Offloaded Computation for QoS Routing in Wireless Sensor Networks
Abstract
1. Introduction
- Functional Metrics: These metrics define Key Performance Indicators (KPIs) that significantly impact user perceptions. Key examples include latency, energy efficiency, throughput, packet loss rate, and jitter. Each functional metric must be clearly defined for each service provided.
- Non-Functional Metrics: These metrics assess service performance concerning deployment and management considerations. Notable examples include service availability, fault tolerance, service processing, and computational load.
Main Contributions
- 1.
- A formal problem formulation that defines multi-constrained QoS routing in WSNs as an NP-complete MC(O)P problem and contextualizes its integration challenges within the structural and computational limitations of the RPL.
- 2.
- 3.
- An edge offloading architecture that delegates path computation and DODAG construction to external servers [2,14,15], significantly reducing the processing burden on constrained sensor nodes. This design contrasts with prior in-network QoS routing approaches [16,17] and aligns with the recent trends in computation offloading to external infrastructures for enhanced QoS, as also explored in hybrid satellite networks [18].
- 4.
- 5.
- Comprehensive performance evaluation under varying network sizes, QoS constraint profiles, and BR placements. The results show that the proposed approach preserves between 143% and 1282% more QoS-satisfying nodes compared to the heuristic- and composition-based baselines, with an average improvement of over 560%, validating its scalability and robustness under strict multi-constraint conditions.
- 6.
- New insights into QoS routing dynamics in WSNs, including how the number of QoS constraints, path feasibility rates, and route lengths interact. These findings offer practical guidelines for QoS-aware WSN planning and deployment.
2. Related Work
2.1. QoS Routing in Wireless Sensor Networks
2.2. QoS Extensions to RPL
2.3. Recent Trends
3. System Model and Problem Formulation
3.1. Network and Graph Model
3.2. Multi-Objective vs. Multi-Constrained Routing
3.3. Key Challenges
4. Proposed Methodology
4.1. Architectural Overview
4.1.1. Centralized Computation Framework
- (a)
- QoS-aware route computation on the topology graph under given constraints.
- (b)
- Network (re)configuration, where DODAGs are deployed and adjusted across nodes.
- (c)
- Monitoring, where nodes report status changes that may trigger reconfiguration.
4.1.2. Feasible and Non-Dominated Path Computation (Algorithm 1)
- 1.
- Initialization: Each node is assigned an initially empty set of paths. The algorithm starts by injecting a fictive zero-weight path containing only the BR.
- 2.
- Path Expansion: Using a breadth-first search style expansion, every path is iteratively extended by one-hop neighbors. For each new candidate path:
- The path’s cumulative QoS metrics are computed.
- If the path exceeds any QoS threshold, it is discarded.
- 3.
- Dominance Checking: Feasible paths are compared to existing paths at the destination node:
- If a new path dominates an existing one, the latter is discarded.
- If it is dominated by another, it is not stored.
- 4.
- Path Limiting: At most, k non-dominated paths are stored per node to limit complexity.
- 5.
- Termination: The expansion continues until no new feasible non-dominated paths are found.
| Algorithm 1 Feasible and Non-Dominated Path Computation |
|
4.2. Conflict-Free DODAG Construction (Algorithm 2)
| Algorithm 2 Conflict-Free DODAG Construction |
|
- Feasible paths: those satisfying all end-to-end QoS constraints.
- Dominated paths: Pareto-dominated by other feasible paths.
- Ready paths: those for which no feasible successors can be obtained by adding adjacent edges.
- 1.
- Computation of feasible and non-dominated paths that meet the QoS constraints.
- 2.
- DODAG construction: Construction of one or more DODAGs from the selected paths.
- 3.
- Redundancy augmentation: Addition of redundant links to enhance robustness and support local repair.
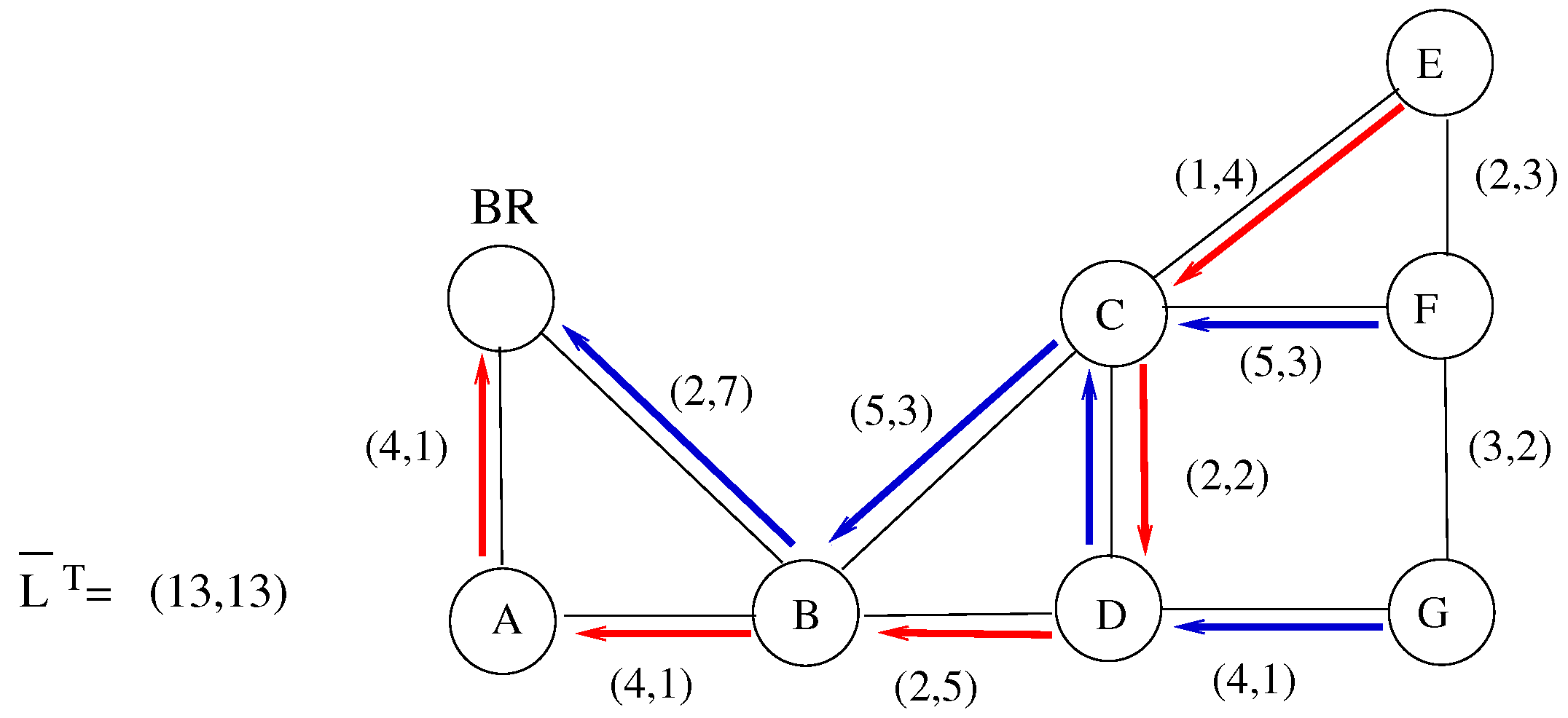
- Initialization: Identify all nodes with at least one feasible QoS-compliant path. These nodes are candidates for DODAG construction. Begin with an empty DODAG set.
- Greedy Path Selection: For each candidate node, select the path with the shortest non-linear length (a cumulative cost over multiple QoS metrics).
