Trust-Enabled Framework for Smart Classroom Ransomware Detection: Advancing Educational Cybersecurity Through Crowdsourcing
Abstract
1. Introduction
- A novel trust-based crowdsourcing framework specifically designed for ransomware detection and mitigation in smart classroom environments.
- An evaluation of the framework’s effectiveness when implemented with two different trust management algorithms, providing insights into the impact of trust computation strategies on ransomware detection.
- A comprehensive analysis of the framework’s performance under varying levels of network compromise, demonstrating its resilience against malicious activities.
- Insights into the application of crowdsourced cybersecurity measures in educational settings, contributing to the development of more robust protection strategies for smart learning environments.
2. Related Work
2.1. Trust Management Systems
2.2. Crowdsourcing in Cybersecurity
2.3. Trust Management in Crowdsourcing Systems
2.4. Ransomware Detection and Mitigation
3. System Design
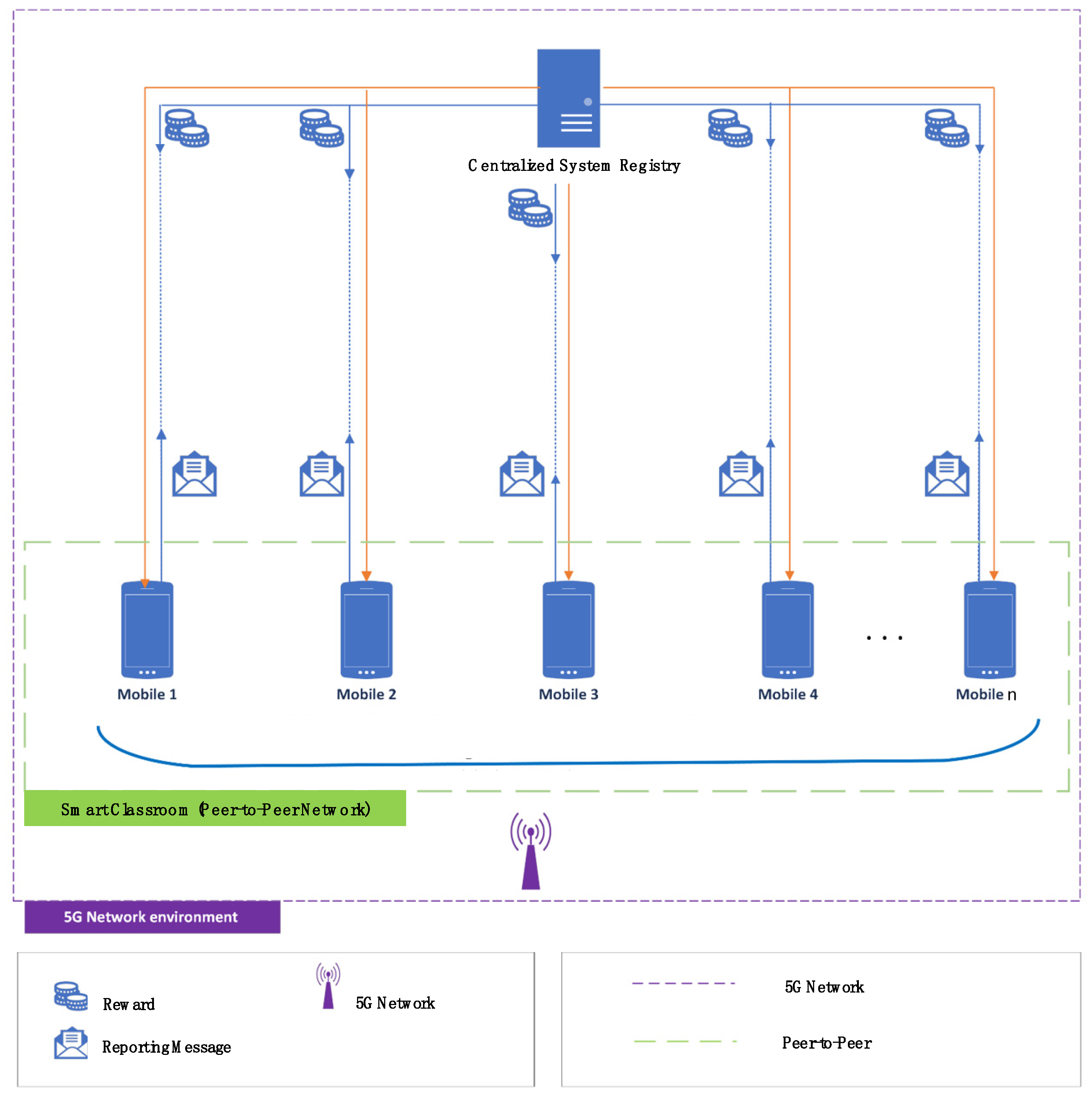
3.1. Key Components
- Smart devices: Represented by mobile devices numbered 1 through n, these are the classroom devices (e.g., student tablets, teacher computers) running a background monitoring application. This application specifically checks for ransomware-related activities, including the following:
- Unusual file system activities (mass file renaming or encryption);
- Attempts to delete shadow copies or disable system restore;
- Communication with known ransomware C&C servers;
- Presence of ransomware-related files or processes.
