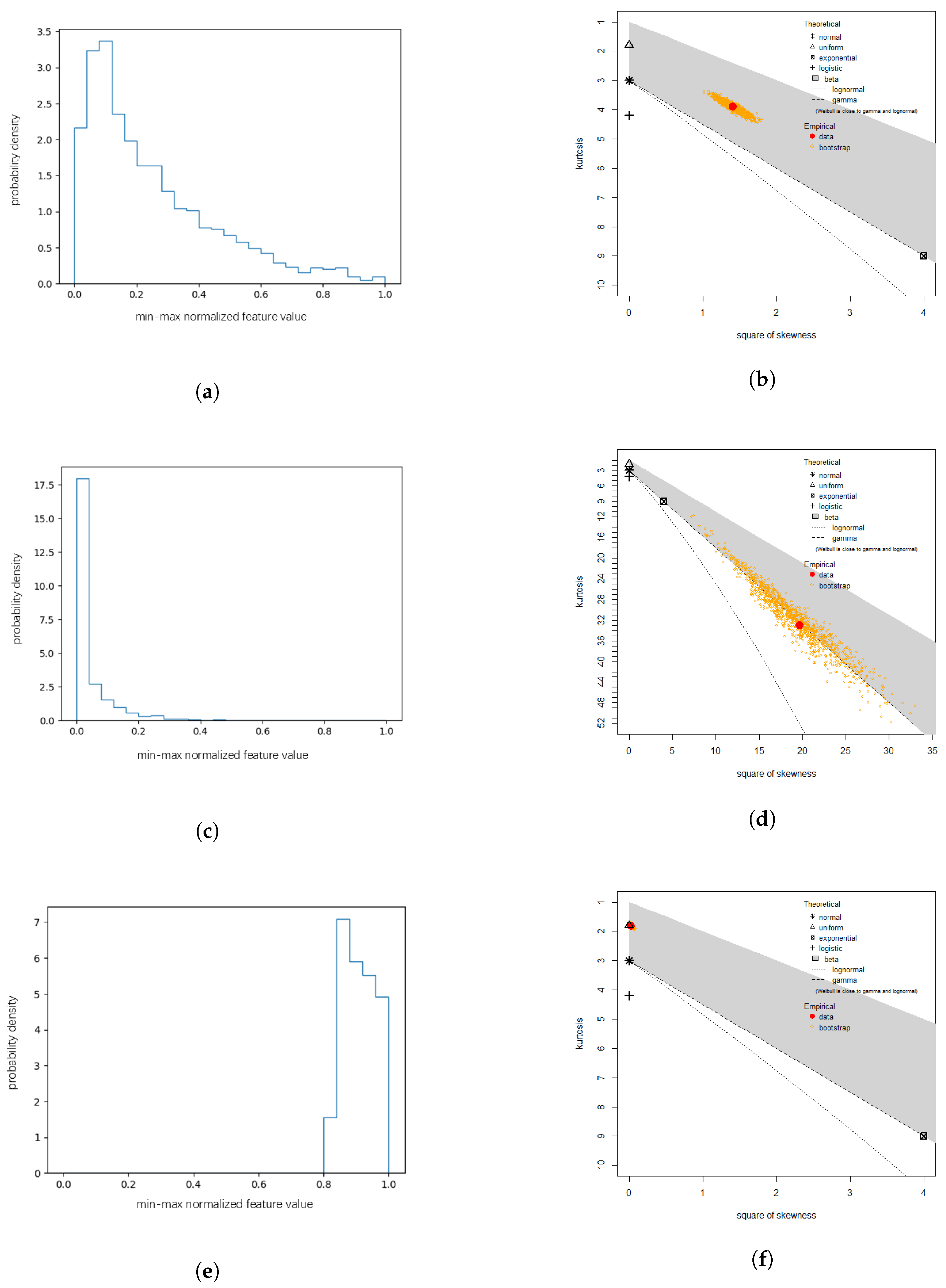
3.3.2. Prob-Based Commonness Evaluation
3.4. Target-Aware Coordination Module
- Post a tweet.
- Update the profile.
- Retweet, mention, or follow an account.
- Create or delete a list.
- Wait for a day.
