Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain
Abstract
1. Introduction
- Proposing a framework to adaptive protection of IoT environments based on deep leaning and blockchain.
- Building and simulating data collection from IoT sensors;
- Logging sensed data and model results using blockchain for secure and immutable records within our hybrid framework.
- Applying a deep learning model to detect anomalies in real time.
- Evaluating system robustness in handling sensor malfunctions.
2. Related Studies
3. Methodology Mechanism
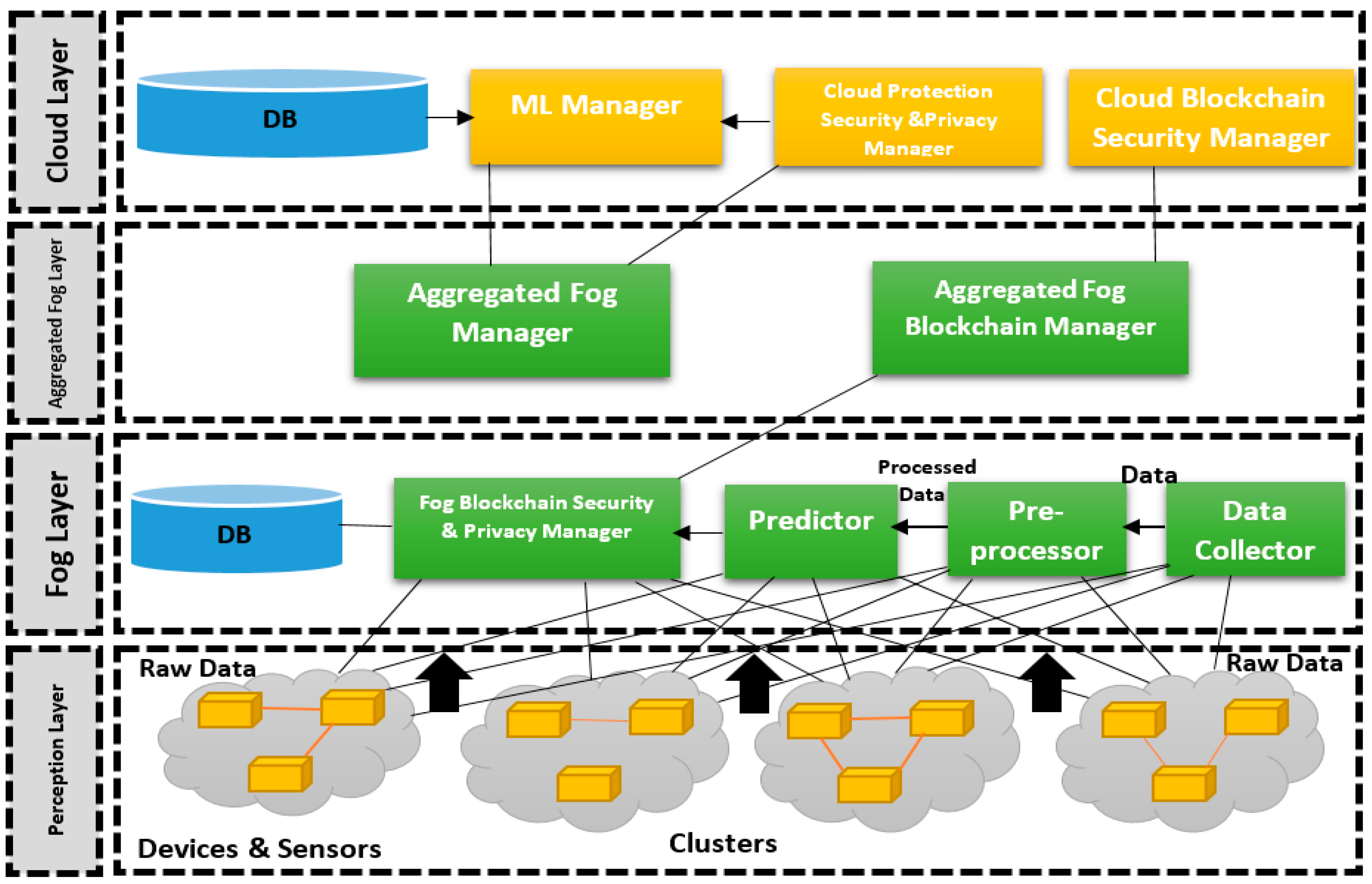
- The Hybrid Framework Layers
- Low-level architecture’s perception layer;
- Low-level architecture’s fog layer;
- Low-level architecture’s aggregated fog layer;
- Low-level architecture’s cloud layer.
4. Addressing IoT Security and Privacy Risks
4.1. Specific Risk Scenarios
- 1.
- Attack scenarios:
- 2.
- Data leakage incidents:
4.2. Mitigation Mechanism Through a Hybrid Framework
4.3. Practical Effectiveness and Benefits
5. Evaluation and Validation
- 1.
- Sensors Configuration
- 2.
- Sensor Malfunction Simulation
- 3.
- DL Model Architecture
- Input layer: 24 features (sensor data attributes);
- Hidden layers: Three hidden layers with ReLU activations (128, 64, and 32 neurons);
- Output layer: A softmax layer for multi-class classification (7 classes).
- 4.
- Model Training and Experiment Steps
- Import libraries;
- Load and preprocess data;
- Define the neural network model;
- Compile the model;
- Train the model;
- Integrate the blockchain class;
- Prepare the IoT device environment;
- Run the simulation function in SimPy.
- 1.
