Enabling Collaborative Forensic by Design for the Internet of Vehicles
Abstract
1. Introduction
2. Related Work
3. Barriers to the Integration of Digital Forensics in the IoV
3.1. Data Variation
- Lack of Standardisation: One of the foremost challenges is the absence of standardised data formats and communication protocols across different manufacturers and service providers. Each entity may use proprietary systems optimised for specific functionalities, leading to a fragmented data landscape. This heterogeneity complicates the process of modelling data in a forensically sound manner, as investigators must understand and interpret multiple data formats and protocols.
- Data Volume and Relevance: The sheer volume of data produced is overwhelming. For instance, a single autonomous vehicle can generate very large data volumes, potentially up to hundreds of GBs or even into the lower TB range under extreme conditions. Collecting and storing all these data for forensic purposes is impractical due to storage limitations and processing constraints. Therefore, it is crucial to develop methods for identifying and extracting relevant data efficiently. Techniques such as data filtering, event-triggered recording, and the use of metadata can help focus on critical information pertinent to forensic investigations.
- Forensic Data Modelling: To handle heterogeneous data effectively, there is a need for robust data models [19] that can accommodate different data types while maintaining forensic integrity. Ontologies and standardised schemas can aid in mapping disparate data sources into a cohesive structure, facilitating analysis and correlation across different systems.
3.2. Solution Highlights with CFPEA
- ○
- Distributed Edge Service Discovery (ESD): CFPEA’s ESD module maintains metadata about each roadside unit’s data offerings. Investigators use ESD to locate data sources pertinent to a crime scene, such as dashcam footage or sensor logs, thus avoiding the need to query every node.
- ○
- standardised Data Formats: By promoting open, non-proprietary artefact storage within vehicles, CFPEA simplifies data parsing across different systems. This enables the seamless correlation of digital evidence.
- ○
- Selective Data Retrieval: Instead of collecting every possible data log (which can be extremely large and introduce privacy concerns), CFPEA identifies just the relevant segments (e.g., timestamped or event-triggered data), streamlining forensic analysis.
3.3. Chain of Custody
- Dynamic Network Topology: Vehicles are constantly moving, joining, and leaving networks. This mobility leads to frequent changes in network connections and data pathways. Establishing a consistent chain of custody requires tracking evidence as it moves through this fluid environment, which is inherently difficult.
- Non-Uniform Node Distribution: The varying density of nodes (vehicles and sensors) across different geographical areas affects network stability and data availability. In sparsely populated areas, connectivity may be limited, hindering the timely collection and transmission of evidence. Conversely, in dense urban areas, the sheer number of nodes can lead to network congestion and data collisions.
- Limited Metadata Storage: Many IoV nodes, particularly sensors and lightweight devices, have limited storage and processing capabilities. They may not record essential metadata such as timestamps, geolocation, device identifiers, or logs of data access and modifications. Without this metadata, it becomes challenging to verify the authenticity and integrity of evidence as there is insufficient context to establish its origin and any alterations.
- Evidence Preservation: Ensuring that data remain unaltered from the point of collection to their presentation in court is vital. In the IoV, data may traverse multiple networks and devices, each introducing potential vulnerabilities. Secure transmission protocols, encryption, and the use of tamper-evident technologies are necessary to safeguard the evidence throughout its lifecycle.
3.4. Solution Highlights with CFPEA
- ○
- Hybrid P2P Architecture: CFPEA accommodates dynamic IoV connectivity. If a vehicle or roadside unit leaves one network sector, the relevant data (or a subset) are replicated or forwarded to a stable repository, preventing data loss.
- ○
- Vehicle Execution Container (VEC): The VEC coordinates investigative queries to roadside units. If the network topology changes, the VEC reroutes subqueries to active RSUs, ensuring that the forensic process remains continuous.
- ○
- Artefact Preservation Module: CFPEA enforces secure data storage protocols that timestamp and cryptographically seal each artefact upon acquisition. This module also tracks every access or transfer request, forming an audit trail vital for legal proceedings.
- ○
- Tamper-Evident Logs: Every operation—such as viewing, copying, or moving evidence—triggers the creation of a tamper-evident record. This method (using cryptographic signatures) provides a robust mechanism to detect any unauthorised changes.
- ○
- Role-Based Access Control (RBAC): CFPEA assigns fine-grained permissions to investigators, law enforcement, and other stakeholders to prevent unauthorised manipulation. Investigators only see the artefacts relevant to their current inquiry, aligning with privacy and need-to-know principles.
3.5. Evidence Meeting Forensic Standards
- Manufacturer Restrictions: Vehicle manufacturers often limit access to in-vehicle data due to concerns over intellectual property [21] and maintaining a competitive advantage. The proprietary nature of vehicle systems means that accessing and interpreting data may require manufacturer-specific tools or permissions, which may not be readily available to investigators. These restrictions can delay investigations or lead to incomplete evidence collection.
- Legal and Jurisdictional Variations: Vehicles are produced and operated globally, crossing multiple jurisdictions with differing laws regarding data access, privacy, and evidence handling. For instance, what is permissible under US law may be restricted under European Union regulations. This diversity complicates efforts to standardise forensic procedures and can result in legal challenges if evidence is collected without proper authorization in a particular jurisdiction.
- Technical Challenges: The complexity of modern vehicle systems, which may include multiple embedded systems, sensors, and software components, makes forensic analysis technically demanding. Investigators need specialised knowledge and tools to extract and interpret data accurately. Moreover, firmware and software updates can alter system behaviour, adding another layer of complexity to forensic examinations.
- Standardisation Efforts: To overcome these challenges, there is a need for collaborative efforts among manufacturers, regulatory bodies, and industry groups to develop standardised interfaces and protocols for data access. Establishing clear guidelines and legal frameworks can facilitate lawful and efficient evidence collection while respecting manufacturers’ proprietary interests.
3.6. Solution Highlights with CFPEA
- ○
- Collaborative Forensic-by-Design Mechanism: CFPEA incorporates forensic principles (based on ISO/IEC 27043) into every stage of data handling, from the moment data are generated in a vehicle to their storage and eventual analysis.
- ○
- Non-Proprietary Formats: By storing artefacts in open, standardised formats, CFPEA facilitates the external verification and replication of analyses, strengthening legal credibility.