| Algorithm 1 Coordinated Network Augmentation |
 |
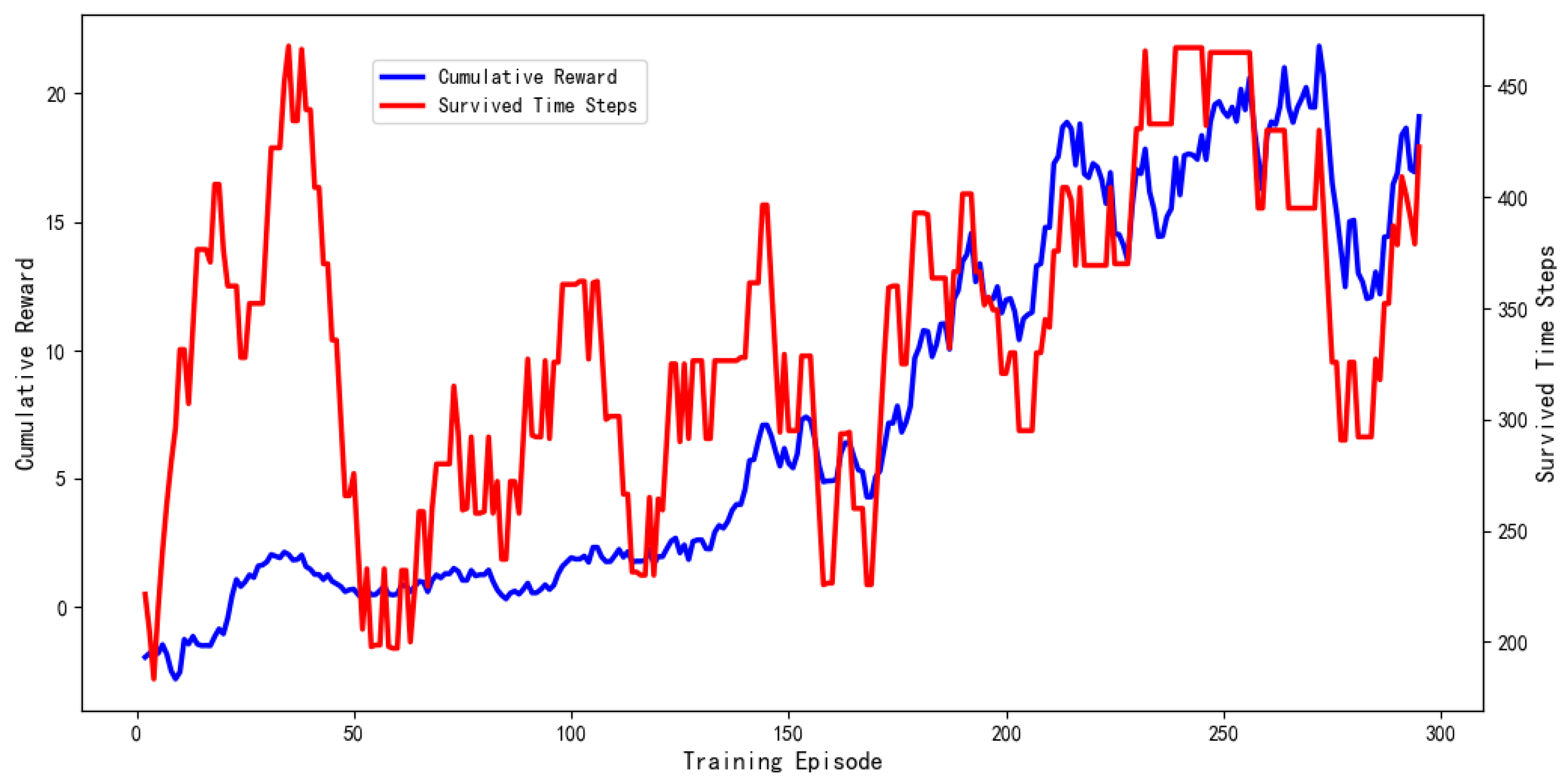
3.5. Reward Formulation
3.6. Virtual Environment
- Profile features: user name length, account age, follower count, etc.
- Friend features: mean account age of friends, maximum follower count among friends, etc.
- Network features: number of nodes and edges in the user’s retweet graph, etc.
4. Experiment
4.1. Experimental Setup
4.1.1. Dataset
4.1.2. Evaluation Metrics
4.1.3. Implementation
- ACORN [8]. This method employs a reinforcement learning framework comprised of an action selection agent and a target selection agent. The action space includes fundamental behaviors such as posting, retweeting, mentioning, and following. The target selection agent operates in a discrete action space mapped to a set of randomly sampled users.
- Rui et al. [36]. Extending the ACORN framework, this model incorporates an expanded action set that includes additional behaviors such as profile updating. Moreover, it enhances the target selection mechanism by mapping the agent’s action space to a set of pre-selected users.
- Base. The agent’s action space is constrained to prevent any inter-bot cooperative actions. Furthermore, the reward function excludes both the commonness term and the collaboration term.
- Base + Collaboration. This setup evaluates the effect of inter-bot cooperation. The action space is expanded to allow cooperative actions between bots, and the collaboration reward term is activated. The commonness reward term, however, is disabled in this setting.
- Base + Commonness. This setup integrates the commonness reward term to incentivize human-like behavior imitation. However, the action space remains constrained, preventing inter-bot cooperation, and the collaboration reward term is not computed.
- Full. This is our complete proposed strategy. The agent operates with the full action space, permitting inter-bot cooperation. Simultaneously, the reward function incorporates both proposed terms: the commonness reward and the collaboration reward.