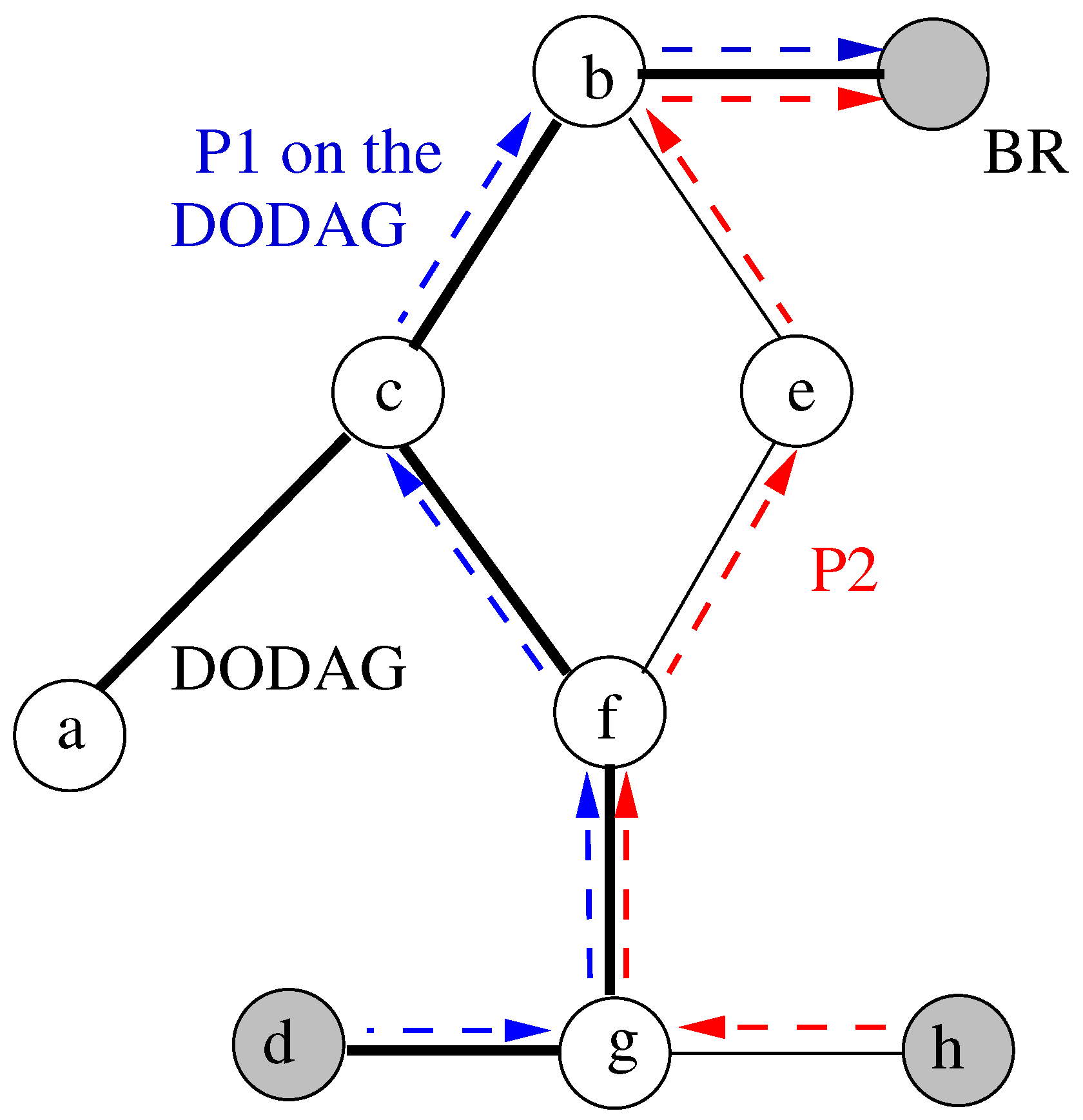
- Conflict Detection: Before integrating a path into the DODAG, verify its structural compatibility:
- –
- Compute the common prefix between the candidate path and the current DODAG, starting from the BR.
- –
- A conflict is detected if the candidate path shares a node with the DODAG outside of this common prefix, which may lead to ambiguous routing decisions.
- Path Integration: If no conflict is detected, the path is added to the DODAG, and the corresponding node is marked as integrated.
- Iteration and Expansion: Repeat the process until no additional non-conflicting paths remain. If any feasible nodes are still unintegrated, initiate a new DODAG and repeat.
- Output: A set of conflict-free DODAGs that preserve QoS constraints and allow for consistent routing semantics.
- (a)
- A common prefix between the candidate path and the current DODAG is computed, starting from the BR. If no common prefix exists, the prefix is simply .
- (b)
- A conflict is detected if the candidate path shares any nodes with the DODAG that lie beyond the common prefix. This structural ambiguity could render routing decisions invalid or contradictory.
| Algorithm 3 Add Redundant Links to a DODAG |
|
4.2.1. Redundancy Augmentation (Algorithm 3)
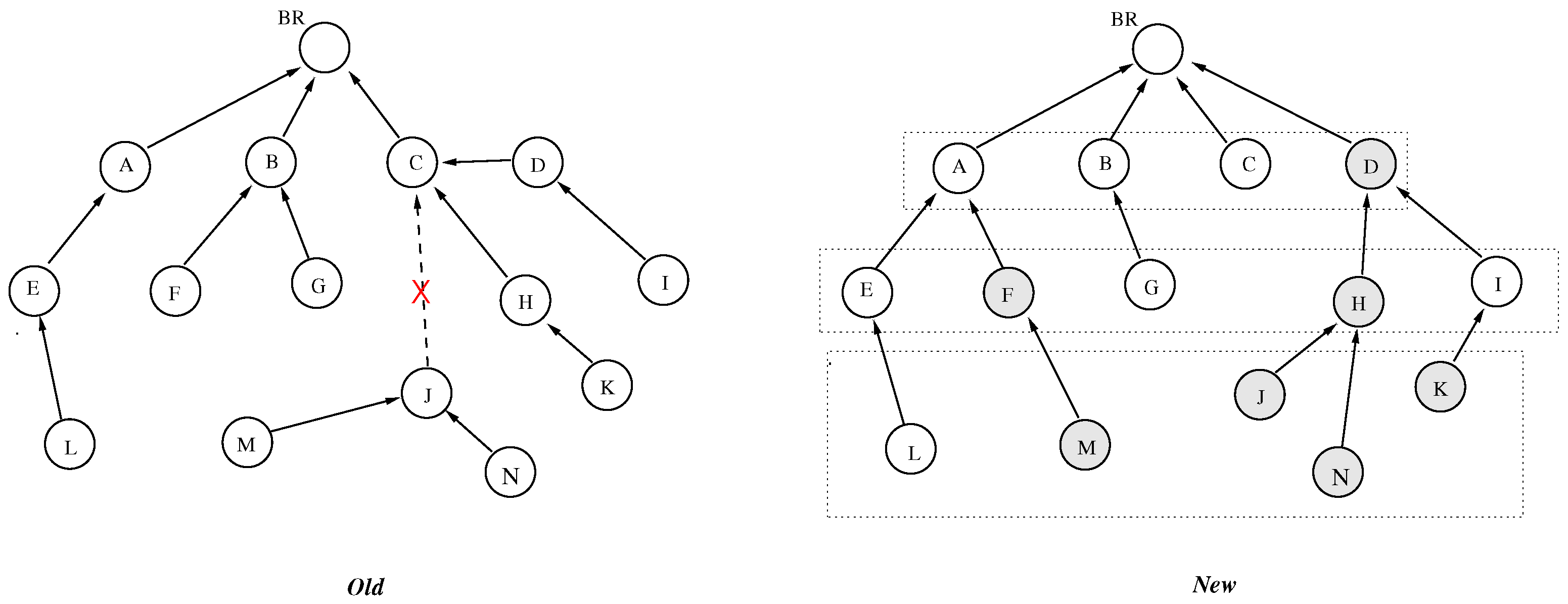
- 1.
- Node b is part of the DODAG and its rank is not higher than that of node a.
- 2.
- The aggregated QoS cost along the path from a leaf node to a, the direct link , and the path from b to the BR, denoted by , satisfies the global QoS constraint .
- 3.
- The resulting path structure remains acyclic and consistent with RPL directionality.
4.2.2. Greedy, Priority-Based, and Descending Reconfiguration
4.2.3. Lightweight Network Monitoring
5. Theoretical and Experimental Evaluation
5.1. Complexity of Algorithm 1: Computation of Non-Dominated QoS Paths
5.1.1. Initialization
- The algorithm initializes paths for each node in P, taking time, where is the number of nodes.
- Creating a fictive path and assigning it to the border router () takes constant time, .
5.1.2. Main Loops and Path Processing
- While Loop (Line 13): Runs until all paths are evaluated. Since paths do not revisit nodes, a path can contain at most nodes. Thus, the While loop executes at most times.
- For Loop (Line 15): Iterates over all nodes, contributing another factor.
- Path Comparisons (Lines 17–30):
- –
- Each node stores at most k paths.
- –
- Every adjacent edge is processed, bounded by .
- –
- The number of path comparisons is per node.
5.2. Complexity of Algorithm 2: Computation of the DODAG(s)
5.2.1. Initialization
- The set of nodes (nodes with at least one QoS path) are constructed in time.
- Initializing the set of DODAGs is conducted in time.
5.2.2. Main Loops and DODAG Construction
- While Loop (Line 12): In the extreme case, each node forms a separate DODAG. Since there can be at most DODAGs, this loop executes at most times.
- For Loop (Line 14): Iterates over all nodes in , adding another factor.
- While Loop (Line 17): Processes paths, with operations involving set operations that take at most time.
5.3. Complexity of Algorithm 3: Adding Redundancy to a DODAG
5.3.1. Initialization and Main Loops
- Outer For Loop (Line 5): Iterates over nodes.
- Inner For Loop (Line 7): Iterates over the adjacent nodes of each node. In the worst case, each node has at most neighbors.