- ○
- Automated Metadata Management: CFPEA automatically collects metadata (e.g., timestamps and geolocation) for every artefact, providing investigators with vital context that helps verify authenticity.
3.7. Privacy
- Location Data: Real-time and historical global positioning system (GPS) data can reveal an individual’s movements and routines.
- Biometric Data: In-vehicle sensors may collect data on driver behaviour, fatigue levels, or even health indicators.
- Communication Records: Infotainment systems can store call logs, messages, and app data.
- Usage Patterns: Data on driving habits, speed, braking patterns, and vehicle usage times.
3.8. Solution Highlights with CFPEA
- ○
- Selective Disclosure and User Consent: CFPEA drivers can opt in or out of sharing specific artefacts, helping align evidence collection with privacy preferences and legal requirements.
- ○
- Secure Key Management: Encryption keys used for data at rest and in transit are safeguarded via strong cryptographic mechanisms, ensuring that only authorised parties can decrypt sensitive information.
- ○
- Relevance Management Centre (RMC): By assigning a relevance score to roadside units that accurately provide evidence while respecting data protection measures, CFPEA encourages compliance with privacy laws.
4. CFPEA’s Role in Overcoming Challenges in IoV Investigations
- Consolidating Data: integrating information from multiple vehicular networks and infrastructure nodes;
- Supporting Distributed Forensic Analysis: enabling investigators from different jurisdictions to collaborate and share relevant evidence securely;
- Establishing Jurisdictional Cooperation: streamlining cross-border investigations by providing common forensic protocols and data formats, thereby reducing legal and technical complexities.
- Automated Logging: recording who collected the evidence, when, and where it was collected while preserving metadata such as timestamps, geolocation, and system identifiers;
- Secure Transfer and Storage: employing encryption and secure storage solutions to maintain the confidentiality and integrity of digital artefacts;
- Immutable Records: utilising secure methods [23] to record all steps taken in evidence collection and analysis immutably, ensuring an unalterable chain of custody.
5. Collaborative Forensic-by-Design (CFbD) Approach in CFPEA
- (1)
- Identify Potential Evidence Sources
- Smart Vehicle Applications and System Logs: Modern vehicles run software that logs driver actions, vehicle performance, location data, and infotainment usage. These logs can serve as pivotal evidence if an incident occurs, offering insights into whether anomalies or malicious commands took place within the vehicle’s control systems.
- Physical System Sensors: Sensors—such as LiDAR, radar, and on-board cameras—provide continuous data on vehicle surroundings. These may include speed, lane positioning, and proximity to other vehicles. Identifying which sensors and logs are relevant is a key step, as it enables investigators to capture evidence of collisions, hacking attempts, or other road crimes.
- (2)
- Plan Pre-Incident Collection
- Definition of Collection Strategies: Before any incident occurs, it is crucial to formulate robust strategies for collecting raw data that might become evidence. This includes determining what types of data will be captured (e.g., video footage, telemetry logs, user access records) and clarifying the frequency and conditions under which data should be retained (e.g., continuous logging versus event-triggered snapshots).
- Automated Metadata Submission: Subsystems within vehicles or roadside infrastructure can be configured to automatically submit event metadata—such as geolocation, date/time, or media quality—to secure roadside unit databases. This proactive approach not only speeds up investigations but also reduces data loss by capturing essential contextual details immediately.
- (3)
- Define Storage and Evidence Handling
- Distributed and Secure Forensic Databases: Evidence drawn from different vehicular networks—ranging from multiple manufacturers to varied infrastructures—demands a distributed storage solution. Distributed databases reside at roadside units, configured with encryption and access controls, ensuring that collected artefacts remain intact, tamper proof, and easily retrievable.
- Chain-of-Custody Protocols: ISO/IEC 27043:2015 mandates the rigorous documentation of how evidence is gathered, transferred, and stored. By defining formal procedures and using cryptographic signatures or immutable records, the CFPEA framework upholds strict chain-of-custody requirements. This safeguards the reliability of evidence in legal or regulatory contexts.
- (4)
- Plan Pre-Incident Analysis
- Strategic Use of Analysis Tools: Before any confirmed incident arises, the CFPEA framework specifies how data analytics will be deployed to detect potential road crimes. This may involve automated licence plate recognition, log monitoring, facial detection, or correlation with known risk factors (e.g., high-accident zones).
- Broader Contextual Insight: Advanced techniques can match a vehicle’s sensor output with other environmental data—such as weather conditions, traffic density, or proximity to sensitive facilities—to spot anomalies that might presage malicious behaviour.
- (5)
- Plan Incident Detection
- Digital Investigation Procedures: Incident detection is a proactive and reactive measure. Proactively, abnormal network patterns, suspicious user commands, or erratic sensor readings can trigger an alert. Reactively, once a suspicious event is flagged, digital investigation procedures specify how to confirm whether a malicious incident has actually taken place.
- Defining Forensic Responsibility Boundaries: In complex IoV ecosystems, multiple entities—from vehicle owners to cloud service providers—share responsibility for forensic tasks. Clearly defining the scope of each party’s forensic obligations (e.g., who collects evidence first, who preserves logs, who notifies law enforcement) prevents confusion and ensures swift action when incidents occur.
5.1. CFbD After Detecting an Anomaly or Road Crime
- (1)
- Identifying the Incident Perpetrator’s Characteristics
- Profiling the Crime: Through advanced data analytics, investigators can glean characteristics of the entity (human or vehicle) that triggered the incident. This may encompass typical methods of vehicle compromise, digital fingerprints (IP addresses, timestamps, geolocation, device attributes—must be correlated collectively), or physical geolocation data that link an attacker to specific patterns of behaviour.
- Crime Classification: By matching these attributes against known cybercrime profiles (e.g., known patterns of sensor tampering, distributed denial-of-service (DDoS) attacks on vehicular networks, or manipulated engine control parameters), investigators can correlate the present incident with previously recorded offences. This correlation is invaluable for quickly identifying and deploying the appropriate response activities—be it isolating compromised vehicles, issuing roadside alerts, or collaborating with law enforcement for arrests.