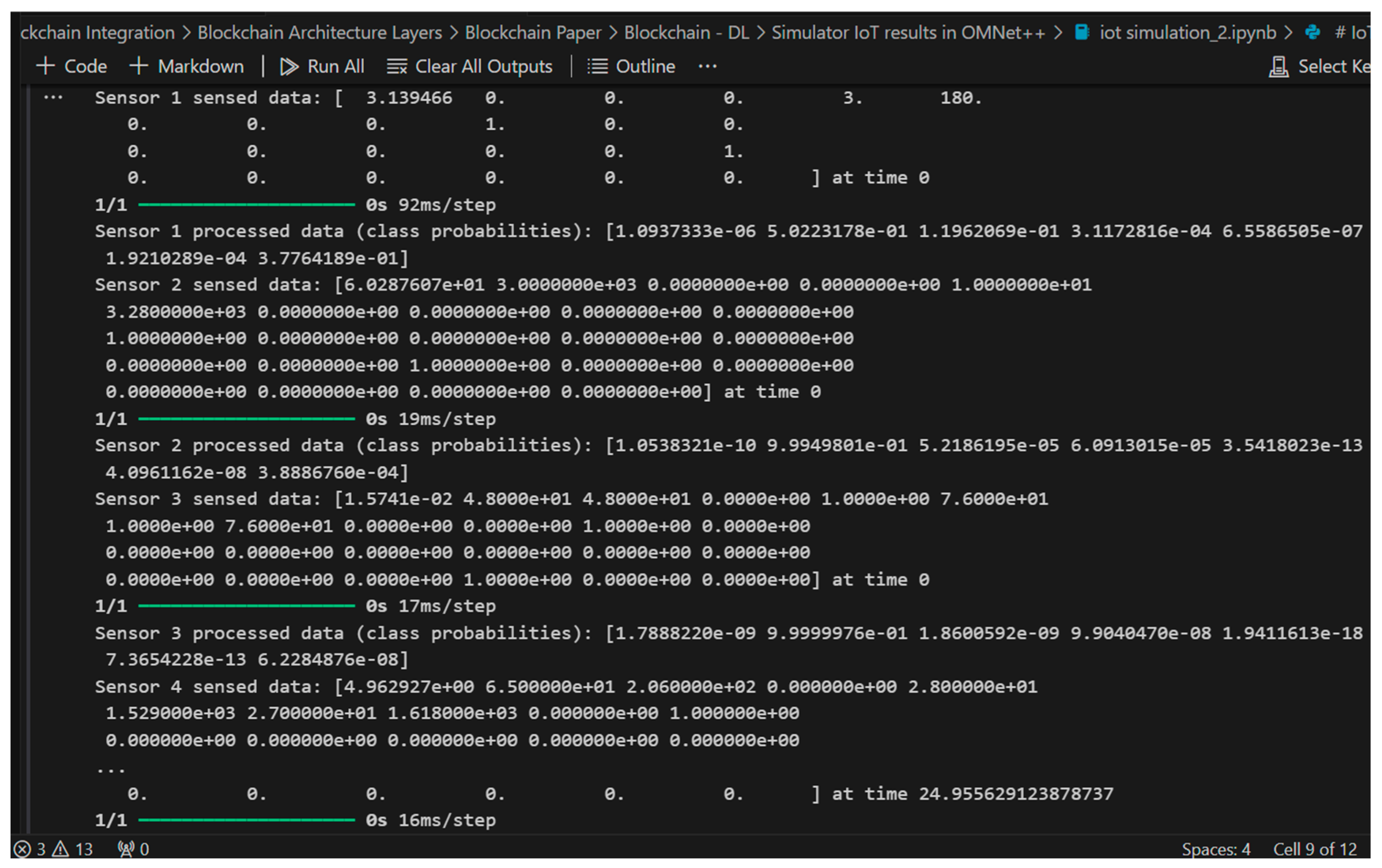
- Sensor Sensed Data Sample
- 2.
- Sensor Malfunction Detection
- Sensor 3 before malfunction: class 1 (50.51% confidence);
- Sensor 3 after malfunction: no data (logged as inactive in the blockchain).
- 3.
- SENSOR 1 DATA Results
- 4.
- SENSOR 2 DATA Results
- 5.
- SENSOR 3 DATA Results
- 6.
- SENSOR 4 DATA Results
