Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings
Abstract
1. Introduction
1.1. Comprehensive Definition of Hajj
1.2. Objectives and Contributions of the Research Work
- i.
- State-of-the-art scalability techniques: Implement new scalability solutions tailored to blockchain systems in transportation, ensuring the transportation system can handle a high volume of transactions.
- ii.
- Mathematical model for throughput optimization: Develop a model that maximizes work integration for peak loads while ensuring high availability and reliability during large-scale events.
- iii.
- Comprehensive security mechanisms: This is a critical examination of blockchain’s security features to protect against cyberattacks and ensure users’ privacy in crowded settings, such as the Hajj.
- iv.
- Real-world application focus: This research is more application-based, emphasizing the issues of mass gathering, where Hajj is considered for piloting the solutions developed.
1.3. Problem Statement
1.4. Scalability and Security in Blockchain
2. Literature Review
Novelty of Our Study
3. Methodology
3.1. Experimental Design and Implementation
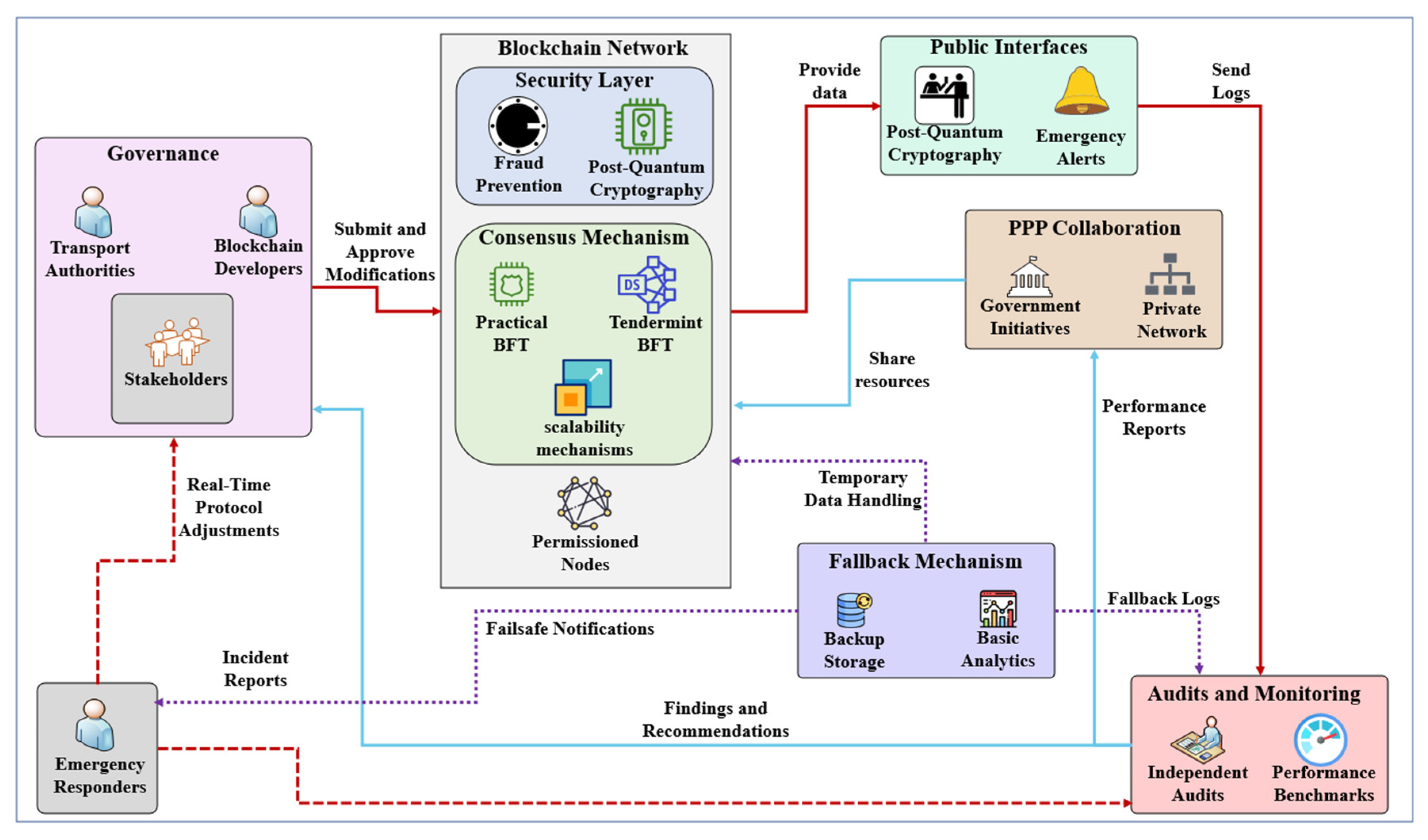
3.2. Strengthen Security and Trust Governance
3.3. Compliance with Data Protection Regulation
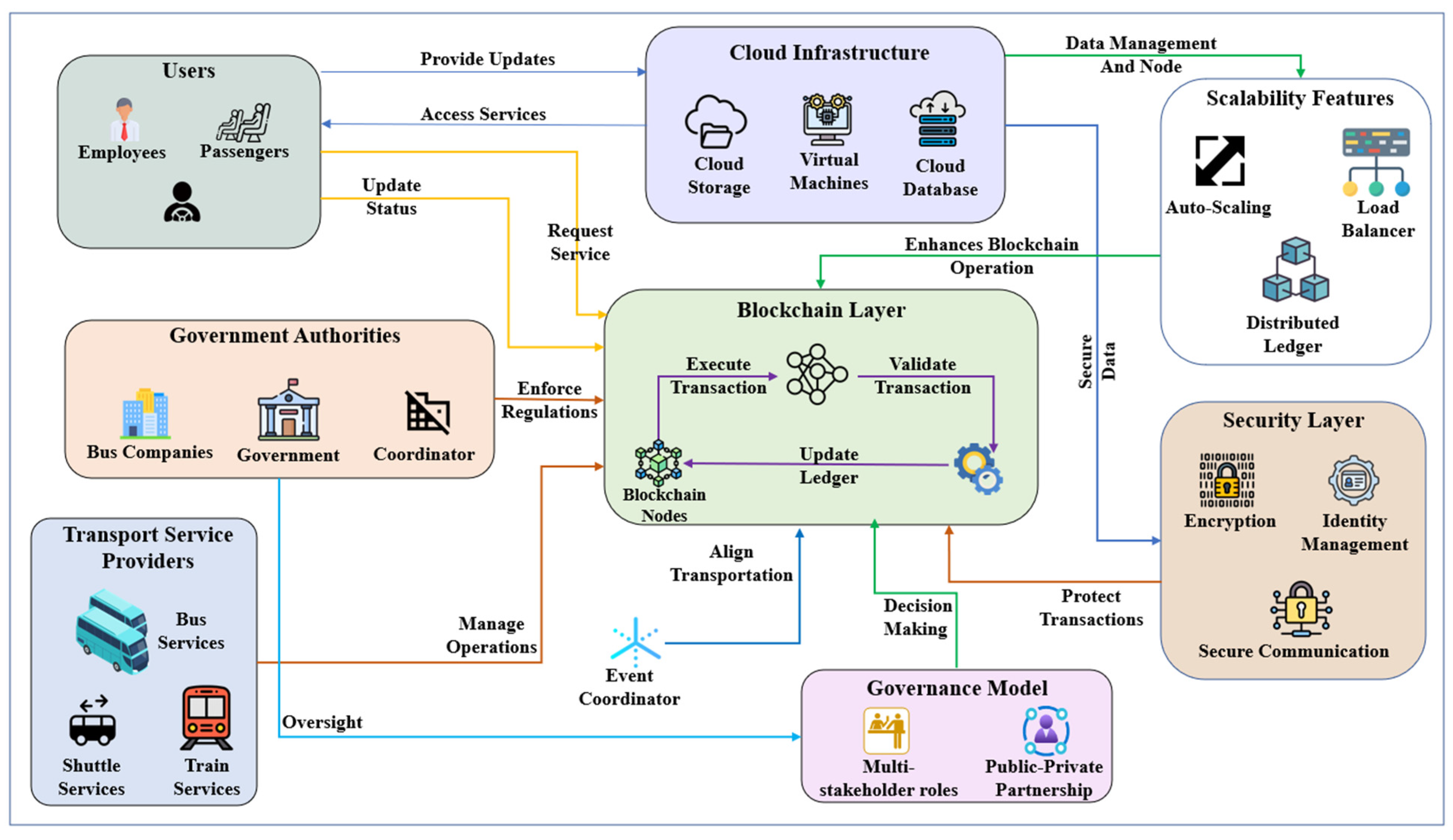
3.4. Model Architecture
3.5. Mathematical Model for Scalability in Blockchain-Based Transportation System
3.6. Mathematical Model for Throughput and Latency
- i.