5.3.2. Edge Feasibility Check (Line 8)
5.4. Experimental Evaluation
5.4.1. Experimental Setup
- EX: The proposed offloaded computation framework constructs QoS-compliant conflict-free DODAGs based on centralized multi-constrained path computation.
- H1: A heuristic baseline inspired by [46], where auxiliary weights are derived and a shortest-path tree is constructed using additive metrics.
- H2: A heuristic approach based on [17], in which each node selects its parent based on the minimum cumulative non-linear path length to the BR.
- Node coordinates were randomly distributed within a square region.
- Communication links were created between nodes within a fixed communication range.
- Each link was assigned k uncorrelated additive QoS parameters uniformly drawn from the interval .
- The number of QoS parameters k and the threshold vector were varied to simulate different levels of constraint tightness and metric dimensionality.
- The number and placement of BRs were modified across experiments to explore topological effects on feasibility and coverage.
- Definition of Path Length. In this context, path length refers to the non-linear additive cost of a routing path, not the simple hop count. Specifically, this metric is computed by aggregating multiple QoS parameters (e.g., delay and ETX) in a weighted or non-linear fashion, as described in our methodology. Consequently, the resulting values may be fractional even though the underlying topology is discrete. This allows us to more accurately represent the performance of different routing strategies under multi-constrained QoS formulations.
5.4.2. Impact of QoS Constraint Tightness
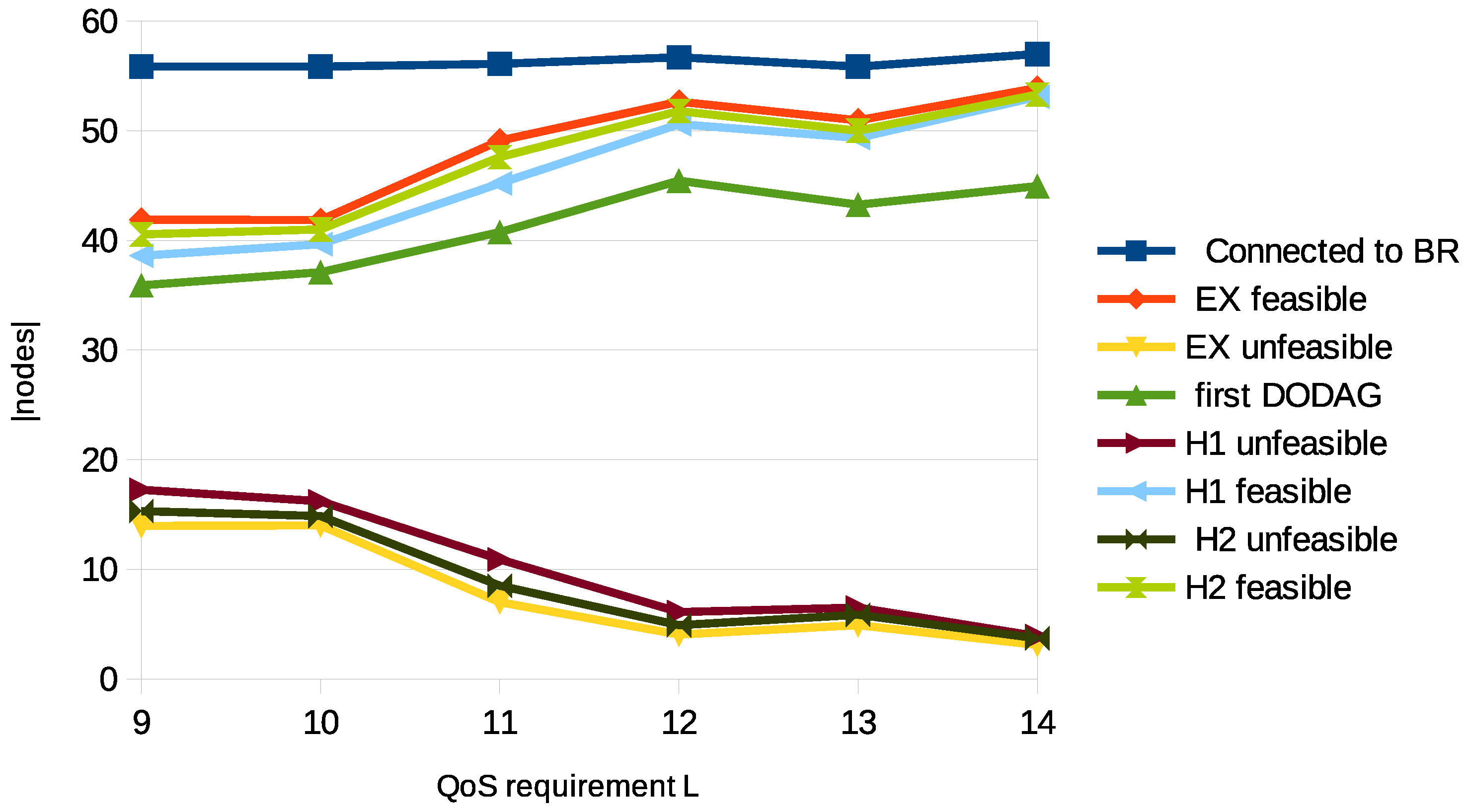
- Significant performance gain: As shown in Table 5, the proposed EX method consistently outperforms both heuristic baselines (H1 and H2) across all tested QoS thresholds, achieving up to 1282.05% gain in the number of feasible nodes, with an average improvement of 563.45%.
- Feasibility trend with relaxed constraints: Figure 5 confirms that the number of QoS-compliant nodes increases as the QoS bound L is relaxed, growing from approximately 42 nodes at to 54 nodes at , validating the sensitivity of path feasibility to the constraint level.
- Improved path efficiency: The EX approach achieves lower average and maximum non-linear path lengths than both heuristics (Table 6), contributing to more reliable and uniformly distributed routing paths.
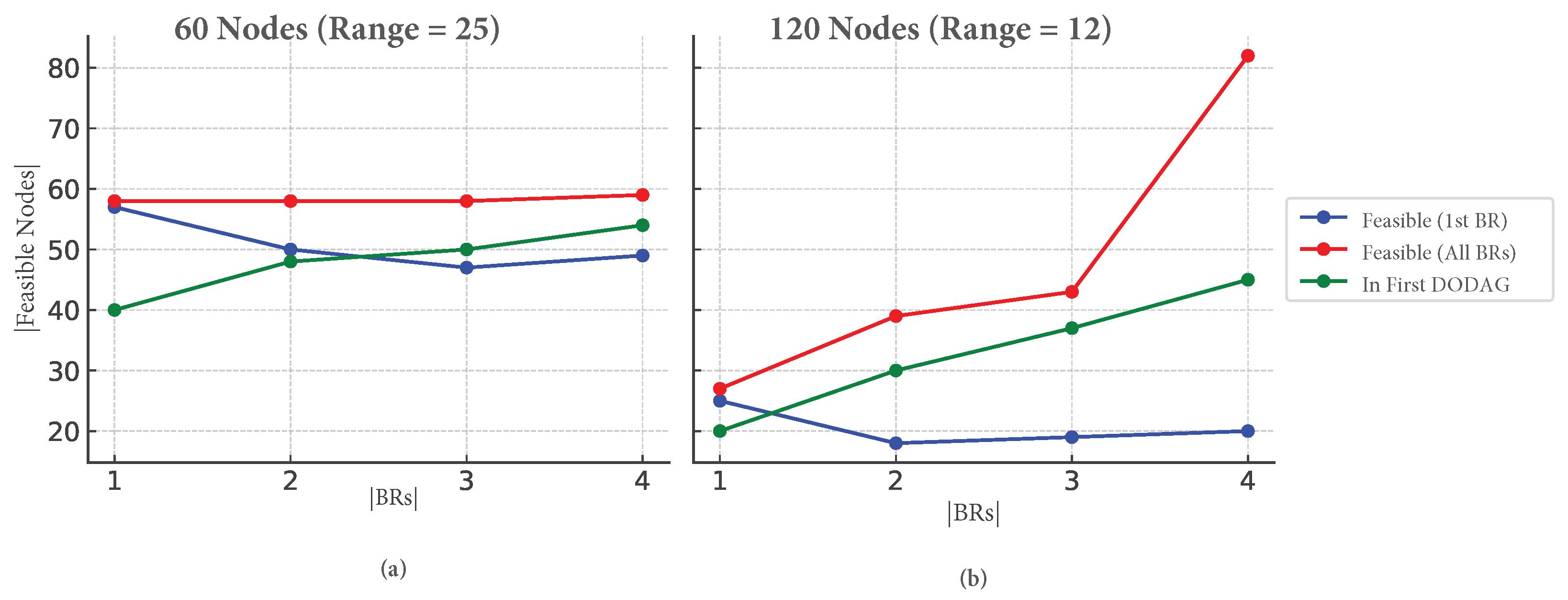
- Structural advantage with BRs: The effectiveness of multi-BR deployment is validated in Figure 8, which shows that optimal BR placement significantly boosts feasible coverage, especially under low-range settings. For example, in the 120-node case with range 12, the number of feasible nodes increased from 25 (1 BR) to over 80 (4 BRs), demonstrating the importance of both BR count and location.