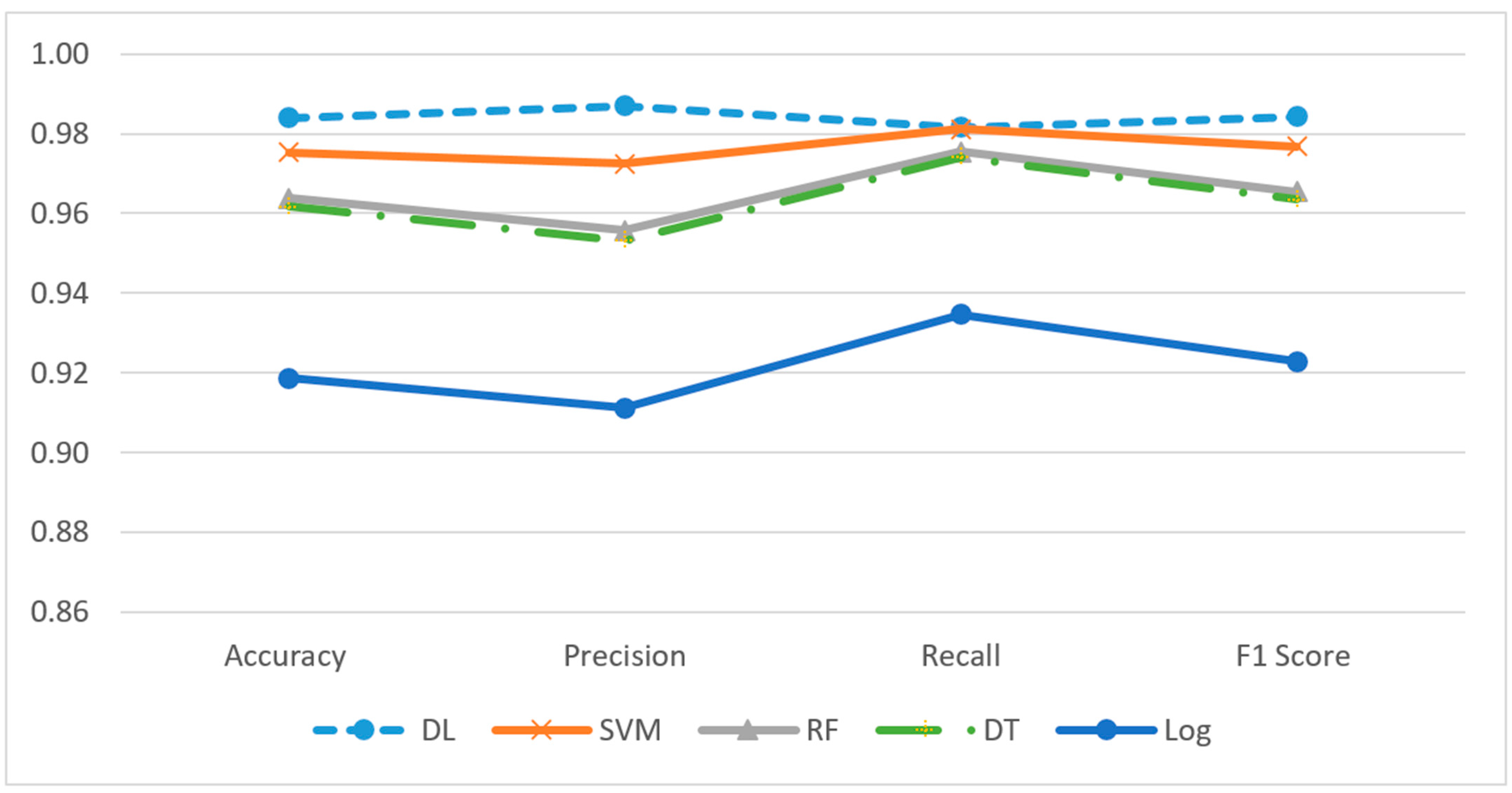
Evaluation Metrics Results and Comparison Results of DL(ANN), SVM, RF, DT, and Log R
- 1.
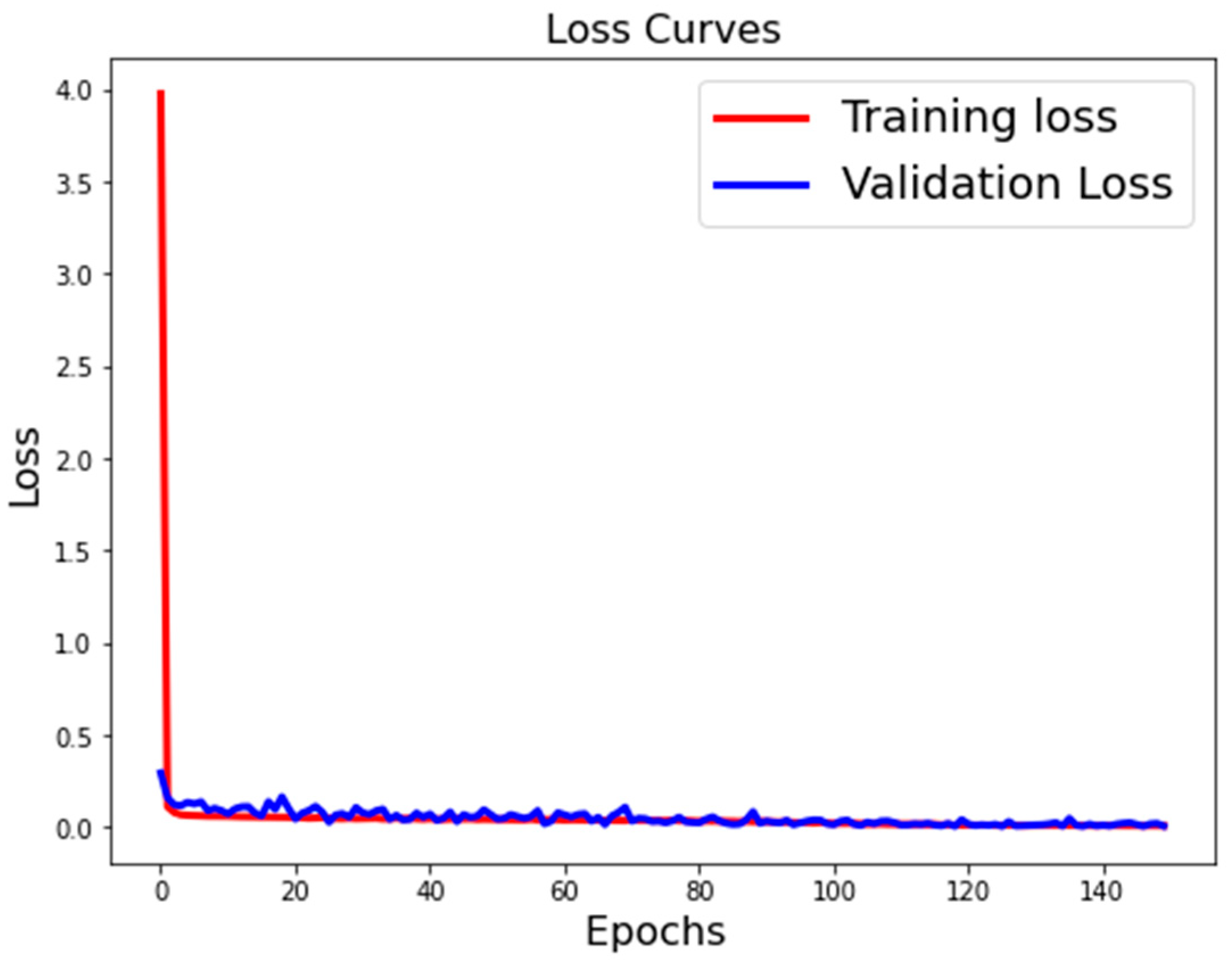
- Model Accuracy and Loss Function Accuracy Metric
- 2.
- Loss Function Metric
- 3.
- Precision Metric
- 4.
- COMPARATIVE EVALUATION WITH STATE-OF-THE-ART METHODS
- 5.