- P2P communication: The dotted green line represents a P2P communication system. The devices communicate with each other in a P2P communication manner, allowing direct information sharing and collaboration on threat detection among devices.
- Central System Registry: It disseminates updates and instructions and maintains an updated database of known ransomware signatures, behaviors, and C&C servers. The registry serves as the hub for data collection, analysis, and management.
3.2. Trust Framework
- Reporting Messages: Devices send these messages to the system registry when they detect suspicious activities. These messages contain details about the observed behavior, including timestamps and specific indicators of potential ransomware activity [16].
- Rewards: The system uses a non-monetary, reputation-based reward system [25]. Rewards can be positive (increasing trustworthiness) or negative (penalties decreasing trustworthiness).
- Trustworthiness Scores: each device is assigned a score that reflects its reliability in providing accurate threat information.
- Trust Threshold: a preset value used by the system registry to determine whether a reporting message from a device is credible and should be acted upon [26].
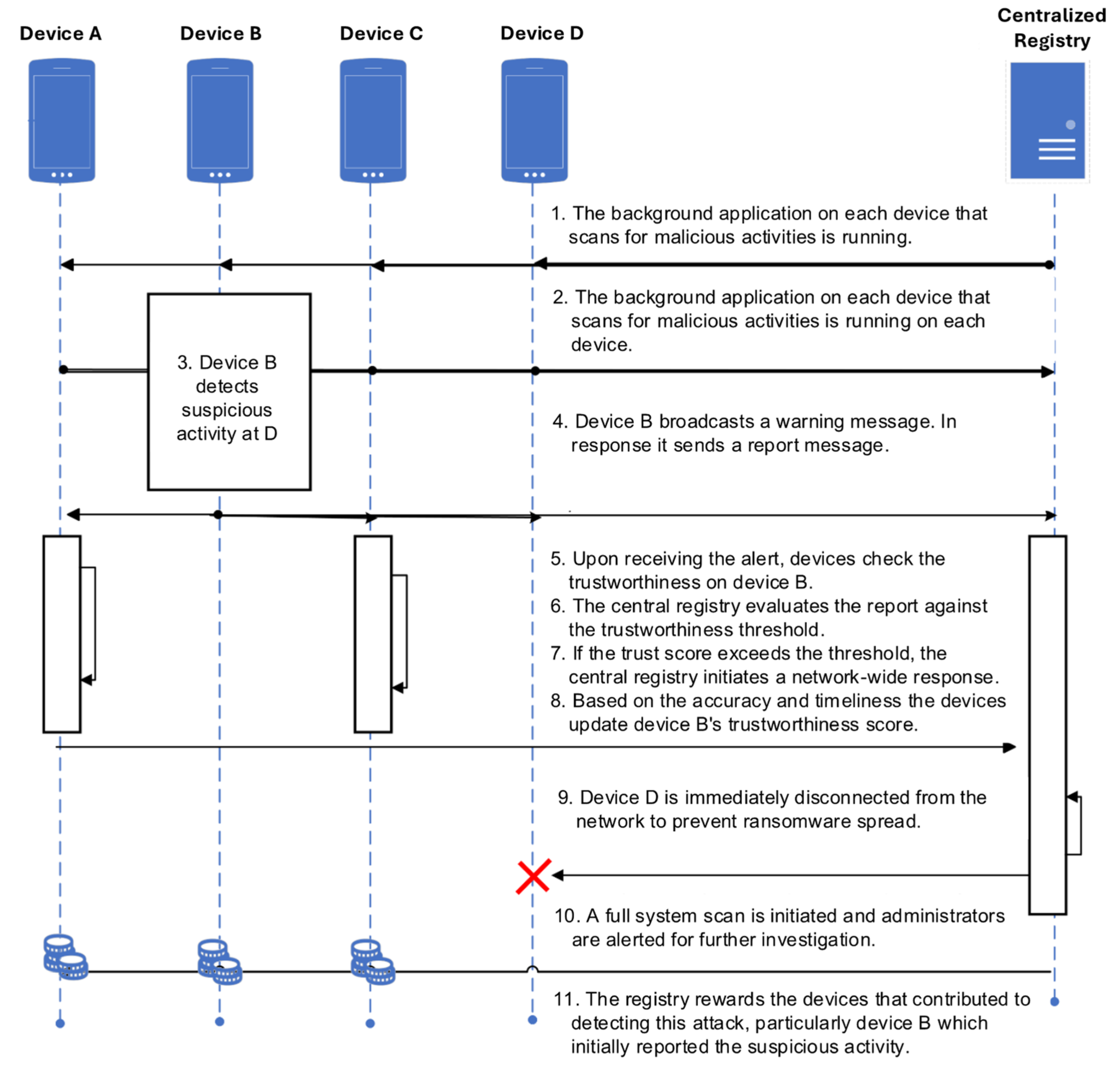
3.3. Operational Scenario
- A phishing URL is sent to the network, leading to device D becoming infected with ransomware;
- Other devices in the network are continuously monitoring network activities;
- Device B detects suspicious behavior on device D;