- Mathematical Model
- ii.
- Throughput Model
- iii.
- Latency Model
4. Results and Findings
4.1. Scalability Analysis
4.2. Proposed System’s Performance
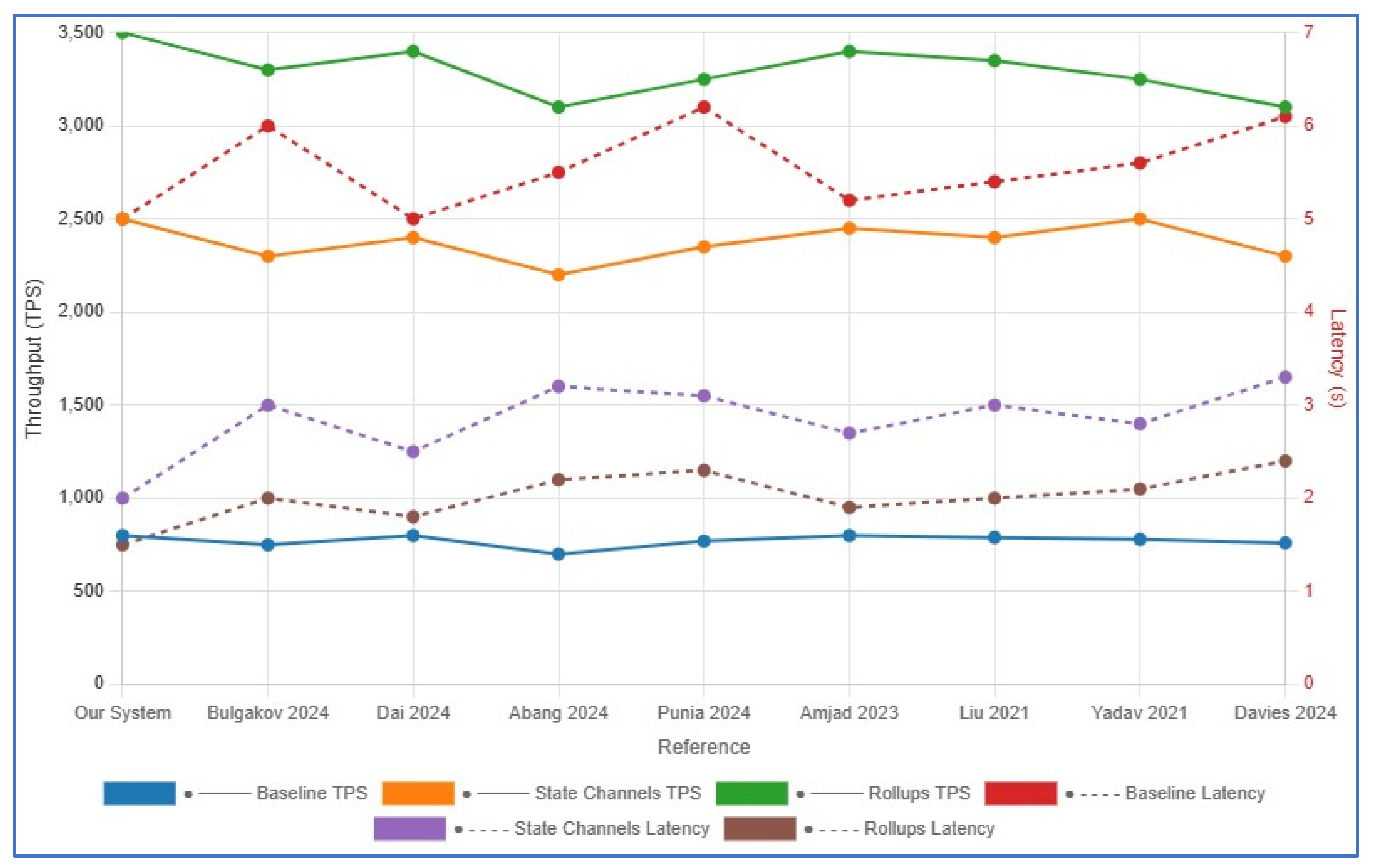
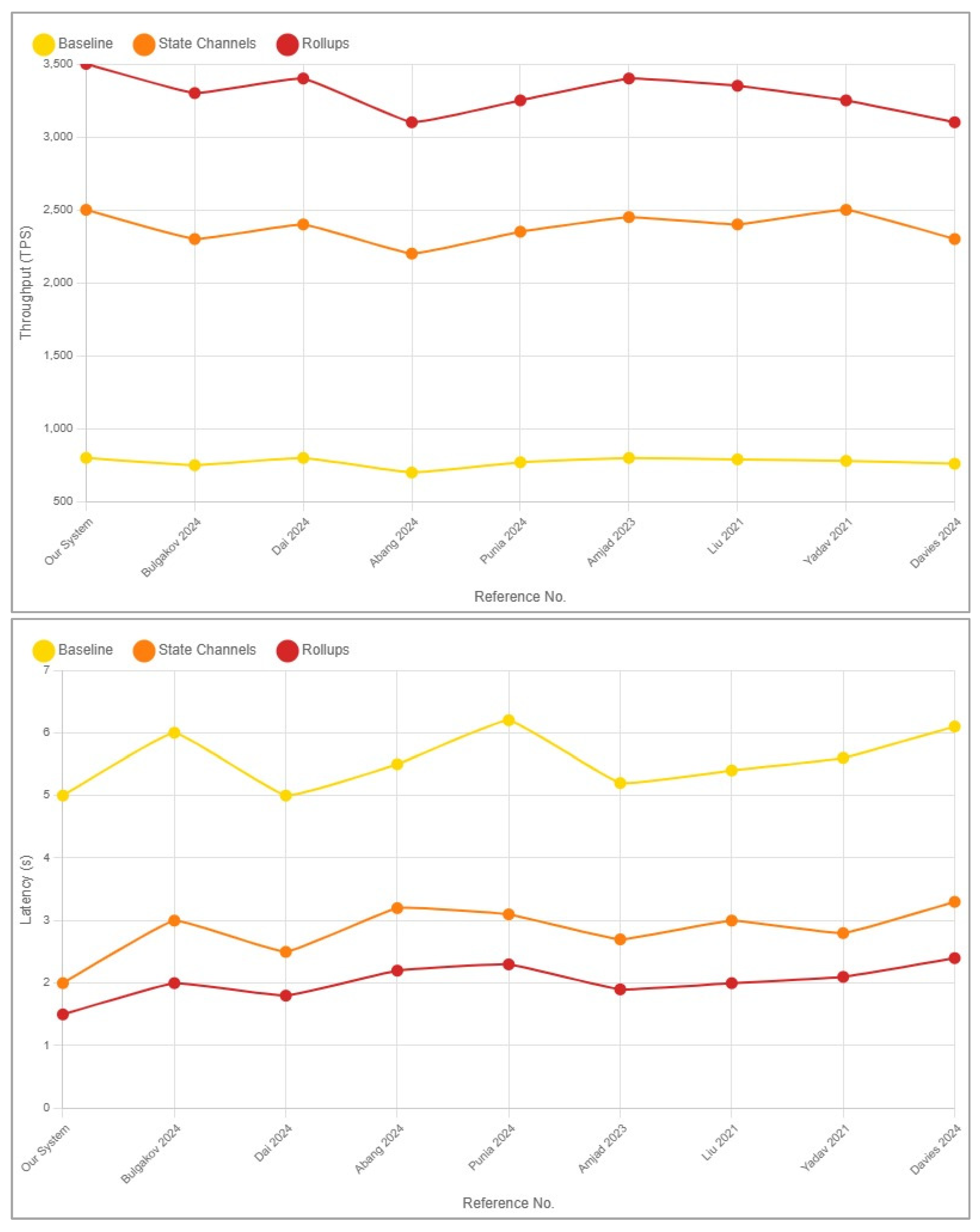
4.3. Comparison with References
4.4. Statistical Validation of Performance Metrics
- i.
- Hypothesis Formulation
- ii.
- ANOVA Test for Throughput (TPS)
- iii.
- ANOVA Test for Latency (s)
- Mean latency for baseline
- Mean latency for State Channels
- Mean latency for Rollups
- Overall Mean:
4.5. Comparative Analysis Methodology
4.6. Comparing the Cost of the Proposed System with Other References
4.7. Security Analysis
Security Metric Comparative Analysis
4.8. Performance Metrics: CPU Usage, Memory Consumption, and Testing Time
- i.
- CPU Usage
| Scenario | CPU Usage (%) | Memory Consumption (GB) | Testing Time (Minutes) |
|---|---|---|---|
| Proposed System | 15–18 | 4 | 10 |
| [33] | 20–25 | 4.5–6.0 | 20 |
| [34] | 22–26 | 5.0–6.5 | 18 |
| [35] | 25–30 | 5.0–7.0 | 22 |
| [36] | 28–32 | 5.5–7.0 | 25 |
| [37] | 22–25 | 5.0–5.5 | 20 |
| [38] | 25–28 | 5.0–6.5 | 20 |
| [39] | 25–30 | 5.0–5.5 | 22 |
| [40] | 28–32 | 5.5–7.5 | 23 |
- ii.