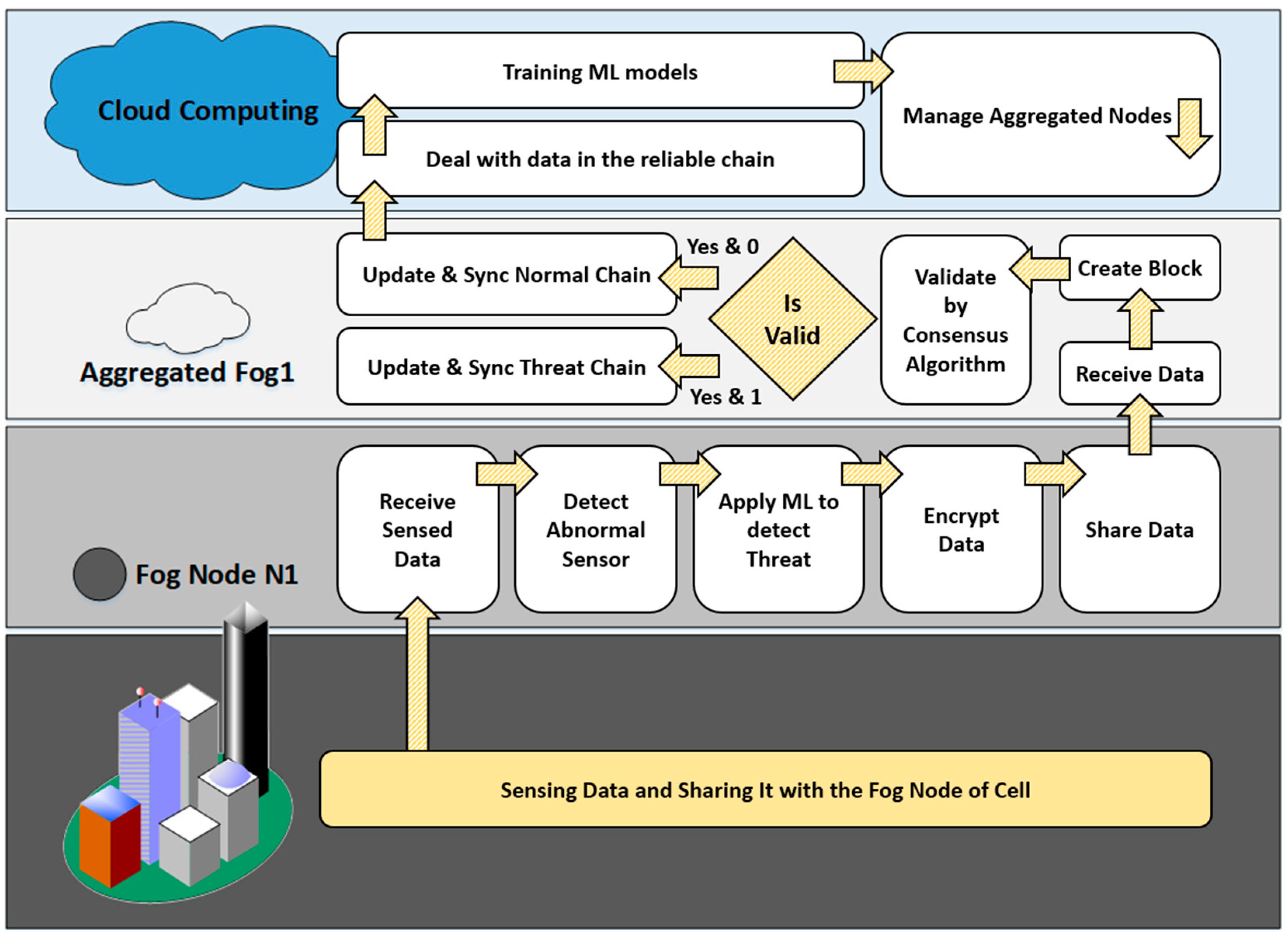
- DYNAMIC INTERACTION and RESPONSE MECHANISM
- (1)
- Statistical level (fog layer);
- (2)
- Automated level (fog layer);
- (3)
- Encryption (fog layer);
- (4)
- Consensus verification (fog and aggregated fog);
- (5)
- Availability level (aggregated fog layer);
- (6)
- Permanent storage level (cloud layer).
6. Discussion
- A.
- Model Performance
- B.
- Robustness to Malfunctions
- C.
- Proposed Cyberattack Detection Method and Algorithm Discussion
| Algorithm 1. IoT Attack Detection with Enhanced Blockchain Logging |
|
| Algorithm 2. Blockchain-Enhanced IoT Attack Detection System with Mathematical Notations and Enhanced Blockchain Logging. |
|
7. Conclusions
- Anomaly detection enhancements: More sophisticated anomaly detection models to detect sensor malfunctions should be implemented.
- Model optimization: Further tuning of the deep learning model, including hyperparameters and architecture improvements, is required.