- General scalability: Across varying network sizes and link constraint dimensions, the centralized offloading model maintains high feasibility, adaptability, and topological flexibility. This reinforces its suitability for real-world constraint-sensitive WSN applications.
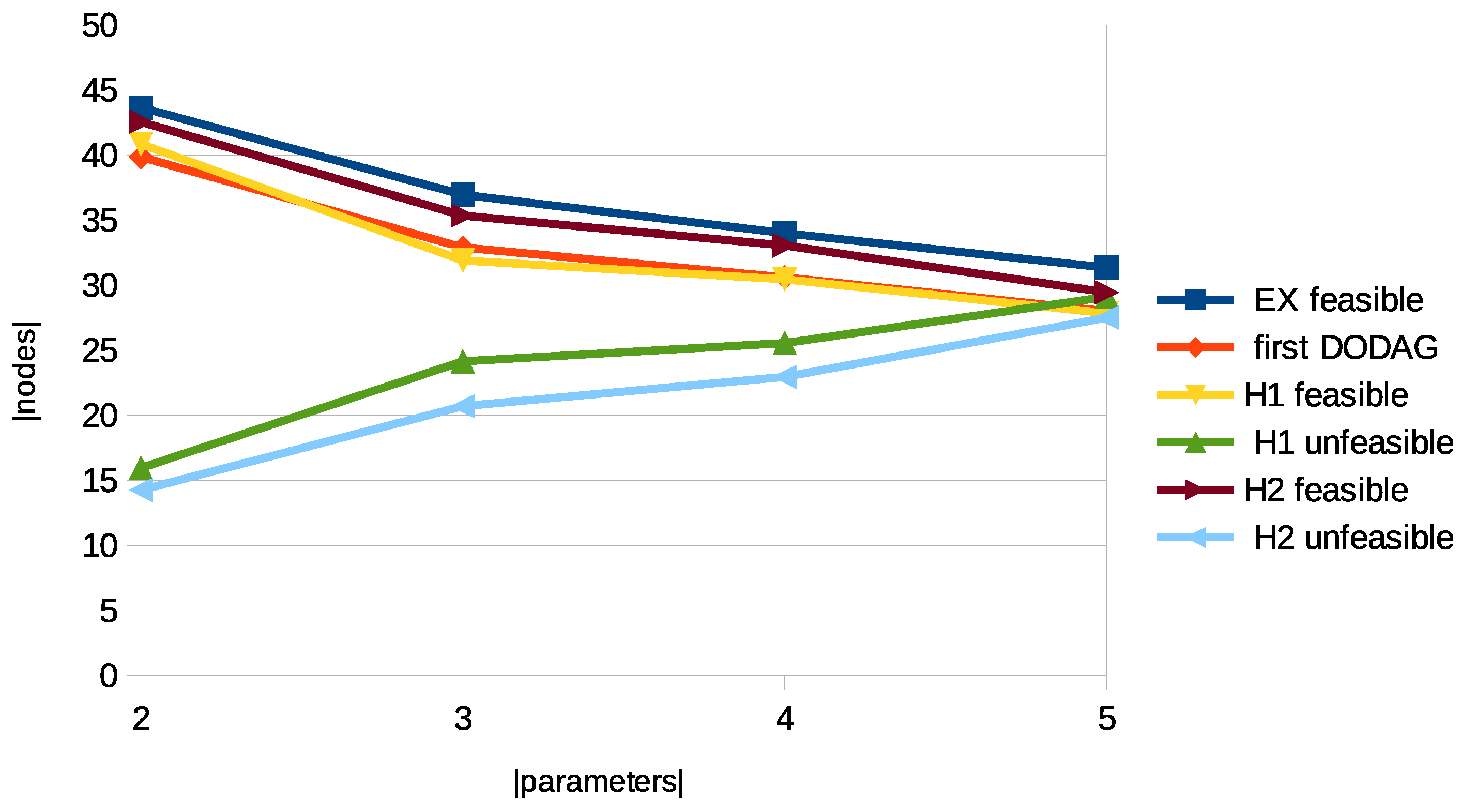
5.4.3. Impact of Number of QoS Parameters
- The proposed method remains consistently superior, maintaining higher feasibility even as dimensionality increases.
- Table 8 shows that both average and maximum path lengths increase with k, indicating higher routing complexity.
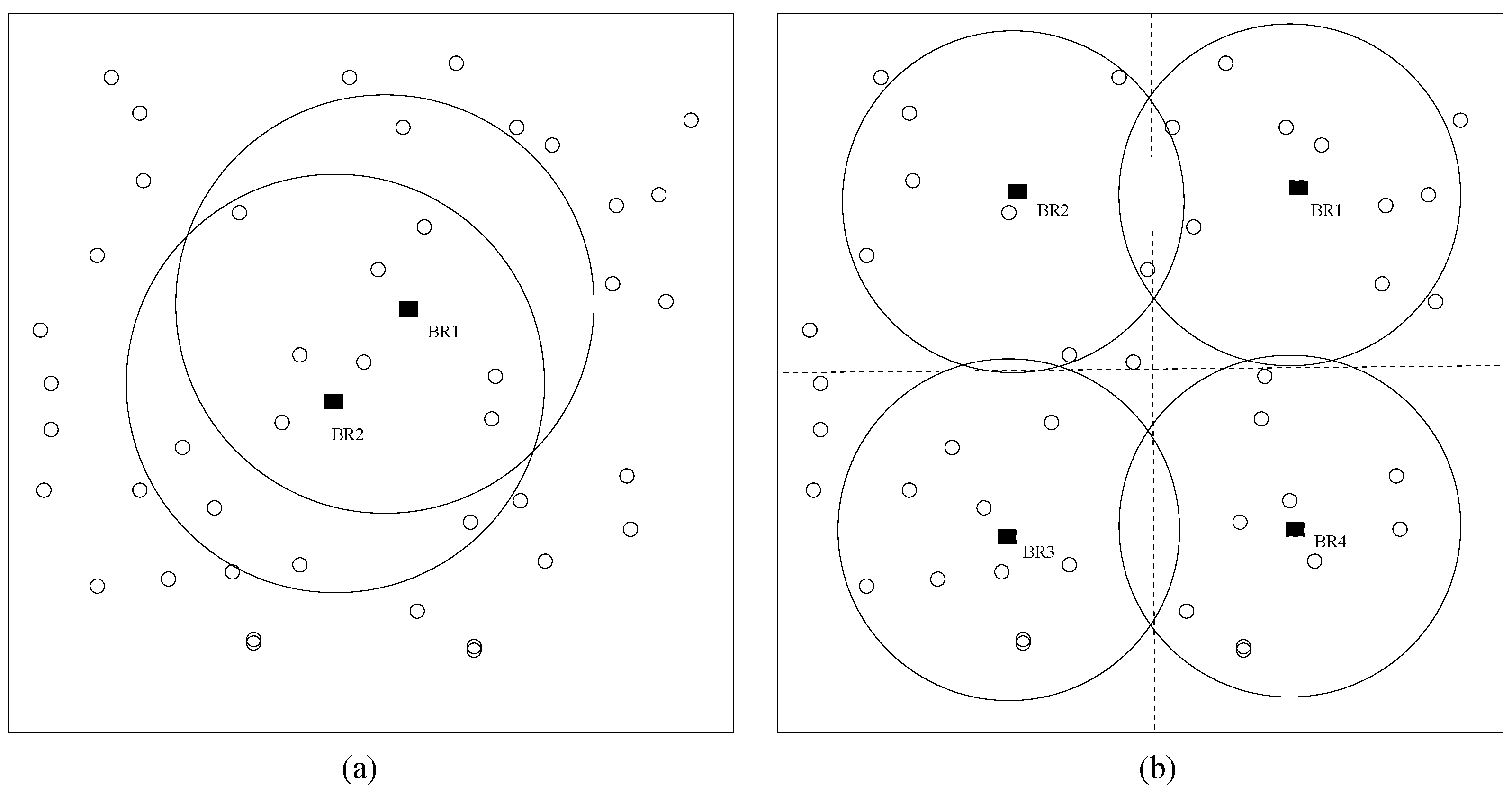
5.4.4. Impact of Border Router Number and Placement
- 1.
- Sixty sensors with a communication range of 25:
- BRs were initially placed at the center, and additional BRs were equitably distributed.
- The first BR covered approximately 50 feasible nodes, while multiple BRs increased coverage to 57–59 nodes (out of 59).
- The improvement from adding more BRs was slight since the first BR already covered most feasible nodes.
- 2.
- One-hundred-twenty sensors with a smaller communication range (12):
- Initially, only 20–25 nodes were feasible out of 120.