- Memory Consumption
- iii.
- Testing Time
4.9. Case Studies Validating the Proposed System
- i.
- The Olympic Games: Streamlining Transportation with Blockchain
- ii.
- The Super Bowl: Enhancing Security and Crowd Flow
5. Discussion
5.1. Practitioner Implications
5.2. Enhancing Novelty and Contribution
5.3. Limitations and Future Research Directions
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Basahel, S.; Alsabban, A.; Yamin, M. Hajj and Umrah management during COVID-19. Int. J. Inf. Technol. 2021, 13, 2491–2495. [Google Scholar] [CrossRef] [PubMed]
- Badshah, A.; Abbas, G.; Waqas, M.; Muhammad, F.; Abbas, Z.H.; Bilal, M.; Song, H. Blockchain-Assisted Lightweight Authenticated Key Agreement Security Framework for Smart Vehicles-Enabled Intelligent Transportation System. IEEE Trans. Autom. Sci. Eng. 2024, 21, 2425–2439. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Kumar, N.; Hassan, M.M. A Privacy-Preserving-Based Secure Framework Using Blockchain-Enabled Deep-Learning in Cooperative Intelligent Transport System. IEEE Trans. Intell. Transp. Syst. 2022, 23, 16492–16503. [Google Scholar] [CrossRef]
- Gazzawe, F.; Albahar, M. Reducing traffic congestion in makkah during Hajj through the use of AI technology. Heliyon 2024, 10, e23304. [Google Scholar] [CrossRef] [PubMed]
- Çaldağ, M.T.; Gökalp, E. Exploring Critical Success Factors for Blockchain-based Intelligent Transportation Systems. Emerg. Sci. J. 2020, 4, 27–44. [Google Scholar] [CrossRef]
- Geng, X.; Wen, Y.; Mo, Z.; Dong, P.; Kong, F.; Xiong, K. On the Evaluation Framework of Comprehensive Trust for Data Interaction in Intermodal Transport. Electronics 2024, 13, 1487. [Google Scholar] [CrossRef]
- Tayal, A.; Solanki, A.; Kondal, R.; Nayyar, A.; Tanwar, S.; Kumar, N. Blockchain-based efficient communication for food supply chain industry: Transparency and traceability analysis for sustainable business. Int. J. Commun. Syst. 2021, 34, e4696. [Google Scholar] [CrossRef]
- Kravenkit, S.; So-In, C. Blockchain-Based Traceability System for Product Recall. IEEE Access 2022, 10, 95132–95150. [Google Scholar] [CrossRef]
- Taherdoost, H. A Critical Review of Blockchain Acceptance Models—Blockchain Technology Adoption Frameworks and Applications. Computers 2022, 11, 24. [Google Scholar] [CrossRef]
- Agrawal, T.K.; Kumar, V.; Pal, R.; Wang, L.; Chen, Y. Blockchain-based framework for supply chain traceability: A case ex-ample of textile and clothing industry. Comput. Ind. Eng. 2021, 154, 107130. [Google Scholar] [CrossRef]
- Mandourah, A.; Yamin, M. Using Blockchain Technology to Manage Hajj and Umrah. In Proceedings of the 2022 9th Inter-national Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 23–25 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 870–875. [Google Scholar] [CrossRef]
- Khanzada, T.J.S.; Shahid, M.F.; Mutahhar, A.; Aslam, M.A.; Ashari, R.B.; Jamal, S.; Nooruddin, M.; Siddiqui, S. Authenticity, and Approval Framework for Bus Transportation Based on Blockchain 2.0 Technology. Appl. Sci. 2023, 13, 11323. [Google Scholar] [CrossRef]
- Haleem, A.; Javaid, M.; Singh, R.P.; Suman, R.; Rab, S. Blockchain technology applications in healthcare: An overview. Int. J. Intell. Netw. 2021, 2, 130–139. [Google Scholar] [CrossRef]
- Jabbar, R.; Dhib, E.; Said, A.B.; Krichen, M.; Fetais, N.; Zaidan, E.; Barkaoui, K. Blockchain Technology for Intelligent Trans-portation Systems: A Systematic Literature Review. IEEE Access 2022, 10, 20995–21031. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. 2016. [Google Scholar]
- Derhab, A.; Mohiuddin, I.; Halboob, W.; Almuhtadi, J. Crowd Congestion Forecasting Framework Using Ensemble Learning Model and Decision Making Algorithm: Umrah Use Case. IEEE Access 2024, 12, 67453–67469. [Google Scholar] [CrossRef]
- Ruiters, C.; Amadi-Echendu, J. Public–private partnerships as investment models for water infrastructure in South Africa. Infrastruct. Asset Manag. 2022, 9, 180–193. [Google Scholar] [CrossRef]
- Zapoglou, N.; Patsakos, I.; Drosatos, G.; Rantos, K. Privacy-Preserving Blockchain-Based Solutions in the Internet of Things. In International Summit Smart City 360°; Springer International Publishing: Cham, Switzerland, 2021; pp. 386–405. [Google Scholar] [CrossRef]
- Hossain, M.D.; Mamun, Q.; Islam, R. A Comparative Study on Permissioned Based Blockchain Implementation on Healthcare Data: From Security and Privacy Perspective. In Proceedings of the 2024 IEEE International Conference on Future Machine Learning and Data Science (FMLDS), Sydney, Australia, 20–23 November 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 222–227. [Google Scholar] [CrossRef]
- Al Sibahee, M.A.; Abduljabbar, Z.A.; Ngueilbaye, A.; Luo, C.; Li, J.; Huang, Y.; Zhang, J.; Khan, N.; Nyangaresi, V.O.; Ali, A.H. Blockchain-Based Authentication Schemes in Smart Environments: A Systematic Literature Review. IEEE Internet Things J. 2024, 11, 34774–34796. [Google Scholar] [CrossRef]
- Dar, A.A.; Reegu, F.A.; Hussain, G. Comprehensive Analysis of Enterprise Blockchain: Hyperledger Fabric/Corda/Quorom: Three Different Distributed Leger Technologies for Business. In Mobile Radio Communications & 5G Networks; Springer Nature: Singapore, 2024; pp. 383–395. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Chen, K.; Liu, X. Privacy-preserving and efficient data sharing for blockchain-based intelligent transportation systems. Inf. Sci. 2023, 635, 72–85. [Google Scholar] [CrossRef]
- Box, G.E.P.; Jenkins, G.M.; Reinsel, G.C.; Ljung, G.M. Time Series Analysis: Forecasting and Control, 5th ed.; John Wiley & Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Antonopoulos, A.; Wood, G. Mastering Ethereum: Building Smart Contracts and Dapps; O’reilly: Beijing, China; Boston, MA, USA; Farnham, UK; Tokyo, Japan, 2019. [Google Scholar]
- Tanenbaum, A.S.; Van Steen, M. Distributed Systems: Principles and Paradigms; Pearson: London, UK, 2017. [Google Scholar]
- Silberschatz, A.; Galvin, P.B.; Gagne, G. Operating System Concepts, 10th ed.; John Wiley & Sons: Hoboken, NJ, USA, 2018. [Google Scholar]
- Liu, C.L.; Layland, J.W. Scheduling Algorithms for Multiprogramming in a Hard-Real-Time Environment. J. ACM 1973, 20, 46–61. [Google Scholar] [CrossRef]
- Kurose, J.F.; Ross, K.W. Computer Networking: A Top-Down Approach, 8th ed.; Pearson: London, UK, 2021. [Google Scholar]
- Hennessy, J.L.; Patterson, D.A. Computer Architecture: A Quantitative Approach, 6th ed.; Morgan Kaufmann: Burlington, MA, USA, 2019. [Google Scholar]
- Stallings, W.; Brown, L. Computer Security: Principles and Practice, 4th ed.; Pearson: London, UK, 2018. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. In Bitcoin.Org. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 April 2025).
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Ethereum Project Yellow Paper. April 2014, pp. 1–32. Available online: https://files.gitter.im/ethereum/yellowpaper/VIyt/Paper.pdf (accessed on 1 April 2025).