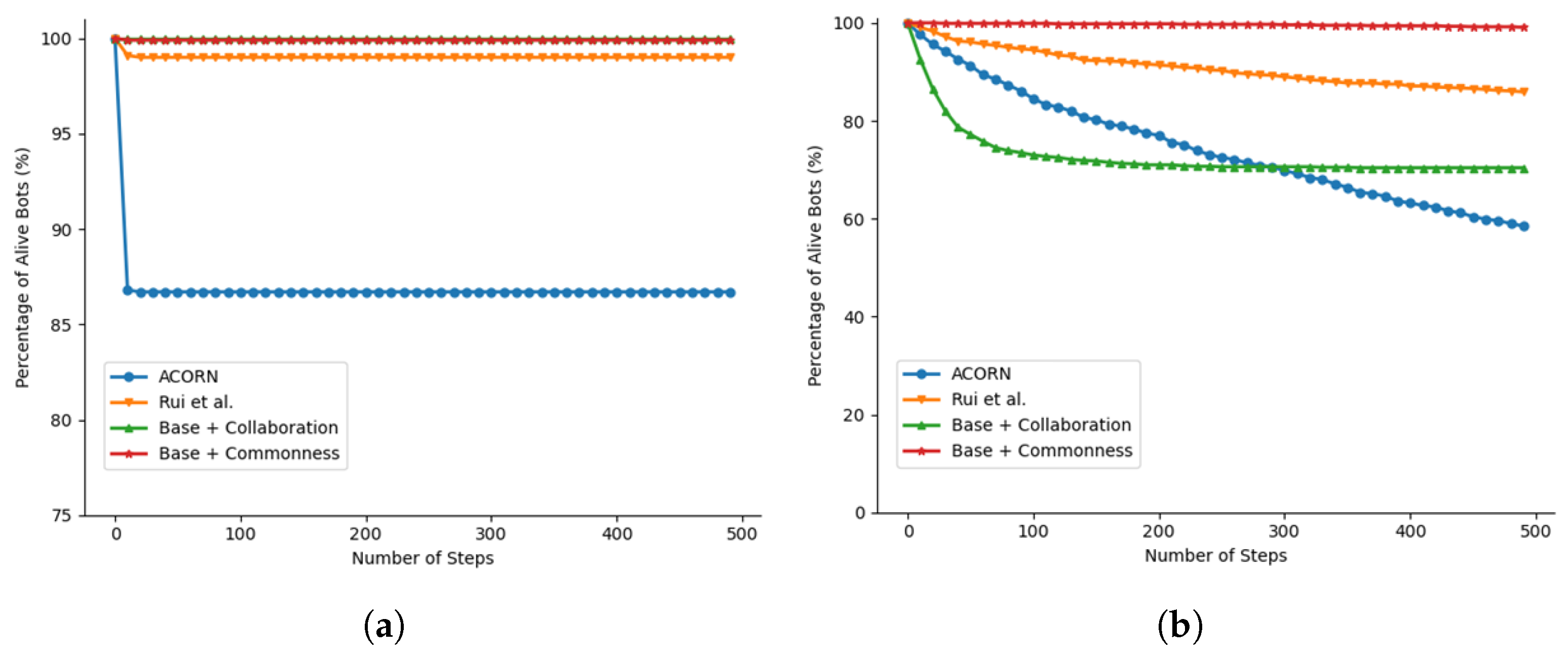
4.2. Fake Account Simulation
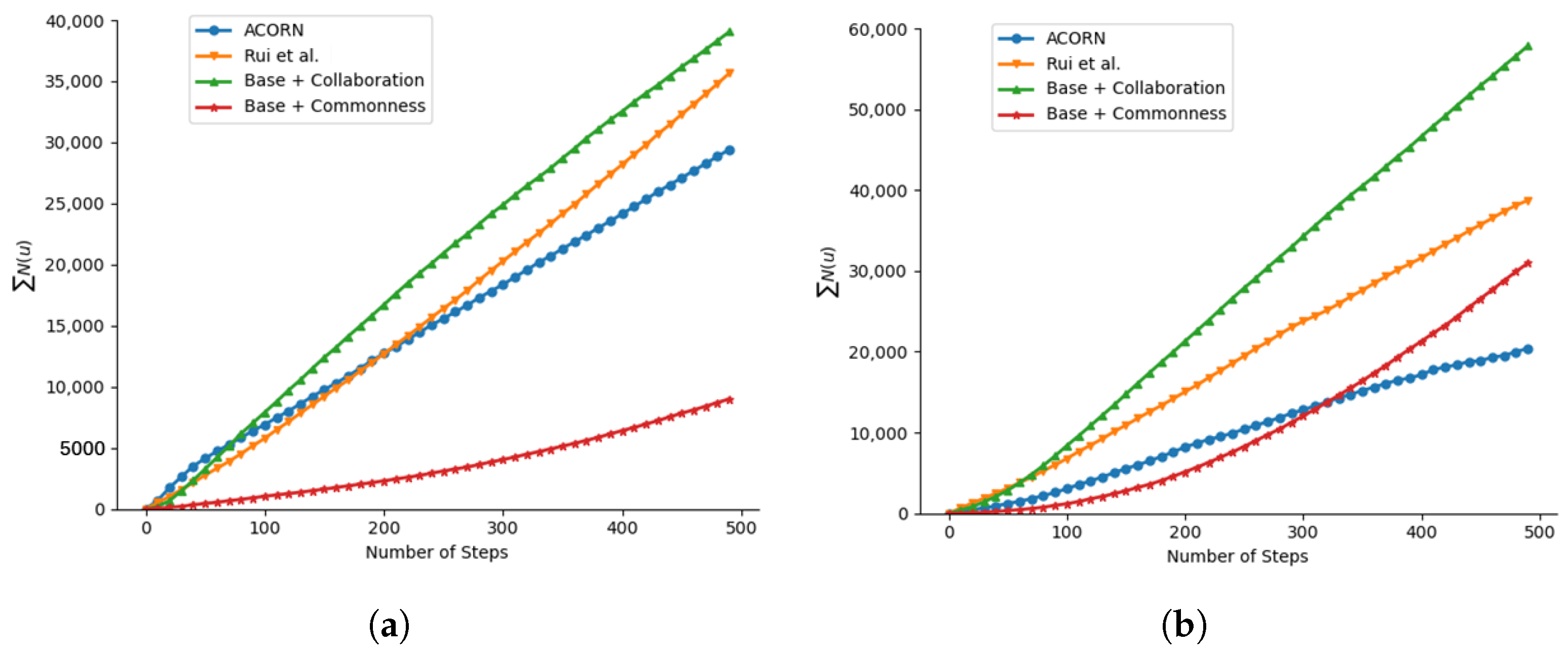
4.3. Influencer Simulation
5. Conclusions and Discussion
- The proposed architecture, combining specialized modules for behavioral modeling and strategic coordination, establishes a viable foundation for simulating advanced social botnets. Experimental results indicate that this dual-module approach enables bots to achieve improved survivability and influence, showing advantages over the baseline methods across multiple detection scenarios.