- Adding 2 to 4 BRs significantly increased feasible nodes and improved coverage in the first computed DODAG.
- Adding BRs increases the number of feasible nodes, especially in low-connectivity settings (e.g., 120 nodes, range = 12).
- Optimal BR placement leads to substantial coverage gains—up to 82 out of 120 nodes become feasible with four BRs.
- For denser topologies (e.g., 60 nodes, range = 25), marginal gains are observed since the first BR already covers most nodes.
- Table 9 summarizes these effects,
5.4.5. Summary of Findings
- The proposed EX framework preserves QoS feasibility under tight constraints significantly better than heuristic approaches.
- It scales robustly with increasing QoS dimensionality and supports improved coverage through intelligent BR deployment.
- By enabling conflict-free multi-DODAG routing, EX ensures both structural resilience and better performance metrics (feasibility, delay, and path uniformity).
6. Conclusions and Perspectives
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Crawley, E.; Nair, R.; Rajagopalan, B.; Sandick, H. A Framework for QoS-Based Routing in the Internet. RFC 2386, Internet Engineering Task Force. 1998. Available online: http://www.rfc-editor.org/rfc/rfc2386.txt (accessed on 24 October 2024).
- Liang, B.; Gregory, M.A.; Li, S. Multi-access edge computing fundamentals, services, enablers and challenges: A complete survey. J. Netw. Comput. Appl. 2022, 199, 103308. [Google Scholar] [CrossRef]
- Atitallah, N.; Cheikhrouhou, O.; Mershad, K.; Koubaa, A.; Hajjej, F. CERP: Cooperative and Efficient Routing Protocol for Wireless Sensor Networks. Sensors 2023, 23, 8834. [Google Scholar] [CrossRef]
- Mangold, S.; Choi, S.; Hiertz, G.R.; Klein, O.; Walke, B. Analysis of IEEE 802.11e for QoS support in wireless LANs. IEEE Wirel. Commun. 2003, 10, 40–50. [Google Scholar] [CrossRef]
- Ghaleb, B.; Al-Dubai, A.Y.; Ekonomou, E.; Alsarhan, A.; Nasser, Y.; Mackenzie, L.M.; Boukerche, A. A Survey of Limitations and Enhancements of the IPv6 Routing Protocol for Low-Power and Lossy Networks: A Focus on Core Operations. IEEE Commun. Surv. Tutor. 2019, 21, 1607–1635. [Google Scholar] [CrossRef]
- Nassar, J.; Berthomé, M.; Dubrulle, J.; Gouvy, N.; Mitton, N.; Quoitin, B. Multiple instances QoS routing in RPL: Application to smart grids. Sensors 2018, 18, 2472. [Google Scholar] [CrossRef]
- Alilou, M.; Babazadeh Sangar, A.; Majidzadeh, K.; Akbari, B.; Parizi, R.M. QFS-RPL: Mobility and energy aware multi-path routing protocol for the Internet of Mobile Things data transfer infrastructures. Telecommun. Syst. 2024, 85, 289–312. [Google Scholar] [CrossRef]
- Gupta, N.; Pughat, A.; Sharma, V. A critical analysis of RPL objective functions in Internet of Things paradigm. Peer-to-Peer Netw. Appl. 2021, 14, 2187–2208. [Google Scholar] [CrossRef]
- Farooq, M.O.; Sreenan, C.J.; Brown, K.N.; Kunz, T. Design and analysis of RPL objective functions for multi-gateway ad-hoc low-power and lossy networks. Ad Hoc Netw. 2017, 65, 78–90. [Google Scholar] [CrossRef]
- Karkazis, P.; Leligou, H.C.; Sarakis, L.; Zahariadis, T.; Trakadas, P.; Velivassaki, T.; Capsalis, C. Design of Primary and Composite Routing Metrics for RPL-Compliant Wireless Sensor Networks. In Proceedings of the 2012 International Conference on Telecommunications and Multimedia (TEMU), Heraklion, Greece, 30 July–1 August 2012; pp. 13–18. [Google Scholar] [CrossRef]
- Gill, S.S.; Xu, M.; Ottaviani, C.; Patros, P.; Bahsoon, R.; Shaghaghi, A.; Golec, M.; Stankovski, V.; Wu, H.; Abraham, A.; et al. AI for next generation computing: Emerging trends and future directions. Internet Things 2022, 19, 100514. [Google Scholar] [CrossRef]
- Alexander, R.; Brandt, A.; Vasseur, J.; Hui, J.; Pister, K.; Thubert, P.; Levis, P.; Struik, R.; Kelsey, R.; Winter, T. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. RFC 6550. 2012. Available online: https://www.rfc-editor.org/info/rfc6550 (accessed on 24 October 2024).
- Gaddour, O.; Koubâa, A. RPL in a nutshell: A survey. Comput. Netw. 2012, 56, 3163–3178. [Google Scholar] [CrossRef]
- Osibo, B.K.; Jin, Z.; Ma, T.; Marah, B.D.; Zhang, C.; Jin, Y. An edge computational offloading architecture for ultra-low latency in smart mobile devices. Wirel. Netw. 2022, 28, 2061–2075. [Google Scholar] [CrossRef]
- Zhang, H.; Yang, Y.; Huang, X.; Fang, C.; Zhang, P. Ultra-Low Latency Multi-Task Offloading in Mobile Edge Computing. IEEE Access 2021, 9, 32569–32581. [Google Scholar] [CrossRef]
- Gaddour, O.; Koubâa, A.; Baccour, N.; Abid, M. OF-FL: QoS-aware fuzzy logic objective function for the RPL routing protocol. In Proceedings of the 2014 12th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt), Hammamet, Tunisia, 12–16 May 2014; pp. 365–372. [Google Scholar] [CrossRef]
- Khallef, W.; Molnár, M.; Benslimane, A.; Durand, S. Multiple constrained QoS routing with RPL. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Lv, W.; Yang, P.; Ding, Y.; Wang, Z.; Lin, C.; Wang, Q. Energy-Efficient and QoS-Aware Computation Offloading in GEO/LEO Hybrid Satellite Networks. Remote Sens. 2023, 15, 3299. [Google Scholar] [CrossRef]
- Semchedine, F.; Ait Saidi, N.; Belouzir, L.; Bouallouche-Medjkoune, L. QoS-Based Protocol for Routing in Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 97, 4413–4429. [Google Scholar] [CrossRef]
- Alishahi, M.; Yaghmaee Moghadam, M.H.; Pourreza, H. Designing Optimized Scheduling QoS-Aware RPL for Sensor-Based Smart Grid Communication Network. Comput. Knowl. Eng. 2017, 1, 60500. [Google Scholar] [CrossRef]
- Shi, P.; Gu, C.; Ge, C.; Jing, Z. QoS aware routing protocol through cross-layer approach in asynchronous duty-cycled WSNs. IEEE Access 2019, 7, 57574–57591. [Google Scholar] [CrossRef]
- Mahadevan, I.; Sivalingam, K.M. Quality of service architectures for wireless networks: IntServ and DiffServ models. In Proceedings of the Fourth International Symposium on Parallel Architectures, Algorithms, and Networks (I-SPAN’99), Perth, WA, Australia, 23–25 June 1999; pp. 420–425. [Google Scholar] [CrossRef]
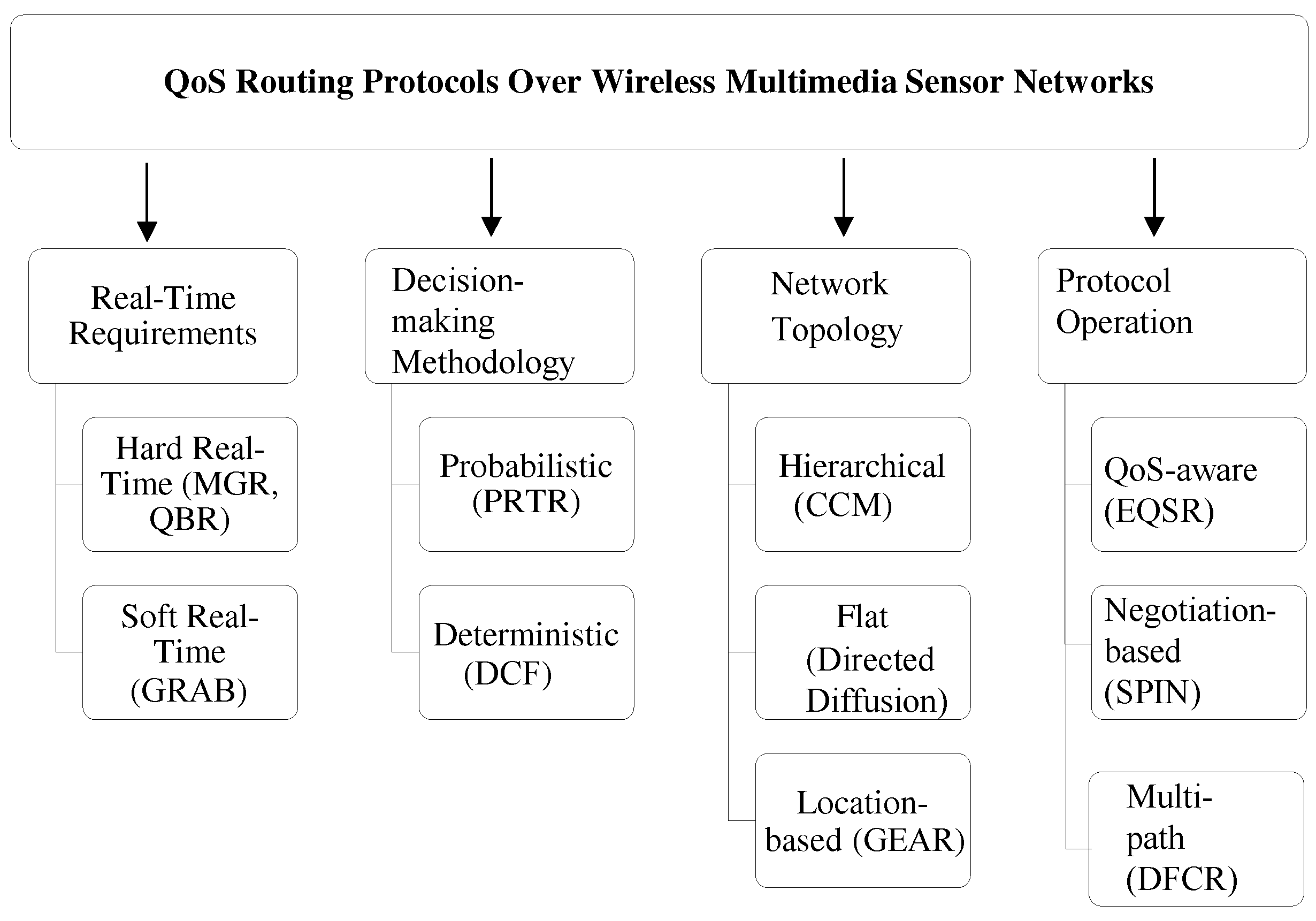
- Alanazi, A.; Elleithy, K. Real-Time QoS Routing Protocols in Wireless Multimedia Sensor Networks: Study and Analysis. Sensors 2015, 15, 22209. [Google Scholar] [CrossRef]