- Bulgakov, A.L.; Aleshina, A.V.; Smirnov, S.D.; Demidov, A.D.; Milyutin, M.A.; Xin, Y. Scalability and Security in Blockchain Networks: Evaluation of Sharding Algorithms and Prospects for Decentralized Data Storage. Mathematics 2024, 12, 3860. [Google Scholar] [CrossRef]
- Dai, Y.; Lu, G.; Huang, Y. A Blockchain-Based Access Control System for Secure and Efficient Hazardous Material Supply Chains. Mathematics 2024, 12, 2702. [Google Scholar] [CrossRef]
- Abang, J.E.; Takruri, H.; Al-Zaidi, R.; Al-Khalidi, M. Latency performance modelling in hyperledger fabric blockchain: Challenges and directions with an IoT perspective. Internet Things 2024, 26, 101217. [Google Scholar] [CrossRef]
- Punia, A.; Gulia, P.; Gill, N.S.; Ibeke, E.; Iwendi, C.; Shukla, P.K. A systematic review on blockchain-based access control systems in cloud environment. J. Cloud Comput. 2024, 13, 146. [Google Scholar] [CrossRef]
- Amjad, M.; Taylor, G.; Huang, Z.; Li, M.; Lai, C.S. Performance Optimization of a Blockchain-Enabled Information and Data Exchange Platform for Smart Grids. Electronics 2023, 12, 1405. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, J.; Wang, J.; Liu, T.; He, X. BSS-ITS: Blockchain Scaling Scheme with Sharding for Intelligent Transportation System. In Proceedings of the 2021 4th International Conference on Blockchain Technology and Applications, Xi’an, China, 17–19 December 2021; ACM: New York, NY, USA, 2021; pp. 128–134. [Google Scholar] [CrossRef]
- Yadav, J.; Shevkar, R. Performance-Based Analysis of Blockchain Scalability Metric. Teh. Glas. 2021, 15, 133–142. [Google Scholar] [CrossRef]
- Davies, J. Enhanced scalability and privacy for blockchain data using Merklized transactions. Front. Blockchain 2024, 6, 1222614. [Google Scholar] [CrossRef]
- Sousa, J.; Bessani, A.; Vukolic, M. A Byzantine Fault-Tolerant Ordering Service for the Hyperledger Fabric Blockchain Platform. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 51–58. [Google Scholar] [CrossRef]
- Xiao, K.; Li, J.; He, Y.; Wang, X.; Wang, C. A secure multi-party payment channel on-chain and off-chain supervisable scheme. Future Gener. Comput. Syst. 2024, 154, 330–343. [Google Scholar] [CrossRef]
- Montgomery, D.C. Design and Analysis of Experiments, 9th ed.; John Wiley & Sons: Hoboken, NJ, USA, 2017. [Google Scholar]
- Koutsandreas, D.; Trachanas, G.P.; Pappis, I.; Nikas, A.; Doukas, H.; Psarras, J. A multicriteria modeling approach for evalu-ating power generation scenarios under uncertainty: The case of green hydrogen in Greece. Energy Strategy Rev. 2023, 50, 101233. [Google Scholar] [CrossRef]
- Dworkin, M.J. SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. 2015. Available online: https://www.nist.gov/publications/sha-3-standard-permutation-based-hash-and-extendable-output-functions (accessed on 4 August 2015).
- Khoshavi, N.; Tristani, G.; Sargolzaei, A. Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey. Electronics 2021, 10, 629. [Google Scholar] [CrossRef]
- Felemban, E.A.; Rehman, F.U.; Biabani, S.A.A.; Ahmad, A.; Naseer, A.; Majid, A.R.M.A.; Hussain, O.K.; Qamar, A.M.; Falemban, R.; Zanjir, F. Digital Revolution for Hajj Crowd Management: A Technology Survey. IEEE Access 2020, 8, 208583–208609. [Google Scholar] [CrossRef]
- Russo, E.; Figueira, A.R.; Kogut, C.S.; Mello, R.D.C.D.E. The Tokyo 2020 Olympic Games: Impacts of COVID-19 and digital transformation. Cad. EBAPE.BR 2022, 20, 318–332. [Google Scholar] [CrossRef]
- Carroll, B. Super Bowl|History & Results. In Encyclopædia Britannica. Available online: https://www.britannica.com/sports/Super-Bowl (accessed on 1 May 2025).
- Ben-Sasson, E.; Chiesa, A.; Tromer, E.; Virza, M. Scalable Zero Knowledge via Cycles of Elliptic Curves. In Advances in Cryptology–CRYPTO 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 276–294. [Google Scholar] [CrossRef]
- Buterin, V.; Foundation, E. An Introduction to ZK-Rollups. Ethereum Blog. Available online: https://ethereum.org/en/developers/docs/scaling/zk-rollups/ (accessed on 1 May 2025).
- Nasser, N.; el Ouadrhiri, A.; el Kamili, M.; Ali, A.; Anan, M. Crowd Management Services in Hajj: A Mean-Field Game Theory Approach. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. In Proceedings of the Third Symposium on Operating Systems Design and Implementation, New Orleans, LA, USA, 22–25 February 1999; pp. 343–359. [Google Scholar]
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef] [PubMed]
- Thibault, L.T.; Sarry, T.; Hafid, A.S. Blockchain Scaling Using Rollups: A Comprehensive Survey. IEEE Access 2022, 10, 93039–93054. [Google Scholar] [CrossRef]
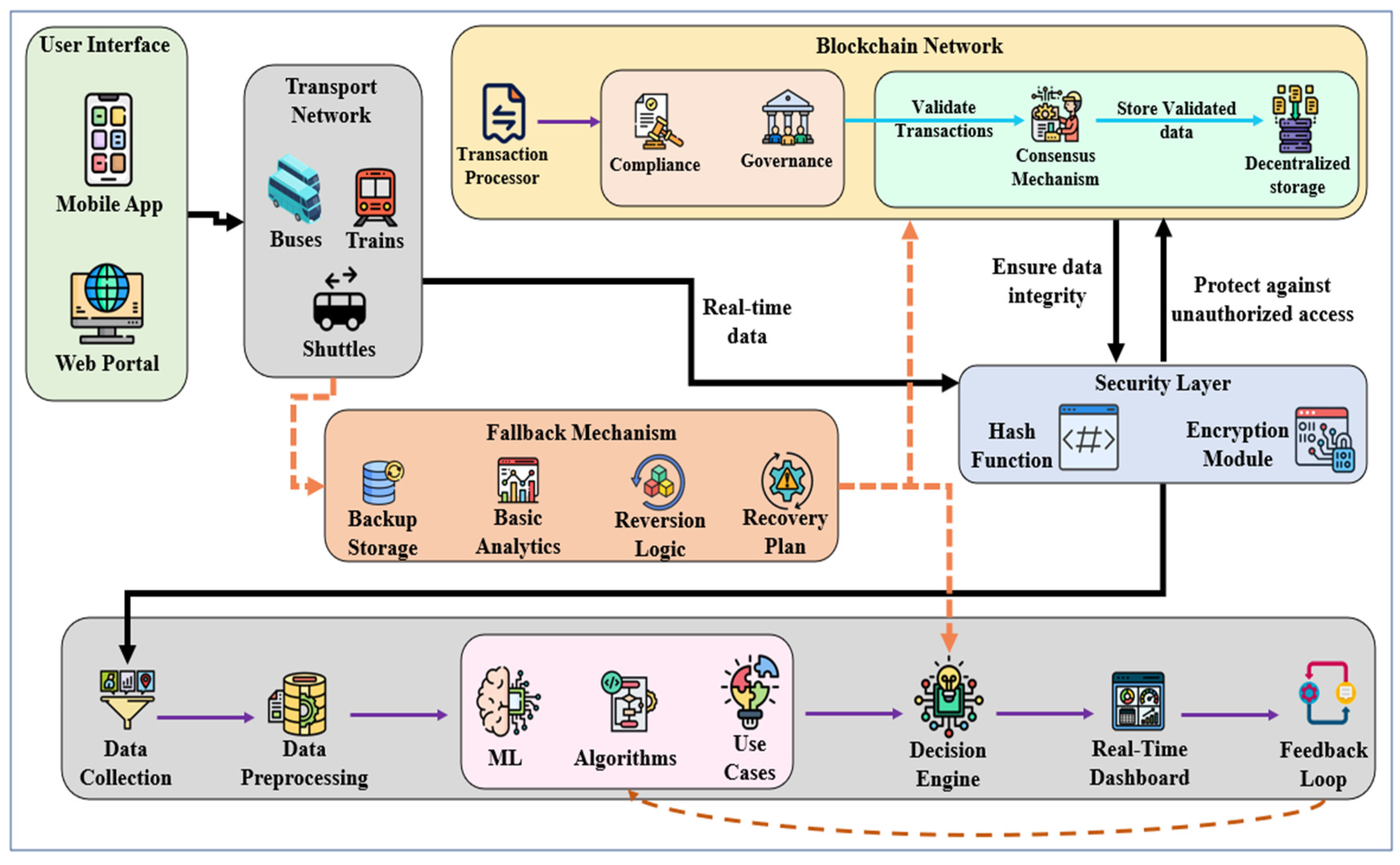
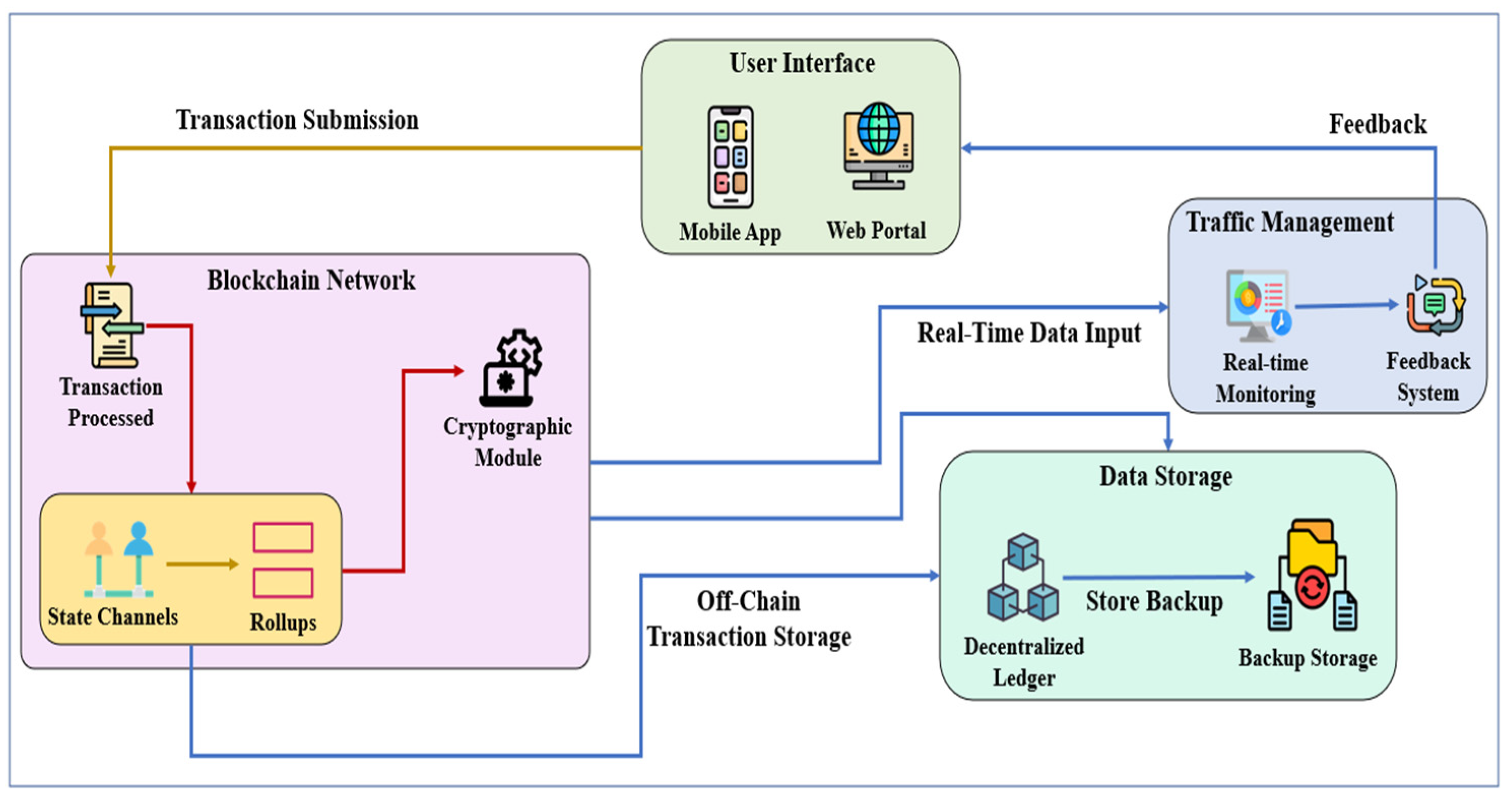
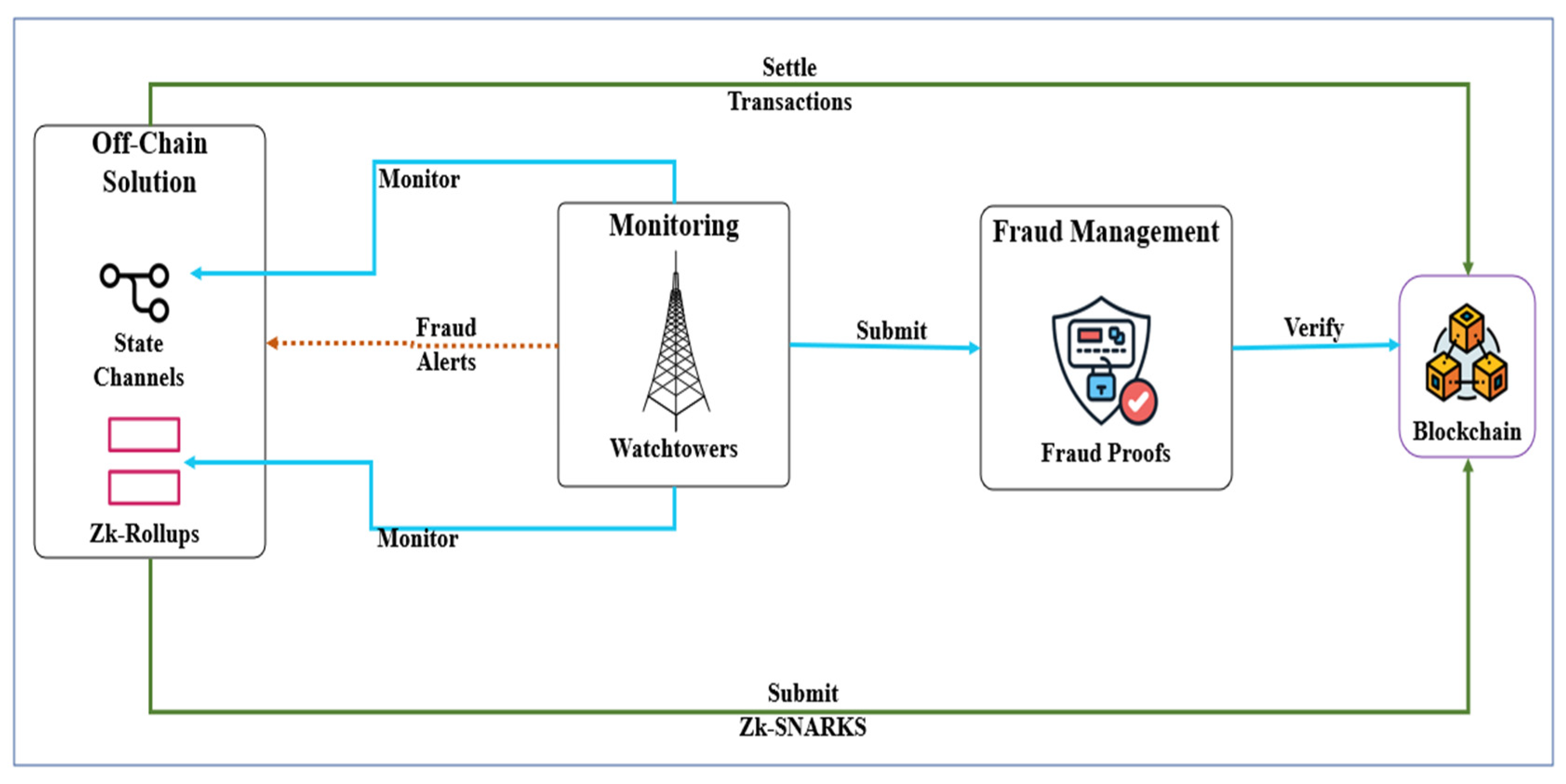
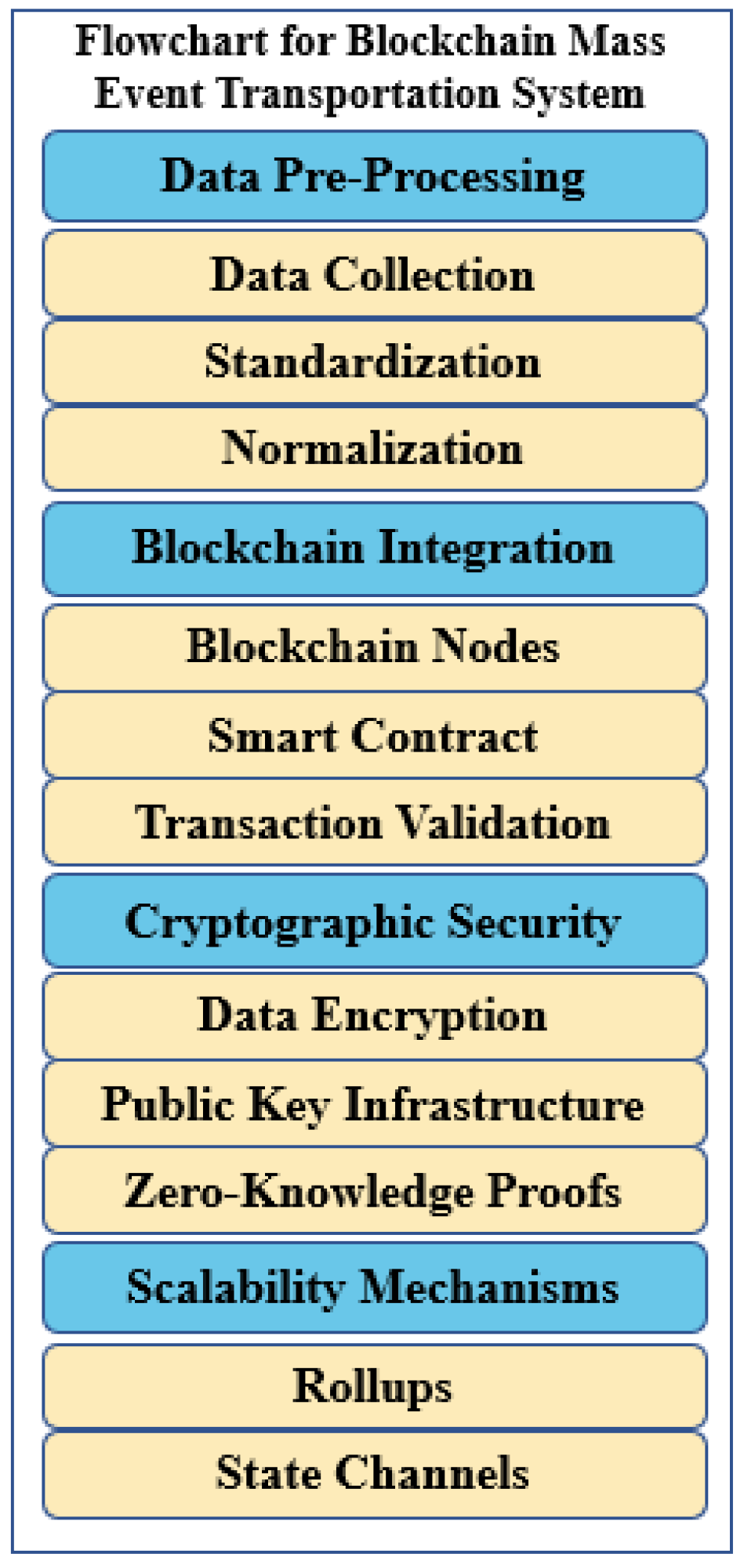
| References | Services | Contributions | Methodology | Limitations | Innovation in Our Study |
|---|---|---|---|---|---|
| [3] | Blockchain-cloud hybrid | Hybrid architecture for scalable transportation. | Proposed hybrid blockchain-cloud computing models. | Limited to cloud applications, lacks edge computing integration. | Our study combines blockchain with edge computing to reduce latency in mass transportation events. |