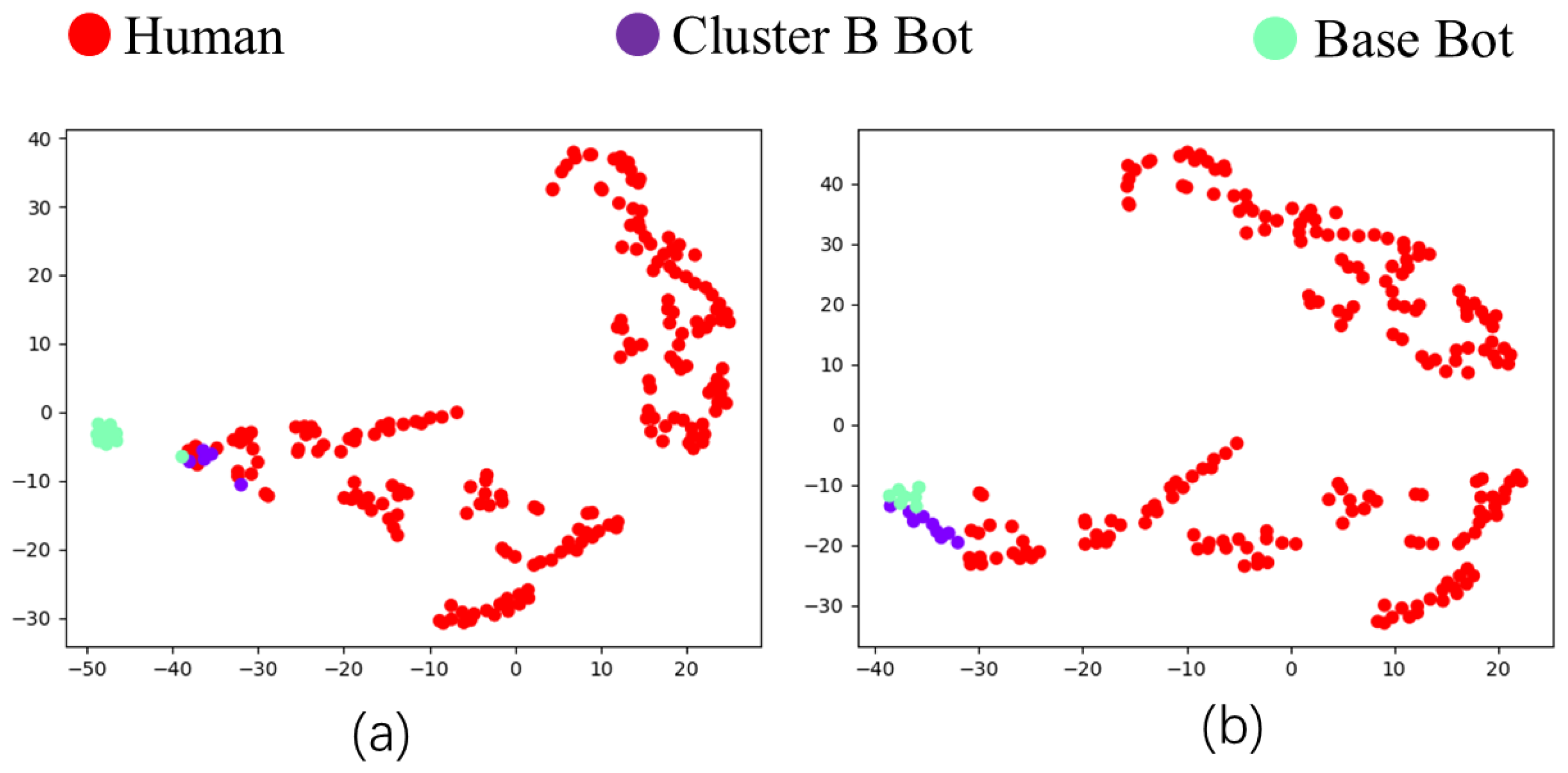
- The proposed reward mechanism based on distributional likelihood shows effectiveness in aligning bot behavior with genuine user patterns. Evaluation through quantitative metrics (e.g., survival rate) and qualitative visualization (t-SNE) suggests that this approach helps reduce detectable behavioral divergence, particularly when emulating low-activity user profiles.