- (2)
- Integrating Collaborative Forensics in CFPEA Framework
- Collecting Necessary Forensic Information: The CFPEA’s collaborative forensic-by-design mechanism ensures the continuous monitoring and logging of relevant data sources. When an incident arises, these logs provide a robust knowledge base reflecting local or regional crime trends—vital for understanding how criminals operate in certain locations or communities.
- Building a Knowledge Base of Attacks and Road Crimes: Historical incidents, including the details of the attacker’s methods or the specific vulnerabilities exploited, are kept in a structured repository. By analysing trends in different geographical locations, security teams can refine the CFPEA’s detection algorithms, prioritise patching for repeated vulnerabilities, and plan targeted law enforcement operations if certain areas are prone to recurring IoV-related offences.
- Road Crime Attribution: Attributing a crime to a specific entity or group, and determining the methods used, guides the choice of the CFbD plans that should be executed. For instance, if an incident stems from a known malware targeting vehicle infotainment systems, investigators can rapidly deploy the relevant CFbD plan—collecting memory dumps, performing software integrity checks, and notifying the relevant manufacturer for software patches.
- Efficient and Cost-Effective Investigations: By having a pre-established framework and toolset for CFbD, the CFPEA helps avoid costly ad hoc data gathering. Investigations become both swifter and more precise, substantially reducing downtime for vehicles and roadside infrastructure. This is particularly important for large-scale IoV deployments where even minor disruptions can have large societal and economic impacts.
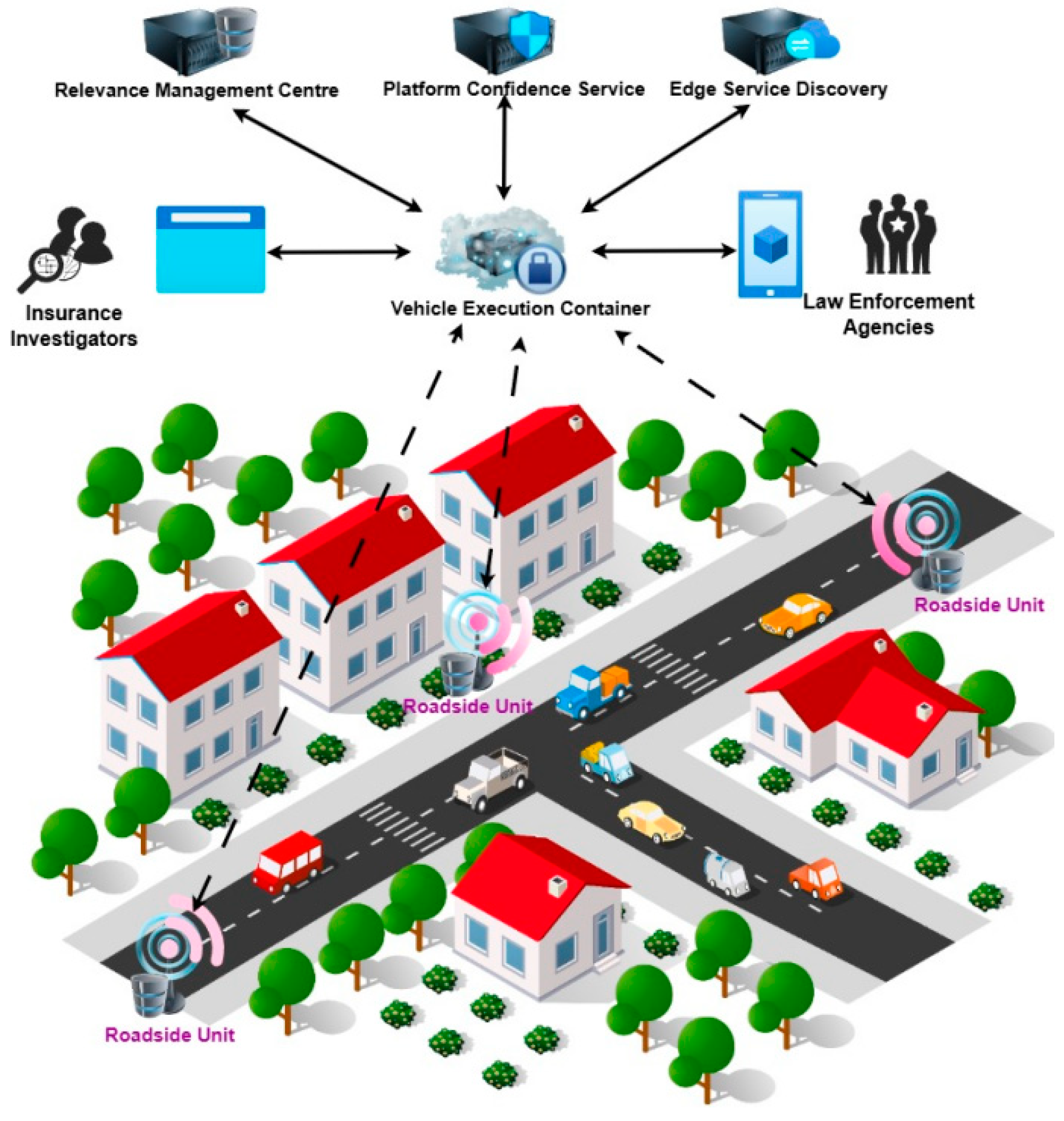
5.2. Extended Components of CFPEA Beyond Traditional Forensic Readiness Models
- Dynamic Trust Scoring: The PCS evaluates the reliability of each roadside unit (RSU) by examining various factors—such as historical data accuracy, frequency of successful evidence submissions, and feedback from investigators.
- Certificate Management: The PCS issues and revokes certificates for RSUs, using cryptographic mechanisms to ensure that only validated participants are authorised to share or access artefacts. This helps maintain a secure environment, minimising the risk of false data insertion or malicious activity.
- Integration with Incident Assignment: When a new incident is detected, the PCS provides real-time trust scores and certificate statuses to the CFPEA modules, allowing investigators to prioritise queries to RSUs that have demonstrated consistent accuracy and security.
- Relevance Score Tracking: The RMC calculates a “relevance” score for each RSU, reflecting the quality and timeliness of the evidence submitted. When investigators confirm that data from a particular RSU are accurate and valuable, that unit’s relevance score increases.