| [4] | Blockchain in public transportation | Real-time tracking of vehicles and passengers. | Survey of blockchain in transportation. | Focuses only on vehicle and passenger tracking. | Our study integrates full-scale transportation services (ticketing, payment, tracking). |
| [5] | Blockchain for public transportation | Enhancing public transport efficiency through blockchain. | Blockchain applied to transportation networks. | Does not address scalability or security in mass gatherings. | Our study combines blockchain with edge computing and hybrid scaling solutions for optimized mass transportation. |
| [6] | Layer-2 scaling solutions | Improved scalability through off-chain solutions. | Evaluation of layer-2 scaling techniques. | Not focused on mass gatherings or transportation systems. | Our study utilizes layer-2 solutions for large-scale transportation at mass gatherings, such as the Hajj. |
| [7] | Blockchain for the food supply chain | Blockchain-based efficient communication for food supply chains. | Explores the efficiency of communication in food supply chains using blockchain. | Limited to the food supply chain, no mass transportation application. | Our study applies blockchain traceability models from the food supply chain to mass transportation systems, enhancing transparency and enabling real-time updates. |
| [8] | Blockchain for product recall | Blockchain-based traceability system for product recall. | Develops a traceability framework for recalling faulty products utilizing blockchain technology. | Focused on product recalls, not mass transportation. | Our study adapts the product traceability concept for tracking vehicles and passengers in real-time during large-scale events, ensuring accountability and safety. |
| [9] | Scalable blockchain solutions | Discussed scalability through sharding and sidechains. | Theoretical analysis of scalability techniques. | Does not address mass gatherings or specific transportation needs. | Our study integrates sharding and sidechains to handle high-volume real-time data in Hajj transportation. |
| [10] | Blockchain for supply chain traceability | Enhancing traceability in supply chains using blockchain. | Evaluation of blockchain systems for supply chain traceability. | Limited to product logistics, not transportation. | Our study expands on supply chain traceability to include real-time passenger tracking and vehicle monitoring in large-scale transportation, ensuring safety and efficiency. |
| [12] | Blockchain-based ticketing systems | Secure and transparent ticketing using blockchain. | Developed blockchain ticketing models. | Focused on ticketing, no broader system integration. | Our study integrates blockchain-based ticketing with vehicle tracking, payment, and real-time data processing. |
| [13] | Blockchain for healthcare data | Securing and tracking healthcare data using blockchain. | Developed models for healthcare data security and traceability. | Focused only on healthcare, not transport systems. | Our study integrates secure patient data management and tracking models from healthcare into mass transportation, ensuring traceability of services during mass gatherings. |
| [14] | Smart contracts in transportation | Automating transport agreements with smart contracts. | Developed smart contract-based solutions. | It primarily focuses on smart contracts, but does not address scalability. | Our study combines smart contracts with scalability solutions for entire transportation systems. |
| [16] | Blockchain for Hajj operations | Blockchain for Hajj transportation improvement. | Case study approach for Hajj operations. | Limited to a case study, lacks generalizability. | Our study proposes a comprehensive blockchain solution that integrates multiple services for Hajj transportation. |
| References No. | Scenario | Throughput (TPS) | Latency (s) |
|---|---|---|---|
| Our System | Baseline | 800 | 5 |
| State Channels | 2500 | 2 | |
| Rollups | 3500 | 1.5 | |
| [33] | Baseline | 750 | 6 |
| State Channels | 2300 | 3 | |
| Rollups | 3300 | 2 | |
| [34] | Baseline | 800 | 5 |
| State Channels | 2400 | 2.5 | |
| Rollups | 3400 | 1.8 | |
| [35] | Baseline | 700 | 5.5 |
| State Channels | 2200 | 3.2 | |
| Rollups | 3100 | 2.2 | |
| [36] | Baseline | 770 | 6.2 |
| State Channels | 2350 | 3.1 | |
| Rollups | 3250 | 2.3 | |
| [37] | Baseline | 800 | 5.2 |
| State Channels | 2450 | 2.7 | |
| Rollups | 3400 | 1.9 | |
| [38] | Baseline | 790 | 5.4 |
| State Channels | 2400 | 3 | |
| Rollups | 3350 | 2 | |
| [39] | Baseline | 780 | 5.6 |
| State Channels | 2500 | 2.8 | |
| Rollups | 3250 | 2.1 | |
| [40] | Baseline | 760 | 6.1 |
| State Channels | 2300 | 3.3 | |
| Rollups | 3100 | 2.4 |
| Scenario | Throughput (TPS) | Latency (s) | Total Cost (USD) | Change in Cost (USD) | Change in Throughput (TPS) | Transaction Cost Coefficient (βtx) | Infrastructure Cost Coefficient (αinfra) | Security Overhead (γsec) | Scalability Cost (Scalability) |
|---|---|---|---|---|---|---|---|---|---|
| Proposed System (Baseline) | 800 | 5 | 50,000 | - | - | - | 62.5 | - | - |