- The collaboration mechanism showed particular effectiveness against advanced detection, with influencer bots achieving an 86.6% survival rate while accumulating substantial influence against the BotRGCN detector. This strategy also contributed to network-wide protection by reducing peer detections, supporting the observation that structured cooperation can aid in evading graph-based detectors.
- While the current human-like behavior module relies on explicit probabilistic modeling of clustered user activities, future iterations could explore more flexible generative paradigms. Energy-based models, for instance, define data likelihood through a scalar energy function without requiring normalized density estimation. This formulation offers enhanced flexibility in capturing multi-modal and non-parametric behavioral distributions, potentially enabling the generation of subtler, less template-driven agent behaviors.
- Another promising extension of this work involves integrating principles from Evolutionary Algorithm-based adversarial training [50,51]. Inspired by this field, the parameters of the behavioral and coordination modules could be encoded as a genome and evolved under iterative adversarial pressure from detection systems. Another key focus would be maintaining strategic diversity throughout this evolutionary process to model a broad range of adaptive threat phenotypes. Such a direction aligns with foundational insights from the evolutionary nature of social bots.
- Building upon the experimental validation within our chosen technical stack, another significant future direction involves establishing a standardized benchmarking framework for adversarial social agent research. While our controlled implementation ensures fair comparisons of algorithmic contributions, cross-framework evaluation remains an open challenge. A constructive path forward is to encapsulate the behavioral and coordination strategies proposed here into a suite of reference agents, enabling systematic evaluation across diverse MARL libraries and swarm systems.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Cresci, S.; Di Pietro, R.; Petrocchi, M.; Spognardi, A.; Tesconi, M. The paradigm-shift of social spambots: Evidence, theories, and tools for the arms race. In Proceedings of the 26th International Conference on World Wide Web Companion, Perth, Australia, 3–7 April 2017; pp. 963–972. [Google Scholar]
- Hajli, N.; Saeed, U.; Tajvidi, M.; Shirazi, F. Social bots and the spread of disinformation in social media: The challenges of artificial intelligence. Br. J. Manag. 2022, 33, 1238–1253. [Google Scholar] [CrossRef]
- Hagen, L.; Neely, S.; Keller, T.E.; Scharf, R.; Vasquez, F.E. Rise of the machines? Examining the influence of social bots on a political discussion network. Soc. Sci. Comput. Rev. 2022, 40, 264–287. [Google Scholar] [CrossRef]
- Feng, S.; Tan, Z.; Wan, H.; Wang, N.; Chen, Z.; Zhang, B.; Zheng, Q.; Zhang, W.; Lei, Z.; Yang, S.; et al. TwiBot-22: Towards graph-based Twitter bot detection. arXiv 2022, arXiv:2206.04564. [Google Scholar]
- Van Der Walt, E.; Eloff, J. Using machine learning to detect fake identities: Bots vs humans. IEEE Access 2018, 6, 6540–6549. [Google Scholar] [CrossRef]
- Wang, L.; Qiao, X.; Xie, Y.; Nie, W.; Zhang, Y.; Liu, A. My brother helps me: Node injection based adversarial attack on social bot detection. In Proceedings of the 31st ACM International Conference on Multimedia, Ottawa, ON, Canada, 29 October–3 November 2023; pp. 6705–6714. [Google Scholar]
- Cresci, S.; Petrocchi, M.; Spognardi, A.; Tognazzi, S. Better safe than sorry: An adversarial approach to improve social bot detection. In Proceedings of the 10th ACM Conference on Web Science, Boston, MA, USA, 30 June–3 July 2019; pp. 47–56. [Google Scholar]
- Le, T.; Tran-Thanh, L.; Lee, D. Socialbots on fire: Modeling adversarial behaviors of socialbots via multi-agent hierarchical reinforcement learning. In Proceedings of the ACM Web Conference 2022, Virtual Event, Lyon, France, 25–29 April 2022; pp. 545–554. [Google Scholar]
- Zeng, X.; Peng, H.; Li, A. Adversarial socialbots modeling based on structural information principles. In Proceedings of the AAAI Conference on Artificial Intelligence, Vancouver, BC, Canada, 20–27 February 2024; Volume 38, pp. 392–400. [Google Scholar]