- Penalising Malicious or Inaccurate Providers: Conversely, if an RSU supplies tampered or incorrect information, or refuses to cooperate with valid investigative requests, its relevance score decreases. Over time, this “community rating” discourages misbehaviour by reducing the future earning or reward potential for untrustworthy nodes.
- Incentive-Based Approach: By offering tangible or reputational rewards (e.g., monetary compensation and insurance discounts), CFPEA motivates vehicle owners and RSUs to participate in forensic data sharing.
- Mobile Code Execution: CFPEA distributes an investigator-defined “mobile code” across RSUs to expedite local data collection and reduce network overhead. This contrasts with typical forensic models that gather all data in a central repository, often overloading communication channels and increasing latency.
- Bridging Multiple Stakeholder Nodes: A hybrid P2P setup allows for direct exchanges between RSUs when appropriate (P2P) while leveraging core infrastructure elements (e.g., the VEC and RMC) to maintain oversight and store critical metadata.
- Resilience to Topological Changes: If certain RSUs are temporarily offline or switch networks, the hybrid P2P design helps reroute queries, ensuring continuous forensic data flow—an issue often left unaddressed in centralised designs.
- Orchestrating Investigative Queries: The VEC receives high-level forensic instructions from investigators, decomposes them into subqueries, and dispatches those subqueries to appropriate RSUs.
- Adaptive Rerouting: If the network topology changes (e.g., vehicles move out of range), the VEC reroutes subqueries to active RSUs, thereby maintaining continuity in evidence collection. This contrasts with static solutions where node unavailability leads to data gaps.
- Sandboxed Execution: By running mobile code within a secure container, CFPEA ensures malicious scripts cannot tamper with broader system resources or data. This layer of isolation is not routinely provided in traditional frameworks.
- Metadata-Based Discovery: The ESD module records what data each RSU possesses (e.g., dashcam footage, GPS logs, sensor data), providing a global “map” of where specific artefacts can be found—without needing to query every node individually.
- Efficient Query Routing: When investigators need evidence related to a particular incident, the ESD points them directly to relevant RSUs, saving bandwidth and reducing the time to gather critical artefacts.
- Scalable Implementation: Each ESD node manages metadata for a specific geographic sector or set of RSUs, making the discovery process more efficient than a purely centralised approach.
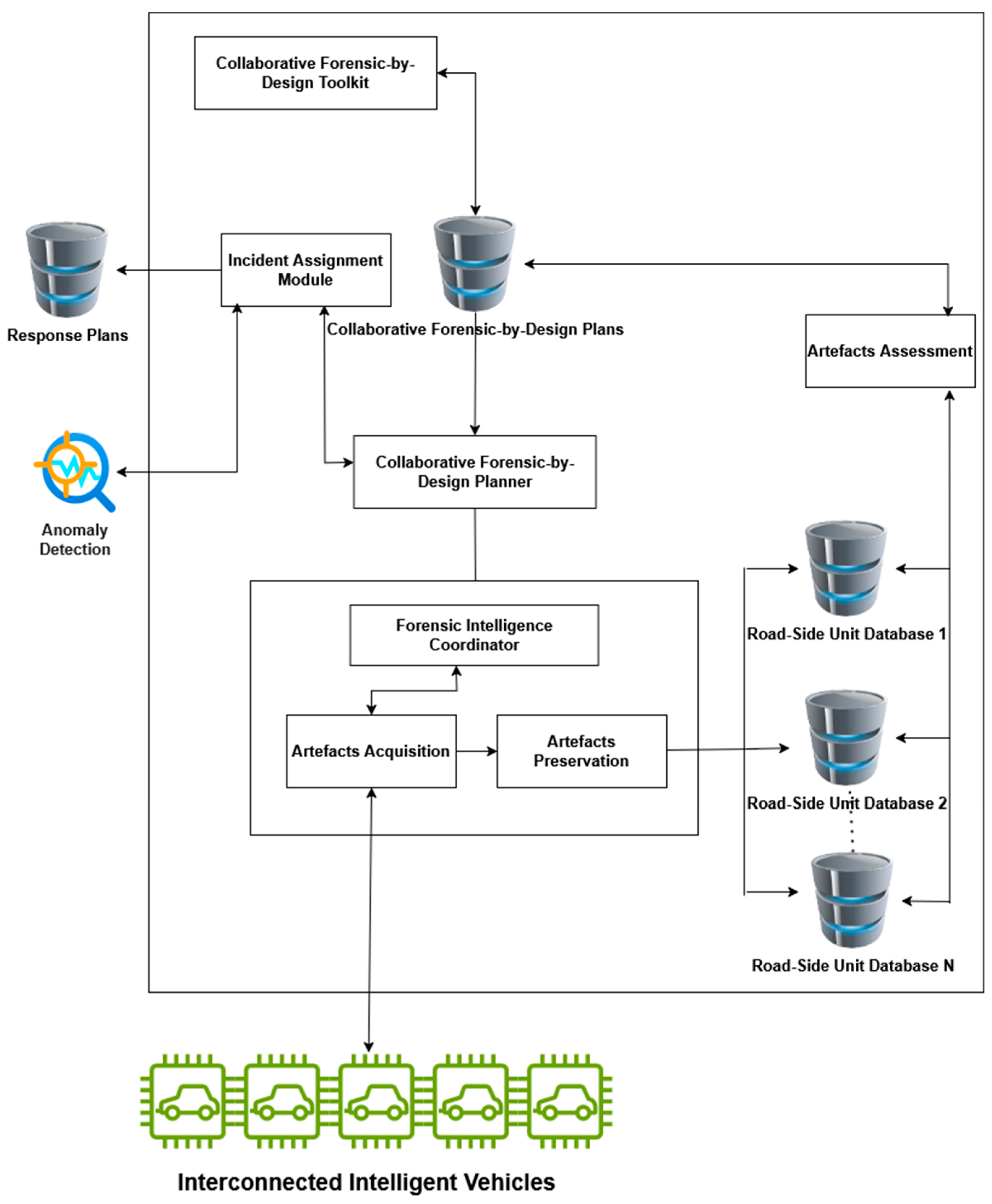
5.3. CFbD Modules
- (1)
- Incident Assignment Module
- Responsibility for Incident Assignation: The module gathers additional information from the IoV environment to build a detailed profile of the incident. It identifies critical attributes such as the type of incident (for example, system manipulation or sensor interference), which IoV components have been compromised, and any likelihood of the incident propagating throughout the network.
