CDAS: A Secure Cross-Domain Data Sharing Scheme Based on Blockchain
Abstract
1. Introduction
- We propose a blockchain-based secure cross-domain data sharing scheme (CDAS) that combines an ABAC and searchable encryption with blockchain to achieve secure and fine-grained access to data for users. While ensuring access control efficiency, it also solves the problems of single point of failure and data privacy protection in traditional data sharing schemes.
- Considering the transmission distance delay between the edge devices and the central organization as well as the limited device resources, we adopt a multi-layer blockchain architecture to assist industrial IoT devices in completing data sharing and other computing authentication operations through edge servers.
- This paper analyzes the security schemes for data privacy in cross-domain data sharing. In order to ensure data security, we transform the traditional cloud-based processing scheme into using IPFS for ciphertext storage, and use anonymous authentication and searchable encryption to achieve the transmission of private data.
2. Related Work
3. Preliminaries
3.1. Blockchain
3.2. Bilinear Map
- Bilinearity: For any and , it holds that .
- Non-degeneracy: There exists at least one element such that .
- Efficiency: For any , can be computed efficiently.
3.3. Access Control Model
3.4. Interplanetary File System
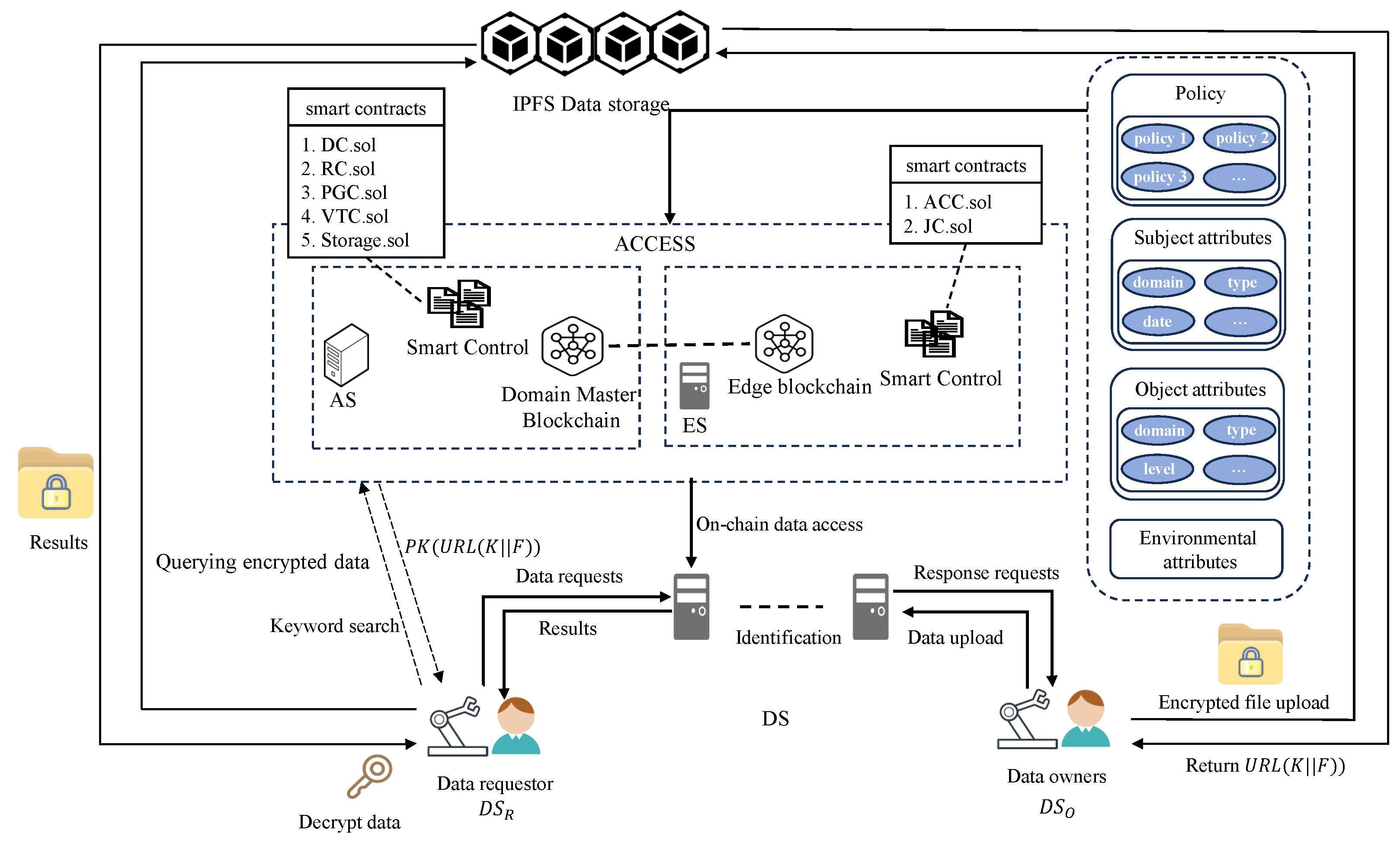
4. Cross-Domain Multi-Layer Blockchain Model
4.1. System Model
- DS (Internet of Things Devices): This represents resource-constrained industrial IoT devices with limited computing power and storage resources.