- Device B broadcasts this information to other devices and the central system registry;
- Upon receiving the alert, other network devices implement immediate precautionary measures;
- Based on the accuracy and timeliness of the report, the devices update device B’s trustworthiness score;
- The central registry evaluates the report against the trustworthiness threshold;
- If the report’s trust score exceeds the threshold, the central registry initiates a network-wide response.
4. Evaluation Methodology
- is the trust score of peer i
- represents the normalized local trust score from peer j to i
- is the global trust score of peer i
- T(A,B) is the trust relationship from peer A to peer B
- b: (belief) represents positive trust feedback
- d: (disbelief) represents negative trust feedback
- u: (uncertainty) represents a lack of sufficient data
- Honesty = 1.0 → A user with an honesty value of exactly 1.0 is classified as a fully trusted entity (good peer).
- Cleanup ≥ 90% → A user with at least 90% cleanup behavior is classified as a trusted participant, meaning they frequently remove malicious files and engage honestly.
- Honesty ≤ 0.0 → A user with 0.0 or lower honesty is categorized as Purely Malicious or Feedback Malicious, indicating untrustworthy behavior.
- Honesty > 0.0 but <1.0 → Users with an honesty score between 0 and 1.0 are classified as potentially deceptive entities, such as Malicious Providers who contribute to harmful activities while maintaining some degree of honesty.