- Outcome and Information Flow: Once sufficient details have been collected and analysed, the module sends the outcome of its assessment to the CFbD planner component, ensuring that a tailored forensic plan can be developed. In parallel, it forwards insights to the mitigation component so that prompt and targeted response strategies may be initiated.
- (2)
- CFbD Planner
- Composition of Digital Forensics Plans: A plan is segmented into discrete digital forensic activities—tasks essential for evidence collection. These activities are housed within an internal repository named the CFbD Plans Repository, where they are updated and retrieved as required.
- Preparation and Cost Efficiency: The module’s main goal is to anticipate events that are inherently unpredictable whilst ensuring that evidence is captured with minimal disruption to everyday IoV functions. It balances the costs of response, recovery, and investigation, striving to preserve normal traffic operations and safety measures during forensic work.
- (3)
- Forensic Intelligence Coordinator
- Artefacts Acquisition: Acting as an interface to the broader IoV infrastructure, this sub-module manages the collection of incident-specific data according to the objectives of the forensics plan. It harvests both network data (including packet flows and communication traces) and host data (captured from vehicle systems, roadside sensors, or other relevant sources). By pinpointing where and how to gather data, artefacts acquisition ensures that evidence is amassed swiftly and methodically.
- Artefact Preservation: After data are gathered, they are timestamped and securely stored within the roadside unit database or an equivalent secure repository. This sub-module maintains the chain of custody, verifying that no alterations occur once the data are ingested. It also enforces checks on evidence integrity and manages access permissions to safeguard the data against unauthorised changes.
- (4)
- CFbD Toolkit
- Ease of Use and Security: The interface prioritises clarity, providing intuitive navigation. At the same time, it integrates robust security controls, allowing only authorised investigators to make substantial changes to existing plans. By merging simplicity with security, the module encourages effective collaboration and governance over critical investigative tasks.
- (5)
- Artefacts Assessment
- Evidence Reconstruction: It reassembles the collected digital artefacts linked to the incident for deeper scrutiny. By correlating data across multiple sources (such as various roadside units or vehicle logs), investigators can establish chronological order, root cause, and contextual factors shaping the incident. This reconstructed viewpoint is indispensable for clarifying how the incident emerged and progressed, enabling more accurate assignments and potential legal follow-up.
- Assessment of Selected Roadside Units: It evaluates the reliability and performance of roadside units that contributed evidence. The factors considered include their confidence rank and historical success rates in providing accurate data. Where any points of failure arise or insufficient insights are detected, investigators can use this knowledge to suggest improvements to the CFbD plans, ensuring that future evidence gathering is better supported and more robust. The feedback gleaned from the artefacts assessment process is distributed to external services for further updates, ensuring that the IoV ecosystem remains resilient and continuously improves its forensic capabilities.
6. CFPEA’s Features as a Collaborative Forensic Platform
6.1. Foundational Criteria for a Forensically Sound Platform
6.2. Driver Empowerment and Non-Proprietary Formats
6.3. Hybrid P2P System
Core Use Cases and Stakeholders: Investigation of Road Crimes
- Crime Solving: Investigators can collect location-specific evidence from vehicles near the crime scene at the relevant time. This may include still images, video recordings, or sensor logs indicating suspicious or illegal activities.
- Insurance Claims: In cases of car accidents or fraudulent claims, insurance firms rely on the collected artefacts to validate or challenge the narratives of involved parties, assessing liability, damage scope, or potential deception.
- Accurate Attribution: Correlating data from multiple vehicles in real-time or post-incident allows investigators to pinpoint the individuals or malicious entities responsible for the crime. Such evidence may subsequently be shared with courts, law enforcement agencies, and corporate stakeholders.
- Law Enforcement: Gain immediate access to credible evidence from multiple vehicles, improving both speed and accuracy in case resolution.
- Insurance Companies: Confirm or dispute claims using digitally timestamped, location-specific data.
- Government Institutions: Address broader security and regulatory concerns. For instance, traffic management authorities might glean insights into road safety hazards.
- Industries and Legal Professionals: Defence lawyers or industry-led investigators can scrutinise datasets on behalf of clients, ensuring the cross-verification of collected evidence.