- ES (Edge Servers): This refers to servers close to edge devices with certain computing and storage capabilities. Each factory may be distributed in different regions and may consist of multiple ES, but the number of ES needs to meet Byzantine or other constraints. The ES of each domain jointly form the edge blockchain layer, which is responsible for assisting DS devices in completing operations such as data sharing.
- AS (Domain Master Device Servers): This consists of master devices in the domain, and each domain has a master device. It is used for cross-domain collaboration, cross-domain authentication, and access control operations. It also supports the management of devices within the domain, the generation of on-chain keys of devices, etc. Additionally, it provides decentralized sharing services and stores the public parameters of on-chain nodes.
4.2. Scheme Process
- User Registration: Users perform anonymous registration before joining the blockchain.
- Data Storage:
- Off-Chain Shared Information Storage: encrypts the original data with a symmetric key and stores it in IPFS, and generates an encrypted file index.
- On-Chain Data Storage: Devices and users upload key data to the blockchain.
- File Keyword Encryption: Devices can encrypt keywords of shareable file in advance and store them on the blockchain for subsequent retrieval of file information.
- Data Request: The data request process is divided into multiple parts.
- (a)
- initiates a cross-domain data request to the edge blockchain layer.
- (b)
- When of receives the request, if the request is authenticated, will synchronize the request with other edge devices on the blockchain.
- (c)
- After of receives the request, it will execute the on-chain access control contract to verify whether the attributes of the requester and the requested object meet the access control policy.
- (d)
- After passing the access control check, invokes the trapdoor generation algorithm to output the trapdoor, and uploads it to the edge blockchain layer.
- (e)
- of the edge blockchain layer invokes the search algorithm and compares in the trapdoor value with m in the keyword ciphertext. If the corresponding ciphertext file is retrieved, the result will be transmitted to the device in the domain. Subsequently, encrypts the encrypted file index and the symmetric key and uploads them to the blockchain, and synchronizes them to the edge blockchain layer.
- Data Decryption: receives the ciphertext information sent by the edge layer, decrypts the encrypted result with the private key to obtain the symmetric key and the link of the original file ciphertext. Then, it sends a link data request to IPFS, obtains the ciphertext of the original file, and decrypts it to obtain the original data file M.
4.3. Threat Model
- IND-CKA security: The IND-CPA security of our scheme uses the game between the adversary A and the challenger C as follows:
- Init: A selects the access structure and sends it to C.
- Setup: C calculates the system parameters and sends them to A.
- Query phase 1: A sends a query to the oracle, and C responds as follows:
- (a)
- Key generation: C executes the key generation algorithm to generate the user’s key and sends it to A.
- (b)
- Threshold phase: A selects any keyword , C executes the algorithm to generate the trapdoor and sends it to A.
- Challenge: A submits two keywords and of equal length, and C randomly selects a bit to calculate the ciphertext and sends it to A.
- Query phase 2: It is similar to phase 1.
- Guess: A outputs the guess value , and wins the game if . The probability of A winning the game is .
- IND-CPA security: The IND-CPA security of our scheme uses the game between adversaries A and C.
- Init: C executes the setup algorithm and then sends to A.
- Query phase 1: A executes the key generation algorithm on the challenger, generates the user’s key, and sends it to A.
- Challenge: A sends two identical messages and to C. C randomly selects a bit , calculates the ciphertext and according to a specific rule, and sends to A.
- Query phase 2: A continues to request operations to C, but the request content cannot contain and .
- Guess: A guesses the bit previously selected by C. The advantage of A in this attack is measured according to the result of his guess, and then the security of the encryption scheme under the IND-CPA security model is evaluated. A outputs the guess value , and if , A will win. The probability of A winning the game is .
5. Specific Algorithm Analysis of the Scheme
5.1. System Initialization
- Select random numbers .
- Calculate , .
- , and .
5.2. Key Generation Algorithm
- Select a random number .
- Calculate the identity-based hash value: .