5. Results and Discussion
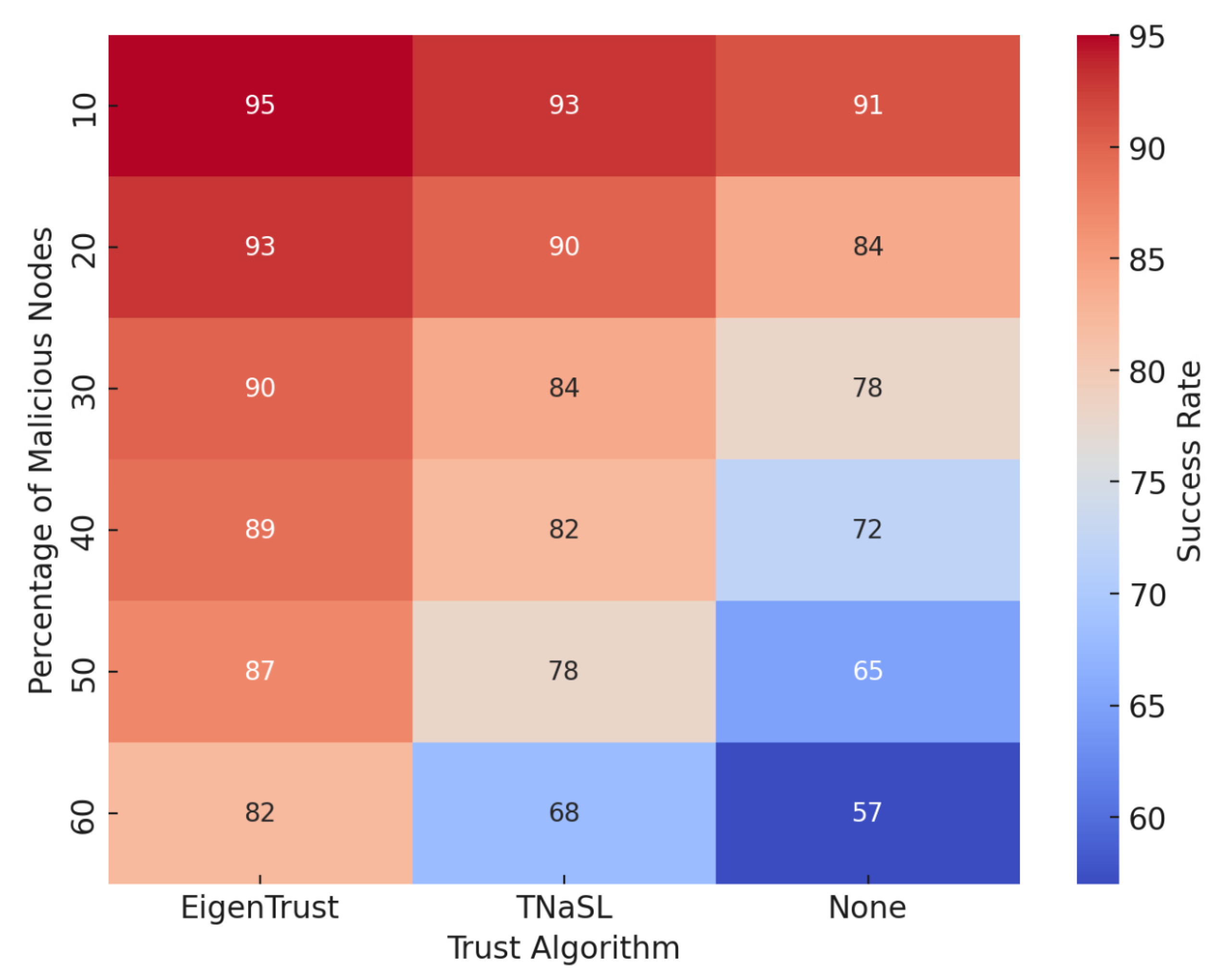
5.1. Success Rate
5.2. Accuracy
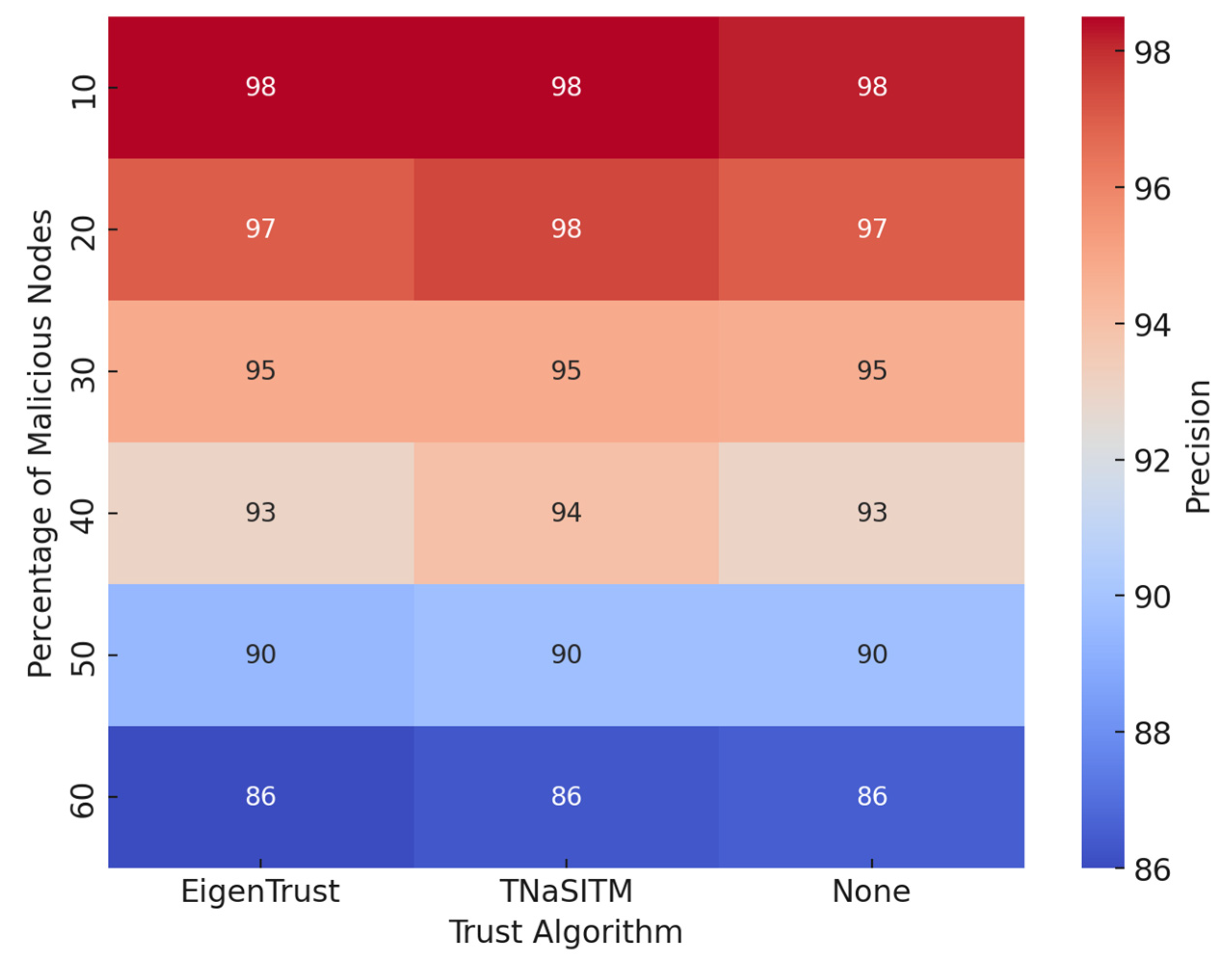
5.3. Precision
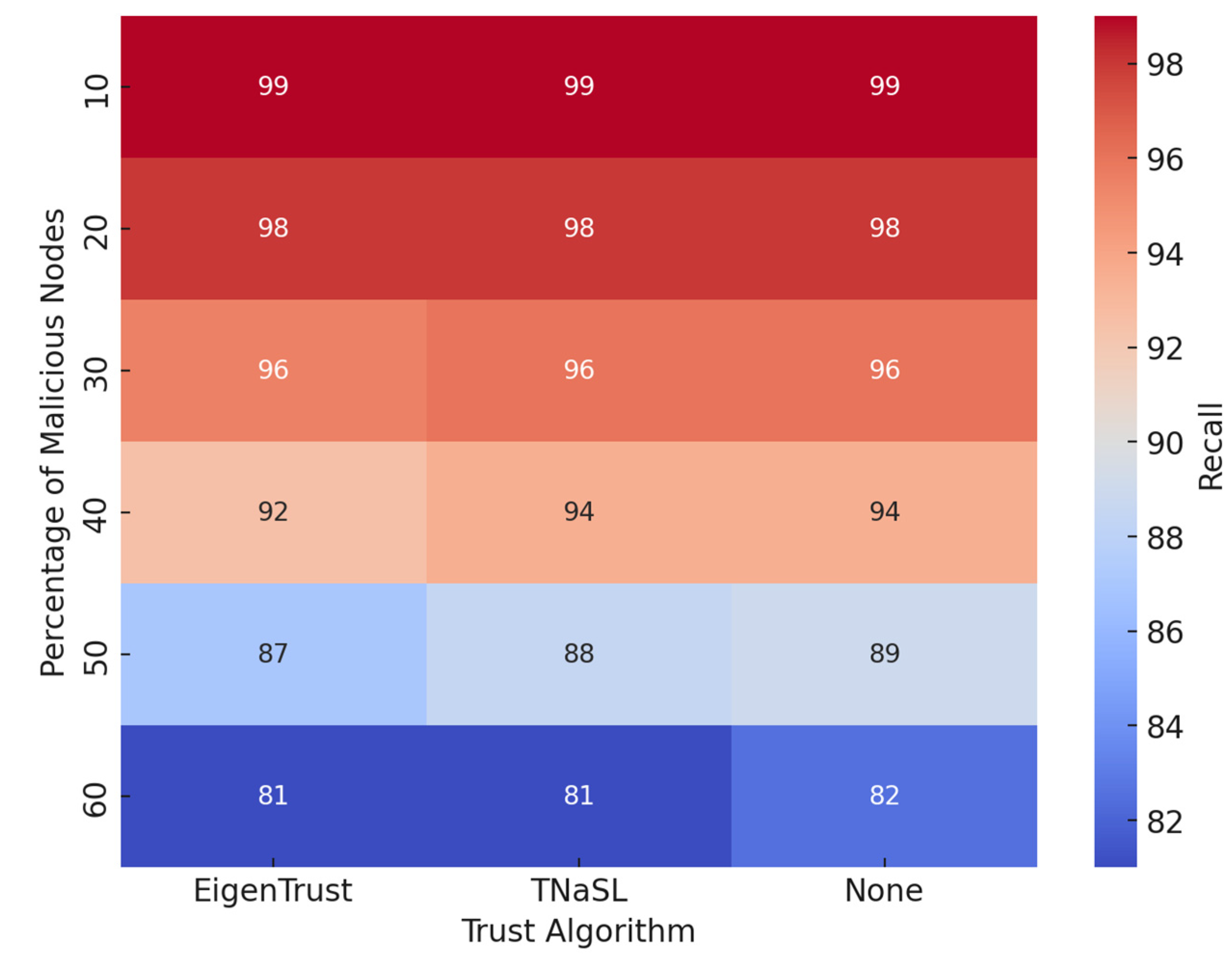
5.4. Recall
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ismail, N. Crowdsourcing Cyber Defence Is Now a Necessity. 2022. Available online: https://www.information-age.com/crowdsourcing-cyber-defence-necessity-6710 (accessed on 10 October 2024).
- Ransomware Attacks on Schools: ‘Dirty, Rotten Scoundrels’ Stop Online Learning, SecureWorld. Available online: https://www.secureworld.io/industry-news/ransomware-attacks-on-schools-online-learning (accessed on 15 June 2024).
- Alert (AA22-040A): People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices, Cybersecurity and Infrastructure Security Agency (CISA). Available online: https://www.cisa.gov/uscert/ncas/alerts/aa22-040a (accessed on 10 October 2024).