- Asif, M.; Khan, S.; Ahmad, R.; Sohail, M.; Singh, D. Quality of Service of Routing Protocols in Wireless Sensor Networks: A Review. IEEE Access 2017, 5, 1846–1871. [Google Scholar] [CrossRef]
- Agarkhed, J.; Dattatraya, P.Y.; Patil, S.R. Performance evaluation of QoS-aware routing protocols in wireless sensor networks. In Proceedings of the First International Conference on Computational Intelligence and Informatics; Satapathy, S., Prasad, V., Rani, B., Udgata, S., Raju, K., Eds.; Advances in Intelligent Systems and Computing; Springer: Singapore, 2017; Volume 507. [Google Scholar] [CrossRef]
- Venugopal, K.; Shiv Prakash, T.; Kumaraswamy, M. QoS Routing Algorithms for Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar] [CrossRef]
- Chandel, A.; Chouhan, V.S.; Sharma, S. A Survey on Routing Protocols for Wireless Sensor Networks. In Proceedings of the Advances in Information Communication Technology and Computing; Goar, V., Kuri, M., Kumar, R., Senjyu, T., Eds.; Springer: Singapore, 2021; pp. 143–164. [Google Scholar]
- Amutha, J.; Sharma, S.; Sharma, S.K. Strategies based on various aspects of clustering in wireless sensor networks using classical, optimization and machine learning techniques: Review, taxonomy, research findings, challenges and future directions. Comput. Sci. Rev. 2021, 40, 100376. [Google Scholar] [CrossRef]
- Zagrouba, R.; Kardi, A. Comparative study of energy efficient routing techniques in wireless sensor networks. Information 2021, 12, 42. [Google Scholar] [CrossRef]
- Singh, S.P.; Kumar, N.; Alghamdi, N.S.; Dhiman, G.; Viriyasitavat, W.; Sapsomboon, A. Next-Gen WSN Enabled IoT for Consumer Electronics in Smart City: Elevating Quality of Service Through Reinforcement Learning-Enhanced Multi-Objective Strategies. IEEE Trans. Consum. Electron. 2024, 70, 6507–6518. [Google Scholar] [CrossRef]
- Benelhouri, A.; Idrissi-Saba, H.; Antari, J. An evolutionary routing protocol for load balancing and QoS enhancement in IoT enabled heterogeneous WSNs. Simul. Model. Pract. Theory 2023, 124, 102729. [Google Scholar] [CrossRef]
- Chandnani, N.; Khairnar, C.N. Quality of Service (QoS) Enhancement of IoT WSNs Using an Efficient Hybrid Protocol for Data Aggregation and Routing. SN Comput. Sci. 2023, 4, 762. [Google Scholar] [CrossRef]
- Lenka, S.; Pradhan, S.K.; Nanda, A. Quality of Service (QoS) enhancement of IoT-based Wireless Sensor Network using fuzzy best first search approach. In Proceedings of the 2022 International Conference on Intelligent Controller and Computing for Smart Power (ICICCSP), Hyderabad, India, 22–23 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Ghawy, M.Z.; Amran, G.A.; AlSalman, H.; Ghaleb, E.; Khan, J.; Al-Bakhrani, A.A.; Alziadi, A.M.; Ali, A.; Ullah, S.S. An effective wireless sensor network routing protocol based on particle swarm optimization algorithm. Wirel. Commun. Mob. Comput. 2022, 2022, 8455065. [Google Scholar] [CrossRef]
- Pundir, M.; Sandhu, J.K. A Systematic Review of Quality of Service in Wireless Sensor Networks using Machine Learning: Recent Trend and Future Vision. J. Netw. Comput. Appl. 2021, 188, 103084. [Google Scholar] [CrossRef]
- Gantassi, R.; Gouissem, B.B.; Cheikhrouhou, O.; el Khediri, S.; Hasnaoui, S. Optimizing Quality of Service of Clustering Protocols in Large-Scale Wireless Sensor Networks with Mobile Data Collector and Machine Learning. Secur. Commun. Netw. 2021, 2021, 5531185:1–5531185:12. [Google Scholar] [CrossRef]
- Afroz, F.; Braun, R. QX-MAC: Improving QoS and Energy Performance of IoT-based WSNs using Q-Learning. In Proceedings of the 2021 IEEE 46th Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 4–7 October 2021; pp. 455–462. [Google Scholar] [CrossRef]
- Samridhi, S.; Liscano, R. Performance comparison of a Software Defined and Wireless Sensor Network. In Proceedings of the 2020 International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Mostafaei, H.; Menth, M. Software-defined wireless sensor networks: A survey. J. Netw. Comput. Appl. 2018, 119, 42–56. [Google Scholar] [CrossRef]
- Karakus, M.; Durresi, A. Quality of Service (QoS) in Software Defined Networking (SDN): A survey. J. Netw. Comput. Appl. 2017, 80, 200–218. [Google Scholar] [CrossRef]
- El-Fouly, F.H.; Kachout, M.; Alharbi, Y.; Alshudukhi, J.S.; Alanazi, A.; Ramadan, R.A. Environment-Aware Energy Efficient and Reliable Routing in Real-Time Multi-Sink Wireless Sensor Networks for Smart Cities Applications. Appl. Sci. 2023, 13, 605. [Google Scholar] [CrossRef]
- Cherappa, V.; Thangarajan, T.; Meenakshi Sundaram, S.S.; Hajjej, F.; Munusamy, A.K.; Shanmugam, R. Energy-Efficient Clustering and Routing Using ASFO and a Cross-Layer-Based Expedient Routing Protocol for Wireless Sensor Networks. Sensors 2023, 23, 2788. [Google Scholar] [CrossRef]
- Panagiotis, K.; Panagiotis, T.; Helen, L.; Sarakis, L.; Papaefstathiou, I.; Zahariadis, T. Evaluating routing metric composition approaches for QoS differentiation in low power and lossy networks. Wirel. Netw. 2013, 19, 1269–1284. [Google Scholar] [CrossRef]
- Abbasi, M.R.; Guleria, A.; Devi, M.S. Traffic engineering in software defined networks: A survey. J. Telecommun. Inf. Technol. 2016, 66, 3–14. [Google Scholar] [CrossRef]
- Ancillotti, E.; Vallati, C.; Bruno, R.; Mingozzi, E. A reinforcement learning-based link quality estimation strategy for RPL and its impact on topology management. Comput. Commun. 2017, 112, 1–13. [Google Scholar] [CrossRef]
- Xue, G.; Sen, A.; Zhang, W.; Tang, J.; Thulasoraman, K. Thulasiraman, Finding a path subject to many additive QoS constraints. IEEE/ACM Trans. Netw. 2007, 15, 201–211. [Google Scholar] [CrossRef]
- De Neve, H.; Van Mieghem, P. TAMCRA: A tunable accuracy multiple constraints routing algorithm. Comput. Commun. 2000, 23, 667–679. [Google Scholar] [CrossRef]
- Singh, B.; Kumar, R.; Singh, V.P. Reinforcement learning in robotic applications: A comprehensive survey. Artif. Intell. Rev. 2022, 55, 945–990. [Google Scholar] [CrossRef]
- Barthel, D.; Vasseur, J.P.; Pister, K.; Kim, M.; Dejean, N. Routing Metrics Used for Path Calculation in Low-Power and Lossy Networks. Technical Report RFC 6551; RFC Editor. 2012, pp. 1–30. Available online: https://datatracker.ietf.org/doc/html/rfc6551 (accessed on 15 May 2025).