| State Channels | 2500 | 2 | 60,000 | 10,000 | 1700 | 5.88 | 62.5 | 10,000 | - |
| Rollups | 3500 | 1.5 | 75,000 | 15,000 | 1000 | 15 | 62.5 | 10,000 | 15,000 |
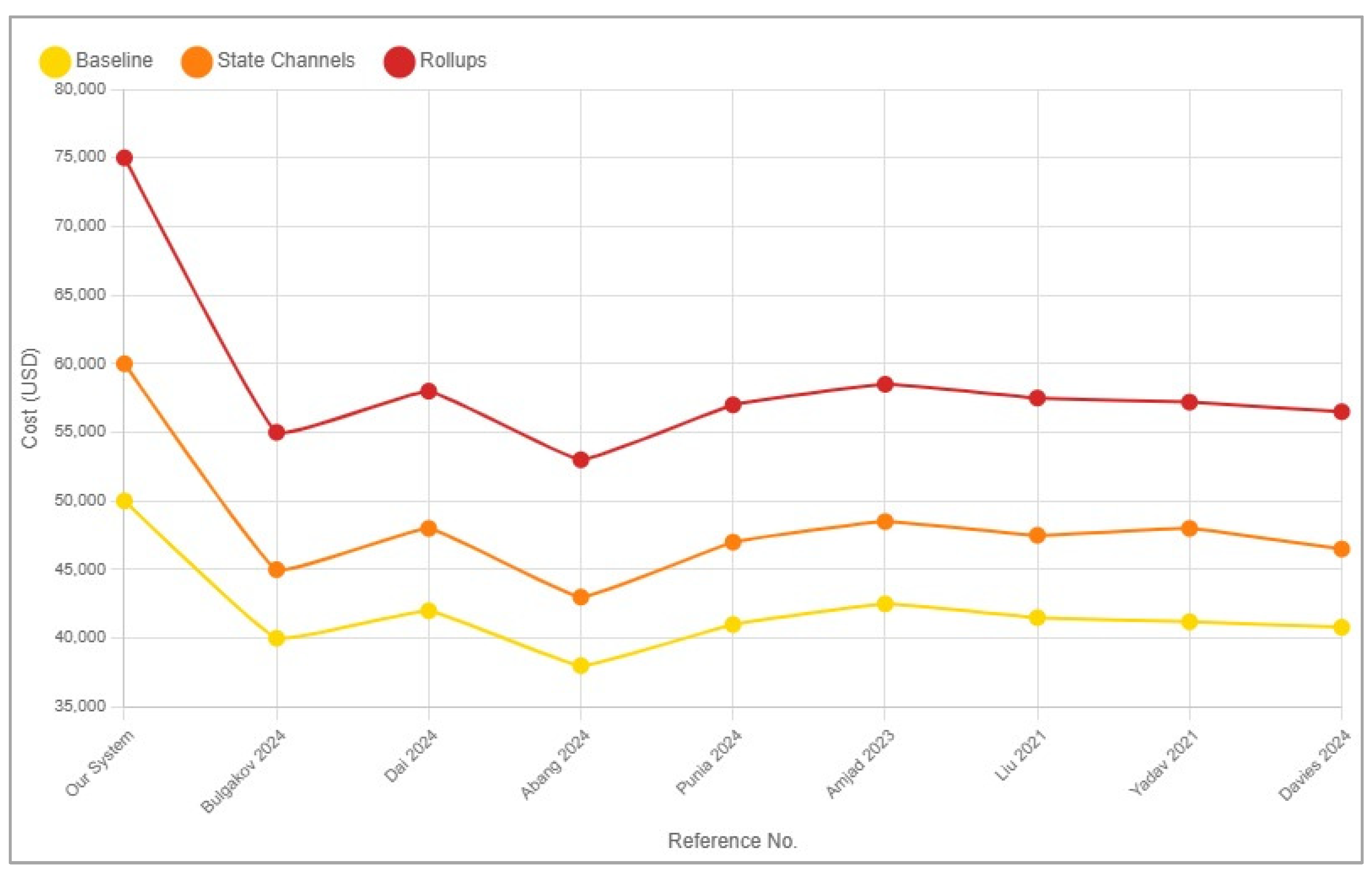
| References No. | Scenario | Throughput (TPS) | Latency (s) | Cost (USD) |
|---|---|---|---|---|
| Our System | Baseline | 800 | 5 | $50,000 |
| State Channels | 2500 | 2 | $60,000 | |
| Rollups | 3500 | 1.5 | $75,000 | |
| [33] | Baseline | 750 | 6 | $40,000 |
| State Channels | 2300 | 3 | $45,000 | |
| Rollups | 3300 | 2 | $55,000 | |
| [34] | Baseline | 800 | 5 | $42,000 |
| State Channels | 2400 | 2.5 | $48,000 | |
| Rollups | 3400 | 1.8 | $58,000 | |
| [35] | Baseline | 700 | 5.5 | $38,000 |
| State Channels | 2200 | 3.2 | $43,000 | |
| Rollups | 3100 | 2.2 | $53,000 | |
| [36] | Baseline | 770 | 6.2 | $41,000 |
| State Channels | 2350 | 3.1 | $47,000 | |
| Rollups | 3250 | 2.3 | $57,000 | |
| [37] | Baseline | 800 | 5.2 | $42,500 |
| State Channels | 2450 | 2.7 | $48,500 | |
| Rollups | 3400 | 1.9 | $58,500 | |
| [38] | Baseline | 790 | 5.4 | $41,500 |
| State Channels | 2400 | 3 | $47,500 | |
| Rollups | 3350 | 2 | $57,500 | |
| [39] | Baseline | 780 | 5.6 | $41,200 |
| State Channels | 2500 | 2.8 | $48,000 | |
| Rollups | 3250 | 2.1 | $57,200 | |
| [40] | Baseline | 760 | 6.1 | $40,800 |
| State Channels | 2300 | 3.3 | $46,500 | |
| Rollups | 3100 | 2.4 | $56,500 |
| Refs. | Pre-Blockchain Tamper Incidents (per Month) | Post-Blockchain Tamper Incidents (per Month) | Pre-Blockchain Data Integrity (%) | Post-Blockchain Data Integrity (%) | Pre-Blockchain Encryption Success (%) | Post-Blockchain Encryption Success (%) | Comments |
|---|---|---|---|---|---|---|---|
| Our Model | 25 | 0 | 89 | 99.99 | 90 | 98 | Blockchain enhances tamper resistance, data integrity, and encryption. |
| [33] | 30 | 1 | 85 | 99.5 | 88 | 96 | Blockchain reduces tampering and weakens data integrity. |
| [34] | 40 | 5 | 80 | 99 | 85 | 94 | Post-blockchain: good integrity, poor encryption. |
| [35] | 50 | 10 | 75 | 98 | 80 | 91 | Pre-blockchain: high tampering, low integrity. |
| [36] | 20 | 2 | 90 | 99.7 | 92 | 97 | Post-blockchain: better, worse tampering, encryption. |
| [37] | 35 | 3 | 85 | 99.2 | 88 | 95 | Post-blockchain: reduced tampering, poor integrity, and encryption. |
| [38] | 45 | 2 | 70 | 99.8 | 80 | 97 | Post-blockchain: improved integrity, weak encryption. |
| [39] | 60 | 12 | 65 | 98 | 75 | 90 | Blockchain has improved, whereas the pre-blockchain model was inferior. |
| [40] | 15 | 1 | 95 | 99.8 | 93 | 96 | Post-blockchain: fewer tampering incidents, higher integrity, and encryption. |
| [46] | 50 | 3 | 80 | 99.6 | 85 | 95 | Blockchain has improved, but it still lacks a comparable model. |
| [47] | 30 | 0 | 88 | 99.95 | 90 | 97 | Close to the model, weaker encryption, similar integrity. |
| Conflict/Issue | Description | Current Solution | Proposed Modifications/Additions | Practical Solutions | References |
|---|---|---|---|---|---|
| Fallback Mechanisms in Case of System Failure | Off-chain systems may fail, resulting in disruptions to time-sensitive operations. | Fallback is not considered in current solutions | Design fallback protocols that switch transactions to on-chain processing in the event of failure. | - Create robust fallback mechanisms that maintain continuity. | [20] |
| - Simulate system performance under fallback conditions. | - Extend the scalability model to account for fallback scenarios during failures. | ||||
| Resistance to Advanced Attacks | Blockchain systems are vulnerable to advanced attacks, including smart contract exploits and potential threats from quantum computers. | Basic cryptographic techniques for transaction validation | - Extend the system with post-quantum cryptography to future-proof against quantum threats. | - Perform regular smart contract audits. | [41] |
| - Explore privacy-enhancing technologies, such as homomorphic encryption. | - Use quantum-resistant cryptographic algorithms. | ||||
| Implement privacy-enhancing technologies, such as multi-party computation. | |||||
| Risks of Third-Party Dependency | Dependency on third-party off-chain solutions introduces risks of breaches of trust, downtime, or vulnerabilities, which can affect system reliability. | Centralized watchtowers for fraud detection | Replace centralized watchtowers with decentralized validators that utilize staking incentives. | - Use decentralized oracles and decentralized watchtowers for improved reliability. | [42] |
| - Propose DAO-based governance to oversee validators. | - Design fallback mechanisms that revert to on-chain systems when off-chain services fail. | ||||
| Scalability Limitations (Trust Issues in Off-Chain Solutions) | Off-chain solutions, such as State Channels and Rollups, require trust among participants, which can lead to disputes if transactions are manipulated or invalidated before being finalized on-chain. | Fraud proofs and watchtower mechanisms | - Introduce Zero-Knowledge Proof (ZKP) for fraud prevention and scalability. | - Implement fraud proofs and watchtower mechanisms. | [41,42,50] |