- Nieto, A.; Acien, A.; Fernandez, G. Crowdsourcing Analysis in 5G IoT: Cybersecurity Threats and Mitigation. Mob. Netw. Appl. 2019, 24, 881–889. [Google Scholar] [CrossRef]
- Ye, B. Trust Management in Crowdsourcing Environments. Ph.D. Thesis, Macquarie University, Sydney, Australia, 2018. [Google Scholar]
- Kamvar, S.D.; Schlosser, M.T.; Garcia-Molina, H. The EigenTrust Algorithm for Reputation Management in P2P Networks. In Proceedings of the 12th International Conference on World Wide Web (WWW 2003), ACM, Budapest, Hungary, 20–24 May 2003; pp. 640–651. [Google Scholar] [CrossRef]
- Jøsang, A.; Hayward, R.; Pope, S. Trust network analysis with subjective logic. In Proceedings of the 29th Australasian Computer Science Conference—Volume 48 (ACSC ’06), Hobart, Australia, 16–19 January 2006; pp. 85–94. [Google Scholar]
- Lu, K.; Wang, J.; Xie, L.; Zhen, Q.; Li, M. An EigenTrust-based Hybrid Trust Model in P2P File Sharing Networks. Procedia Comput. Sci. 2016, 94, 366–371. [Google Scholar] [CrossRef][Green Version]
- Al-Otaiby, N.; Alhindi, A.; Kurdi, H. AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks. Sensors 2022, 22, 533. [Google Scholar] [CrossRef] [PubMed]
- Cotronei, M.; Giuffre, S.; Marcianò, A.; Rosaci, D.; Sarnè, M.L.G. Improving the Effectiveness of Eigentrust in Computing the Reputation of Social Agents in Presence of Collusion. Int. J. Neural Syst. 2024, 34, 2350063. [Google Scholar] [CrossRef] [PubMed]
- Kalala, K.; Feng, T.; Kiringa, I. EigenTrust for Hierarchically Structured Chord. Security and Trust Management; Springer: Berlin/Heidelberg, Germany, 2017; pp. 203–212. [Google Scholar] [CrossRef]
- Chamba-Eras, L.; Arruarte, A.; Elorriaga, J.A. Bayesian Networks to Predict Reputation in Virtual Learning Communities. In Proceedings of the 2016 IEEE Latin American Conference on Computational Intelligence (LA-CCI), Cartagena, Colombia, 2–4 November 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Mikhailovitch, N.M.; Yurievitch, D.K. Reputation Systems in E-commerce: Comparative Analysis and Perspectives to Model Uncertainty Inherent in Them. Proc. Inst. Syst. Program. RAS 2019, 31, 99–122. [Google Scholar]
- Bellaj, B.; Ouaddah, A.; Mezrioui, A.; Crespi, N.; Bertin, E. GBTrust: Leveraging Edge Attention in Graph Neural Networks for Trust Management in P2P Networks. In Proceedings of the 2023 IEEE 22nd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Exeter, UK, 1–3 November 2023; pp. 1272–1278. [Google Scholar]
- De Marchi, A.C.; Gregio, A.; Bonacin, R. Enhancing the creation of detection rules for malicious software through ontologies and crowdsourcing. In Proceedings of the 2017 IEEE 26th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Poznan, Poland, 21–23 June 2017. [Google Scholar] [CrossRef]
- Hu, J.; Lin, H.; Guo, X.; Yang, J. DTCS: An Integrated Strategy for Enhancing Data Trustworthiness in Mobile Crowdsourcing. IEEE Internet Things J. 2018, 5, 4663–4671. [Google Scholar] [CrossRef]
- Jayasinghe, U.; Otebolaku, A.; Um, T.-W.; Lee, G.M. Data centric trust evaluation and prediction framework for IOT. In Proceedings of the 2017 ITU Kaleidoscope: Challenges for a Data-Driven Society (ITU K), Nanjing, China, 27–29 November 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Zhou, J.; Jin, X.; Yu, L.; Xue, L.; Ren, Y. TruthTrust: Trust Inference-Based Trust Management Mechanism on a Crowdsourcing Platform. Sensors 2021, 21, 2578. [Google Scholar] [CrossRef] [PubMed]
- Al-Zawi, B.; Wang, Q.; Shaw, P.; Sheltami, T.R.; Abdel-Maguid, M. Trustworthy Sensing for Crowd Management in Smart Cities. In Proceedings of the 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 25–28 June 2018. [Google Scholar]
- Li, S.; Da Xu, L.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Liu, W. Modeling ransomware spreading by a dynamic node-level method. IEEE Access 2019, 7, 142224–142232. [Google Scholar] [CrossRef]