- Cresci, S.; Di Pietro, R.; Petrocchi, M.; Spognardi, A.; Tesconi, M. Social fingerprinting: Detection of spambot groups through DNA-inspired behavioral modeling. IEEE Trans. Dependable Secur. Comput. 2017, 15, 561–576. [Google Scholar] [CrossRef]
- Abreu, J.V.F.; Fernandes, J.H.C.; Gondim, J.J.C.; Ralha, C.G. Bot development for social engineering attacks on Twitter. arXiv 2020, arXiv:2007.11778. [Google Scholar] [CrossRef]
- Abreu, J.V.F.; Ralha, C.G.; Gondim, J.J.C. Twitter bot detection with reduced feature set. In Proceedings of the 2020 IEEE International Conference on Intelligence and Security Informatics (ISI), Arlington, VA, USA, 9–10 November 2020; pp. 1–6. [Google Scholar]
- Davis, C.A.; Varol, O.; Ferrara, E.; Flammini, A.; Menczer, F. Botornot: A system to evaluate social bots. In Proceedings of the 25th International Conference Companion on World Wide Web, Montréal, QC, Canada, 11–15 April 2016; pp. 273–274. [Google Scholar]
- Ji, Y.; He, Y.; Jiang, X.; Cao, J.; Li, Q. Combating the evasion mechanisms of social bots. Comput. Secur. 2016, 58, 230–249. [Google Scholar] [CrossRef]
- Beskow, D.M.; Carley, K.M. Bot-hunter: A tiered approach to detecting & characterizing automated activity on twitter. In Proceedings of the Conference Paper. SBP-BRiMS: International Conference on Social Computing, Behavioral-Cultural Modeling and Prediction and Behavior Representation in Modeling and Simulation, Washington, DC, USA, 10–13 July 2018; Volume 3. [Google Scholar]
- Varol, O.; Ferrara, E.; Davis, C.; Menczer, F.; Flammini, A. Online human-bot interactions: Detection, estimation, and characterization. In Proceedings of the International AAAI Conference on Web and Social Media, Montreal, QC, Canada, 15–18 May 2017; Volume 11, pp. 280–289. [Google Scholar]
- Yang, K.C.; Varol, O.; Davis, C.A.; Ferrara, E.; Flammini, A.; Menczer, F. Arming the public with artificial intelligence to counter social bots. Hum. Behav. Emerg. Technol. 2019, 1, 48–61. [Google Scholar] [CrossRef]
- Al-Qurishi, M.; Alrubaian, M.; Rahman, S.M.M.; Alamri, A.; Hassan, M.M. A prediction system of Sybil attack in social network using deep-regression model. Future Gener. Comput. Syst. 2018, 87, 743–753. [Google Scholar] [CrossRef]
- Kudugunta, S.; Ferrara, E. Deep neural networks for bot detection. Inf. Sci. 2018, 467, 312–322. [Google Scholar] [CrossRef]
- Heidari, M.; Jones, J.H.; Uzuner, O. Deep contextualized word embedding for text-based online user profiling to detect social bots on twitter. In Proceedings of the 2020 International Conference on Data Mining Workshops (ICDMW), Sorrento, Italy, 17–20 November 2020; pp. 480–487. [Google Scholar]
- Feng, S.; Wan, H.; Wang, N.; Li, J.; Luo, M. Satar: A self-supervised approach to twitter account representation learning and its application in bot detection. In Proceedings of the 30th ACM International Conference on Information & Knowledge Management, Virtual Event, Queensland, Australia, 1–5 November 2021; pp. 3808–3817. [Google Scholar]
- Cardaioli, M.; Conti, M.; Di Sorbo, A.; Fabrizio, E.; Laudanna, S.; Visaggio, C.A. It’sa matter of style: Detecting social bots through writing style consistency. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Loyola-González, O.; Monroy, R.; Rodríguez, J.; López-Cuevas, A.; Mata-Sánchez, J.I. Contrast pattern-based classification for bot detection on twitter. IEEE Access 2019, 7, 45800–45817. [Google Scholar] [CrossRef]
- Wei, F.; Nguyen, U.T. Twitter bot detection using bidirectional long short-term memory neural networks and word embeddings. In Proceedings of the 2019 First IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Los Angeles, CA, USA, 12–14 December 2019; pp. 101–109. [Google Scholar]
- Dukić, D.; Keča, D.; Stipić, D. Are you human? Detecting bots on Twitter Using BERT. In Proceedings of the 2020 IEEE 7th International Conference on Data Science and Advanced Analytics (DSAA), Sydney, NSW, Australia, 6–9 October 2020; pp. 631–636. [Google Scholar]