- Elhabyan, R.; Shi, W.; St-Hilaire, M. A Pareto optimization-based approach to clustering and routing in wireless sensor networks. J. Netw. Comput. Appl. 2018, 114, 57–69. [Google Scholar] [CrossRef]
- Shin, B.; Lee, D. An efficient local repair-based multi-constrained routing for congestion control in wireless mesh networks. Wirel. Commun. Mob. Comput. 2018, 2893494. [Google Scholar] [CrossRef]
- Van Mieghem, P.; Kuipers, F.A. Concepts of exact QoS routing algorithms. IEEE/ACM Trans. Netw. 2004, 12, 851–864. [Google Scholar] [CrossRef]
- Torkzadeh, S.; Soltanizadeh, H.; Orouji, A.A. Multi-constraint QoS routing using a customized lightweight evolutionary strategy. Soft Comput. 2019, 23, 693–706. [Google Scholar] [CrossRef]
- Julstrom, B. Greedy heuristics for the bounded diameter minimum spanning tree problem. J. Exp. Algorithmics 2009, 14, 1. [Google Scholar] [CrossRef]
- Hou, X.; Hu, Y.; Wang, F. Overview of Task Offloading of Wireless Sensor Network in Edge Computing Environment. In Proceedings of the 2023 IEEE 6th International Conference on Electronic Information and Communication Technology (ICEICT), Qingdao, China, 21–24 July 2023; pp. 1018–1022. [Google Scholar] [CrossRef]
- Almutairi, J.; Aldossary, M. A novel approach for IoT tasks offloading in edge-cloud environments. J. Cloud Comput. 2021, 10, 28. [Google Scholar] [CrossRef]
- Liu, F.; Huang, Z.; Wang, L. Energy-Efficient Collaborative Task Computation Offloading in Cloud-Assisted Edge Computing for IoT Sensors. Sensors 2019, 19, 1105. [Google Scholar] [CrossRef]
- Abbasi, M.; Shahraki, A.; Taherkordi, A. Deep Learning for Network Traffic Monitoring and Analysis (NTMA): A Survey. Comput. Commun. 2021, 170, 19–41. [Google Scholar] [CrossRef]
- Khallef, W.; Molnar, M.; Bensliman, A.; Durand, S. On the QoS Routing with RPL. In Proceedings of the 2017 International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 28–30 November 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Cousin, B.; Molnar, M. Fast Reconfiguration of Dynamic Networks. In Proceedings of the 2007 International Workshop on Dynamic Networks, San José, CA, USA, 31 October–2 November 2007; pp. 1–6. [Google Scholar]
- Cousin, B.; Adépo, J.C.; Oumtanaga, S.; Babri, M. Tree reconfiguration without lightpath interruption in WDM optical networks. Int. J. Internet Protoc. Technol. 2012, 7, 85–95. [Google Scholar] [CrossRef]
- Mostafa, B.; Molnár, M.; Saleh, M.; Benslimane, A.; Kassem, S. Dynamic Distributed Monitoring for 6LoWPAN-based IoT Networks. Infocommun. J. 2023, 15, 64–76. [Google Scholar] [CrossRef]
- Mehlhorn, K.; Näher, S. LEDA: A Platform for Combinatorial and Geometric Computing; Cambridge University Press: Cambridge, UK, 1999; Available online: https://dl.acm.org/doi/10.5555/331319 (accessed on 15 May 2025).
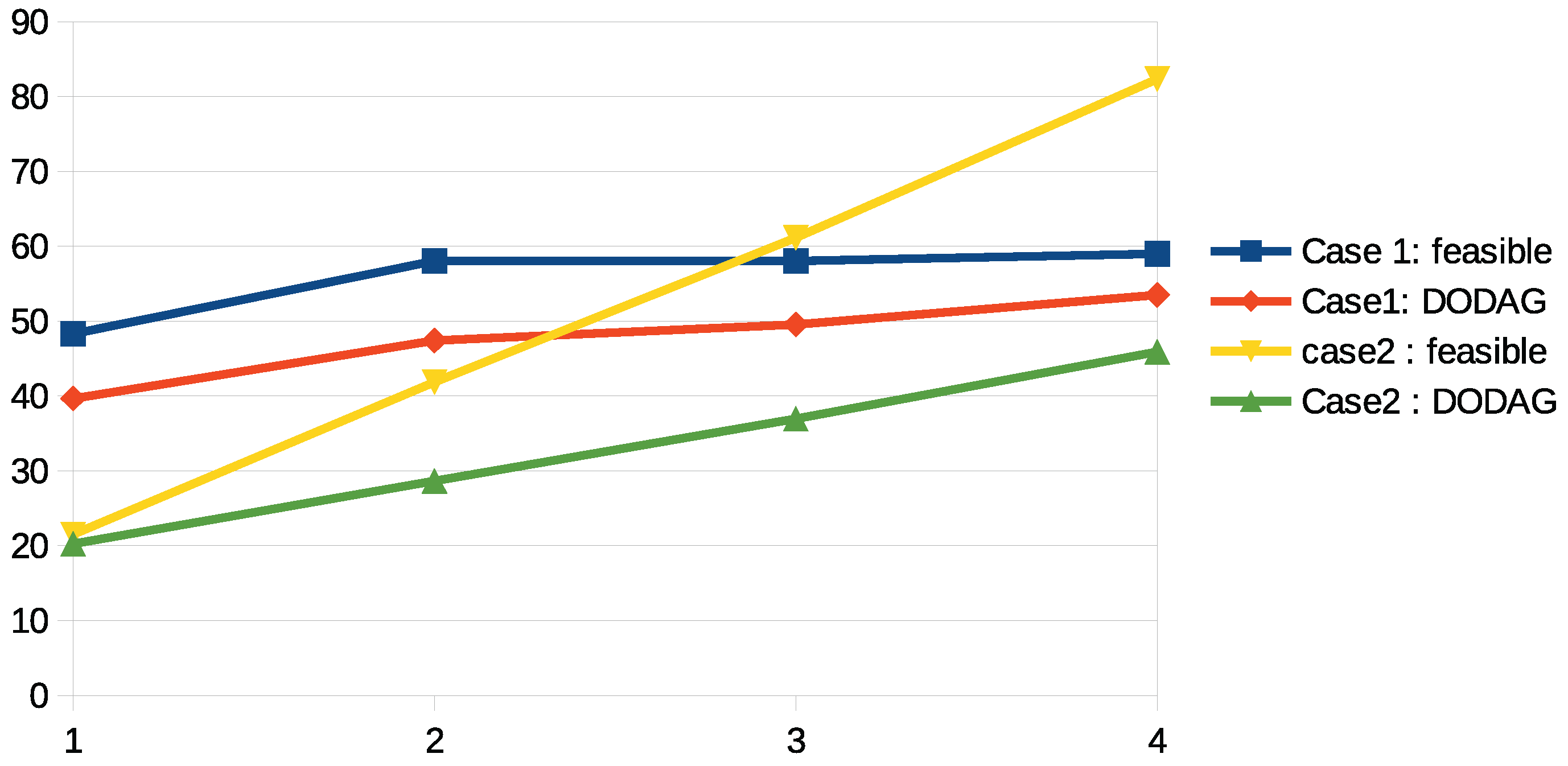
| Aspect | Gaddour et al. [16] | Ghaleb et al. [5] | GRPAR [19] | OMC-RPL [20] | TDL-BasedProtocol [21] | ProposedApproach |
|---|---|---|---|---|---|---|
| Modification of Objective Function | Yes | Yes (Composite metrics) | No | Yes (custom multi-metric) | No (cross-layer based) | No |
| Increase in Control Overhead | Yes (Fuzzy logic extension) | Moderate (multi-metric dissemination) | Low (greedy heuristic) | Moderate (multi-class weighting) | Moderate (cross-layer metrics) | No |
| External Offloading to Edge | No | No | No | No | No | Yes |
| Lightweight Conflict Detection | No | No | No | No | No | Yes |
| Redundancy Augmentation Mechanism | No | No | No | No | No | Yes |
| Standard Compliance with RPL | Partial | Partial (Objective Function modifications) | Partial | Partial | No (non-RPL based) | Full |
| Ref. | Objectives and Contributions | Limitations |
|---|---|---|
| Singh et al. [30] | Introduced reinforcement learning for multi-objective QoS optimization in edge-enabled WSN-IoT systems. | complexity of simultaneous multi-objective optimization. |
| Benelhourri et al. [31] | Proposed an evolutionary genetic algorithm for Cluster Head (CH) selection in WSNs; energy-efficient CH selection and routing. | Fitness function tuning can be computationally intensive. |
| Chandnani et al. [32] | Proposed a hybrid protocol for data aggregation and reactive routing to improve QoS at the network layer in WSNs. Enhances routing efficiency and data collection. | Not explicitly tested for energy efficiency in large-scale deployments. Primarily simulation-based, and lacks implementation in diverse environments. |
| Lenka et al. [33] | Proposed hierarchical routing for IoT using k-means clustering and fuzzy inference. Effective CH selection and reduced intra-cluster communication. | Computational complexity of CH selection in resource-constrained networks. |
| Ghawy et al. [34] | Developed a multi-path protocol using Particle Swarm Optimization (PSO) for traffic fairness and load balancing in WSNs. | PSO may require high computation time and lacks real-world testing on dynamic WSN topologies. |
| Pundir et al. [35] | Comprehensive analysis of QoS parameters and frameworks of machine-learning-based QoS techniques in WSNs. | Focused on literature review without detailed implementation. |