6.4. Privacy Concerns in CFPEA Framework
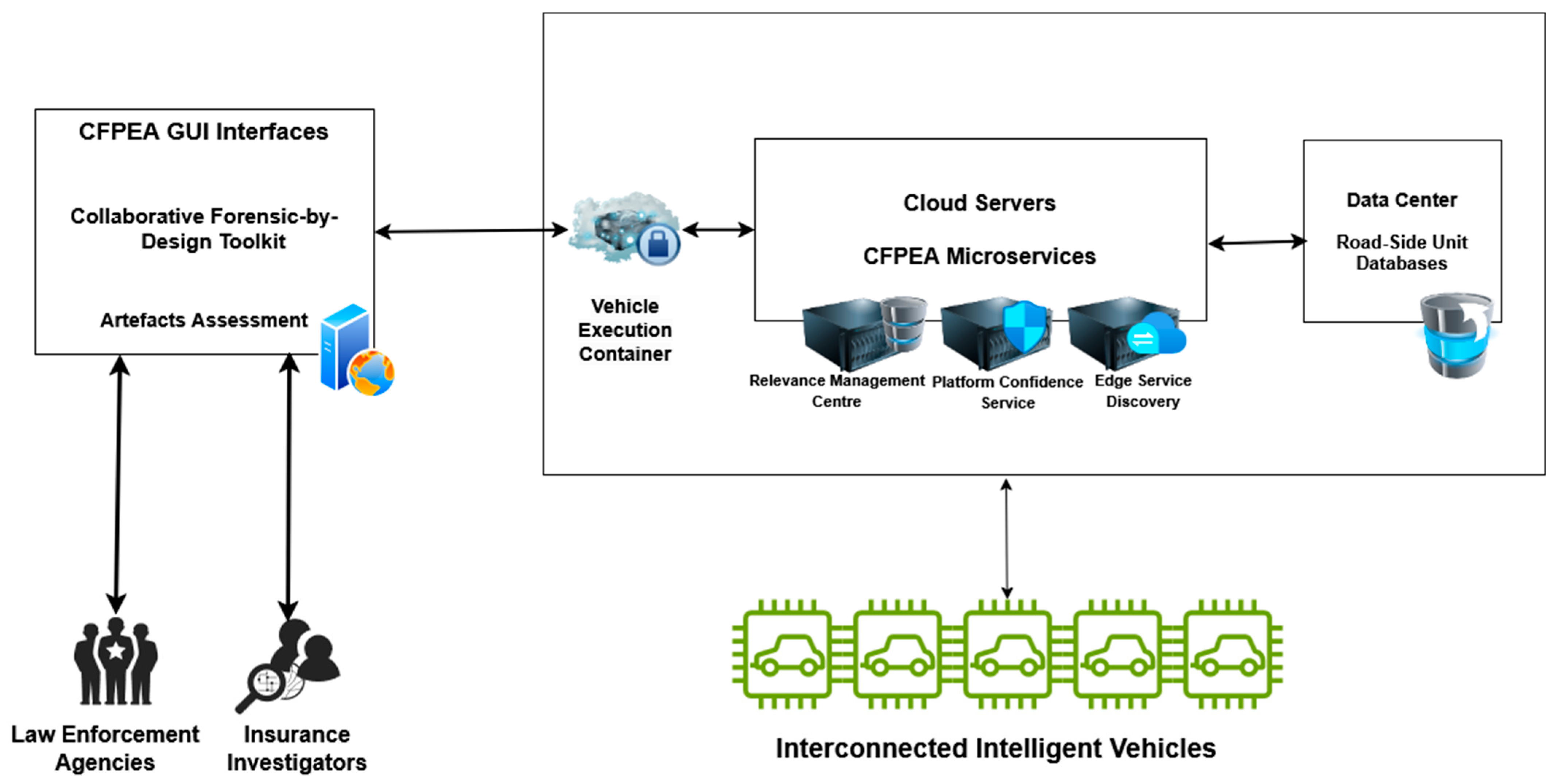
7. Operational Flow of CFPEA Core Components
- Vehicle Execution Container (VEC)
- Edge Service Discovery (ESD)
- Roadside Units (RSUs) and Driver Participation
- Platform Confidence Service (PCS)
- Relevance Management Centre (RMC)
- The Forensic Investigator
8. Digital Artefact Workflows in CFPEA
9. Discussion
9.1. Dual Purpose: Legal and Technological
- Legal Perspective
- Goal: Ensure that any gathered data (e.g., sensor readings, dashcam footage, network logs) adhere to rigorous forensic standards.
- Chain of Custody: Every artefact is securely preserved and timestamped, ensuring that it remains admissible for legal proceedings.
- Structured Approach: From the time an incident is assigned to the composition of a forensic plan, CFbD provides a systematic method to verify facts and enable accurate incident reconstruction.
- Technological Perspective
- Continuous Evolution: CFbD consults and updates a repository of proven digital forensic plans, enabling data-driven improvements and innovative strategies for evidence collection.
- Incident Mitigation: Beyond gathering legal-grade evidence, CFbD also guides the coordinated containment of incidents. By leveraging past documented experiences, the mechanism can swiftly recommend how to address threats and secure necessary data.
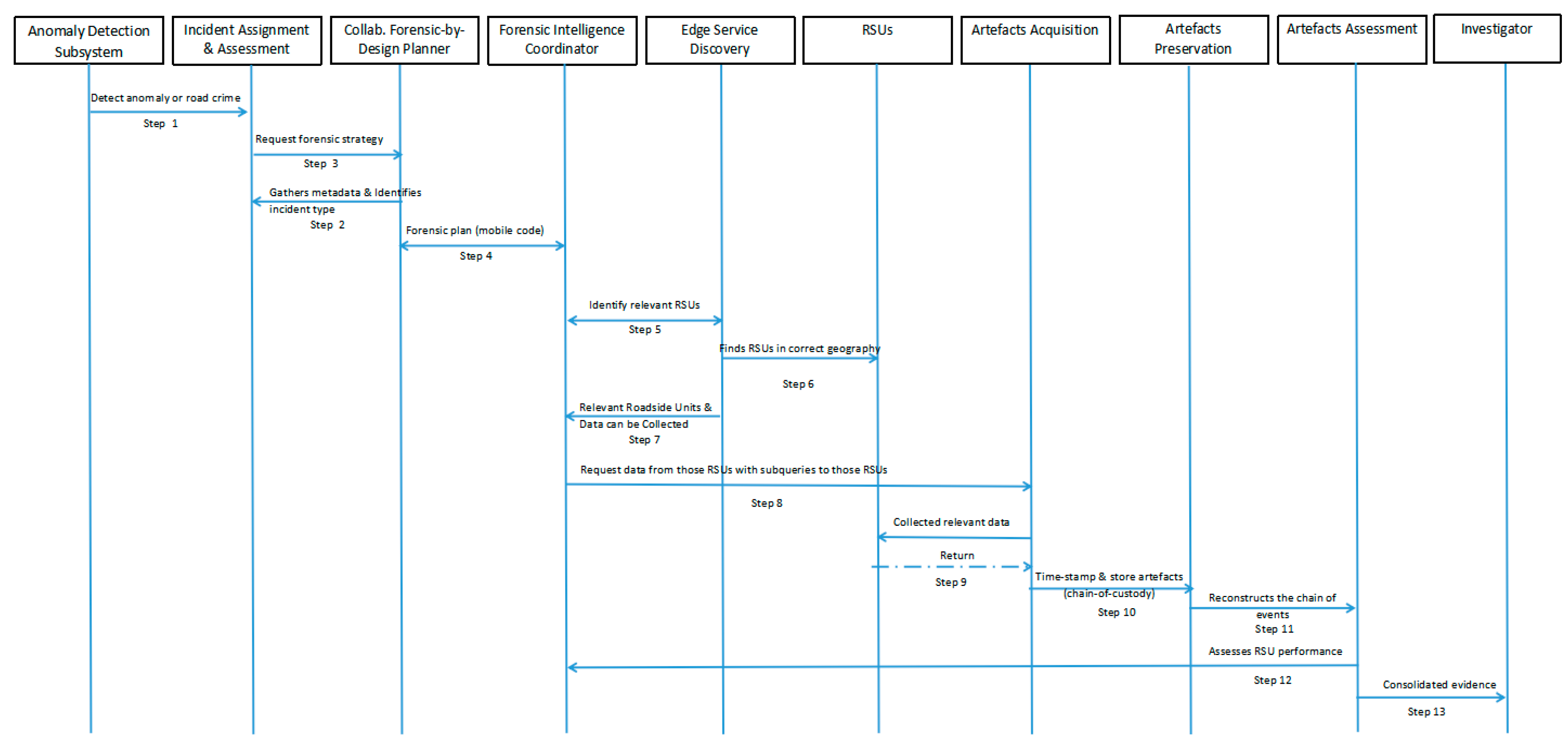
9.2. Key Phases in the CFbD Mechanism
- Incident Assignation
- ▪
- Purpose: Correlate details (e.g., location, type of event, potential risk level) with an appropriate investigative path.