- Blockchain integration: The blockchain functionality should be extended to automatically trigger alerts upon detecting sensor malfunctions or data anomalies, in addition to creating another chain for roles and models.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Balaji, S.; Nathani, K.; Santhakumar, R. IoT technology, applications and challenges: A contemporary survey. Wirel. Pers. Commun. 2019, 108, 363–388. [Google Scholar] [CrossRef]
- Costa, F.; Genovesi, S.; Borgese, M.; Michel, A.; Dicandia, F.A.; Manara, G. A review of RFID sensors, the new frontier of internet of things. Sensors 2021, 21, 3138. [Google Scholar] [CrossRef] [PubMed]
- Andriulo, F.C.; Fiore, M.; Mongiello, M.; Traversa, E.; Zizzo, V. Edge Computing and Cloud Computing for Internet of Things: A Review. Informatics 2024, 11, 71. [Google Scholar] [CrossRef]
- Ogonji, M.M.; Okeyo, G.; Wafula, J.M. A survey on privacy and security of Internet of Things. Comput. Sci. Rev. 2020, 38, 100312. [Google Scholar] [CrossRef]
- Hussain, A.; Ali, T.; Althobiani, F.; Draz, U.; Irfan, M.; Yasin, S.; Alqhtani, S. Security framework for IoT based real-time health applications. Electronics 2021, 10, 719. [Google Scholar] [CrossRef]
- Abi Sen, A.A.; Eassa, F.A.; Jambi, K.; Yamin, M. Preserving privacy in internet of things: A survey. Int. J. Inf. Technol. 2018, 10, 189–200. [Google Scholar] [CrossRef]
- Ali, I.A.; Bukhari, W.A.; Adnan, M.; Kashif, M.I.; Danish, A.; Sikander, A. Security and privacy in IoT-based Smart Farming: A review. Multimed. Tools Appl. 2024, 1–61. [Google Scholar] [CrossRef]
- Fabrègue, B.F.G.; Bogoni, A. Privacy and Security Concerns in the Smart City. Smart Cities 2023, 6, 586–613. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Surashe, S.V. Privacy and security comparison of web browsers: A review. In International Conference on Advanced Information Networking and Applications; Springer International Publishing: Cham, Switzerland, 2022; pp. 459–470. [Google Scholar]
- Zhang, Y.; Wu, S.; Jin, B. A secure and privacy-aware framework for IoT based on edge and fog computing. Future Gener. Comput. Syst. 2023, 148, 110–122. [Google Scholar]
- Ju, Z.; Zhang, H.; Li, X.; Chen, X.; Han, J.; Yang, M. A survey on attack detection and resilience for connected and automated vehicles: From vehicle dynamics and control perspective. IEEE Trans. Intell. Veh. 2022, 7, 815–837. [Google Scholar] [CrossRef]
- Chen, M.; Challita, U.; Saad, W.; Yin, C.; Debbah, M. Artificial neural networks-based machine learning for wireless networks: A tutorial. IEEE Commun. Surv. Tutor. 2019, 21, 3039–3071. [Google Scholar] [CrossRef]
- Batista, A.J.; Campello, R.J.; Sander, J. Active semi-supervised classification based on multiple clustering hierarchies. In Proceedings of the IEEE International Conference on Data Science and Advanced Analytics (DSAA), Montreal, QC, Canada, 17–19 October 2016; pp. 11–20. [Google Scholar]
- Pang, G.; Shen, C.; Cao, L.; Hengel, A.V.D. Deep learning for anomaly detection: A review. ACM Comput. Surv. (CSUR) 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the Internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Okfie, M.I.H.; Mishra, S. Anomaly Detection in IIoT Transactions using Machine Learning: A Lightweight Blockchain-based Approach. Engineering. Technol. Appl. Sci. Res. 2024, 14, 14645–14653. [Google Scholar] [CrossRef]