- Calculate , , and . Generate the identity-based public-private key pair for ES and DS. Generate the user’s private key for later decryption, and the user’s public key
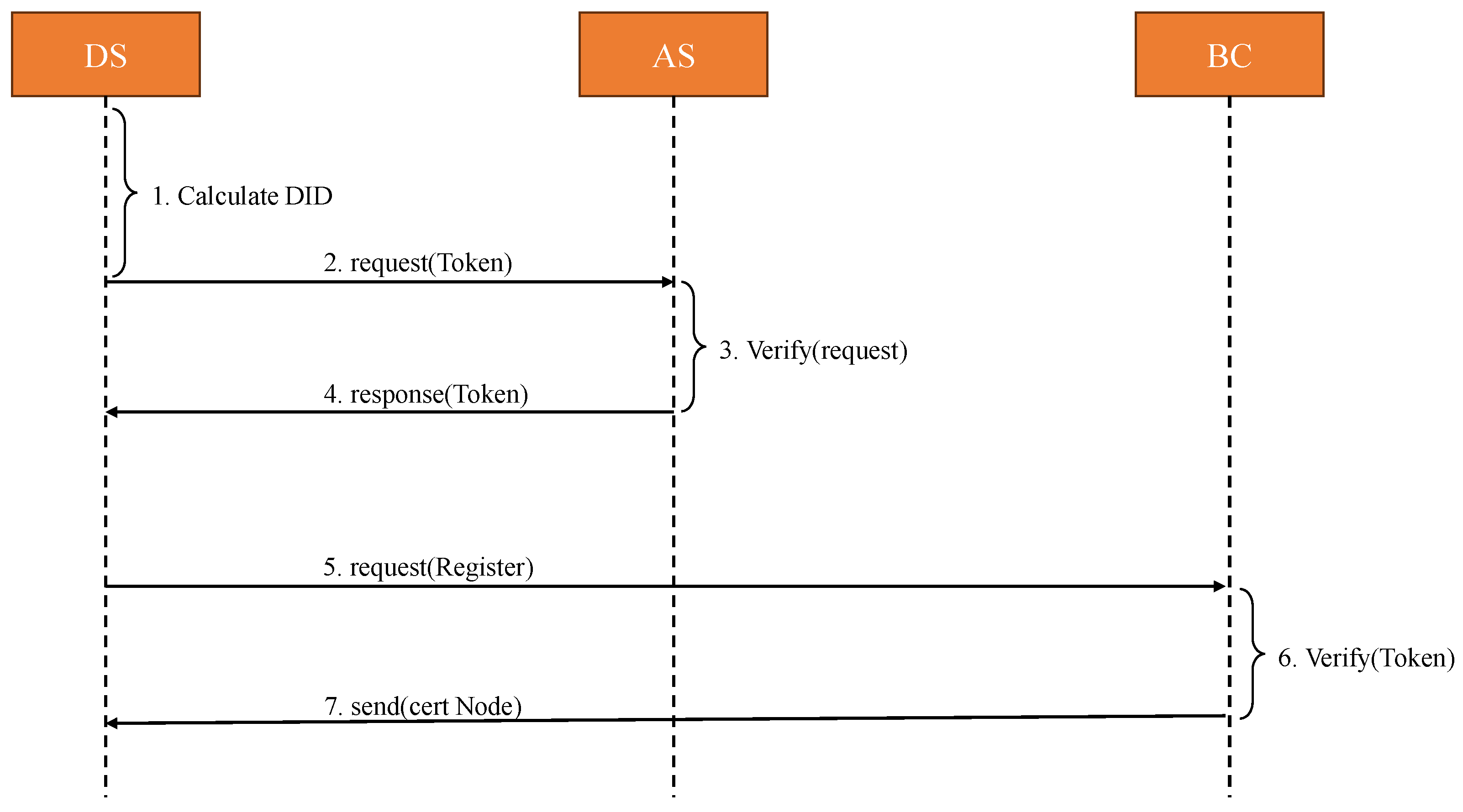
5.3. User Registration
- DS selects a secure random number and combines it with its own real identity UID to generate its anonymous identity.
- Application for identity certificate DS initiates an identity certificate request and uses the private key of DS to sign the anonymous identity message of DS.
- AS verifies the identity of the DS and signs the message.
- AS issues in-domain identity credentials, while AS signs the identity using the private key on the blockchain.
- DS initiates a registration request to the blockchain network.
- The blockchain (BC) uses the corresponding AS’s on-chain public key from the respective domain to verify its identity credentials.
- The aforementioned steps lead to the successful registration of DS, and BC returns the node certificate.
5.4. Data Storage
- Off-chain Shared Data Storage: encrypts the original data with a symmetric key and stores it in IPFS, then returns the link . The data owner encrypts the data of the industrial IoT device. Specifically, it uses the AES-based symmetric key K to encrypt the original file . Then it uploads the encrypted file to IPFS and obtains the IPFS file link . The data owner saves and the symmetric key K of the encrypted file to the domain master device (AS) within the domain through in-domain transmission for subsequent data sharing.
- On-Chain Data StorageDevices and users upload key data to the blockchain. The master device uploads the data of all nodes to the blockchain according to requirements and synchronizes with other consensus nodes to complete the data storage of the blockchain.: The master device (AS) of each domain combines the key data of all devices within the domain, device attributes, device resource attributes, resource access policies, and other information with the address, and then invokes the corresponding smart contract to upload them to the blockchain. The nodes of the on-chain device can obtain the public key data of other on-chain devices through the address of the target device. The key data of the device includes the following:It includes the user’s anonymous identity and affiliated domain , the device’s public key , the device type , the timestamp , the encrypted file link, etc.
5.5. Data Keyword Encryption
- Randomly select .
- Calculate: , , .
- Calculate: , , .
- .
5.6. Data Request
5.6.1. Access Control
- DC: It can manage and query the attributes of device entities (DS), and store multiple DS attributes: , where each address can store only one set of DS attributes: . As shown in Table 1, DC can perform operations such as adding, modifying, and querying attributes.
- RC: It can manage and query the attributes of resource entities (RS), and store multiple RS attributes: , where each device address can store only one set of RS attributes: . As shown in Table 2, it can perform operations such as adding, modifying, and querying attributes.
- PGC: As shown in Table 3, it mainly implements the management function of access control policy, including adding and modifying policies, etc. The data applicant must verify that its access request complies with the policy by invoking this contract. An access request will be approved only if the attributes of the requester and the resource being accessed meet all the management policy criteria.For example, assume that a resource has the following attributes: , and the access policy of is , , . Among them, means that the resource type is assembly process, means that the resource level is confidential, and means that the applicable equipment is machine operation. If a device has the attributes , then it can access .