| Comparative analysis of ZK-Rollups versus Optimistic Rollups in terms of latency, scalability, and trust. | - Use ZKPs and ZK-Rollups for improved scalability and security. | ||||
| - Incorporate multi-signature contracts to ensure agreement on transactions. | |||||
| Vulnerability Attack | Permissioned blockchains may face risks if centralized governance allows a malicious entity to control the majority of network nodes and manipulate data. | Centralized governance in permissioned blockchains | - Introduce multi-stakeholder governance to distribute decision-making. | - Strengthen governance policies to prevent centralized control. | [51] |
| - Utilize Byzantine Fault Tolerant (BFT) consensus mechanisms, such as Tendermint, to enhance resilience. | - Use dynamic node allocation and randomization. | ||||
| - Implement BFT consensus mechanisms. | |||||
| High Implementation Costs | Blockchain solutions, such as State Channels and Rollups, require significant infrastructure investment, which may be unaffordable for small organizations or regions. Transitioning systems disrupt operations. | Infrastructure investment for scaling solutions | - Recommend public–private partnerships (PPP) to share infrastructure costs. | - Leverage PPP to reduce implementation barriers. | [52] |
| - Suggest hybrid models for phased adoption of blockchain. | - Start with hybrid systems for initial adoption. | ||||
| - Utilize open-source solutions to minimize licensing expenses. | - Adopt open-source blockchain platforms. | ||||
| Latency in Real-World Scenarios | Real-world conditions (network congestion, unpredictable traffic, resource allocation) may cause delays in time-sensitive tasks like booking or alerts. | Centralized processing for transactions | Propose integrating edge computing to process critical data closer to its source. | - Implement edge computing to reduce latency. | [53] |
| - Enhance the mathematical model to simulate edge processing capabilities. | - Use dynamic load balancing and AI-based traffic analytics. | ||||
| - Shorten dispute windows for faster fraud-proof resolution. | Optimize cooperation between edge nodes and centralized nodes for improved resource allocation. | ||||
| Trust and User Adoption | End-users may hesitate to adopt blockchain-based systems due to complexity or lack of understanding of how the technology works. | User education and training programs | - Provide public–private partnerships to reduce costs for smaller regions. | - Offer educational workshops and intuitive user interfaces. | [54] |
| - Discuss phased adoption strategies, focusing on critical components first. | - Use phased adoption to introduce blockchain gradually. | ||||
| Governance and Decentralization | Centralized control in permissioned blockchains increases the risk of collusion and manipulation. | Centralized governance in watchtowers | - Introduce multi-stakeholder governance models to distribute authority. | - Implement DAO-based governance for watchtower oversight. | [55] |
| - Use decentralized validation networks (watchtowers). | - Use BFT consensus mechanisms to improve blockchain resilience. | ||||
| Resource Allocation Efficiency | Inefficient resource allocation during peak traffic could degrade system performance. | Traditional load-balancing techniques | - Incorporate AI-driven predictive analytics to forecast transaction spikes. | Implement AI-based algorithms to allocate resources dynamically. | [54] |
| - Utilize adaptive resource allocation to prioritize tasks during peak times. | - Use predictive traffic analytics to optimize transaction flow during peak periods. | ||||
| 1. Scalability Limitations (Trust Issues in Off-Chain Solutions) | Off-chain solutions, such as State Channels and Rollups, require trust among participants, which can lead to disputes if transactions are manipulated or invalidated before being finalized on-chain. | Fraud proofs and watchtower mechanisms | - Introduce Zero-Knowledge Proof (ZKP) for fraud prevention and scalability. | - Implement fraud proofs and watchtower mechanisms. | [41,42,50] |
| Comparative analysis of ZK-Rollups versus Optimistic Rollups in terms of latency, scalability, and trust. | - Use ZKPs and ZK-Rollups for improved scalability and security. | ||||
| - Incorporate multi-signature contracts to ensure agreement on transactions. | |||||
| 2. Vulnerability Attack | Permissioned blockchains may face risks if centralized governance allows a malicious entity to control the majority of network nodes and manipulate data. | Centralized governance in permissioned blockchains | - Introduce multi-stakeholder governance to distribute decision-making. | - Strengthen governance policies to prevent centralized control. | [51] |
| - Utilize Byzantine Fault Tolerant (BFT) consensus mechanisms, such as Tendermint, to enhance resilience. | - Use dynamic node allocation and randomization. | ||||
| - Implement BFT consensus mechanisms. | |||||