- Martín-Gutiérrez, D.; Hernández-Peñaloza, G.; Hernández, A.B.; Lozano-Diez, A.; Álvarez, F. A deep learning approach for robust detection of bots in twitter using transformers. IEEE Access 2021, 9, 54591–54601. [Google Scholar] [CrossRef]
- Jia, J.; Wang, B.; Gong, N.Z. Random walk based fake account detection in online social networks. In Proceedings of the 2017 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Denver, CO, USA, 26–29 June 2017; pp. 273–284. [Google Scholar]
- Breuer, A.; Eilat, R.; Weinsberg, U. Friend or faux: Graph-based early detection of fake accounts on social networks. In Proceedings of the Web Conference 2020, Taipei, Taiwan, 20–24 April 2020; pp. 1287–1297. [Google Scholar]
- Ali Alhosseini, S.; Bin Tareaf, R.; Najafi, P.; Meinel, C. Detect me if you can: Spam bot detection using inductive representation learning. In Proceedings of the Companion Proceedings of the 2019 World Wide Web Conference, San Francisco, CA, USA, 13–17 May 2019; pp. 148–153. [Google Scholar]
- Feng, S.; Tan, Z.; Li, R.; Luo, M. Heterogeneity-aware twitter bot detection with relational graph transformers. In Proceedings of the AAAI Conference on Artificial Intelligence, Virtually, 22 February–1 March 2022; Volume 36, pp. 3977–3985. [Google Scholar]
- Liu, Y.; Tan, Z.; Wang, H.; Feng, S.; Zheng, Q.; Luo, M. Botmoe: Twitter bot detection with community-aware mixtures of modal-specific experts. In Proceedings of the 46th International ACM SIGIR Conference on Research and Development in Information Retrieval, Taipei, Taiwan, 23–27 July 2023; pp. 485–495. [Google Scholar]
- Yang, Y.; Yang, R.; Li, Y.; Cui, K.; Yang, Z.; Wang, Y.; Xu, J.; Xie, H. Rosgas: Adaptive social bot detection with reinforced self-supervised gnn architecture search. ACM Trans. Web 2023, 17, 1–31. [Google Scholar] [CrossRef]
- He, B.; Yang, Y.; Wu, Q.; Liu, H.; Yang, R.; Peng, H.; Wang, X.; Liao, Y.; Zhou, P. Botdgt: Dynamicity-aware social bot detection with dynamic graph transformers. arXiv 2024, arXiv:2404.15070. [Google Scholar]
- Feng, S.; Wan, H.; Wang, N.; Luo, M. BotRGCN: Twitter bot detection with relational graph convolutional networks. In Proceedings of the 2021 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, Virtual Event, The Netherlands, 8–11 November 2021; pp. 236–239. [Google Scholar]
- Cai, Z.; Tan, Z.; Lei, Z.; Zhu, Z.; Wang, H.; Zheng, Q.; Luo, M. LMbot: Distilling graph knowledge into language model for graph-less deployment in twitter bot detection. In Proceedings of the 17th ACM International Conference on Web Search and Data Mining, Merida, Mexico, 4–8 March 2024; pp. 57–66. [Google Scholar]
- Jin, R.; Liao, Y. Prevention Is Better than Cure: Exposing the Vulnerabilities of Social Bot Detectors with Realistic Simulations. Appl. Sci. 2025, 15, 6230. [Google Scholar] [CrossRef]
- Gao, C.; Lan, X.; Lu, Z.; Mao, J.; Piao, J.; Wang, H.; Jin, D.; Li, Y. S3: Social-network Simulation System with Large Language Model-Empowered Agents. arXiv 2023, arXiv:2307.14984. [Google Scholar] [CrossRef]
- Feng, S.; Wan, H.; Wang, N.; Tan, Z.; Luo, M.; Tsvetkov, Y. What Does the Bot Say? Opportunities and Risks of Large Language Models in Social Media Bot Detection. arXiv 2024, arXiv:2402.00371. [Google Scholar] [CrossRef]
- Liu, Y.; Ott, M.; Goyal, N.; Du, J.; Joshi, M.; Chen, D.; Levy, O.; Lewis, M.; Zettlemoyer, L.; Stoyanov, V. Roberta: A robustly optimized bert pretraining approach. arXiv 2019, arXiv:1907.11692. [Google Scholar]
- Cullen, A.C.; Frey, H.C. Probabilistic Techniques in Exposure Assessment: A Handbook for Dealing with Variability and Uncertainty in Models and Inputs; Springer Science & Business Media: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Delignette-Muller, M.L.; Dutang, C. fitdistrplus: An R package for fitting distributions. J. Stat. Softw. 2015, 64, 1–34. [Google Scholar] [CrossRef]
- Sklar, A. Random variables, joint distribution functions, and copulas. Kybernetika 1973, 9, 449–460. [Google Scholar]
- Standen, M.; Kim, J.; Szabo, C. Adversarial machine learning attacks and defences in multi-agent reinforcement learning. ACM Comput. Surv. 2025, 57, 1–35. [Google Scholar] [CrossRef]
- Ghosh, S.; Chen, T.; Wu, W. Enhanced group influence maximization in social networks using deep reinforcement learning. IEEE Trans. Comput. Soc. Syst. 2024, 12, 573–585. [Google Scholar] [CrossRef]