- Khammas, B.M. Ransomware Detection using Random Forest Technique. ICT Express 2020, 6, 325–331. Available online: https://www.sciencedirect.com/science/article/pii/S2405959520304756 (accessed on 15 June 2024). [CrossRef]
- Masum, M.; Faruk, M.J.H.; Shahriar, H.; Qian, K.; Lo, D.; Adnan, M.I. Ransomware classification and detection with machine learning algorithms. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022. [Google Scholar]
- Alraizza, A.; Algarni, A. Ransomware detection using machine learning: A survey. Big Data Cogn. Comput. 2023, 7, 143. [Google Scholar] [CrossRef]
- Sehrawat, S.; Singh, D.D. Malware and malware detection techniques: A survey. Int. J. Res. Appl. Sci. Eng. Technol. 2022, 10, 3947–3953. [Google Scholar] [CrossRef]
- Brierley, C.; Pont, J.; Arief, B.; Barnes, D.; Hernandez-Castro, J. PaperW8: An IoT Bricking Ransomware Proof of Concept. In Proceedings of the ARES ’20: The 15th International Conference on Availability, Reliability and Security, New York, NY, USA, 25–28 August 2020. [Google Scholar] [CrossRef]
- QTM: P2P Trust Simulator. Real-Time and Embedded Systems Lab, University of Pennsylvania. Available online: https://rtg.cis.upenn.edu/qtm (accessed on 15 January 2024).
- Jøsang, A.; Ismail, R.; Boyd, C. A survey of trust and reputation systems for online service provision. Decis. Support Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]

| Trust Model | Strengths | Limitations | Complexity |
|---|---|---|---|
| EigenTrust | Efficient global trust computation; mitigates collusion; computationally lightweight [8]. | Relies on pre-trusted nodes, which may introduce centralization biases [10]. | O(k × n2); Where n = number of peers; k = number of iterations for convergence [6]. |
| TNA-SL | Models uncertainty in trust decisions; dynamically adapts trust scores [9]. | Higher computational overhead compared to EigenTrust [11]. | O(n) [7]. |
| Bayesian Inference Models | Strong in probabilistic trust prediction; well suited for long-term behavior analysis [12]. | Requires large historical datasets; struggles with real-time decision-making. | Depends on dataset size |
| Blockchain-based Reputation Systems | Tamper-proof trust management; decentralized reputation storage [13]. | High computational and storage overhead; slow consensus mechanisms hinder real-time responses [14]. | High (varies by chain and protocol used) |
| User Type | Cleanup | Honesty |
|---|---|---|
| Good Peers | 90–100% | 100% |
| Purely Malicious | 0–10% | 0% |
| Feedback Malicious | 90–100% | 0% |
| Malicious Provider | 0-10% | 100% |
| Accurate | Inaccurate | |
|---|---|---|
| Timely | True Positive (TP) “Good Peers” | False Positive (FP) “Feedback Malicious” |
| Slow | True Negative (TN) “Malicious Providers” | False Negative (FN) “Purely Malicious” |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ismail, Q.; Almutairi, S.; Kurdi, H. Trust-Enabled Framework for Smart Classroom Ransomware Detection: Advancing Educational Cybersecurity Through Crowdsourcing. Information 2025, 16, 312. https://doi.org/10.3390/info16040312
Ismail Q, Almutairi S, Kurdi H. Trust-Enabled Framework for Smart Classroom Ransomware Detection: Advancing Educational Cybersecurity Through Crowdsourcing. Information. 2025; 16(4):312. https://doi.org/10.3390/info16040312
Chicago/Turabian StyleIsmail, Qatrunnada, Shatha Almutairi, and Heba Kurdi. 2025. "Trust-Enabled Framework for Smart Classroom Ransomware Detection: Advancing Educational Cybersecurity Through Crowdsourcing" Information 16, no. 4: 312. https://doi.org/10.3390/info16040312
APA StyleIsmail, Q., Almutairi, S., & Kurdi, H. (2025). Trust-Enabled Framework for Smart Classroom Ransomware Detection: Advancing Educational Cybersecurity Through Crowdsourcing. Information, 16(4), 312. https://doi.org/10.3390/info16040312