- Alsharif, N.A.; Mishra, S.; Alshehri, M. IDS in IoT using Machine Learning and Blockchain. Engineering. Technol. Appl. Sci. Res. 2023, 13, 11197–11203. [Google Scholar] [CrossRef]
- Abusitta, A.; de Carvalho, G.H.; Wahab, O.A.; Halabi, T.; Fung, B.C.; Al Mamoori, S. Deep learning-enabled anomaly detection for IoT systems. Internet Things 2023, 21, 100656. [Google Scholar] [CrossRef]
- Guo, L. Application of blockchain-based deep learning algorithm in the enterprise Internet of Things system. Mob. Inf. Syst. 2022, 2022, 9943452. [Google Scholar] [CrossRef]
- Shafay, M.; Ahmad, R.W.; Salah, K.; Yaqoob, I.; Jayaraman, R.; Omar, M. Blockchain for deep learning: Review and open challenges. Clust. Comput. 2023, 26, 197–221. [Google Scholar] [CrossRef]
- Khan, M.A.; Abbas, S.; Rehman, A.; Saeed, Y.; Zeb, A.; Uddin, M.I.; Ali, A. A machine learning approach for blockchain-based smart home network security. IEEE Netw. 2020, 35, 223–229. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Kumar, A.; Franklin, A.A.; Garg, S.; Singh, S. Blockchain and deep learning for secure communication in digital twin-empowered industrial IoT network. IEEE Trans. Netw. Sci. Eng. 2022, 10, 2802–2813. [Google Scholar] [CrossRef]
- Gadekallu, T.R.; Manoj, M.K.; Kumar, N.; Hakak, S.; Bhattacharya, S. Blockchain-based attack detection on machine learning algorithms for IoT-based e-health applications. IEEE Internet Things Mag. 2021, 4, 30–33. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A privacy-preserving and secure framework using blockchain-based machine learning for IoT-driven smart cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Sharma, M.; Pant, S.; Kumar Sharma, D.; Datta Gupta, K.; Vashishth, V.; Chhabra, A. Enabling security for the Industrial Internet of Things using deep learning, blockchain, and coalitions. Trans. Emerg. Telecommun. Technol. 2021, 32, e4137. [Google Scholar] [CrossRef]
- Rathore, S.; Park, J.H.; Chang, H. Deep learning and blockchain-empowered security framework for intelligent 5G-enabled IoT. IEEE Access 2021, 9, 90075–90083. [Google Scholar] [CrossRef]
- Almasabi, A.M.; Khemakhem, M.; Eassa, F.; Abi Sen, A.A.; Alkhodre, A.B.; Harbaoui, A. A Smart Framework to Detect Threats and Protect Data of IoT based on Machine Learning. IEEE Access 2024, 12, 176833–176844. [Google Scholar] [CrossRef]



| Techniques Used | Feature Focus | Key Findings | Limitation |
|---|---|---|---|
| Deep learning (DL) and blockchain in IoT networks [19] | The accuracy and time efficiency of the Internet of Things system were improved, and the burden of the system operators was greatly reduced | They used a base of 3 layers to integrate the application and the network’s IoT. | It lacks certain protection mechanisms. |
| Blockchain-based deep neural networks (DLs) in clinical, and biomarker datasets within IoT environment [20] | To monitor classification and assess the response time and accuracy | They enhanced the speed and delivery of healthcare data in a healthcare management system. | The method reached accurate (98%) responses to the query. Blockchain needs to more effectively record addresses via DL or ML. |