- ▪
- Outcome: Ensure that the incident is assigned to the most relevant forensic modules, setting the stage for effective data collection.
- 2.
- Incident Attribution
- ▪
- Purpose: Determine the nature and origin of the incident (e.g., sensor malfunction or a deliberate crash).
- ▪
- Outcome: Accurate attribution shapes the severity of the response and identifies which data sources need to be targeted.
- 3.
- Forensic Strategy Composition
- ▪
- Purpose: Draw upon the CFPEA’s repository of pre-configured strategies for evidence collection.
- ▪
- Outcome: A tailored forensic plan is selected or adapted to fit the incident’s unique context (vehicles, roadside units, external data sources).
- 4.
- Plan Execution
- ▪
- Purpose: Convert the finalised plan into mobile code or executable instructions, orchestrating data collection.
- ▪
- Key Consideration: Driver consent and user privacy are integrated, ensuring compliance with legal and ethical standards.
- 5.
- Artefact Preservation
- ▪
- Purpose: Store collected evidence securely (e.g., in dedicated repositories or the Vehicle Execution Container).
- ▪
- Outcome: Timestamps, checksums, and access logs are maintained to preserve chain of custody.
- 6.
- Evidence Reconstruction and Verification
- ▪
- Purpose: Examine the gathered artefacts to create a chronological account of the event.
- ▪
- Outcome: In cases of incomplete or inconsistent data, further collection may be triggered, or trust scores for unreliable data sources may be adjusted.
9.3. Importance of Timing and Artefact Availability
- Volatile Data: IoV components often overwrite crucial information quickly. Swift action is essential to preserve time-sensitive logs and sensor readings.
- Immediate Response: Once an anomaly is detected, the system triggers the artefacts acquisition module to capture relevant data from vehicles, roadside units, and network logs.
- Adaptive Plans: If key data types are missing, CFPEA refines the active forensic plan in real time, ensuring comprehensive evidence collection.
9.4. Continuous Update of Plans
- Real-Time Refinement: CFPEA maintains an active repository of forensic strategies and outcomes, allowing for the quick identification of the best approach for capturing artefacts.
- Feedback Loop: Any shortfalls in a current plan lead to immediate updates, reinforcing the overall resilience of the IoV ecosystem.
9.5. Forward-Looking and Iterative Benefits
- Learning from Past Incidents: Every successful investigation is documented, enabling the more efficient handling of similar incidents in the future.
- Evolving Strategies: Effective techniques and valuable data sources are prioritised, while less effective methods are improved or replaced.
9.6. Wider Ecosystem Engagement
- Multi-Stakeholder Cooperation: CFPEA coordinates law enforcement, insurance investigators, drivers, and roadside units.
- Ethical and Forensic Integrity: Drivers are assured that private data are managed responsibly, while investigators benefit from streamlined detection, analysis, and response.
- Shared Insights: Lessons learned in one case inform better practices for all stakeholders, reinforcing a cycle of continuous improvement.
10. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ariffin, K.A.Z.; Ahmad, F.H. Indicators for maturity and readiness for digital forensic investigation in era of industrial revolution 4.0. Comput. Secur. 2021, 105, 102237. [Google Scholar] [CrossRef]
- Guide, I.H. Techniques into Incident Response. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=127a0e4555394b782949a3a6dbebff902ef433c4 (accessed on 23 January 2025).
- Tan, J. Forensic Readiness. 2001. Available online: https://home.engineering.iastate.edu/~guan/course/CprE-536/paperreadinglist920/forensic_readiness.pdf (accessed on 23 January 2025).
- ISO/IEC 27043:2015; Information Technology—Security Techniques—Incident Investigation Principles and Processes. ISO: Geneva, Switzerland, 2015; p. 30.
- Lagrasse, M.; Singh, A.; Munkhondya, H.; Ikuesan, A.; Venter, H. (Eds.) Digital forensic readiness framework for software-defined networks using a trigger-based collection mechanism. In Proceedings of the 15th International Conference on Cyber Warfare and Security, ICCWS, Norfolk, VA, USA, 12–13 March 2020. [Google Scholar]
- Alenezi, A.; Atlam, H.F.; Wills, G.B. Experts reviews of a cloud forensic readiness framework for organizations. J. Cloud Comput. 2019, 8, 11. [Google Scholar] [CrossRef]
- Kebande, V.R.; Ray, I. (Eds.) A generic digital forensic investigation framework for internet of things (IoT). In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; IEEE: New York, NY, USA, 2016; pp. 356–362. [Google Scholar]
- Ab Rahman, N.H.; Glisson, W.B.; Yang, Y.; Choo, K.-K.R. Forensic-by-design framework for cyber-physical cloud systems. IEEE Cloud Comput. 2016, 3, 50–59. [Google Scholar] [CrossRef]
- Mudau, P.P.; Venter, H.; Kebande, V.R.; Ikuesan, R.A.; Karie, N.M. (Eds.) Cursory view of IoT-forensic readiness framework based on ISO/IEC 27043 recommendations. In Proceedings of the International Conference on Emerging Applications and Technologies for Industry 4.0 (EATI’2020) Emerging Applications and Technologies for Industry 4.0, Uyo, Nigeria, 21–23 July 2020; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Forfot, A.D.; Østby, G. (Eds.) Digital forensic readiness in IoT-a risk assessment model. In Proceedings of the Intelligent Technologies and Applications: Third International Conference, INTAP 2020, Grimstad, Norway, 28–30 September 2020; Revised Selected Papers 3. Springer: Cham, Switzerland, 2021. [Google Scholar]
- Fagbola, F.I.; Venter, H.S. Smart digital forensic readiness model for shadow IoT devices. Appl. Sci. 2022, 12, 730. [Google Scholar] [CrossRef]
- ISO/IEC 27034-1:2011; Information Technology—Security Techniques—Application Security. ISO: Geneva, Switzerland, 2011.