- JC: As shown in Table 4, it mainly determines whether the current data accessor meets the normal access status and detects whether its attributes are in the temporary blacklist. If a node is monitored, any malicious behaviors it performs will be added to the temporary blacklist. When ACC determines that the current data request is malicious, the JC will be triggered. At the same time, JC records the current access record to audit the access behavior on the chain. When the number of malicious behaviors monitored on the current node exceeds a certain number, it will be added to the permanent blacklist, and access control will not be possible.
- ACC: It controls the access between the current account and the access object, and only allows accounts that meet all conditions to pass. It compares the received access control attributes with the attributes specified in the access control policy and returns the corresponding access result.
- (a)
- RequestListen function: When monitoring for malicious behavior, the AddBlocked() in the JC will be triggered to freeze the account’s transactions until the end of the penalty period. In addition, if the account has committed more than 10 illegal behaviors, the AddBlackList() will be called to add it to the permanent blacklist.
- (b)
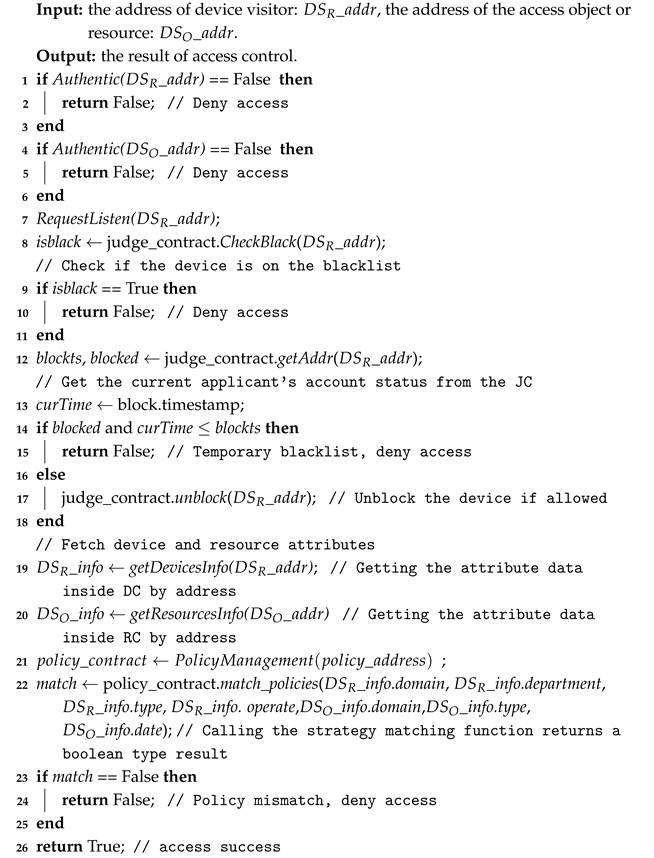
- Access function: As shown in Algorithm 1, the visitor and requester are first authenticated by calling Authentic() to verify the account addresses of the visitor and data provider and query whether they exist in the blockchain system. Then, the checkBlackList() in the JC is called to determine if the account is blacklisted. Additionally, the checkBlocked() is called to verify that the account is currently on the temporary blacklist and whether the transaction has been released. If the transaction has been released, the subsequent operations continue. Finally, the DC, RC, and PC contracts are invoked to match the attributes of visitors with the policy of the access object.
| Algorithm 1: Access Function |
 |
5.6.2. Trapdoor Generation
- Randomly select .
- Calculate: .
- Calculate: , , , and .
5.6.3. Encrypted File Retrieval
- Calculate:
- Calculate:If the keyword input by the user is equal to the encrypted keyword, i.e., and , then the edge blockchain layer returns the link for the encrypted file ; otherwise, it returns ⊥.
- : The AS located in the data owner encrypts both the and the symmetric key K of the encrypted file. Subsequently, it uploads these encrypted elements to the edge blockchain, where .
- (a)
- Select a random .
- (b)
- Calculate .
- (c)
- Calculate .
- (d)
- Calculate , .
5.6.4. Decryption and Authentication of Integrity
- Calculate:
- Calculate:
- Calculate:
6. Security Analysis
6.1. Security Based on Adversarial Model
- Init: A selects the access strategy and challenges C.
- Setup: C first selects two cyclic multiplication groups and with the prime number q as order, then randomly selects and calculates , , , to obtain public global parameters , and finally sends them to A.
- Query phase 1: A submits a query to the oracle, and C responds as follows:
- (a)
- Key generation phase: C first selects a random number , then calculates the identity-based hash value: to generate an identity-based public and private key pair , C sends to A.
- (b)
- Trapdoor generation phase: A inputs any keyword, then C executes the algorithm to generate a trapdoor , selects a random number to calculate , then sends to A.
- Challenge phase: A first submits two keywords of equal length and , then C will randomly select a bit and calculate the following ciphertext , which consists of , , , and (random ), and then send to A.
- Query phase 2: A submits the keyword datasets to C for encrypted query, and the submitted datasets cannot be and .