| Deep extreme learning machine (DELM)-based system, along with blockchain (involving privacy and security) in IoT [21] | To evaluate its reliability, privacy, integrity, and accessibility | They introduced simulation results to estimate the overhead distribution, processing time, and energy. | The results were marginal in terms of their protection and privacy benefits. The result demonstrated 93.91% accuracy. |
| Integration of digital twin (DT), deep learning, and blockchain in IIoT along with the long short-term memory–sparse autoencoder (LSTMSAE) technique [22] | To ensure the integrity and authenticity of data, DL-based IDS was compared with three contemporary ML techniques, namely naive Bayes (NB), decision tree (DT) and random forest (RF), with values of 99.65%, 99.14%, 94.88%, and 95.77% | They associated a long short-term memory–sparse autoencoder (LSTMSAE) technique with DL to learn the spatial–temporal representation. | A multi-head self-attention (MHSA)-based bidirectional gated recurrent unit (BiGRU) algorithm was used to learn long-distance features and accurately detect attacks. It lacks the integration of federated learning in digital twin-enabled networks. |
| Machine learning (ML) along with blockchain (BC) [23] | To secure IoT data integrity | They used BC to secure IoT devices in e-health apps, whereas ML was used for training purposes. | It needs to focus more on feasibility checks with a different consensus for large scenarios that consider processing time, power, and data resources. |
| Blockchain-based machine learning in IoT-driven smart cities using gradient-boosting anomaly detector (GBAD) for evaluation privacy [24] | To preserve privacy and data integrity | They used a two-level privacy scheme and an intrusion detection scheme, and they used principal component analysis (PCA) to transfer raw IoT data into a novel phase. | This model detected diverse attacks with an average of 91%. |
| Blockchain and deep learning associated with coalition formation theory in IIotT [25] | To keep the IIoT network sufficiently secure | They used a proof-of-reliance algorithm to enhance computational difficulties. | The algorithm boosted the complexity of computation. Real-world IIoT apps need to be applied. |
| Deep learning (DL) along with blockchain (BC) in 5G-enabled IoT [26] | To enhance the user experience and quality of service (QoS) | They made use of DL competency for an intelligent data analysis operation and blockchain for data security. | The traditional data analytics and security methods that were used are inadequate for 5G-enabled IoT due to their distinct need for low latency and high throughput. |
| Deep learning along with blockchain technique [27] | To enhance security in IoT environment using six levels of detection and upward and downward direction among four layers to ensure and simulate a real-time IoT environment | Our hybrid makes use of a combination of two significant algorithms, deep learning and blockchain. | We successfully achieved 100% accuracy, precision, recall, and F1 score rate. We applied five different machine learning models (DL, SVM, RF, DT, and Log R). Each model achieved a different performance level. DL was the best, with 100%. |