| Gantassi et al. [36] | Combined K-means clustering with a mobile data collector (MDC) for QoS improvement in large-scale WSNs. | MDC introduces additional complexity and latency; mobility optimization is not addressed. |
| Afroz et al. [37] | Proposed an energy-efficient MAC protocol using Q-learning and adaptive modulation for QoS improvement. | Limited to specific scenarios; may lack scalability in diverse WSN applications. |
| Samridhi et al. [38] | Compared SDN-enabled WSNs to conventional WSNs using the RPL and identified overhead trade-offs. | Limited to small-scale testbeds. |
| Mostafaei et al. [39] | Highlighted SD-WSN improvements via OpenFlow for QoS provisioning in resource-constrained environments. | Design flaws identified in SDN-based WSNs, with high computational overhead. |
| Cisco [22] | Differentiated Services (DiffServ) approach for prioritizing traffic classes to meet QoS requirements. | Less suited for resource-constrained WSNs; focused on Internet-scale networks. |
| Karakas et al. [40] | Provided a detailed overview of SDN architecture for centralized and programmable flow management to enhance QoS and optimize resource allocation. | Overhead in resource-limited WSNs and latency in centralized SDN designs. |
| Algorithm | Worst-Case Complexity |
|---|---|
| Algorithm 1 (Non-Dominated QoS Paths) | |
| Algorithm 2 (DODAG Computation) | |
| Algorithm 3 (DODAG Redundancy) |
| L | Connected to the BR | Feasible Nodes () | Unfeasible Nodes () | Nodes in the First DODAG | Unfeasible Nodes Using | Unfeasible Nodes Using |
|---|---|---|---|---|---|---|
| 9 | 55.85 | 41.9 | 13.95 | 35.9 | 17.25 | 15.3 |
| 10 | 55.85 | 41.85 | 14 | 37.1 | 16.2 | 14.85 |
| 11 | 56.1 | 49.1 | 7 | 40.75 | 10.9 | 8.5 |
| 12 | 56.7 | 52.65 | 4.05 | 45.45 | 6.1 | 4.9 |
| 13 | 55.85 | 50.95 | 4.9 | 43.25 | 6.5 | 5.85 |
| 14 | 57 | 53.9 | 3.1 | 44.95 | 3.9 | 3.7 |
| QoS Threshold (L) | EX | Baseline Max | Preservation (%) | ||
|---|---|---|---|---|---|
| 9 | 41.90 | 17.25 | 15.30 | 17.25 | 142.90 |
| 10 | 41.85 | 16.20 | 14.85 | 16.20 | 158.64 |
| 11 | 49.10 | 10.90 | 8.50 | 10.90 | 350.46 |
| 12 | 52.65 | 6.10 | 4.90 | 6.10 | 763.11 |
| 13 | 50.95 | 6.50 | 5.85 | 6.50 | 683.08 |
| 14 | 53.90 | 3.90 | 3.70 | 3.90 | 1282.05 |
| L | Average NL with | Average NL with | Average of Max NL with | Max NL with | Average NL with | Average of Max NL with | Max NL with |
|---|---|---|---|---|---|---|---|
| 9 | 0.86868405 | 0.7970677 | 1.7778945 | 2.70073 | 0.7702697 | 1.7467435 | 2.62914 |
| 10 | 0.86217155 | 0.7661964 | 1.6855505 | 1.70626 | 0.7437832 | 1.600896 | 3.07739 |
| 11 | 0.8869539 | 0.6627487 | 1.4499615 | 2.06338 | 0.6373038 | 1.3756695 | 2.01094 |
| 12 | 0.8927291 | 0.5788719 | 1.28033855 | 2.29483 | 0.5586699 | 1.2328301 | 2.36877 |
| 13 | 0.8978134 | 0.59460195 | 1.2450855 | 2.34292 | 0.5738024 | 1.21144645 | 2.35253 |
| 14 | 0.90484325 | 0.52155955 | 1.2165917 | 1.81337 | 0.5088827 | 1.1766933 | 1.80848 |
| Number k of Parameters | Feasible Paths | Feasible Nodes () | Nodes in DODAG | Feasible Nodes () | Unfeasible Nodes () | Feasible Nodes () | Unfeasible Nodes () |
|---|---|---|---|---|---|---|---|
| 2 | 2490.2 | 43.65 | 39.85 | 40.85 | 15.95 | 42.55 | 14.25 |
| 3 | 666.5 | 36.95 | 32.9 | 31.9 | 24.15 | 35.35 | 20.7 |
| 4 | 404.5 | 34 | 30.6 | 30.45 | 25.55 | 33.05 | 22.95 |
| 5 | 382.65 | 31.35 | 28 | 27.85 | 29.1 | 29.45 | 27.5 |
| Number k of Parameters | Feasible Paths () | Average NL with | Average NL with | NL with | Average NL with | Max NL with |
|---|---|---|---|---|---|---|
| 2 | 43.65 | 0.86887645 | 0.76564 | 1.6954283 | 0.73822055 | 1.60968735 |
| 3 | 36.95 | 0.86503695 | 0.88879065 | 1.809788 | 0.8404888 | 1.737761 |
| 4 | 34 | 0.85768205 | 0.9211531 | 1.842404 | 0.88596795 | 1.727532 |
| 5 | 31.35 | 0.85400845 | 1.08513055 | 2.2432795 | 1.04401305 | 2.0862665 |
| Number of BRs | Not Conn. to the First BR | Feasible with the First BR | Feasible (All BRs) | Active BRs from 4 | Feasible Nodes | Nodes in DODAG | |
|---|---|---|---|---|---|---|---|
| 1st case | |||||||
| Nb of | 1 | 0 | 57 | 57 | 1 | 48 | 40 |
| Nodes = 60 | 2 | 1 | 50 | 58 | 2 | 58 | 47 |
| 3 | 4 | 47 | 58 | 3 | 58 | 50 | |
| Range = 25 | 4 | 5 | 48 | 59 | 4 | 59 | 54 |
| 2nd case | |||||||
| Nb of | 1 | 48 | 25 | 25 | 1 | 22 | 20 |
| Nodes = 120 | 2 | 55 | 20 | 40 | 2 | 42 | 29 |
| 3 | 68 | 21 | 43 | 3 | 61 | 37 | |
| Range = 12 | 4 | 57 | 22 | 82 | 4 | 82 | 46 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mostafa, B.; Molnar, M. Offloaded Computation for QoS Routing in Wireless Sensor Networks. Information 2025, 16, 464. https://doi.org/10.3390/info16060464
Mostafa B, Molnar M. Offloaded Computation for QoS Routing in Wireless Sensor Networks. Information. 2025; 16(6):464. https://doi.org/10.3390/info16060464
Chicago/Turabian StyleMostafa, Basma, and Miklos Molnar. 2025. "Offloaded Computation for QoS Routing in Wireless Sensor Networks" Information 16, no. 6: 464. https://doi.org/10.3390/info16060464
APA StyleMostafa, B., & Molnar, M. (2025). Offloaded Computation for QoS Routing in Wireless Sensor Networks. Information, 16(6), 464. https://doi.org/10.3390/info16060464