- Guess: If , A will win the game, and the probability is as follows. In keyword encryption, for , assuming that , , , where and are randomly selected from . It is computationally infeasible to distinguish from Z in polynomial time. At the same time, for , assuming that the advantage of A in winning the game is , if C outputs a valid ciphertext from , the advantage of A in winning the game is . However, if c is a random number, not a valid ciphertext, the advantage of winning the game is , A will not have an advantage in attacking the CKA game. The advantage of A in breaking the DBDH problem is calculated as follows:
- Init: A chooses a challenge for C.
- Setup: C selects two cyclic multiplication groups and with the prime number q as order and random , then calculates , , , to obtain public global parameters , finally sends them to A.
- Query phase 1: A requests a key, and C selects a random number and calculates the identity-based values: to generate an identity-based public–private key pair , C sends to A.
- Challenge phase: Taking decryption K as an example, A sends two identical messages , to challenger then C selects a bit , calculates , , and C sends to A.
- Query phase 2: It is similar to the phase 1, but it does not include and .
- Guess: A guesses the value of , where the advantage to solve DBDH is .
6.2. Security Analysis of the System
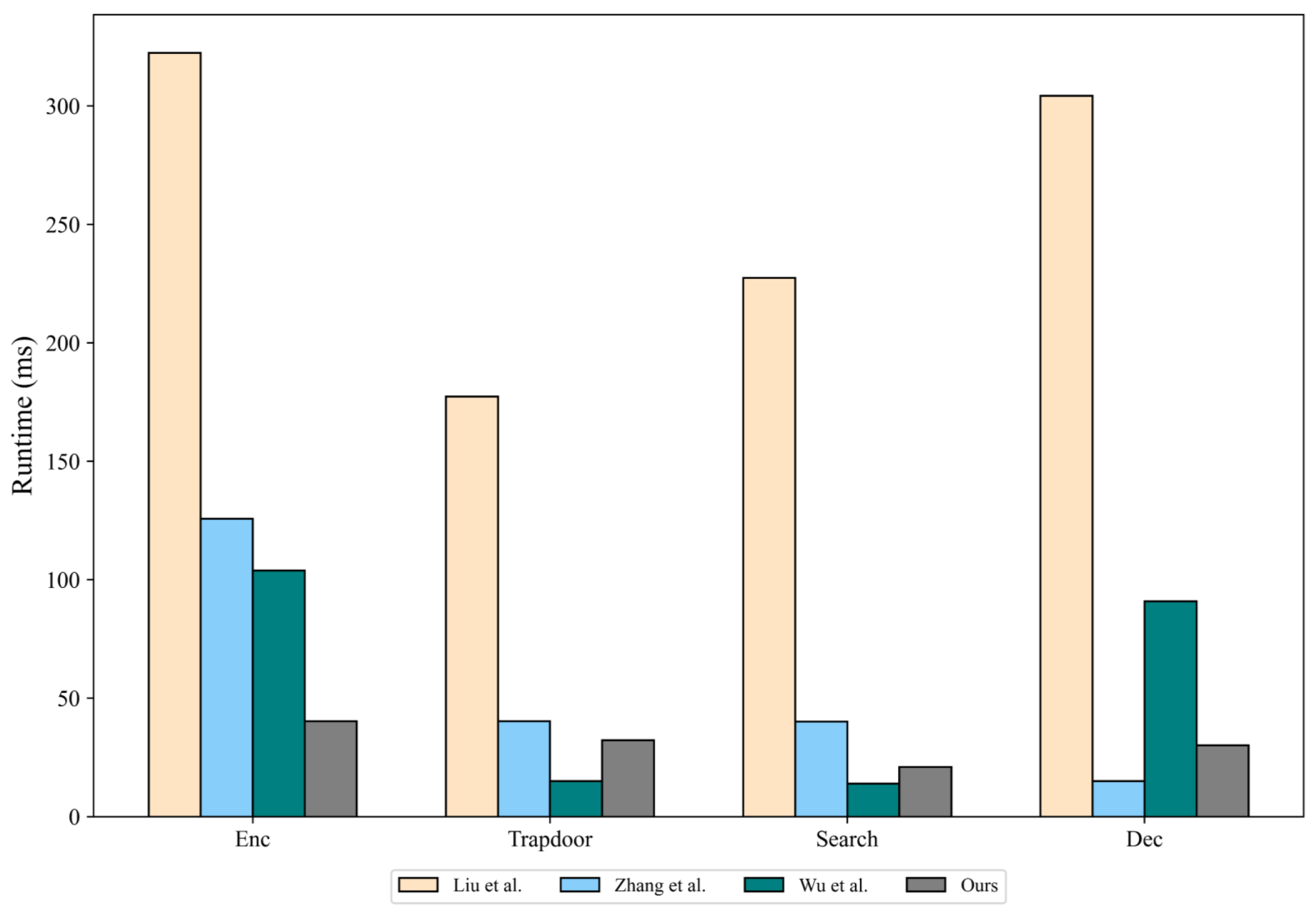
7. Experiment
7.1. Time Cost Analysis
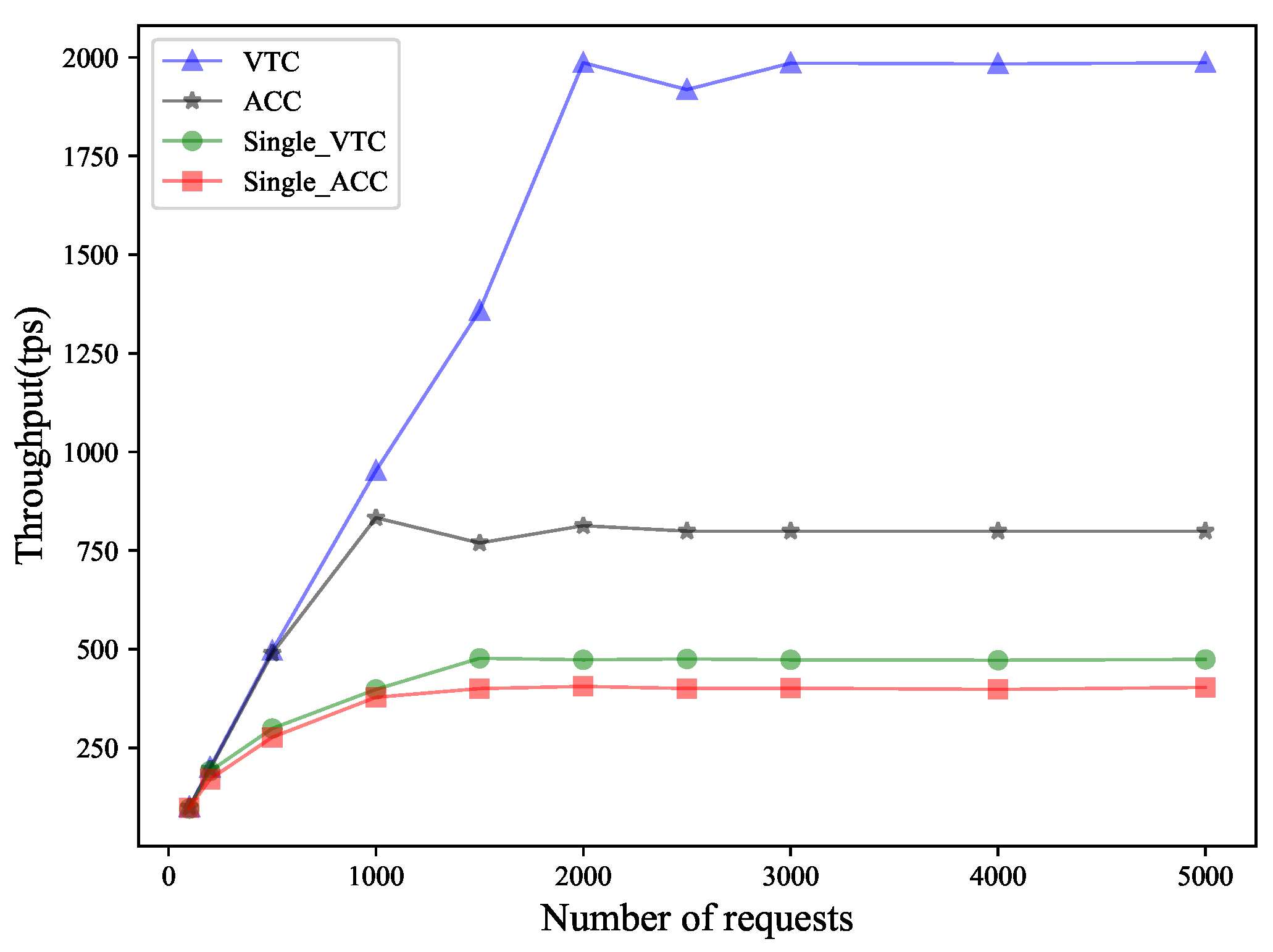
7.2. Transactions Throughput Analysis
7.3. Gas Cost Analysis
7.4. Cryptographic Algorithms Analysis
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yang, L.; Zou, W.; Wang, J.; Tang, Z. EdgeShare: A blockchain-based edge data-sharing framework for Industrial Internet of Things. Neurocomputing 2022, 485, 219–232. [Google Scholar] [CrossRef]
- Tsai, C.W.; Lai, C.F.; Vasilakos, A.V. Future internet of things: Open issues and challenges. Wirel. Netw. 2014, 20, 2201–2217. [Google Scholar] [CrossRef]
- Duan, M.; Ouyang, A.; Tan, G.; Tian, Q. Age estimation using aging/rejuvenation features with device-edge synergy. IEEE Trans. Circuits Syst. Video Technol. 2020, 31, 608–620. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-assisted secure device authentication for cross-domain industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Ma, Z.; Liu, L.; Meng, W. Towards multiple-mix-attack detection via consensus-based trust management in IoT networks. Comput. Secur. 2020, 96, 101898. [Google Scholar] [CrossRef]
- Chi, J.; Li, Y.; Huang, J.; Liu, J.; Jin, Y.; Chen, C.; Qiu, T. A secure and efficient data sharing scheme based on blockchain in industrial Internet of Things. J. Netw. Comput. Appl. 2020, 167, 102710. [Google Scholar] [CrossRef]
- Chen, N.; Qiu, T.; Zhou, X.; Li, K.; Atiquzzaman, M. An intelligent robust networking mechanism for the Internet of Things. IEEE Commun. Mag. 2019, 57, 91–95. [Google Scholar] [CrossRef]
- Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. Security and privacy challenges in mobile cloud computing: Survey and way ahead. J. Netw. Comput. Appl. 2017, 84, 38–54. [Google Scholar] [CrossRef]
- Pal, S.; Dorri, A.; Jurdak, R. Blockchain for IoT access control: Recent trends and future research directions. J. Netw. Comput. Appl. 2022, 203, 103371. [Google Scholar] [CrossRef]
- Bouras, M.A.; Lu, Q.; Dhelim, S.; Ning, H. A lightweight blockchain-based IoT identity management approach. Future Internet 2021, 13, 24. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Searchable encryption for healthcare clouds: A survey. IEEE Trans. Serv. Comput. 2017, 11, 978–996. [Google Scholar] [CrossRef]
- Sun, W.; Yu, S.; Lou, W.; Hou, Y.T.; Li, H. Protecting your right: Attribute-based keyword search with fine-grained owner-enforced search authorization in the cloud. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 226–234. [Google Scholar]
- Yu, J.; Liu, S.; Xu, M.; Guo, H.; Zhong, F.; Cheng, W. An efficient revocable and searchable MA-ABE scheme with blockchain assistance for C-IoT. IEEE Internet Things J. 2022, 10, 2754–2766. [Google Scholar] [CrossRef]
- Zhang, K.; Jiang, Z.; Ning, J.; Huang, X. Subversion-resistant and consistent attribute-based keyword search for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1771–1784. [Google Scholar] [CrossRef]
- Dabbagh, M.; Choo, K.K.R.; Beheshti, A.; Tahir, M.; Safa, N.S. A survey of empirical performance evaluation of permissioned blockchain platforms: Challenges and opportunities. Comput. Secur. 2021, 100, 102078. [Google Scholar] [CrossRef]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-based IoT access control system: Towards security, lightweight, and cross-domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]
- Huo, R.; Zeng, S.; Wang, Z.; Shang, J.; Chen, W.; Huang, T.; Wang, S.; Yu, F.R.; Liu, Y. A comprehensive survey on blockchain in industrial internet of things: Motivations, research progresses, and future challenges. IEEE Commun. Surv. Tutorials 2022, 24, 88–122. [Google Scholar] [CrossRef]
- Yu, X.; Xie, Y.; Xu, Q.; Xu, Z.; Xiong, R. Secure Data Sharing for Cross-domain Industrial IoT Based on Consortium Blockchain. In Proceedings of the 2023 26th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Rio de Janeiro, Brazil, 24–26 May 2023; pp. 1508–1513. [Google Scholar]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Singh, P.; Masud, M.; Hossain, M.S.; Kaur, A. Cross-domain secure data sharing using blockchain for industrial IoT. J. Parallel Distrib. Comput. 2021, 156, 176–184. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S. Smart contract and ipfs-based trustworthy secure data storage and device authentication scheme in fog computing environment. Peer-to-Peer Netw. Appl. 2023, 16, 1–21. [Google Scholar] [CrossRef]
- Zeng, S.; Cao, B.; Sun, Y.; Sun, C.; Wan, Z.; Peng, M. Blockchain-Assisted Cross-Domain Data Sharing in Industrial IoT. IEEE Internet Things J. 2023, 11, 26778–26792. [Google Scholar] [CrossRef]