- Jafri, M.S.; Raharjo, S.; Arief, M.R. Implementation of ACPO Framework for Digital Evidence Acquisition in Smartphones. CCIT J. 2022, 15, 82–105. [Google Scholar] [CrossRef]
- Watson, D.L.; Jones, A. Digital Forensics Processing and Procedures: Meeting the Requirements of ISO 17020, ISO 17025, ISO 27001 and Best Practice Requirements; Newnes: Oxford, UK, 2013. [Google Scholar]
- Zander, M. PACE (The Police and Criminal Evidence) Act 1984: Past, Present and Future. Nat’l L. Sch. India Rev. 2011, 23, 47. [Google Scholar]
- SWGDE. SWGDE Best Practices for Vehicle Infotainment and Telematics Systems 2016 23 June. Contract No.: Version 2.0. Available online: https://www.swgde.org/best-practices-for-vehicle-infotainment-and-telematics-systems-v3-0 (accessed on 23 January 2025).
- Samanta, P.; Jain, S. (Eds.) E-Witness: Preserve and prove forensic soundness of digital evidence. In Proceedings of the 24th Annual International Conference on Mobile Computing and Networking, New Delhi, India, 29 October–2 November 2018. [Google Scholar]
- Abassi, R. VANET security and forensics: Challenges and opportunities. Wiley Interdiscip. Rev. Forensic Sci. 2019, 1, e1324. [Google Scholar] [CrossRef]
- Al-Dhaqm, A.; Abd Razak, S.; Othman, S.H.; Ali, A.; Ghaleb, F.A.; Rosman, A.S.; Marni, N. Database forensic investigation process models: A review. IEEE Access 2020, 8, 48477–48490. [Google Scholar] [CrossRef]
- Prayudi, Y.; Sn, A. Digital chain of custody: State of the art. Int. J. Comput. Appl. 2015, 114. [Google Scholar] [CrossRef]
- McCarthy, M.; Seidl, M.; Mohan, S.; Hopkin, J.; Stevens, A.; Ognissanto, F.; Kathuria, N.; Cuerden, R. Access to In-Vehicle Data and Resources; Study Comissioned by European Commission CPR2419; European Commission: Brussels, Belgium, 2017; Volume 10. [Google Scholar]
- Zavvos, E.; Gerding, E.H.; Yazdanpanah, V.; Maple, C.; Stein, S. Privacy and Trust in the Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 10126–10141. [Google Scholar] [CrossRef]
- Alruwaili, F.F. Custodyblock: A distributed chain of custody evidence framework. Information 2021, 12, 88. [Google Scholar] [CrossRef]
- Elmisery, A.M. Collaborative Forensic Platform for Electronic Artefacts in the Internet of Vehicles. In Proceedings of the Future Technologies Conference (FTC), London, UK, 14–15 November 2024; Springer Nature: Cham, Switzerland, 2024; Volume 2. [Google Scholar] [CrossRef]
- Do, Q.; Martini, B.; Choo, K.-K.R. A forensically sound adversary model for mobile devices. PLoS ONE 2015, 10, e0138449. [Google Scholar] [CrossRef] [PubMed]
- Ripeanu, M. Peer-to-peer architecture case study: Gnutella network. In Proceedings of the Proceedings First International Conference on Peer-to-Peer Computing, Linkoping, Sweden, 27–29 August 2001; IEEE: New York, NY, USA, 2001. [Google Scholar]
- Elmisery, A.M.; Rho, S.; Botvich, D. A Fog Based Middleware for Automated Compliance with OECD Privacy Principles in Internet of Healthcare Things. IEEE Access 2016, 4, 8418–8441. [Google Scholar] [CrossRef]
- Elmisery, A.M.; Sertovic, M. (Eds.) Privacy Preserving Threat Hunting in Smart Home Environments; Springer: Singapore, 2020. [Google Scholar]
- Elmisery, A.M.; Rho, S.; Aborizka, M. A new computing environment for collective privacy protection from constrained healthcare devices to IoT cloud services. Clust. Comput. 2017, 22, 1611–1638. [Google Scholar] [CrossRef]
- Luehr, P.; Reilly, B. Data minimisation: A crucial pillar of cyber security. Cyber Secur. Peer-Rev. J. 2025, 8, 243–254. [Google Scholar] [CrossRef]
- Arora, R.; Du, H.; Kazmi, R.A.; Le, D.-P. Privacy-Enhancing Technologies for CBDC Solutions; Bank of Canada: Ottawa, ON, Canada, 2025. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elmisery, A.M.; Sertovic, M. Enabling Collaborative Forensic by Design for the Internet of Vehicles. Information 2025, 16, 354. https://doi.org/10.3390/info16050354
Elmisery AM, Sertovic M. Enabling Collaborative Forensic by Design for the Internet of Vehicles. Information. 2025; 16(5):354. https://doi.org/10.3390/info16050354
Chicago/Turabian StyleElmisery, Ahmed M., and Mirela Sertovic. 2025. "Enabling Collaborative Forensic by Design for the Internet of Vehicles" Information 16, no. 5: 354. https://doi.org/10.3390/info16050354
APA StyleElmisery, A. M., & Sertovic, M. (2025). Enabling Collaborative Forensic by Design for the Internet of Vehicles. Information, 16(5), 354. https://doi.org/10.3390/info16050354