- McPherson, M.; Smith-Lovin, L.; Cook, J.M. Birds of a feather: Homophily in social networks. Annu. Rev. Sociol. 2001, 27, 415–444. [Google Scholar] [CrossRef]
- Granovetter, M.S. The strength of weak ties. Am. J. Sociol. 1973, 78, 1360–1380. [Google Scholar] [CrossRef]
- Yang, Z.; Chen, X.; Wang, H.; Wang, W.; Miao, Z.; Jiang, T. A new joint approach with temporal and profile information for social bot detection. Secur. Commun. Netw. 2022, 2022, 9119388. [Google Scholar] [CrossRef]
- Terry, J.; Black, B.; Grammel, N.; Jayakumar, M.; Hari, A.; Sullivan, R.; Santos, L.S.; Dieffendahl, C.; Horsch, C.; Perez-Vicente, R.; et al. Pettingzoo: Gym for multi-agent reinforcement learning. Adv. Neural Inf. Process. Syst. 2021, 34, 15032–15043. [Google Scholar]
- Raffin, A.; Hill, A.; Gleave, A.; Kanervisto, A.; Ernestus, M.; Dormann, N. Stable-Baselines3: Reliable Reinforcement Learning Implementations. J. Mach. Learn. Res. 2021, 22, 1–8. [Google Scholar]
- Wang, C.; Xu, C.; Yao, X.; Tao, D. Evolutionary generative adversarial networks. IEEE Trans. Evol. Comput. 2019, 23, 921–934. [Google Scholar] [CrossRef]
- Dang, Q.; Zhang, G.; Wang, L.; Yang, S.; Zhan, T. A generative adversarial networks model based evolutionary algorithm for multimodal multi-objective optimization. IEEE Trans. Emerg. Top. Comput. Intell. 2024, early access. [Google Scholar] [CrossRef]

| Setting | Bot Strategy | Cluster A | Cluster B | ||
|---|---|---|---|---|---|
| Survival Rate | Avg. Bot Score | Survival Rate | Avg. Bot Score | ||
| Fake account & RF detector | ACORN [8] | 86.7% | 0.410 (0.014) | - | - |
| Rui et al. [36] | 99.0% | 0.354 (0.013) | - | - | |
| Base | 96.7% | 0.403 (0.007) | - | - | |
| Base + Collaboration | 100.0% | 0.404 (0.012) | - | - | |
| Base + Commonness | 99.9% | 0.436 (0.010) | 76.6% | 0.437 (0.024) | |
| Full | 98.2% | 0.418 (0.016) | 98.0% | 0.433 (0.009) | |
| Fake account & BotRGCN | ACORN [8] | 58.5% | 0.082 (0.084) | - | - |
| Rui et al. [36] | 85.9% | 0.115 (0.063) | - | - | |
| Base | 75.3% | 0 (0) | - | - | |
| Base + Collaboration | 73.6% | 0 (0) | - | - | |
| Base + Commonness | 99.1% | 0.076 (0.048) | 86.4% | 0.065 (0.078) | |
| Full | 93.6% | 0.114 (0.072) | 75.6% | 0.053 (0.077) | |
| Setting | Bot Strategy | Survival Rate | Avg. Bot Score | ||
|---|---|---|---|---|---|
| Influencer & RF detector | ACORN [8] | 65.4% | 0.382 (0.015) | 29,942 (8.057) | 7,595,250 (1845.121) |
| Rui et al. [36] | 97.9% | 0.359 (0.014) | 36,320 (8.042) | 7,878,764 (2016.605) | |
| Base | 100.0% | 0.409 (0.014) | 38,108 (3.888) | 8,071,728 (970.661) | |
| Base + Collaboration | 99.4% | 0.393 (0.014) | 39,144 (4.603) | 9,056,252 (1325.422) | |
| Base + Commonness | 96.3% | 0.419 (0.015) | 9004 (2.650) | 316,150 (143.870) | |
| Full | 96.0% | 0.418 (0.015) | 16,496 (3.051) | 809,716 (192.503) | |
| Influencer & BotRGCN | ACORN [8] | 34.1% | 0.009 (0.054) | 20,874 (7.366) | 4,335,142 (2374.298) |
| Rui et al. [36] | 60.0% | 0.002 (0.041) | 39,542 (8.030) | 8,932,088 (2629.436) | |
| Base | 62.2% | 0 (0) | 38,690 (5.735) | 8,377,174 (1669.028) | |
| Base + Collaboration | 86.6% | 0 (0) | 57,388 (5.758) | 12,903,272 (1671.150) | |
| Base + Commonness | 92.2% | 0.011 (0.039) | 30,962 (10.889) | 4,754,262 (2307.996) | |
| Full | 50.4% | 0.002 (0.012) | 17,364 (8.324) | 2,401,084 (1939.262) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.
Share and Cite
Jin, R.; Liao, Y. Simulating Advanced Social Botnets: A Framework for Behavior Realism and Coordinated Stealth. Information 2026, 17, 27. https://doi.org/10.3390/info17010027
Jin R, Liao Y. Simulating Advanced Social Botnets: A Framework for Behavior Realism and Coordinated Stealth. Information. 2026; 17(1):27. https://doi.org/10.3390/info17010027
Chicago/Turabian StyleJin, Rui, and Yong Liao. 2026. "Simulating Advanced Social Botnets: A Framework for Behavior Realism and Coordinated Stealth" Information 17, no. 1: 27. https://doi.org/10.3390/info17010027
APA StyleJin, R., & Liao, Y. (2026). Simulating Advanced Social Botnets: A Framework for Behavior Realism and Coordinated Stealth. Information, 17(1), 27. https://doi.org/10.3390/info17010027