- Kamboj, P.; Khare, S.; Pal, S. User authentication using Blockchain based smart contract in role-based access control. Peer-to-Peer Netw. Appl. 2021, 14, 2961–2976. [Google Scholar] [CrossRef]
- Han, D.; Zhu, Y.; Li, D.; Liang, W.; Souri, A.; Li, K.C. A blockchain-based auditable access control system for private data in service-centric IoT environments. IEEE Trans. Ind. Inform. 2021, 18, 3530–3540. [Google Scholar] [CrossRef]
- Wu, A.; Zheng, D.; Zhang, Y.; Yang, M. Hidden policy attribute-based data sharing with direct revocation and keyword search in cloud computing. Sensors 2018, 18, 2158. [Google Scholar] [CrossRef] [PubMed]
- Liu, S.; Yu, J.; Xiao, Y.; Wan, Z.; Wang, S.; Yan, B. BC-SABE: Blockchain-aided searchable attribute-based encryption for cloud-IoT. IEEE Internet Things J. 2020, 7, 7851–7867. [Google Scholar] [CrossRef]
- Zhang, K.; Zhang, Y.; Li, Y.; Liu, X.; Lu, L. A blockchain-based anonymous attribute-based searchable encryption scheme for data sharing. IEEE Internet Things J. 2023, 11, 1685–1697. [Google Scholar] [CrossRef]
- Guo, F.; Shen, G.; Huang, Z.; Yang, Y.; Cai, M.; Wei, L. DABAC: Smart contract-based spatio-temporal domain access control for the Internet of Things. IEEE Access 2023, 11, 36452–36463. [Google Scholar] [CrossRef]
- Guo, H.; Yu, X. A survey on blockchain technology and its security. Blockchain Res. Appl. 2022, 3, 100067. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Khan, S.; Suman, R. Blockchain technology applications for Industry 4.0: A literature-based review. Blockchain Res. Appl. 2021, 2, 100027. [Google Scholar] [CrossRef]
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E.; Bani-Hani, A. Blockchain smart contracts: Applications, challenges, and future trends. Peer-to-Peer Netw. Appl. 2021, 14, 2901–2925. [Google Scholar] [CrossRef]
- Zhang, F.; Safavi-Naini, R.; Susilo, W. An efficient signature scheme from bilinear pairings and its applications. In Proceedings of the Public Key Cryptography–PKC 2004: 7th International Workshop on Theory and Practice in Public Key Cryptography, Singapore, 1–4 March 2004; pp. 277–290. [Google Scholar]
- Zhu, Y.; Yu, R.; Ma, D.; Chu, W.C.C. Cryptographic attribute-based access control (ABAC) for secure decision making of dynamic policy with multiauthority attribute tokens. IEEE Trans. Reliab. 2019, 68, 1330–1346. [Google Scholar] [CrossRef]
- Li, J.; Han, D.; Wu, Z.; Wang, J.; Li, K.C.; Castiglione, A. A novel system for medical equipment supply chain traceability based on alliance chain and attribute and role access control. Future Gener. Comput. Syst. 2023, 142, 195–211. [Google Scholar] [CrossRef]
- Jayabalan, J.; Jeyanthi, N. Scalable blockchain model using off-chain IPFS storage for healthcare data security and privacy. J. Parallel Distrib. Comput. 2022, 164, 152–167. [Google Scholar] [CrossRef]