| Model | Advantages | Disadvantages |
|---|---|---|
| DL (ANN) | High accuracy, excels at modeling complex relationships, adaptable to diverse and high-dimensional data types. | Requires substantial data and computational resources for training, less interpretable due to its “black box” nature. |
| SVM | Effective in high-dimensional spaces, robust to overfitting with proper kernel choice. | Kernel selection can be challenging, may not scale efficiently with very large datasets |
| RF | Handles missing values well, reduces overfitting via ensemble learning, provides feature importance insights. | Slower training and prediction with many trees, less effective on sparse or highly complex data |
| DT | Easy to interpret, fast to train and predict, handles both numerical and categorical data. | Prone to overfitting with deep trees, may not generalize as well to complex patterns. |
| Log R | Simple to implement, interpretable, quick to train on smaller datasets | Assumes linear relationships, underperforms with complex, non-linear data |
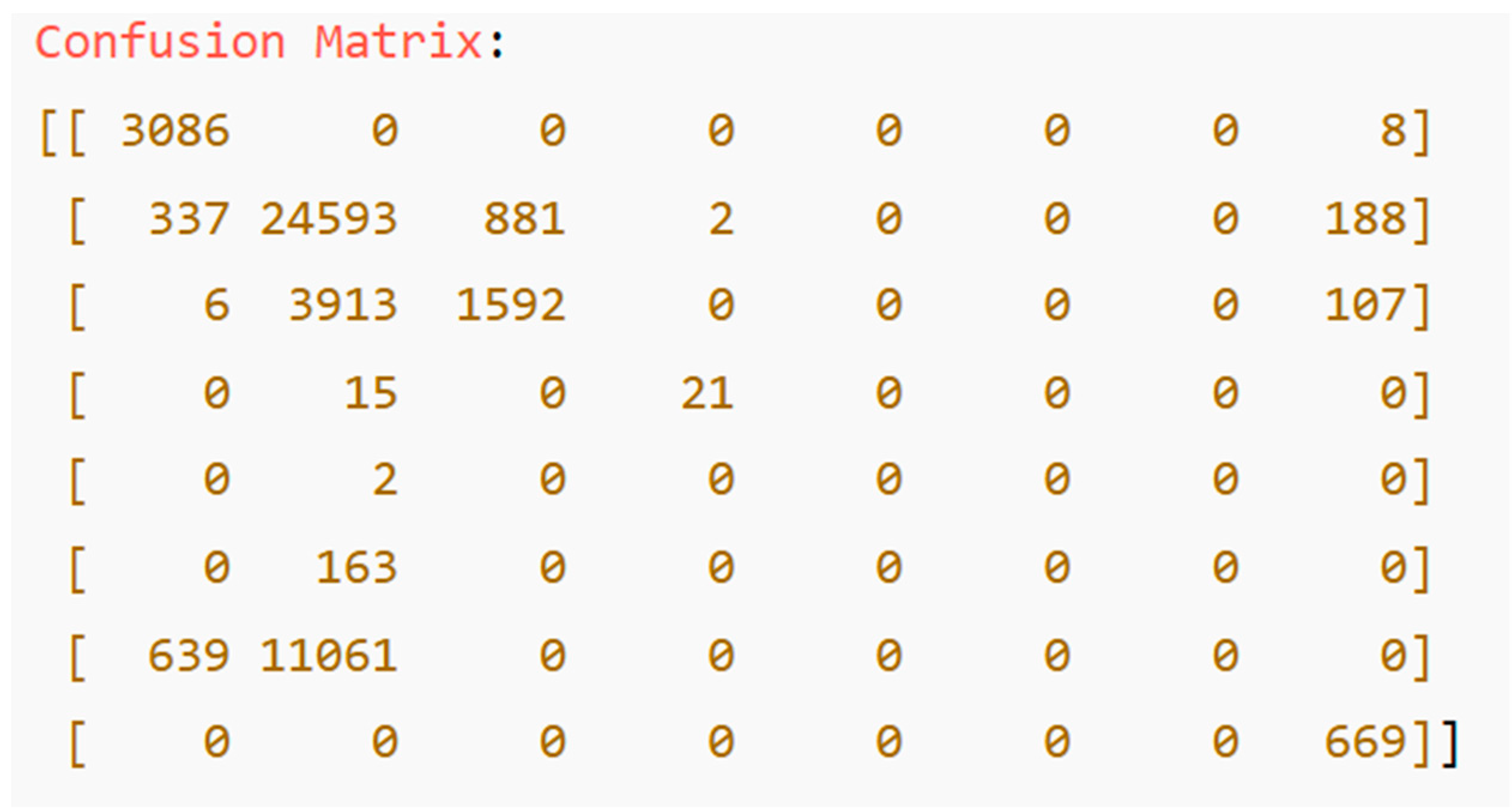
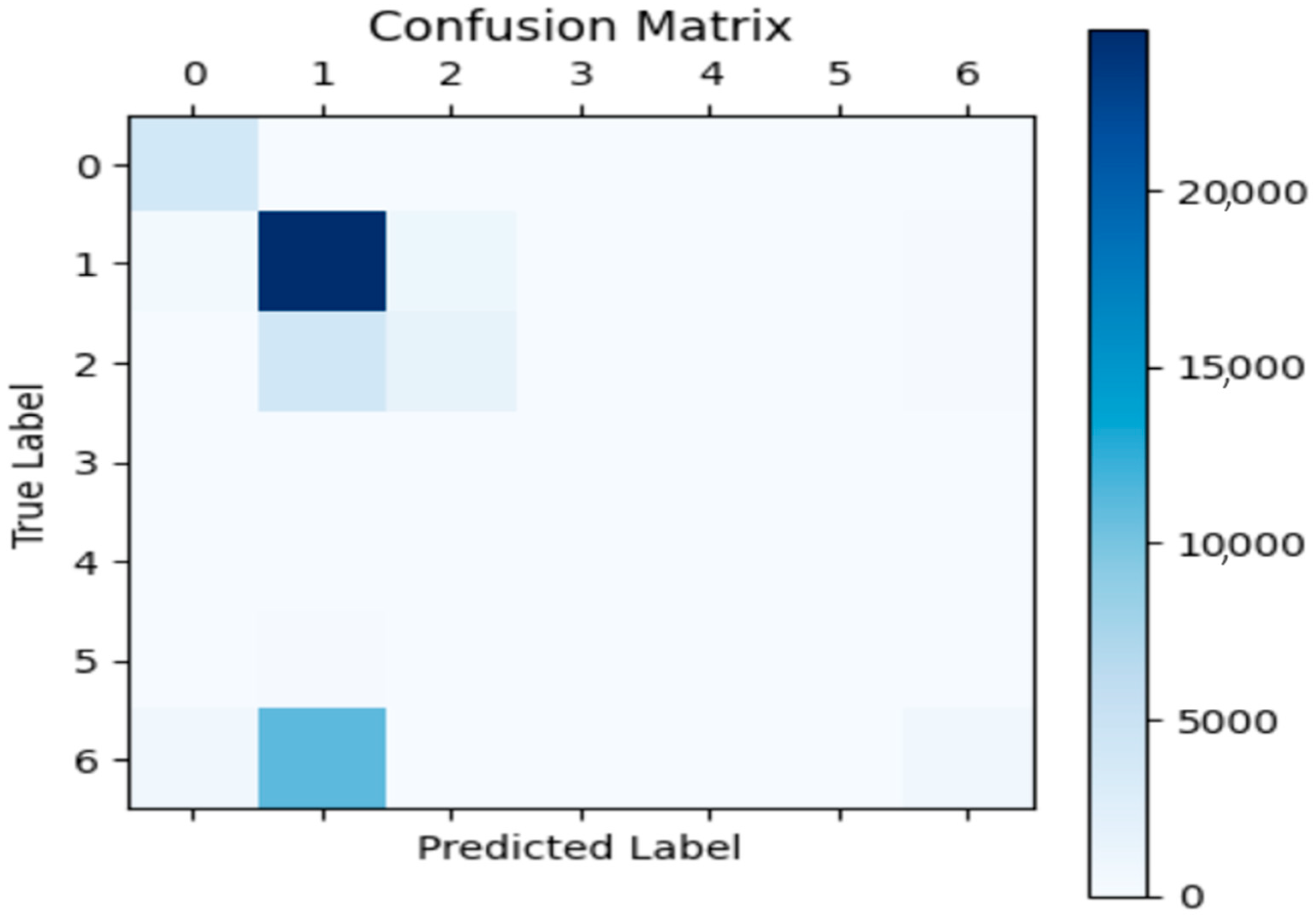
| TP | TN | FP | FN | Accuracy | Precision | Recall | F1 Score | |
|---|---|---|---|---|---|---|---|---|
| DL | 2511 | 2398 | 33 | 47 | 0.98 | 0.99 | 0.98 | 0.98 |
| SVM | 778 | 685 | 22 | 15 | 0.98 | 0.97 | 0.98 | 0.98 |
| RF | 755 | 681 | 35 | 19 | 0.96 | 0.96 | 0.98 | 0.97 |
| DT | 753 | 680 | 37 | 20 | 0.96 | 0.95 | 0.97 | 0.96 |
| LogR | 729 | 649 | 71 | 51 | 0.92 | 0.91 | 0.93 | 0.92 |
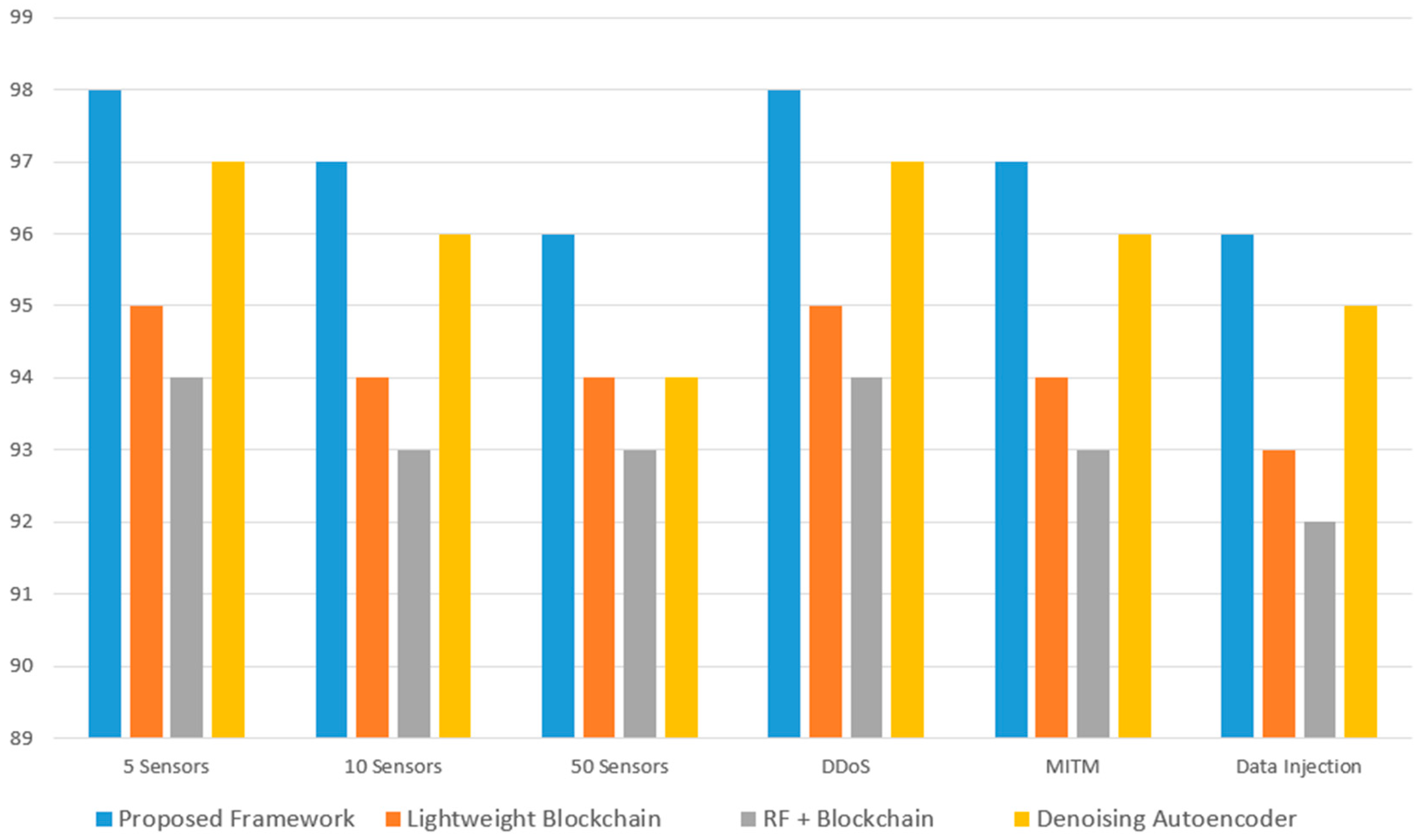
| Method | Accuracy | F1 Score | Score Detection Time (ms) | Key Features |
|---|---|---|---|---|
| Proposed Framework | 98% | 98% | 16–19 | DL + Blockchain, layered architecture |
| Lightweight Blockchain [16] | 95% | 94% | 15–20 | K-means + Blockchain, lightweight |
| RF + Blockchain [17] | 94% | 93% | 20–25 | Random Forest + Blockchain |
| Denoising Autoencoder [18] | 97% | 97% | 20–25 | Deep learning, no blockchain |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almasabi, A.M.; Alkhodre, A.B.; Khemakhem, M.; Eassa, F.; Abi Sen, A.A.; Harbaoui, A. Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain. Information 2025, 16, 406. https://doi.org/10.3390/info16050406
Almasabi AM, Alkhodre AB, Khemakhem M, Eassa F, Abi Sen AA, Harbaoui A. Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain. Information. 2025; 16(5):406. https://doi.org/10.3390/info16050406
Chicago/Turabian StyleAlmasabi, Ahmad M., Ahmad B. Alkhodre, Maher Khemakhem, Fathy Eassa, Adnan Ahmed Abi Sen, and Ahmed Harbaoui. 2025. "Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain" Information 16, no. 5: 406. https://doi.org/10.3390/info16050406
APA StyleAlmasabi, A. M., Alkhodre, A. B., Khemakhem, M., Eassa, F., Abi Sen, A. A., & Harbaoui, A. (2025). Internet of Things-Based Anomaly Detection Hybrid Framework Simulation Integration of Deep Learning and Blockchain. Information, 16(5), 406. https://doi.org/10.3390/info16050406