| 3. High Implementation Costs | Blockchain solutions, such as State Channels and Rollups, require significant infrastructure investment, which may be unaffordable for small organizations or regions. Transitioning systems disrupt operations. | Infrastructure investment for scaling solutions | - Recommend public–private partnerships (PPP) to share infrastructure costs. | - Leverage PPP to reduce implementation barriers. | [52] |
| - Suggest hybrid models for phased adoption of blockchain. | - Start with hybrid systems for initial adoption. | ||||
| - Utilize open-source solutions to minimize licensing expenses. | - Adopt open-source blockchain platforms. | ||||
| 4. Latency in Real-World Scenarios | Real-world conditions (network congestion, unpredictable traffic, resource allocation) may cause delays in time-sensitive tasks like booking or alerts. | Centralized processing for transactions | Propose integrating edge computing to process critical data closer to its source. | - Implement edge computing to reduce latency. | [53] |
| - Enhance the mathematical model to simulate edge processing capabilities. | - Use dynamic load balancing and AI-based traffic analytics. | ||||
| - Shorten dispute windows for faster fraud-proof resolution. | Optimize cooperation between edge nodes and centralized nodes for improved resource allocation. | ||||
| 5. Risks of Third-Party Dependency | Dependency on third-party off-chain solutions introduces risks of breaches of trust, downtime, or vulnerabilities, which can affect system reliability. | Centralized watchtowers for fraud detection | Replace centralized watchtowers with decentralized validators that utilize staking incentives. | - Use decentralized oracles and decentralized watchtowers for improved reliability. | [42] |
| - Propose DAO-based governance to oversee validators. | - Design fallback mechanisms that revert to on-chain systems when off-chain services fail. | ||||
| 6. Resistance to Advanced Attacks | Blockchain systems are vulnerable to advanced attacks, including smart contract exploits and potential threats from quantum computers. | Basic cryptographic techniques for transaction validation | - Extend the system with post-quantum cryptography to future-proof against quantum threats. | - Perform regular smart contract audits. | [41] |
| - Explore privacy-enhancing technologies, such as homomorphic encryption. | - Use quantum-resistant cryptographic algorithms. | ||||
| Implement privacy-enhancing technologies, such as multi-party computation. | |||||
| 7. Trust and User Adoption | End-users may hesitate to adopt blockchain-based systems due to complexity or lack of understanding of how the technology works. | User education and training programs | - Provide public–private partnerships to reduce costs for smaller regions. | - Offer educational workshops and intuitive user interfaces. | [54] |
| - Discuss phased adoption strategies, focusing on critical components first. | - Use phased adoption to introduce blockchain gradually. | ||||
| 8. Governance and Decentralization | Centralized control in permissioned blockchains increases the risk of collusion and manipulation. | Centralized governance in watchtowers | - Introduce multi-stakeholder governance models to distribute authority. | - Implement DAO-based governance for watchtower oversight. | [55] |
| - Use decentralized validation networks (watchtowers). | - Use BFT consensus mechanisms to improve blockchain resilience. | ||||
| 9. Resource Allocation Efficiency | Inefficient resource allocation during peak traffic could degrade system performance. | Traditional load-balancing techniques | - Incorporate AI-driven predictive analytics to forecast transaction spikes. | Implement AI-based algorithms to allocate resources dynamically. | [54] |
| - Utilize adaptive resource allocation to prioritize tasks during peak times. | - Use predictive traffic analytics to optimize transaction flow during peak periods. | ||||
| 10. Fallback Mechanisms in Case of System Failure | Off-chain systems may fail, resulting in disruptions to time-sensitive operations. | Fallback is not considered in current solutions | Design fallback protocols that switch transactions to on-chain processing in the event of failure. | - Create robust fallback mechanisms that maintain continuity. | [20] |
| - Simulate system performance under fallback conditions. | - Extend the scalability model to account for fallback scenarios during failures. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mutahhar, A.; Khanzada, T.J.S.; Shahid, M.F. Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings. Information 2025, 16, 641. https://doi.org/10.3390/info16080641
Mutahhar A, Khanzada TJS, Shahid MF. Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings. Information. 2025; 16(8):641. https://doi.org/10.3390/info16080641
Chicago/Turabian StyleMutahhar, Ahmad, Tariq J. S. Khanzada, and Muhammad Farrukh Shahid. 2025. "Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings" Information 16, no. 8: 641. https://doi.org/10.3390/info16080641
APA StyleMutahhar, A., Khanzada, T. J. S., & Shahid, M. F. (2025). Enhanced Scalability and Security in Blockchain-Based Transportation Systems for Mass Gatherings. Information, 16(8), 641. https://doi.org/10.3390/info16080641