- Kang, P.; Yang, W.; Zheng, J. Blockchain private file storage-sharing method based on IPFS. Sensors 2022, 22, 5100. [Google Scholar] [CrossRef] [PubMed]
- Han, R.; Wang, Y.; Wan, M.; Yuan, T.; Sun, G. FIBPRO: Peer-to-peer data management and sharing cloud storage system based on blockchain. Peer-to-Peer Netw. Appl. 2023, 16, 2850–2864. [Google Scholar] [CrossRef]
| Contract | Interface | Function |
|---|---|---|
| DC.sol | Authorities_only() | Only the permission owner can invoke the functions |
| DSAdd() | AS Adds the attributes of the device in the domain | |
| DSDelete() | Delete the attributes of the device | |
| DSUpdate() | Update the attributes of the device | |
| CheckDS() | Check the device’s attributes in the BC |
| Contract | Interface | Function |
|---|---|---|
| RC.sol | Authorities_only() | Only the permission owner can invoke the functions |
| RSAdd() | AS adds the attributes of the resource in the domain | |
| RSDelete() | Delete the attributes of the resource | |
| RSUpdate() | Update the attributes of the resource | |
| CheckRS() | Check the resource’s attributes in the BC |
| Contract | Interface | Function |
|---|---|---|
| PG.sol | AddPolicy() | Add policy |
| DeletePolicy() | Deletion policy | |
| Match() | Policy matching |
| Contract | Interface | Function |
|---|---|---|
| JC.sol | AddBlackList() | Add to the permanent blacklist |
| CheckBlackList() | Check if the user is in the blacklist | |
| AddBlocked() | Add to the temporary blacklist | |
| CheckBlocked() | Check if the user is blocked |
| Function | Time Consuming |
|---|---|
| Access | 1476 ms |
| match | 709 ms |
| RequestListen | 285 ms |
| VerifyToken | 833 ms |
| Check_Black | 63 ms |
| Check_Data | 108 ms |
| Time Period | ACC Times | VT Times |
|---|---|---|
| 100 ms–200 ms | 4 | 0 |
| 200 ms–400 ms | 83 | 45 |
| 400 ms–1000 ms | 375 | 702 |
| 1000 ms–2000 ms | 295 | 253 |
| >2000 ms | 243 | 0 |
| Function | Gas Cost |
|---|---|
| Access | 126,870 gwei |
| AddPolicy | 96,722 gwei |
| VerifyToken | 13,717 gwei |
| match | 66,192 gwei |
| StorageData | 52,707 gwei |
| setBlackList | 4954 gwei |
| Operater | E | P | H |
|---|---|---|---|
| Time (ms) | 8.06 | 6.99 | 0.021 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, J.; Pei, T.; Chen, J.; Hou, Z. CDAS: A Secure Cross-Domain Data Sharing Scheme Based on Blockchain. Information 2025, 16, 394. https://doi.org/10.3390/info16050394
Jiang J, Pei T, Chen J, Hou Z. CDAS: A Secure Cross-Domain Data Sharing Scheme Based on Blockchain. Information. 2025; 16(5):394. https://doi.org/10.3390/info16050394
Chicago/Turabian StyleJiang, Jiahui, Tingrui Pei, Jiahao Chen, and Zhiwen Hou. 2025. "CDAS: A Secure Cross-Domain Data Sharing Scheme Based on Blockchain" Information 16, no. 5: 394. https://doi.org/10.3390/info16050394
APA StyleJiang, J., Pei, T., Chen, J., & Hou, Z. (2025). CDAS: A Secure Cross-Domain Data Sharing Scheme Based on Blockchain. Information, 16(5), 394. https://doi.org/10.3390/info16050394